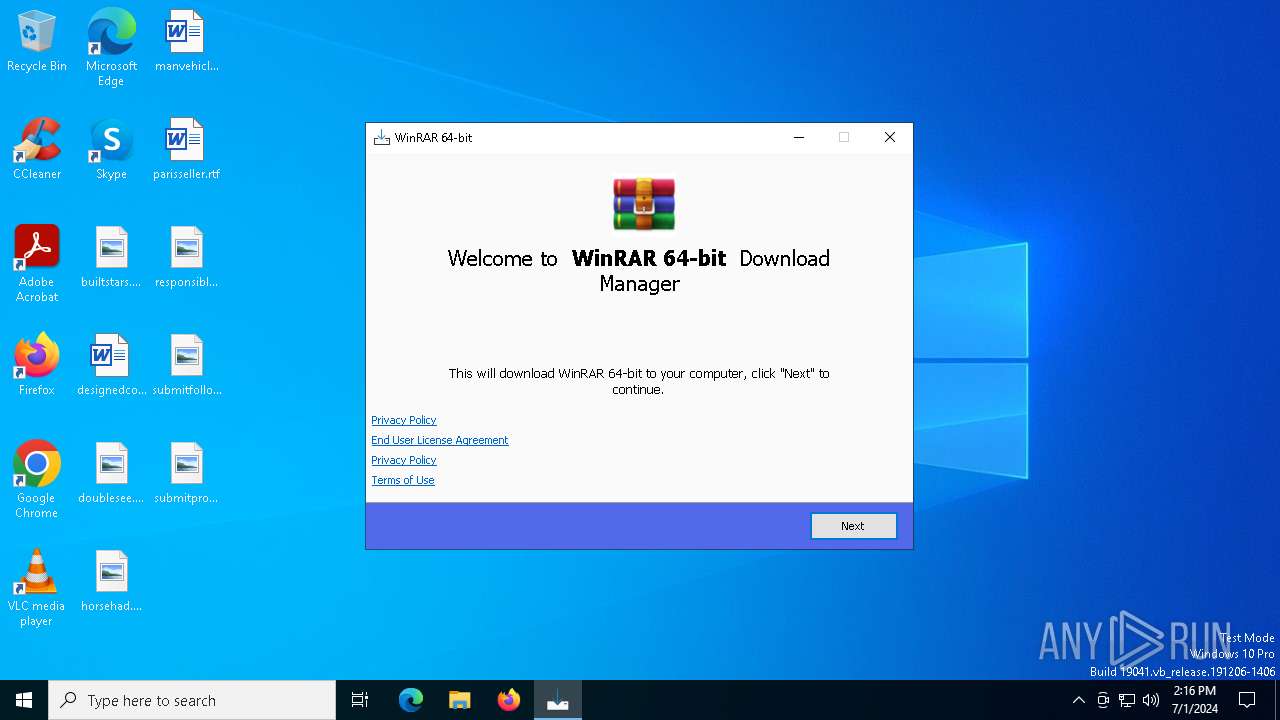
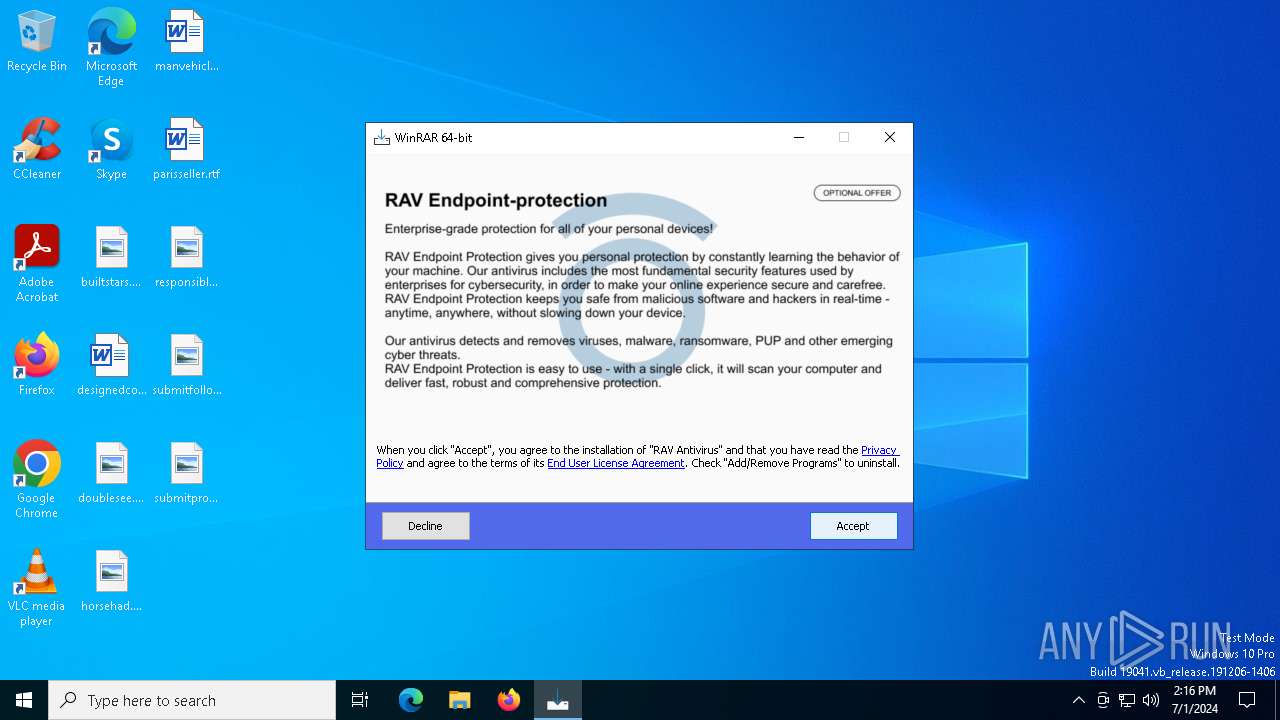
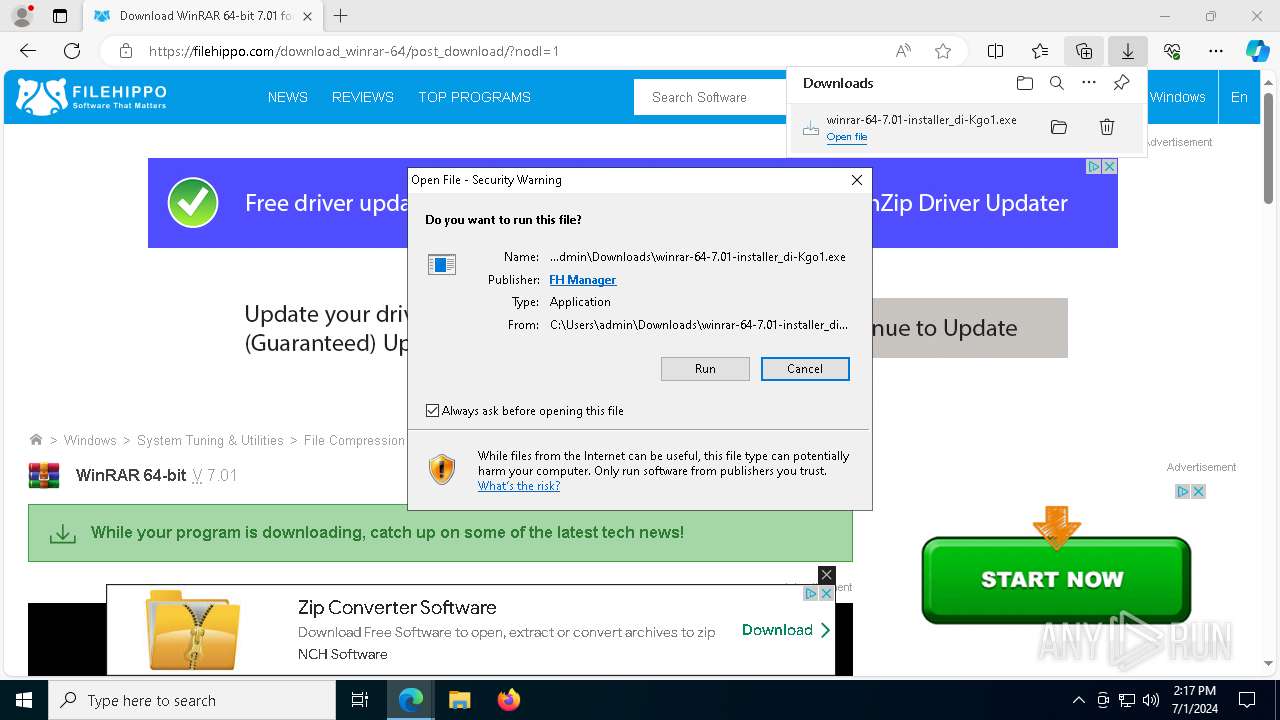
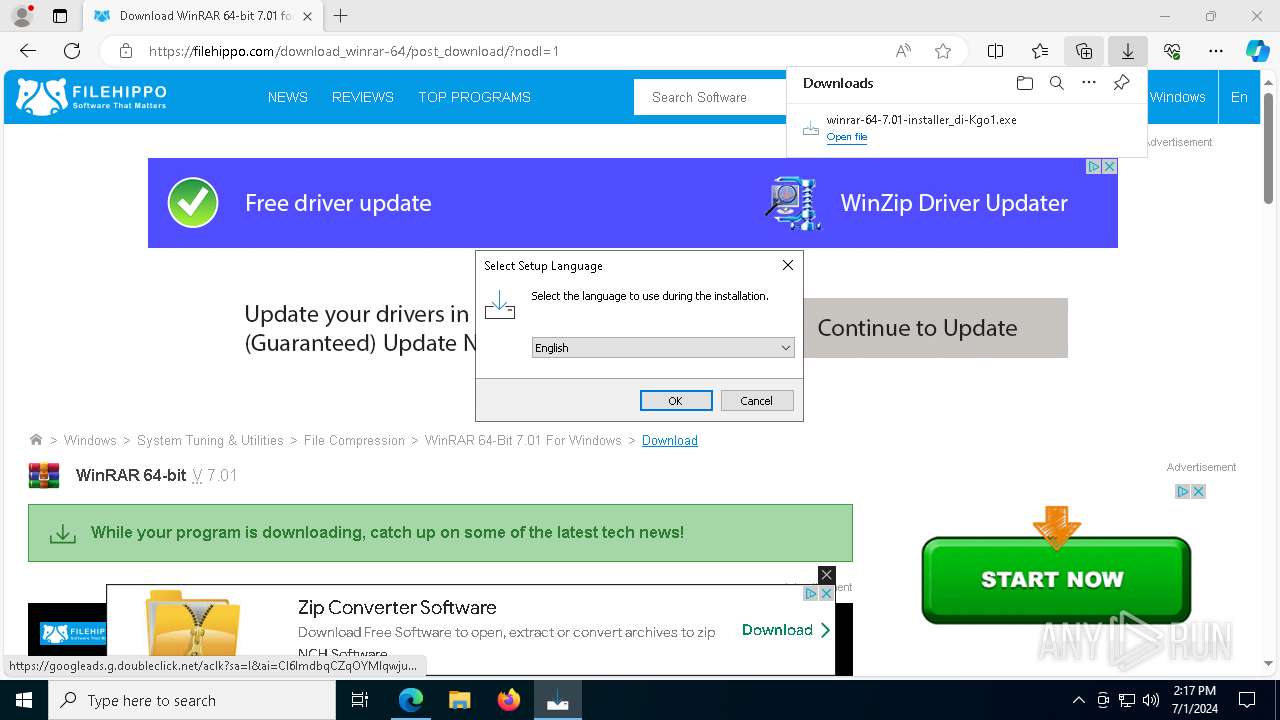
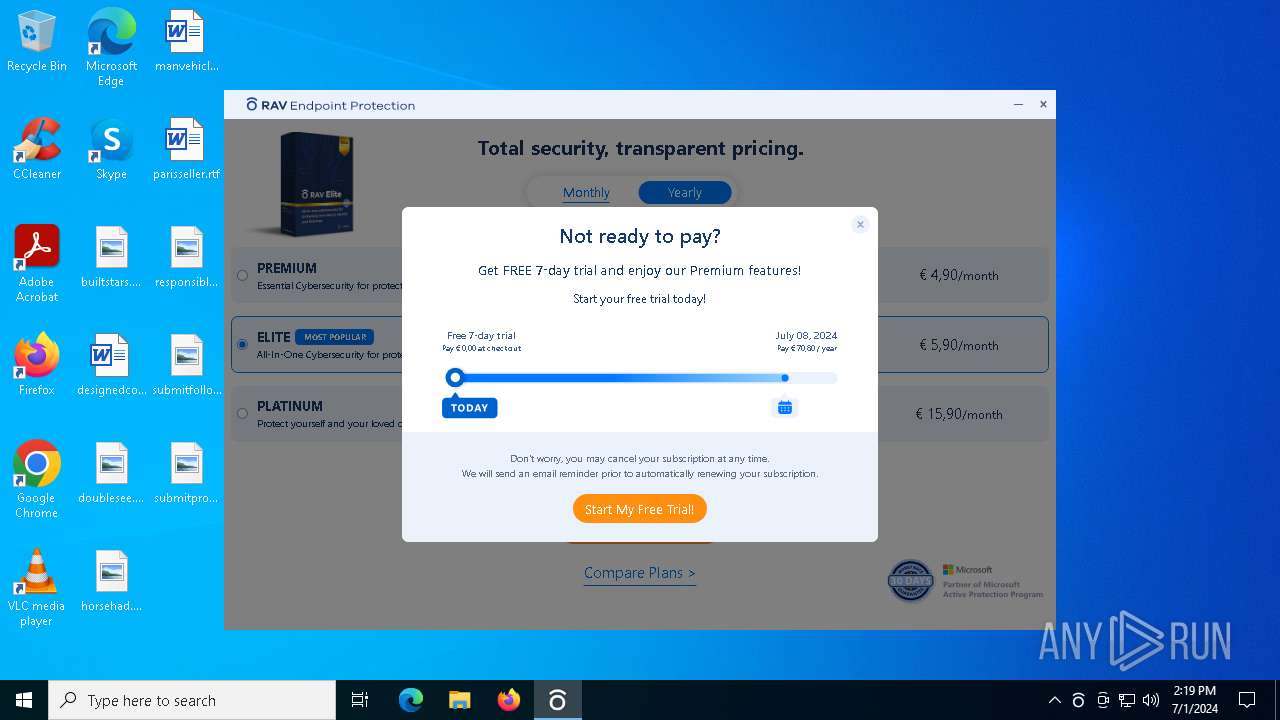
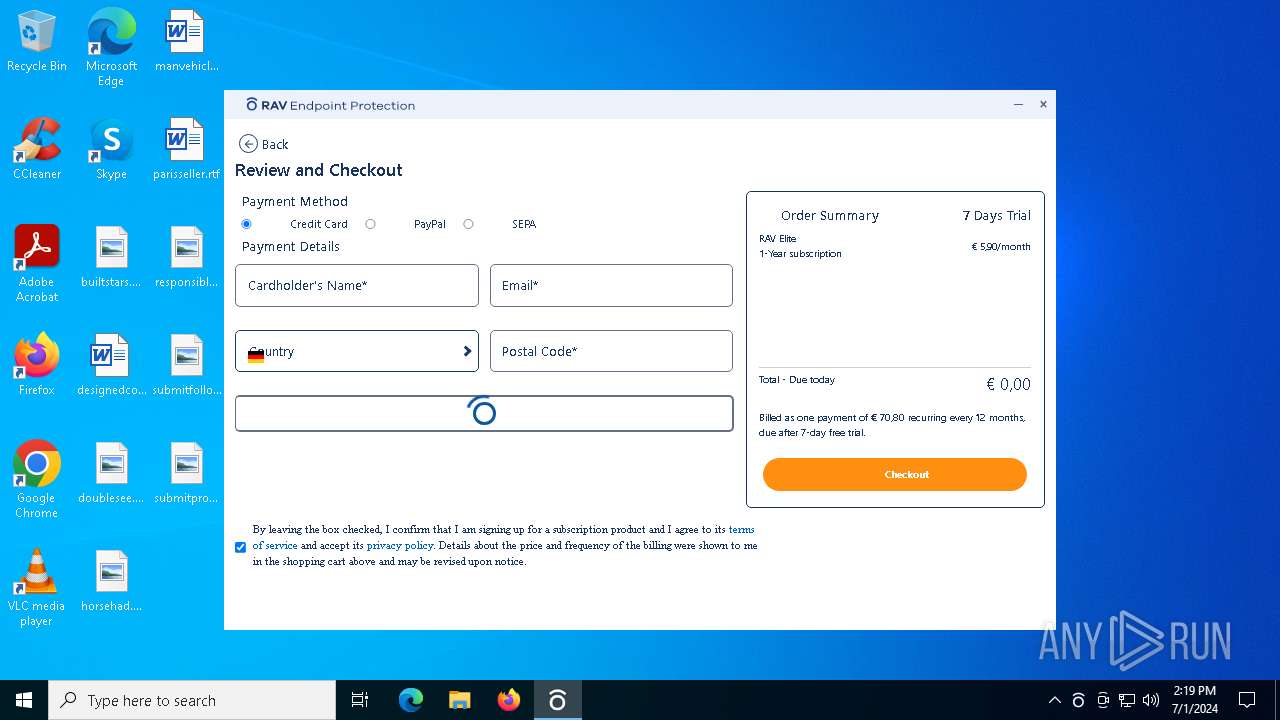
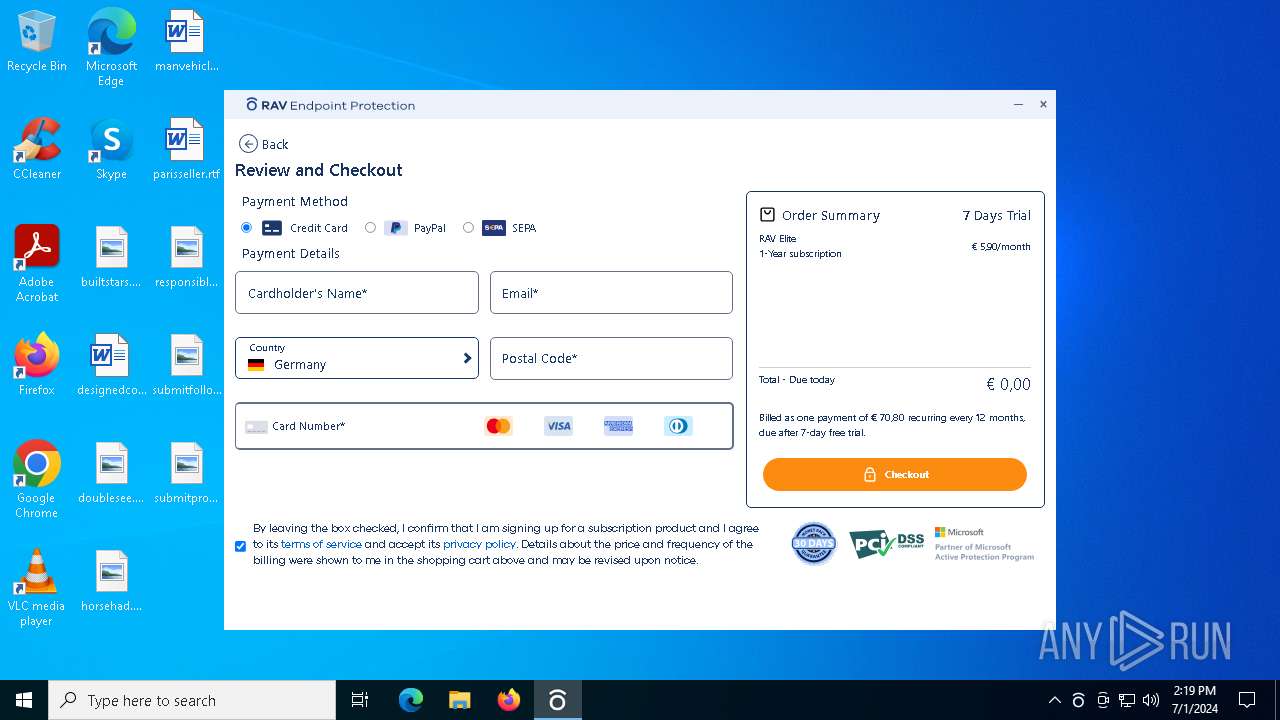
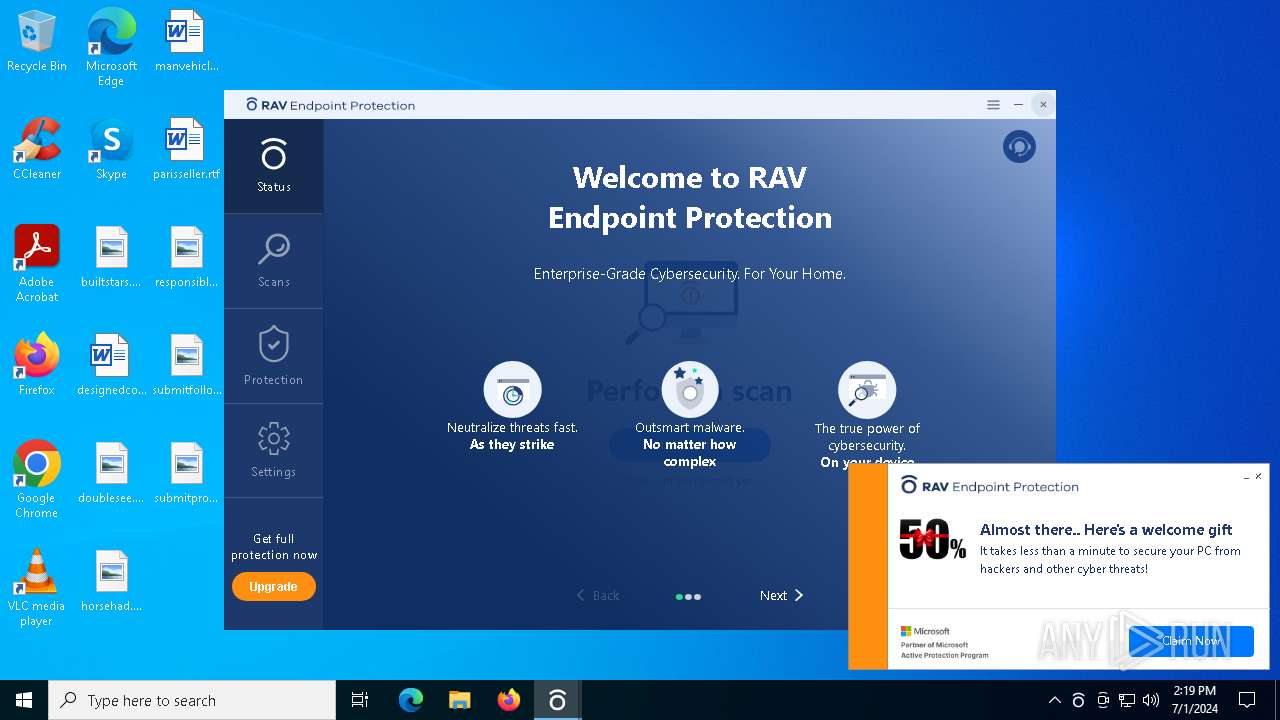
| File name: | winrar-64-6.21-installer_AmGAP-1.exe |
| Full analysis: | https://app.any.run/tasks/87d3d8d1-4029-4738-8d2b-650e27eacada |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | July 01, 2024, 14:16:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 17B1EA1089CCF5E5EF81C5DFAFDB90FF |
| SHA1: | AF0C22F715C97474303FF13364A71280C1D0F698 |
| SHA256: | F81C79DE1B8BEC0FFCD299C964D8CF0BEE0D983AB465B693DBFD7347D2C64F87 |
| SSDEEP: | 49152:z7HecD4dnbibBlh/hYjPfySXi8AWAkCk1pW0RA/8XLHqwy8xSIuZfalHuxBoa4kp:/+cD4dnEhYjPfySXzAaPQYLHqw9SIuZp |
MALICIOUS
Drops the executable file immediately after the start
- winrar-64-6.21-installer_AmGAP-1.exe (PID: 244)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- 4bxsh541.exe (PID: 380)
- winrar-64-7.01-installer_di-Kgo1.exe (PID: 3128)
- winrar-64-7.01-installer_di-Kgo1.exe (PID: 8152)
- UnifiedStub-installer.exe (PID: 1280)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- winrar-64-6.21-installer_AmGAP-1.exe (PID: 2828)
- winrar-64-7.01-installer.exe (PID: 7228)
- saBSI.exe (PID: 7416)
- installer.exe (PID: 6684)
- installer.exe (PID: 6776)
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 1280)
- rsEngineSvc.exe (PID: 6804)
- rsEDRSvc.exe (PID: 6172)
- uihost.exe (PID: 3596)
- servicehost.exe (PID: 7720)
Creates a writable file in the system directory
- UnifiedStub-installer.exe (PID: 1280)
- rsEDRSvc.exe (PID: 6172)
Changes the autorun value in the registry
- rundll32.exe (PID: 7800)
Registers / Runs the DLL via REGSVR32.EXE
- installer.exe (PID: 6776)
Steals credentials from Web Browsers
- servicehost.exe (PID: 7720)
SUSPICIOUS
Executable content was dropped or overwritten
- winrar-64-6.21-installer_AmGAP-1.exe (PID: 244)
- winrar-64-6.21-installer_AmGAP-1.exe (PID: 2828)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- UnifiedStub-installer.exe (PID: 1280)
- 4bxsh541.exe (PID: 380)
- winrar-64-7.01-installer_di-Kgo1.exe (PID: 3128)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.exe (PID: 8152)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- winrar-64-7.01-installer.exe (PID: 7228)
- saBSI.exe (PID: 7416)
- installer.exe (PID: 6684)
- installer.exe (PID: 6776)
Reads the date of Windows installation
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 3848)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- winrar-64-7.01-installer.exe (PID: 7228)
- rsEDRSvc.exe (PID: 6172)
- rsEngineSvc.exe (PID: 6804)
Reads security settings of Internet Explorer
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 3848)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- winrar-64-7.01-installer.exe (PID: 7228)
- saBSI.exe (PID: 7416)
- UnifiedStub-installer.exe (PID: 1280)
- installer.exe (PID: 6776)
- rsWSC.exe (PID: 7656)
- rsEngineSvc.exe (PID: 6732)
- rsEDRSvc.exe (PID: 6360)
- rsEngineSvc.exe (PID: 6804)
- uihost.exe (PID: 3596)
Process drops legitimate windows executable
- 4bxsh541.exe (PID: 380)
- UnifiedStub-installer.exe (PID: 1280)
- installer.exe (PID: 6776)
Searches for installed software
- UnifiedStub-installer.exe (PID: 1280)
- Uninstall.exe (PID: 5884)
- rsEDRSvc.exe (PID: 6172)
- updater.exe (PID: 8464)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 1280)
- Uninstall.exe (PID: 5884)
- installer.exe (PID: 6776)
- servicehost.exe (PID: 7720)
Executes as Windows Service
- rsSyncSvc.exe (PID: 6216)
- rsWSC.exe (PID: 6276)
- rsClientSvc.exe (PID: 6580)
- rsEngineSvc.exe (PID: 6804)
- rsEDRSvc.exe (PID: 6172)
- WmiApSrv.exe (PID: 6836)
- servicehost.exe (PID: 7720)
Reads the Windows owner or organization settings
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
Reads Microsoft Outlook installation path
- winrar-64-7.01-installer.exe (PID: 7228)
Reads Internet Explorer settings
- winrar-64-7.01-installer.exe (PID: 7228)
Checks Windows Trust Settings
- saBSI.exe (PID: 7416)
- rsWSC.exe (PID: 7656)
- rsEngineSvc.exe (PID: 6732)
- rsWSC.exe (PID: 6276)
- installer.exe (PID: 6776)
- rsEDRSvc.exe (PID: 6360)
- rsEDRSvc.exe (PID: 6172)
- rsEngineSvc.exe (PID: 6804)
- servicehost.exe (PID: 7720)
- uihost.exe (PID: 3596)
- updater.exe (PID: 8464)
Executes application which crashes
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
The process verifies whether the antivirus software is installed
- saBSI.exe (PID: 7416)
- installer.exe (PID: 6684)
- installer.exe (PID: 6776)
- regsvr32.exe (PID: 1224)
- regsvr32.exe (PID: 6920)
- regsvr32.exe (PID: 7936)
- rsEngineSvc.exe (PID: 6804)
- rsEDRSvc.exe (PID: 6172)
- cmd.exe (PID: 8300)
- cmd.exe (PID: 8504)
- cmd.exe (PID: 8524)
- uihost.exe (PID: 3596)
- cmd.exe (PID: 8700)
- updater.exe (PID: 8464)
- servicehost.exe (PID: 7720)
- cmd.exe (PID: 8640)
Drops 7-zip archiver for unpacking
- winrar-64-7.01-installer.exe (PID: 7228)
- UnifiedStub-installer.exe (PID: 1280)
The process creates files with name similar to system file names
- UnifiedStub-installer.exe (PID: 1280)
- installer.exe (PID: 6776)
The process drops C-runtime libraries
- UnifiedStub-installer.exe (PID: 1280)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 1280)
Creates/Modifies COM task schedule object
- Uninstall.exe (PID: 5884)
- regsvr32.exe (PID: 6920)
- regsvr32.exe (PID: 7936)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 1280)
- rundll32.exe (PID: 7800)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 1280)
Adds/modifies Windows certificates
- saBSI.exe (PID: 7416)
- rsEngineSvc.exe (PID: 6732)
- servicehost.exe (PID: 7720)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 1280)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 1280)
Patches Antimalware Scan Interface function (YARA)
- component0.exe (PID: 420)
Dropped object may contain URLs of mainers pools
- rsEngineSvc.exe (PID: 6804)
Reads the BIOS version
- rsEDRSvc.exe (PID: 6172)
- rsEngineSvc.exe (PID: 6804)
Application launched itself
- rsAppUI.exe (PID: 2104)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 6172)
The process checks if it is being run in the virtual environment
- rsEngineSvc.exe (PID: 6804)
Potential Corporate Privacy Violation
- rsAppUI.exe (PID: 5816)
Reads Mozilla Firefox installation path
- servicehost.exe (PID: 7720)
- uihost.exe (PID: 3596)
Hides command output
- cmd.exe (PID: 8300)
- cmd.exe (PID: 8504)
- cmd.exe (PID: 8524)
Starts CMD.EXE for commands execution
- servicehost.exe (PID: 7720)
- updater.exe (PID: 8464)
INFO
Create files in a temporary directory
- winrar-64-6.21-installer_AmGAP-1.exe (PID: 244)
- winrar-64-6.21-installer_AmGAP-1.exe (PID: 2828)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- 4bxsh541.exe (PID: 380)
- winrar-64-7.01-installer_di-Kgo1.exe (PID: 3128)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.exe (PID: 8152)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- UnifiedStub-installer.exe (PID: 1280)
- saBSI.exe (PID: 7416)
- installer.exe (PID: 6776)
- rsAppUI.exe (PID: 2104)
Checks supported languages
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 3848)
- winrar-64-6.21-installer_AmGAP-1.exe (PID: 244)
- component0.exe (PID: 420)
- 4bxsh541.exe (PID: 380)
- UnifiedStub-installer.exe (PID: 1280)
- rsSyncSvc.exe (PID: 4676)
- rsSyncSvc.exe (PID: 6216)
- identity_helper.exe (PID: 7184)
- winrar-64-7.01-installer_di-Kgo1.exe (PID: 3128)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.exe (PID: 8152)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- winrar-64-6.21-installer_AmGAP-1.exe (PID: 2828)
- saBSI.exe (PID: 7416)
- winrar-64-7.01-installer.exe (PID: 7228)
- Uninstall.exe (PID: 5884)
- identity_helper.exe (PID: 6420)
- rsWSC.exe (PID: 7656)
- installer.exe (PID: 6776)
- installer.exe (PID: 6684)
- rsWSC.exe (PID: 6276)
- rsEngineSvc.exe (PID: 6732)
- rsEngineSvc.exe (PID: 6804)
- rsClientSvc.exe (PID: 6528)
- rsClientSvc.exe (PID: 6580)
- rsHelper.exe (PID: 5332)
- rsEDRSvc.exe (PID: 6360)
- rsEDRSvc.exe (PID: 6172)
- EPP.exe (PID: 6256)
- rsAppUI.exe (PID: 2104)
- rsAppUI.exe (PID: 5316)
- rsAppUI.exe (PID: 3680)
- rsAppUI.exe (PID: 4988)
- rsLitmus.A.exe (PID: 6820)
- rsAppUI.exe (PID: 7068)
- rsAppUI.exe (PID: 5816)
- rsAppUI.exe (PID: 3884)
- servicehost.exe (PID: 7720)
- rsAppUI.exe (PID: 2652)
- rsAppUI.exe (PID: 7072)
- uihost.exe (PID: 3596)
- updater.exe (PID: 8464)
- rsAppUI.exe (PID: 9028)
- rsAppUI.exe (PID: 9100)
- rsAppUI.exe (PID: 8792)
- rsAppUI.exe (PID: 8852)
- rsAppUI.exe (PID: 8900)
- rsAppUI.exe (PID: 8976)
- rsAppUI.exe (PID: 9208)
Process checks computer location settings
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 3848)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- winrar-64-7.01-installer.exe (PID: 7228)
- rsAppUI.exe (PID: 2104)
- rsAppUI.exe (PID: 3680)
- rsAppUI.exe (PID: 4988)
- rsAppUI.exe (PID: 3884)
- rsAppUI.exe (PID: 7068)
- rsAppUI.exe (PID: 2652)
- rsAppUI.exe (PID: 7072)
- servicehost.exe (PID: 7720)
- rsAppUI.exe (PID: 8792)
- rsAppUI.exe (PID: 8852)
- rsAppUI.exe (PID: 8900)
- rsAppUI.exe (PID: 8976)
- rsAppUI.exe (PID: 9028)
- rsAppUI.exe (PID: 9100)
- rsAppUI.exe (PID: 9208)
Reads the computer name
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 3848)
- component0.exe (PID: 420)
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- UnifiedStub-installer.exe (PID: 1280)
- rsSyncSvc.exe (PID: 4676)
- rsSyncSvc.exe (PID: 6216)
- identity_helper.exe (PID: 7184)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- winrar-64-7.01-installer.exe (PID: 7228)
- saBSI.exe (PID: 7416)
- Uninstall.exe (PID: 5884)
- identity_helper.exe (PID: 6420)
- rsWSC.exe (PID: 7656)
- installer.exe (PID: 6776)
- rsWSC.exe (PID: 6276)
- rsEngineSvc.exe (PID: 6732)
- rsClientSvc.exe (PID: 6580)
- rsEngineSvc.exe (PID: 6804)
- rsClientSvc.exe (PID: 6528)
- rsEDRSvc.exe (PID: 6360)
- rsHelper.exe (PID: 5332)
- rsEDRSvc.exe (PID: 6172)
- rsAppUI.exe (PID: 2104)
- rsAppUI.exe (PID: 5316)
- rsAppUI.exe (PID: 5816)
- servicehost.exe (PID: 7720)
- uihost.exe (PID: 3596)
- updater.exe (PID: 8464)
Reads the machine GUID from the registry
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- UnifiedStub-installer.exe (PID: 1280)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- saBSI.exe (PID: 7416)
- rsWSC.exe (PID: 7656)
- installer.exe (PID: 6776)
- rsWSC.exe (PID: 6276)
- rsEngineSvc.exe (PID: 6732)
- rsHelper.exe (PID: 5332)
- rsEngineSvc.exe (PID: 6804)
- rsEDRSvc.exe (PID: 6172)
- rsEDRSvc.exe (PID: 6360)
- rsAppUI.exe (PID: 2104)
- servicehost.exe (PID: 7720)
- uihost.exe (PID: 3596)
- updater.exe (PID: 8464)
Checks proxy server information
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- UnifiedStub-installer.exe (PID: 1280)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- winrar-64-7.01-installer.exe (PID: 7228)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- saBSI.exe (PID: 7416)
- WerFault.exe (PID: 540)
- WerFault.exe (PID: 4308)
- rsWSC.exe (PID: 7656)
- rsEngineSvc.exe (PID: 6732)
- rsAppUI.exe (PID: 2104)
Reads the software policy settings
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- component0.exe (PID: 420)
- UnifiedStub-installer.exe (PID: 1280)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 3724)
- winrar-64-7.01-installer_di-Kgo1.tmp (PID: 7188)
- saBSI.exe (PID: 7416)
- WerFault.exe (PID: 4308)
- WerFault.exe (PID: 540)
- rsWSC.exe (PID: 7656)
- installer.exe (PID: 6776)
- rsEngineSvc.exe (PID: 6732)
- rsEngineSvc.exe (PID: 6804)
- rsWSC.exe (PID: 6276)
- rsEDRSvc.exe (PID: 6360)
- rsEDRSvc.exe (PID: 6172)
- servicehost.exe (PID: 7720)
- uihost.exe (PID: 3596)
- updater.exe (PID: 8464)
Reads Environment values
- component0.exe (PID: 420)
- UnifiedStub-installer.exe (PID: 1280)
- rsEngineSvc.exe (PID: 6804)
- rsEDRSvc.exe (PID: 6172)
- rsAppUI.exe (PID: 2104)
- servicehost.exe (PID: 7720)
Disables trace logs
- component0.exe (PID: 420)
- UnifiedStub-installer.exe (PID: 1280)
- rsEngineSvc.exe (PID: 6804)
- rsEDRSvc.exe (PID: 6172)
Application launched itself
- msedge.exe (PID: 2196)
- msedge.exe (PID: 6348)
- msedge.exe (PID: 1540)
Reads Microsoft Office registry keys
- winrar-64-6.21-installer_AmGAP-1.tmp (PID: 4052)
- msedge.exe (PID: 6348)
- msedge.exe (PID: 2196)
- msedge.exe (PID: 1540)
Manual execution by a user
- msedge.exe (PID: 6348)
Creates files in the program directory
- UnifiedStub-installer.exe (PID: 1280)
- saBSI.exe (PID: 7416)
- winrar-64-7.01-installer.exe (PID: 7228)
- Uninstall.exe (PID: 5884)
- rsWSC.exe (PID: 7656)
- installer.exe (PID: 6684)
- installer.exe (PID: 6776)
- rsEngineSvc.exe (PID: 6732)
- rsEngineSvc.exe (PID: 6804)
- rsEDRSvc.exe (PID: 6172)
- rsEDRSvc.exe (PID: 6360)
- servicehost.exe (PID: 7720)
- uihost.exe (PID: 3596)
Drops the executable file immediately after the start
- msedge.exe (PID: 6632)
- msedge.exe (PID: 6348)
The process uses the downloaded file
- msedge.exe (PID: 2344)
- msedge.exe (PID: 6348)
Executable content was dropped or overwritten
- msedge.exe (PID: 6348)
- msedge.exe (PID: 6632)
Process checks Internet Explorer phishing filters
- winrar-64-7.01-installer.exe (PID: 7228)
Creates files or folders in the user directory
- WerFault.exe (PID: 540)
- WerFault.exe (PID: 4308)
- Uninstall.exe (PID: 5884)
- rsWSC.exe (PID: 7656)
- rsEngineSvc.exe (PID: 6732)
- rsAppUI.exe (PID: 2104)
- rsEngineSvc.exe (PID: 6804)
- rsAppUI.exe (PID: 5816)
Reads the time zone
- runonce.exe (PID: 7884)
- rsEDRSvc.exe (PID: 6172)
- rsEngineSvc.exe (PID: 6804)
Reads security settings of Internet Explorer
- runonce.exe (PID: 7884)
Reads product name
- rsEDRSvc.exe (PID: 6172)
- rsAppUI.exe (PID: 2104)
- rsEngineSvc.exe (PID: 6804)
- servicehost.exe (PID: 7720)
Reads CPU info
- rsEDRSvc.exe (PID: 6172)
- rsEngineSvc.exe (PID: 6804)
.NET Reactor protector has been detected
- rsWSC.exe (PID: 6276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:04:14 16:10:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.7.2431.0 |
| ProductVersionNumber: | 8.7.2431.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Capturāl Lmk |
| FileVersion: | 8.7.2431 |
| LegalCopyright: | ©2023 Capturāl Lmk |
| OriginalFileName: | |
| ProductName: | Capturāl Lmk |
| ProductVersion: | 8.7.2431 |
Total processes
302
Monitored processes
153
Malicious processes
27
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | "C:\Users\admin\AppData\Local\Temp\winrar-64-6.21-installer_AmGAP-1.exe" | C:\Users\admin\AppData\Local\Temp\winrar-64-6.21-installer_AmGAP-1.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Capturāl Lmk Exit code: 0 Version: 8.7.2431 Modules
| |||||||||||||||
| 380 | "C:\Users\admin\AppData\Local\Temp\4bxsh541.exe" /silent | C:\Users\admin\AppData\Local\Temp\4bxsh541.exe | component0.exe | ||||||||||||
User: admin Company: ReasonLabs Integrity Level: HIGH Description: ReasonLabs-setup-wizard.exe Exit code: 0 Version: 6.0.1 Modules
| |||||||||||||||
| 420 | "C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\component0.exe" -ip:"dui=bb926e54-e3ca-40fd-ae90-2764341e7792&dit=20240701141638&is_silent=true&oc=ZB_RAV_Cross_Solo_Soft&p=58f9&a=100&b=&se=true" -i | C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\component0.exe | winrar-64-6.21-installer_AmGAP-1.tmp | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: rsStubActivator Exit code: 0 Version: 1.6.1.0 Modules
| |||||||||||||||
| 540 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7188 -s 944 | C:\Windows\SysWOW64\WerFault.exe | winrar-64-7.01-installer_di-Kgo1.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 964 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6156 --field-trial-handle=2256,i,7856325367257210656,12069246961281581977,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1192 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --mojo-platform-channel-handle=8096 --field-trial-handle=2256,i,7856325367257210656,12069246961281581977,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1224 | regsvr32.exe /s "C:\Program Files\McAfee\WebAdvisor\win32\WSSDep.dll" | C:\Windows\System32\regsvr32.exe | — | installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | .\UnifiedStub-installer.exe /silent | C:\Users\admin\AppData\Local\Temp\7zSC71D445B\UnifiedStub-installer.exe | 4bxsh541.exe | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: UnifiedStub Exit code: 0 Version: 6.0.1 Modules
| |||||||||||||||
| 1332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5192 --field-trial-handle=2256,i,7856325367257210656,12069246961281581977,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=5060 --field-trial-handle=2256,i,7856325367257210656,12069246961281581977,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
133 998
Read events
133 072
Write events
831
Delete events
95
Modification events
| (PID) Process: | (4052) winrar-64-6.21-installer_AmGAP-1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: D40F000031F94546C1CBDA01 | |||
| (PID) Process: | (4052) winrar-64-6.21-installer_AmGAP-1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: F8B9C587D7555060D23950343822CCEDEBDBD484A3EE91C2DB0EDFDDEB033009 | |||
| (PID) Process: | (4052) winrar-64-6.21-installer_AmGAP-1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (4052) winrar-64-6.21-installer_AmGAP-1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4052) winrar-64-6.21-installer_AmGAP-1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4052) winrar-64-6.21-installer_AmGAP-1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4052) winrar-64-6.21-installer_AmGAP-1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (420) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (420) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (420) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
563
Suspicious files
860
Text files
1 114
Unknown types
74
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2828 | winrar-64-6.21-installer_AmGAP-1.exe | C:\Users\admin\AppData\Local\Temp\is-520Q2.tmp\winrar-64-6.21-installer_AmGAP-1.tmp | executable | |
MD5:2C3299A97AAF7B14C4BC0145186A5851 | SHA256:CA7D4BF7EA7E7A1F3EA77B885E3402D1040AD4473DB3279F59376E52A980CBA2 | |||
| 4052 | winrar-64-6.21-installer_AmGAP-1.tmp | C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 4052 | winrar-64-6.21-installer_AmGAP-1.tmp | C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4052 | winrar-64-6.21-installer_AmGAP-1.tmp | C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\is-IMBKN.tmp | html | |
MD5:9A8D73B7A1D5A6DDBFB78F52096C1486 | SHA256:75D4931C6051E27799926FF815D6A95D761FE6D05683FBC2D05EDFFAE0DE56D9 | |||
| 4052 | winrar-64-6.21-installer_AmGAP-1.tmp | C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\winrar-64-6.21-installer.exe | html | |
MD5:9A8D73B7A1D5A6DDBFB78F52096C1486 | SHA256:75D4931C6051E27799926FF815D6A95D761FE6D05683FBC2D05EDFFAE0DE56D9 | |||
| 4052 | winrar-64-6.21-installer_AmGAP-1.tmp | C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\component0.exe | executable | |
MD5:4F09061B0024B67C673377CFD336E2BB | SHA256:2FBC1D7320F0896BD21D241D493AB3077D7709380BA1806F239AD477D1FDF30F | |||
| 244 | winrar-64-6.21-installer_AmGAP-1.exe | C:\Users\admin\AppData\Local\Temp\is-UF099.tmp\winrar-64-6.21-installer_AmGAP-1.tmp | executable | |
MD5:2C3299A97AAF7B14C4BC0145186A5851 | SHA256:CA7D4BF7EA7E7A1F3EA77B885E3402D1040AD4473DB3279F59376E52A980CBA2 | |||
| 4052 | winrar-64-6.21-installer_AmGAP-1.tmp | C:\Users\admin\Downloads\winrar-64-6.21-installer.exe | html | |
MD5:9A8D73B7A1D5A6DDBFB78F52096C1486 | SHA256:75D4931C6051E27799926FF815D6A95D761FE6D05683FBC2D05EDFFAE0DE56D9 | |||
| 4052 | winrar-64-6.21-installer_AmGAP-1.tmp | C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\RAV_Cross.png | image | |
MD5:4167C79312B27C8002CBEEA023FE8CB5 | SHA256:C3BF350627B842BED55E6A72AB53DA15719B4F33C267A6A132CB99FF6AFE3CD8 | |||
| 4052 | winrar-64-6.21-installer_AmGAP-1.tmp | C:\Users\admin\AppData\Local\Temp\is-NU2PR.tmp\is-4P0FP.tmp | image | |
MD5:4167C79312B27C8002CBEEA023FE8CB5 | SHA256:C3BF350627B842BED55E6A72AB53DA15719B4F33C267A6A132CB99FF6AFE3CD8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
74
TCP/UDP connections
598
DNS requests
391
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3800 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3800 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
2064 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
2064 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
5996 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6348 | msedge.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | unknown |
5080 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3800 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6072 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1320 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4052 | winrar-64-6.21-installer_AmGAP-1.tmp | 108.139.241.9:443 | d1voknowivy5w4.cloudfront.net | AMAZON-02 | US | unknown |
3800 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
3800 | svchost.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 104.46.162.227:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | AU | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d1voknowivy5w4.cloudfront.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
r.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6632 | msedge.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
5816 | rsAppUI.exe | Potential Corporate Privacy Violation | AV POLICY Observed TikTok Domain in TLS SNI (tiktok.com) |
5816 | rsAppUI.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
5816 | rsAppUI.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
5816 | rsAppUI.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
5816 | rsAppUI.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5816 | rsAppUI.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
Process | Message |
|---|---|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-0EVHS.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-0EVHS.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-0EVHS.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-0EVHS.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-0EVHS.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-0EVHS.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|