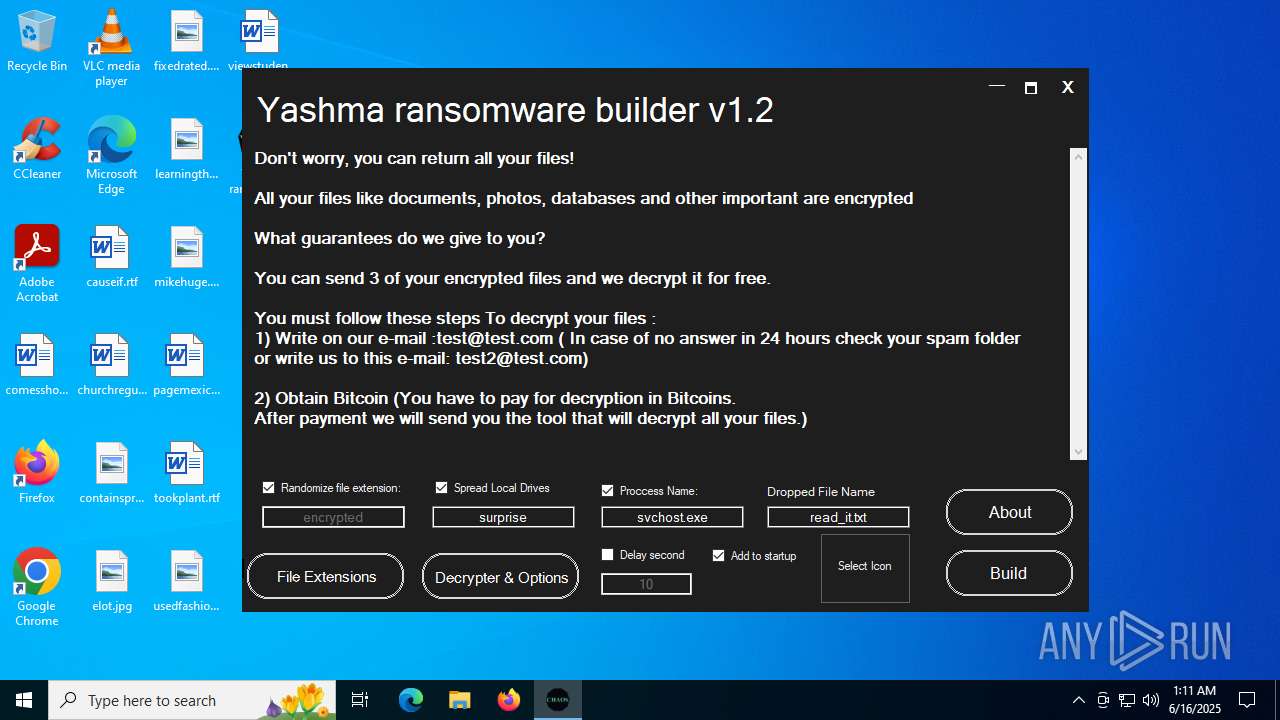
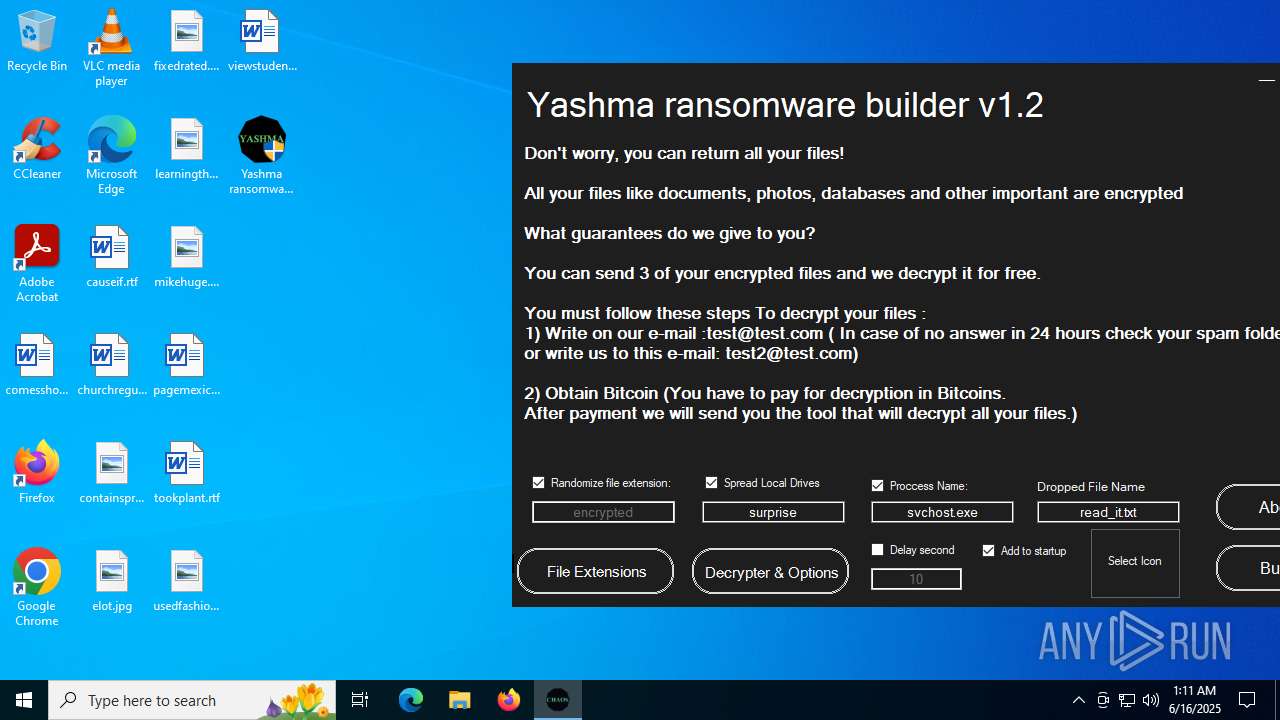
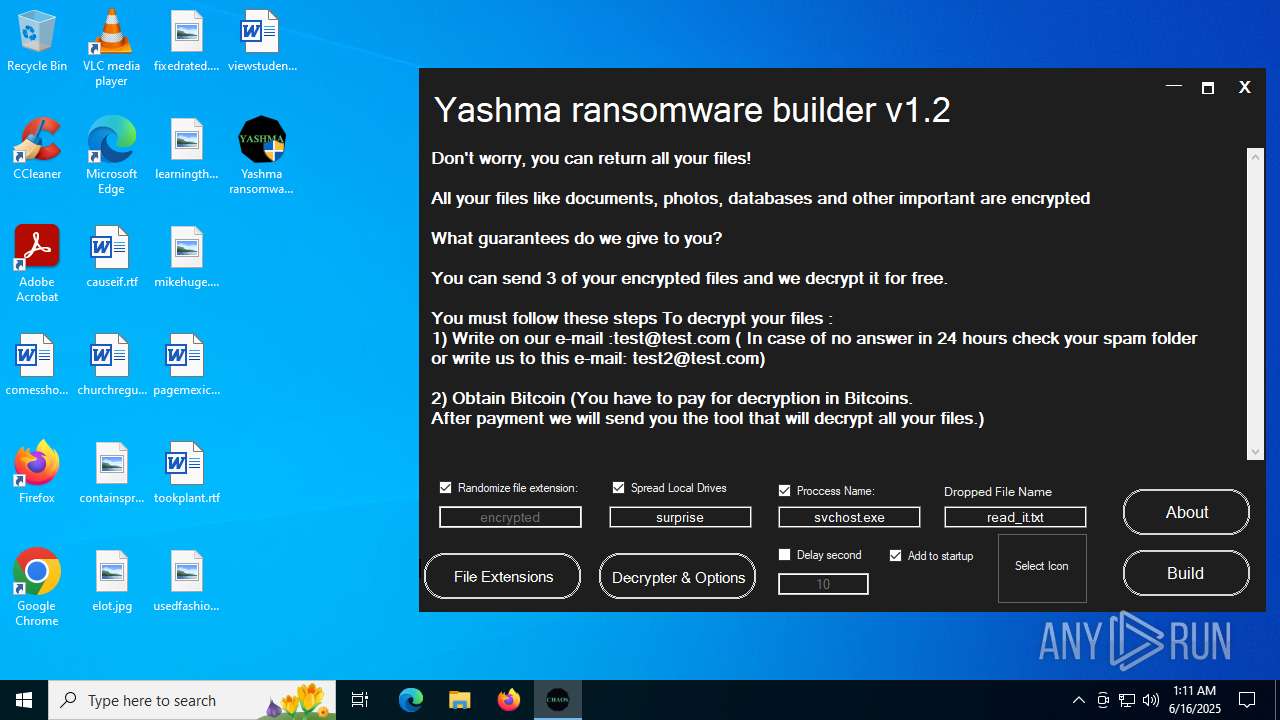
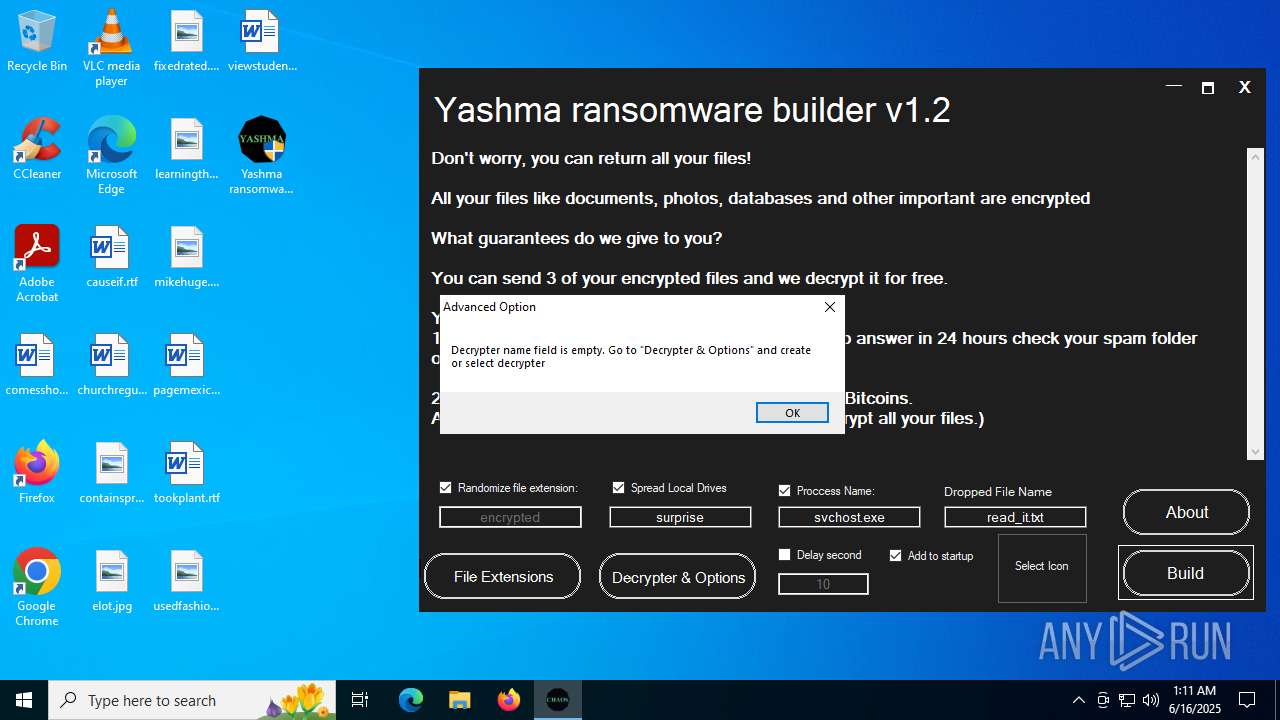
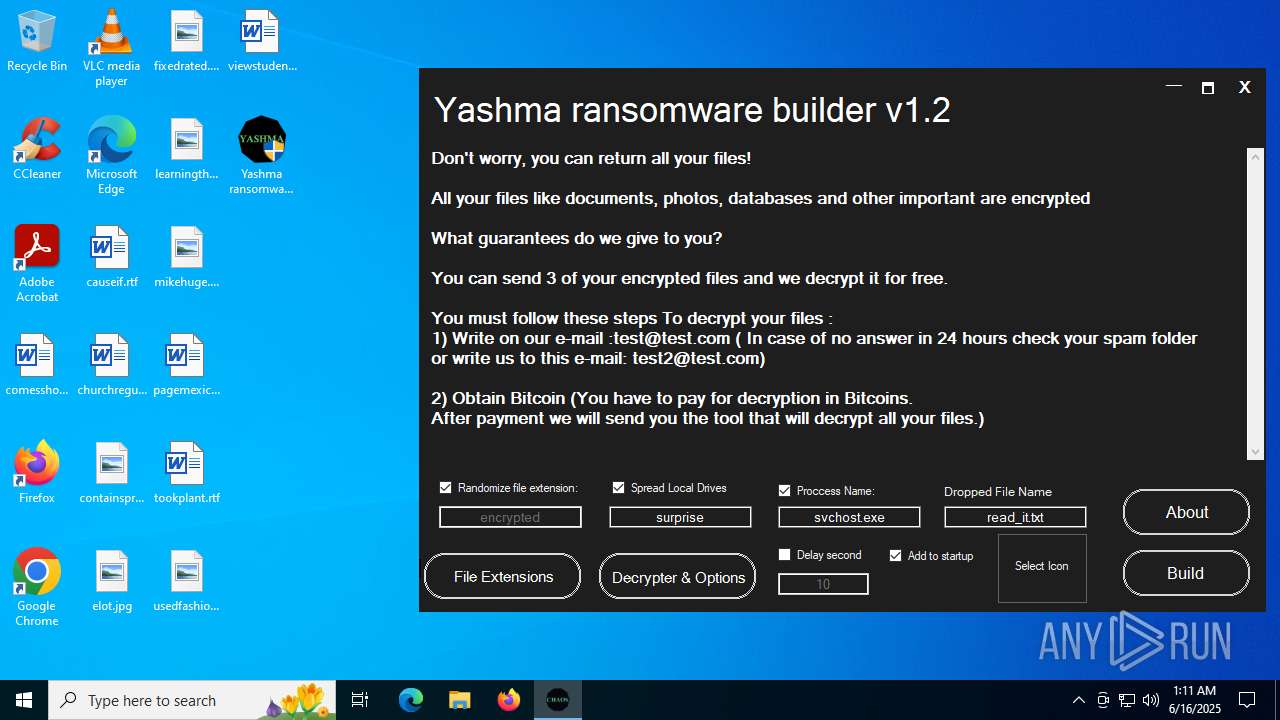
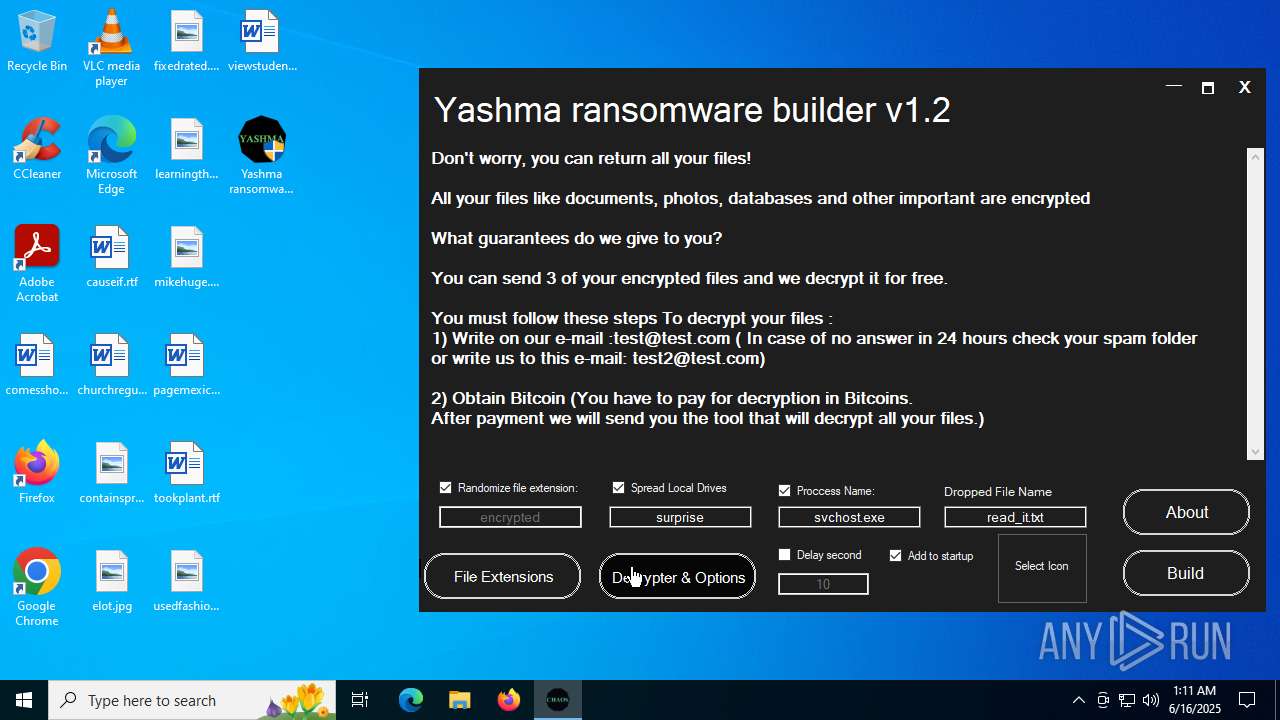
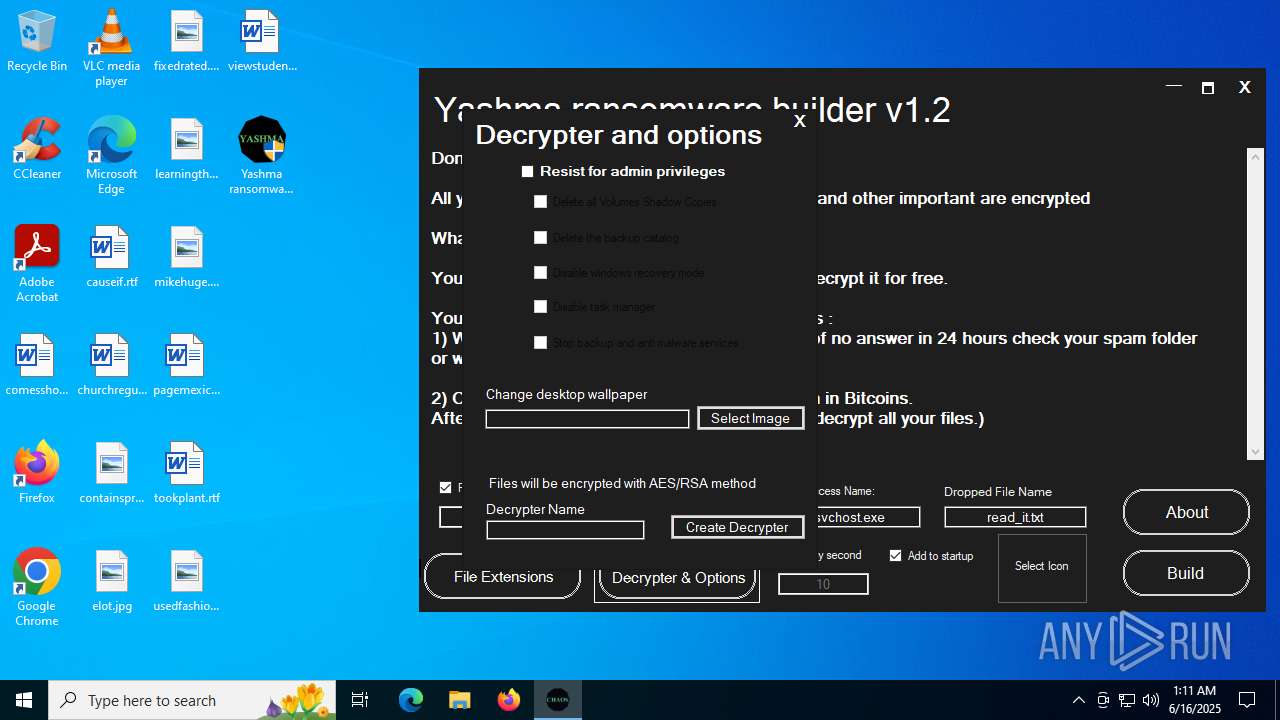
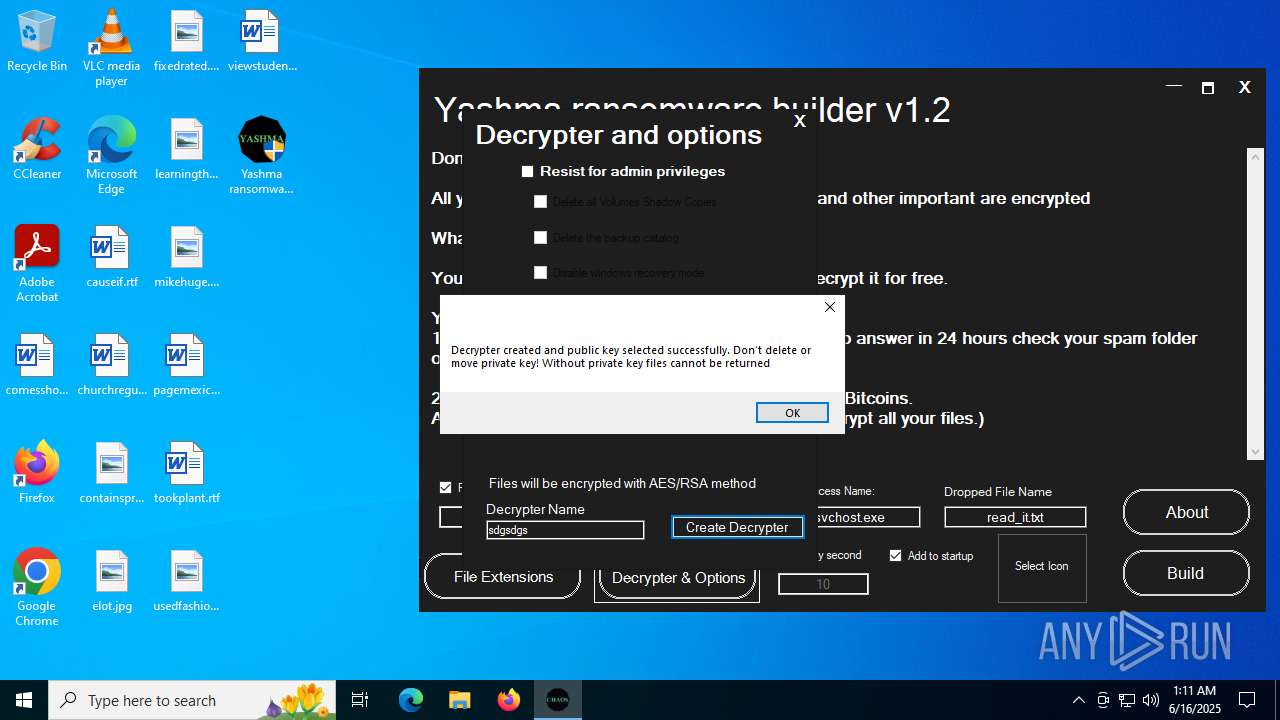
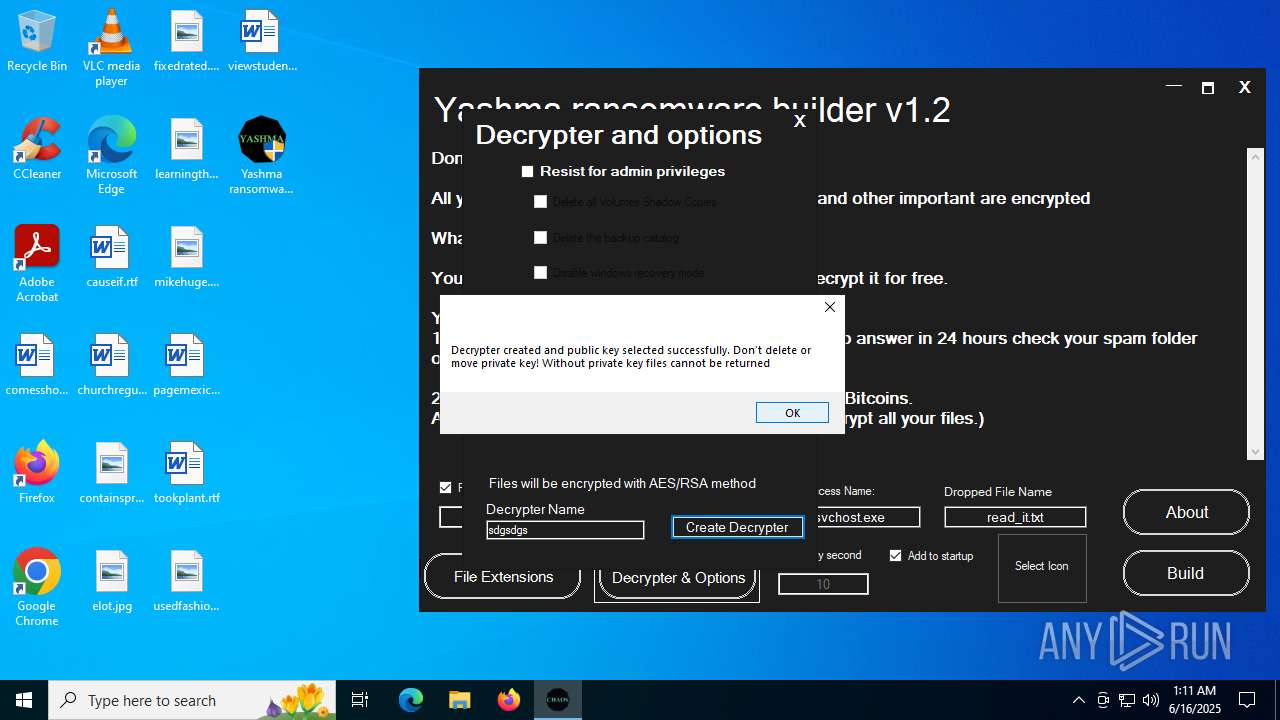
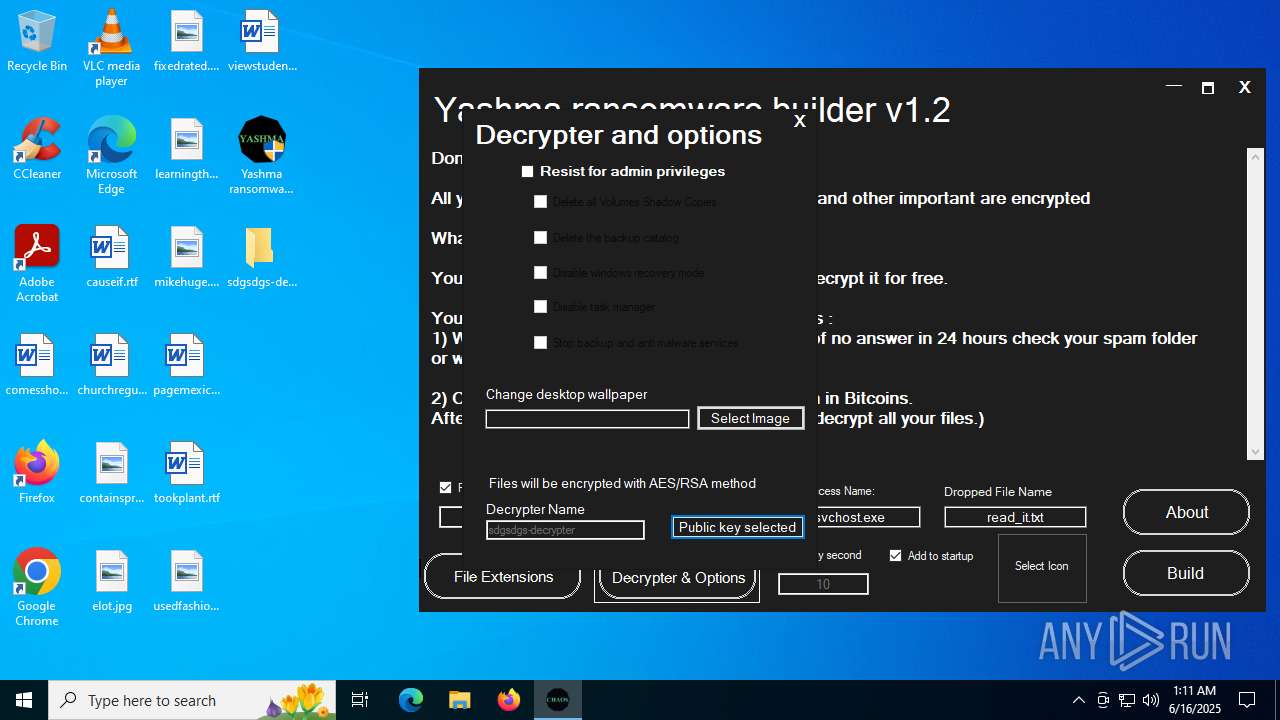
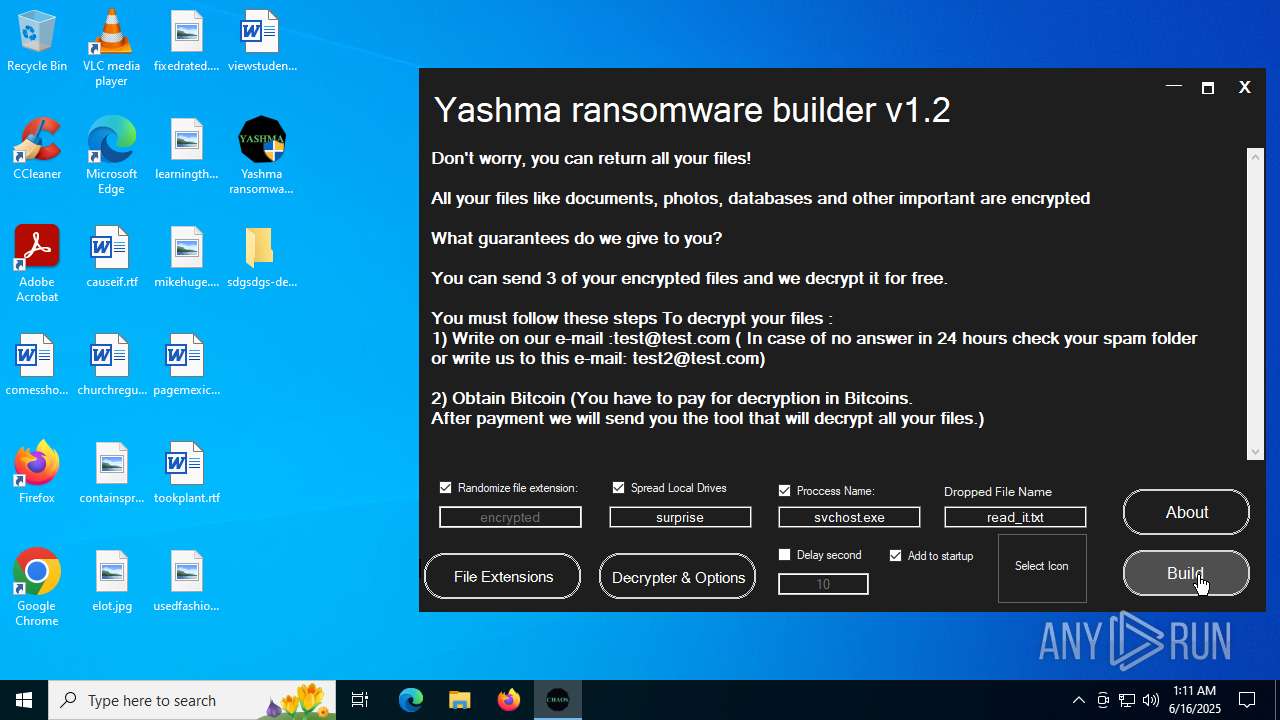
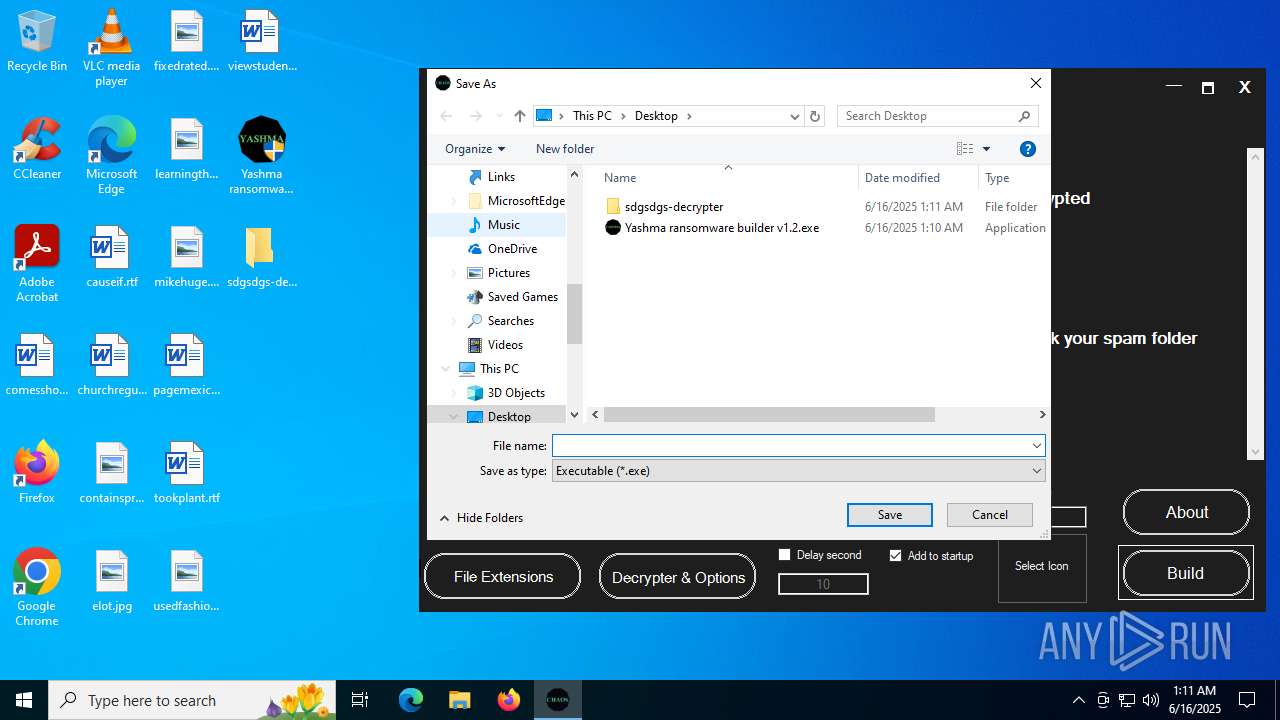
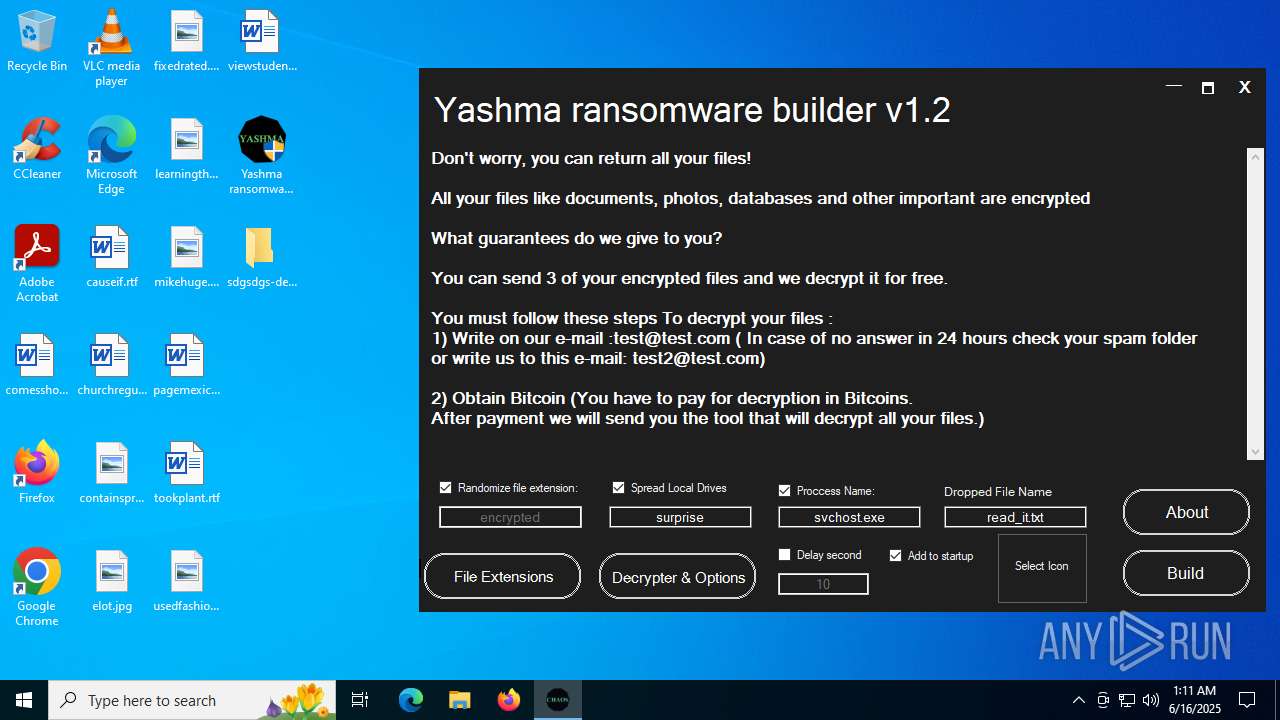
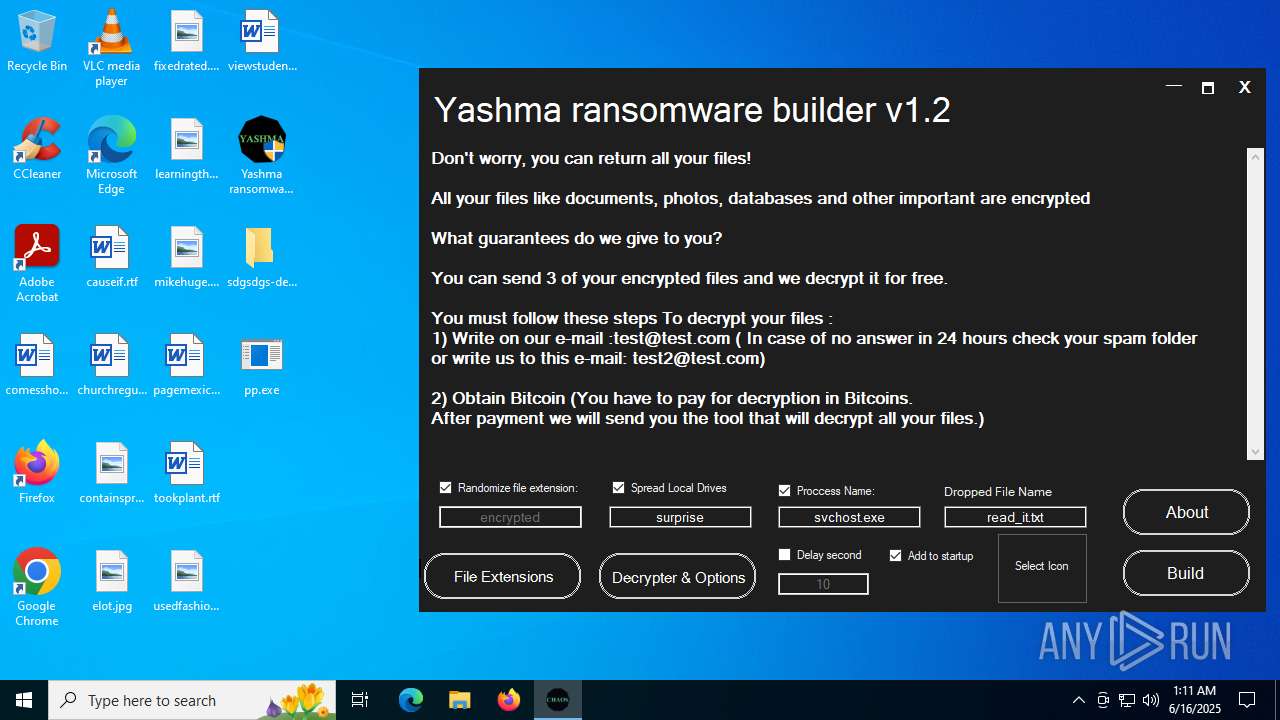
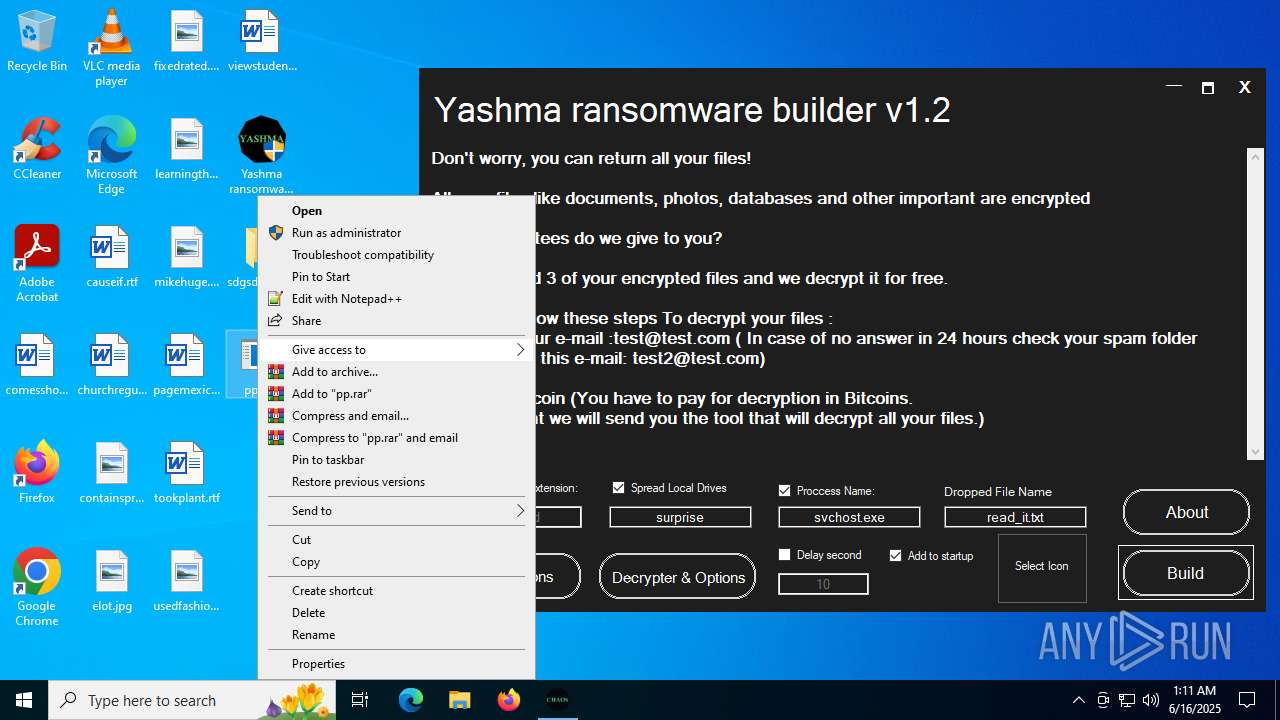
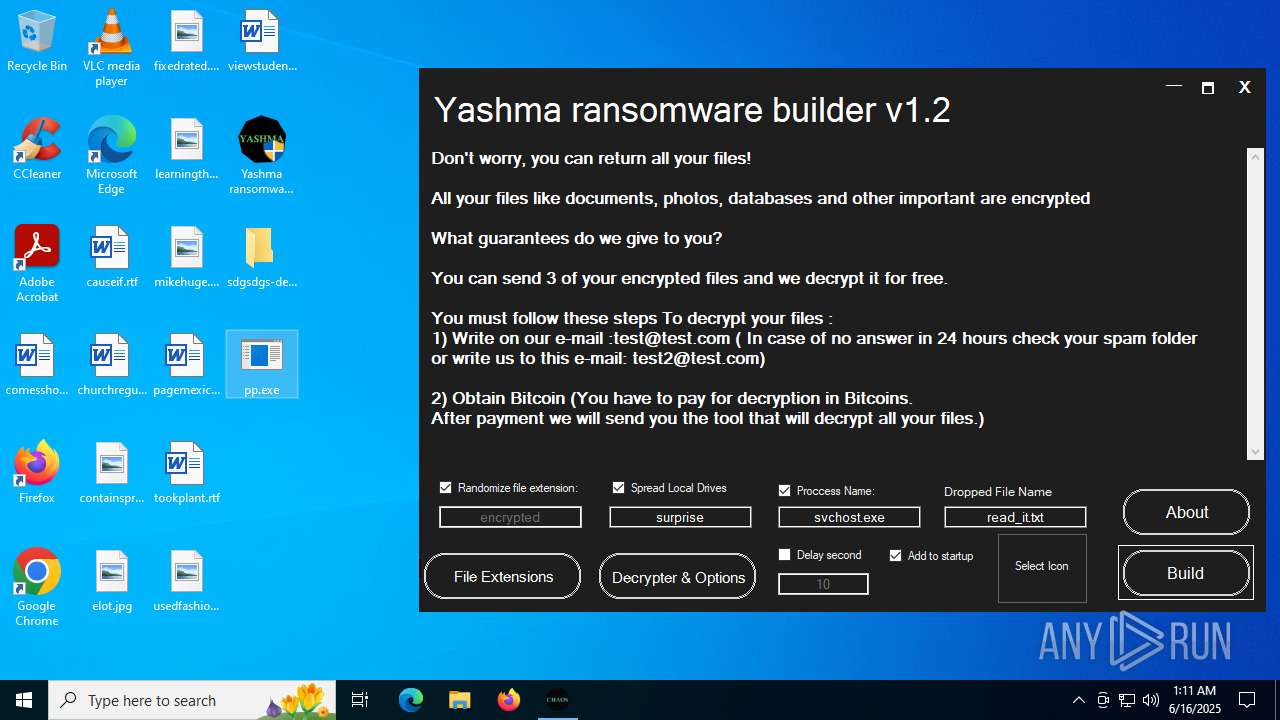
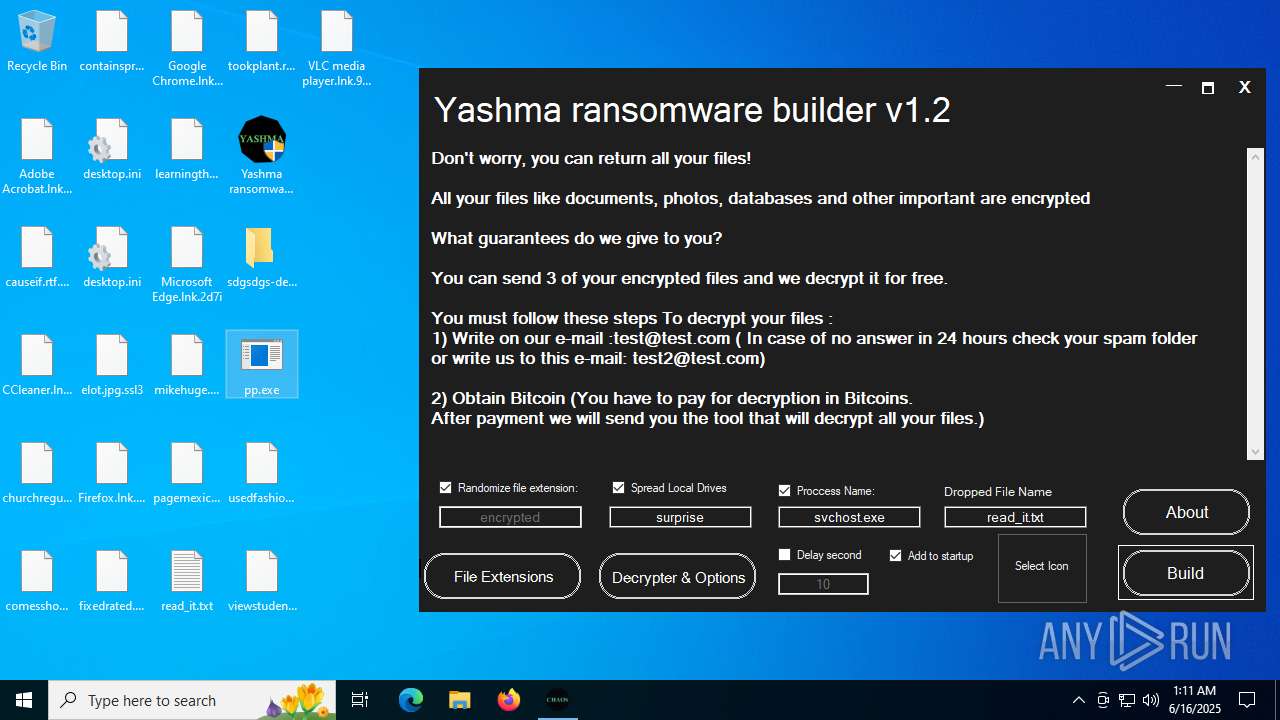
| File name: | Yashma ransomware builder v1.2.exe |
| Full analysis: | https://app.any.run/tasks/b1faf05d-d458-4b9c-bbdf-0bc696934b5e |
| Verdict: | Malicious activity |
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | June 16, 2025, 01:10:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 13E878ED7E547523CFFC5728F6BA4190 |
| SHA1: | 878AD3025F8EA6B61AD4521782035963B3675A52 |
| SHA256: | F9A5A72EAD096594C5D59ABE706E3716F6000C3B4EBD7690F2EB114A37D1A7DB |
| SSDEEP: | 3072:tq0G/vqRT5i2YcRVm16Pn690H7GMgXuD//bFLAkCgkUKEyF9aT5Zt19r+E1/bFLx:U0G/GiWm16YaGMVFLQdD8FLzd |
MALICIOUS
CHAOS has been detected (YARA)
- Yashma ransomware builder v1.2.exe (PID: 6240)
- svchost.exe (PID: 4040)
Changes the autorun value in the registry
- svchost.exe (PID: 4040)
RANSOMWARE has been detected
- svchost.exe (PID: 4040)
Modifies files in the Chrome extension folder
- svchost.exe (PID: 4040)
Create files in the Startup directory
- svchost.exe (PID: 4040)
SUSPICIOUS
Found regular expressions for crypto-addresses (YARA)
- Yashma ransomware builder v1.2.exe (PID: 6240)
- svchost.exe (PID: 4040)
Executable content was dropped or overwritten
- Yashma ransomware builder v1.2.exe (PID: 6240)
- csc.exe (PID: 1216)
- pp.exe (PID: 6216)
Reads security settings of Internet Explorer
- Yashma ransomware builder v1.2.exe (PID: 6240)
- pp.exe (PID: 6216)
Reads the date of Windows installation
- pp.exe (PID: 6216)
The process creates files with name similar to system file names
- pp.exe (PID: 6216)
Starts itself from another location
- pp.exe (PID: 6216)
INFO
Reads the machine GUID from the registry
- Yashma ransomware builder v1.2.exe (PID: 6240)
- csc.exe (PID: 1216)
- svchost.exe (PID: 4040)
Reads the computer name
- Yashma ransomware builder v1.2.exe (PID: 6240)
- svchost.exe (PID: 4040)
- pp.exe (PID: 6216)
Checks supported languages
- Yashma ransomware builder v1.2.exe (PID: 6240)
- csc.exe (PID: 1216)
- cvtres.exe (PID: 3608)
- svchost.exe (PID: 4040)
- pp.exe (PID: 6216)
Create files in a temporary directory
- Yashma ransomware builder v1.2.exe (PID: 6240)
- cvtres.exe (PID: 3608)
- svchost.exe (PID: 4040)
Creates files in the program directory
- svchost.exe (PID: 4040)
Launching a file from a Registry key
- svchost.exe (PID: 4040)
Creates files or folders in the user directory
- svchost.exe (PID: 4040)
- pp.exe (PID: 6216)
Manual execution by a user
- pp.exe (PID: 6216)
Process checks computer location settings
- pp.exe (PID: 6216)
Launching a file from the Startup directory
- svchost.exe (PID: 4040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:05:07 06:45:02+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 440320 |
| InitializedDataSize: | 110080 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6d61e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.1 |
| ProductVersionNumber: | 2.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
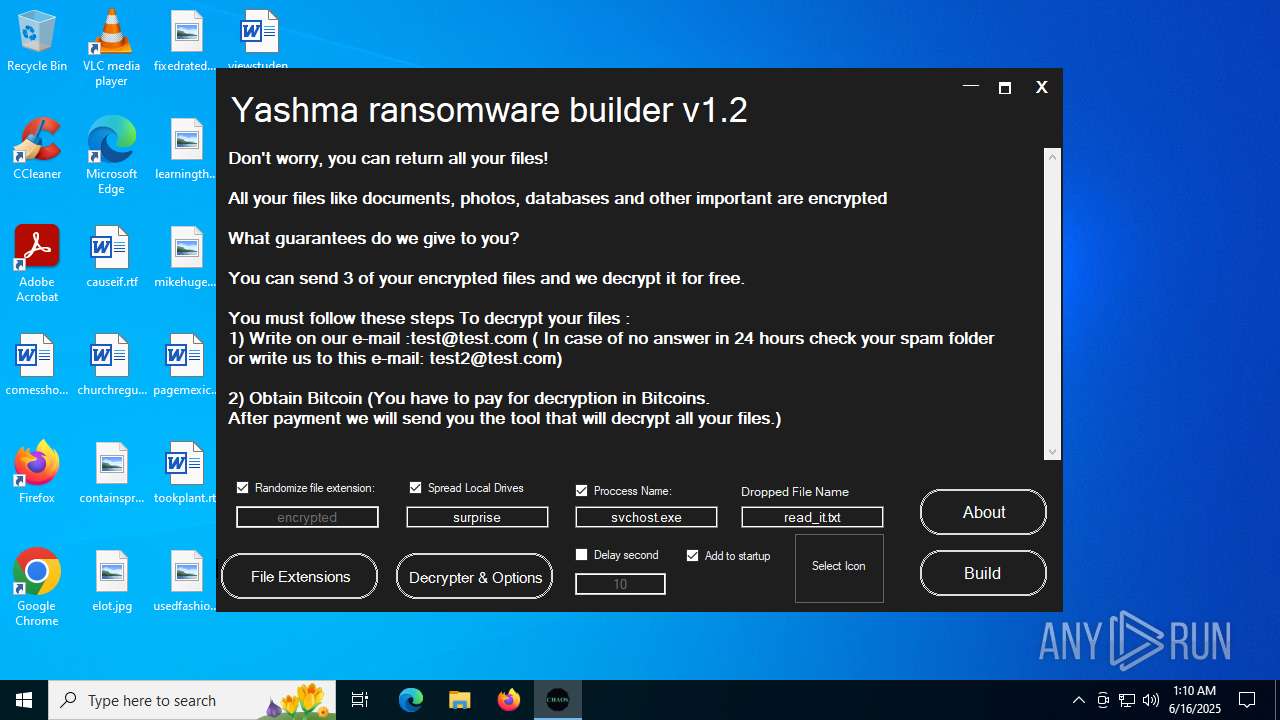
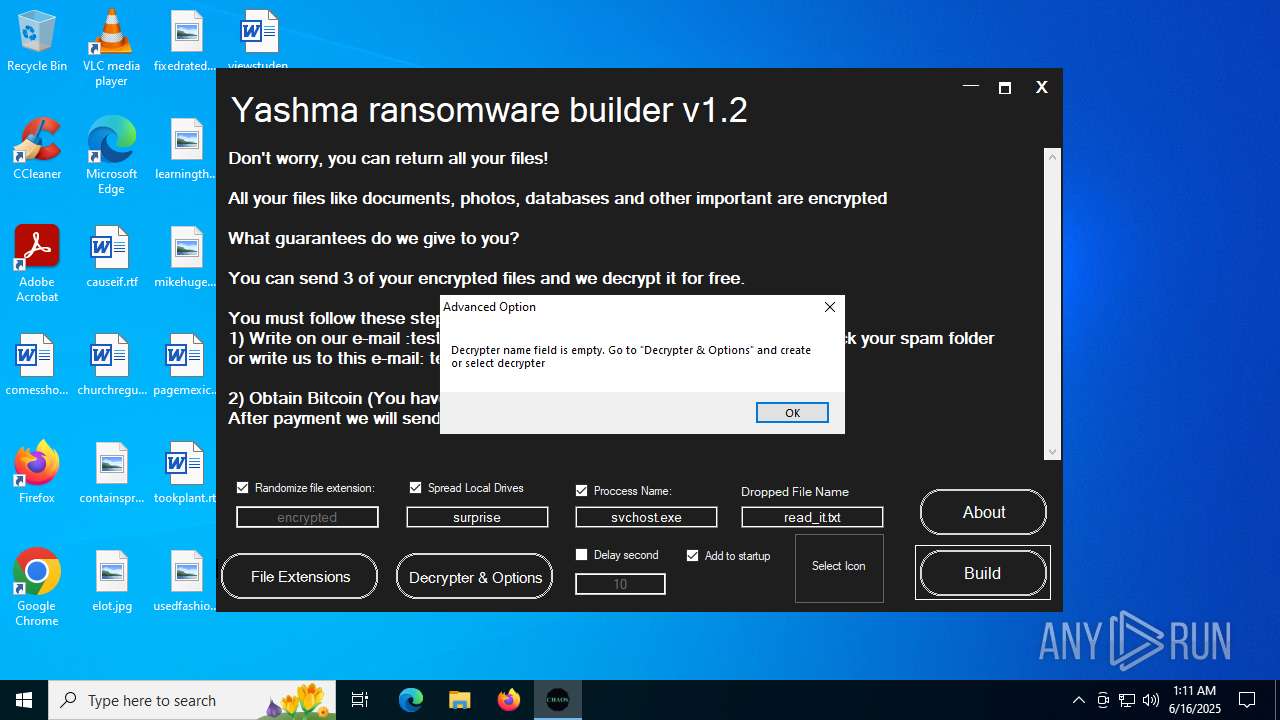
| FileDescription: | Yashma ransomware builder v1.2 |
| FileVersion: | 2.0.0.1 |
| InternalName: | Yashma ransomware builder v1.2.exe |
| LegalCopyright: | Copyright © 2022 |
| OriginalFileName: | Yashma ransomware builder v1.2.exe |
| ProductName: | Yashma ransomware builder v1.2 |
| ProductVersion: | 2.0.0.1 |
| AssemblyVersion: | 2.0.0.1 |
Total processes
144
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1216 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\niextr5v\niextr5v.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | Yashma ransomware builder v1.2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\Desktop\Yashma ransomware builder v1.2.exe" | C:\Users\admin\Desktop\Yashma ransomware builder v1.2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Yashma ransomware builder v1.2 Exit code: 3221226540 Version: 2.0.0.1 Modules
| |||||||||||||||
| 3608 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES182.tmp" "c:\Users\admin\Desktop\CSCE51125A152C846AEA3F9AC187C6DB2C4.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 3980 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | pp.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 5716 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6216 | "C:\Users\admin\Desktop\pp.exe" | C:\Users\admin\Desktop\pp.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 1 Version: 0.0.0.0 Modules
| |||||||||||||||
| 6240 | "C:\Users\admin\Desktop\Yashma ransomware builder v1.2.exe" | C:\Users\admin\Desktop\Yashma ransomware builder v1.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Yashma ransomware builder v1.2 Version: 2.0.0.1 Modules
| |||||||||||||||
Total events
5 498
Read events
5 458
Write events
39
Delete events
1
Modification events
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\oAnWieozQPsRK7Bj83r4 |
| Operation: | write | Name: | oAnWieozQPsRK7Bj83r4 |
Value: oAnWieozQPsRK7Bj83r4 | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000003000000110000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000003000000050000000400000002000000FFFFFFFF | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Modules\NavPane |
| Operation: | write | Name: | ExpandedState |
Value: 15000000160014001F80CB859F6720028040B29B5540CC05AAB60000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F60983FFBB4EAC18D42A78AD1F5659CBA930000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F7840F05F6481501B109F0800AA002F954E0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F706806EE260AA0D7449371BEB064C986830000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F580D1A2CF021BE504388B07367FC96EF3C0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F5425481E03947BC34DB131E946B44C8DD50000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F50E04FD020EA3A6910A2D808002B30309D0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000003C003A001F44471A0359723FA74489C55595FE6B30EE260001002600EFBE1000000034E9025AA9B7D80155EC262BAAB7D8018F3827B5B0B7D80114000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000003C003A001F42665C8D01334507439B53224DE2ED1FE6260001002600EFBE11000000A1C1E0E0AF27D301F77F6305B0B7D8019F22F307B0B7D80114000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000940092003200000080004658D1892000474F4F474C457E312E5A49500000760009000400EFBE4658D1894658D1892E000000F55D05000000090000000000000000000000000000001F47700047006F006F0067006C0065004300680072006F006D00650045006E0074006500720070007200690073006500420075006E0064006C006500360034002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000005C005A00320099030000F2588C582000657874312E7A69700000420009000400EFBEF2588C58F2588C582E000000A70D00000000160000000000000000000000000000003A91F90065007800740031002E007A0069007000000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000050004E00310000000000F258CE5810006578743100003A0009000400EFBEF258CE58F258CE582E000000DE0200000000170000000000000000000000000000001CB7E9006500780074003100000014000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000006E006C0032001EEC0500F258826620005052454645527E312E5A49500000500009000400EFBEF2588266F25882662E00000028D4000000001900000000000000000000000000000005A1250050007200650066006500720065006E006300650073002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000005800560032007E0D0000F258866620006578742E7A697000400009000400EFBEF2588666F25886662E0000002AD4000000001E0000000000000000000000000000005498DF006500780074002E007A0069007000000016000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000062006000310000000000F2588D6610005052454645527E310000480009000400EFBEF2588D66F2588F662E0000002E2F0100000017000000000000000000000000000000CF57130150007200650066006500720065006E00630065007300000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000004C004A00310000000000F2589066100065787400380009000400EFBEF2589066F25890662E000000E88D0100000007000000000000000000000000000000DE8B4100650078007400000012000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000780076003200C1862C03F258957920004F4D4E495F327E312E5A495000005A0009000400EFBEF258E578F25895792E0000007C600500000039000000000000000000000000000000DE6FED006F006D006E0069005F00320033005F00310030005F0032003000320034005F002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000070006E0032007E0D0000F2587B7920004348524F4D497E312E5A49500000520009000400EFBEF2587B79F2587B792E000000C260050000001800000000000000000000000000000028F586006300680072006F006D00690075006D005F006500780074002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000620060003100000000006B5A8B31100046495245464F7E310000480009000400EFBE6B5AD2346B5AD3342E0000006A27000000001100000000000000000000000000000000000000660069007200650066006F0078005F00650078007400000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000006C006A0032005EEA00006B5A30352000414E5952554E7E312E5A495000004E0009000400EFBE6B5A30356B5A30352E0000005927000000001600000000000000000000000000000055464B0061006E007900720075006E005F006500780074002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000006E006C00310000000000D05A6F0910005344475344477E310000540009000400EFBED05A6F09D05A6F092E000000C53400000000110000000000000000000000000000000F46550073006400670073006400670073002D00640065006300720079007000740065007200000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000 | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | 2 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C641540032000000000000000000800070702E65786500003E0009000400EFBE00000000000000002E0000000000000000000000000000000000000000000000000000000000700070002E00650078006500000016000000 | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | 9 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C641540032000000000000000000800070702E65786500003E0009000400EFBE00000000000000002E0000000000000000000000000000000000000000000000000000000000700070002E00650078006500000016000000 | |||
| (PID) Process: | (6240) Yashma ransomware builder v1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 09000000070000000800000006000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
Executable files
3
Suspicious files
288
Text files
752
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3608 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES182.tmp | binary | |
MD5:2C326C2F2B364DE5FBCF2E17ABC0576E | SHA256:5BB9A38E11135E1E74D2ABF5E19EDC31C5300BEFDDB4CD7B11BD0E94F90685C7 | |||
| 6240 | Yashma ransomware builder v1.2.exe | C:\Users\admin\Desktop\sdgsdgs-decrypter\privateKey.yashma | xml | |
MD5:8E7FB982FF9723641C1DE644FFBDD60B | SHA256:07EEEE7DF88F2B5C21DDFF1D10E67963191A79C324D7D74BB0FBE9E34FAA8889 | |||
| 6216 | pp.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:7F05C1254624889510788F8E2568AF2E | SHA256:B974D59CB4A4D96DB84CED0418666CA5097B72518314E01921D98566399DF68E | |||
| 6240 | Yashma ransomware builder v1.2.exe | C:\Users\admin\AppData\Local\Temp\niextr5v\niextr5v.0.cs | text | |
MD5:8CCFDE4005C9E6D0F454DF56C53C3DDD | SHA256:860439D091FFEB72FB6D701309E73D7D77AB220685B36CA5CAA0F2C3EE4C4860 | |||
| 6240 | Yashma ransomware builder v1.2.exe | C:\Users\admin\Desktop\sdgsdgs-decrypter\Decrypter.exe | executable | |
MD5:F30CE6004E05994FFD89124C5F0290DF | SHA256:00A48C79F453FA1B13C3F37FEAE3711C7EC35FD82B7BDE2432D8C56CCDAF544D | |||
| 1216 | csc.exe | C:\Users\admin\AppData\Local\Temp\niextr5v\niextr5v.out | text | |
MD5:986053EDE4460591EC64AC76C236BF65 | SHA256:C9A709FD8A87EF1849AC15938748D44CFA6B496593CD919AAB36659043F53874 | |||
| 6240 | Yashma ransomware builder v1.2.exe | C:\Users\admin\AppData\Local\Temp\niextr5v\niextr5v.cmdline | text | |
MD5:8B1E1D8853C3620D0BD904074A400841 | SHA256:76A8E485FC08696B343BF90E6A41BE5EEE12EF62E006C36D2E85FD7C57525D0F | |||
| 1216 | csc.exe | C:\Users\admin\Desktop\CSCE51125A152C846AEA3F9AC187C6DB2C4.TMP | binary | |
MD5:762AD75837C06C889C500F049CA97C6E | SHA256:2C09F2DA313FE83F276BD0EF76D97CF0A8EB5510401E185359CD8511CE3F5F86 | |||
| 1216 | csc.exe | C:\Users\admin\Desktop\pp.exe | executable | |
MD5:7F05C1254624889510788F8E2568AF2E | SHA256:B974D59CB4A4D96DB84CED0418666CA5097B72518314E01921D98566399DF68E | |||
| 4040 | svchost.exe | C:\$WinREAgent\RollbackInfo.ini.3osl | binary | |
MD5:D5BAC7A49B31FAE90FB8BB07425C6140 | SHA256:1E12358E30CB28C63F7FB3758D7319EC46CD02AFA9017146EE8FAE0B45803E1B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1948 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1948 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3936 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3956 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1948 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |