| File name: | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe |
| Full analysis: | https://app.any.run/tasks/593a58e4-1040-4712-abc9-55f742e61b7a |
| Verdict: | Malicious activity |
| Threats: | Raccoon is an info stealer type malware available as a Malware as a Service. It can be obtained for a subscription and costs $200 per month. Raccoon malware has already infected over 100,000 devices and became one of the most mentioned viruses on the underground forums in 2019. |
| Analysis date: | March 24, 2024, 04:31:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E79211AC8585538E841B54C4A72AF824 |
| SHA1: | E6136C5E0724F0C720E48B3EEA0339B91F53EBFC |
| SHA256: | F9DB076BD8F99C606CDAE2D6EB5F4EC112A705CF285138331B33AE180C352FEC |
| SSDEEP: | 786432:SZ1AIF3dJszFfSDUPf+VKlRSadNdUTDaRXXaNu947NV3:U7ihKDUXiK3JndyGF/94f |
MALICIOUS
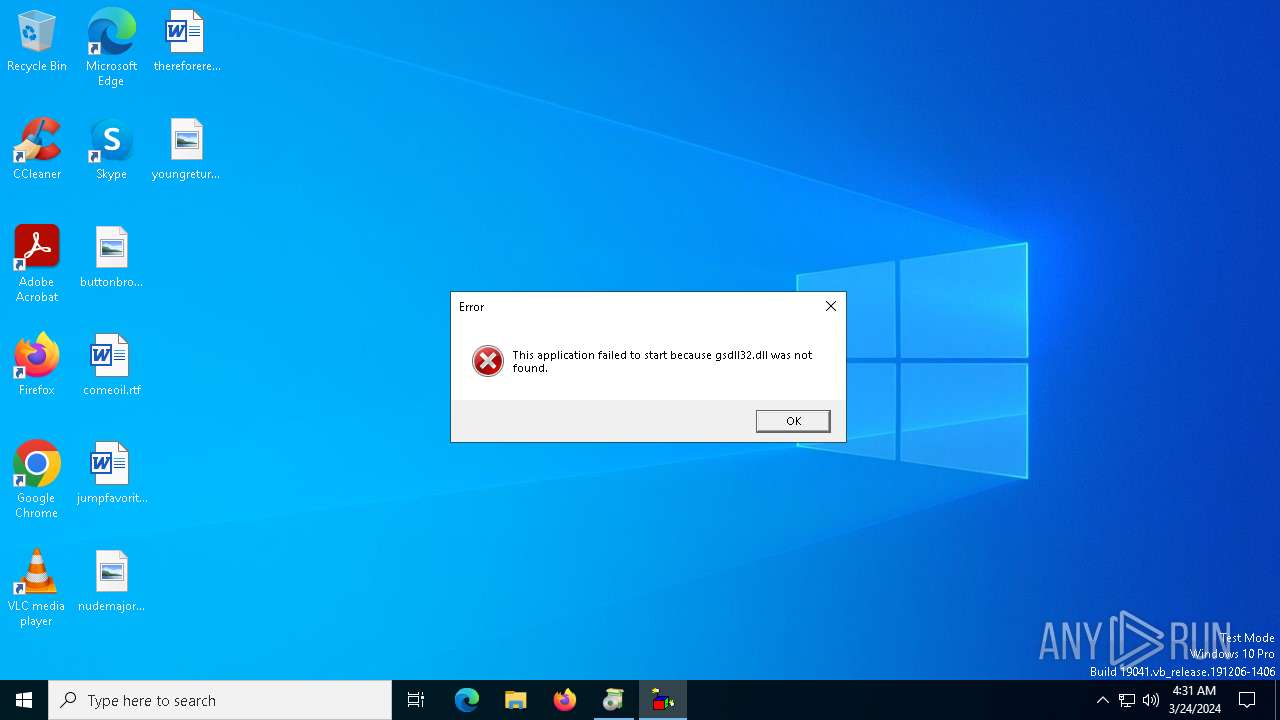
Drops the executable file immediately after the start
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe (PID: 3536)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe (PID: 1404)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 5116)
Bypass execution policy to execute commands
- powershell.exe (PID: 7048)
RACCOON has been detected (YARA)
- Snapseed.exe (PID: 5092)
RACCOON has been detected (SURICATA)
- Snapseed.exe (PID: 5092)
Connects to the CnC server
- Snapseed.exe (PID: 5092)
SUSPICIOUS
Reads the date of Windows installation
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 1192)
Executable content was dropped or overwritten
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe (PID: 1404)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe (PID: 3536)
Reads the Windows owner or organization settings
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
Reads security settings of Internet Explorer
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 1192)
- Snapseed.exe (PID: 5092)
Starts CMD.EXE for commands execution
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
Executing commands from a ".bat" file
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
The process hide an interactive prompt from the user
- cmd.exe (PID: 5116)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5116)
Base64-obfuscated command line is found
- cmd.exe (PID: 5116)
Starts a Microsoft application from unusual location
- Snapseed.exe (PID: 2292)
- Snapseed.exe (PID: 5092)
- Snapseed.exe (PID: 5916)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 5116)
Accesses current user name via WMI (SCRIPT)
- powershell.exe (PID: 7048)
The process creates files with name similar to system file names
- powershell.exe (PID: 7048)
The process executes VB scripts
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 1192)
Process drops legitimate windows executable
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
Process drops SQLite DLL files
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
Application launched itself
- Snapseed.exe (PID: 2292)
Connects to the server without a host name
- Snapseed.exe (PID: 5092)
Non-standard symbols in registry
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
INFO
Process checks computer location settings
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 1192)
Checks supported languages
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe (PID: 3536)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe (PID: 1404)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 1192)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
- Snapseed.exe (PID: 2292)
- Snapseed.exe (PID: 5092)
Create files in a temporary directory
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe (PID: 3536)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe (PID: 1404)
Creates files or folders in the user directory
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
Reads the computer name
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 1192)
- f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp (PID: 6476)
- Snapseed.exe (PID: 5092)
- Snapseed.exe (PID: 2292)
Reads the machine GUID from the registry
- Snapseed.exe (PID: 5092)
- Snapseed.exe (PID: 2292)
Checks proxy server information
- Snapseed.exe (PID: 5092)
- slui.exe (PID: 3652)
Reads the software policy settings
- slui.exe (PID: 3652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Raccoon
(PID) Process(5092) Snapseed.exe
C2 (1)http://91.107.239.231:80
Keys
xor3c1e19ca7e90eb061bab2909496bea51
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 98816 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | xrecode3 |
| FileDescription: | XRECODE 3 Pro Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | XRECODE 3 Pro |
| ProductVersion: | 4.8.4.3 |
Total processes
140
Monitored processes
12
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1192 | "C:\Users\admin\AppData\Local\Temp\is-P1T1C.tmp\f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp" /SL5="$401CC,32170687,841728,C:\Users\admin\AppData\Local\Temp\f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe" | C:\Users\admin\AppData\Local\Temp\is-P1T1C.tmp\f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | — | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe | |||||||||||
User: admin Company: xrecode3 Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1404 | "C:\Users\admin\AppData\Local\Temp\f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe" | C:\Users\admin\AppData\Local\Temp\f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe | explorer.exe | ||||||||||||
User: admin Company: xrecode3 Integrity Level: MEDIUM Description: XRECODE 3 Pro Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2292 | "C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\XRECODE 3 Pro\Snapseed.exe" | C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\XRECODE 3 Pro\Snapseed.exe | — | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Authenticode(R) - signing and verifying tool Exit code: 0 Version: 4.00 (th2_release_sec.160328-1908) Modules
| |||||||||||||||
| 3536 | "C:\Users\admin\AppData\Local\Temp\f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe" /SPAWNWND=$4004A /NOTIFYWND=$401CC | C:\Users\admin\AppData\Local\Temp\f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | ||||||||||||
User: admin Company: xrecode3 Integrity Level: HIGH Description: XRECODE 3 Pro Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3652 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5092 | "C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\XRECODE 3 Pro\Snapseed.exe" | C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\XRECODE 3 Pro\Snapseed.exe | Snapseed.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Authenticode(R) - signing and verifying tool Exit code: 4294967295 Version: 4.00 (th2_release_sec.160328-1908) Modules
Raccoon(PID) Process(5092) Snapseed.exe C2 (1)http://91.107.239.231:80 Keys xor3c1e19ca7e90eb061bab2909496bea51 | |||||||||||||||
| 5116 | "C:\WINDOWS\system32\cmd.exe" /C ""C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\WebrootCommAgentService.bat"" | C:\Windows\SysWOW64\cmd.exe | — | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5912 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\XRECODE 8 Pro\FormatMessage.vbs" | C:\Windows\SysWOW64\wscript.exe | — | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5916 | "C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\XRECODE 3 Pro\Snapseed.exe" | C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\XRECODE 3 Pro\Snapseed.exe | — | Snapseed.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Authenticode(R) - signing and verifying tool Exit code: 4294967295 Version: 4.00 (th2_release_sec.160328-1908) Modules
| |||||||||||||||
Total events
11 822
Read events
11 783
Write events
33
Delete events
6
Modification events
| (PID) Process: | (6476) f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 4C190000264D5B1DA47DDA01 | |||
| (PID) Process: | (6476) f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 160C3E966E6F3FDB0116489A8007F771E6A5CCF847B54684EA5AE61985079AE0 | |||
| (PID) Process: | (6476) f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6476) f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\XRECODE 3 Pro\base.dll | |||
| (PID) Process: | (6476) f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 1B3B355614267EE27D2467D65EBB72E14BB2B41A4841A3D76AA5A761C0A8F0FF | |||
| (PID) Process: | (7048) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7048) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7048) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7048) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1192) f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
158
Suspicious files
6
Text files
19
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 1404 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.exe | C:\Users\admin\AppData\Local\Temp\is-P1T1C.tmp\f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | executable | |
MD5:5CAFAFE235446F048B1F54C6419A91F0 | SHA256:CC472469FC5619D08938372C578D7CC7282B2FFE67B1457BAA859A49A804279E | |||
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\XRECODE 3 Pro\eos.dll | executable | |
MD5:74866B0AD75E124534729CA7D97F7272 | SHA256:F668DEB9DEB8E2417E278D5397CFCC18F12AB735F37FAFC4CCA6DDE629188D21 | |||
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\Temp\is-3GUID.tmp\innocallback.dll | executable | |
MD5:1C55AE5EF9980E3B1028447DA6105C75 | SHA256:6AFA2D104BE6EFE3D9A2AB96DBB75DB31565DAD64DD0B791E402ECC25529809F | |||
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\XRECODE 3 Pro\is-71F4K.tmp | executable | |
MD5:4BAA06B1EF7109AC18DC9E58A8652EBD | SHA256:78478A574BFCE81B4E7742D36FD6012B1B4B9A2D3C45A70C84233BBD4F8C7B4F | |||
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\XRECODE 3 Pro\is-LTCN8.tmp | executable | |
MD5:0352AEBD6674FDAF9688CAAE374259E8 | SHA256:7A454F18E0112874B65EF9EB27F7D2F1A9DE5EE6AF7FB0DB39BCE0E45D78C135 | |||
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\XRECODE 3 Pro\ColorManager.dll | executable | |
MD5:4BAA06B1EF7109AC18DC9E58A8652EBD | SHA256:78478A574BFCE81B4E7742D36FD6012B1B4B9A2D3C45A70C84233BBD4F8C7B4F | |||
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\XRECODE 3 Pro\devjwprf.dll | executable | |
MD5:9DB459F64EDF9B748BE285AB41201F56 | SHA256:6A25F497428FF6A0C224A8F9BD800A4459C2D74BE09D447D81752FC3725D14AB | |||
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\XRECODE 3 Pro\is-CI96M.tmp | executable | |
MD5:74866B0AD75E124534729CA7D97F7272 | SHA256:F668DEB9DEB8E2417E278D5397CFCC18F12AB735F37FAFC4CCA6DDE629188D21 | |||
| 6476 | f9db076bd8f99c606cdae2d6eb5f4ec112a705cf285138331b33ae180c352fec.tmp | C:\Users\admin\AppData\Local\XRECODE 3 Pro\is-IADFI.tmp | executable | |
MD5:0780FDE45D90EF4977183E6FDAD7365A | SHA256:363EB6DB63FA7AE11AF8A4BD085471461A9D7FDE44153F7CB1F34000D700DBE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
31
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3996 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1260 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
2772 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
6100 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
5092 | Snapseed.exe | POST | 403 | 128.140.90.181:80 | http://128.140.90.181/ | unknown | html | 146 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3996 | svchost.exe | 40.126.32.134:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1280 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3996 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4080 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3996 | svchost.exe | 20.190.160.20:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1260 | backgroundTaskHost.exe | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1280 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1260 | backgroundTaskHost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5092 | Snapseed.exe | A Network Trojan was detected | ET MALWARE Win32/RecordBreaker CnC Checkin M1 |