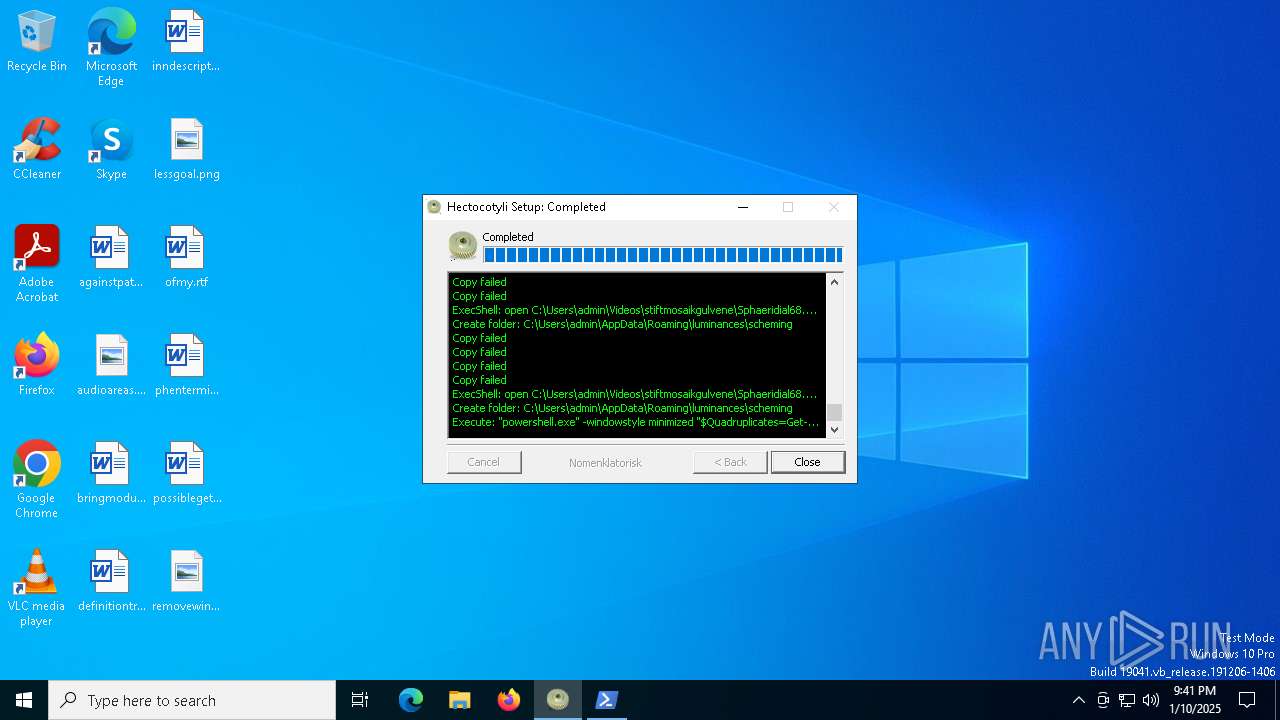
| File name: | f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f |
| Full analysis: | https://app.any.run/tasks/8608a61c-77fc-446d-b005-c1b9ce761b35 |
| Verdict: | Malicious activity |
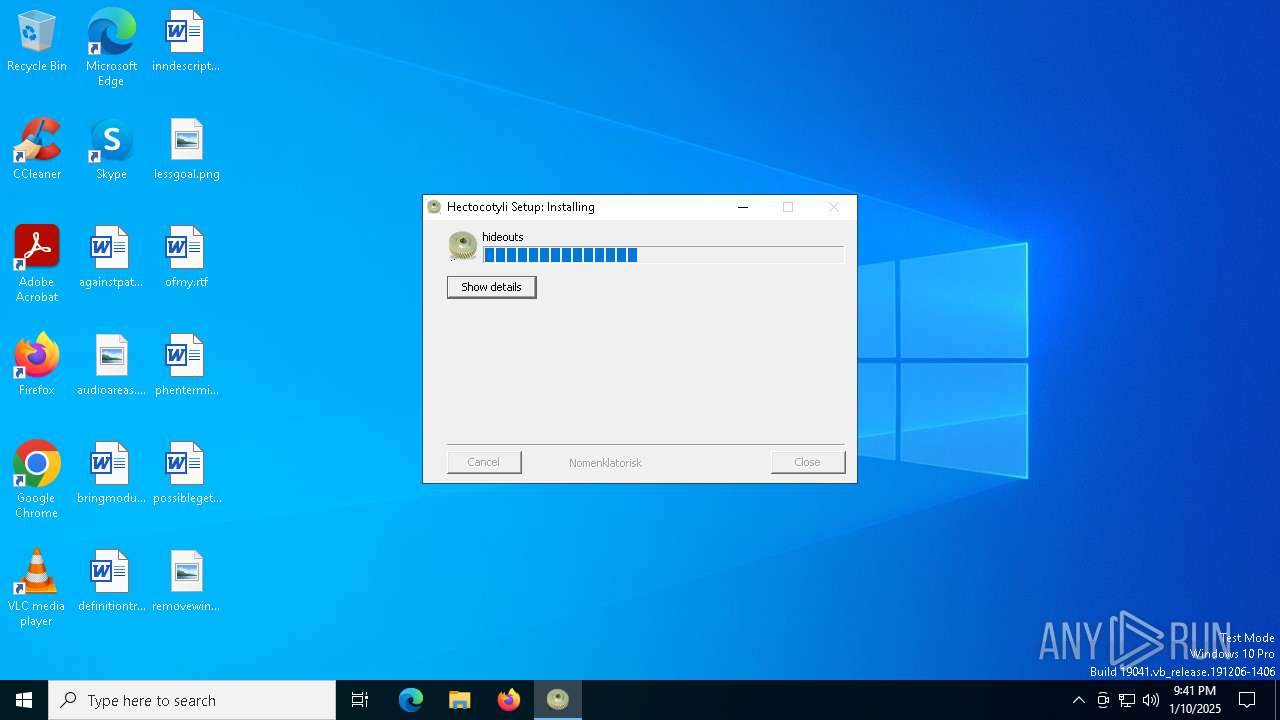
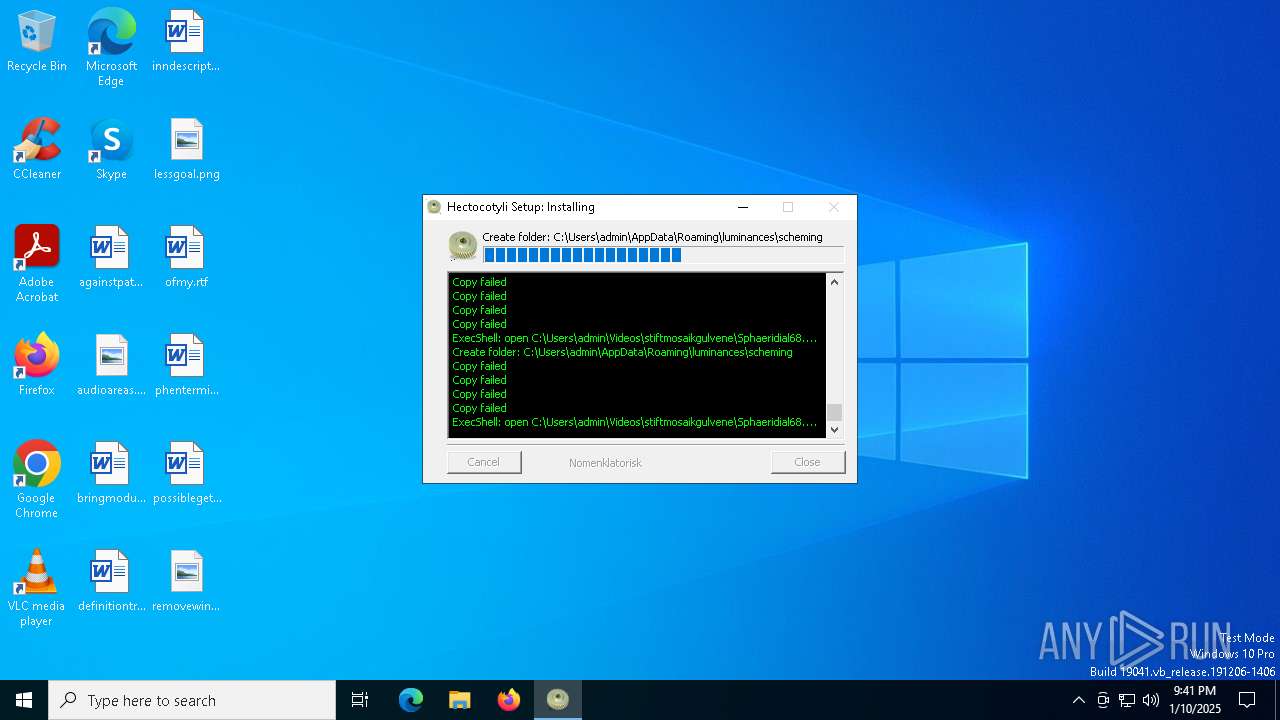
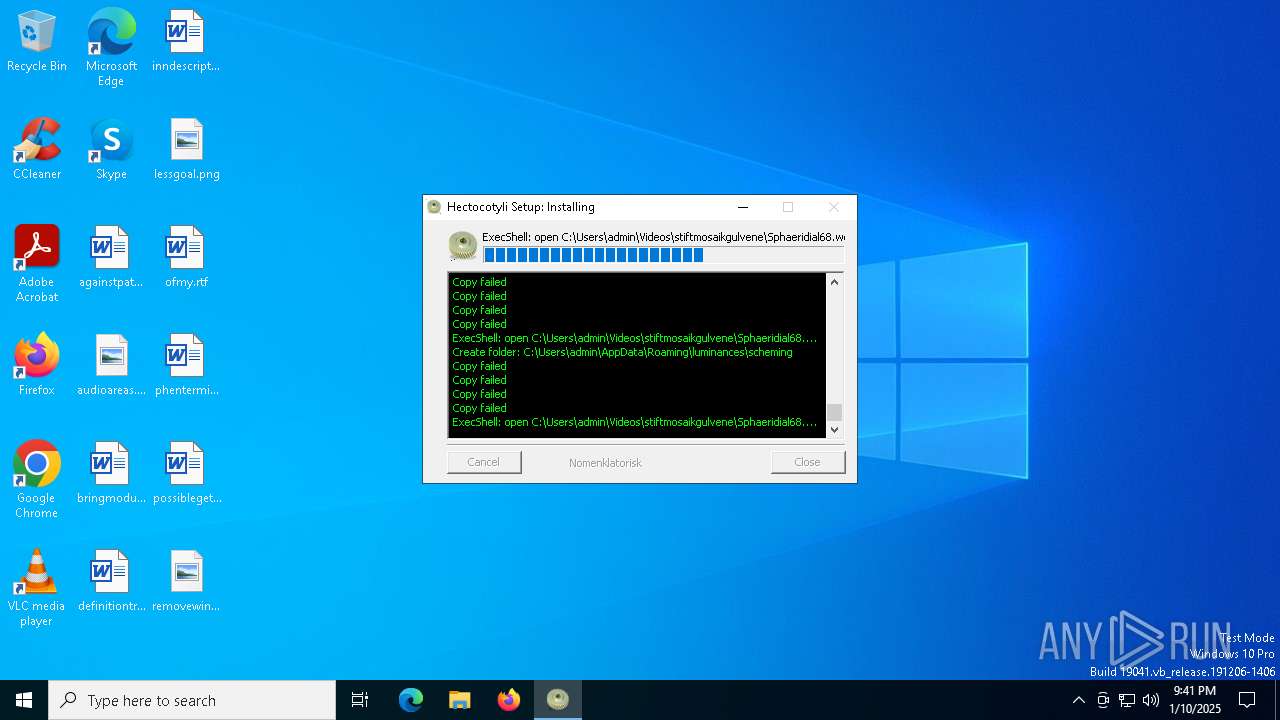
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | January 10, 2025, 21:41:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | C642619AD2A1AC39867C56CB2F889E78 |
| SHA1: | A15C485E5DBACDB5776E2CEC6C3A1AF3C4A400D2 |
| SHA256: | F973B482345D4FF8AC164868B9F50CE95E47ED2648B57C400AB59F04457C9A4F |
| SSDEEP: | 49152:t91NaX3dIhFR9D166ePZAS6kdJGTDEQqi6bI2sODFRr9ZQRDgQS6ZjwlxdD/g2CJ:tb8X3mhFTZV8ZASPDQqDcYJMR0QSOjwY |
MALICIOUS
GULOADER has been detected
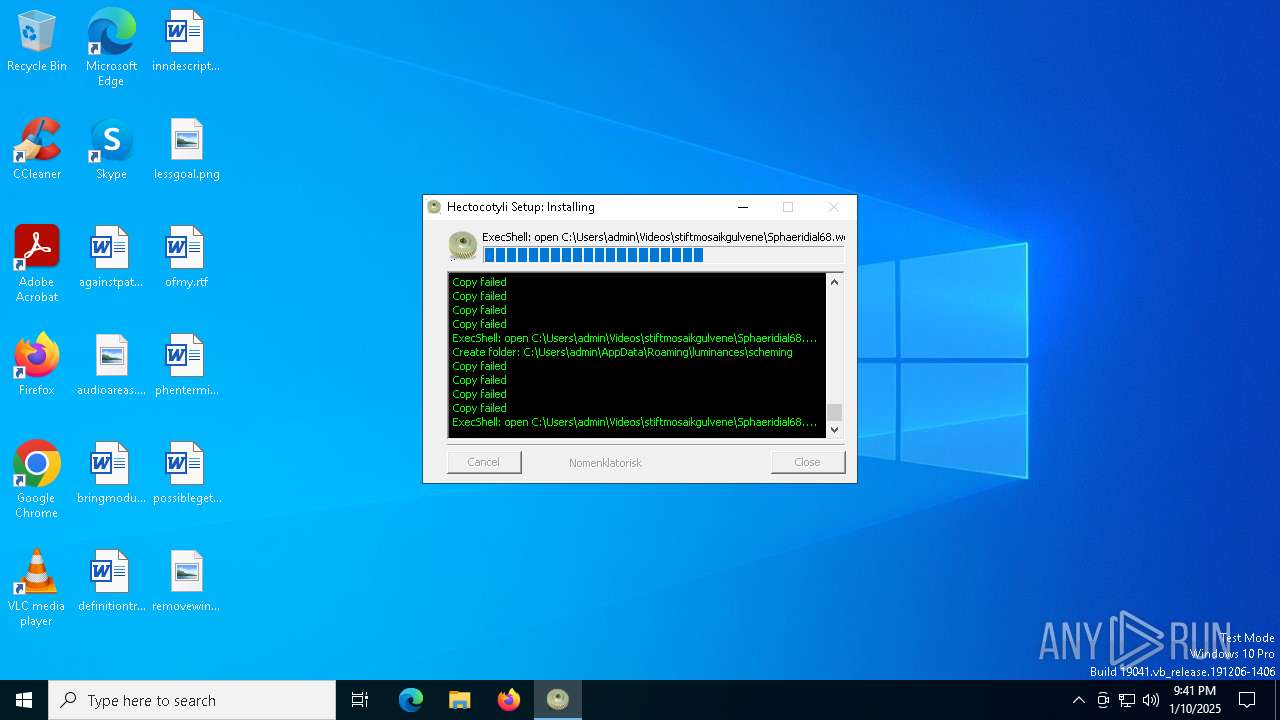
- f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe (PID: 556)
SUSPICIOUS
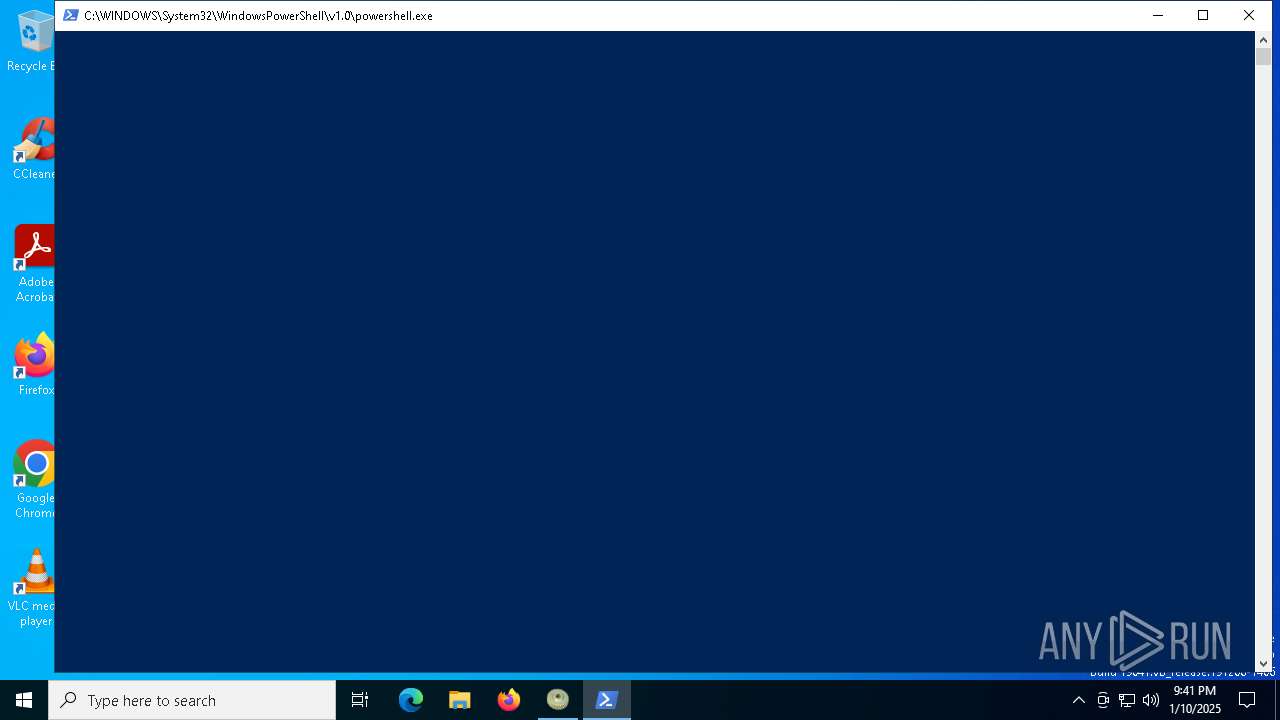
Starts POWERSHELL.EXE for commands execution
- f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe (PID: 556)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3188)
Checks supported languages
- f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe (PID: 556)
Reads the computer name
- f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe (PID: 556)
The sample compiled with english language support
- f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe (PID: 556)
The process uses the downloaded file
- powershell.exe (PID: 3188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:24:27+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25600 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3359 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.1.0.0 |
| ProductVersionNumber: | 3.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | dusren barcarole sulcalize |
| CompanyName: | alarmsystems |
| FileDescription: | udstykningsplan uidentificerbares vrdipapircentralerne |
| FileVersion: | 3.1.0.0 |
| LegalCopyright: | dulcigenic asterix |
| LegalTrademarks: | civilisationer markild goalless |
| ProductName: | bristly sublustrously frgende |
Total processes
129
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | "C:\Users\admin\AppData\Local\Temp\f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe" | C:\Users\admin\AppData\Local\Temp\f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe | explorer.exe | ||||||||||||
User: admin Company: alarmsystems Integrity Level: MEDIUM Description: udstykningsplan uidentificerbares vrdipapircentralerne Exit code: 0 Version: 3.1.0.0 Modules
| |||||||||||||||
| 3188 | "powershell.exe" -windowstyle minimized "$Quadruplicates=Get-Content -Raw 'C:\Users\admin\AppData\Local\Temp\depersonaliseredes\Opjustering\ubekrftede.Amo';$syndactylus=$Quadruplicates.SubString(8202,3);.$syndactylus($Quadruplicates)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 381
Read events
7 378
Write events
3
Delete events
0
Modification events
| (PID) Process: | (556) f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe | Key: | HKEY_CURRENT_USER\skurestriber\Absee |
| Operation: | write | Name: | grandevous |
Value: %islandhood%\oveni\restaureredes.con | |||
Executable files
0
Suspicious files
6
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 556 | f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe | C:\Users\admin\AppData\Local\Temp\depersonaliseredes\Wadder.Uns | binary | |
MD5:FCF8B2C76841993BF7C2177DD2C95355 | SHA256:C048A296F897683FD8DE87F573E56C4480865DB3E7D0F52E3A49CA558BFD07D3 | |||
| 3188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gtertszl.vj4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 556 | f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe | C:\Users\admin\AppData\Local\Temp\depersonaliseredes\Opjustering\ubekrftede.Amo | text | |
MD5:209C7B647C3E79CED487D0AD4EB5FA7A | SHA256:25DE529A818ED3E2C5609D0C210F2D259385591B27AA5DF9D42E5D1AABB3381B | |||
| 556 | f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe | C:\Users\admin\AppData\Local\Temp\depersonaliseredes\Opjustering\gerties\Fleece.kar | binary | |
MD5:8A6A8A75FE9A08909B09C7242C1B0C73 | SHA256:1AAD58A3F50A3EF4E50AFCECBAF81D840F4E3F0C512BCC5844A1AEC594A06FF7 | |||
| 3188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dznhq21s.5db.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_eymgz2z3.gaw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0liyyce4.qfa.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3188 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:5F62DFB53E47D6CD6715ABE772A855F8 | SHA256:C327736DF96A1BC7AC8A64CFC9935A7665EE601ACCC469BAB24E3822FA7AEFC0 | |||
| 556 | f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe | C:\Users\admin\AppData\Local\Temp\depersonaliseredes\udsds.aut | binary | |
MD5:152C1126D35B77FC957526436ADBEA38 | SHA256:67780594962B62DD23C55340C9AB1CD11858C15F464E8EE312A690A1759EAFD3 | |||
| 556 | f973b482345d4ff8ac164868b9f50ce95e47ed2648b57c400ab59f04457c9a4f.exe | C:\Users\admin\AppData\Local\Temp\depersonaliseredes\Opjustering\gerties\Ceylonteer.kae | binary | |
MD5:03ADD5EC69F2D821F4BDDF502603364B | SHA256:A8850B76F116EB91305228F5F39B2B6152927531705DE707A60FC74B86DF4003 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6400 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6400 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1668 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5156 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |