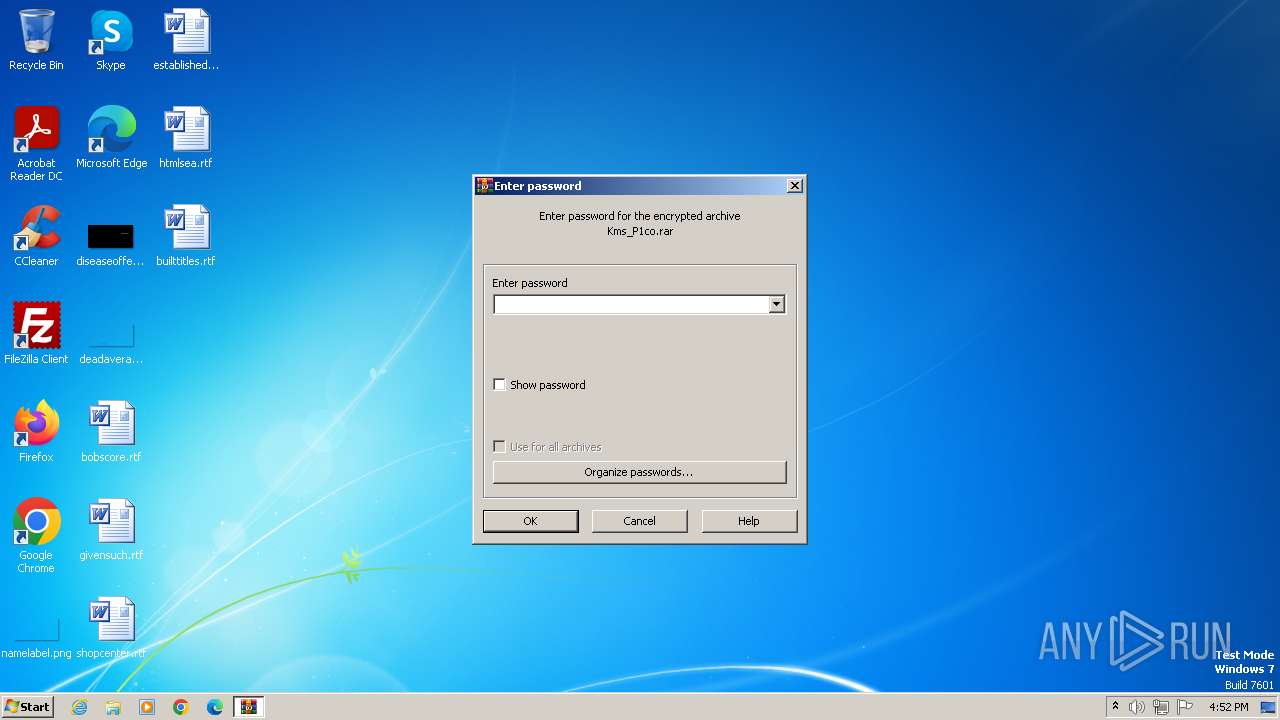
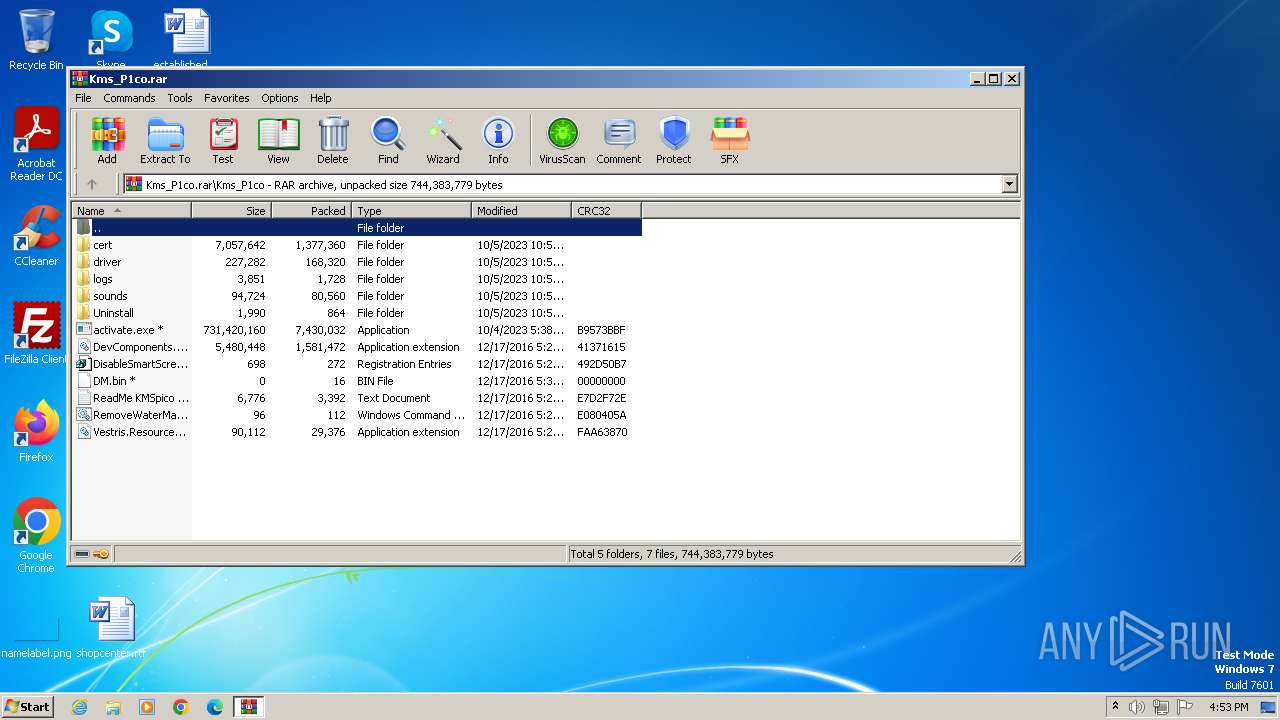
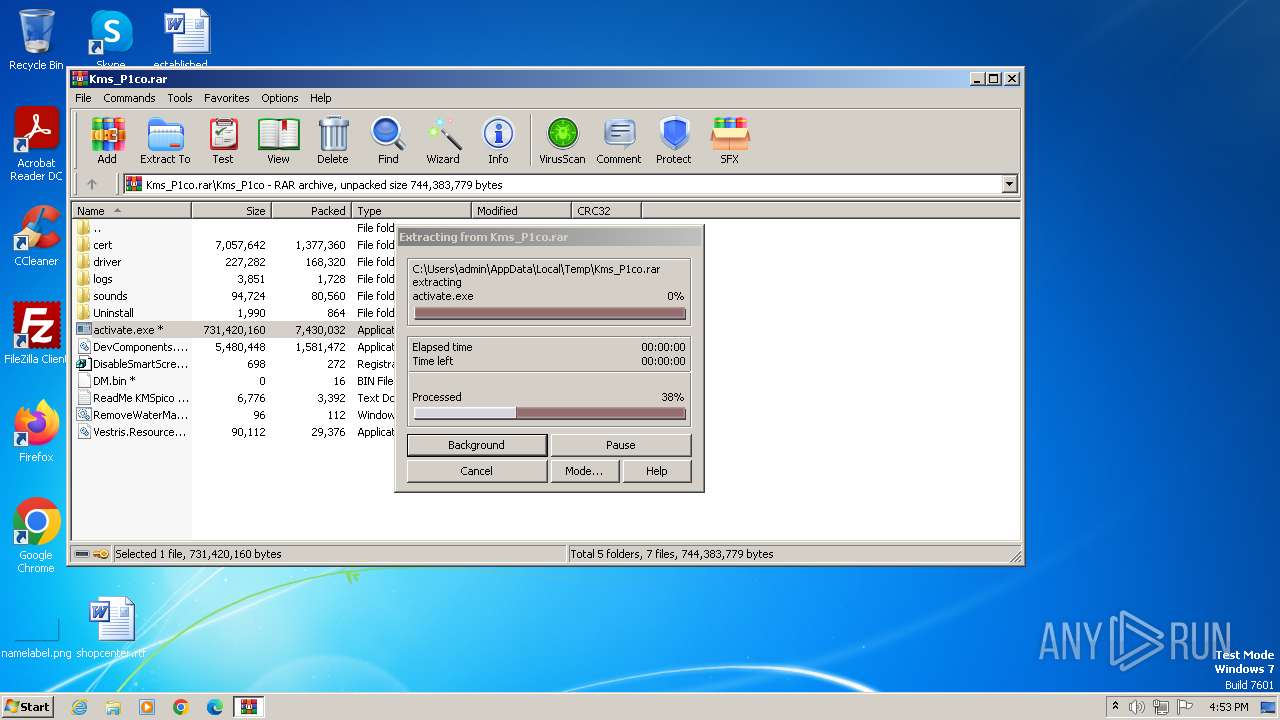
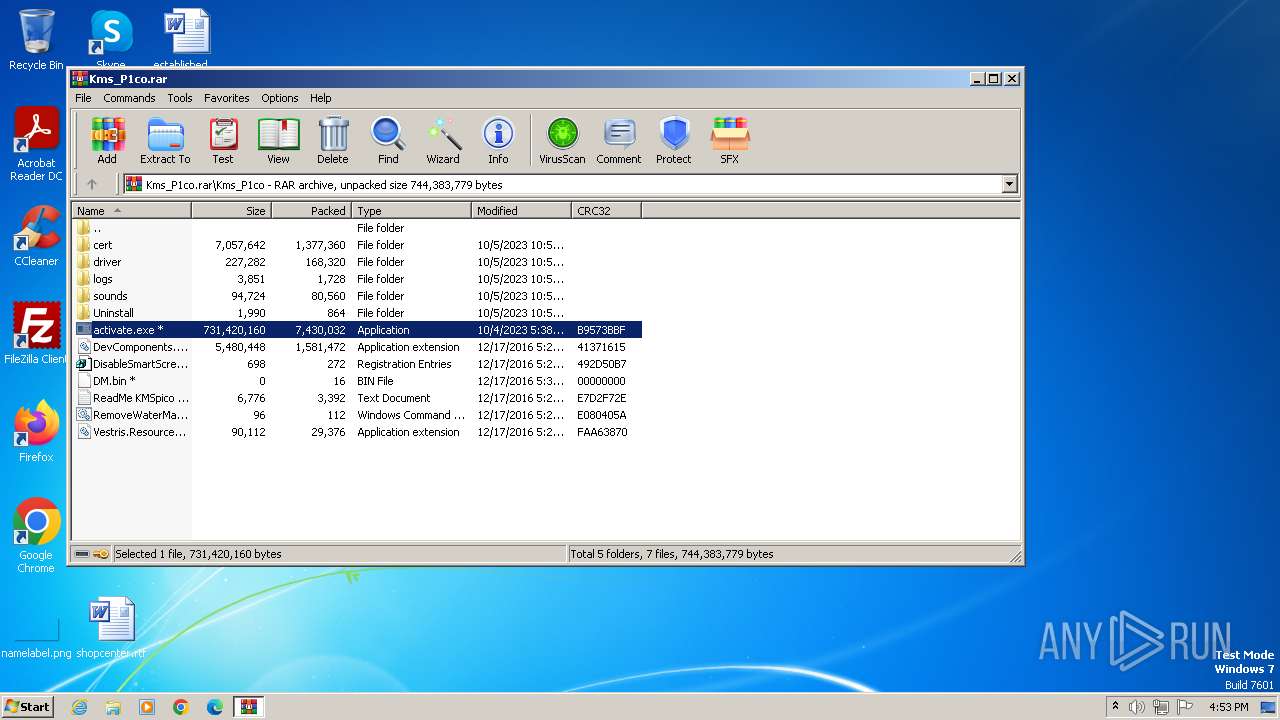
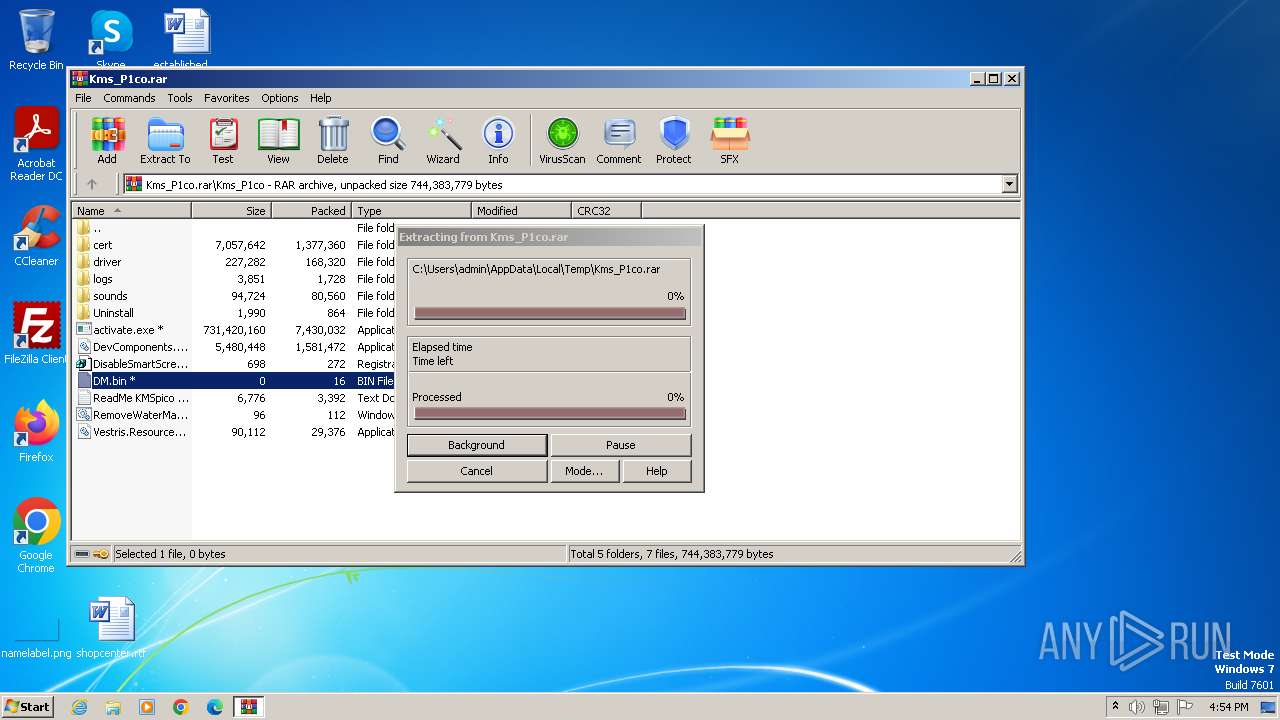
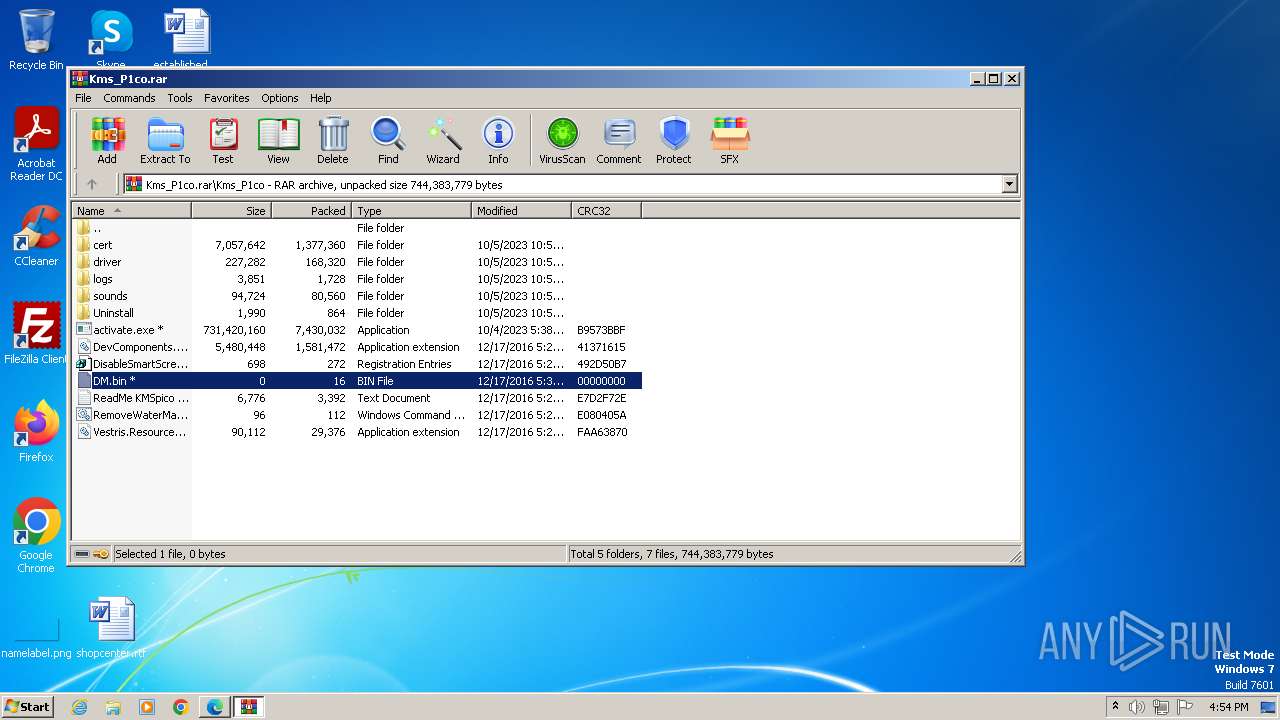
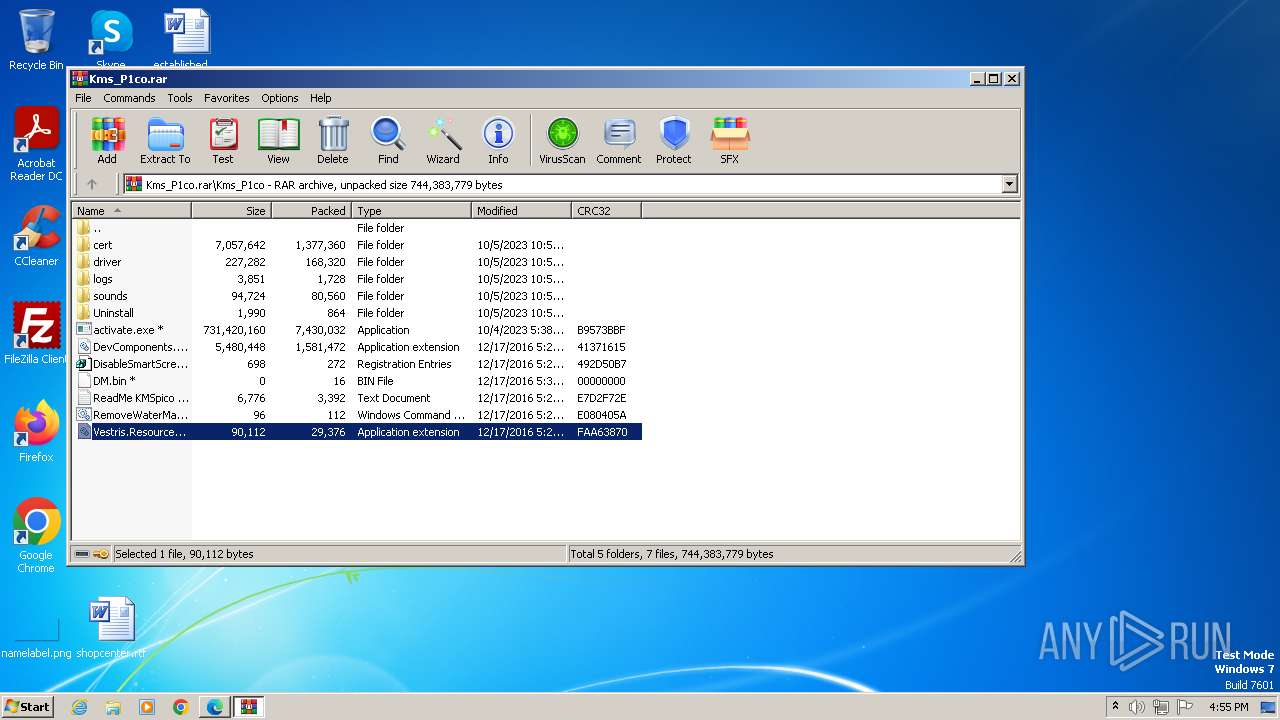
| File name: | Kms_P1co.rar |
| Full analysis: | https://app.any.run/tasks/3d28ed71-1b3d-47a3-b5ca-916c833f842e |
| Verdict: | Malicious activity |
| Threats: | CryptBot is an advanced Windows-targeting infostealer delivered via pirate sites with "cracked" software. It has been first observed in the wild in 2019. |
| Analysis date: | October 05, 2023, 15:52:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D60DAFB0433BFA2B680F794CF45F1C86 |
| SHA1: | 370F524E1781412D491E4F9ECC319831FEDF9A84 |
| SHA256: | FB6575B6281A746833EC4341BB8EF1DA5D5CCAAC0DD437746A1B923B4BA529AD |
| SSDEEP: | 98304:c9VR0H665vA6Wxyq5eFNiJwH3ci+HOMinV2jK/UBSauhj3JN9fKbgrZU6THHcH9q:B+yX1opfQBcimmLua09BQ |
MALICIOUS
Connects to the CnC server
- activate.exe (PID: 4076)
CRYPTBOT was detected
- activate.exe (PID: 4076)
Drops the executable file immediately after the start
- activate.exe (PID: 4076)
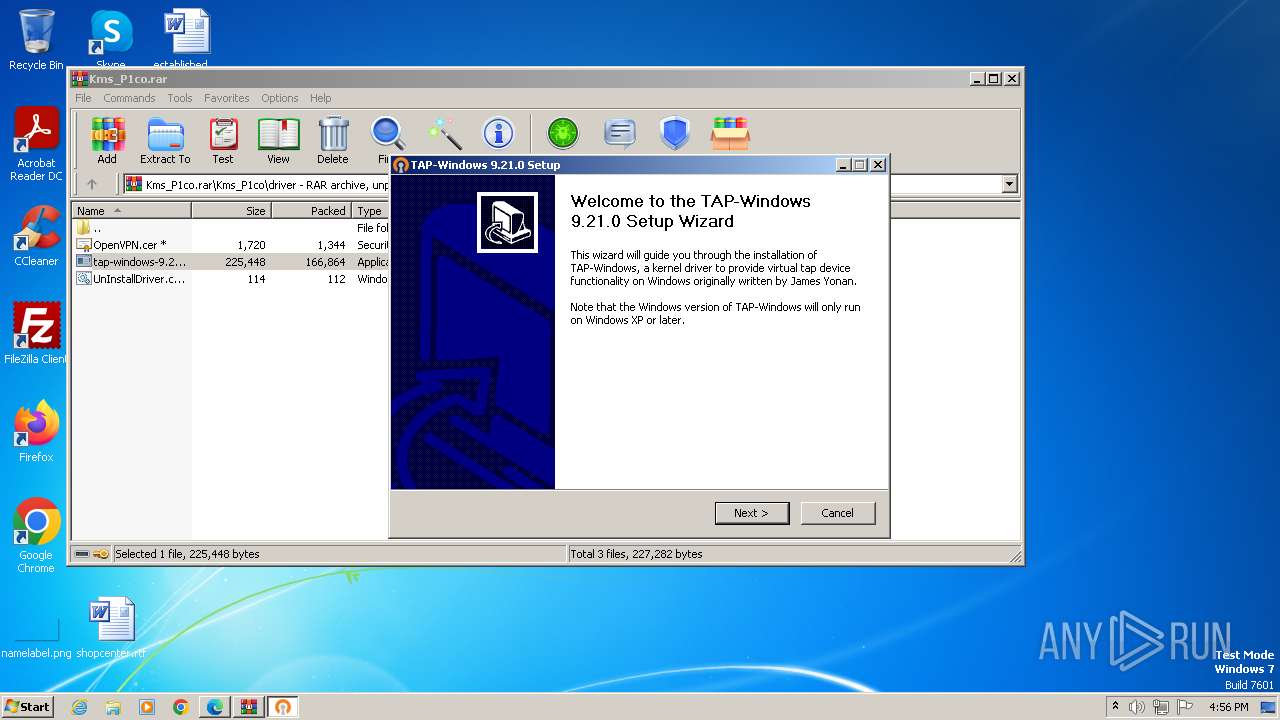
- tap-windows-9.21.0.exe (PID: 2512)
- devcon.exe (PID: 3388)
- drvinst.exe (PID: 3316)
- drvinst.exe (PID: 3228)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2372)
Application was dropped or rewritten from another process
- Gedapoko.exe (PID: 3324)
- tap-windows-9.21.0.exe (PID: 3140)
- tap-windows-9.21.0.exe (PID: 2512)
- devcon.exe (PID: 1284)
- devcon.exe (PID: 3388)
Actions looks like stealing of personal data
- activate.exe (PID: 4076)
Unusual connection from system programs
- rundll32.exe (PID: 3268)
Creates a writable file the system directory
- drvinst.exe (PID: 3316)
- drvinst.exe (PID: 3228)
SUSPICIOUS
Searches for installed software
- activate.exe (PID: 4076)
Starts CMD.EXE for commands execution
- activate.exe (PID: 4076)
- WinRAR.exe (PID: 1648)
Drops the AutoIt3 executable file
- activate.exe (PID: 4076)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 1648)
Reads the Internet Settings
- rundll32.exe (PID: 1480)
- activate.exe (PID: 4076)
- rundll32.exe (PID: 3268)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 1648)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 1648)
The process executes via Task Scheduler
- Gedapoko.exe (PID: 3324)
Malware-specific behavior (creating "System.dll" in Temp)
- tap-windows-9.21.0.exe (PID: 2512)
Drops a system driver (possible attempt to evade defenses)
- tap-windows-9.21.0.exe (PID: 2512)
- devcon.exe (PID: 3388)
- drvinst.exe (PID: 3316)
- drvinst.exe (PID: 3228)
Starts application with an unusual extension
- tap-windows-9.21.0.exe (PID: 2512)
The process creates files with name similar to system file names
- tap-windows-9.21.0.exe (PID: 2512)
Process drops legitimate windows executable
- msedge.exe (PID: 2648)
Reads security settings of Internet Explorer
- devcon.exe (PID: 3388)
Reads settings of System Certificates
- devcon.exe (PID: 3388)
- rundll32.exe (PID: 3332)
- rundll32.exe (PID: 3268)
Checks Windows Trust Settings
- devcon.exe (PID: 3388)
- drvinst.exe (PID: 3316)
- drvinst.exe (PID: 3228)
Creates files in the driver directory
- drvinst.exe (PID: 3316)
- drvinst.exe (PID: 3228)
Executes as Windows Service
- VSSVC.exe (PID: 3684)
INFO
Checks supported languages
- activate.exe (PID: 4076)
- activate.exe (PID: 4016)
- Gedapoko.exe (PID: 3324)
- tap-windows-9.21.0.exe (PID: 2512)
- devcon.exe (PID: 1284)
- ns2113.tmp (PID: 2008)
- ns2018.tmp (PID: 3768)
- devcon.exe (PID: 3388)
- drvinst.exe (PID: 3316)
- drvinst.exe (PID: 3228)
Reads product name
- activate.exe (PID: 4076)
Reads Environment values
- activate.exe (PID: 4076)
- drvinst.exe (PID: 3228)
Reads the computer name
- activate.exe (PID: 4076)
- tap-windows-9.21.0.exe (PID: 2512)
- devcon.exe (PID: 1284)
- devcon.exe (PID: 3388)
- drvinst.exe (PID: 3316)
- drvinst.exe (PID: 3228)
Checks proxy server information
- activate.exe (PID: 4076)
Creates files or folders in the user directory
- activate.exe (PID: 4076)
- rundll32.exe (PID: 3268)
Reads CPU info
- activate.exe (PID: 4076)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1648)
- msedge.exe (PID: 3272)
- msedge.exe (PID: 2648)
Reads the machine GUID from the registry
- activate.exe (PID: 4076)
- devcon.exe (PID: 3388)
- drvinst.exe (PID: 3316)
- drvinst.exe (PID: 3228)
Application launched itself
- msedge.exe (PID: 3272)
Reads mouse settings
- Gedapoko.exe (PID: 3324)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3268)
- rundll32.exe (PID: 3332)
Create files in a temporary directory
- tap-windows-9.21.0.exe (PID: 2512)
- devcon.exe (PID: 3388)
Loads dropped or rewritten executable
- tap-windows-9.21.0.exe (PID: 2512)
Creates files in the program directory
- tap-windows-9.21.0.exe (PID: 2512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
92
Monitored processes
45
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6cf6f598,0x6cf6f5a8,0x6cf6f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 396 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3344 --field-trial-handle=1244,i,12331054116738006116,14303850040422449046,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 592 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3864 --field-trial-handle=1244,i,12331054116738006116,14303850040422449046,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 876 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1276 --field-trial-handle=1244,i,12331054116738006116,14303850040422449046,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
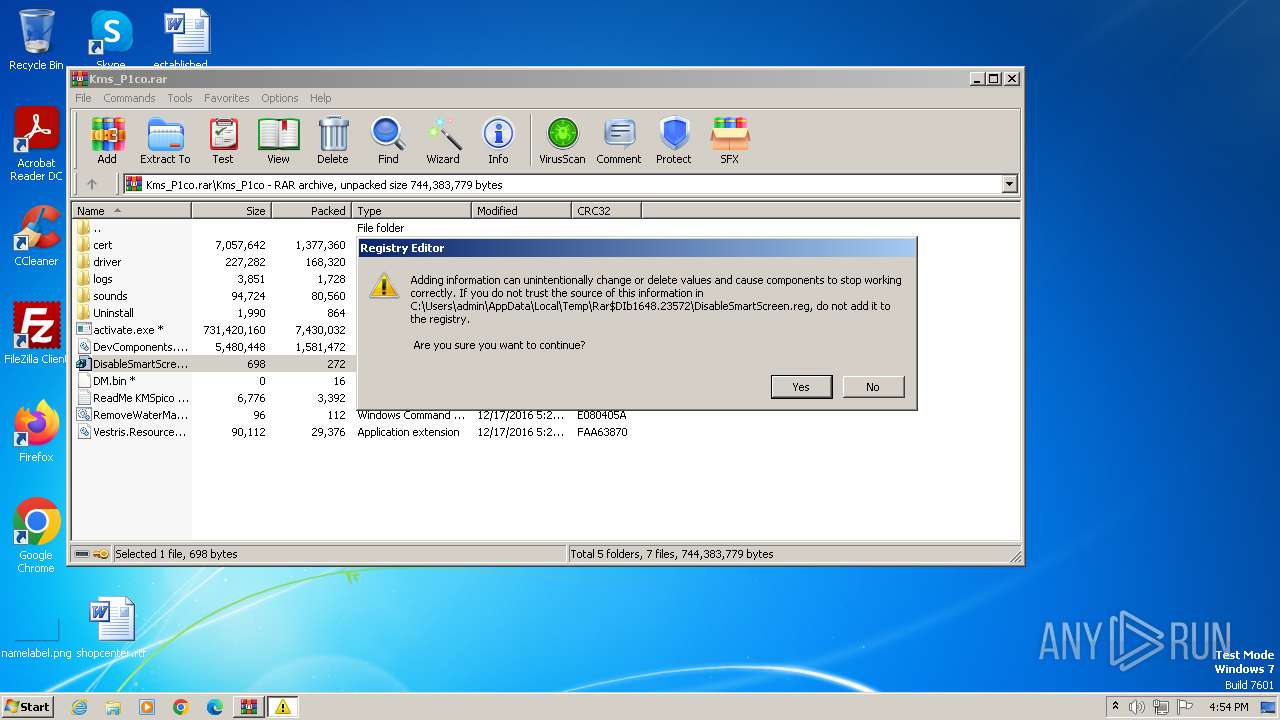
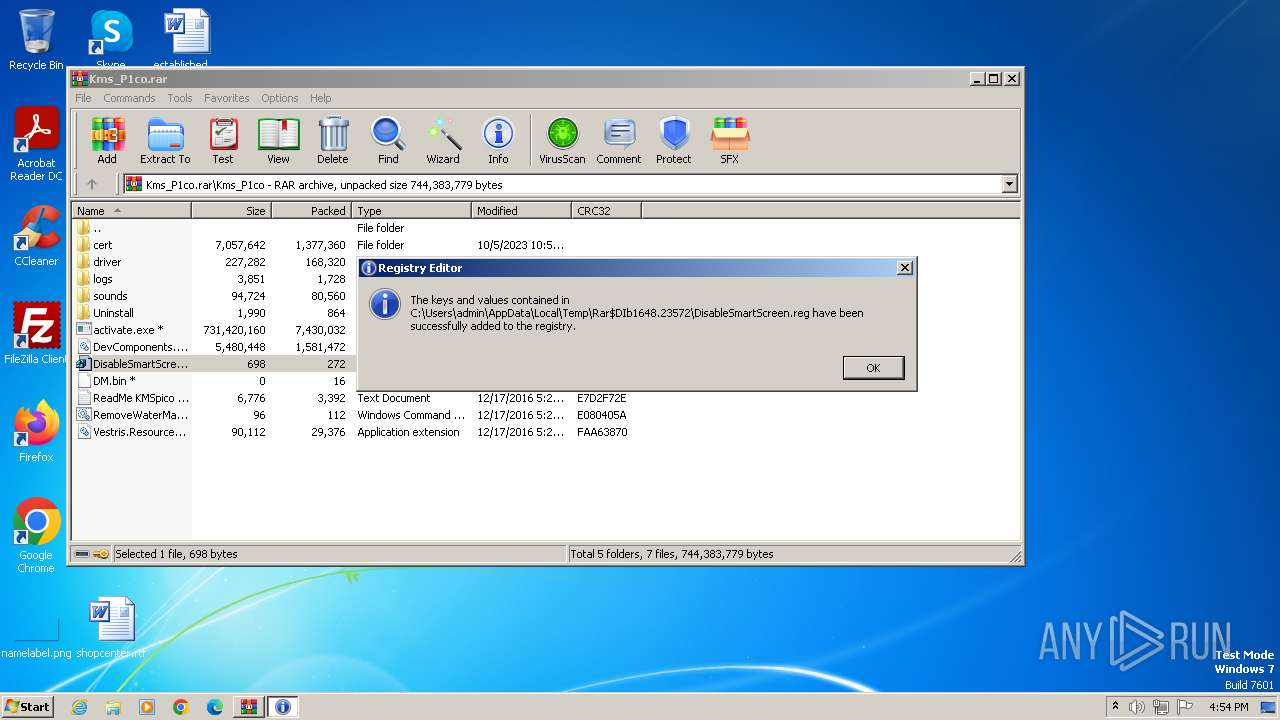
| 1120 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb1648.23572\DisableSmartScreen.reg" | C:\Windows\regedit.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1284 | "C:\Program Files\TAP-Windows\bin\devcon.exe" hwids tap0901 | C:\Program Files\TAP-Windows\bin\devcon.exe | — | ns2018.tmp | |||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
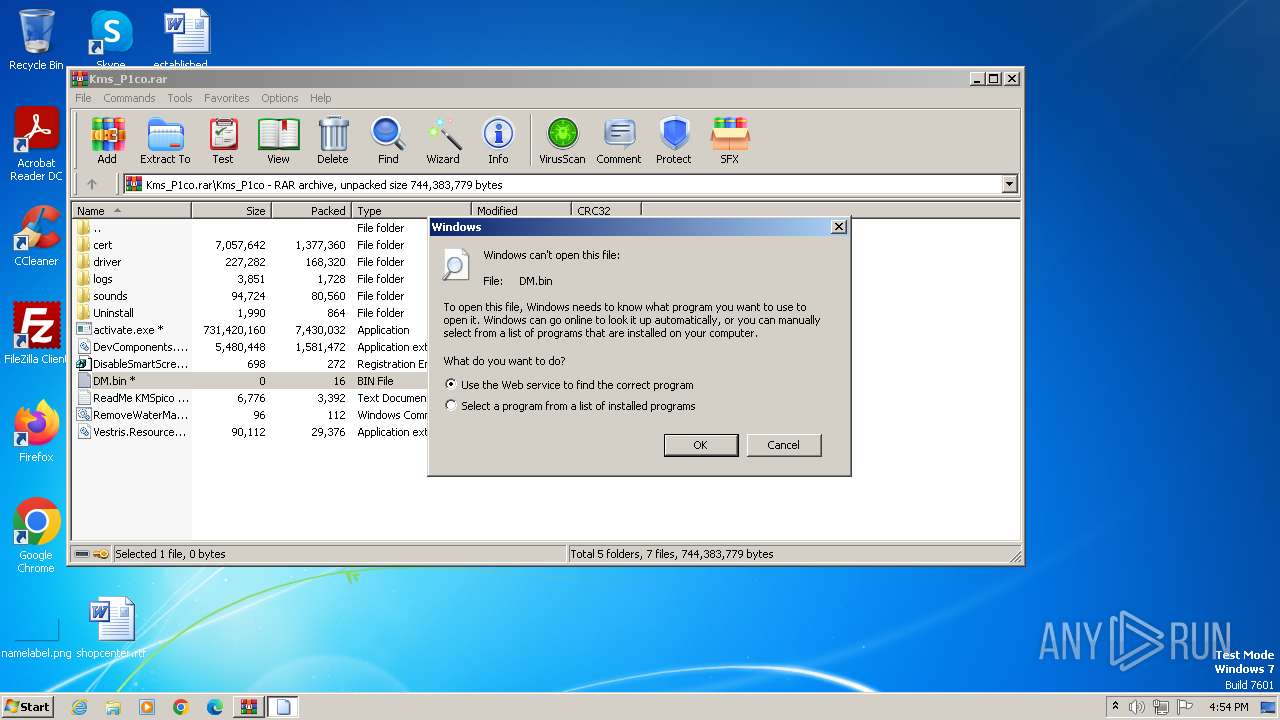
| 1480 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb1648.26138\DM.bin | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1648 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Kms_P1co.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1956 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2512 --field-trial-handle=1244,i,12331054116738006116,14303850040422449046,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2008 | "C:\Users\admin\AppData\Local\Temp\nsw461.tmp\ns2113.tmp" "C:\Program Files\TAP-Windows\bin\devcon.exe" install "C:\Program Files\TAP-Windows\driver\OemVista.inf" tap0901 | C:\Users\admin\AppData\Local\Temp\nsw461.tmp\ns2113.tmp | — | tap-windows-9.21.0.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
27 662
Read events
27 355
Write events
256
Delete events
51
Modification events
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1648) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
38
Suspicious files
215
Text files
1 088
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\activate.exe | — | |
MD5:— | SHA256:— | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Excel\Excel_KMS_Client.RAC_Pub.xrm-ms | xml | |
MD5:F337534801463A265E94DD34745B3302 | SHA256:AE237C3EAFD09ED83FFD4A27376703D4DCB3EC2C142D557BDFD3FE1C761690AC | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Excel\Excel_KMS_Client.RAC_Priv.xrm-ms | xml | |
MD5:F337534801463A265E94DD34745B3302 | SHA256:AE237C3EAFD09ED83FFD4A27376703D4DCB3EC2C142D557BDFD3FE1C761690AC | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Excel\Excel_KMS_Client.OOB.xrm-ms | xml | |
MD5:14D12F9F6107BBF0C0314FE02FF5DC27 | SHA256:C66AA472011A02DAD09971C29320E55F6B46DF9DCCCE4D9F01EC6D147D9BC99F | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Access\AccessVLReg32.reg | text | |
MD5:19506B075C7448CE328682DA3D1A57B0 | SHA256:0BB62DF2FDAB1A42A2303729400C343D70090C1F18123357456922C7544131B8 | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Excel\Excel_KMS_Client.PPDLIC.xrm-ms | xml | |
MD5:29D5DA4B2382E5161095D0BE9BE6DD92 | SHA256:741A714776A9AF2846EDA66F8A499C18F53D237F0D4C4C532C421DECFC5D9FEA | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Access\Access_KMS_Client.RAC_Priv.xrm-ms | xml | |
MD5:A279AB8F8C617DF9C5411FDC199E7676 | SHA256:9084E7F35F7220EC760719B29721A267943178972578E739BDAC2D6475A573E3 | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Groove\GrooveVLReg64.reg | text | |
MD5:CA3B110B7359F1B73B1DC2B4C592ADE4 | SHA256:09EC94B042D00F3729798CC12813A008CEAC8A725DC22F4FABF35C4D126024E6 | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Excel\ExcelVLReg64.reg | text | |
MD5:E7102112F58F9A4FE2E6C28AE9F29343 | SHA256:2080AEC1D6D2DC9F4BBF825560981F00181F1918426DD8129F99F0EF4CADFADD | |||
| 1648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1648.18269\Kms_P1co\cert\kmscert2010\Groove\GrooveVLReg32.reg | text | |
MD5:D653C9540D303B02A3F101B38A04C6AB | SHA256:3CB9211D25221B322FD0185BA69D83CFC039EF49DD33B37DA3B0DE014FB6D20B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
43
DNS requests
65
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
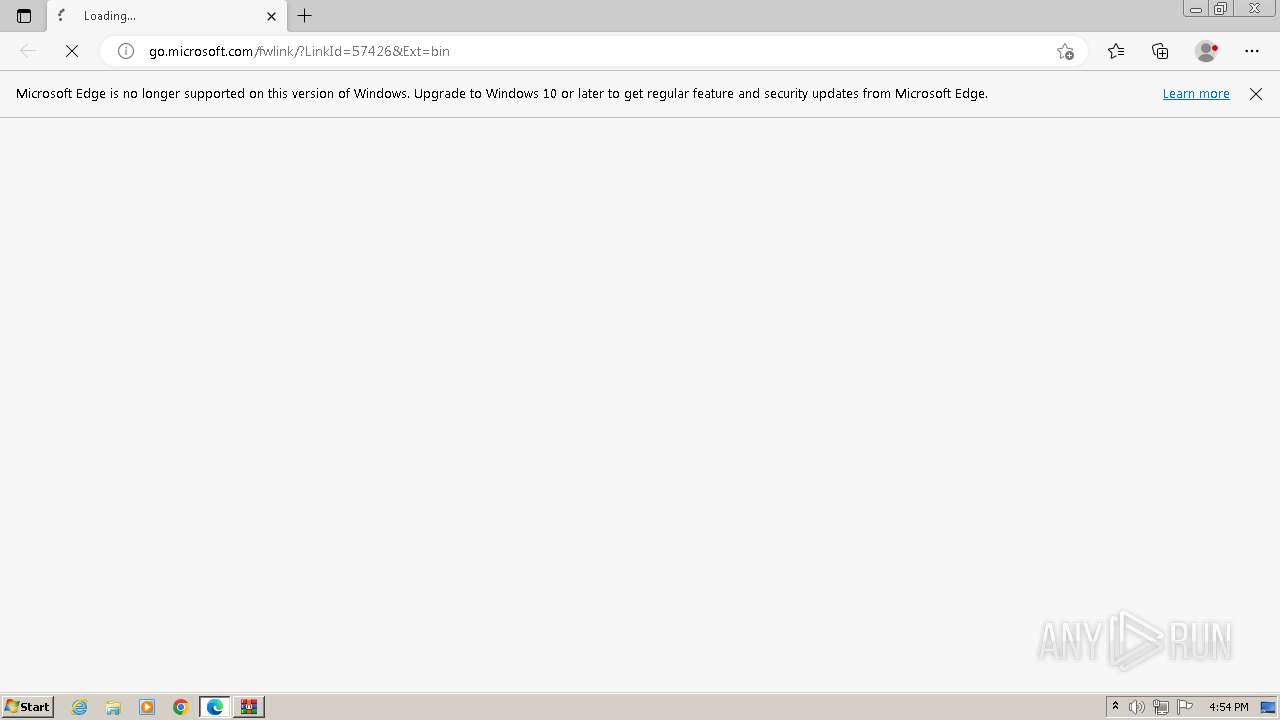
3896 | msedge.exe | GET | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=bin | unknown | — | — | unknown |
3896 | msedge.exe | GET | 301 | 2.21.20.150:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=bin | unknown | — | — | unknown |
864 | svchost.exe | HEAD | 200 | 8.241.121.126:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d9a961cd-afbe-4cd8-8aee-c21eaf7d7c04?P1=1696921869&P2=404&P3=2&P4=TK3DoIkp6g1CjPCi%2bDblBWEv4CVe%2bj9w0e6bmBBsura8qeUXYFbN7oNV18v%2fTofbPFHUGapUZGoGSXps0b6v3g%3d%3d | unknown | — | — | unknown |
864 | svchost.exe | HEAD | — | 8.241.121.126:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c50698d5-282c-4c8d-9fa6-c155f2d8d379?P1=1696921866&P2=404&P3=2&P4=k1oHJ0sTMSLbGn2IO9C9iQzVyMGu3vtXyXk8lwZtc3z%2fDeIL9JxW%2fQ2AHUhyB31f0saZTl7akSH1aooKJKIT9g%3d%3d | unknown | — | — | unknown |
864 | svchost.exe | GET | 206 | 8.241.121.126:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d9a961cd-afbe-4cd8-8aee-c21eaf7d7c04?P1=1696921869&P2=404&P3=2&P4=TK3DoIkp6g1CjPCi%2bDblBWEv4CVe%2bj9w0e6bmBBsura8qeUXYFbN7oNV18v%2fTofbPFHUGapUZGoGSXps0b6v3g%3d%3d | unknown | binary | 8.04 Kb | unknown |
4076 | activate.exe | POST | 200 | 193.106.174.220:80 | http://qqseven7ht.top/zip.php | unknown | text | 2 b | unknown |
864 | svchost.exe | GET | 206 | 8.241.121.126:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d9a961cd-afbe-4cd8-8aee-c21eaf7d7c04?P1=1696921869&P2=404&P3=2&P4=TK3DoIkp6g1CjPCi%2bDblBWEv4CVe%2bj9w0e6bmBBsura8qeUXYFbN7oNV18v%2fTofbPFHUGapUZGoGSXps0b6v3g%3d%3d | unknown | binary | 119 Kb | unknown |
864 | svchost.exe | GET | 206 | 8.241.121.126:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d9a961cd-afbe-4cd8-8aee-c21eaf7d7c04?P1=1696921869&P2=404&P3=2&P4=TK3DoIkp6g1CjPCi%2bDblBWEv4CVe%2bj9w0e6bmBBsura8qeUXYFbN7oNV18v%2fTofbPFHUGapUZGoGSXps0b6v3g%3d%3d | unknown | binary | 278 Kb | unknown |
864 | svchost.exe | GET | 206 | 8.241.121.126:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d9a961cd-afbe-4cd8-8aee-c21eaf7d7c04?P1=1696921869&P2=404&P3=2&P4=TK3DoIkp6g1CjPCi%2bDblBWEv4CVe%2bj9w0e6bmBBsura8qeUXYFbN7oNV18v%2fTofbPFHUGapUZGoGSXps0b6v3g%3d%3d | unknown | binary | 10.2 Kb | unknown |
864 | svchost.exe | GET | 206 | 8.241.121.126:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d9a961cd-afbe-4cd8-8aee-c21eaf7d7c04?P1=1696921869&P2=404&P3=2&P4=TK3DoIkp6g1CjPCi%2bDblBWEv4CVe%2bj9w0e6bmBBsura8qeUXYFbN7oNV18v%2fTofbPFHUGapUZGoGSXps0b6v3g%3d%3d | unknown | binary | 13.3 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4076 | activate.exe | 193.106.174.220:80 | qqseven7ht.top | IQHost Ltd | RU | unknown |
3896 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3272 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3896 | msedge.exe | 23.35.238.131:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3896 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3896 | msedge.exe | 20.103.180.120:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3896 | msedge.exe | 51.104.176.40:443 | data-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
qqseven7ht.top |
| unknown |
config.edge.skype.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
4076 | activate.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
4076 | activate.exe | A Network Trojan was detected | ET MALWARE Win32/Cryptbot CnC Activity (POST) |
4076 | activate.exe | A Network Trojan was detected | ET HUNTING Observed Malicious Filename in Outbound POST Request (Information.txt) |