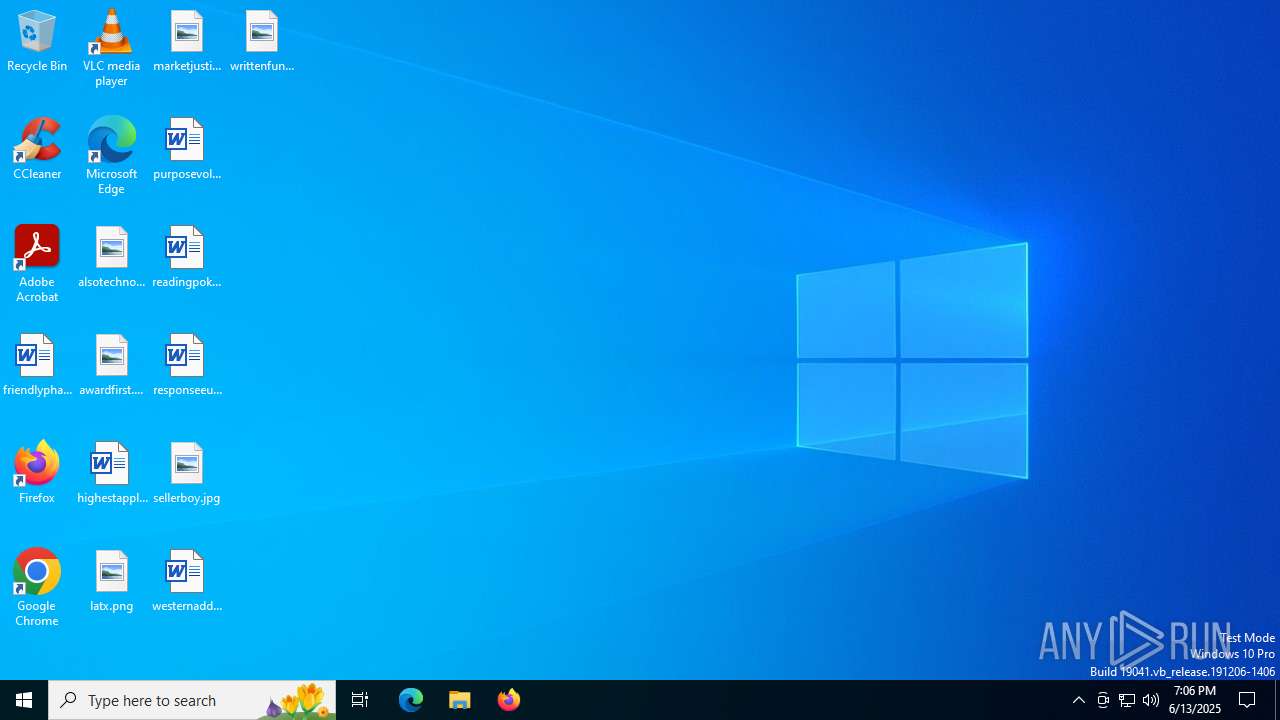
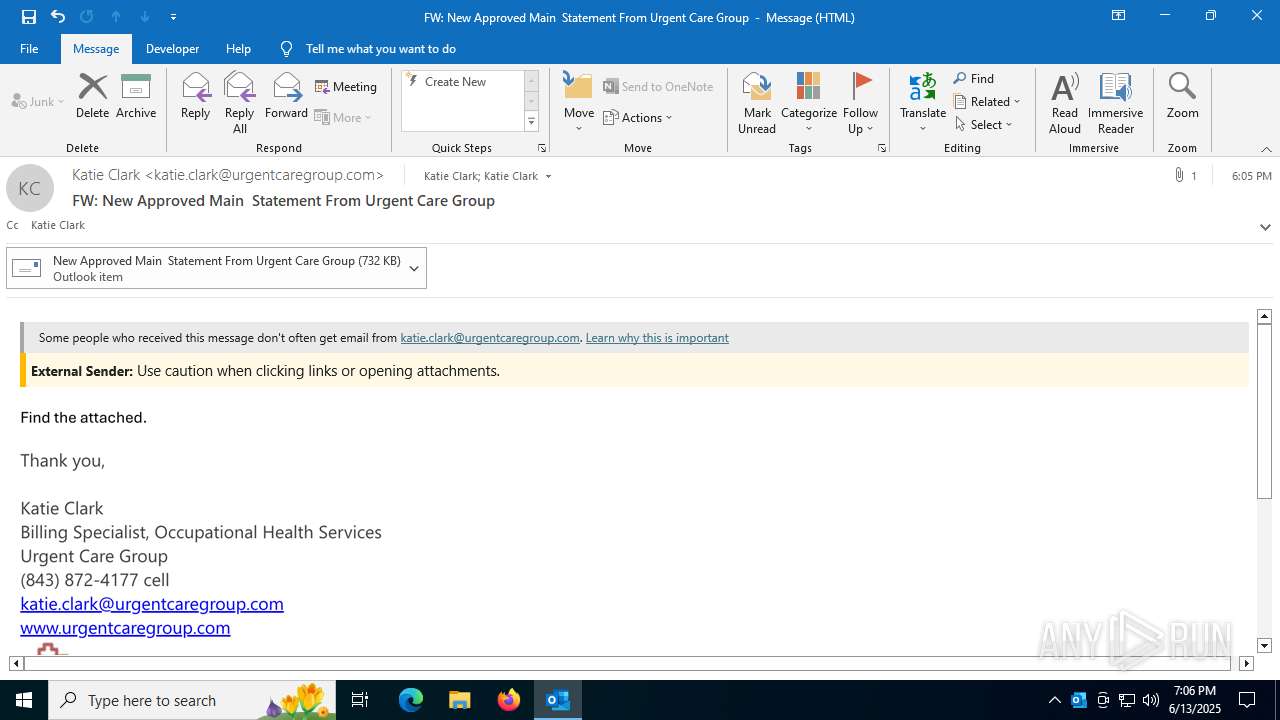
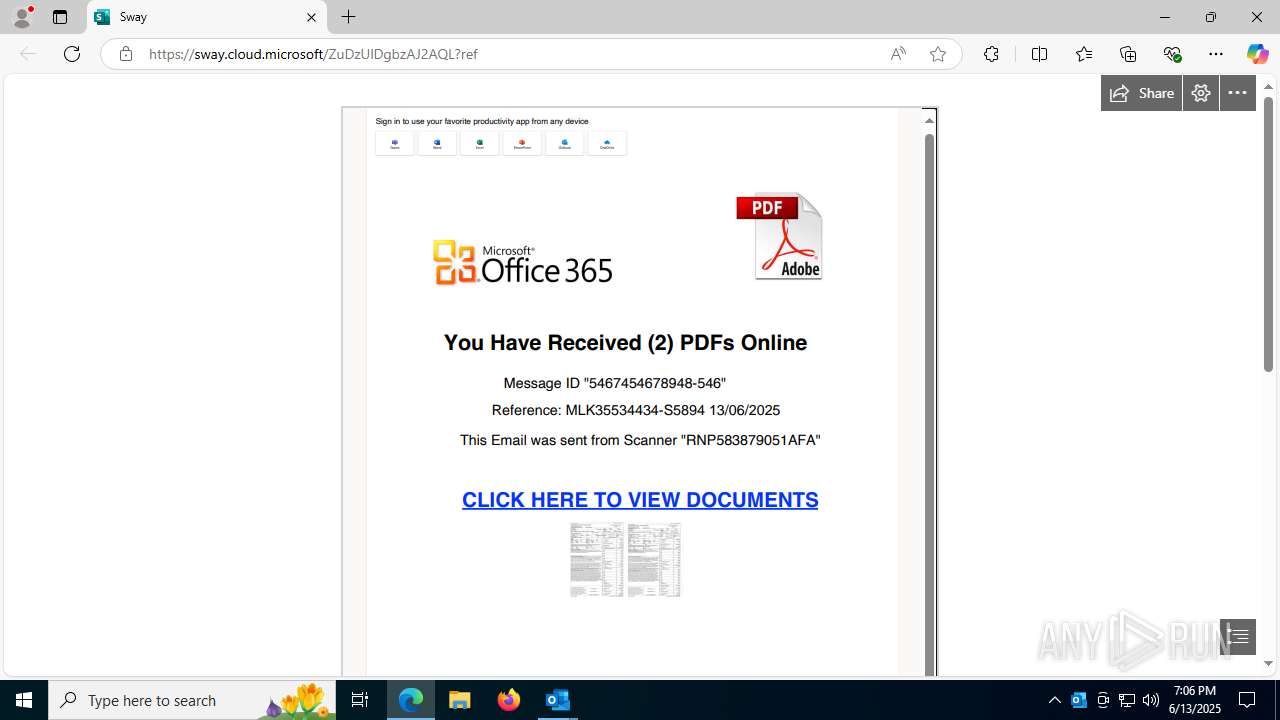
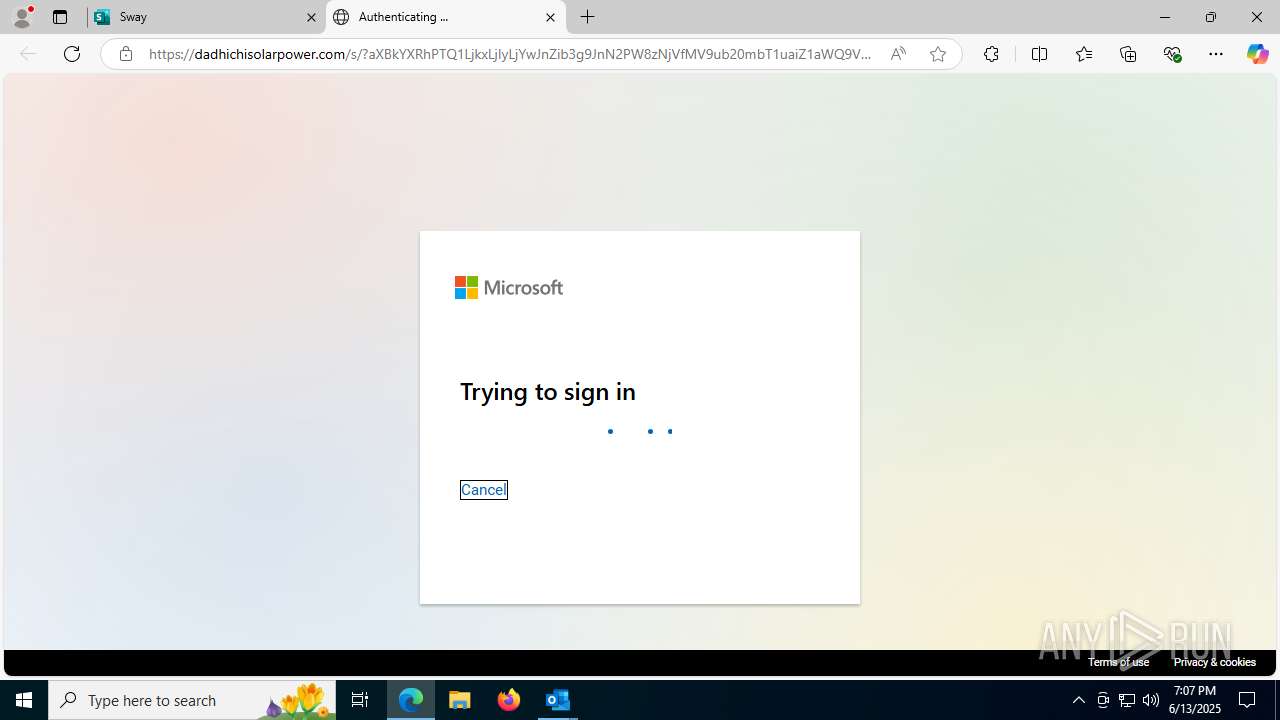
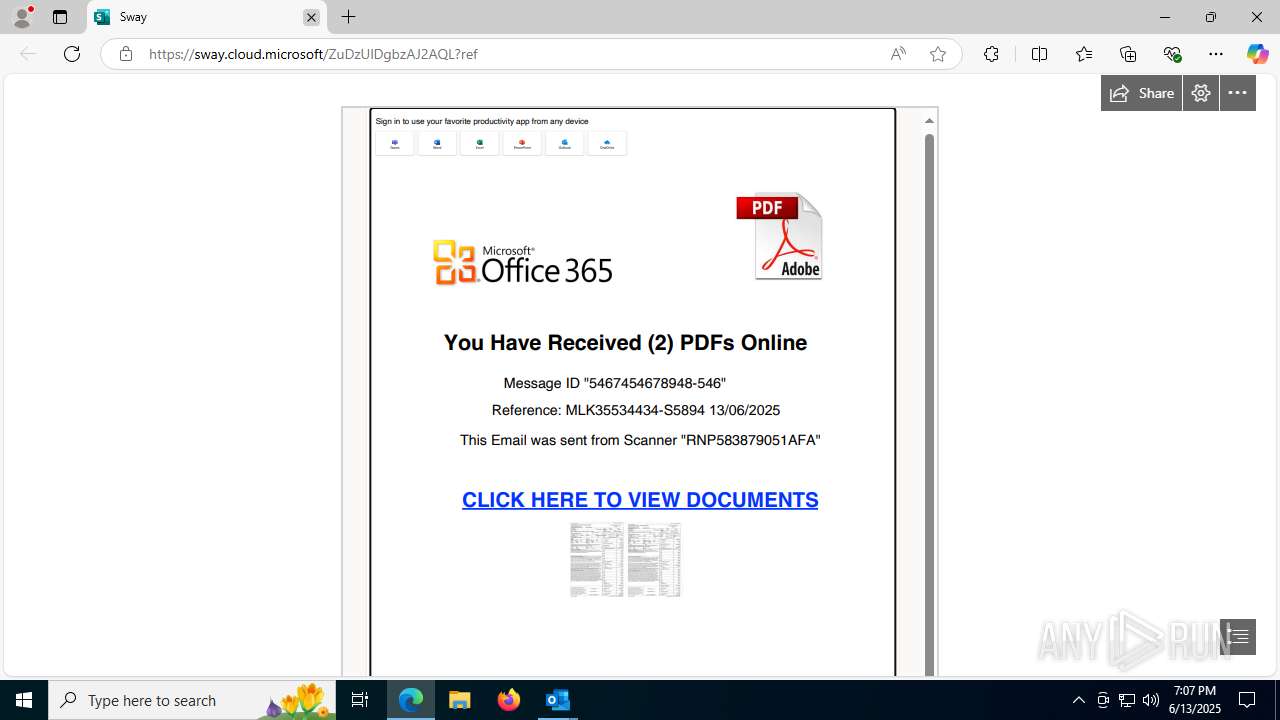
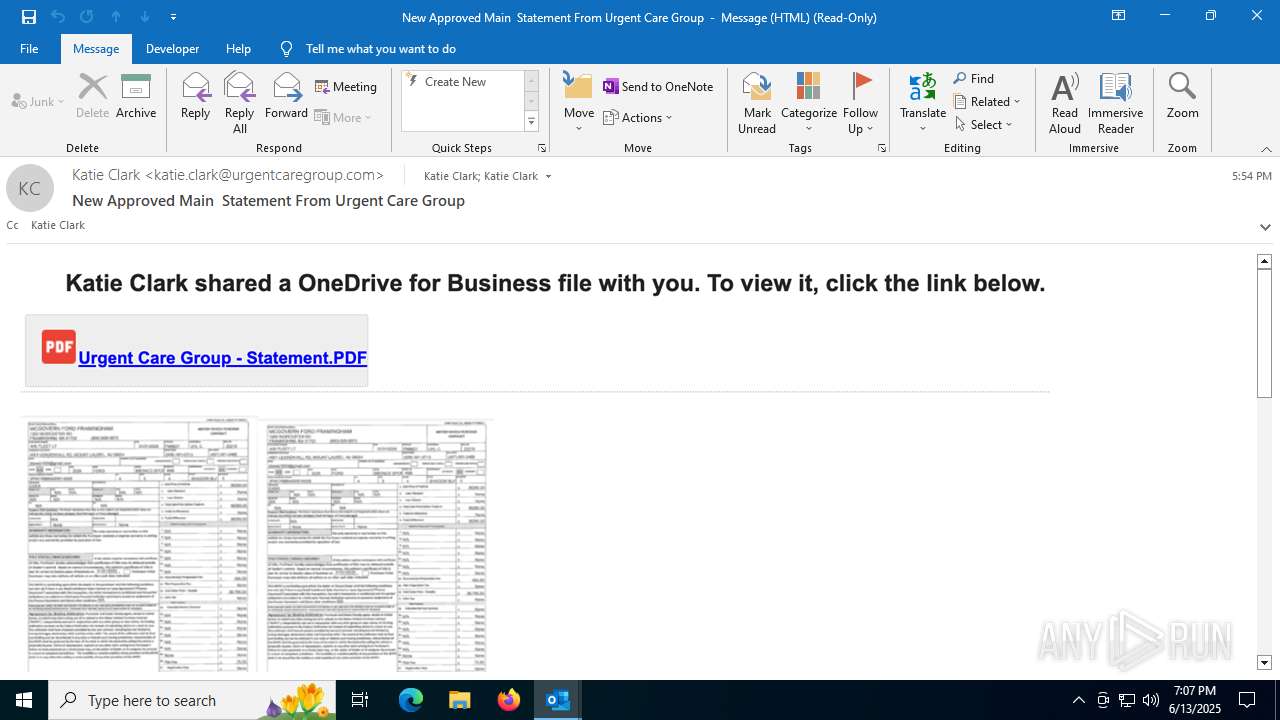
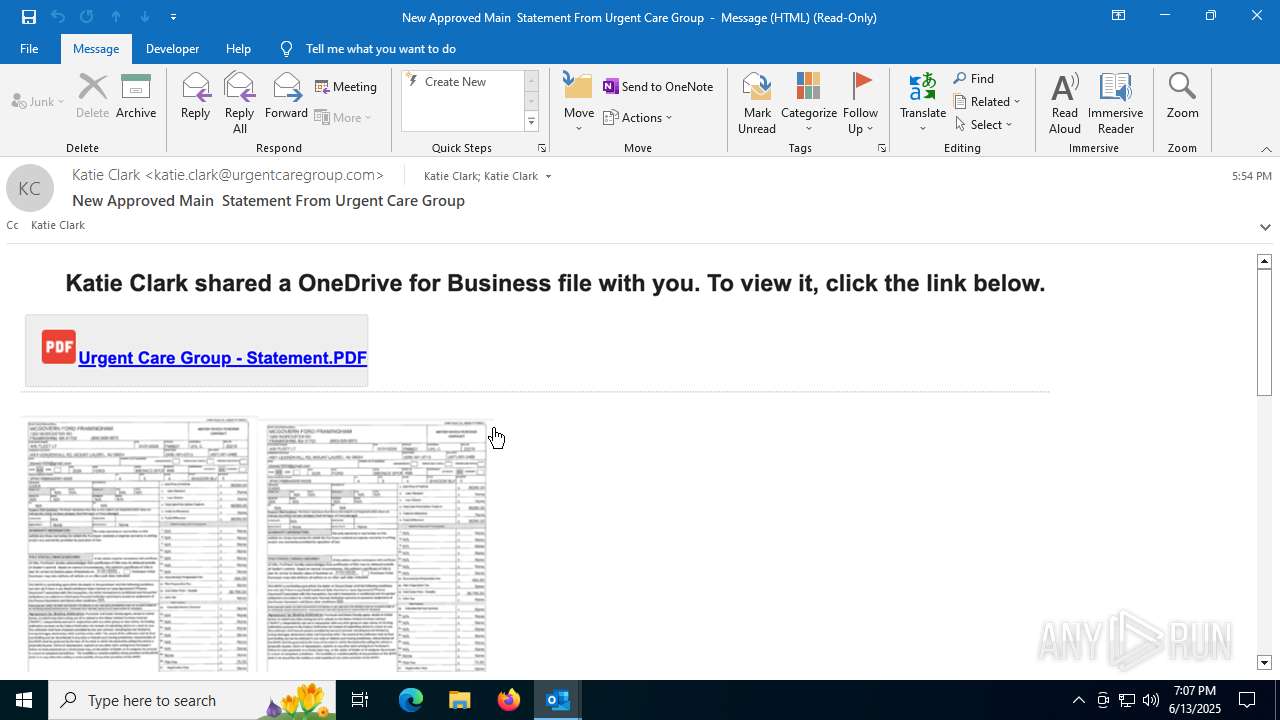
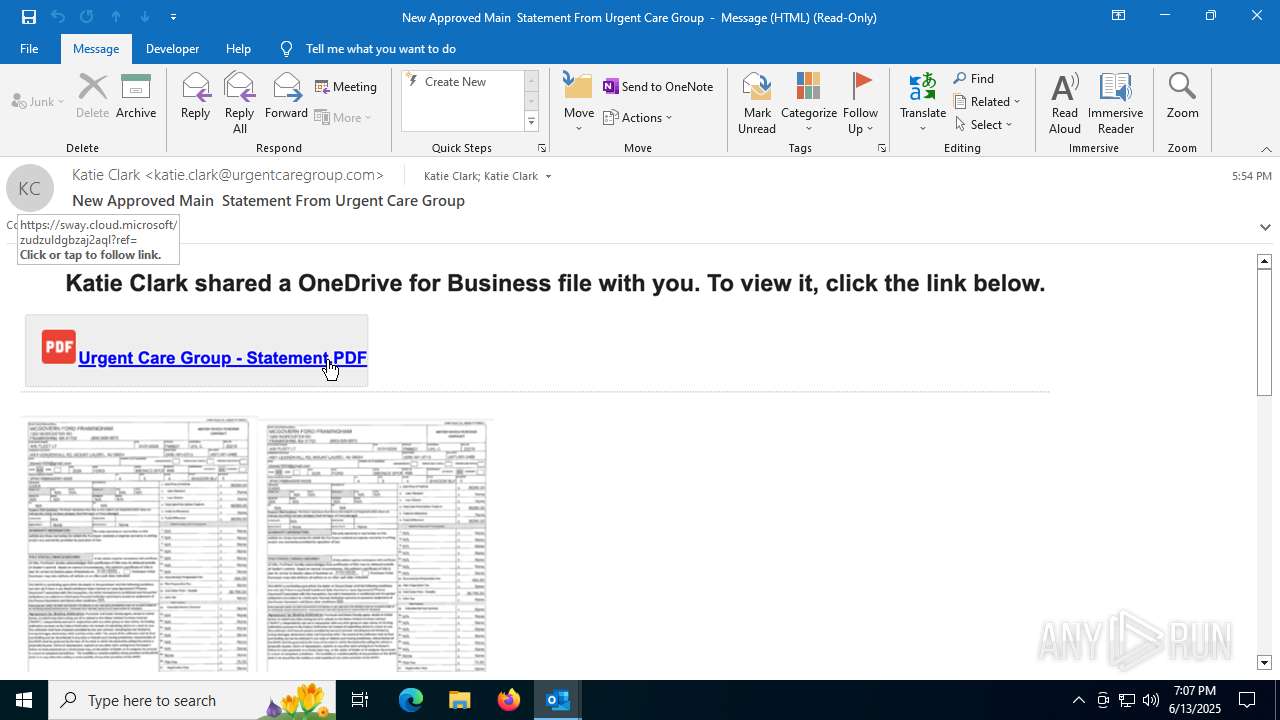
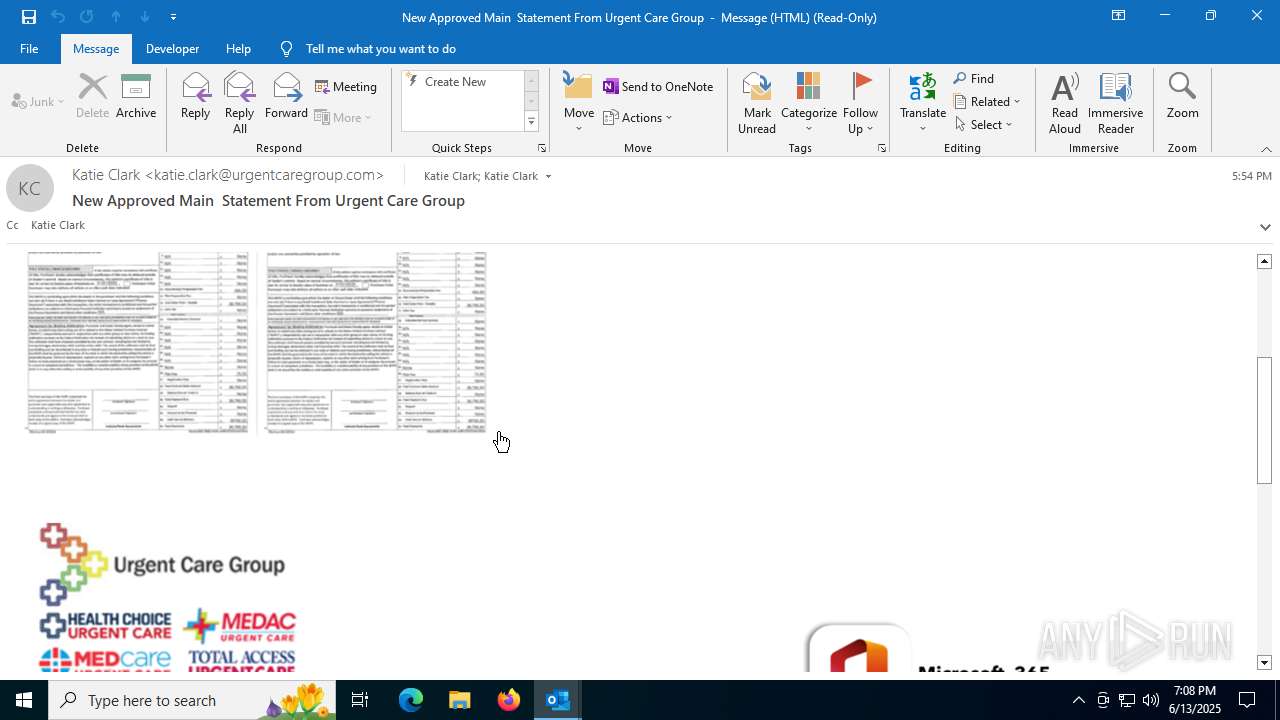
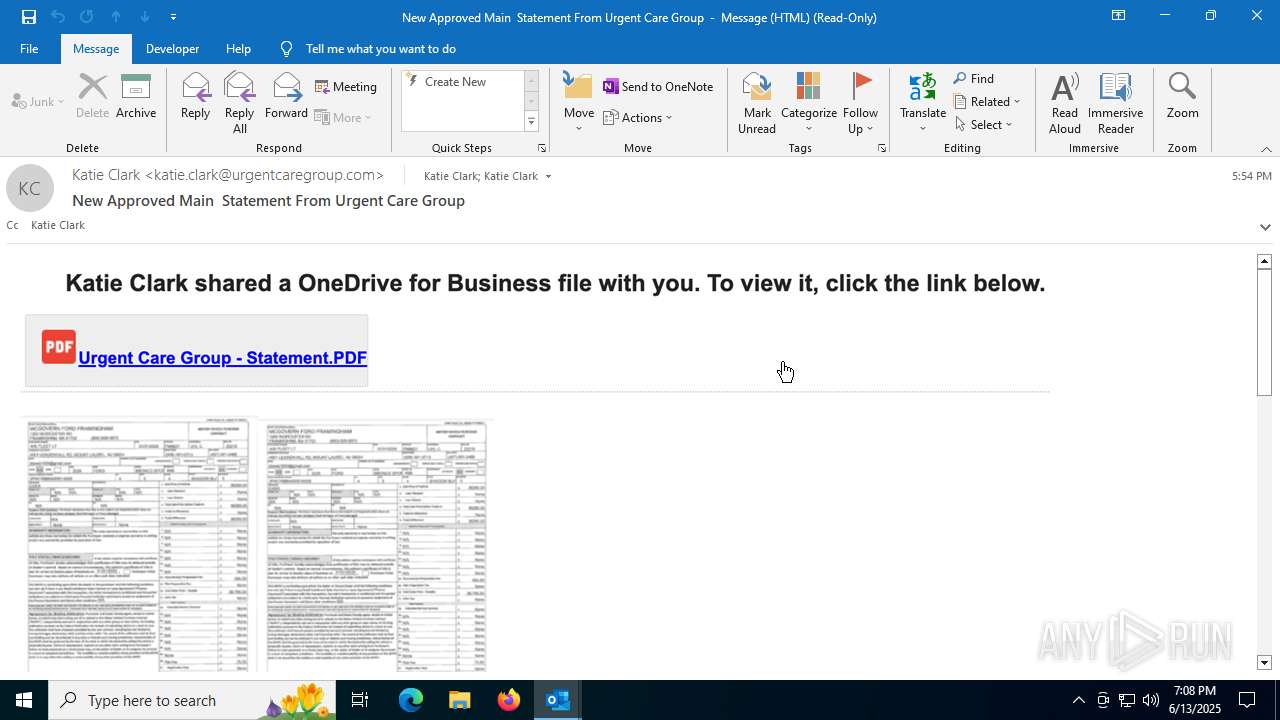
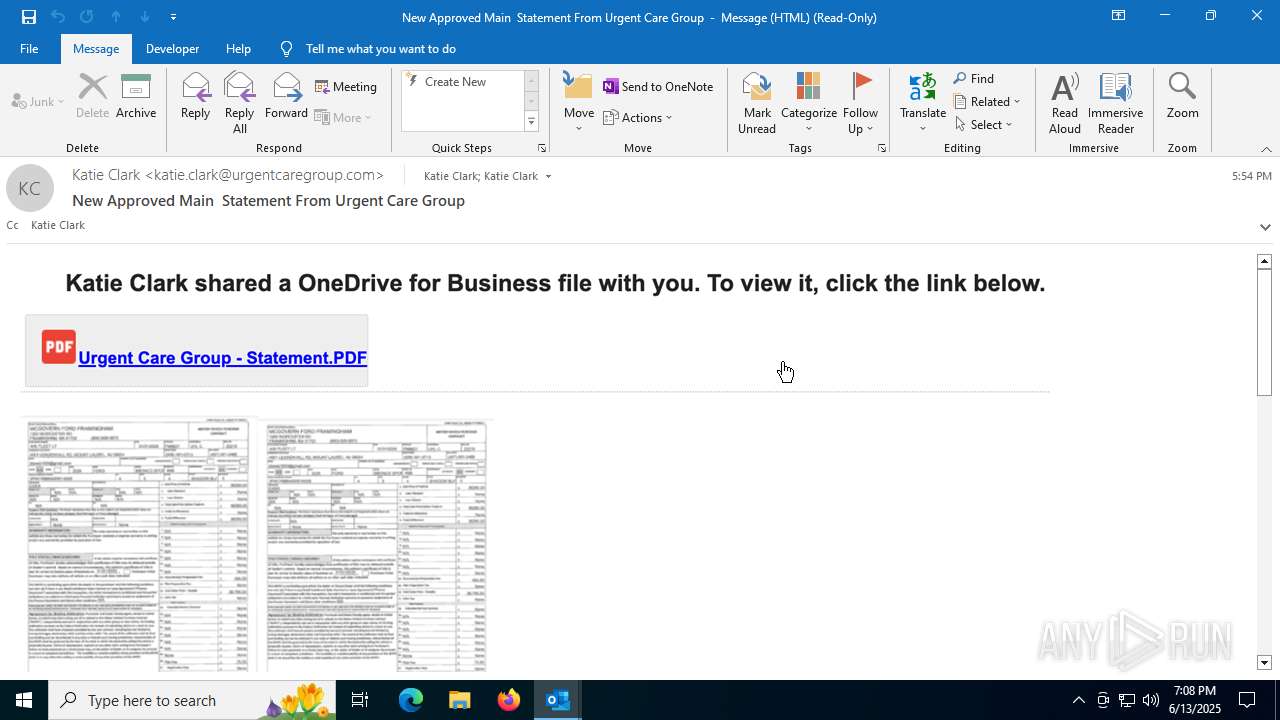
| File name: | a1s-root6=email_banfield_2025_06_13_18_SMTP-att-1-4bJpXr0lbxz6C6hv-2025-06-13T18_57_00.eml.infected |
| Full analysis: | https://app.any.run/tasks/21fb46ee-d4e8-44a8-8d20-63c2c0b5a387 |
| Verdict: | Malicious activity |
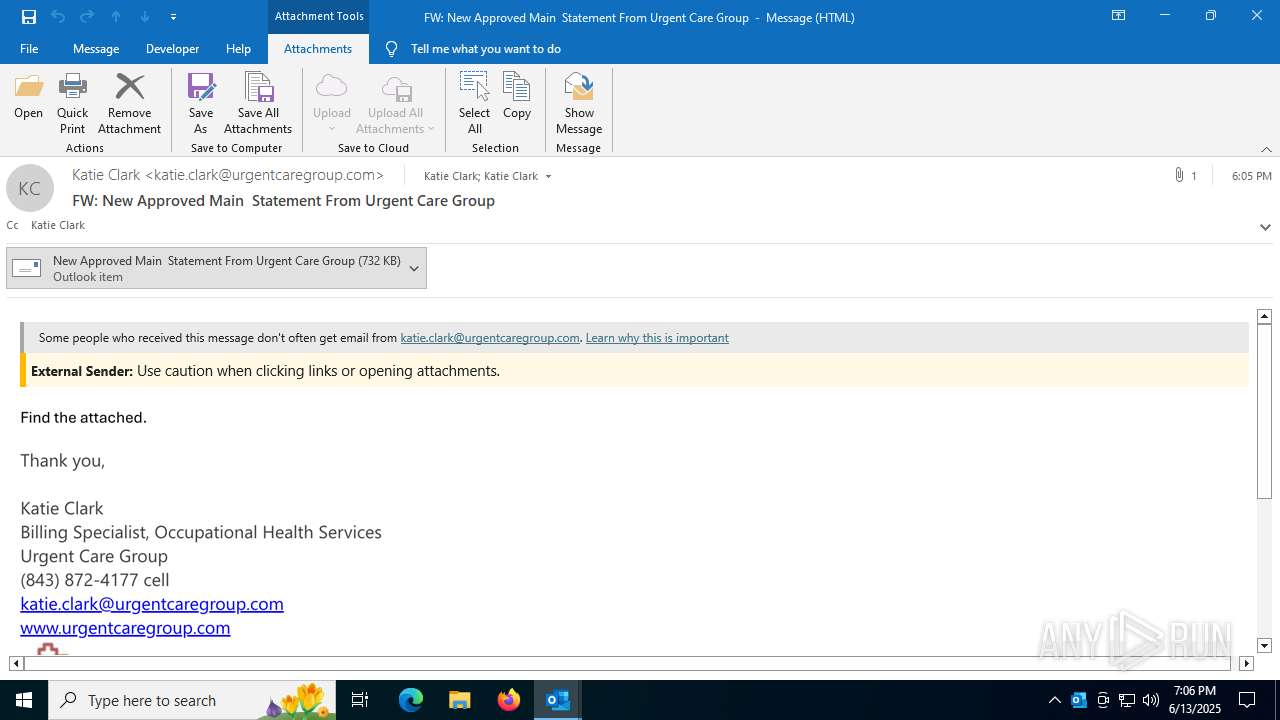
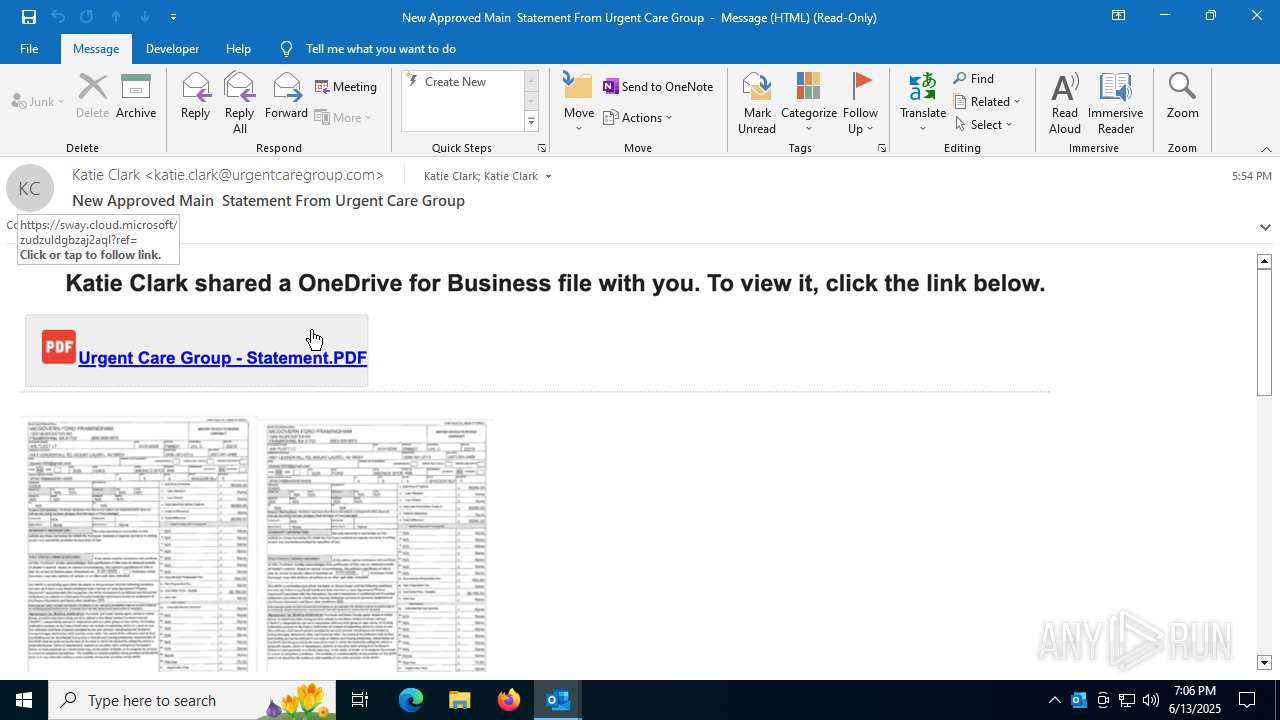
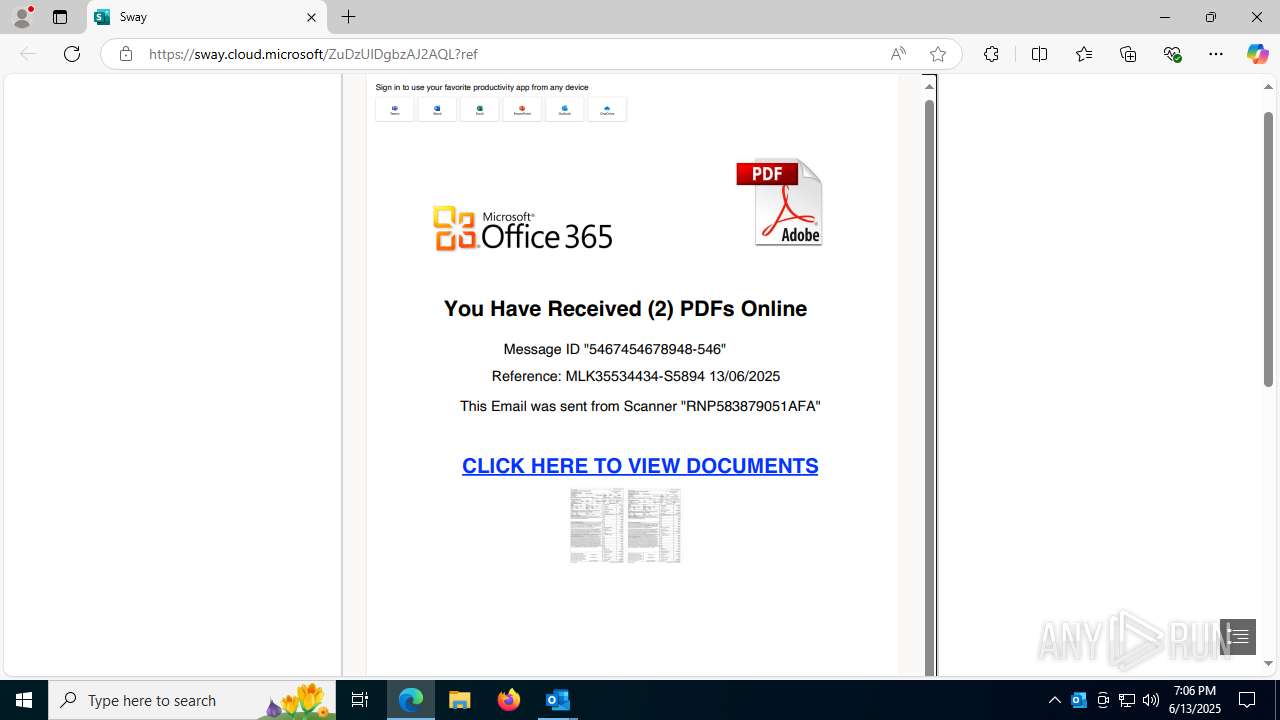
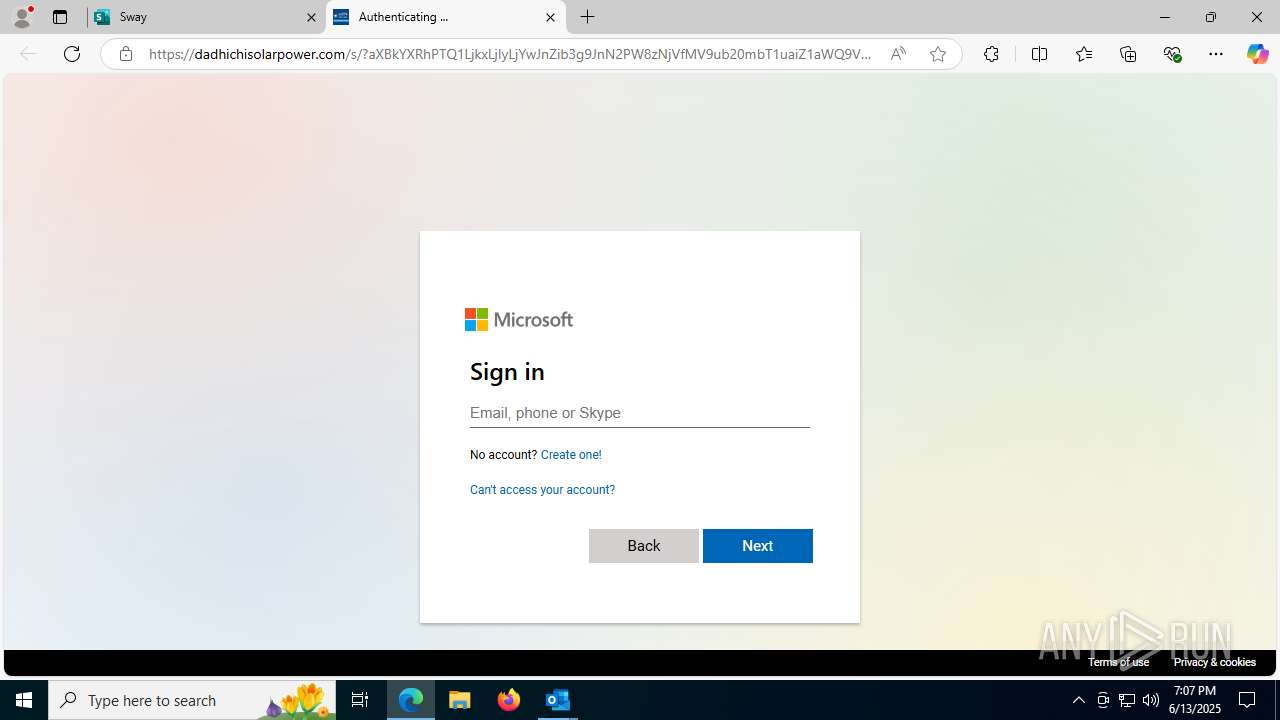
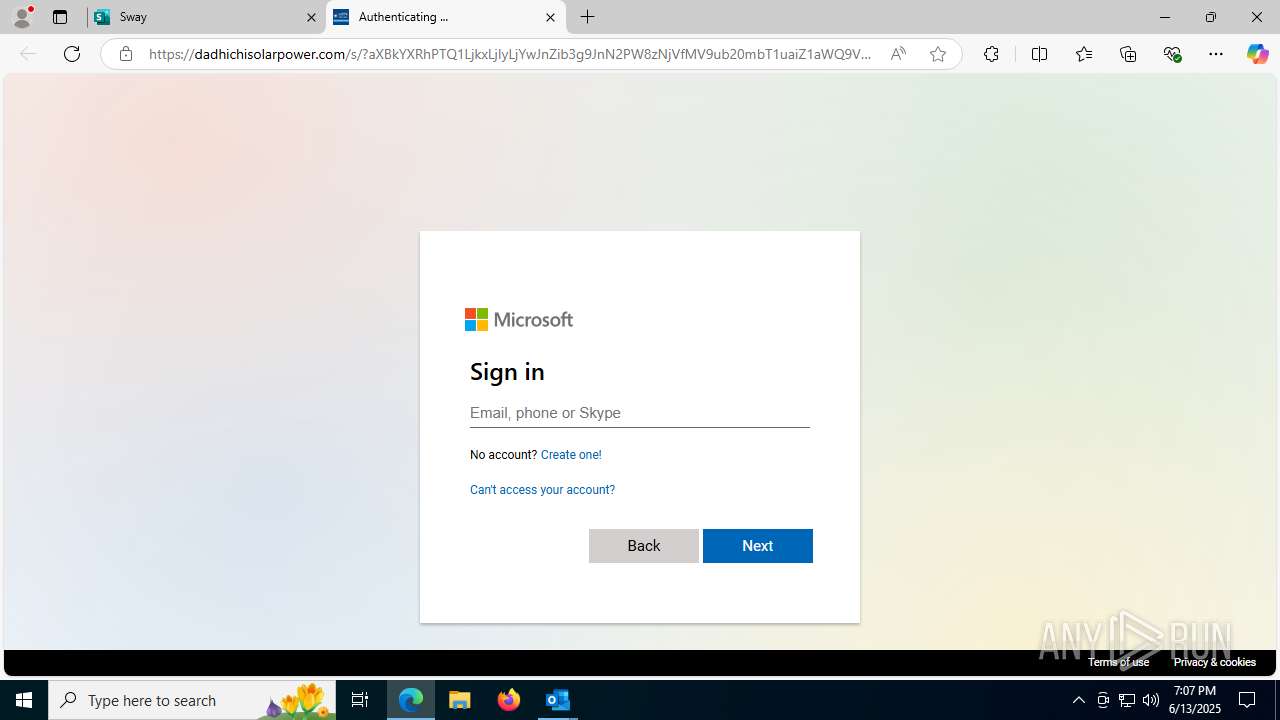
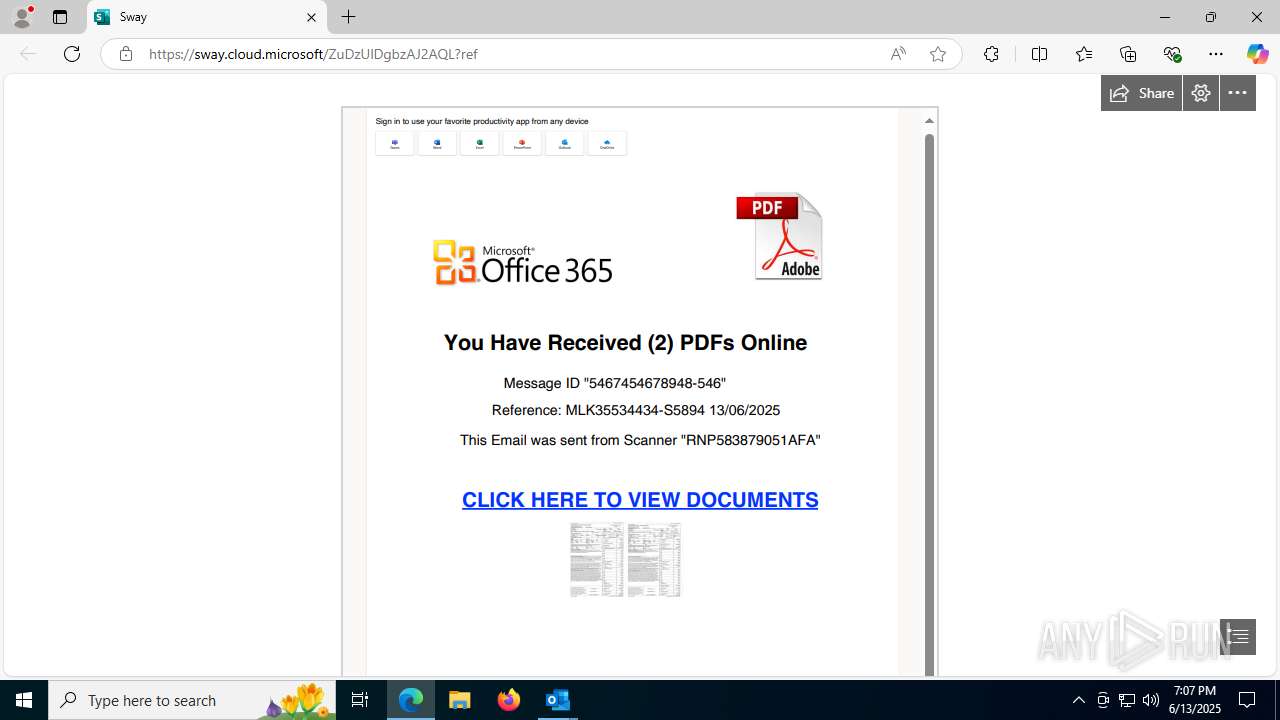
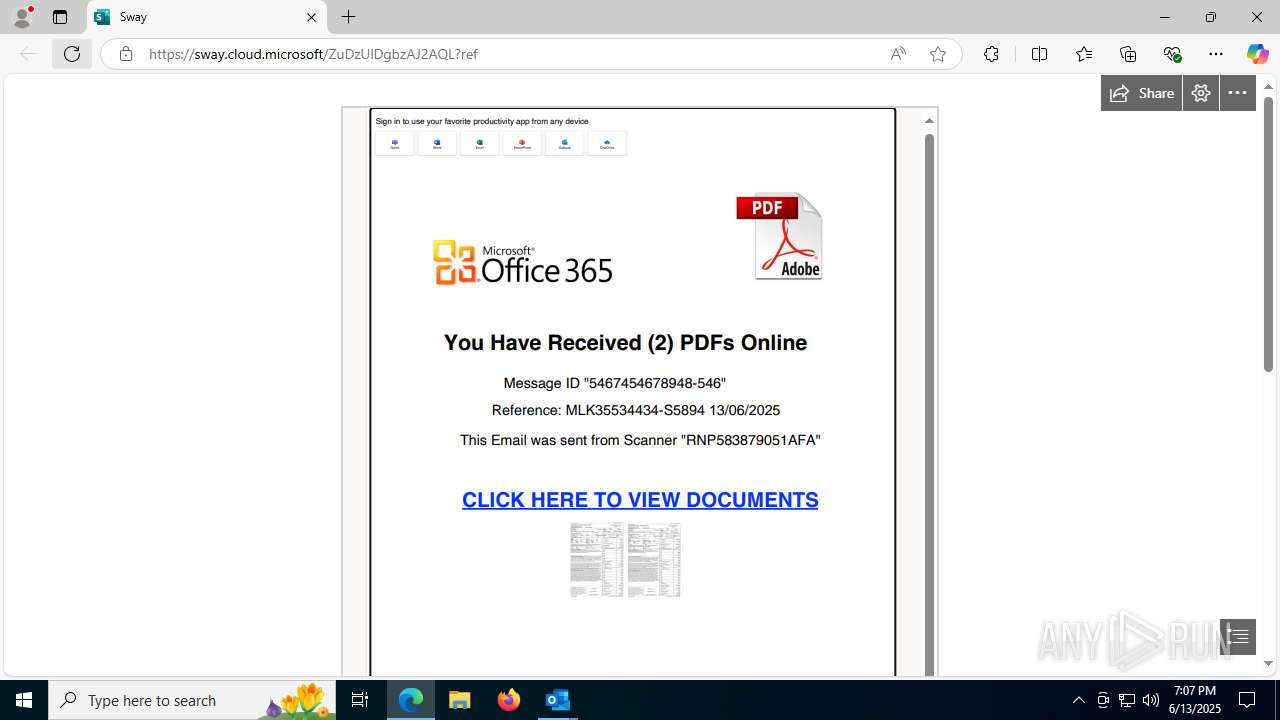
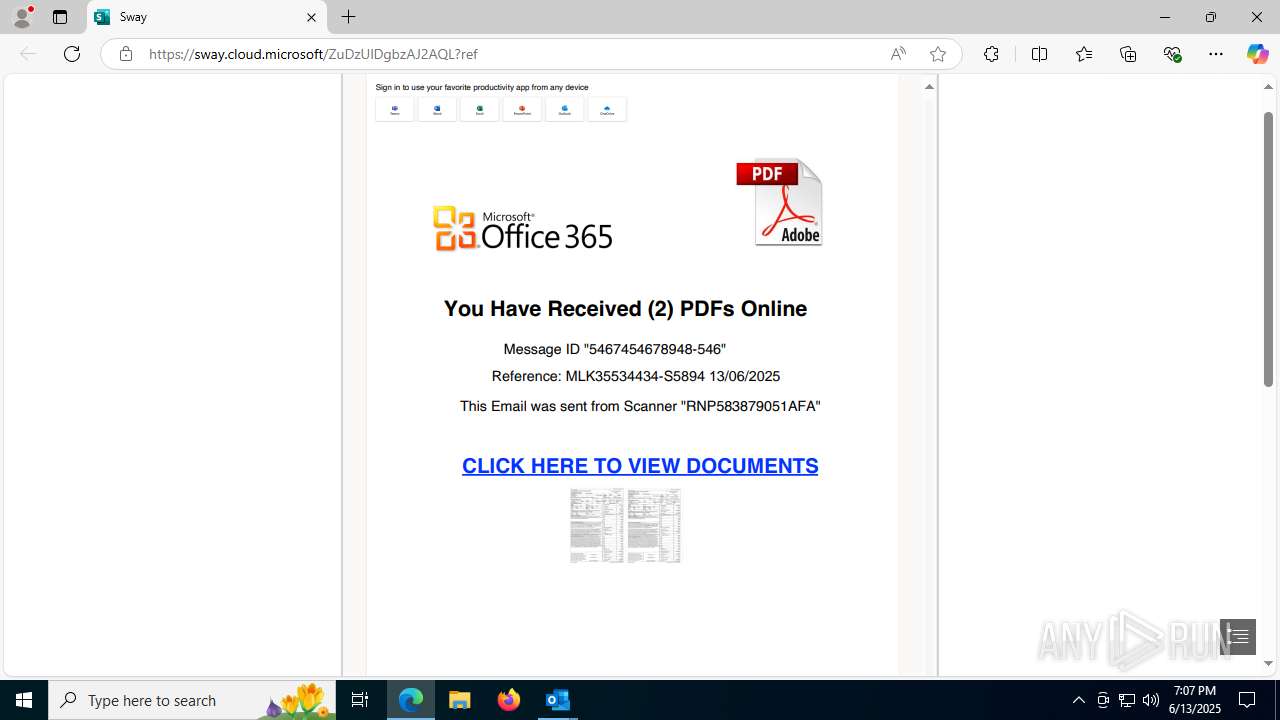
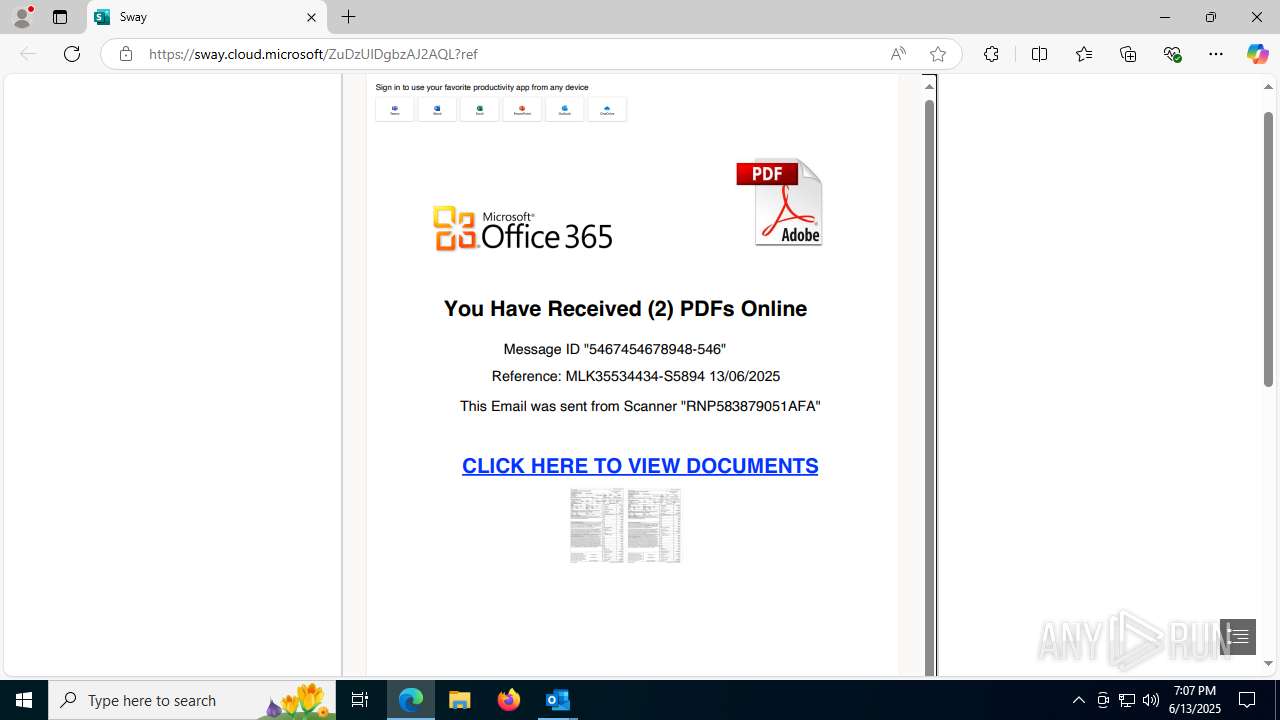
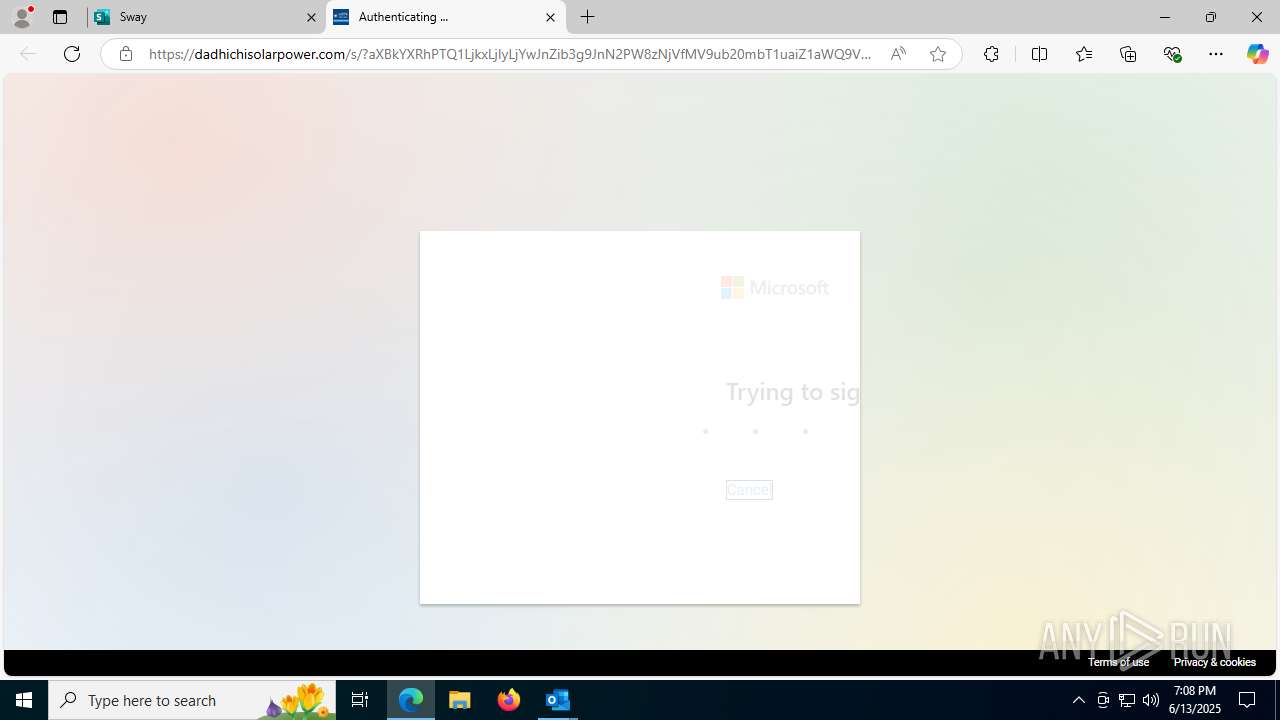
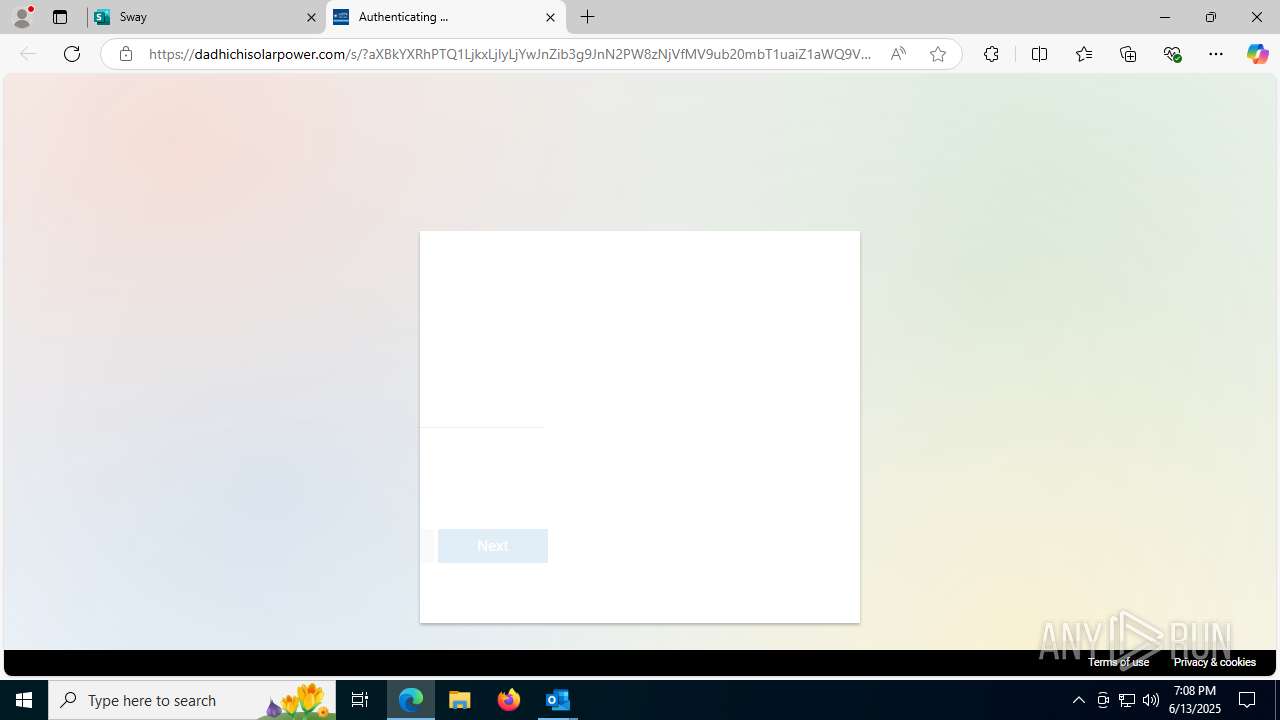
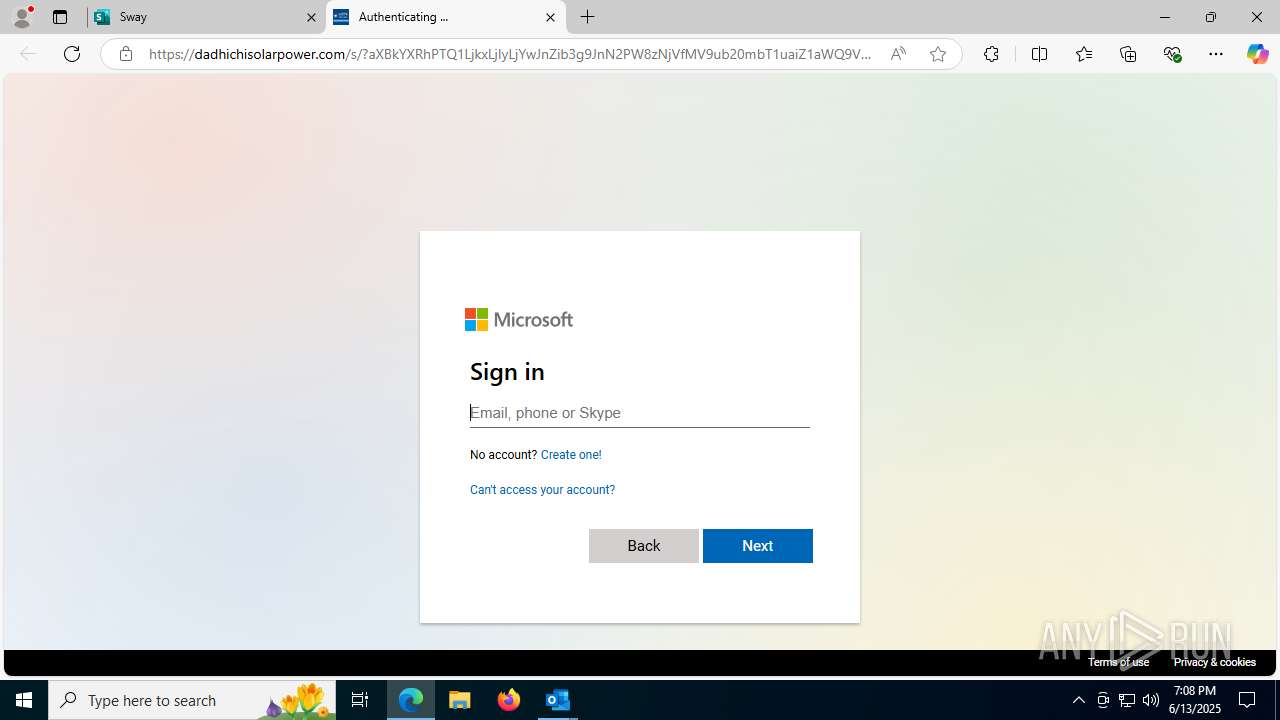
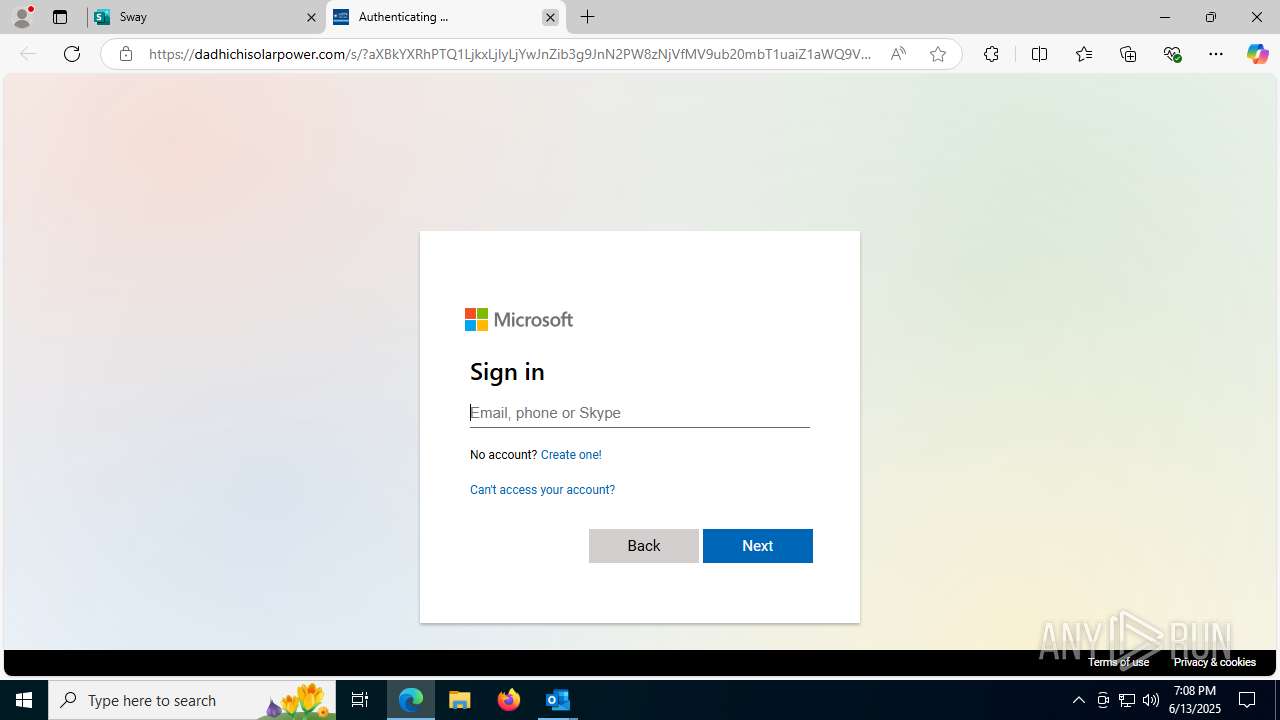
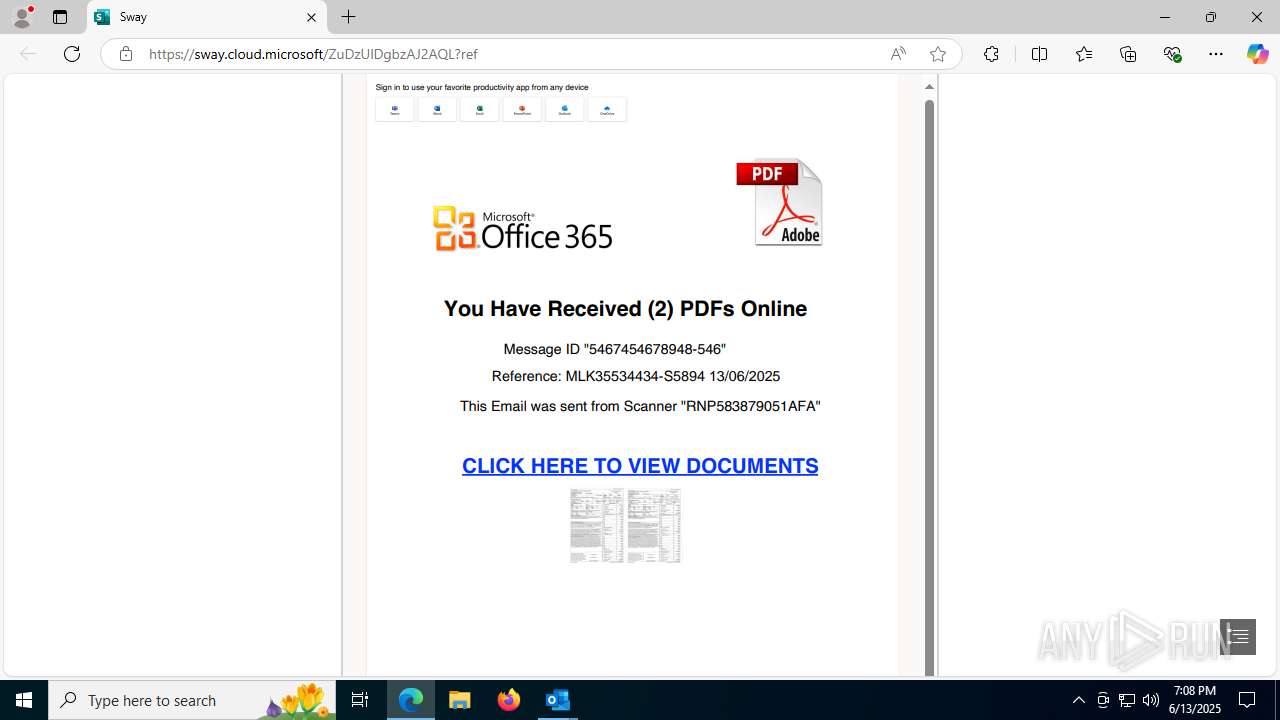
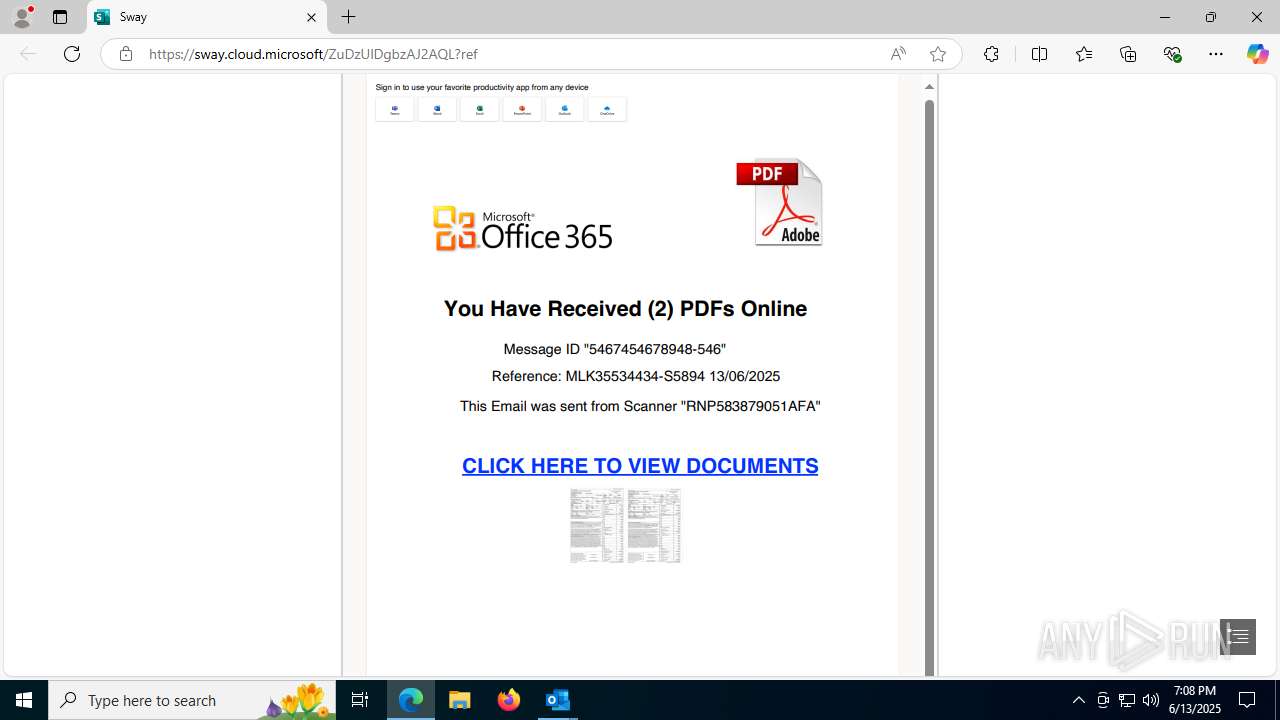
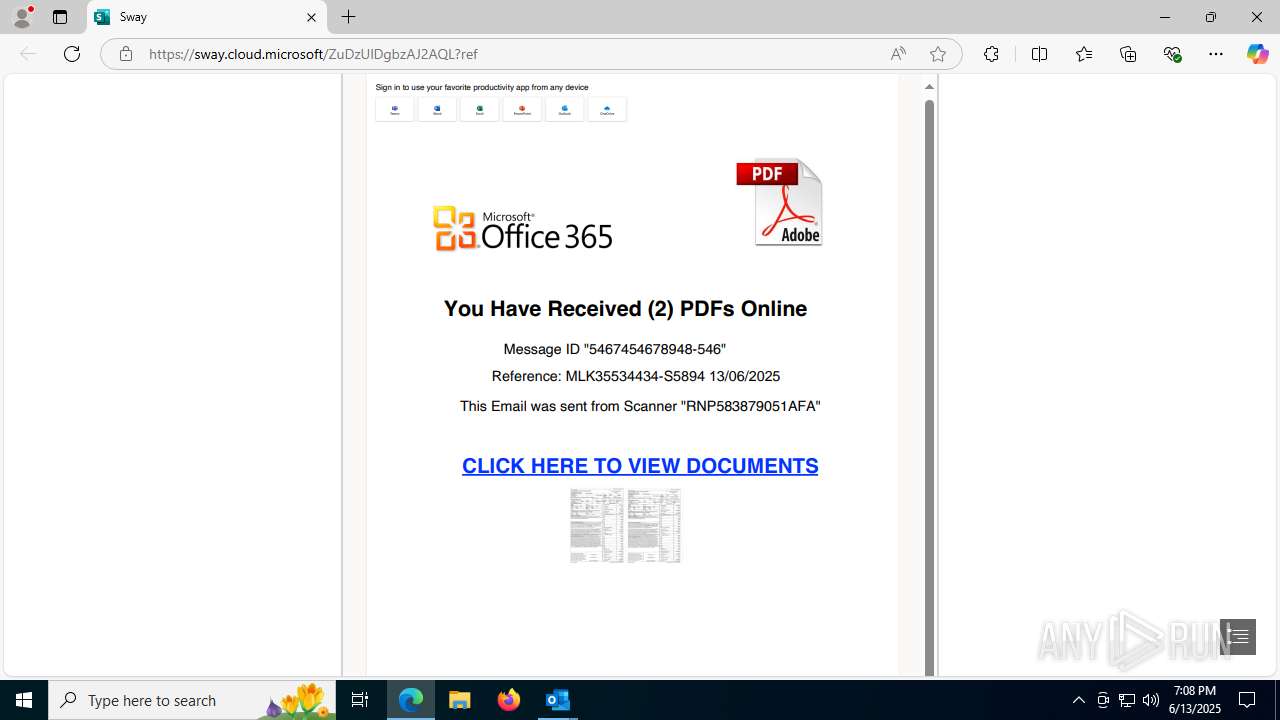
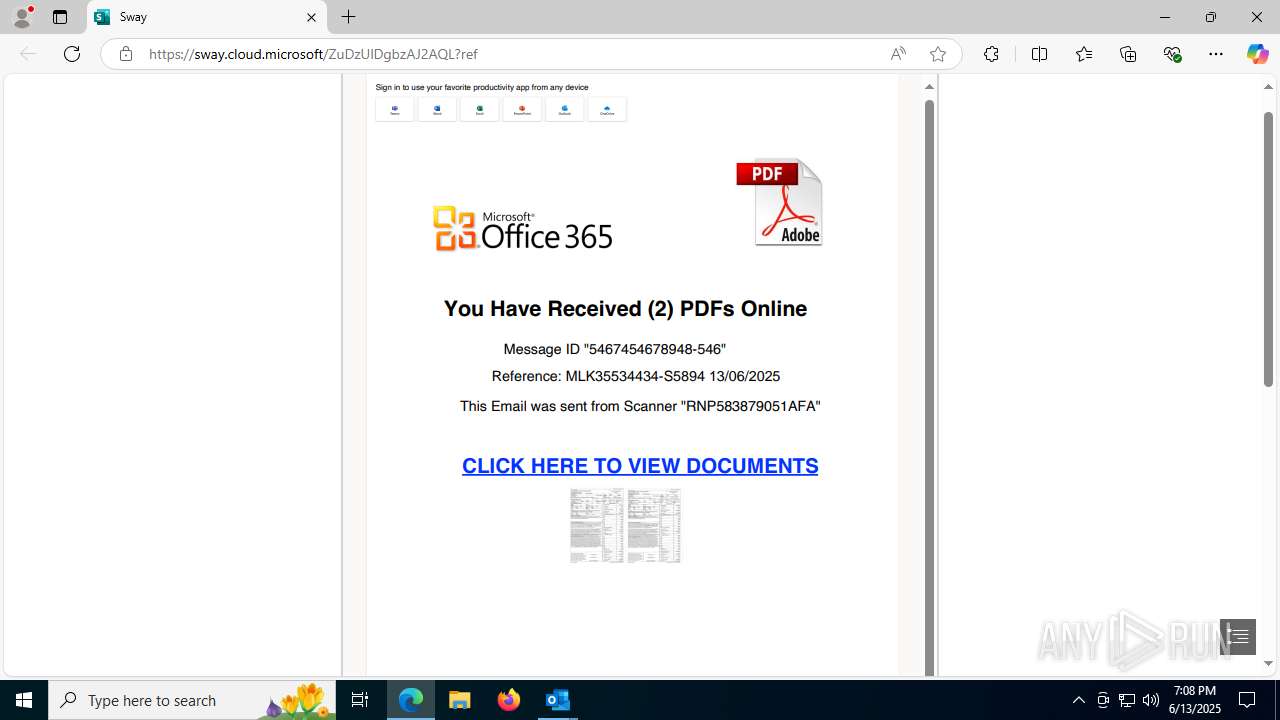
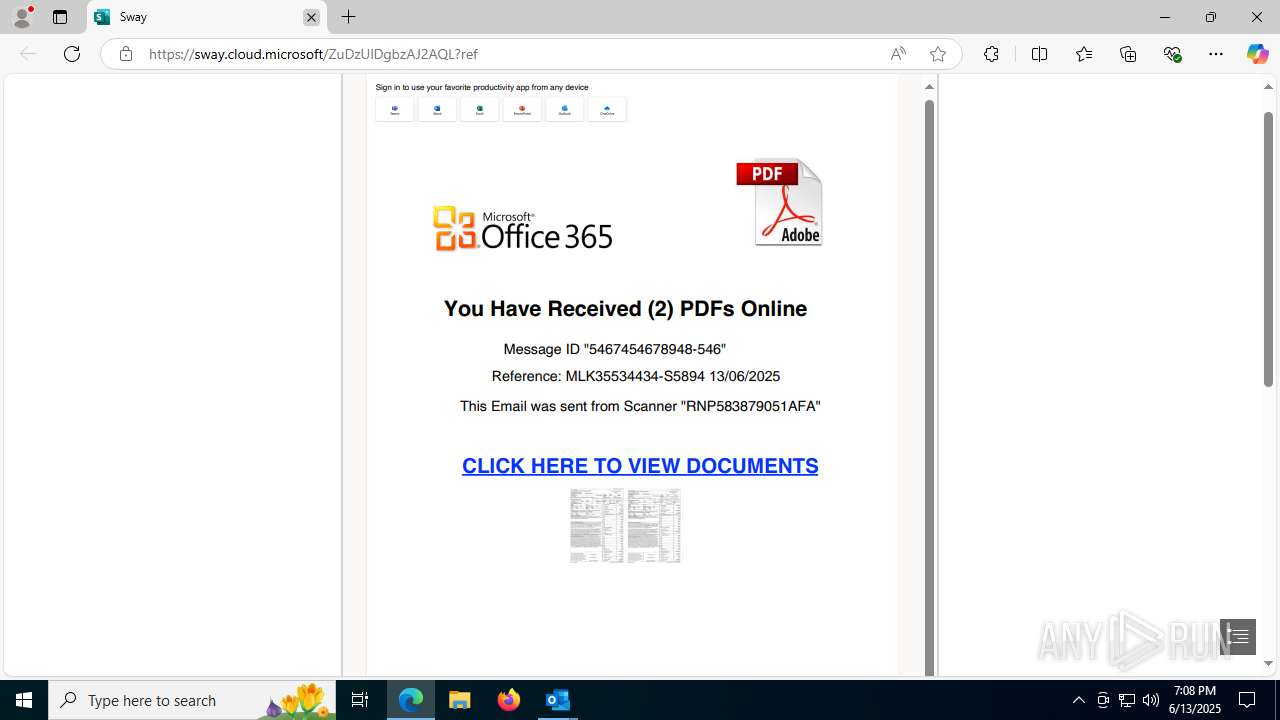
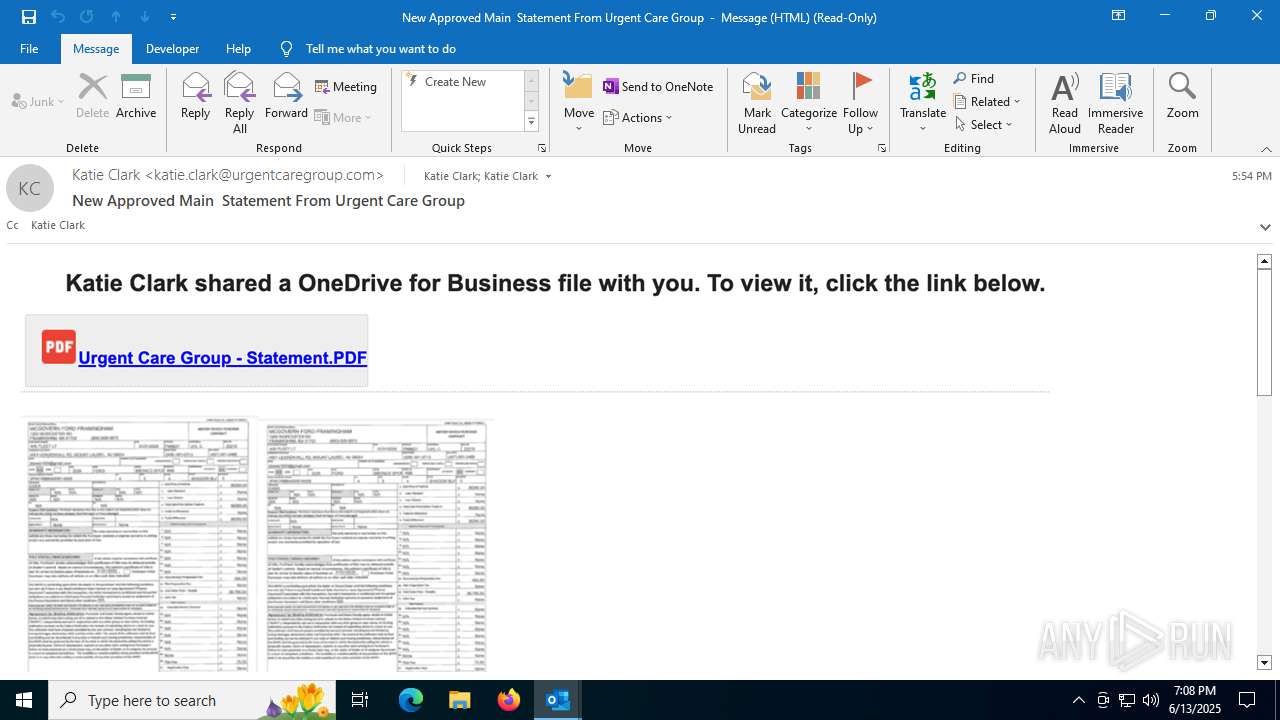
| Threats: | Mamba 2FA is an advanced phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) and target Microsoft 365 accounts. It focuses on intercepting authentication flows in real-time and enables threat actors to hijack user sessions and access sensitive systems even when additional security measures are in place. |
| Analysis date: | June 13, 2025, 19:06:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines (2201), with CRLF line terminators |
| MD5: | 91A601C8B93BB541FC7F58AB40ABBD6C |
| SHA1: | C0ED6696F513CC0B7771495DC746054127FDEDB7 |
| SHA256: | F75C98D8E53EDB28D578791979F0F7EBDE259567424BEBAC0D3A7E0B0965A0A0 |
| SSDEEP: | 24576:ilzlRIyNkuzQt3cxWiX25YHbxnxotzlRIyNkuzQ3:ijscxDCYHbR2M |
MALICIOUS
Phishing has been detected
- msedge.exe (PID: 7672)
- msedge.exe (PID: 3788)
- msedge.exe (PID: 7672)
- msedge.exe (PID: 3788)
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 3788)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- msedge.exe (PID: 6348)
- msedge.exe (PID: 5476)
- msedge.exe (PID: 6220)
Reads Environment values
- identity_helper.exe (PID: 7776)
Reads the computer name
- identity_helper.exe (PID: 7776)
Checks supported languages
- identity_helper.exe (PID: 7776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
198
Monitored processes
56
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2612,i,17408462549614034868,13111888033407103954,262144 --variations-seed-version --mojo-platform-channel-handle=2604 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\a1s-root6=email_banfield_2025_06_13_18_SMTP-att-1-4bJpXr0lbxz6C6hv-2025-06-13T18_57_00.eml.infected.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1496 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --pdf-upsell-enabled --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --always-read-main-dll --field-trial-handle=5096,i,234088484511086094,211070725761090264,262144 --variations-seed-version --mojo-platform-channel-handle=6452 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3668,i,17408462549614034868,13111888033407103954,262144 --variations-seed-version --mojo-platform-channel-handle=3684 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2128 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2316,i,13847914377367675177,17260632540353503352,262144 --variations-seed-version --mojo-platform-channel-handle=2328 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3676,i,17408462549614034868,13111888033407103954,262144 --variations-seed-version --mojo-platform-channel-handle=2104 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2732 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=7144,i,234088484511086094,211070725761090264,262144 --variations-seed-version --mojo-platform-channel-handle=7108 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3608 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "4F2134A5-DD04-48BC-A6D1-38AE9FB78A2F" "953BAA2A-70FC-44A6-82E7-7A85A2C7B445" "1296" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 3788 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=1832,i,17408462549614034868,13111888033407103954,262144 --variations-seed-version --mojo-platform-channel-handle=2692 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4196 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2212,i,13847914377367675177,17260632540353503352,262144 --variations-seed-version --mojo-platform-channel-handle=2396 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
21 464
Read events
20 230
Write events
1 101
Delete events
133
Modification events
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | write | Name: | OutlookBootFlag |
Value: 1 | |||
| (PID) Process: | (1296) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{02CAC15F-D4BE-400E-9127-D54982AA4AE9} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
388
Text files
145
Unknown types
61
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1296 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 1296 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk6823.tmp | binary | |
MD5:D77F9AFD8C3D34814110CCEDAA266969 | SHA256:1C05CD5906DF4FE9803F11A0BBCA6F751E574D84C957952F0C869119796B7548 | |||
| 1296 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk6834.tmp | binary | |
MD5:F2047E05BB0D768317B599D917601C29 | SHA256:BDAE68CF22233F05763BAA3E073C0E1C4EC1282FC88594AE7636EF4D569F62FB | |||
| 1296 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk6810.tmp | binary | |
MD5:F2047E05BB0D768317B599D917601C29 | SHA256:BDAE68CF22233F05763BAA3E073C0E1C4EC1282FC88594AE7636EF4D569F62FB | |||
| 1296 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk6811.tmp | text | |
MD5:B160F7C4F6C949456C09AA449CFF1781 | SHA256:3D5B5B3B9D68A7A453940D69F1F79959824E6F007E3E34E4E6AC32356992AB5A | |||
| 1296 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF17b48a.TMP | — | |
MD5:— | SHA256:— | |||
| 6348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF17b48a.TMP | — | |
MD5:— | SHA256:— | |||
| 1296 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | der | |
MD5:231169DF4D5BED78C80372ECDED1A6D3 | SHA256:5B5D664C9838D0DACC7F7662233B790D258E1AB7DF5530F86E2F070CFDA0E4B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
168
DNS requests
179
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2764 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3788 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:6WqB7ANO_8lgVs5oWnuGd8Bd3E24MW2yDf7N-sGBugI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1296 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7748 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750176377&P2=404&P3=2&P4=G1yjuB6aejZM03duR8apkDM2psIjjK3cDT0O1Ltxabh5t7ECcB9RXi456hovWEqod6BFfl3SOjIU%2bWzfyq24Kg%3d%3d | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7476 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7748 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750176377&P2=404&P3=2&P4=G1yjuB6aejZM03duR8apkDM2psIjjK3cDT0O1Ltxabh5t7ECcB9RXi456hovWEqod6BFfl3SOjIU%2bWzfyq24Kg%3d%3d | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.19.105.127:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7748 | svchost.exe | HEAD | 200 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750176377&P2=404&P3=2&P4=G1yjuB6aejZM03duR8apkDM2psIjjK3cDT0O1Ltxabh5t7ECcB9RXi456hovWEqod6BFfl3SOjIU%2bWzfyq24Kg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4380 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1296 | OUTLOOK.EXE | 52.123.243.203:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1296 | OUTLOOK.EXE | 23.50.131.86:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
1296 | OUTLOOK.EXE | 52.111.236.4:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2764 | svchost.exe | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
3788 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
3788 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (socketaad) |