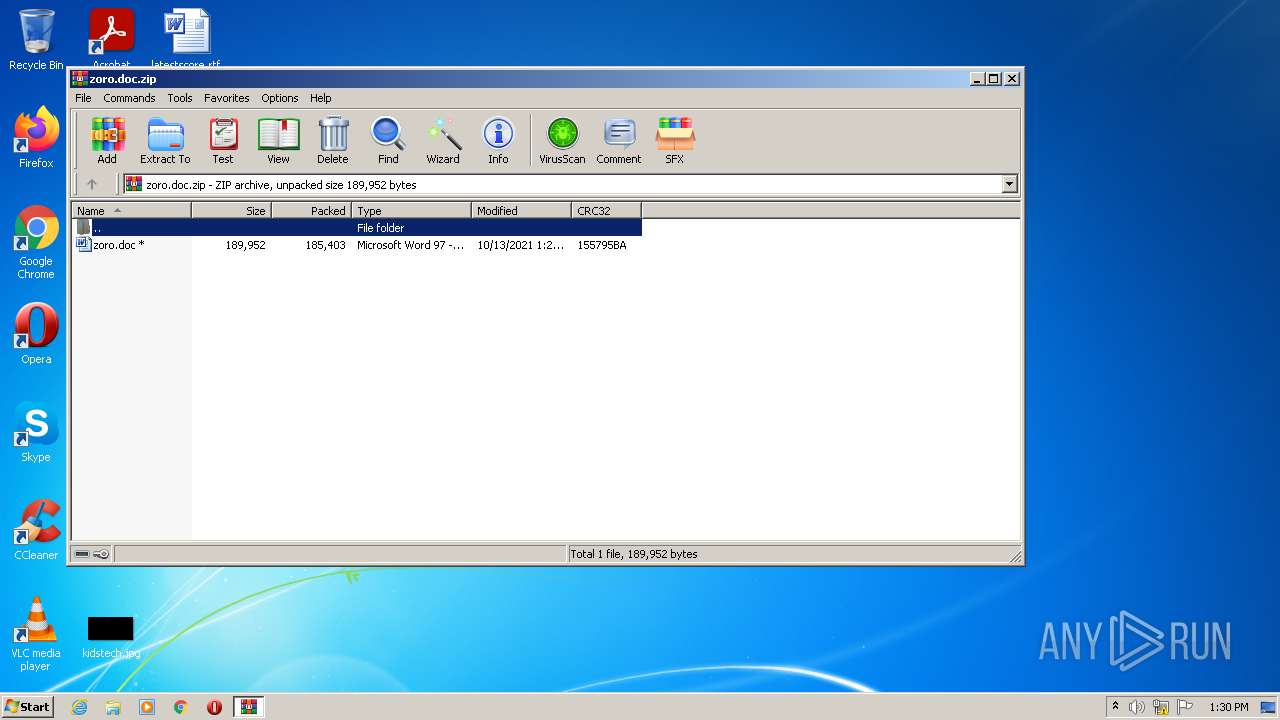
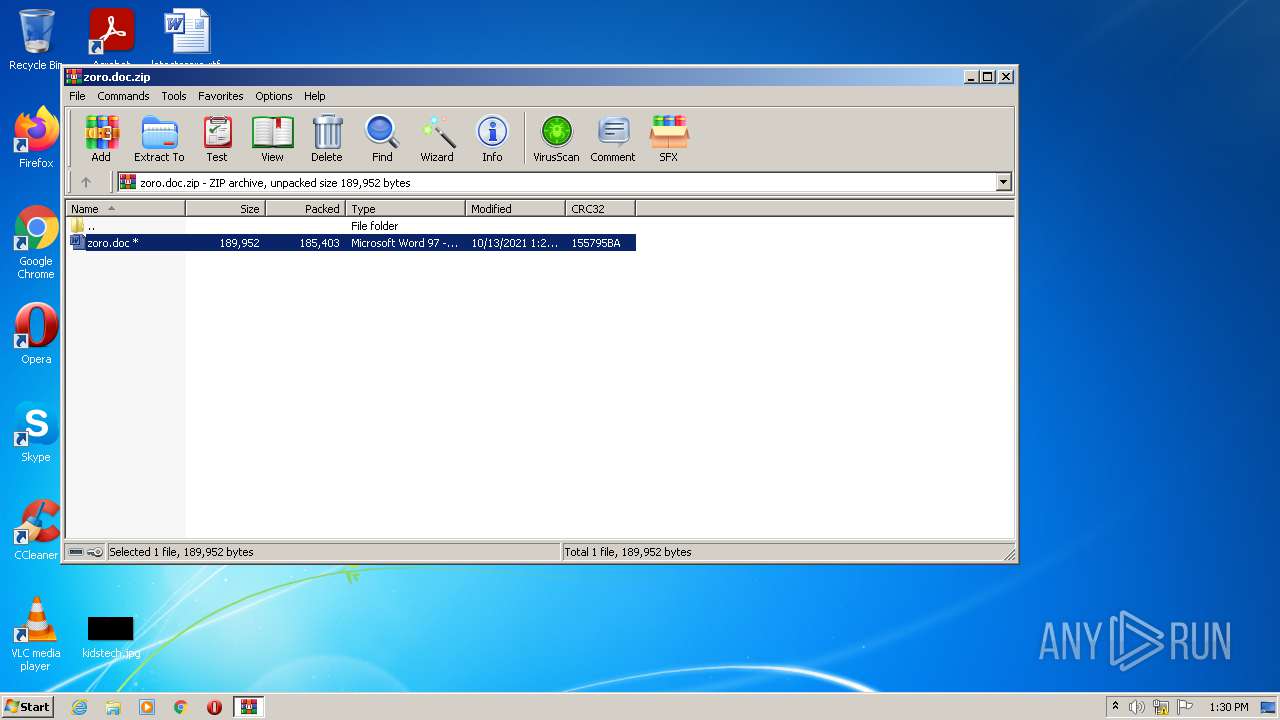
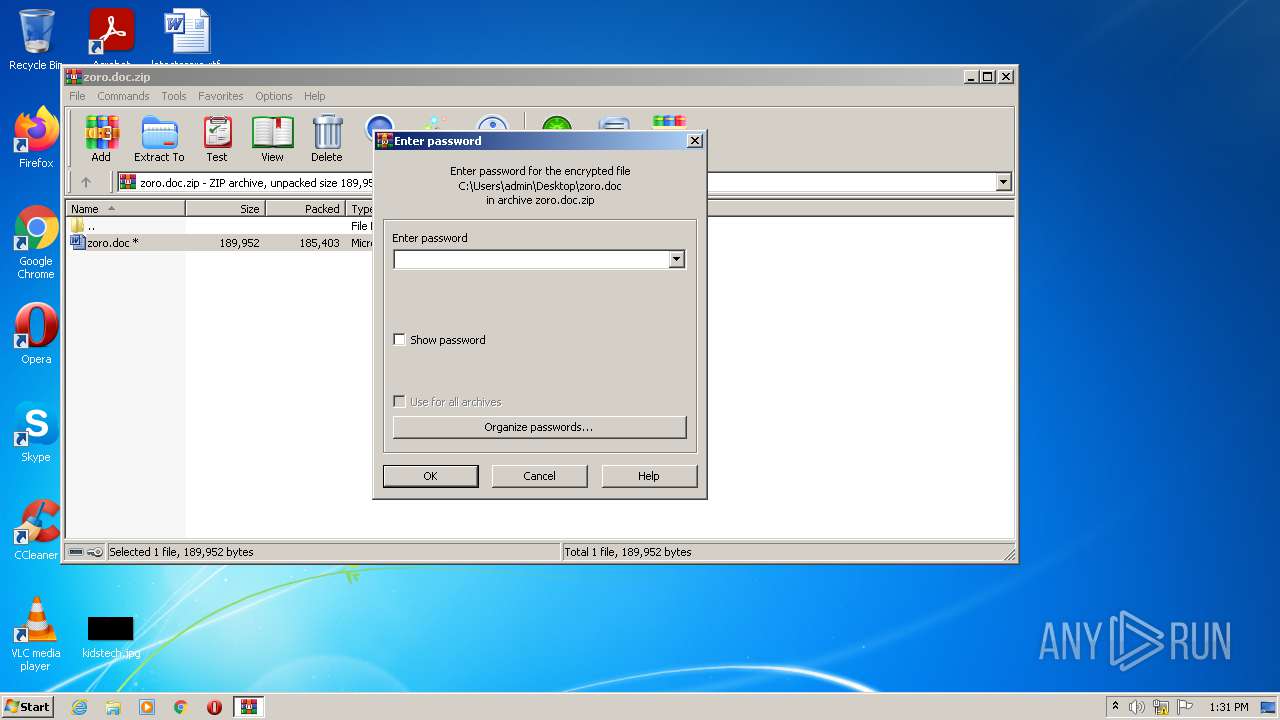
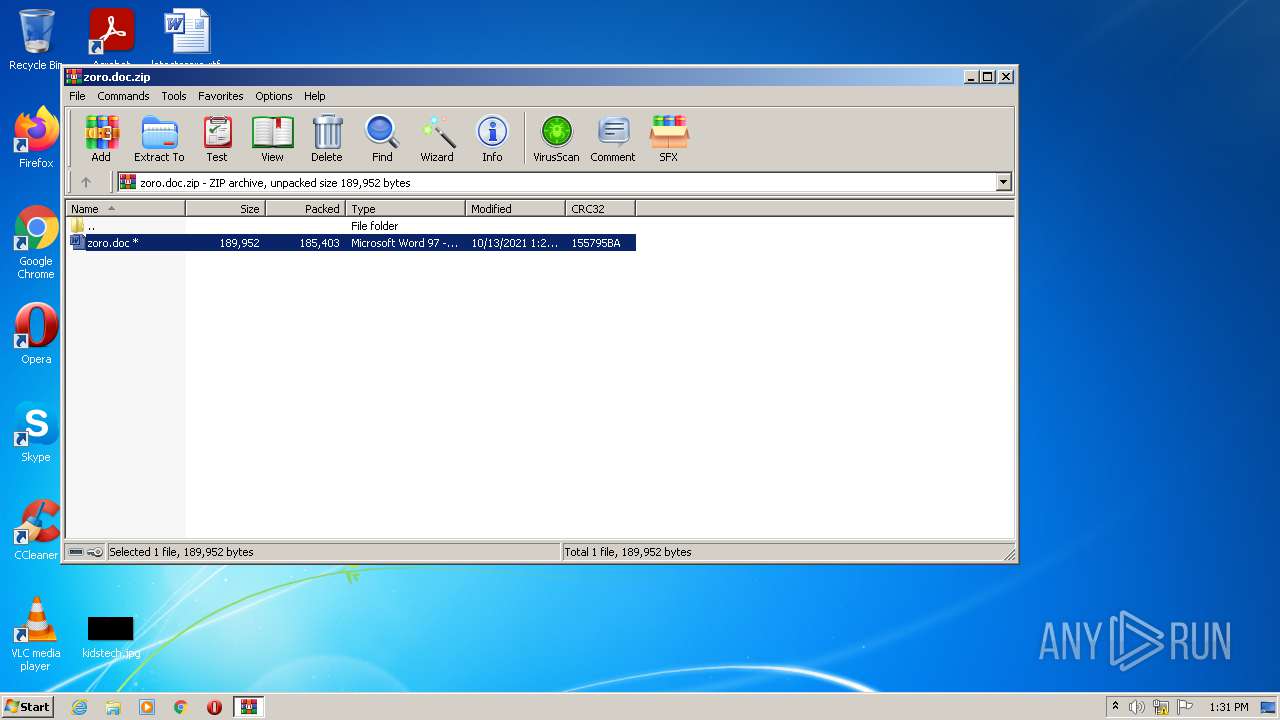
| File name: | zoro.doc.zip |
| Full analysis: | https://app.any.run/tasks/6d29556f-4aad-4640-92e6-30d6ac681680 |
| Verdict: | Malicious activity |
| Threats: | Hancitor was created in 2014 to drop other malware on infected machines. It is also known as Tordal and Chanitor. This malware is available as a service which makes it accessible tools to criminals and contributes to the popularity of this virus. |
| Analysis date: | October 13, 2021, 12:30:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B4F30A2626526692CDE3944FD44BABF5 |
| SHA1: | 24E70C87C94A3B158D991CBE032F29981D98366D |
| SHA256: | F96D2080BF79C591E1CA112215C88A5A2DADB8A16D745CFD1375C2AA62A5A716 |
| SSDEEP: | 3072:k4jrCrgGL1MaLGNZWz6d8D0Xdd8iOZGgQyljtH91xR9mv5BRlRUVIZFZ4eUzZ:HOz5QXd8D0XdKvp1VD15qHl5d4JzZ |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2760)
Connects to CnC server
- rundll32.exe (PID: 2840)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2760)
HANCITOR was detected
- rundll32.exe (PID: 2840)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 680)
- WinRAR.exe (PID: 2712)
Checks supported languages
- WinRAR.exe (PID: 680)
- WinRAR.exe (PID: 2712)
Reads default file associations for system extensions
- WinRAR.exe (PID: 680)
- WinRAR.exe (PID: 2712)
- WINWORD.EXE (PID: 2760)
Drops a file that was compiled in debug mode
- WINWORD.EXE (PID: 2760)
Uses RUNDLL32.EXE to load library
- WINWORD.EXE (PID: 2760)
Checks for external IP
- rundll32.exe (PID: 2840)
INFO
Checks supported languages
- WINWORD.EXE (PID: 3020)
- WINWORD.EXE (PID: 2760)
- rundll32.exe (PID: 2840)
Reads the computer name
- WINWORD.EXE (PID: 3020)
- WINWORD.EXE (PID: 2760)
- rundll32.exe (PID: 2840)
Manual execution by user
- WINWORD.EXE (PID: 3020)
- WinRAR.exe (PID: 2712)
- WINWORD.EXE (PID: 2760)
Creates files in the user directory
- WINWORD.EXE (PID: 3020)
- WINWORD.EXE (PID: 2760)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3020)
- WINWORD.EXE (PID: 2760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:10:13 12:28:16 |
| ZipCRC: | 0x155795ba |
| ZipCompressedSize: | 185403 |
| ZipUncompressedSize: | 189952 |
| ZipFileName: | zoro.doc |
Total processes
45
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\zoro.doc.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2712 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\zoro.doc.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2760 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\zoro.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2840 | rundll32.exe c:\users\admin\appdata\roaming\microsoft\templates\gelforr.dap,BNJAFSRSQIX | C:\Windows\system32\rundll32.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3020 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\zoro.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
6 027
Read events
4 729
Write events
746
Delete events
552
Modification events
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\zoro.doc.zip | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
10
Text files
2
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3020 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRFCC8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2760 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9EE4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3020 | WINWORD.EXE | C:\Users\admin\Desktop\~$zoro.doc | pgc | |
MD5:— | SHA256:— | |||
| 3020 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 680 | WinRAR.exe | C:\Users\admin\Desktop\zoro.doc | binary | |
MD5:— | SHA256:— | |||
| 3020 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF75C17B192DF1E36E.TMP | binary | |
MD5:— | SHA256:— | |||
| 2760 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3020 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF5F797476DDF28274.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2712 | WinRAR.exe | C:\Users\admin\Desktop\zoro.doc | binary | |
MD5:— | SHA256:— | |||
| 2760 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFC8EF237A3F6313F5.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
7
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2840 | rundll32.exe | GET | 200 | 54.243.29.214:80 | http://api.ipify.org/ | US | text | 12 b | shared |
2840 | rundll32.exe | POST | — | 194.147.115.132:80 | http://forkineler.com/8/forum.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2840 | rundll32.exe | 54.243.29.214:80 | api.ipify.org | Amazon.com, Inc. | US | suspicious |
2840 | rundll32.exe | 194.147.115.132:80 | forkineler.com | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ipify.org |
| shared |
forkineler.com |
| malicious |
yemodene.ru |
| unknown |
fordecits.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2840 | rundll32.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup api.ipify.org |
2840 | rundll32.exe | A Network Trojan was detected | ET TROJAN Tordal/Hancitor/Chanitor Checkin |