| URL: | https://mega.nz/file/Mf0kWAhI#DEOJWLRNAb_-WeXAyWssn8JPJ3IY_ETx4pUaUsJ-uY4 |
| Full analysis: | https://app.any.run/tasks/f3612137-25c5-40cb-a162-842c587acef0 |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | July 19, 2024, 17:04:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CD802A3C037B9CF77BC251736AD720A7 |
| SHA1: | 63DF6C39D699DD9F122C5054EE393F17245FFC7D |
| SHA256: | F9E9C0F7C2D696A066B69EA3497090DC6D618CF94CF53CAF06B66C65D3E909D5 |
| SSDEEP: | 3:N8X/idk/3ypijTBMtloLb1woIpR:2IkaIyPgepR |
MALICIOUS
Stealers network behavior
- qacyxoji.au3 (PID: 5024)
HIJACKLOADER has been detected (YARA)
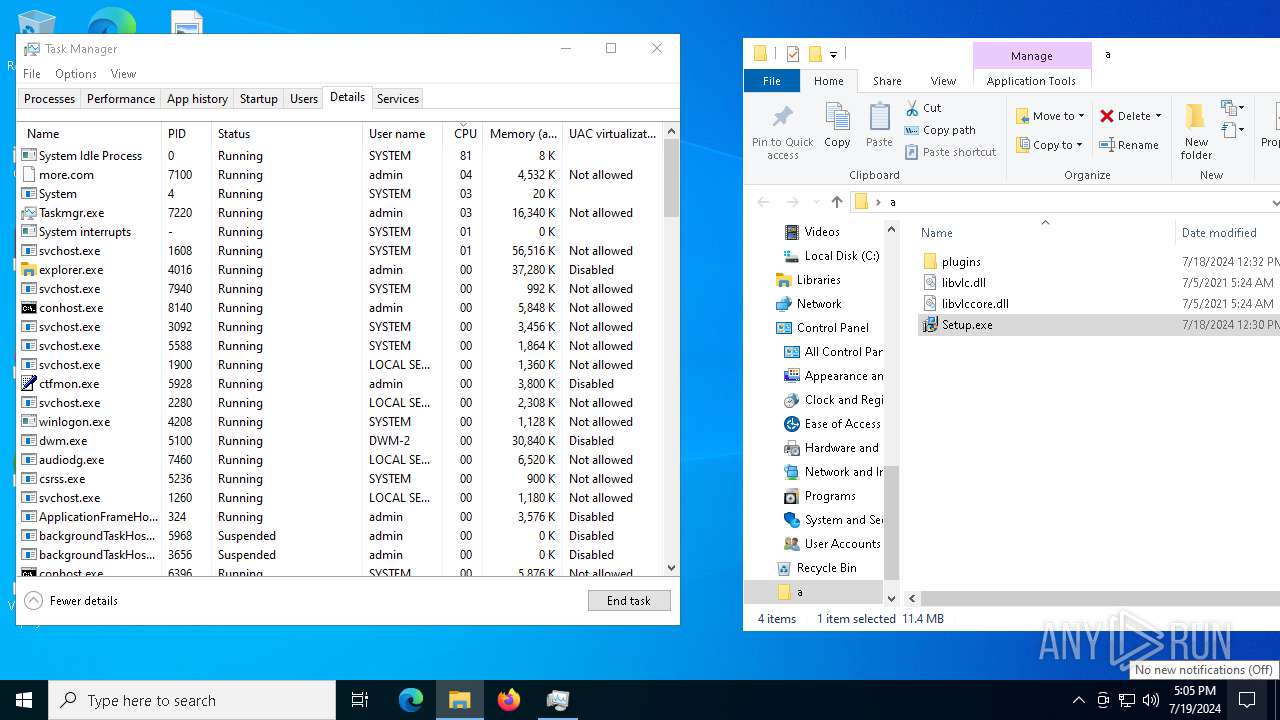
- more.com (PID: 7100)
- qacyxoji.au3 (PID: 5024)
LUMMA has been detected (YARA)
- more.com (PID: 7100)
- qacyxoji.au3 (PID: 5024)
LUMMA has been detected (SURICATA)
- qacyxoji.au3 (PID: 5024)
Actions looks like stealing of personal data
- qacyxoji.au3 (PID: 5024)
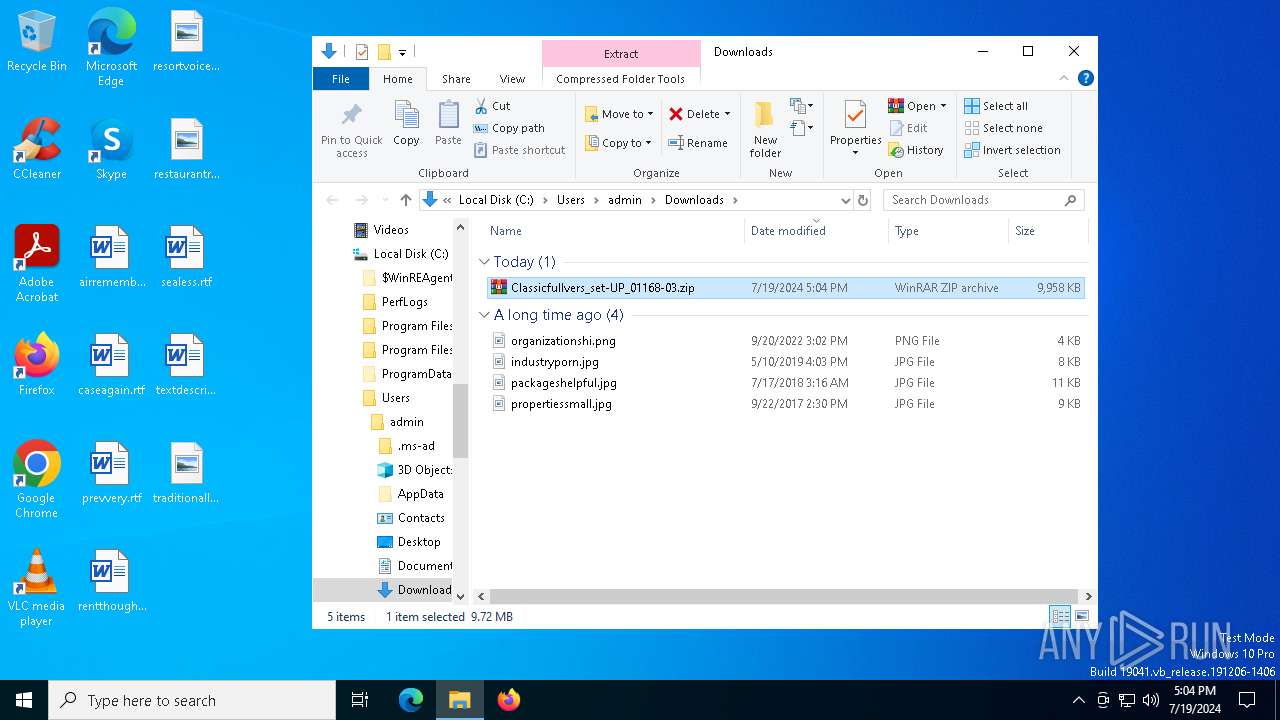
Drops the executable file immediately after the start
- more.com (PID: 7100)
SUSPICIOUS
Reads security settings of Internet Explorer
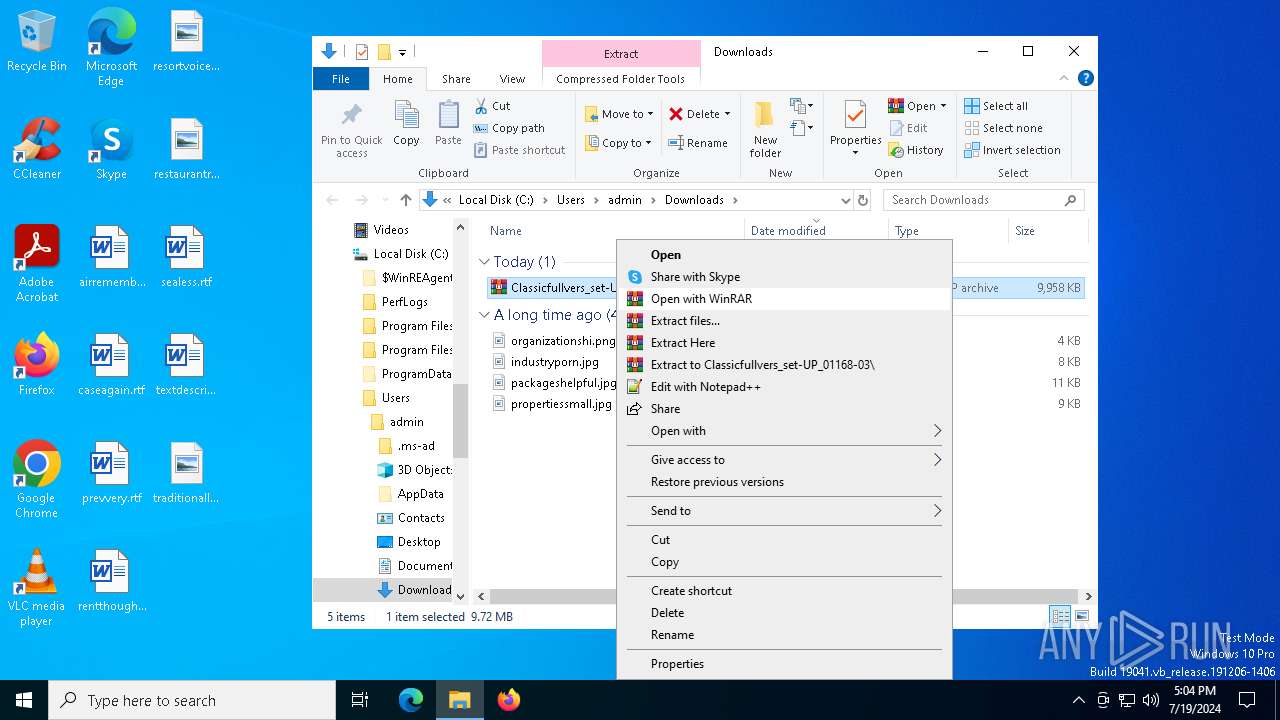
- WinRAR.exe (PID: 7196)
Application launched itself
- WinRAR.exe (PID: 7196)
- Taskmgr.exe (PID: 4020)
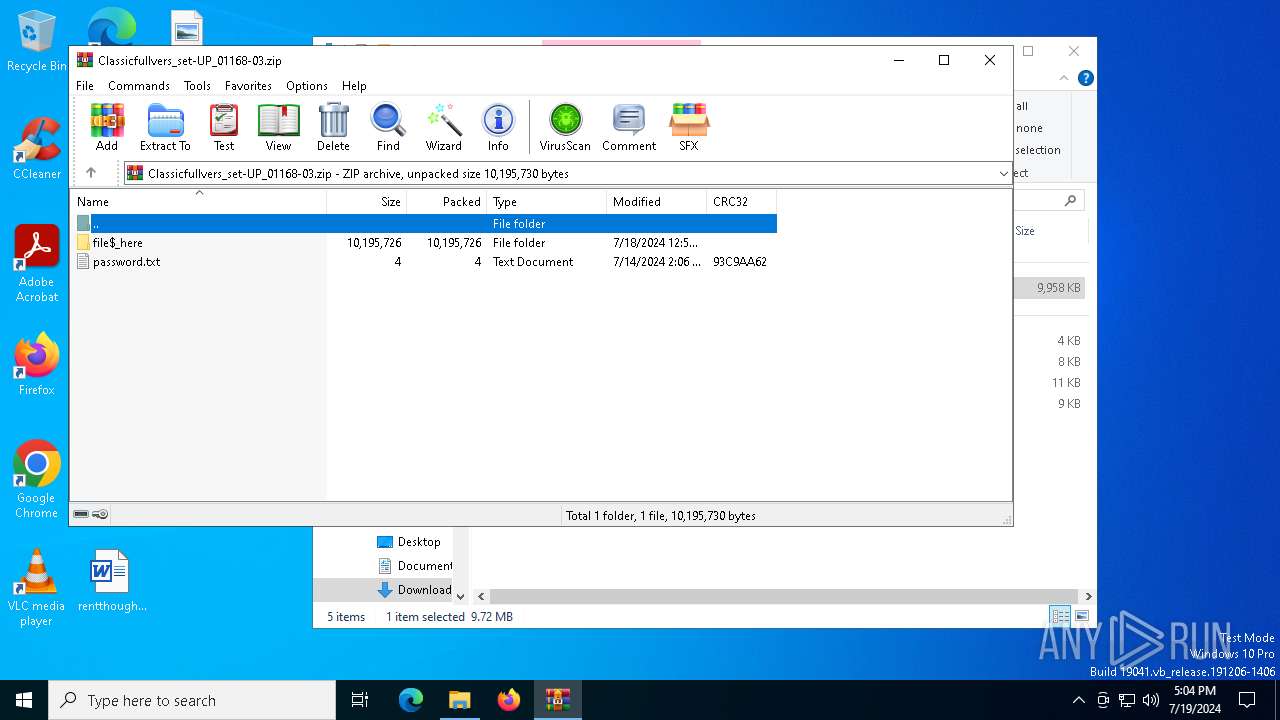
Process drops legitimate windows executable
- WinRAR.exe (PID: 2632)
Starts application with an unusual extension
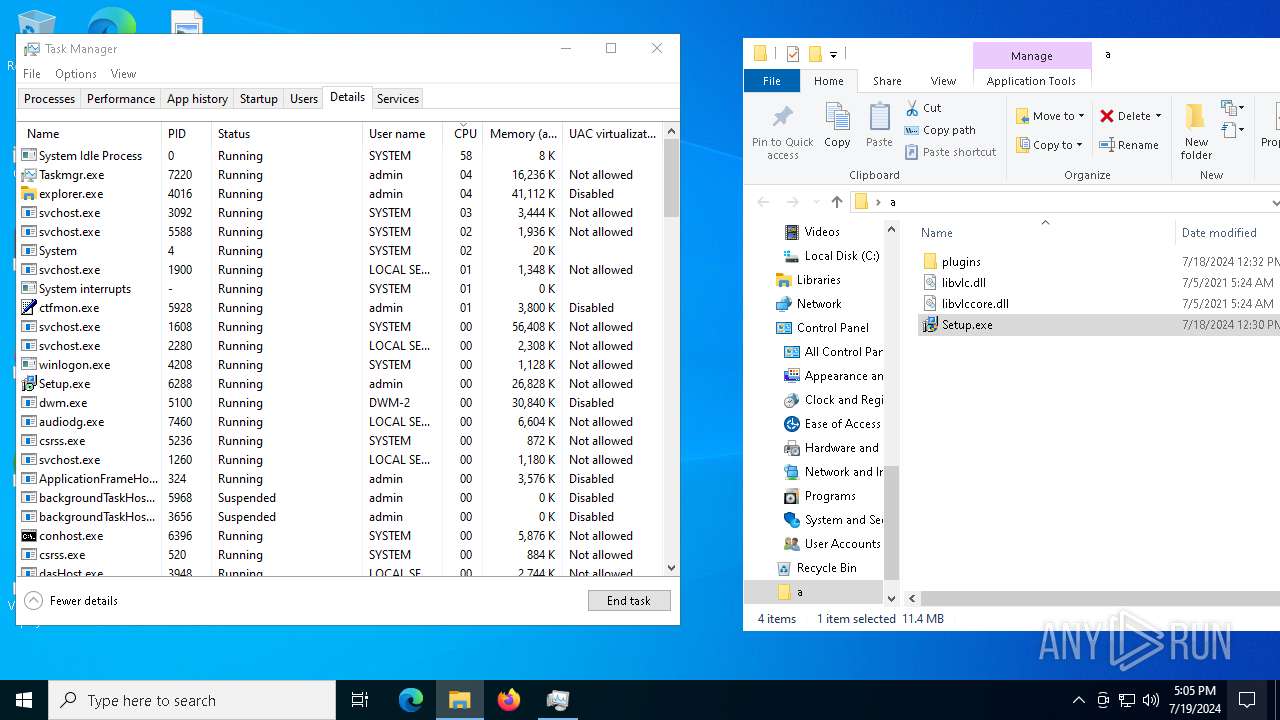
- Setup.exe (PID: 6288)
- more.com (PID: 7100)
Searches for installed software
- qacyxoji.au3 (PID: 5024)
Executable content was dropped or overwritten
- more.com (PID: 7100)
INFO
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 4020)
- Taskmgr.exe (PID: 7220)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2632)
The process uses the downloaded file
- WinRAR.exe (PID: 7196)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2632)
Checks supported languages
- Setup.exe (PID: 6288)
- more.com (PID: 7100)
- qacyxoji.au3 (PID: 5024)
Reads the computer name
- Setup.exe (PID: 6288)
- more.com (PID: 7100)
- qacyxoji.au3 (PID: 5024)
Create files in a temporary directory
- Setup.exe (PID: 6288)
- more.com (PID: 7100)
Reads the software policy settings
- qacyxoji.au3 (PID: 5024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Processunknown
C2 (9)upknittsoappz.shop
sicillyosopzv.shop
callosallsaospz.shop
outpointsozp.shop
shepherdlyopzc.shop
unseaffarignsk.shop
indexterityszcoxp.shop
liernessfornicsa.shop
lariatedzugspd.shop
(PID) Processunknown
C2 (9)upknittsoappz.shop
sicillyosopzv.shop
callosallsaospz.shop
outpointsozp.shop
shepherdlyopzc.shop
unseaffarignsk.shop
indexterityszcoxp.shop
liernessfornicsa.shop
lariatedzugspd.shop
Total processes
163
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1068 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
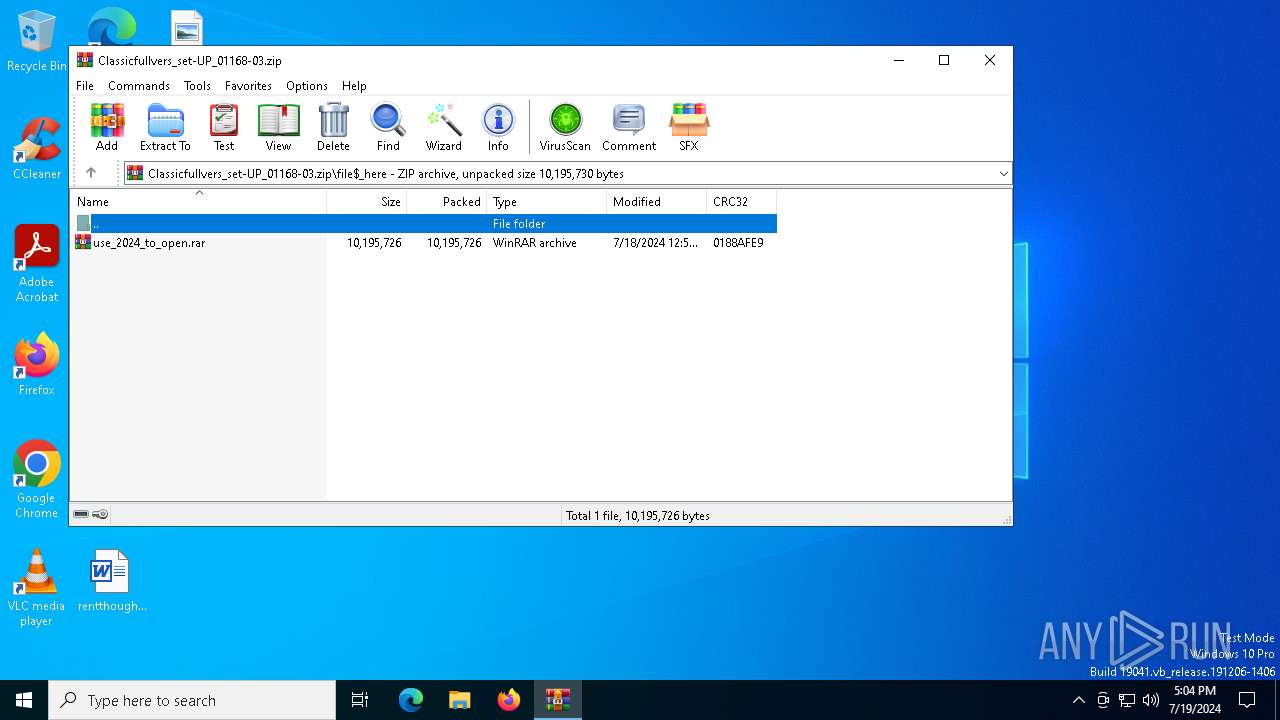
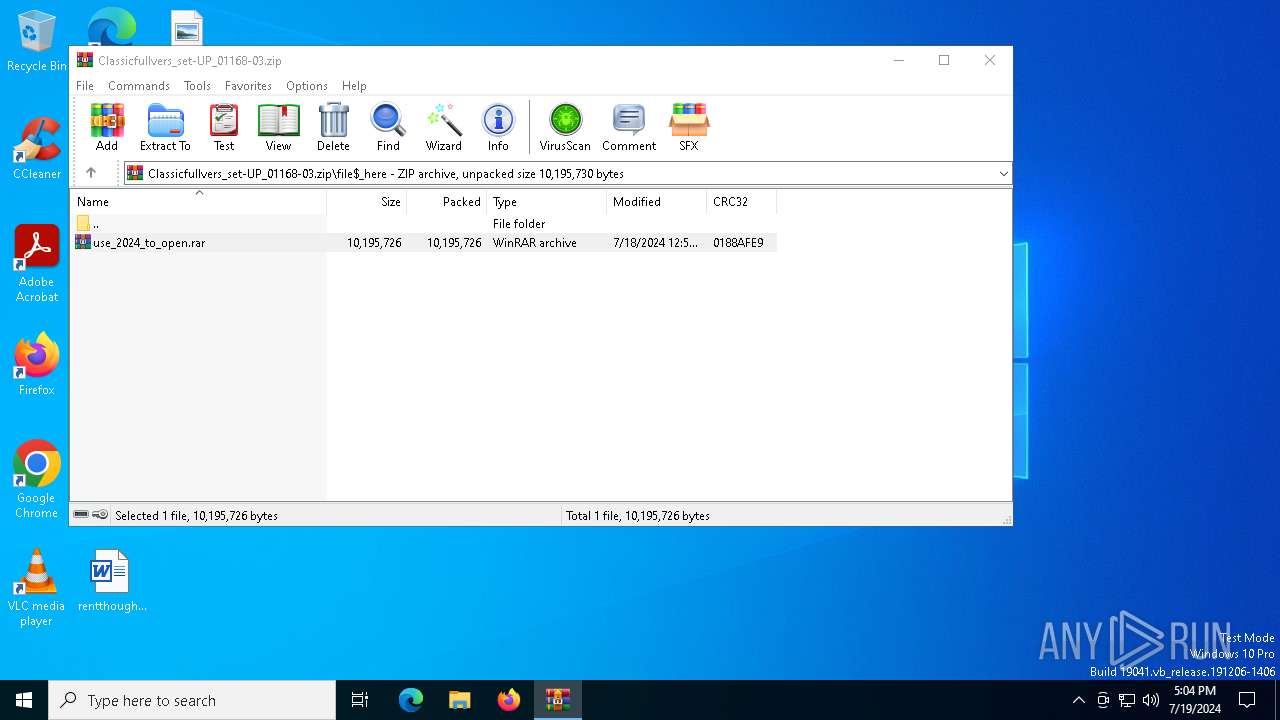
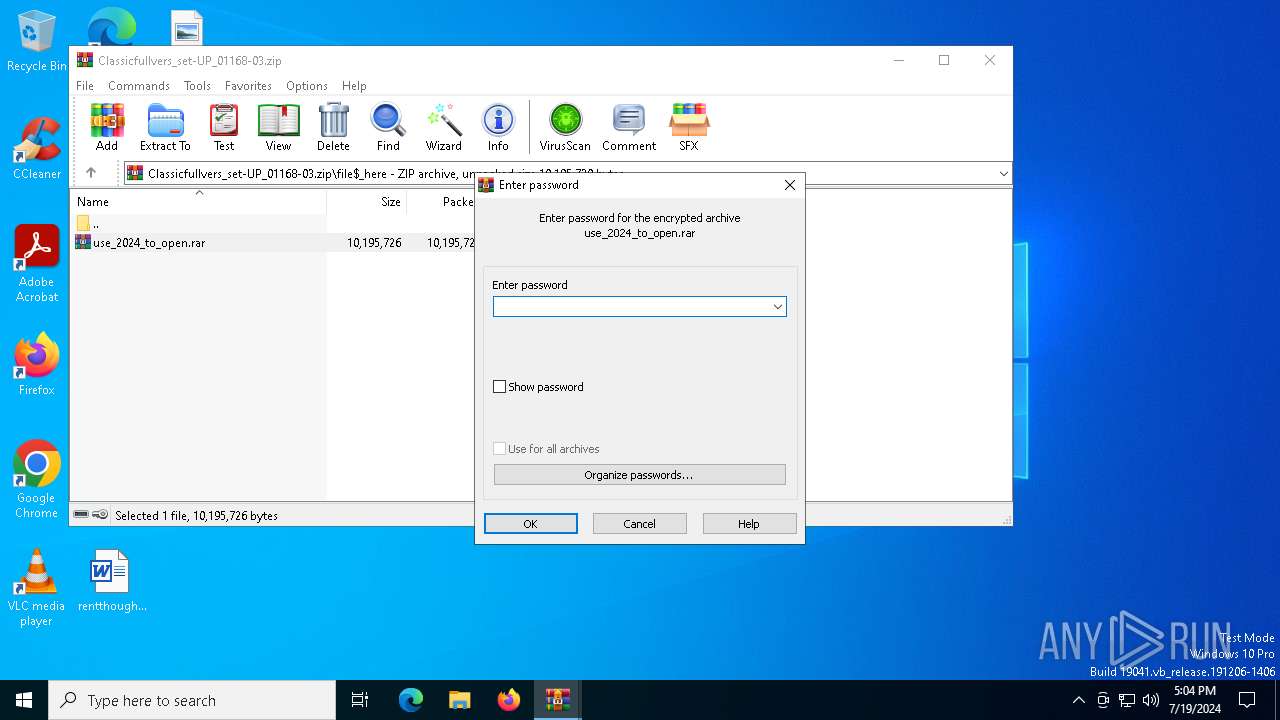
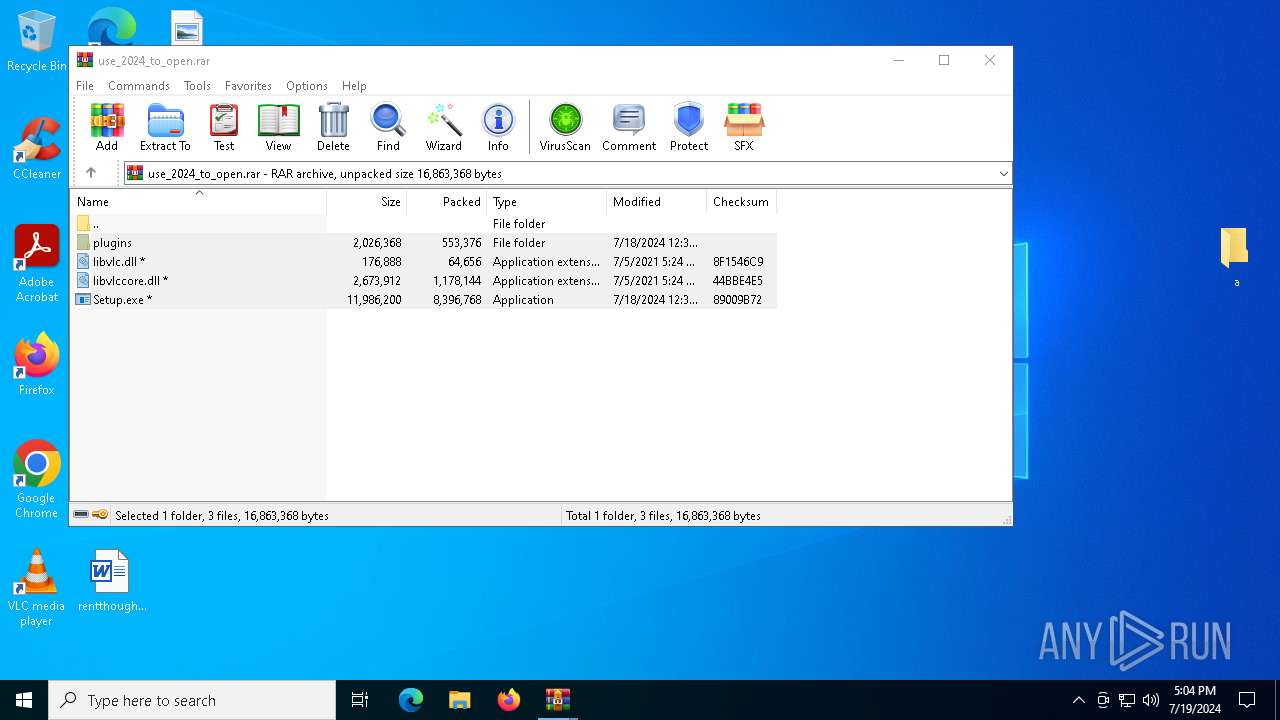
| 2632 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa7196.49618\use_2024_tо_оpen.rar | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4020 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5024 | C:\Users\admin\AppData\Local\Temp\qacyxoji.au3 | C:\Users\admin\AppData\Local\Temp\qacyxoji.au3 | more.com | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: HIGH Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
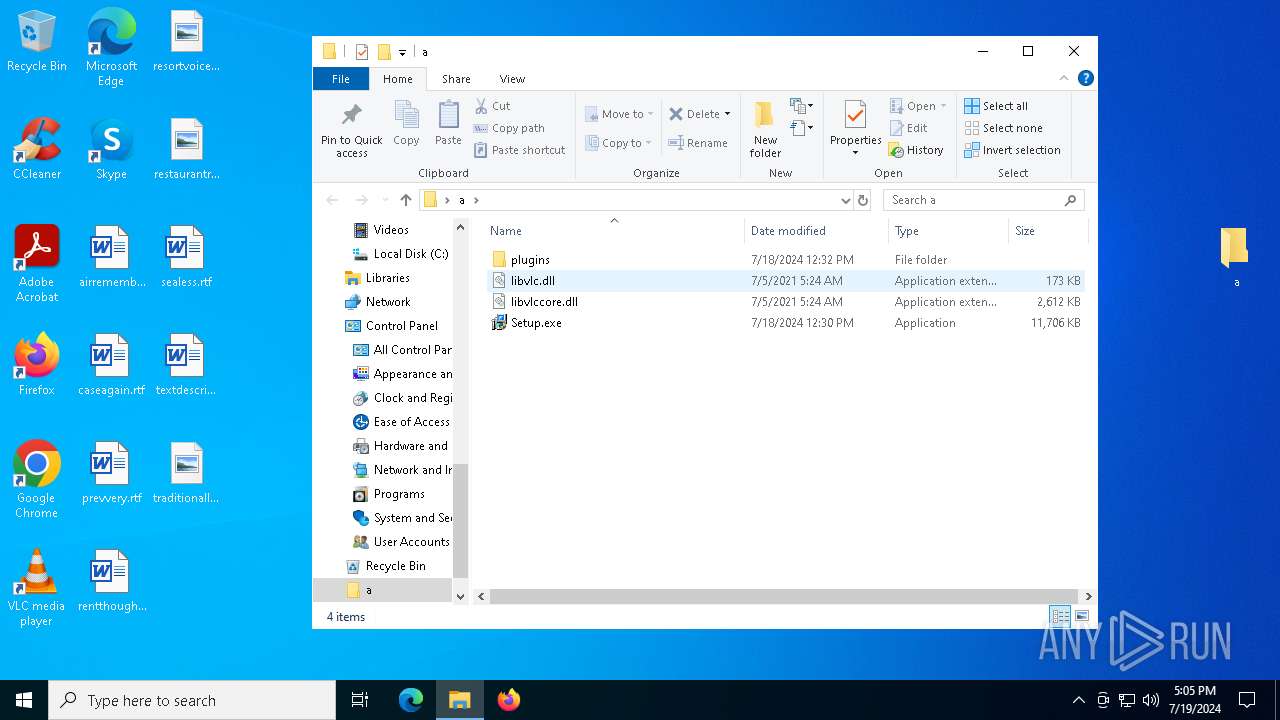
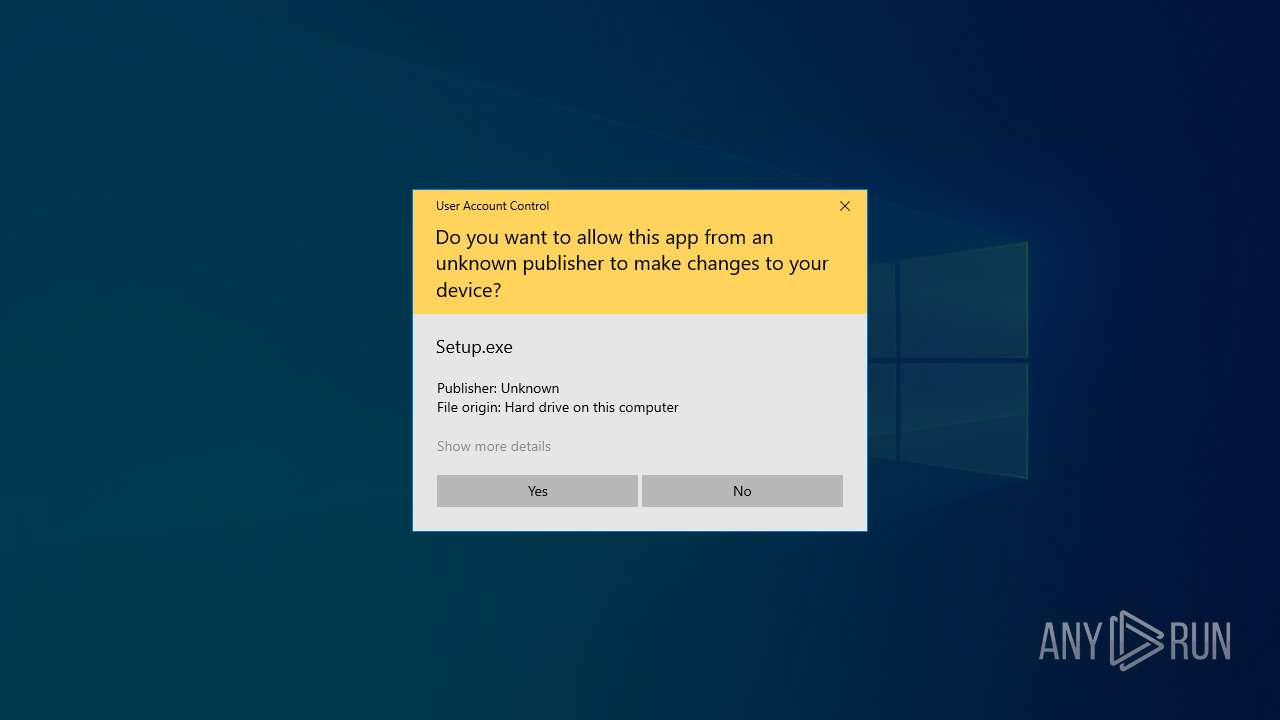
| 6288 | "C:\Users\admin\Desktop\a\Setup.exe" | C:\Users\admin\Desktop\a\Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 7100 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
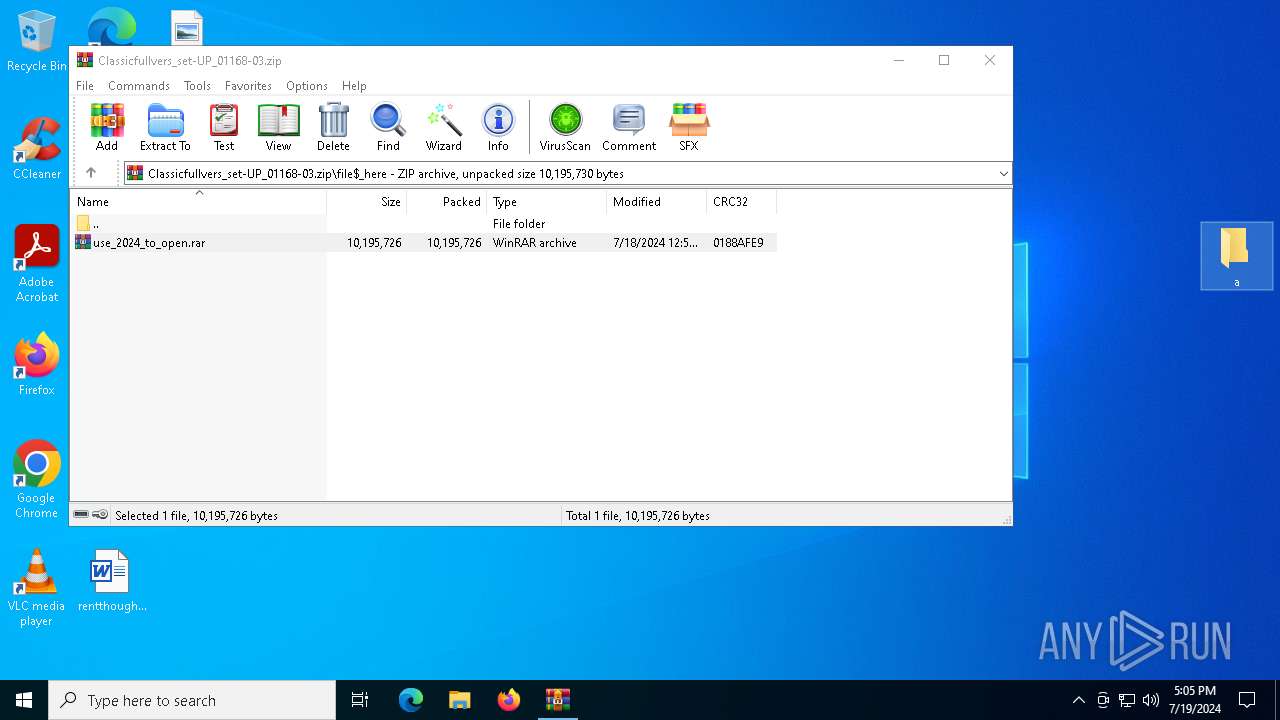
| 7196 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Classicfullvers_set-UP_01168-03.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7220 | "C:\WINDOWS\system32\taskmgr.exe" /1 | C:\Windows\System32\Taskmgr.exe | — | Taskmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 992
Read events
15 917
Write events
67
Delete events
8
Modification events
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Classicfullvers_set-UP_01168-03.zip | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
9
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7196.49618\use_2024_tо_оpen.rar | — | |
MD5:— | SHA256:— | |||
| 7100 | more.com | C:\Users\admin\AppData\Local\Temp\xcqjofsgqjqogx | — | |
MD5:— | SHA256:— | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2632.629\plugins\lang-1049.dll | executable | |
MD5:0AC98A4BFC717523E344010A42C2F4BA | SHA256:68546336232AA2BE277711AFA7C1F08ECD5FCC92CC182F90459F0C61FB39507F | |||
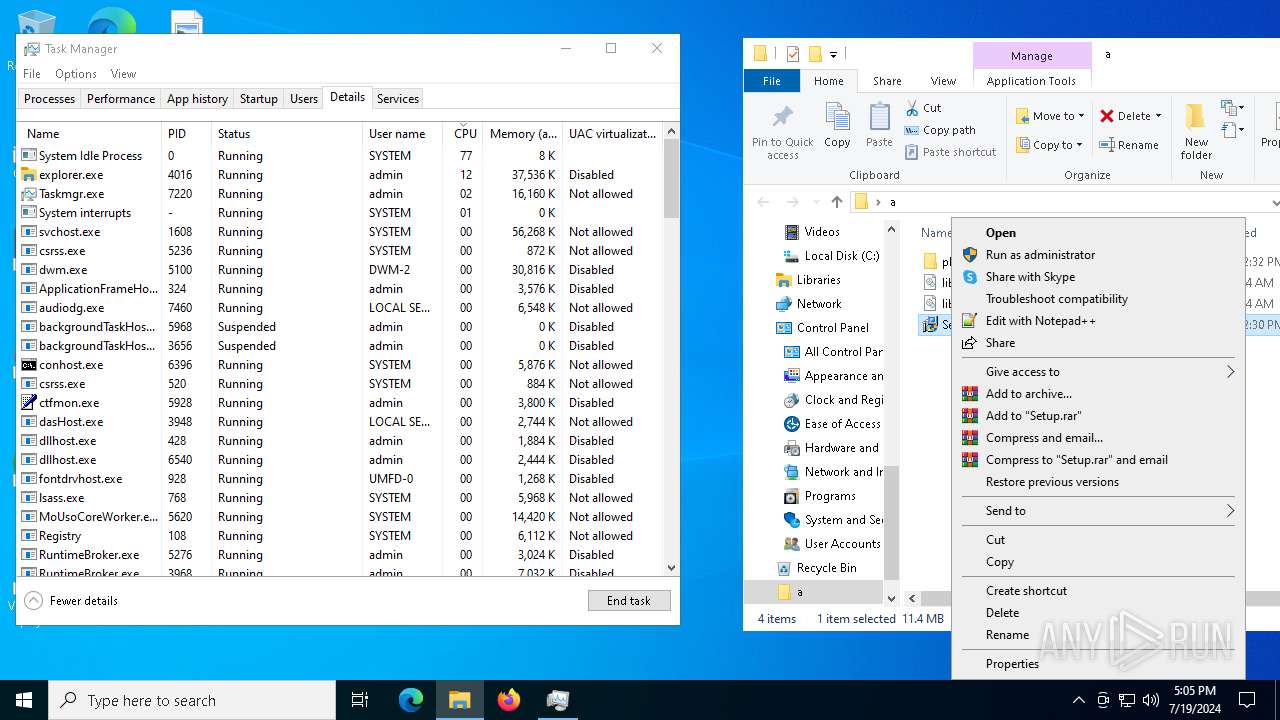
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2632.629\Setup.exe | executable | |
MD5:0D2FF13B2906B77339600254EDB31F0D | SHA256:FDAF718247FD123A912A6858B536DE2DB3A217A4845416719C195C74DBF4CFB5 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2632.629\plugins\Microsoft.VisualStudio.VsWebProtocol | executable | |
MD5:91ACF072FE60B3EF9867FAEC1A7A8CB0 | SHA256:1F49ADC807A564E7C1ECF32F58074A1230A6FE4764E8F54CE7FFA8C2E880DCCA | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2632.629\plugins\lang-1058.dll | executable | |
MD5:41C75E831A5571C3F72287794391A0E6 | SHA256:B3AD99AFDAEE3B9365E7A3FFCC44C2761E22A4F92DFF5E5EFDC52F6B08EA0105 | |||
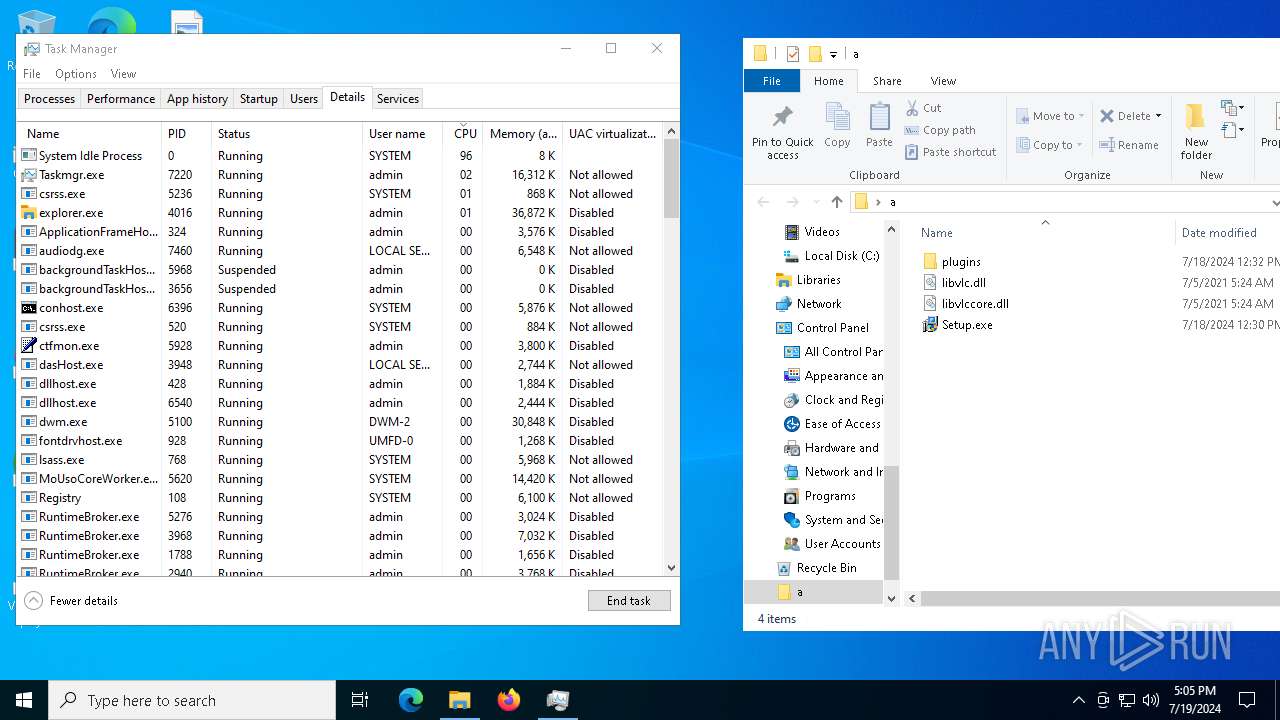
| 6288 | Setup.exe | C:\Users\admin\AppData\Local\Temp\b3175f7f | binary | |
MD5:8E198B99AEE718122925A8A043D20C8E | SHA256:8C17A4686A5E4FC5490157A9C2CB2C7B9E2542719963D7397A48BD9C0CB36B81 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2632.629\libvlc.dll | executable | |
MD5:96214B94B796BFFC48D63289854AE5A2 | SHA256:528C416CFB4813EE5F1DA52743EF4ADB20043171230098B27E25D1DD90E3F288 | |||
| 4020 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2632.629\libvlccore.dll | executable | |
MD5:E25413BB41C2F239FFDD3569F76E74B0 | SHA256:9126D9ABF91585456000FFFD9336478E91B9EA07ED2A25806A4E2E0437F96D29 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
92
DNS requests
102
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 184.24.77.47:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 172.217.16.131:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 184.24.77.47:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 184.24.77.47:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 172.217.16.131:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 184.24.77.80:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | unknown |
— | — | POST | 200 | 184.24.77.80:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | unknown |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4716 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 31.216.144.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
— | — | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
— | — | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
— | — | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
mega.nz |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
— | — | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
— | — | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
— | — | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
— | — | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
— | — | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |