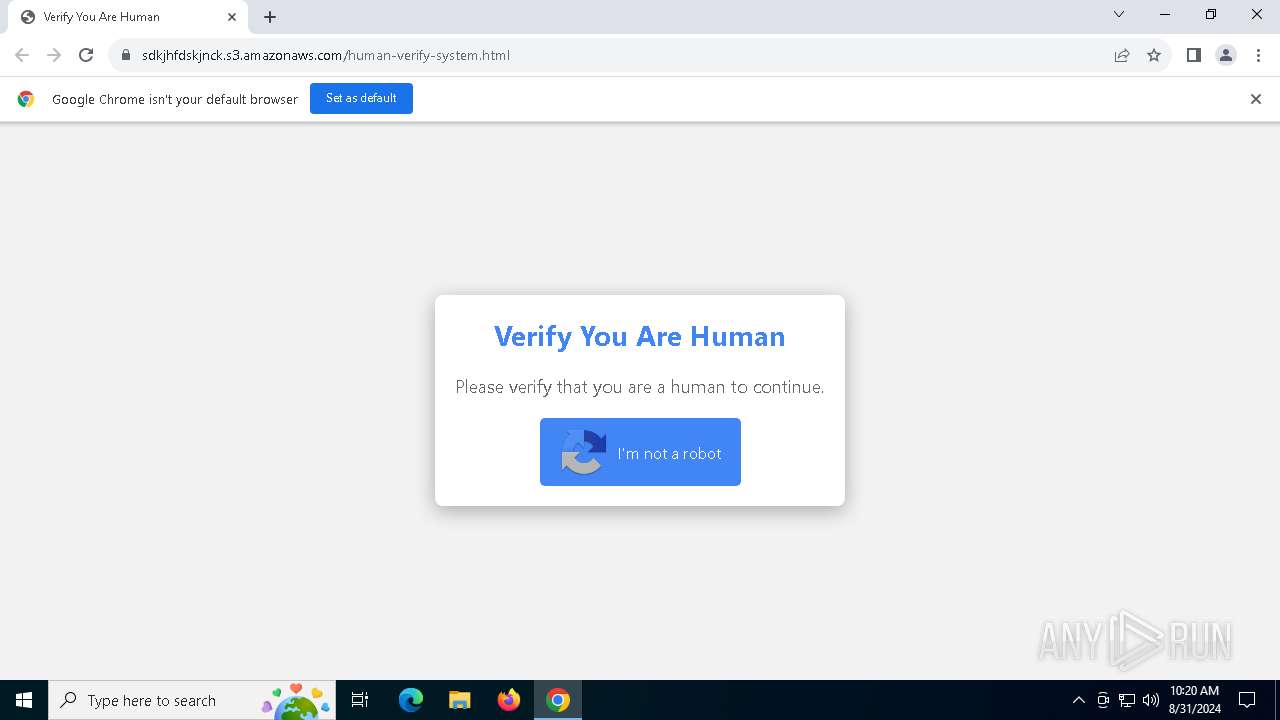
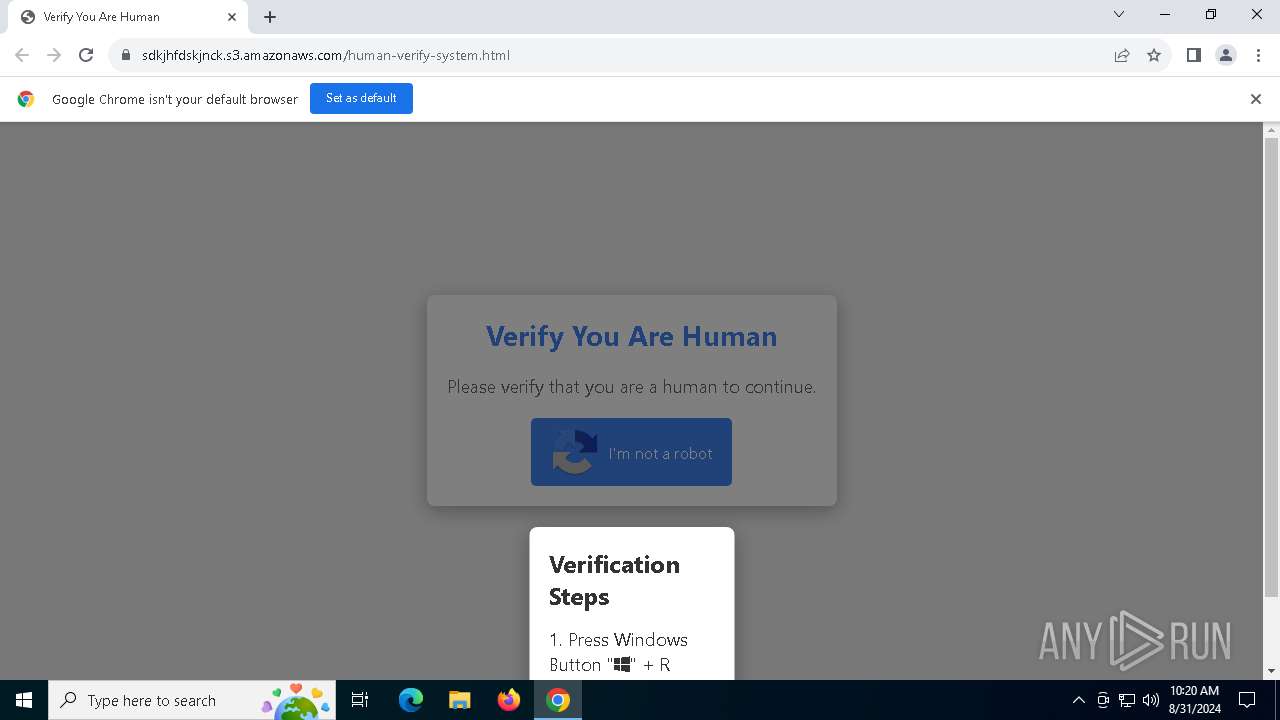
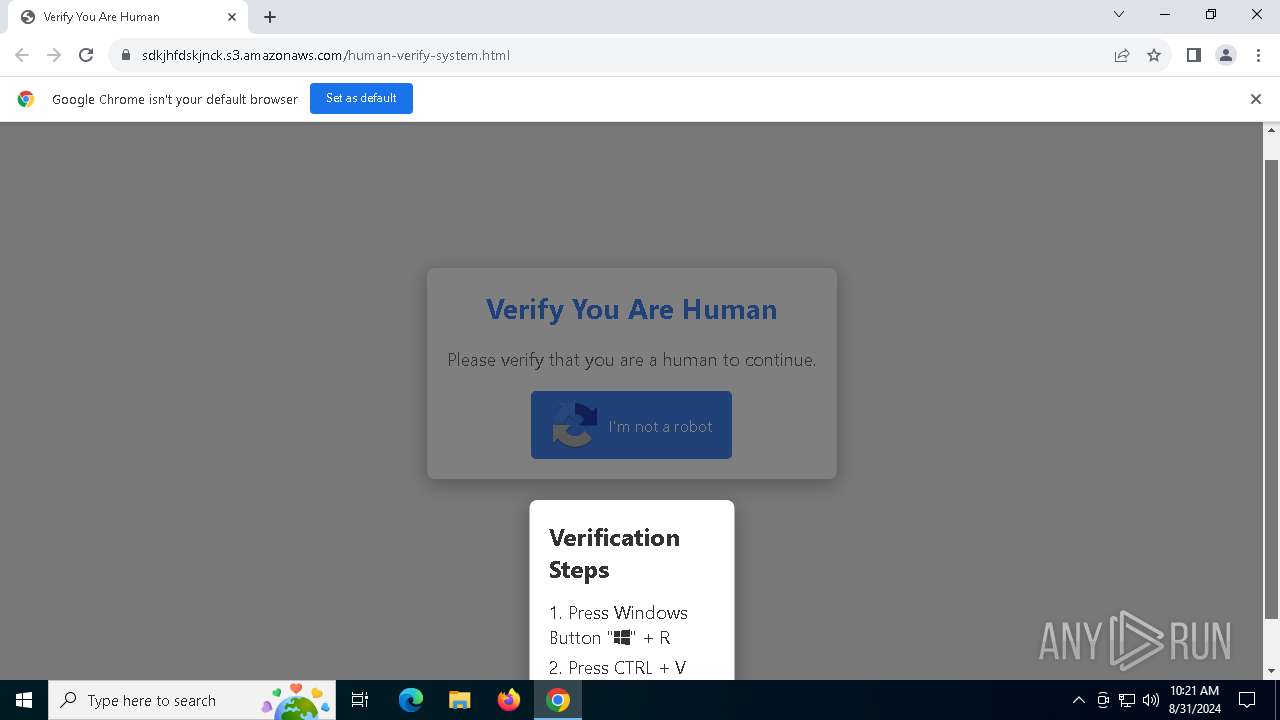
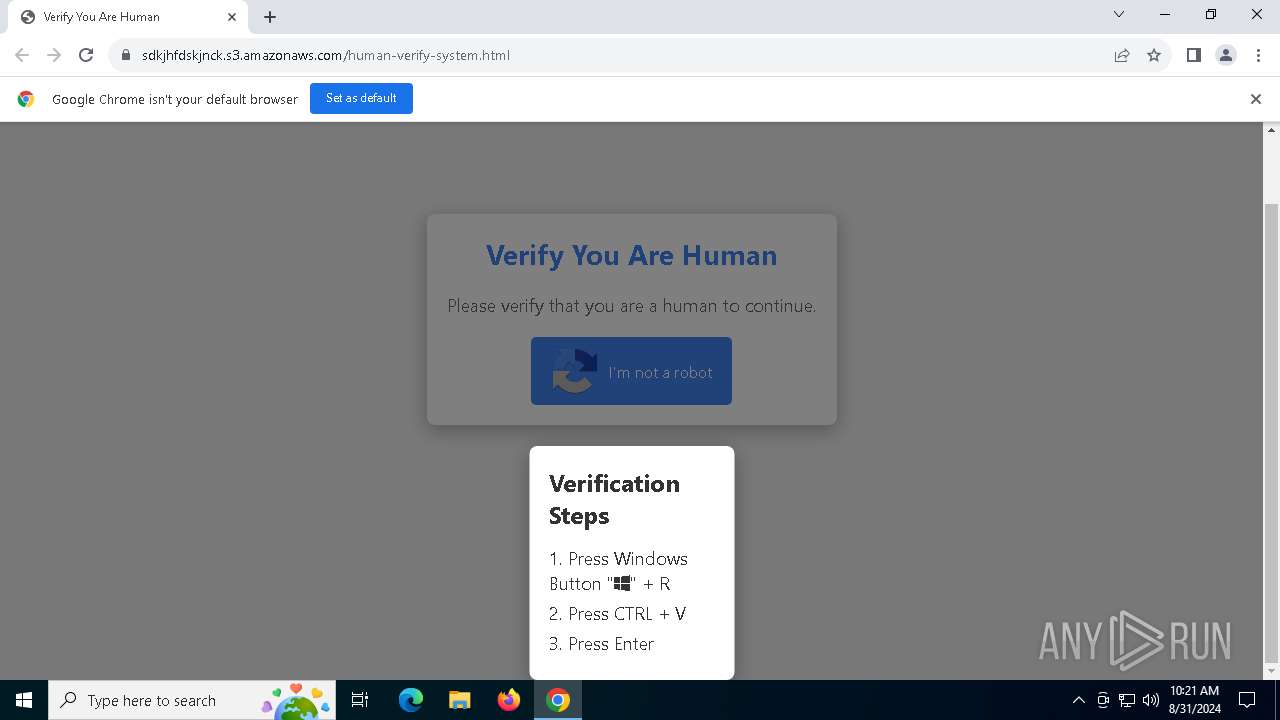
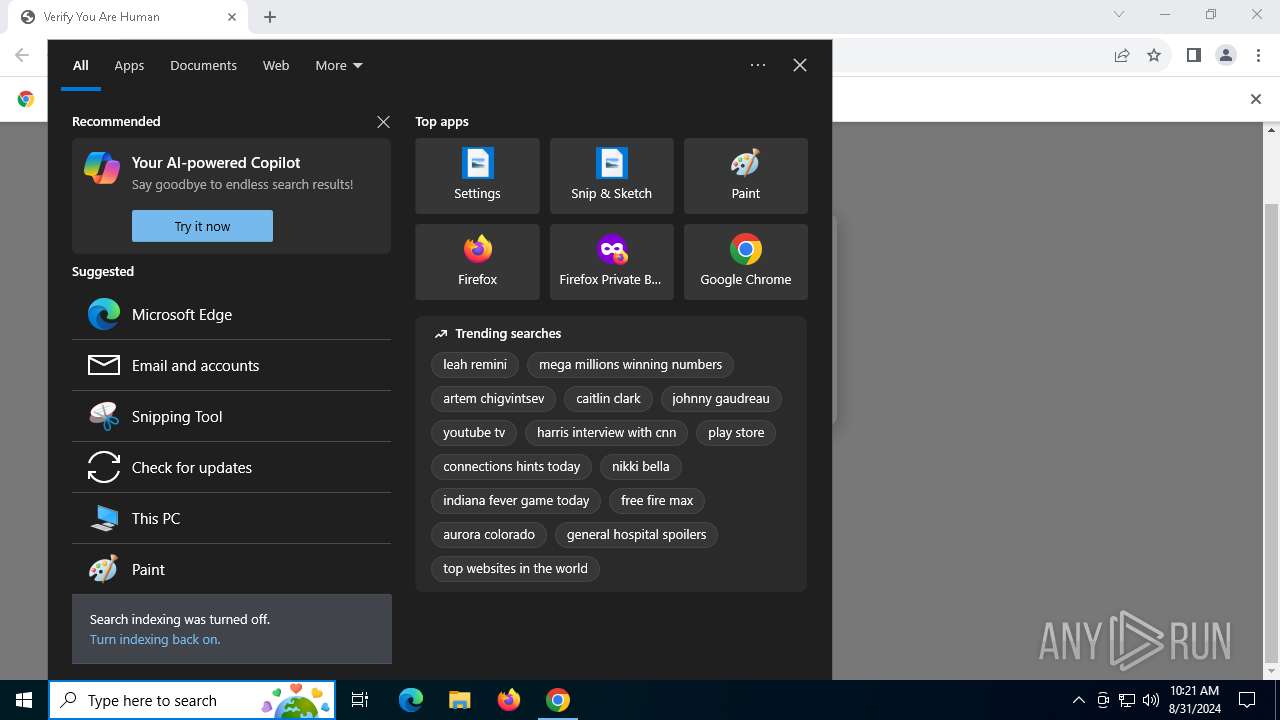
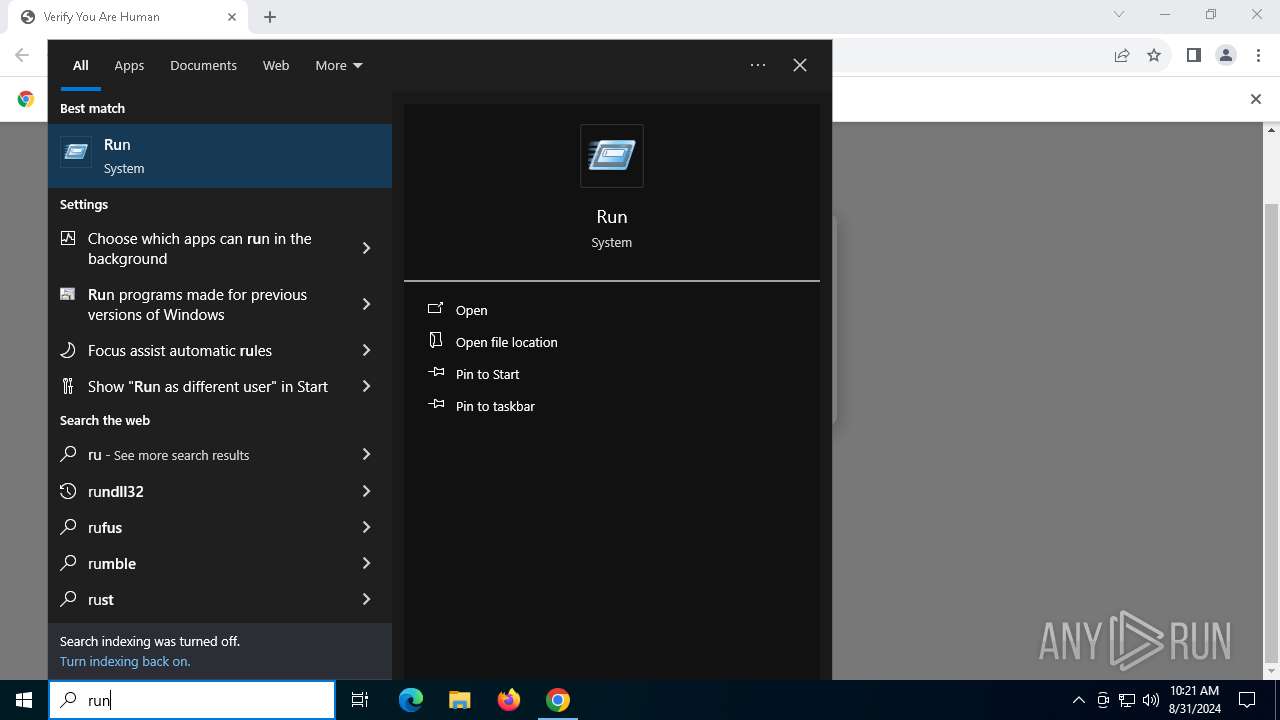
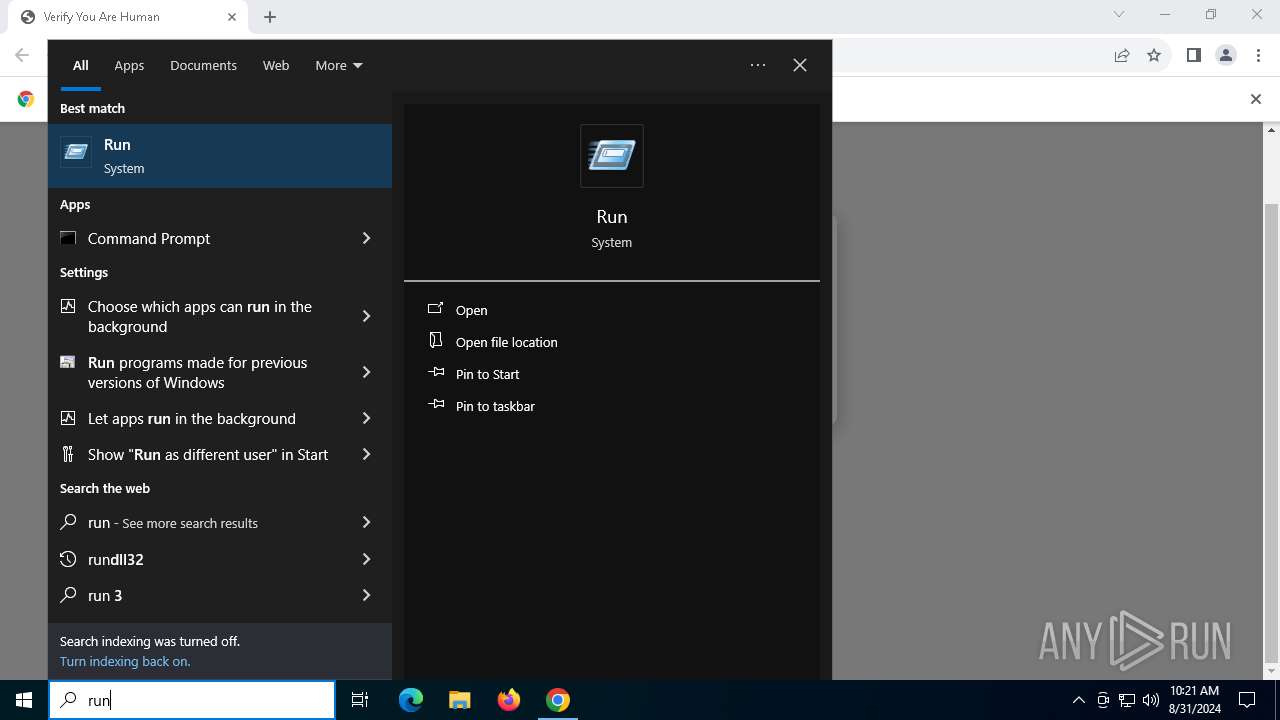
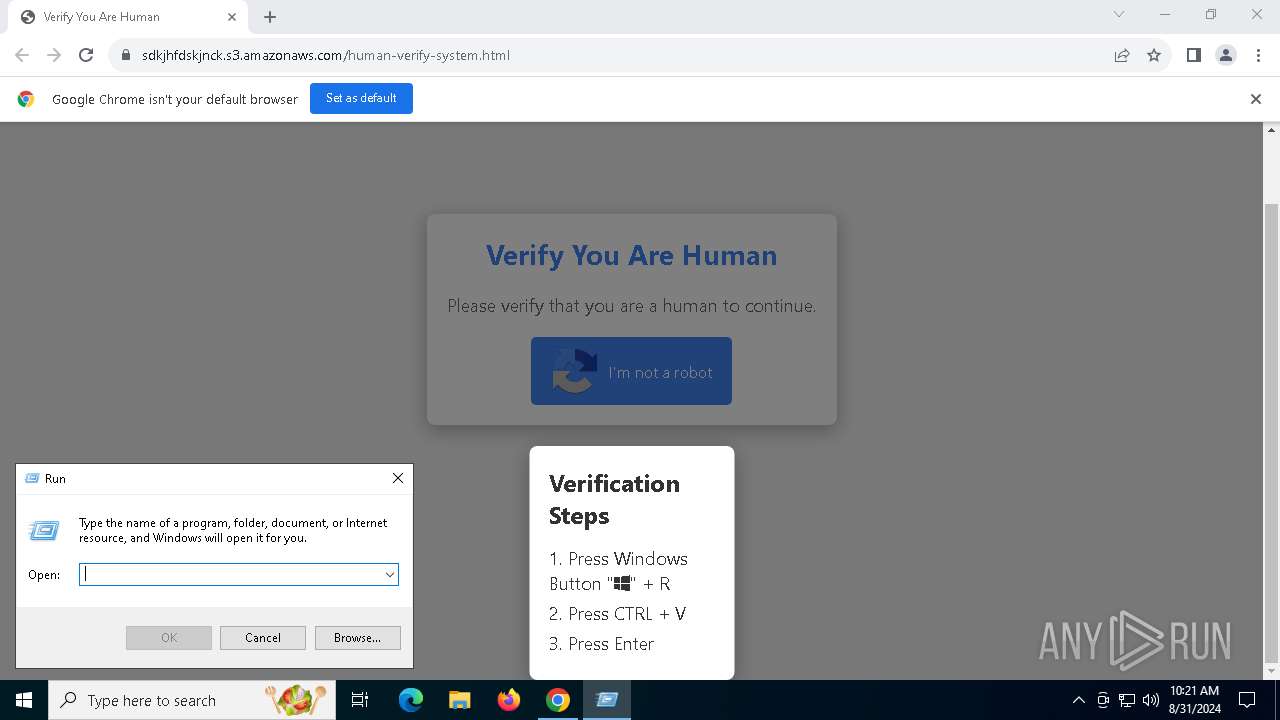
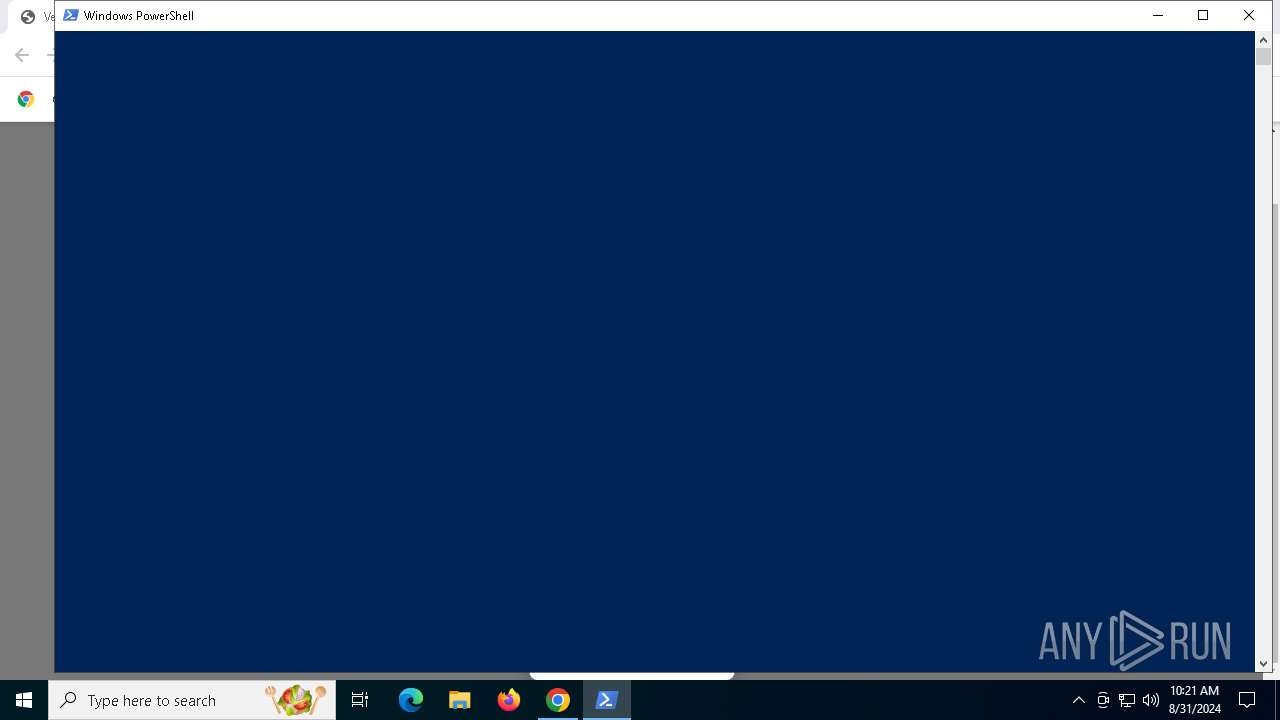
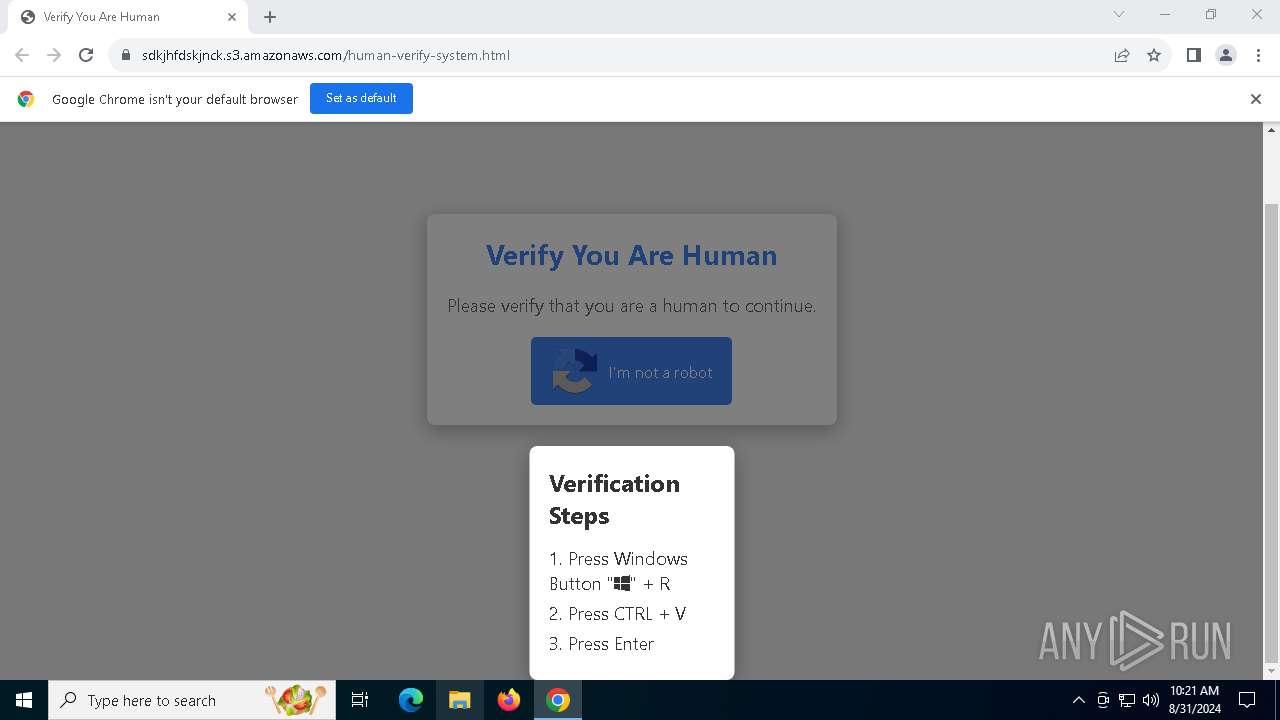
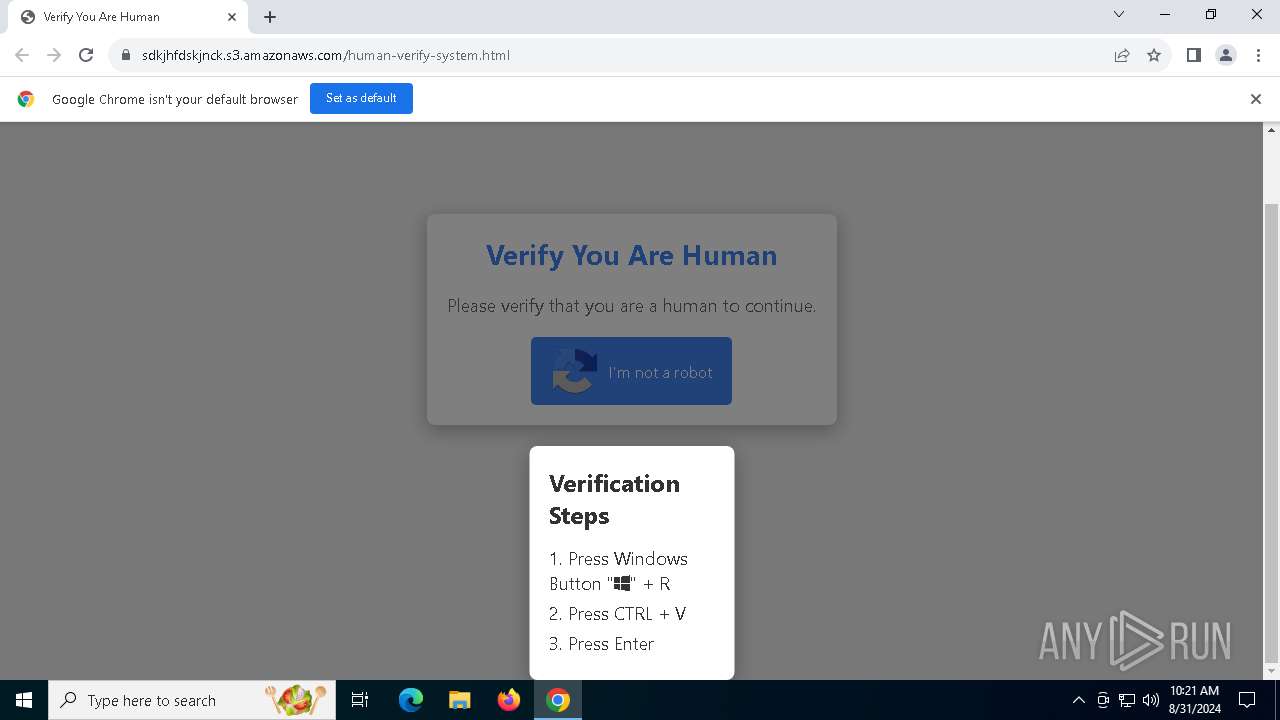
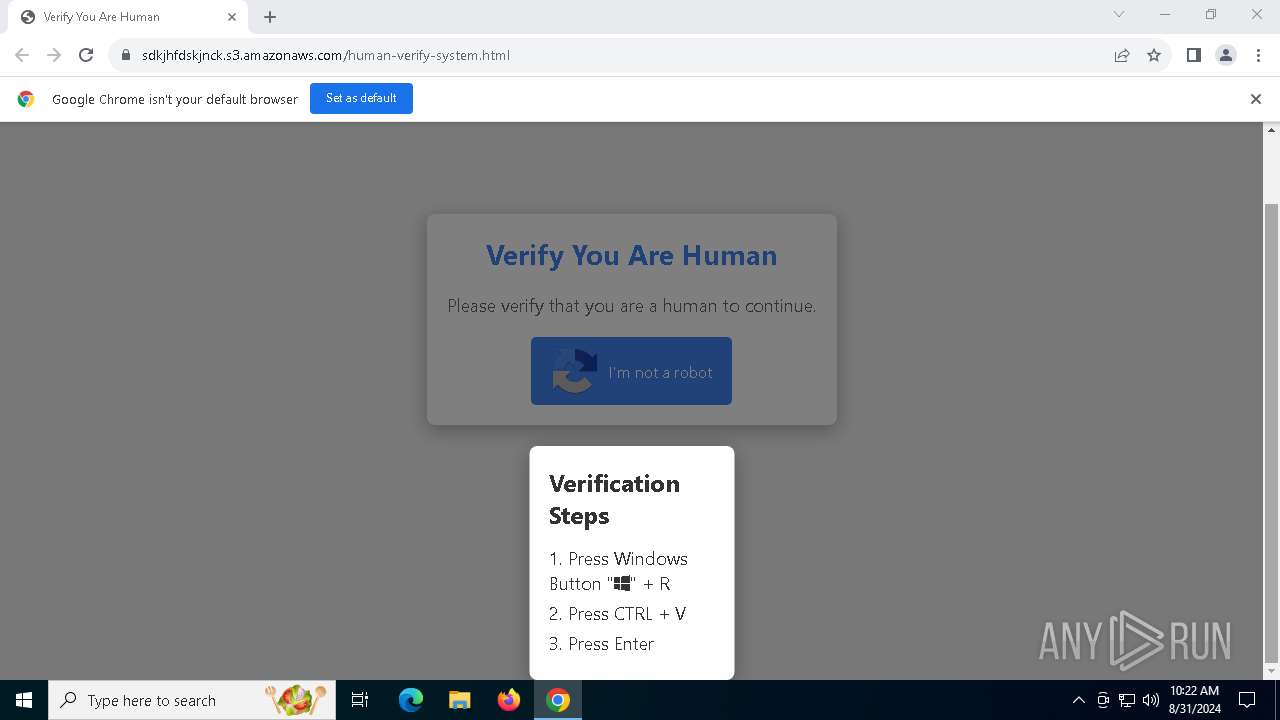
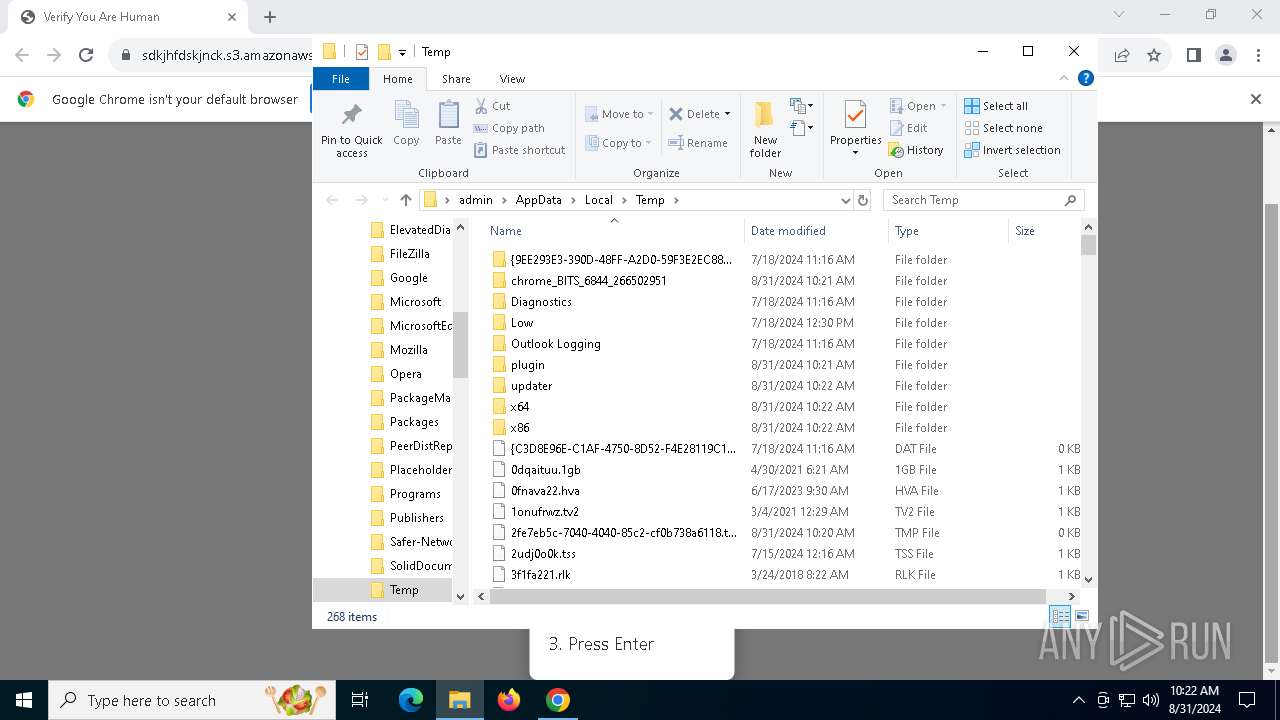
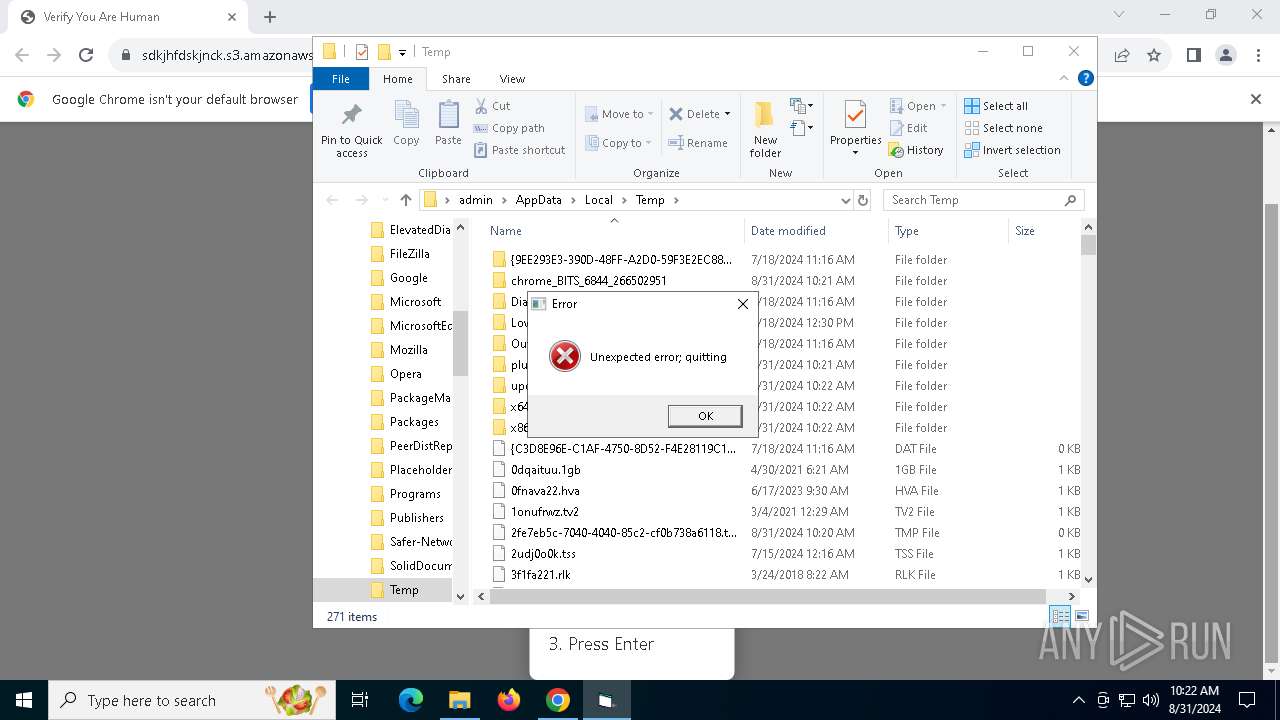
| URL: | https://sdkjhfdskjnck.s3.amazonaws.com\human-verify-system.html |
| Full analysis: | https://app.any.run/tasks/ee1351bc-5b1d-4ae2-8a5c-7909de4d8ffb |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | August 31, 2024, 10:20:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FA06550957DAA5FB1CD21473E82C78BF |
| SHA1: | D82586CA7DDCE07576DE1184FBFD19309522CACA |
| SHA256: | FA339469DC87578EBE761BF7C3D070D8C3644CC48A88CF39EE12CBB53025610E |
| SSDEEP: | 3:N8MpgLGOiWmo7W0ELI35yRRIJn:2MKLZ1moJEOA30 |
MALICIOUS
Scans artifacts that could help determine the target
- mshta.exe (PID: 5116)
Run PowerShell with an invisible window
- powershell.exe (PID: 5464)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 5116)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 5464)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 5464)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 5464)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 5464)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2256)
- mshta.exe (PID: 5116)
- powershell.exe (PID: 5464)
- py.exe (PID: 2904)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2256)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 5464)
Actions looks like stealing of personal data
- py.exe (PID: 2904)
Stealers network behavior
- py.exe (PID: 2904)
SUSPICIOUS
Executable content was dropped or overwritten
- mshta.exe (PID: 5116)
- powershell.exe (PID: 5464)
- Setup.exe (PID: 400)
- more.com (PID: 6532)
Drops the executable file immediately after the start
- mshta.exe (PID: 5116)
- powershell.exe (PID: 5464)
- Setup.exe (PID: 400)
- more.com (PID: 6532)
Cryptography encrypted command line is found
- powershell.exe (PID: 5464)
Process drops legitimate windows executable
- mshta.exe (PID: 5116)
- powershell.exe (PID: 5464)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 5116)
Base64-obfuscated command line is found
- mshta.exe (PID: 5116)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 5116)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 5116)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 5464)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 5464)
Contacting a server suspected of hosting an CnC
- mshta.exe (PID: 5116)
- svchost.exe (PID: 2256)
- powershell.exe (PID: 5464)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 5464)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 5464)
Checks for external IP
- powershell.exe (PID: 5464)
- svchost.exe (PID: 2256)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2256)
- powershell.exe (PID: 5464)
Starts application with an unusual extension
- Setup.exe (PID: 400)
Searches for installed software
- py.exe (PID: 2904)
INFO
Application launched itself
- chrome.exe (PID: 6844)
Reads Internet Explorer settings
- mshta.exe (PID: 5116)
Checks proxy server information
- mshta.exe (PID: 5116)
- powershell.exe (PID: 5464)
- slui.exe (PID: 1680)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6844)
Manual execution by a user
- powershell.exe (PID: 5944)
- py.exe (PID: 6636)
The process uses the downloaded file
- mshta.exe (PID: 5116)
- powershell.exe (PID: 5464)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5464)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5464)
Disables trace logs
- powershell.exe (PID: 5464)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5464)
Checks supported languages
- Setup.exe (PID: 400)
- StrCmp.exe (PID: 4436)
- more.com (PID: 6532)
- py.exe (PID: 2904)
- py.exe (PID: 6636)
The executable file from the user directory is run by the Powershell process
- Setup.exe (PID: 400)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5464)
Reads the computer name
- Setup.exe (PID: 400)
- StrCmp.exe (PID: 4436)
- more.com (PID: 6532)
- py.exe (PID: 2904)
Creates files or folders in the user directory
- Setup.exe (PID: 400)
Create files in a temporary directory
- Setup.exe (PID: 400)
- more.com (PID: 6532)
Creates files in the program directory
- more.com (PID: 6532)
Reads the software policy settings
- slui.exe (PID: 6192)
- py.exe (PID: 2904)
- slui.exe (PID: 1680)
Executable content was dropped or overwritten
- chrome.exe (PID: 7076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
173
Monitored processes
41
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3032 --field-trial-handle=1836,i,17145825842281475802,2946538962004987194,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 400 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | powershell.exe | ||||||||||||
User: admin Company: Apple Inc. Integrity Level: MEDIUM Description: Apple Software Update Exit code: 1 Version: 2.7.0.3 Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4860 --field-trial-handle=1836,i,17145825842281475802,2946538962004987194,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 940 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | py.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4620 --field-trial-handle=1836,i,17145825842281475802,2946538962004987194,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1680 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4932 --field-trial-handle=1836,i,17145825842281475802,2946538962004987194,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5104 --field-trial-handle=1836,i,17145825842281475802,2946538962004987194,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 745
Read events
31 677
Write events
62
Delete events
6
Modification events
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
48
Suspicious files
445
Text files
75
Unknown types
80
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12bb88.TMP | — | |
MD5:— | SHA256:— | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12bba7.TMP | — | |
MD5:— | SHA256:— | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:F96D0EF8D63094D714514A441F8CD3FB | SHA256:2083625CA1E32D366F0B664D9B87B591791EF2EA2B770F4FA6ABE13FECA01196 | |||
| 6844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:A95974F48FC4A0E16E9D7729D7874157 | SHA256:926422473F59B7759EA8EB2064FD6DF9D00A88B548DEF1D5C3E08860357C03A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
79
DNS requests
44
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4164 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5116 | mshta.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
6404 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6404 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5116 | mshta.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEAO9ExOMvLBqk2jkjdZnyjA%3D | unknown | — | — | whitelisted |
6168 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adg4gxhoc4ipq24nrkpgca3xuqta_3040/jflookgnkcckhobaglndicnbbgbonegd_3040_all_j6kvwuv5hzxeixor5sxkklnez4.crx3 | unknown | — | — | whitelisted |
6168 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adg4gxhoc4ipq24nrkpgca3xuqta_3040/jflookgnkcckhobaglndicnbbgbonegd_3040_all_j6kvwuv5hzxeixor5sxkklnez4.crx3 | unknown | — | — | whitelisted |
6168 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adg4gxhoc4ipq24nrkpgca3xuqta_3040/jflookgnkcckhobaglndicnbbgbonegd_3040_all_j6kvwuv5hzxeixor5sxkklnez4.crx3 | unknown | — | — | whitelisted |
6168 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adg4gxhoc4ipq24nrkpgca3xuqta_3040/jflookgnkcckhobaglndicnbbgbonegd_3040_all_j6kvwuv5hzxeixor5sxkklnez4.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
740 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4008 | chrome.exe | 52.216.53.57:443 | sdkjhfdskjnck.s3.amazonaws.com | AMAZON-02 | US | shared |
6844 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4008 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
4008 | chrome.exe | 104.17.25.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | whitelisted |
4008 | chrome.exe | 172.217.18.3:443 | www.gstatic.com | GOOGLE | US | whitelisted |
4760 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
sdkjhfdskjnck.s3.amazonaws.com |
| shared |
accounts.google.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4008 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
4008 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2256 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain was identified as Phishing (myapt67 .s3.amazonaws.com) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (myapt67 .s3 .amazonaws .com) |
5116 | mshta.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (myapt67 .s3 .amazonaws .com in TLS SNI) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (myapt67 .s3 .amazonaws .com) |
5464 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (myapt67 .s3 .amazonaws .com in TLS SNI) |
5464 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (myapt67 .s3 .amazonaws .com in TLS SNI) |
2904 | py.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
2 ETPRO signatures available at the full report