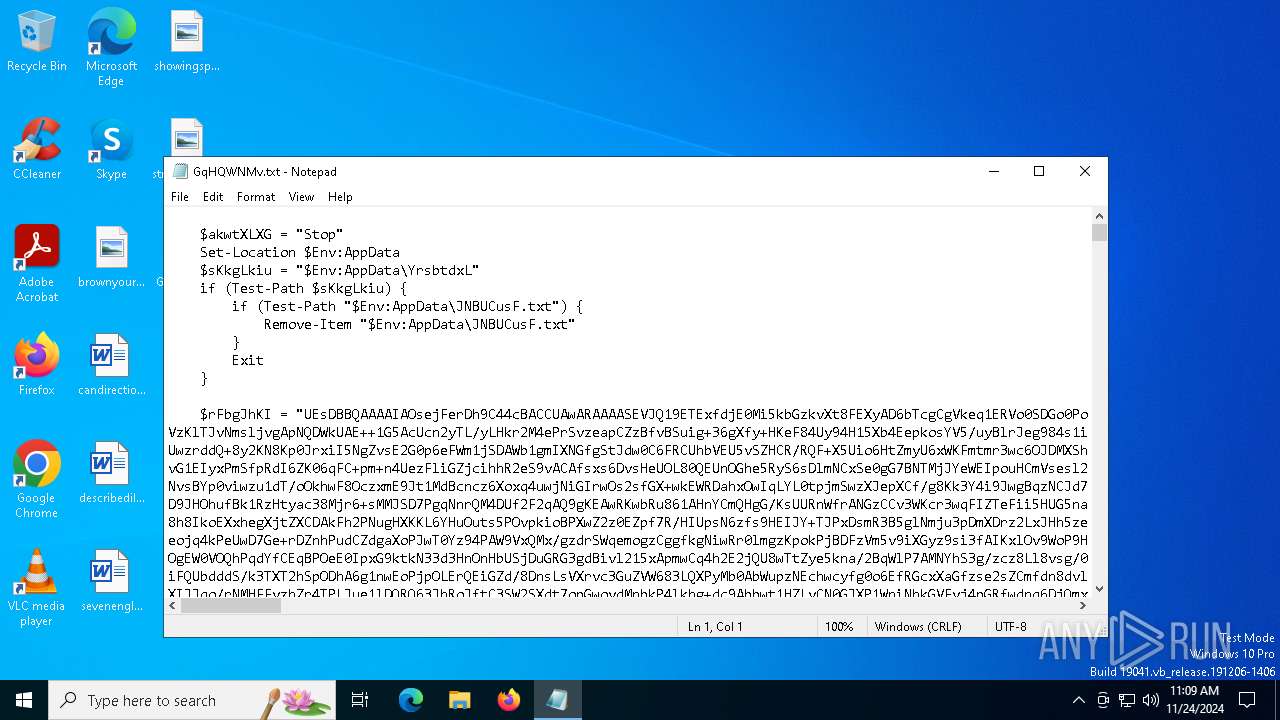
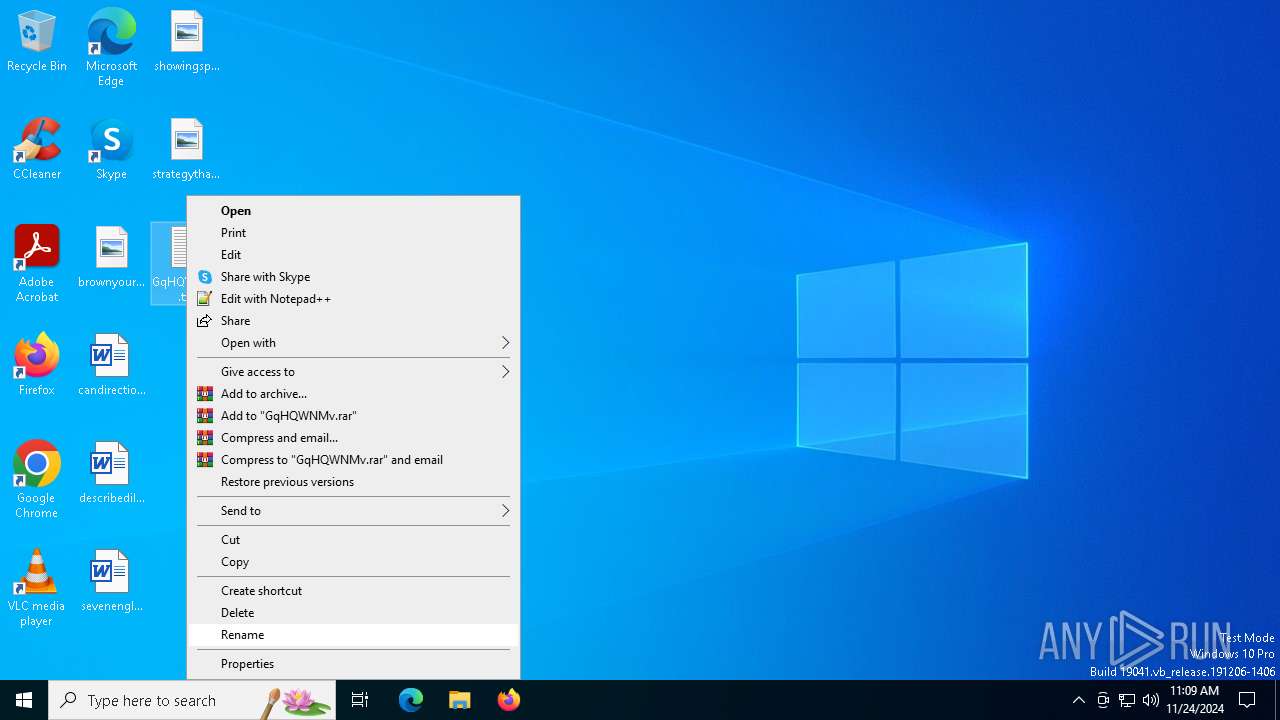
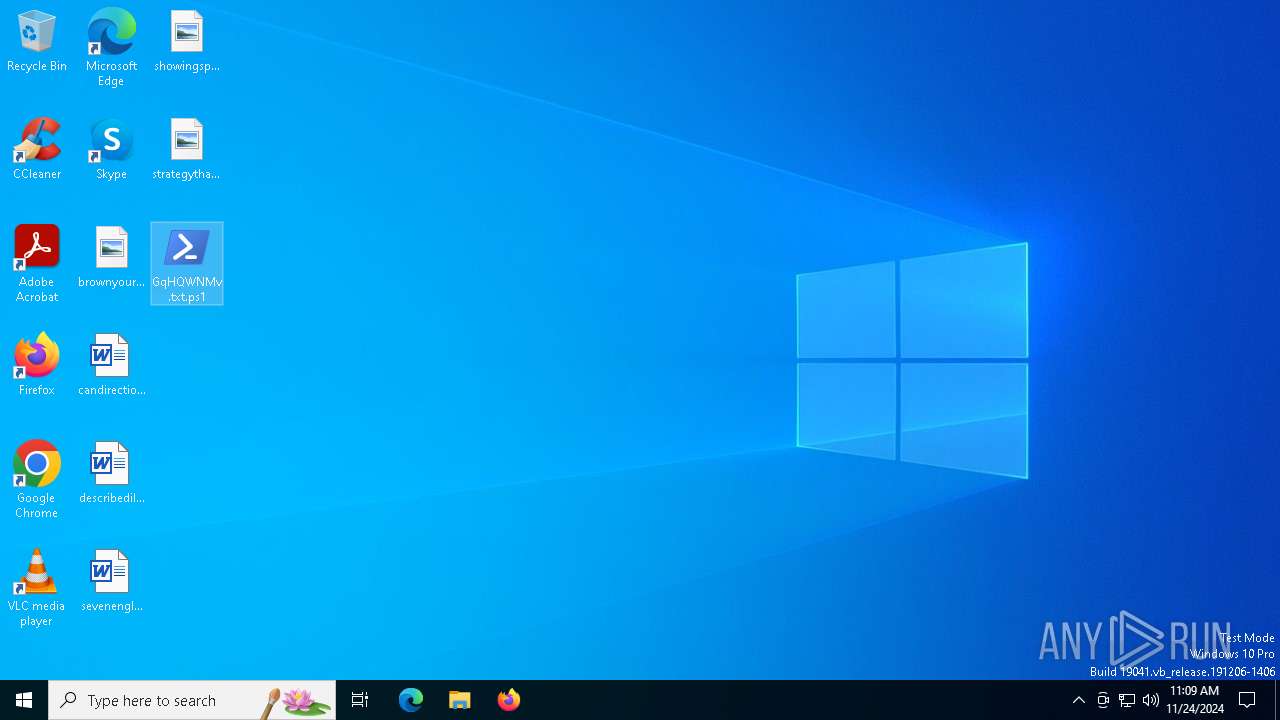
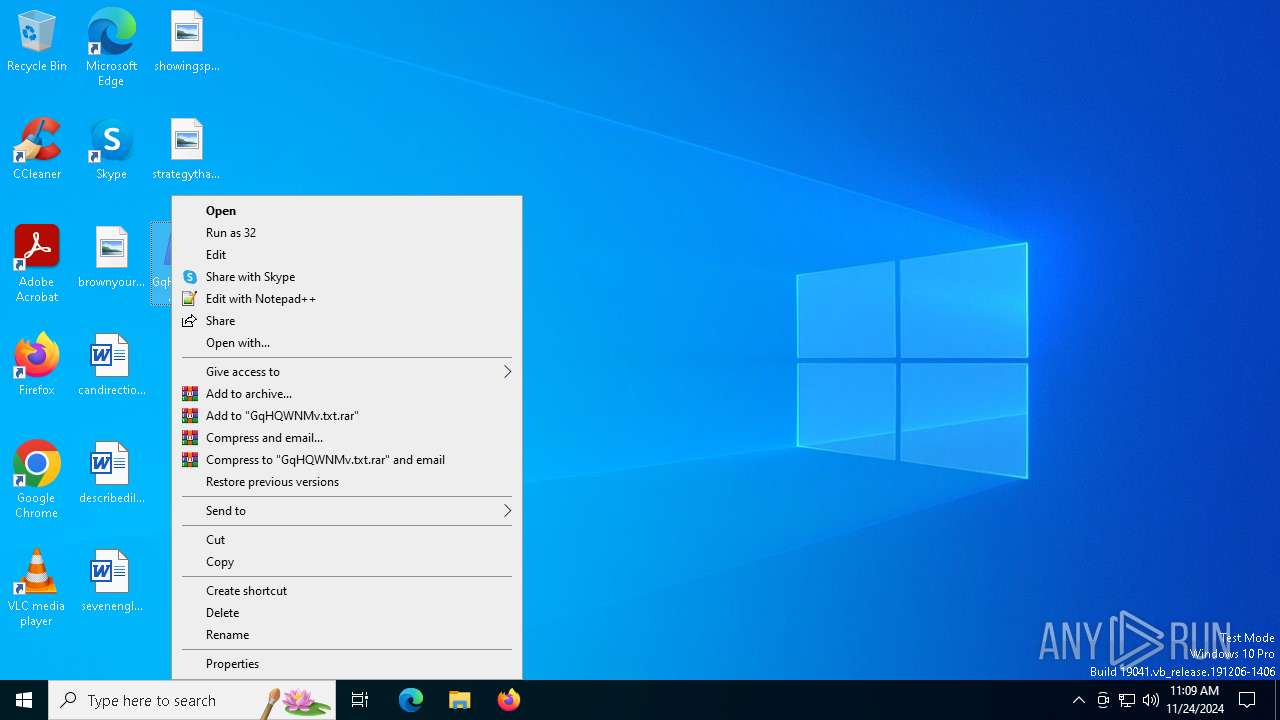
| File name: | GqHQWNMv.txt |
| Full analysis: | https://app.any.run/tasks/d63691b1-079f-4e63-a582-402d727ca11c |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | November 24, 2024, 11:09:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (65265), with CRLF line terminators |
| MD5: | 17917B9AB6492A66D3751C21C4EBB768 |
| SHA1: | CDC619BAC0FD3BEA62FCB5DA052CA6B8380CFA0B |
| SHA256: | F8278FE32A0916F85BD703AA8975D4E559466EE96A188F68BD2A2816FDBB18A8 |
| SSDEEP: | 49152:NuviW4pThmwMmgZGnCFpZXo2p3qjNibnvLXa89D3PQxBPm7aN2rtYYcd0Bke2GfQ:T |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 4132)
Actions looks like stealing of personal data
- msiexec.exe (PID: 2796)
Steals credentials from Web Browsers
- msiexec.exe (PID: 2796)
LUMMA has been detected (YARA)
- msiexec.exe (PID: 2796)
SUSPICIOUS
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4132)
Executable content was dropped or overwritten
- powershell.exe (PID: 4132)
- mdnsresponder.exe (PID: 1740)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 4132)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 4132)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 4132)
The process drops C-runtime libraries
- powershell.exe (PID: 4132)
Process drops legitimate windows executable
- powershell.exe (PID: 4132)
Process drops SQLite DLL files
- powershell.exe (PID: 4132)
- mdnsresponder.exe (PID: 1740)
Starts application with an unusual extension
- mdnsresponder.exe (PID: 1740)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 396)
Manual execution by a user
- powershell.exe (PID: 4132)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4132)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4132)
Checks supported languages
- mdnsresponder.exe (PID: 1740)
- more.com (PID: 5316)
The process uses the downloaded file
- powershell.exe (PID: 4132)
Reads the computer name
- mdnsresponder.exe (PID: 1740)
- more.com (PID: 5316)
Creates files or folders in the user directory
- mdnsresponder.exe (PID: 1740)
Reads the software policy settings
- msiexec.exe (PID: 2796)
Create files in a temporary directory
- mdnsresponder.exe (PID: 1740)
- more.com (PID: 5316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
124
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\GqHQWNMv.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
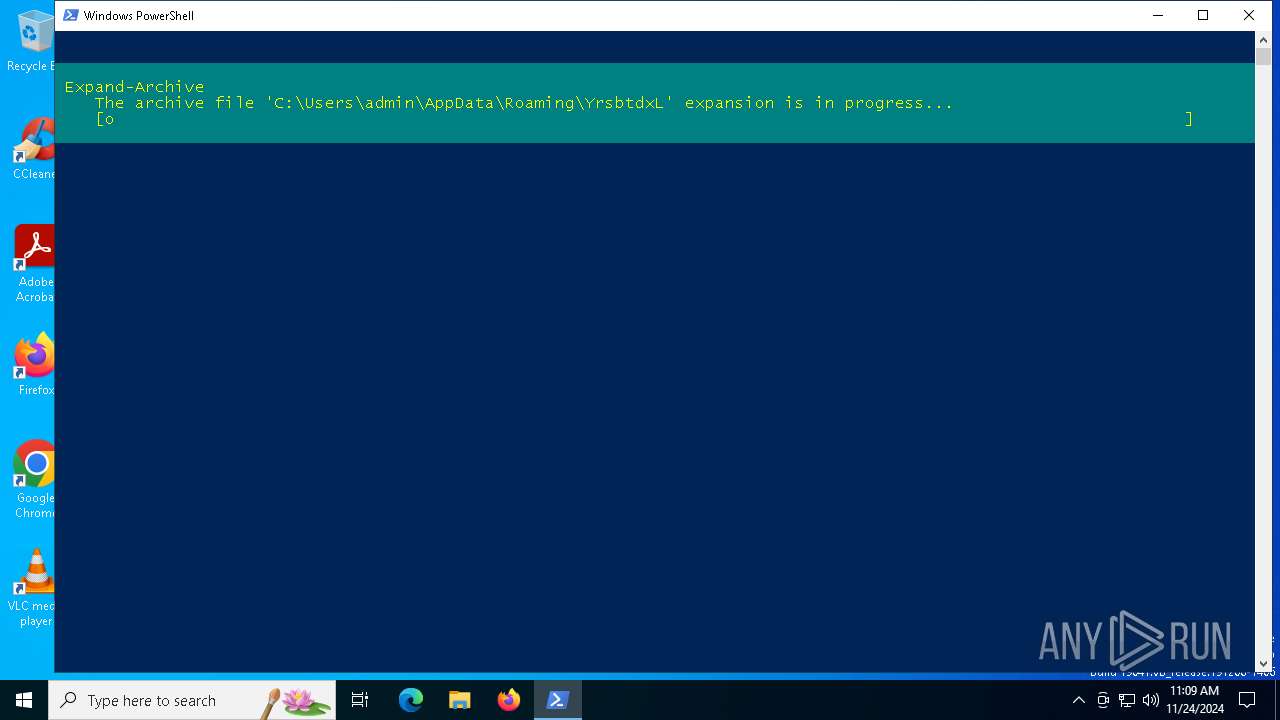
| 1740 | "C:\Users\admin\AppData\Roaming\YrsbtdxL\mdnsresponder.exe" | C:\Users\admin\AppData\Roaming\YrsbtdxL\mdnsresponder.exe | powershell.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: iTop Data Recovery Service Exit code: 1 Version: 4.0.0.168 Modules
| |||||||||||||||
| 1760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | C:\WINDOWS\SysWOW64\msiexec.exe | C:\Windows\SysWOW64\msiexec.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4132 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\GqHQWNMv.txt.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5316 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | mdnsresponder.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 690
Read events
8 689
Write events
1
Delete events
0
Modification events
| (PID) Process: | (4132) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | NetUtilityApp |
Value: C:\Users\admin\AppData\Roaming\YrsbtdxL\mdnsresponder.exe | |||
Executable files
78
Suspicious files
10
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4132 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:8C080D077E76C8CDC16108EE5704AB72 | SHA256:B062653B421044CCC1E30F63F510BD8D1F9E67C7DF9CBCA728025C16528BD6B7 | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4BJ15MQT91Z44ZWH1Q71.temp | binary | |
MD5:8C080D077E76C8CDC16108EE5704AB72 | SHA256:B062653B421044CCC1E30F63F510BD8D1F9E67C7DF9CBCA728025C16528BD6B7 | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_h5qlz2ii.0ve.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Roaming\YrsbtdxL\HEIC_DLL_v142.dll | executable | |
MD5:A706480C10F094BBCE144E92A48A9E63 | SHA256:27D4A7C49206D81B0BCDBD2922C0A1BC36177ECB315041233126B654A78A8A86 | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF13c14f.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Roaming\YrsbtdxL\HEIC_SWIG_DLL_v142.dll | executable | |
MD5:0EDD60513A12689189309B50261E8979 | SHA256:54F9E01DF5A6061A4D84BDC0FC0D263A70F4FA2BAE307146BAE9D00B90226DAB | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kfqnzkj3.35c.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Roaming\YrsbtdxL\Microsoft.Web.WebView2.Core.dll | executable | |
MD5:28C6A96591A4890D33DEAA7DBABEBF10 | SHA256:6E7B8869B538417CC361C97A37F7CEEC92DDC8AD84E0585BCF7021DABBF6F985 | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Roaming\YrsbtdxL\Microsoft.AppCenter.Crashes.dll | executable | |
MD5:C3EA6FFEBCF0943FEFC6A793CE84E33B | SHA256:1F4113C085C5AB1ED9DE41DDE307A28632851444F331F90CA1B5B76159794FEC | |||
| 4132 | powershell.exe | C:\Users\admin\AppData\Roaming\YrsbtdxL\Microsoft.AppCenter.Analytics.dll | executable | |
MD5:06C46082C5D357EABCA5698946BDDF19 | SHA256:52591E162196D5EB495E9530A0334A72D940EFA977881B31EF4A399BB275E13B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
26
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6068 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6068 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 104.21.20.178:443 | https://sturdy-operated.cyou/api | unknown | text | 17.1 Kb | unknown |
— | — | POST | 200 | 172.67.193.71:443 | https://sturdy-operated.cyou/api | unknown | text | 2 b | unknown |
— | — | POST | 200 | 172.67.193.71:443 | https://sturdy-operated.cyou/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 104.21.20.178:443 | https://sturdy-operated.cyou/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 172.67.193.71:443 | https://sturdy-operated.cyou/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 104.21.20.178:443 | https://sturdy-operated.cyou/api | unknown | text | 15 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6068 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6068 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6068 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
sturdy-operated.cyou |
| unknown |
self.events.data.microsoft.com |
| whitelisted |