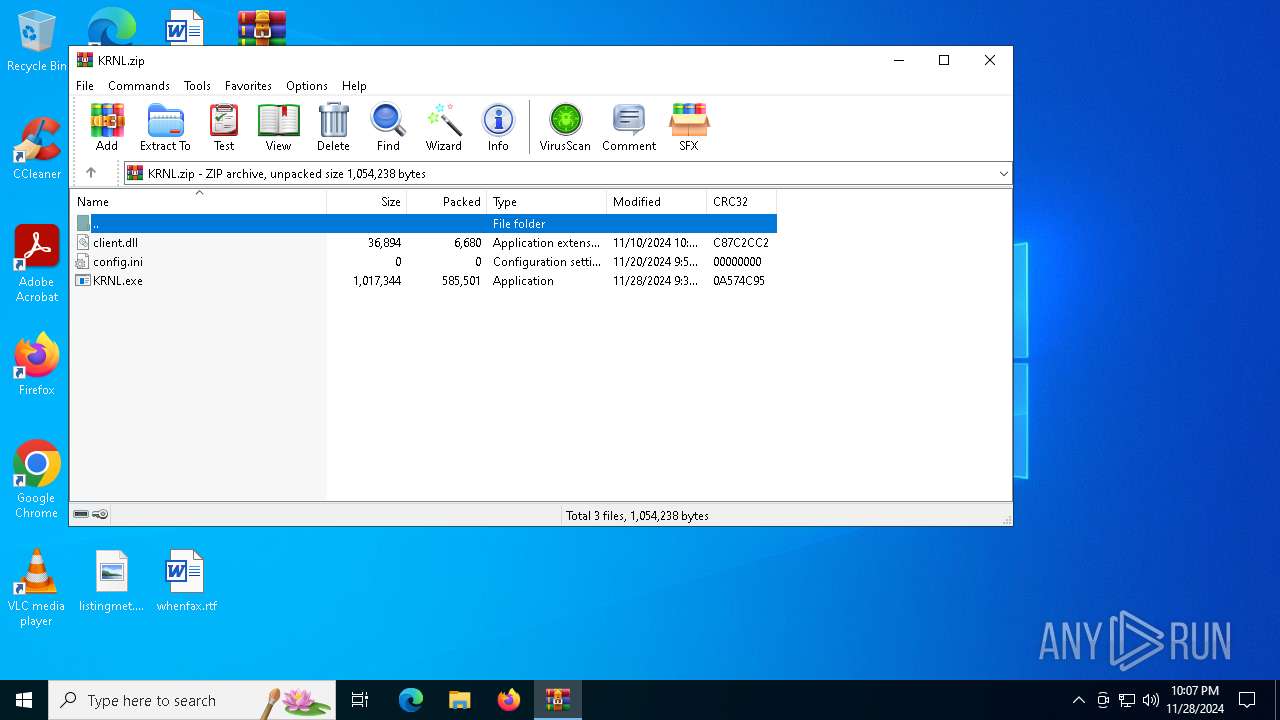
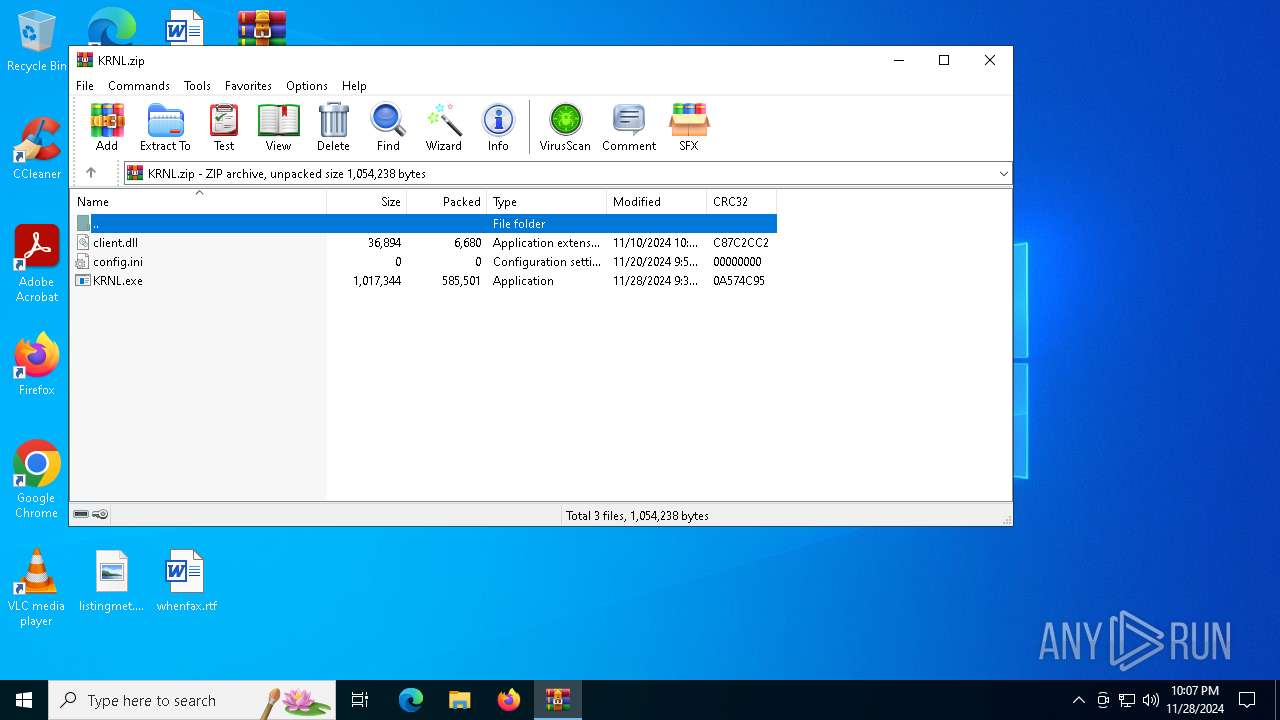
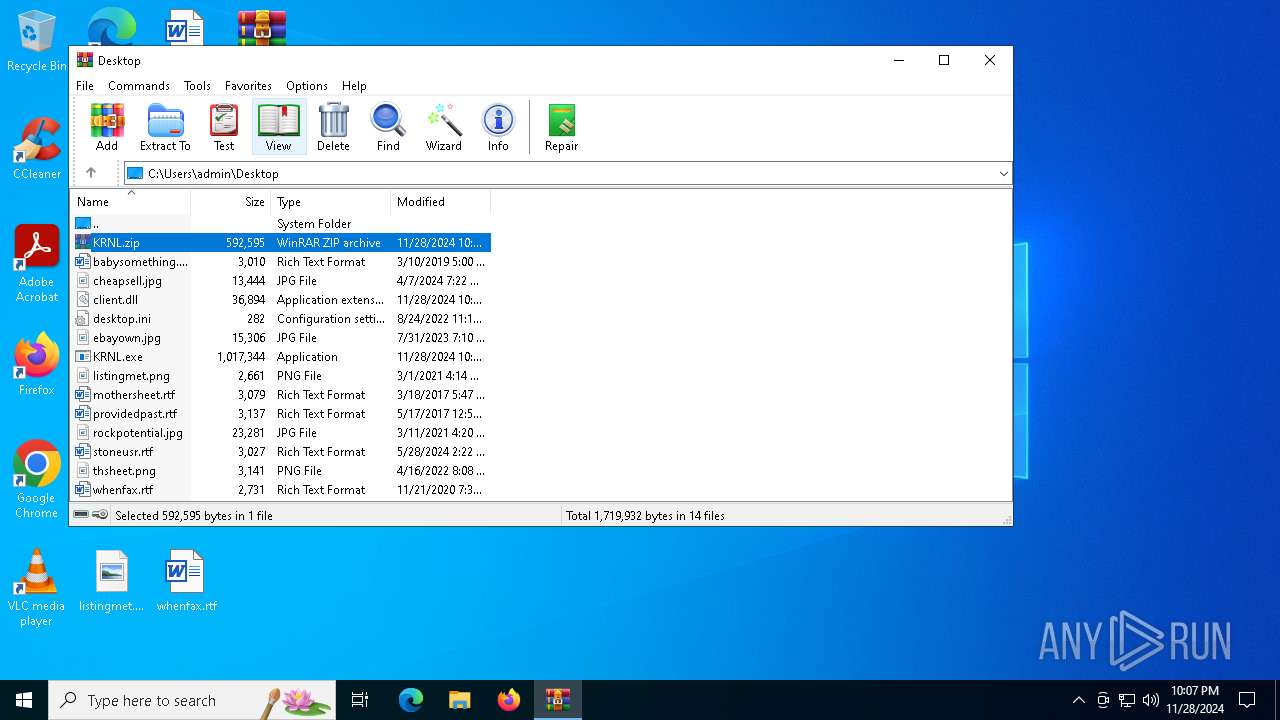
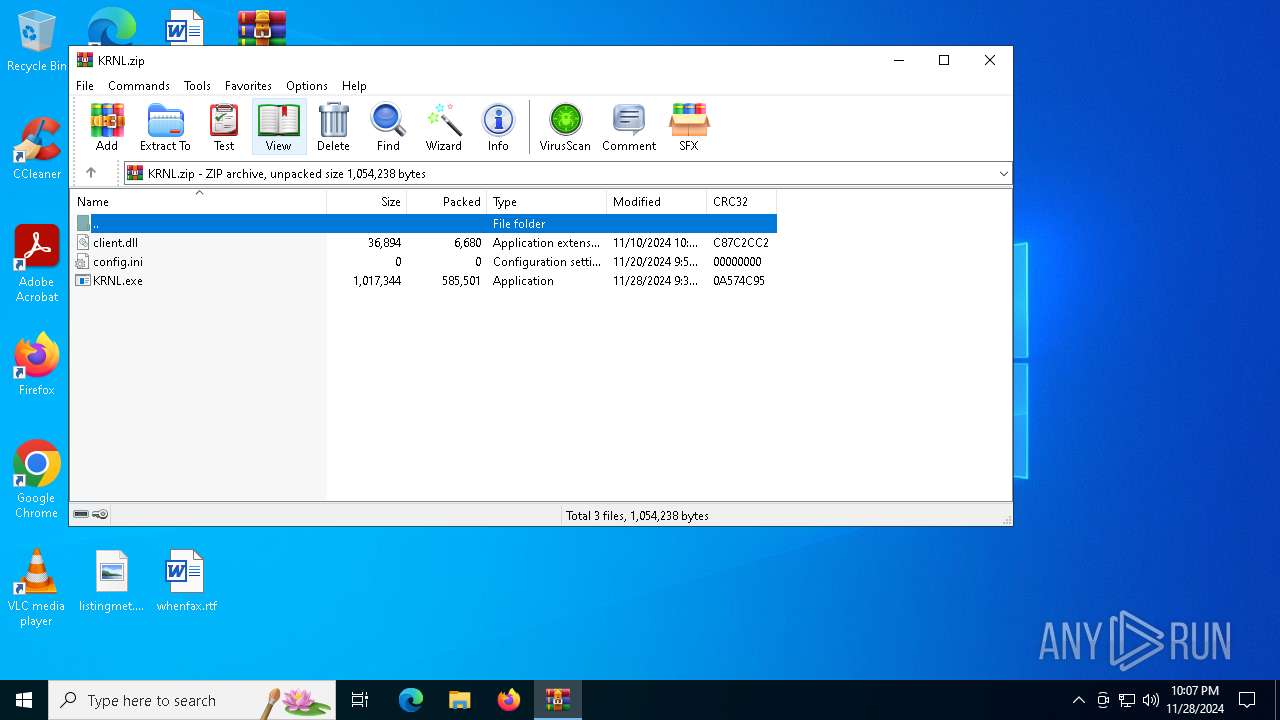
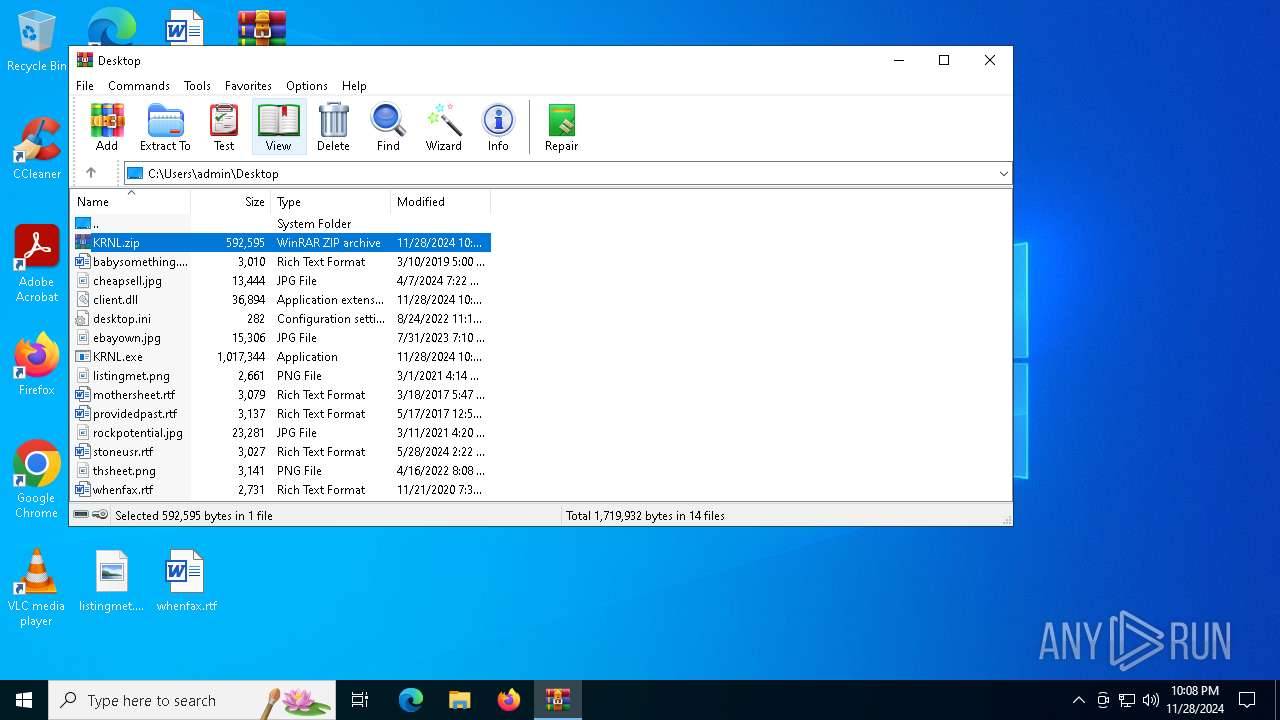
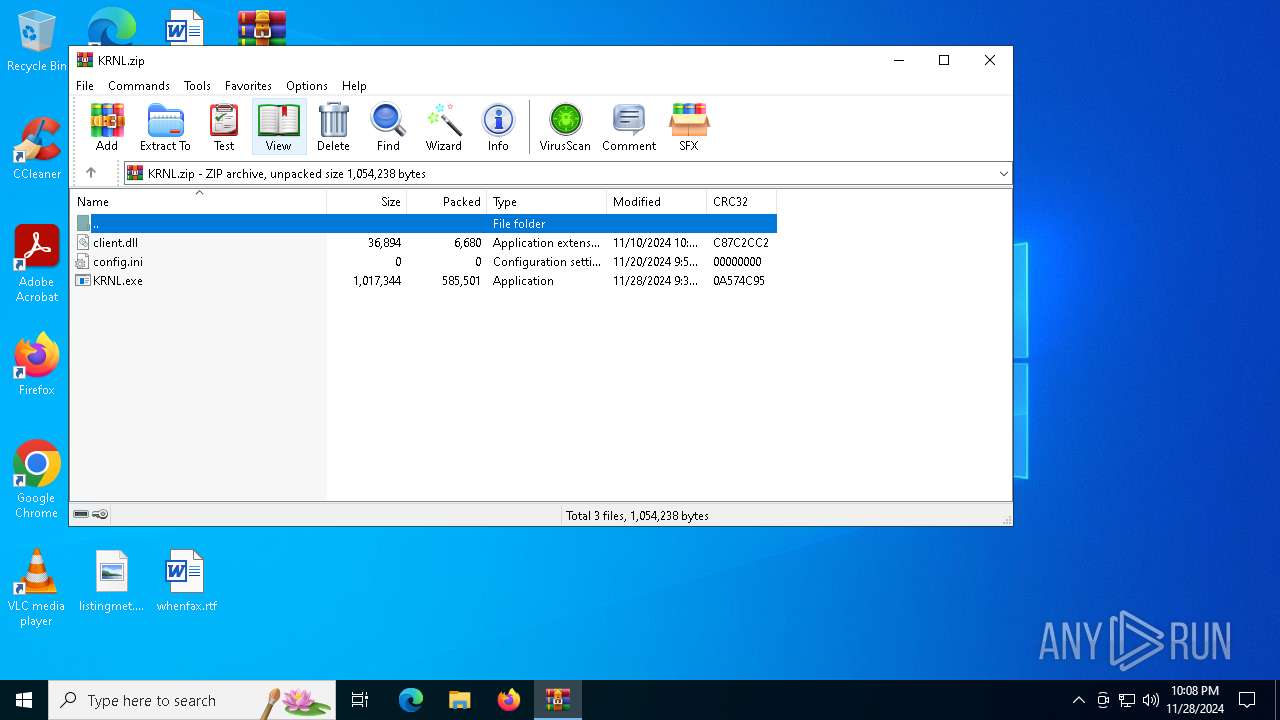
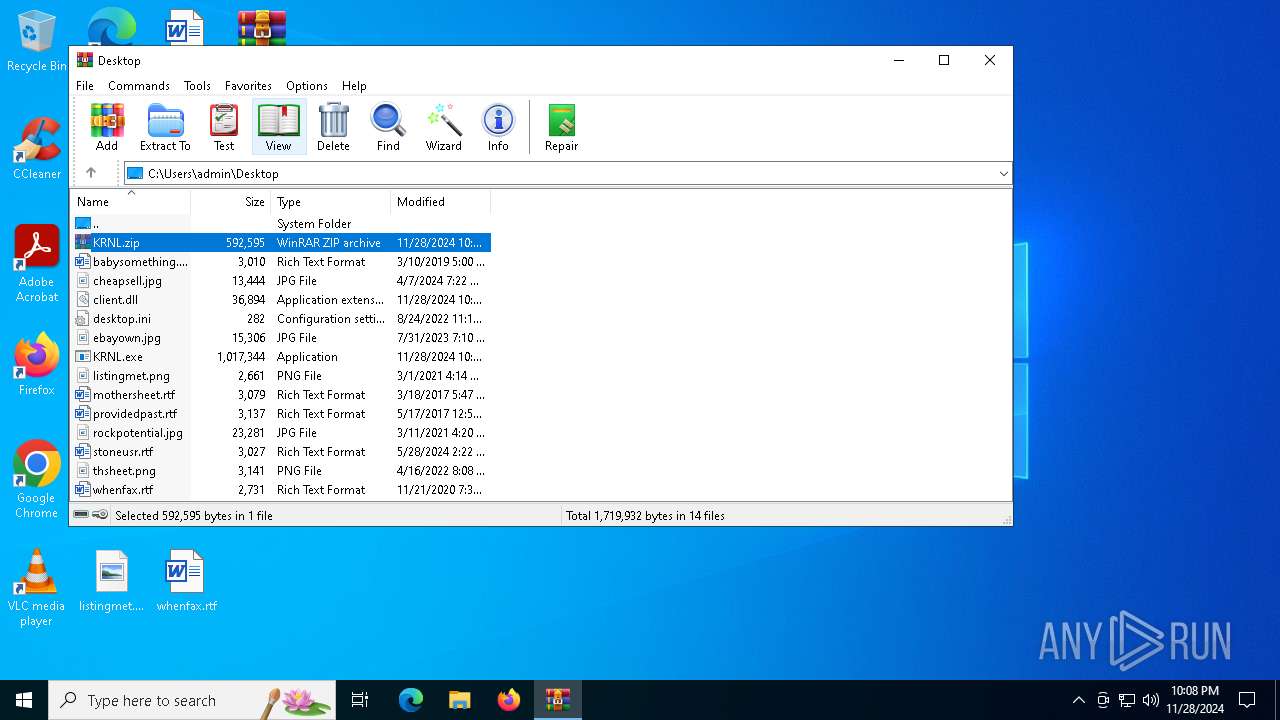
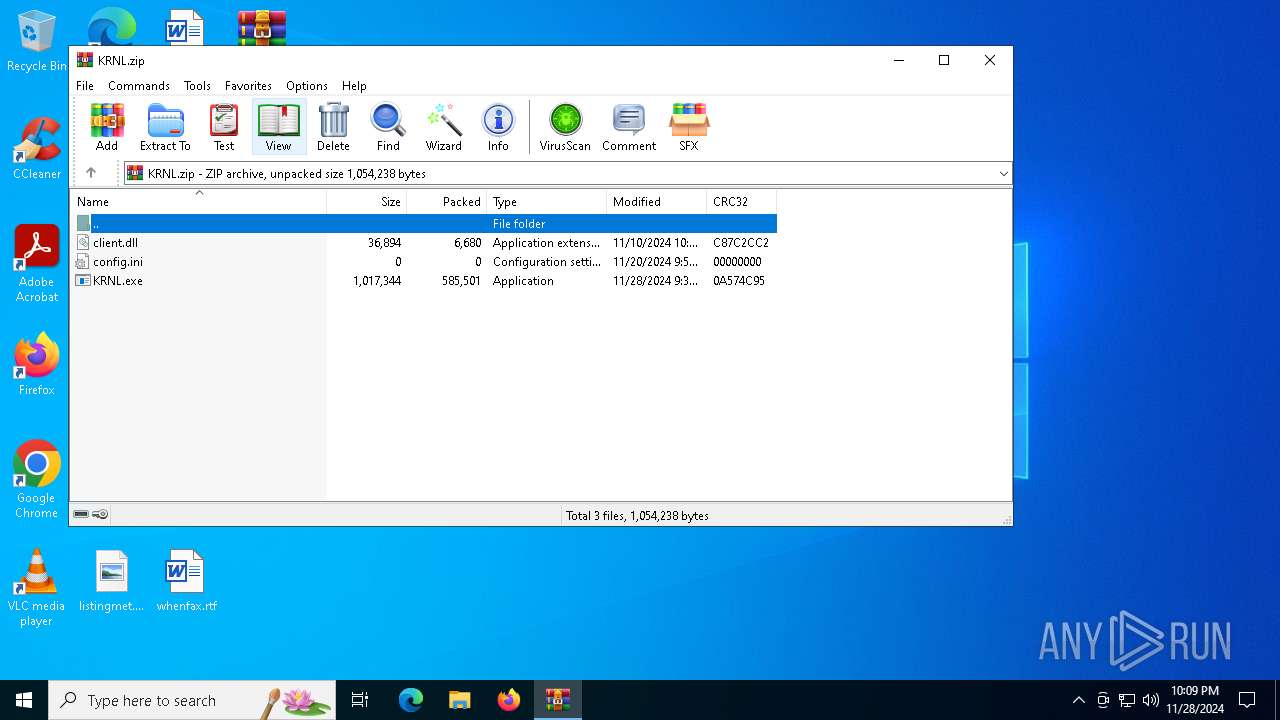
| File name: | KRNL.zip |
| Full analysis: | https://app.any.run/tasks/9ec1434d-241f-4489-a055-1d2f8aa839b6 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | November 28, 2024, 22:07:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E6F3A885C1F4F060B3BB1DB5C01C050E |
| SHA1: | D1217EFC9646BC983D8B3354D40549E574D23157 |
| SHA256: | F9F45ADDDCC93D75C10D4EEBDD4EAFEA0CF58869F390EEE3359DB41C1805C22E |
| SSDEEP: | 24576:8iNOWS8Mt9PrCqjjjiVp/+pGBRMzqCiP4GQyNW++IyF:8iNOWHMt9P+qvjiVp/wGBRMzXiP4GQOi |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6500)
LUMMA has been detected (SURICATA)
- KRNL.exe (PID: 6744)
- svchost.exe (PID: 2192)
Connects to the CnC server
- svchost.exe (PID: 2192)
Actions looks like stealing of personal data
- KRNL.exe (PID: 6744)
Steals credentials from Web Browsers
- KRNL.exe (PID: 6744)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- KRNL.exe (PID: 6744)
- svchost.exe (PID: 2192)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6500)
Application launched itself
- KRNL.exe (PID: 6660)
INFO
Checks supported languages
- KRNL.exe (PID: 6660)
- KRNL.exe (PID: 6744)
Manual execution by a user
- KRNL.exe (PID: 6660)
Reads the computer name
- KRNL.exe (PID: 6744)
- KRNL.exe (PID: 6660)
Reads the machine GUID from the registry
- KRNL.exe (PID: 6744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:28 12:36:36 |
| ZipCRC: | 0x0a574c95 |
| ZipCompressedSize: | 585501 |
| ZipUncompressedSize: | 1017344 |
| ZipFileName: | KRNL.exe |
Total processes
122
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6500 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\KRNL.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6660 | "C:\Users\admin\Desktop\KRNL.exe" | C:\Users\admin\Desktop\KRNL.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | KRNL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6744 | "C:\Users\admin\Desktop\KRNL.exe" | C:\Users\admin\Desktop\KRNL.exe | KRNL.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
5 450
Read events
5 387
Write events
63
Delete events
0
Modification events
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\KRNL.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
27
DNS requests
18
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1416 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 188.114.97.3:443 | https://marshal-zhukov.com/api | unknown | text | 16 b | malicious |
— | — | GET | 200 | 92.122.104.90:443 | https://steamcommunity.com/profiles/76561199724331900 | unknown | html | 34.3 Kb | whitelisted |
— | — | POST | 200 | 188.114.96.3:443 | https://marshal-zhukov.com/api | unknown | text | 16 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://marshal-zhukov.com/api | unknown | text | 16 b | malicious |
— | — | POST | 200 | 188.114.96.3:443 | https://marshal-zhukov.com/api | unknown | text | 16 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://marshal-zhukov.com/api | unknown | text | 16 b | malicious |
— | — | POST | 200 | 188.114.96.3:443 | https://marshal-zhukov.com/api | unknown | text | 48 b | malicious |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1416 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1416 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6744 | KRNL.exe | 92.122.104.90:443 | steamcommunity.com | AKAMAI-AS | DE | whitelisted |
1416 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
hallowed-noisy.sbs |
| unknown |
plastic-mitten.sbs |
| unknown |
looky-marked.sbs |
| unknown |
wrench-creter.sbs |
| unknown |
slam-whipp.sbs |
| unknown |
record-envyp.sbs |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (marshal-zhukov .com) |
6744 | KRNL.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (marshal-zhukov .com in TLS SNI) |
6744 | KRNL.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (marshal-zhukov .com in TLS SNI) |
6744 | KRNL.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (marshal-zhukov .com in TLS SNI) |
6744 | KRNL.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (marshal-zhukov .com in TLS SNI) |
6744 | KRNL.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (marshal-zhukov .com in TLS SNI) |
6744 | KRNL.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (marshal-zhukov .com in TLS SNI) |