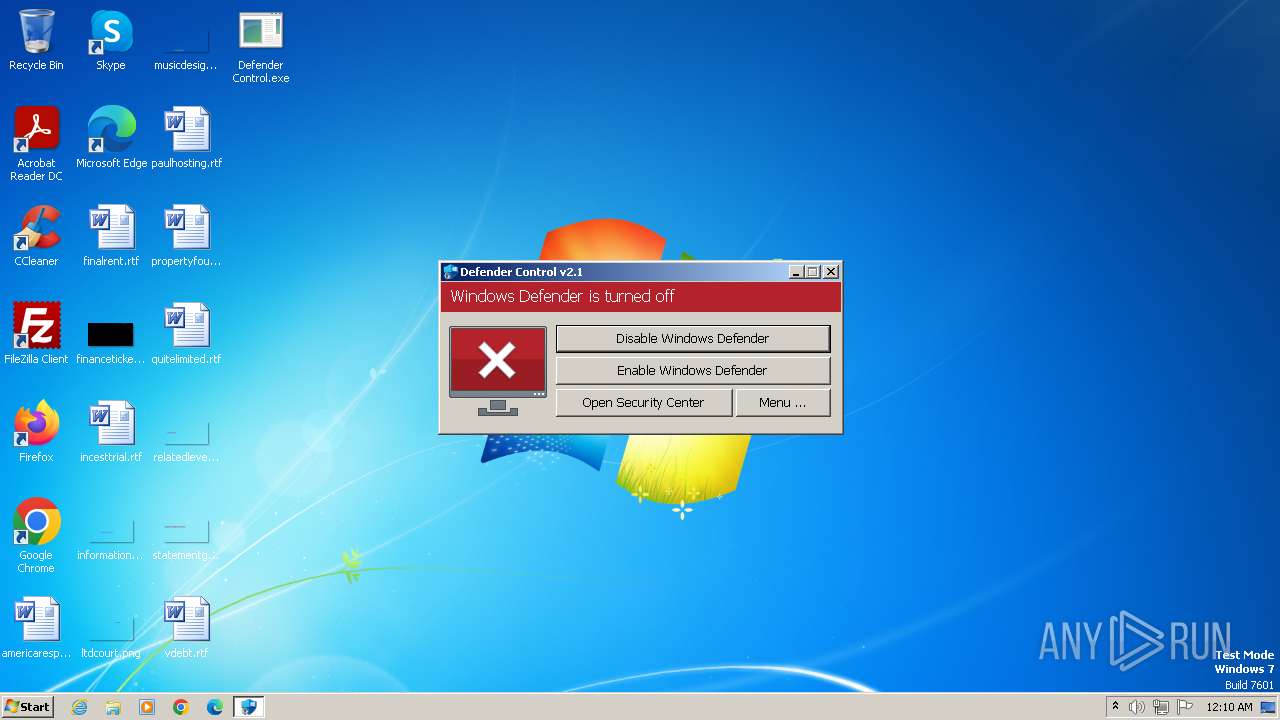
| File name: | Defender Control.exe |
| Full analysis: | https://app.any.run/tasks/dd31c2a3-4c64-4ba2-a552-ebd941c8f69a |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 17, 2024, 00:07:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9F6C34EF2775B528772CE4AF517EE292 |
| SHA1: | 0E18276BADAD6CD1AD56C168E55273850AA21BE2 |
| SHA256: | F9702EE002E8BB5857D7B3555022A68F5303547677B5F4A0A75BA744939C28F2 |
| SSDEEP: | 49152:54yJX3DOZDNghYjRjlpaDw11SjsHb+msjca3ZiPNcr0P/+kveK3BYGTI30xdpjfO:5TFuzxwprLeiZbyKOqkWX8tik |
MALICIOUS
Drops the executable file immediately after the start
- Defender Control.exe (PID: 2472)
- csc.exe (PID: 1496)
- Orcus.exe (PID: 3068)
- dlhost.exe (PID: 4044)
- svchost.exe (PID: 2624)
- dllhost.exe (PID: 3460)
Orcus is detected
- dlhost.exe (PID: 4044)
- Orcus.exe (PID: 3068)
- Orcus.exe (PID: 3068)
- Orcus.exe (PID: 2744)
- OrcusWatchdog.exe (PID: 1308)
Starts Visual C# compiler
- dlhost.exe (PID: 4044)
Changes the autorun value in the registry
- Orcus.exe (PID: 3068)
- dllhost.exe (PID: 3460)
- svchost.exe (PID: 2624)
NjRAT is detected
- svchost.exe (PID: 2624)
Create files in the Startup directory
- svchost.exe (PID: 2624)
NJRAT has been detected (YARA)
- svchost.exe (PID: 2624)
ASYNCRAT has been detected (YARA)
- svhost.exe (PID: 2632)
ORCUS has been detected (YARA)
- Orcus.exe (PID: 3068)
SUSPICIOUS
Reads the Internet Settings
- Defender Control.exe (PID: 2472)
- Orcus.exe (PID: 3068)
- dlhost.exe (PID: 4044)
- OrcusWatchdog.exe (PID: 1308)
The process creates files with name similar to system file names
- Defender Control.exe (PID: 2472)
- dllhost.exe (PID: 3460)
Reads security settings of Internet Explorer
- Defender Control.exe (PID: 2472)
- dlhost.exe (PID: 4044)
- OrcusWatchdog.exe (PID: 1308)
- Orcus.exe (PID: 3068)
Reads the date of Windows installation
- Defender Control.exe (PID: 2472)
Executable content was dropped or overwritten
- Defender Control.exe (PID: 2472)
- csc.exe (PID: 1496)
- Orcus.exe (PID: 3068)
- dlhost.exe (PID: 4044)
- svchost.exe (PID: 2624)
- dllhost.exe (PID: 3460)
Application launched itself
- dControl.exe (PID: 2840)
- dControl.exe (PID: 3464)
- OrcusWatchdog.exe (PID: 1308)
Uses .NET C# to load dll
- dlhost.exe (PID: 4044)
The process executes via Task Scheduler
- Orcus.exe (PID: 2744)
Starts itself from another location
- dlhost.exe (PID: 4044)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3980)
Uses NETSH.EXE to add a firewall rule or allowed programs
- svchost.exe (PID: 2624)
Executing commands from a ".bat" file
- dllhost.exe (PID: 3460)
Starts CMD.EXE for commands execution
- dllhost.exe (PID: 3460)
The executable file from the user directory is run by the CMD process
- svhost.exe (PID: 2632)
Uses TASKKILL.EXE to kill process
- svchost.exe (PID: 2624)
Connects to unusual port
- svchost.exe (PID: 2624)
- svhost.exe (PID: 2632)
INFO
Create files in a temporary directory
- Defender Control.exe (PID: 2472)
- dControl.exe (PID: 2840)
- dControl.exe (PID: 3992)
- dlhost.exe (PID: 4044)
- csc.exe (PID: 1496)
- cvtres.exe (PID: 3164)
- Orcus.exe (PID: 3068)
- dllhost.exe (PID: 3460)
Reads the computer name
- Defender Control.exe (PID: 2472)
- dControl.exe (PID: 2840)
- dControl.exe (PID: 3464)
- dllhost.exe (PID: 3460)
- dControl.exe (PID: 3992)
- dlhost.exe (PID: 4044)
- Orcus.exe (PID: 3068)
- Orcus.exe (PID: 2744)
- OrcusWatchdog.exe (PID: 1308)
- OrcusWatchdog.exe (PID: 2484)
- svhost.exe (PID: 2632)
- svchost.exe (PID: 2624)
Reads the machine GUID from the registry
- Defender Control.exe (PID: 2472)
- dlhost.exe (PID: 4044)
- dllhost.exe (PID: 3460)
- csc.exe (PID: 1496)
- cvtres.exe (PID: 3164)
- Orcus.exe (PID: 3068)
- Orcus.exe (PID: 2744)
- OrcusWatchdog.exe (PID: 1308)
- OrcusWatchdog.exe (PID: 2484)
- svhost.exe (PID: 2632)
- svchost.exe (PID: 2624)
Reads mouse settings
- dControl.exe (PID: 3464)
- dControl.exe (PID: 2840)
- dControl.exe (PID: 3992)
Checks supported languages
- Defender Control.exe (PID: 2472)
- dllhost.exe (PID: 3460)
- dControl.exe (PID: 3464)
- svchost.exe (PID: 2624)
- dControl.exe (PID: 3992)
- dlhost.exe (PID: 4044)
- csc.exe (PID: 1496)
- cvtres.exe (PID: 3164)
- Orcus.exe (PID: 3068)
- OrcusWatchdog.exe (PID: 2484)
- OrcusWatchdog.exe (PID: 1308)
- Orcus.exe (PID: 2744)
- svhost.exe (PID: 2632)
- dControl.exe (PID: 2840)
Creates files in the program directory
- dlhost.exe (PID: 4044)
Creates files or folders in the user directory
- dlhost.exe (PID: 4044)
- svchost.exe (PID: 2624)
Reads Environment values
- svchost.exe (PID: 2624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(2624) svchost.exe
C2physical-several.at.ply.gg
Ports51206
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\10e16ea1fd352d48d0c7f69840d59b0c
Splitter|'|'|
Versionim523
AsyncRat
(PID) Process(2632) svhost.exe
C2 (1)social-mod.gl.at.ply.gg
Ports (1)40537
BotnetDefault
Version1.0.7
Options
AutoRuntrue
MutexDcRatMutex_qwqdanchun
InstallFolder%Temp%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICMDCCAZmgAwIBAgIVANoU6b07slJvyzssq7+iH/K8iUpBMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIwMTIxNTEwMDUyOFoXDTMxMDkyNDEwMDUyOFowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignatureLcG3OA4RoAxG0Q3iYJrRZz//TAd63CRm2xLVGCOw9vXjchpYRFr3pPuhzJD93DwpiPAu26+TYX82mi0Bi2CbppGpGBCDtrvlGPKuRDFLo5+fyF/Ddtjfb9IInZK+k3HSz8JcqGo4JJaRlTTk7GkJEzOjy9yfCxJbF4zAuVpmVjk=
Keys
AES5846c14298adad997effdfb42dec188be92ea336ff61900cccae85a7cf0e5951
SaltDcRatByqwqdanchun
Orcus
(PID) Process(3068) Orcus.exe
C2 (2)127.0.0.1:4444
alternative-residents.gl.at.ply.gg :41086
Keys
AESf730821b49f2770b6d8a93947dfd4e269ecdcb39de188ab9d570810f5668e96a
Salt
Options
AutostartBuilderProperty
AutostartMethodRegistry
TaskSchedulerTaskNameOrcus
TaskHighestPrivilegestrue
RegistryHiddenStarttrue
RegistryKeyNameOrcus
TryAllAutostartMethodsOnFailtrue
ChangeAssemblyInformationBuilderProperty
ChangeAssemblyInformationfalse
AssemblyTitlenull
AssemblyDescriptionnull
AssemblyCompanyNamenull
AssemblyProductNamenull
AssemblyCopyrightnull
AssemblyTrademarksnull
AssemblyProductVersion1.0.0.0
AssemblyFileVersion1.0.0.0
ChangeCreationDateBuilderProperty
IsEnabledfalse
NewCreationDate2024-01-14T09:04:57
ChangeIconBuilderProperty
ChangeIconfalse
IconPathnull
ClientTagBuilderProperty
ClientTagnull
DataFolderBuilderProperty
Path%appdata%\Orcus
DefaultPrivilegesBuilderProperty
RequireAdministratorRightstrue
DisableInstallationPromptBuilderProperty
IsDisabledtrue
FrameworkVersionBuilderProperty
FrameworkVersionNET35
HideFileBuilderProperty
HideFiletrue
InstallationLocationBuilderProperty
Path%programfiles%\Orcus\Orcus.exe
InstallBuilderProperty
Installtrue
KeyloggerBuilderProperty
IsEnabledfalse
MutexBuilderProperty
Mutexc9fed2adfe5c487bb1b27e0925228432
ProxyBuilderProperty
ProxyOptionNone
ProxyAddressnull
ProxyPort1080
ProxyType2
ReconnectDelayProperty
Delay10000
RequireAdministratorPrivilegesInstallerBuilderProperty
RequireAdministratorPrivilegestrue
RespawnTaskBuilderProperty
IsEnabledtrue
TaskNameOrcus Respawner
ServiceBuilderProperty
Installfalse
SetRunProgramAsAdminFlagBuilderProperty
SetFlagtrue
WatchdogBuilderProperty
IsEnabledtrue
NameOrcusWatchdog.exe
WatchdogLocationTemp
PreventFileDeletiontrue
Plugins
PluginNameBSoD Protection
PluginVersion2.0
ResourceNamebd430dcb7f574f62808db7f46e25f4f7
ResourceTypeClientPlugin
Guiddccbc1db-f7d1-413d-bba4-72611d485d3a
PluginNameDisable Webcam Lights
PluginVersion1.0
ResourceName89779748b0df40e7b3d96b3a96e7f318
ResourceTypeClientPlugin
Guide6ee5674-bb94-46c7-8bbc-5729af6e2c28
PluginNameSilent Elevation
PluginVersion1.5
ResourceName99a4cbe2b6234236bae640728e13cbca
ResourceTypeClientPlugin
Guid0a189c79-87ca-4d8d-bfb5-fac811f4048e
TRiD
| .exe | | | Win64 Executable (generic) (76.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:02:16 22:20:02+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 1.73 |
| CodeSize: | 1803264 |
| InitializedDataSize: | 1536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
69
Monitored processes
20
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1308 | "C:\Users\admin\AppData\Local\Temp\OrcusWatchdog.exe" /launchSelfAndExit "C:\Program Files\Orcus\Orcus.exe" 3068 /protectFile | C:\Users\admin\AppData\Local\Temp\OrcusWatchdog.exe | Orcus.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2484 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1496 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\4uazkdsx.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | dlhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 1540 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Local\Temp\svchost.exe" "svchost.exe" ENABLE | C:\Windows\System32\netsh.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | taskkill /F /IM Avast.exe | C:\Windows\System32\taskkill.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2472 | "C:\Users\admin\Desktop\Defender Control.exe" | C:\Users\admin\Desktop\Defender Control.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2484 | "C:\Users\admin\AppData\Local\Temp\OrcusWatchdog.exe" /watchProcess "C:\Program Files\Orcus\Orcus.exe" 3068 "/protectFile" | C:\Users\admin\AppData\Local\Temp\OrcusWatchdog.exe | — | OrcusWatchdog.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2624 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" | C:\Users\admin\AppData\Local\Temp\svchost.exe | Defender Control.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
NjRat(PID) Process(2624) svchost.exe C2physical-several.at.ply.gg Ports51206 BotnetHacKed Options Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\10e16ea1fd352d48d0c7f69840d59b0c Splitter|'|'| Versionim523 | |||||||||||||||
| 2632 | "C:\Users\admin\AppData\Local\Temp\svhost.exe" | C:\Users\admin\AppData\Local\Temp\svhost.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.7.0 Modules
AsyncRat(PID) Process(2632) svhost.exe C2 (1)social-mod.gl.at.ply.gg Ports (1)40537 BotnetDefault Version1.0.7 Options AutoRuntrue MutexDcRatMutex_qwqdanchun InstallFolder%Temp% BSoDfalse AntiVMfalse Certificates Cert1MIICMDCCAZmgAwIBAgIVANoU6b07slJvyzssq7+iH/K8iUpBMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIwMTIxNTEwMDUyOFoXDTMxMDkyNDEwMDUyOFowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A... Server_SignatureLcG3OA4RoAxG0Q3iYJrRZz//TAd63CRm2xLVGCOw9vXjchpYRFr3pPuhzJD93DwpiPAu26+TYX82mi0Bi2CbppGpGBCDtrvlGPKuRDFLo5+fyF/Ddtjfb9IInZK+k3HSz8JcqGo4JJaRlTTk7GkJEzOjy9yfCxJbF4zAuVpmVjk= Keys AES5846c14298adad997effdfb42dec188be92ea336ff61900cccae85a7cf0e5951 SaltDcRatByqwqdanchun | |||||||||||||||
| 2744 | "C:\Program Files\Orcus\Orcus.exe" | C:\Program Files\Orcus\Orcus.exe | taskeng.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
16 241
Read events
15 812
Write events
429
Delete events
0
Modification events
| (PID) Process: | (2472) Defender Control.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2472) Defender Control.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2472) Defender Control.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2472) Defender Control.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2472) Defender Control.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2624) svchost.exe | Key: | HKEY_CURRENT_USER |
| Operation: | write | Name: | di |
Value: ! | |||
| (PID) Process: | (4044) dlhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4044) dlhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4044) dlhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4044) dlhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
9
Suspicious files
7
Text files
11
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3464 | dControl.exe | C:\Windows\TEMP\3n4l6n4j.tmp | text | |
MD5:E00DCC76E4DCD90994587375125DE04B | SHA256:C8709F5A8B971D136E2273D66E65449791CA8EBA1F47DD767733EA52EE635447 | |||
| 3464 | dControl.exe | C:\Windows\TEMP\autF463.tmp | binary | |
MD5:EFE44D9F6E4426A05E39F99AD407D3E7 | SHA256:5EA3B26C6B1B71EDAEF17CE365D50BE963AE9F4CB79B39EC723FE6E9E4054366 | |||
| 2472 | Defender Control.exe | C:\Users\admin\AppData\Local\Temp\dControl.exe | executable | |
MD5:58008524A6473BDF86C1040A9A9E39C3 | SHA256:1EF6C1A4DFDC39B63BFE650CA81AB89510DE6C0D3D7C608AC5BE80033E559326 | |||
| 2840 | dControl.exe | C:\Users\admin\AppData\Local\Temp\2l8k4p0r.tmp | text | |
MD5:E00DCC76E4DCD90994587375125DE04B | SHA256:C8709F5A8B971D136E2273D66E65449791CA8EBA1F47DD767733EA52EE635447 | |||
| 2840 | dControl.exe | C:\Users\admin\AppData\Local\Temp\autF339.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
| 3464 | dControl.exe | C:\Windows\TEMP\autF443.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
| 2840 | dControl.exe | C:\Users\admin\AppData\Local\Temp\autF34B.tmp | binary | |
MD5:ECFFD3E81C5F2E3C62BCDC122442B5F2 | SHA256:9874AB363B07DCC7E9CD6022A380A64102C1814343642295239A9F120CB941C5 | |||
| 3992 | dControl.exe | C:\Windows\TEMP\autF53F.tmp | binary | |
MD5:ECFFD3E81C5F2E3C62BCDC122442B5F2 | SHA256:9874AB363B07DCC7E9CD6022A380A64102C1814343642295239A9F120CB941C5 | |||
| 4044 | dlhost.exe | C:\Users\admin\AppData\Local\Temp\4uazkdsx.0.cs | text | |
MD5:716629450944773311A3FCFE7803D1E1 | SHA256:17DC45930397C4A08A326DD60DCCF48B835795EFCAE8359AD1EB97CC362F02E5 | |||
| 1496 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCF7FC.tmp | res | |
MD5:697F148DC1B31DEB9E707997646DEF0B | SHA256:AB014A36B78FEBF2234C8576AC531548C047DD7F45873D108C698740C503DEFF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
19
DNS requests
3
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2632 | svhost.exe | 147.185.221.16:40537 | social-mod.gl.at.ply.gg | PLAYIT-GG | US | malicious |
2624 | svchost.exe | 209.25.141.211:51206 | physical-several.at.ply.gg | PLAYIT-GG | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
social-mod.gl.at.ply.gg |
| unknown |
physical-several.at.ply.gg |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |