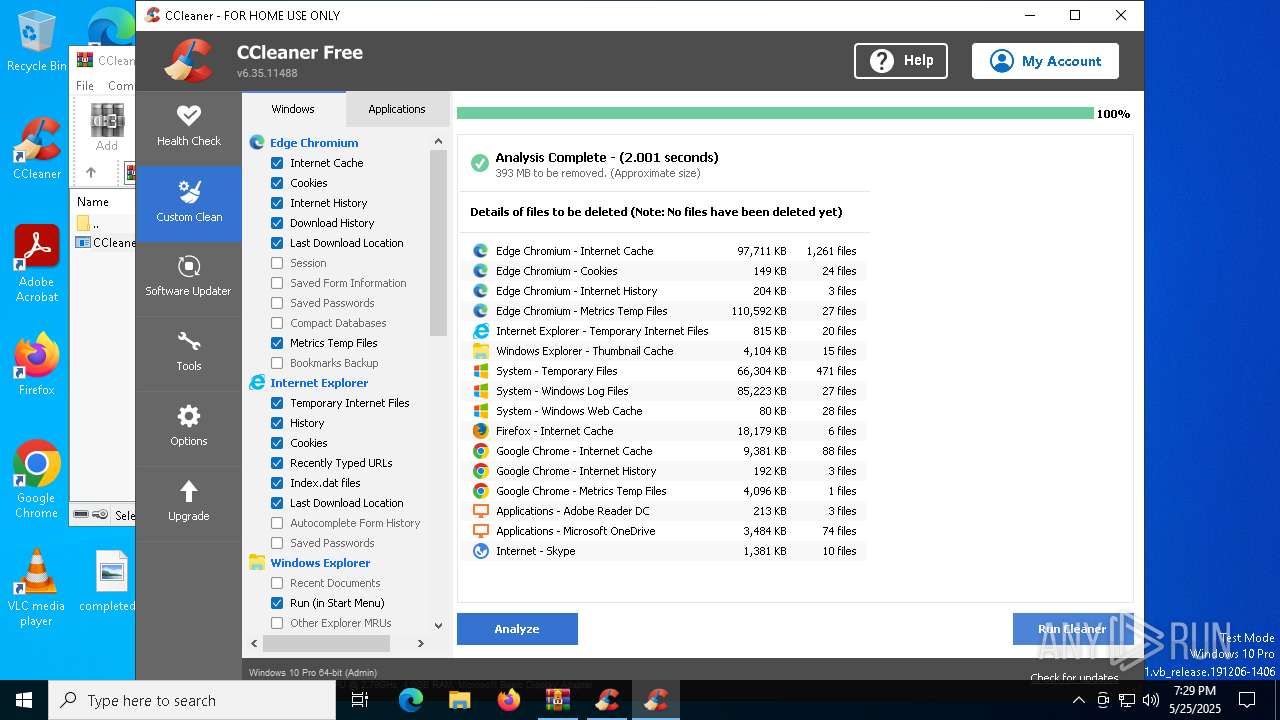
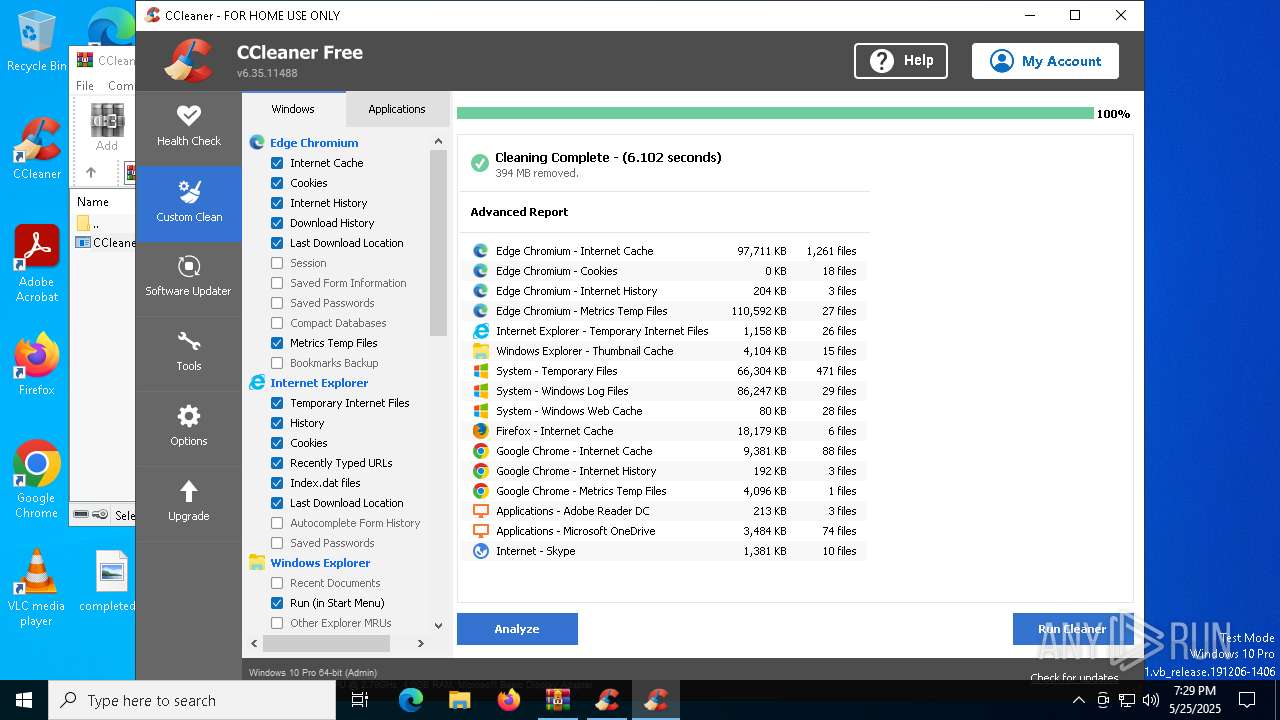
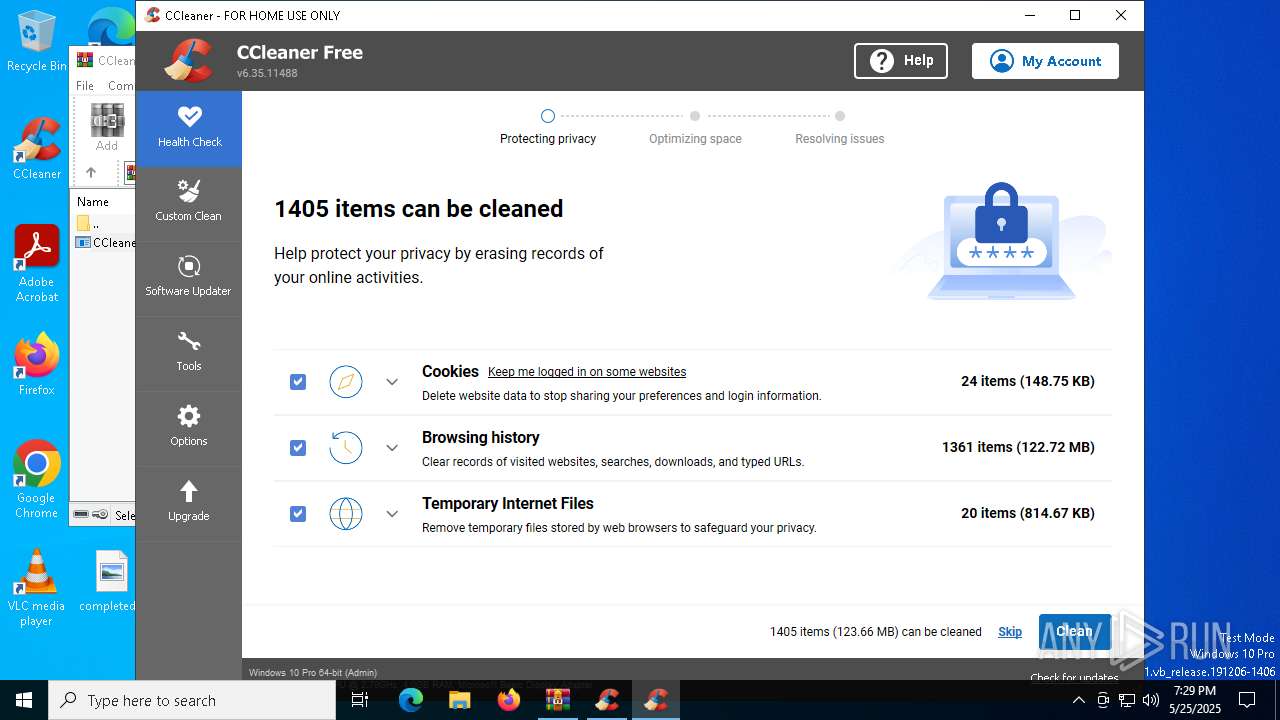
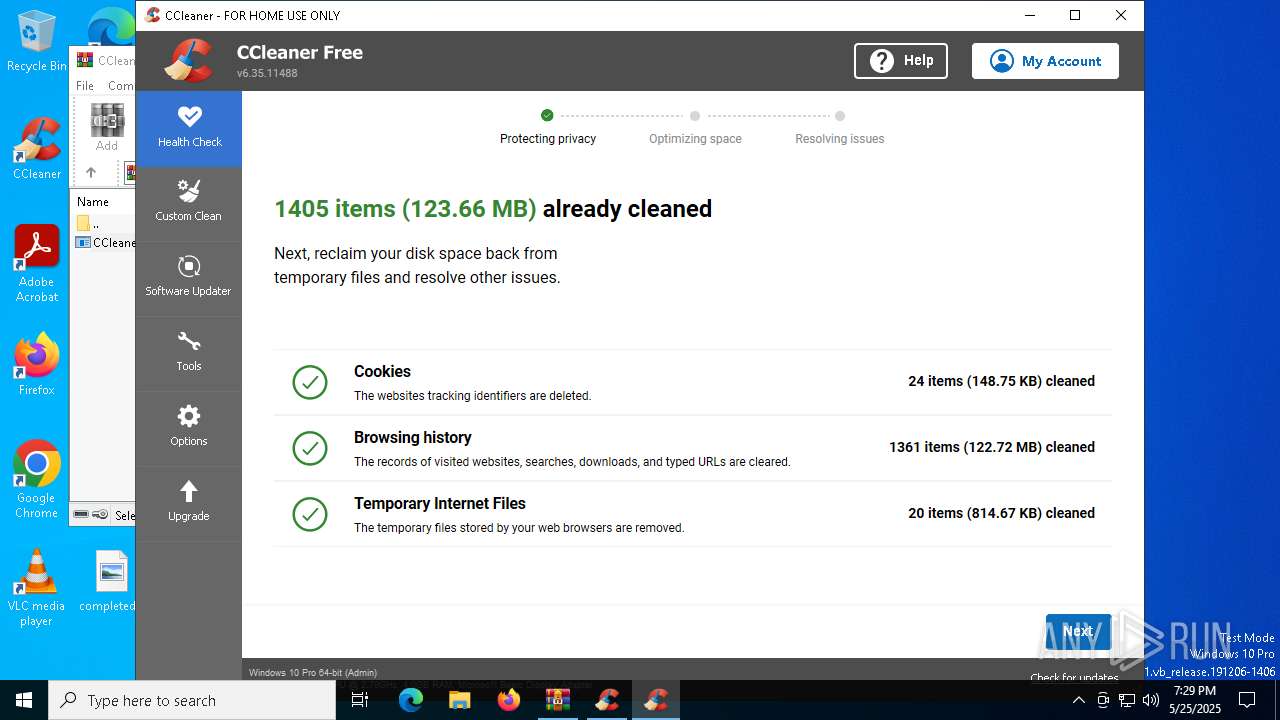
| File name: | CCleaner.7z |
| Full analysis: | https://app.any.run/tasks/933bedf5-fb28-4850-b9f7-b08022c536d9 |
| Verdict: | Malicious activity |
| Threats: | PrivateLoader is a malware family that is specifically created to infect computer systems and drop additional malicious programs. It operates using a pay-per-install business model, which means that the individuals behind it are paid for each instance of successful deployment of different types of harmful programs, including trojans, stealers, and other ransomware. |
| Analysis date: | May 25, 2025, 19:28:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 8D2413B374B933D2B80F542E08C4238D |
| SHA1: | 82F07FC1F2B32F42D6865679DE0E0C366C68293F |
| SHA256: | F81294FED725868329940B5FBDD29960E7B3EAD7E90F9005DE5F6E1FA2CC3241 |
| SSDEEP: | 98304:MLss3n2Lsx9E40Op7DWmPRJYCtdQckEOj8Ah3HqZuTcoSGmwmNdl6Tgrj+PP/NBD:21bPTD8wluDPN0f/T5AtGHmH |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2432)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 7804)
PRIVATELOADER has been detected (YARA)
- CCleaner.exe (PID: 7804)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2432)
- CCleaner.exe (PID: 7660)
- CCleaner.exe (PID: 7592)
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Application launched itself
- CCleaner.exe (PID: 7592)
- CCleaner.exe (PID: 7660)
Reads Internet Explorer settings
- CCleaner.exe (PID: 7876)
- CCleaner.exe (PID: 7804)
Executable content was dropped or overwritten
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Searches for installed software
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Checks for external IP
- CCleaner.exe (PID: 7876)
- CCleaner.exe (PID: 7804)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 7804)
The process checks if it is being run in the virtual environment
- CCleaner.exe (PID: 7804)
The process verifies whether the antivirus software is installed
- CCleaner.exe (PID: 7804)
Starts application from unusual location
- CCleaner.exe (PID: 7804)
INFO
Checks supported languages
- CCleaner.exe (PID: 7592)
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
- CCleaner.exe (PID: 7660)
Process checks computer location settings
- CCleaner.exe (PID: 7592)
- CCleaner.exe (PID: 7660)
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Reads the computer name
- CCleaner.exe (PID: 7660)
- CCleaner.exe (PID: 7592)
- CCleaner.exe (PID: 7876)
- CCleaner.exe (PID: 7804)
Reads Environment values
- CCleaner.exe (PID: 7592)
- CCleaner.exe (PID: 7660)
- CCleaner.exe (PID: 7876)
- CCleaner.exe (PID: 7804)
Checks proxy server information
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Reads the machine GUID from the registry
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Create files in a temporary directory
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Reads CPU info
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
The sample compiled with english language support
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Reads product name
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Reads the software policy settings
- CCleaner.exe (PID: 7876)
- CCleaner.exe (PID: 7804)
Creates files or folders in the user directory
- CCleaner.exe (PID: 7804)
- CCleaner.exe (PID: 7876)
Reads Microsoft Office registry keys
- CCleaner.exe (PID: 7804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:04:09 10:05:08+00:00 |
| ArchivedFileName: | CCleaner.exe |
Total processes
142
Monitored processes
7
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2432 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\CCleaner.7z | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7276 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7308 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7592 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14105\CCleaner.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14105\CCleaner.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.35.0.11488 Modules
| |||||||||||||||
| 7660 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14341\CCleaner.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14341\CCleaner.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.35.0.11488 Modules
| |||||||||||||||
| 7804 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14105\CCleaner.exe" /uac | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14105\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: CCleaner Version: 6.35.0.11488 Modules
| |||||||||||||||
| 7876 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14341\CCleaner.exe" /uac | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14341\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: CCleaner Version: 6.35.0.11488 Modules
| |||||||||||||||
Total events
24 265
Read events
23 890
Write events
207
Delete events
168
Modification events
| (PID) Process: | (2432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CCleaner.7z | |||
| (PID) Process: | (2432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7804) CCleaner.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | DAST |
Value: 05/25/2025 19:28:56 | |||
| (PID) Process: | (7804) CCleaner.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | UpdateBackground |
Value: 1 | |||
Executable files
7
Suspicious files
189
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14105\CCleaner.exe | — | |
MD5:— | SHA256:— | |||
| 2432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14341\CCleaner.exe | — | |
MD5:— | SHA256:— | |||
| 7876 | CCleaner.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14341\Setup\config.def | text | |
MD5:05927E894C81EB42C3B4DAE5A5A6C937 | SHA256:09C65B39BC891E12956AB7BB30FAE147EF7C8FA37542B6F040613436B566E7F8 | |||
| 7876 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\80f95e07734d4c3f.customDestinations-ms | binary | |
MD5:A4647879B769E8098819E3D7D2CC894C | SHA256:ED46D6B3058335F0C654A1B4D392BCC4B7B5B5FA54481A630871B5E9C6C45BC5 | |||
| 7876 | CCleaner.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.14341\gcapi_17482013377876.dll | executable | |
MD5:F637D5D3C3A60FDDB5DD397556FE9B1D | SHA256:641B843CB6EE7538EC267212694C9EF0616B9AC9AB14A0ABD7CF020678D50B02 | |||
| 7804 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fcac93a007d0fd4.customDestinations-ms | binary | |
MD5:5203F47FAF052005F554294510911E4E | SHA256:7E078AF2DB5EB2C6EE587FB25301E56A8BDFE658AEE3382F5A3000ADEBF8FABE | |||
| 7876 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IS8EDP30I1YAITXL2WYY.temp | binary | |
MD5:A4647879B769E8098819E3D7D2CC894C | SHA256:ED46D6B3058335F0C654A1B4D392BCC4B7B5B5FA54481A630871B5E9C6C45BC5 | |||
| 7804 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1W9SL6ZZZ3B6GQ04UG9D.temp | binary | |
MD5:5203F47FAF052005F554294510911E4E | SHA256:7E078AF2DB5EB2C6EE587FB25301E56A8BDFE658AEE3382F5A3000ADEBF8FABE | |||
| 7876 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:68C5E32FB9CB959F491342A7CAD5D966 | SHA256:3FCDB7A57C80EE3DB2EAE8D197F5218FEB4D834FA4897590A7D7342ECA599806 | |||
| 7876 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:1DE8723382D25C8EAD924F55E95A217F | SHA256:FE9A0E34EC08D55F16ABD01C05A3C9A393448F9FEEA046DA6EB6FA8957C1B82A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
45
DNS requests
26
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7804 | CCleaner.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
7804 | CCleaner.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
7804 | CCleaner.exe | GET | 200 | 23.50.131.202:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
7804 | CCleaner.exe | GET | 200 | 172.217.18.3:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7876 | CCleaner.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
7876 | CCleaner.exe | GET | 200 | 172.217.18.3:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
7804 | CCleaner.exe | GET | 200 | 172.217.18.3:80 | http://o.pki.goog/s/wr3/BhM/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEAYTImF6xaxMEJAS2j2k4Ng%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1196 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7804 | CCleaner.exe | 23.50.131.202:80 | ncc.avast.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ncc.avast.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
analytics.avcdn.net |
| whitelisted |
shepherd.ff.avast.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
7804 | CCleaner.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
7876 | CCleaner.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |