| File name: | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar |
| Full analysis: | https://app.any.run/tasks/8e0afd77-1928-4687-91e9-72a8e6c5adb7 |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | June 18, 2025, 05:31:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | F1E3728E2CEB8F3C627848B240E3D563 |
| SHA1: | 94E82ED6238B46620799A1C0189799AAE930BD01 |
| SHA256: | F5F1EBB6BC5FDC4D33A6D5975E8DFF37FB221156FE2571E9C136772F938D2A85 |
| SSDEEP: | 98304:cC3CpAOUEyShDPCH4mAtOD6H9yciGnBU8nA4sOVi0gPj6OylTFD47yRQ7AFpSCO7:ZOdL5NsTPvfkj881mwe/kix9UZlI |
MALICIOUS
Uses Task Scheduler to run other applications
- LIME RAT.exe (PID: 5764)
- LIME RAT.exe (PID: 684)
- svchost.exe (PID: 5456)
- svchost.exe (PID: 1948)
- svchost.exe (PID: 4580)
- svchost.exe (PID: 5708)
- svchost.exe (PID: 6292)
- svchost.exe (PID: 4580)
NJRAT mutex has been found
- LIME RAT.exe (PID: 5764)
- LIME RAT.exe (PID: 684)
- svchost.exe (PID: 5456)
- svchost.exe (PID: 1948)
- svchost.exe (PID: 5708)
- svchost.exe (PID: 4580)
- svchost.exe (PID: 6292)
- svchost.exe (PID: 4580)
Changes the autorun value in the registry
- svchost.exe (PID: 5456)
Create files in the Startup directory
- svchost.exe (PID: 5456)
SUSPICIOUS
Application launched itself
- powershell.exe (PID: 5564)
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
The process drops C-runtime libraries
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
Process drops legitimate windows executable
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
Process drops python dynamic module
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
Executable content was dropped or overwritten
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
- cmd.exe (PID: 3780)
- xx-svchost.exe (PID: 3788)
- SWAInstaller.exe (PID: 2076)
- SWAInstaller.tmp (PID: 6936)
- LIME RAT.exe (PID: 5764)
- svchost.exe (PID: 5456)
Starts POWERSHELL.EXE for commands execution
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
- powershell.exe (PID: 5564)
- cmd.exe (PID: 3780)
Base64-obfuscated command line is found
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
- powershell.exe (PID: 5564)
The process creates files with name similar to system file names
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
- LIME RAT.exe (PID: 5764)
- svchost.exe (PID: 5456)
Executing commands from a ".bat" file
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
Starts CMD.EXE for commands execution
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3780)
There is functionality for taking screenshot (YARA)
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 5172)
Reads the date of Windows installation
- xx-svchost.exe (PID: 3788)
Reads security settings of Internet Explorer
- xx-svchost.exe (PID: 3788)
- LIME RAT.exe (PID: 5764)
The executable file from the user directory is run by the CMD process
- xx-svchost.exe (PID: 3788)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 5900)
- schtasks.exe (PID: 1512)
- schtasks.exe (PID: 2972)
- schtasks.exe (PID: 4460)
- schtasks.exe (PID: 4084)
- schtasks.exe (PID: 6428)
- schtasks.exe (PID: 4960)
- schtasks.exe (PID: 1508)
- schtasks.exe (PID: 4708)
- schtasks.exe (PID: 3048)
- schtasks.exe (PID: 6776)
- schtasks.exe (PID: 6828)
- schtasks.exe (PID: 1948)
- schtasks.exe (PID: 7156)
- schtasks.exe (PID: 6676)
- schtasks.exe (PID: 7096)
Reads the Windows owner or organization settings
- SWAInstaller.tmp (PID: 6936)
Starts itself from another location
- LIME RAT.exe (PID: 5764)
Connects to unusual port
- svchost.exe (PID: 5456)
Loads Python modules
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
BASE64 encoded PowerShell command has been detected
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
- powershell.exe (PID: 5564)
The process executes via Task Scheduler
- svchost.exe (PID: 6292)
- svchost.exe (PID: 4580)
INFO
Checks supported languages
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
- xx-svchost.exe (PID: 3788)
- SWAInstaller.exe (PID: 2076)
- LIME RAT.exe (PID: 5764)
- SWAInstaller.tmp (PID: 6936)
- LIME RAT.exe (PID: 684)
- svchost.exe (PID: 5456)
- svchost.exe (PID: 1948)
- svchost.exe (PID: 4580)
- svchost.exe (PID: 5708)
- svchost.exe (PID: 6292)
- svchost.exe (PID: 4580)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5456)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5456)
Create files in a temporary directory
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
- SWAInstaller.exe (PID: 2076)
- SWAInstaller.tmp (PID: 6936)
The sample compiled with english language support
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
Reads the computer name
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
- xx-svchost.exe (PID: 3788)
- SWAInstaller.tmp (PID: 6936)
- LIME RAT.exe (PID: 5764)
- SWAInstaller.exe (PID: 2076)
- LIME RAT.exe (PID: 684)
- svchost.exe (PID: 5456)
- svchost.exe (PID: 1948)
- svchost.exe (PID: 4580)
- svchost.exe (PID: 5708)
- svchost.exe (PID: 6292)
- svchost.exe (PID: 4580)
Creates files or folders in the user directory
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
- xx-svchost.exe (PID: 3788)
- svchost.exe (PID: 5456)
PyInstaller has been detected (YARA)
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4156)
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5172)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4644)
Process checks computer location settings
- xx-svchost.exe (PID: 3788)
- LIME RAT.exe (PID: 5764)
Reads the machine GUID from the registry
- xx-svchost.exe (PID: 3788)
- LIME RAT.exe (PID: 5764)
- LIME RAT.exe (PID: 684)
- svchost.exe (PID: 5456)
- svchost.exe (PID: 5708)
Launching a file from Task Scheduler
- LIME RAT.exe (PID: 5764)
- LIME RAT.exe (PID: 684)
- svchost.exe (PID: 1948)
- svchost.exe (PID: 5456)
- svchost.exe (PID: 4580)
- svchost.exe (PID: 5708)
- svchost.exe (PID: 6292)
- svchost.exe (PID: 4580)
Manual execution by a user
- LIME RAT.exe (PID: 684)
- svchost.exe (PID: 1948)
- svchost.exe (PID: 4580)
- svchost.exe (PID: 5708)
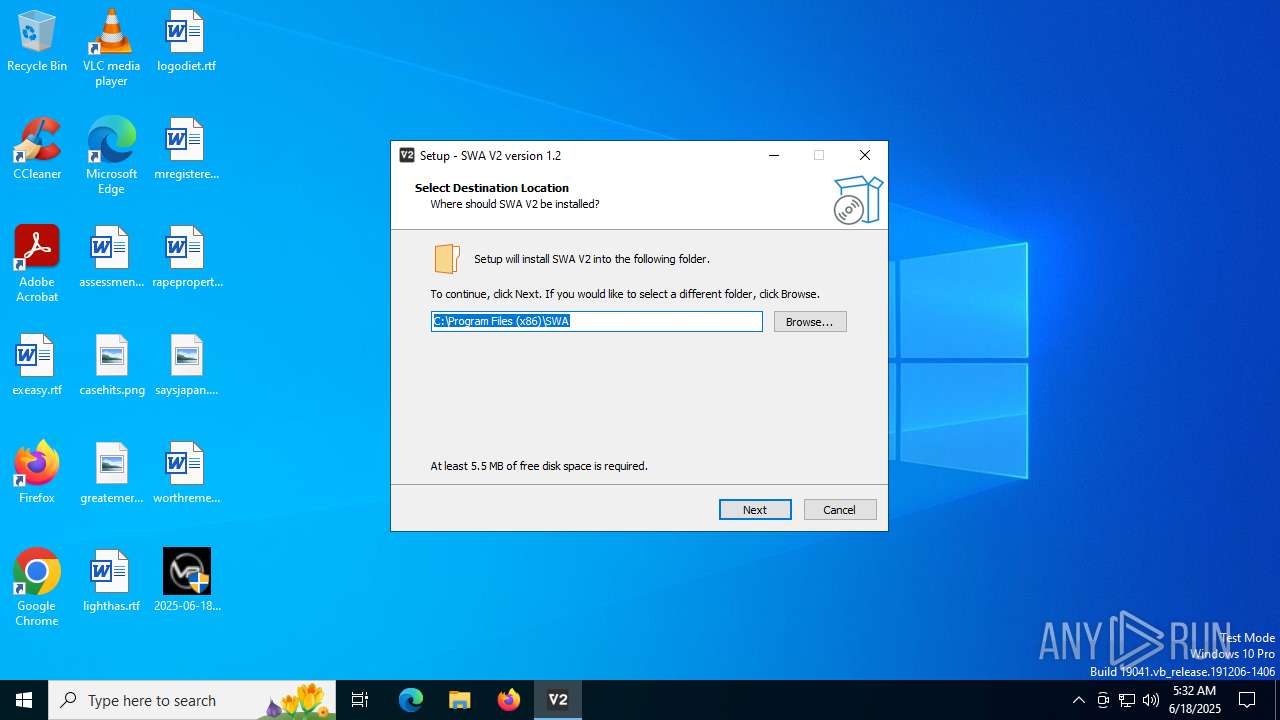
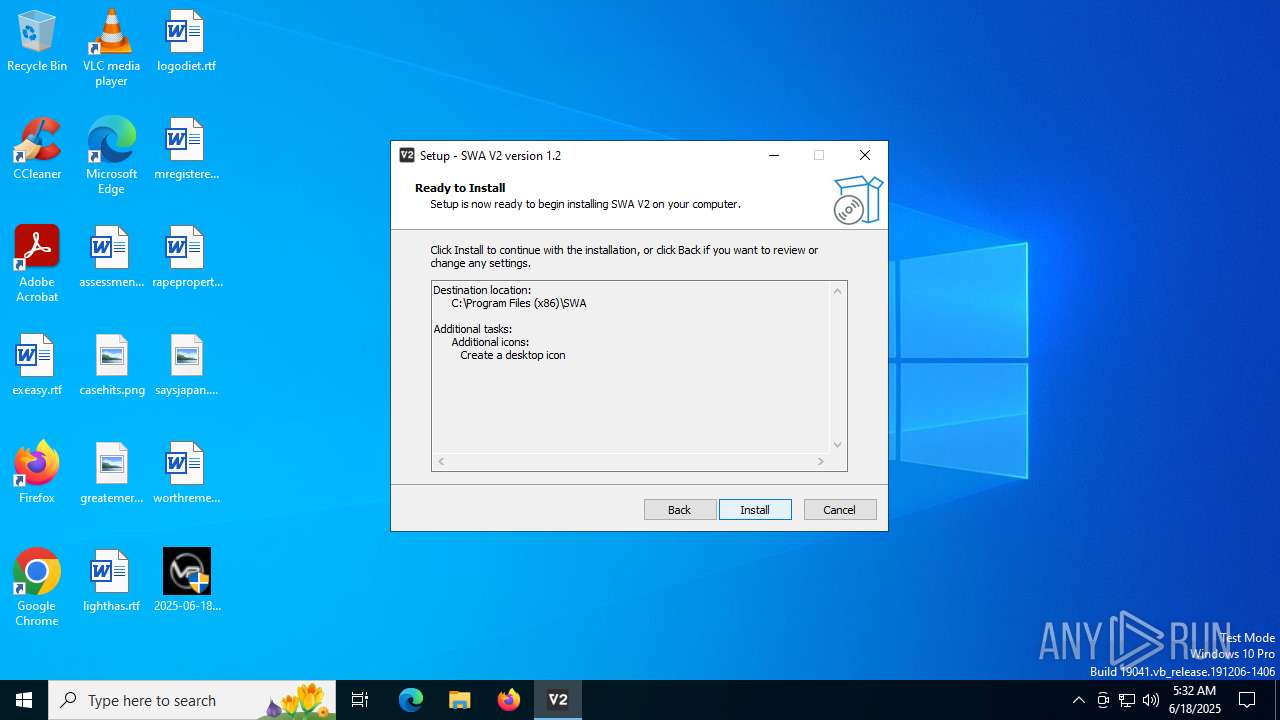
Detects InnoSetup installer (YARA)
- SWAInstaller.tmp (PID: 6936)
- SWAInstaller.exe (PID: 2076)
Compiled with Borland Delphi (YARA)
- SWAInstaller.exe (PID: 2076)
- SWAInstaller.tmp (PID: 6936)
Launching a file from a Registry key
- svchost.exe (PID: 5456)
Launching a file from the Startup directory
- svchost.exe (PID: 5456)
.NET Reactor protector has been detected
- svchost.exe (PID: 5456)
Checks proxy server information
- slui.exe (PID: 6364)
Reads the software policy settings
- slui.exe (PID: 6364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:14 19:11:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 174592 |
| InitializedDataSize: | 99840 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd0d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
217
Monitored processes
86
Malicious processes
10
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\LIME RAT.exe" | C:\Users\admin\AppData\Local\LIME RAT.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | schtasks /create /tn NYANP /tr "C:\Users\admin\AppData\Local\LIME RAT.exe" /sc minute /mo 5 | C:\Windows\SysWOW64\schtasks.exe | — | LIME RAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | schtasks /create /tn NYAN /tr "C:\WINDOWS\svchost.exe" /sc minute /mo 1 | C:\Windows\SysWOW64\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 247
Read events
21 003
Write events
244
Delete events
0
Modification events
| (PID) Process: | (5456) svchost.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | SEE_MASK_NOZONECHECKS |
Value: 1 | |||
| (PID) Process: | (5456) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | svchost.exe |
Value: "C:\WINDOWS\svchost.exe" .. | |||
| (PID) Process: | (5456) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | svchost.exe |
Value: "C:\WINDOWS\svchost.exe" .. | |||
| (PID) Process: | (5456) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\svchost.exe |
| Operation: | write | Name: | [kl] |
Value: | |||
Executable files
71
Suspicious files
5
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_raw_aesni.pyd | executable | |
MD5:0B2596C23BD2792FA5CDB304417DD36D | SHA256:2369F44274DC7F03B5F37D77F39BA77EC9146CF53170CB4E9EFC2001197C698F | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_pkcs1_decode.pyd | executable | |
MD5:0900E8E081214B321E38C80670BE196E | SHA256:5ACAE29721A43D32B2602D32BF8CC9F4224191F886894CBB0BC0A4407C4D16FE | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_Salsa20.pyd | executable | |
MD5:73D2494C8BCD6738B2767FE7819DF72A | SHA256:93ECBA417C3E6E0C44DFD0D86D2A04474E0DDDCA5C7835E4802E6139C0A732D4 | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_ARC4.pyd | executable | |
MD5:41851AA1DD56679C1F5EC9853B9CC616 | SHA256:0E17085905FA32E6C16DC6E40F1D8348BFCFAC838B879E6D54D8640B40B39445 | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_chacha20.pyd | executable | |
MD5:AE0D9CBAF7463843E438DBCCEF1B27FE | SHA256:F044DF62C4F14E5E7608463D34EC3B5F4229F6F8F3E7EB29F8A1A235079F4296 | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_raw_ocb.pyd | executable | |
MD5:A9C3970A60893D6649CF3C1CD5B7C58E | SHA256:7349AD8A9F9E67552A23DB5C8A86D6F560B7887EC5299A6B0A4FE5F872A84FC9 | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_raw_ecb.pyd | executable | |
MD5:FC23D10DB102260CED6D1B0A82E83017 | SHA256:633CB61F67986877CDB10E6D2FCD19B29B8F1880FAFBE17E6CE3CF3DF3E64952 | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_raw_eksblowfish.pyd | executable | |
MD5:1A6B2B8D0ED65C54C609815445D6C45B | SHA256:3800ED2BEAB7F9C33337A8E9C7B14CCBDC17D538DE8EF35E2B179F9A77F927F4 | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_raw_des3.pyd | executable | |
MD5:7B0BCE99E559C6868CC43FB9C3F921D9 | SHA256:8EA8CFD1D8714343EADF340C060DDBAE685438A6B986CDD07282ED4663B7DA6E | |||
| 4156 | 2025-06-18_f1e3728e2ceb8f3c627848b240e3d563_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI41562\Cryptodome\Cipher\_raw_des.pyd | executable | |
MD5:53F7B88C994A12109A43169E16D9FEA0 | SHA256:89446AFF1D4833DCFCF3EB6F4392900CD095F656FA621928D69C589477DF772A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
24
DNS requests
7
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3788 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3788 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3788 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3788 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3788 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
published-experience.gl.at.ply.gg |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (.ply .gg) |
2200 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES Tunneling Service in DNS Lookup (* .ply .gg) |
2200 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |