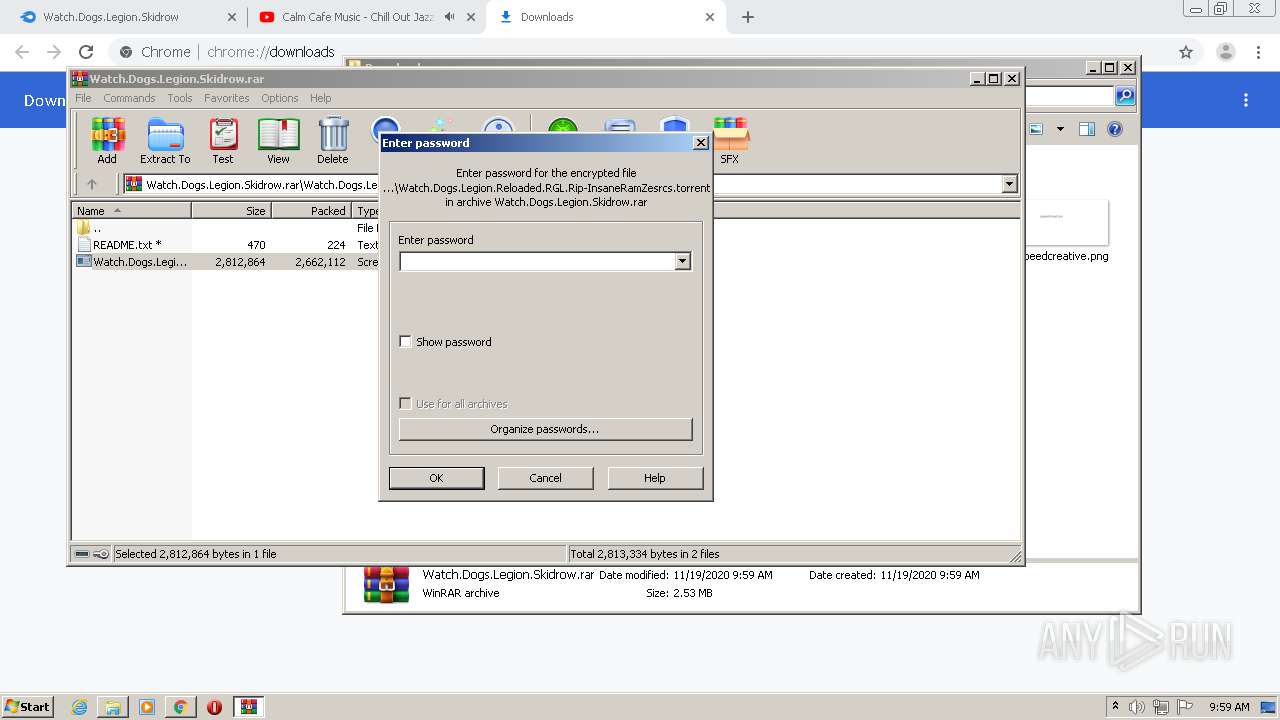
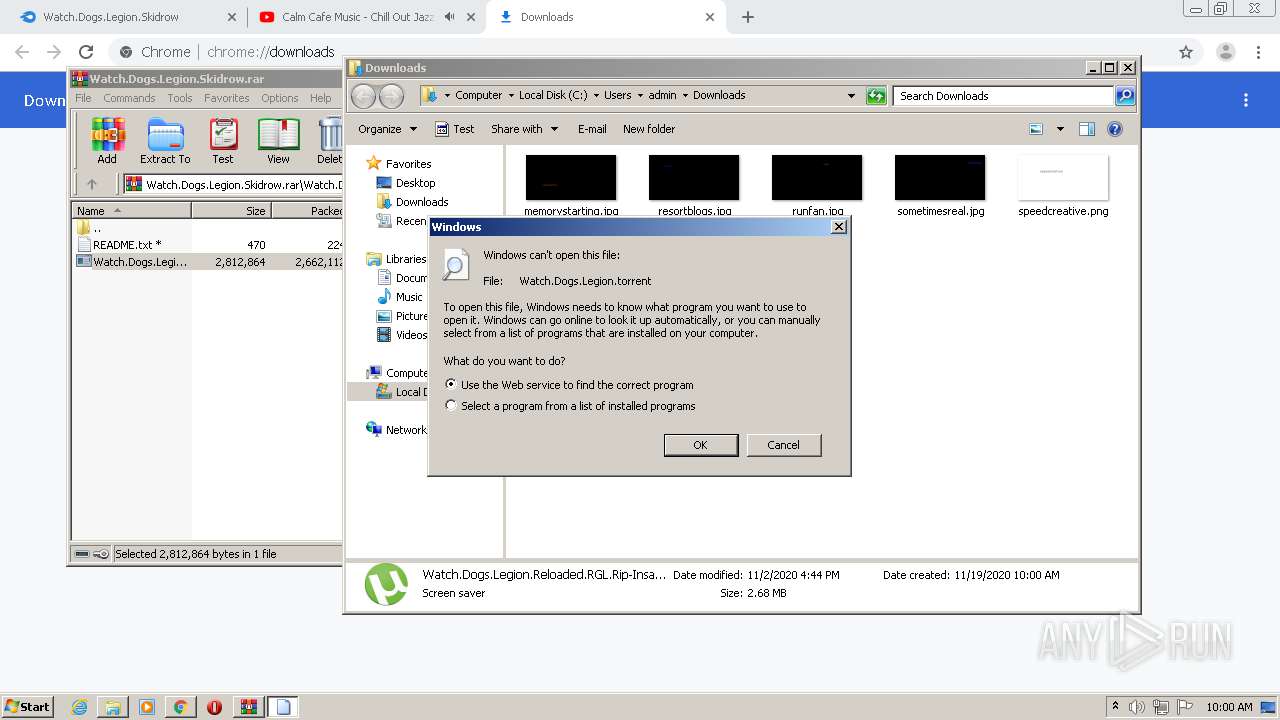
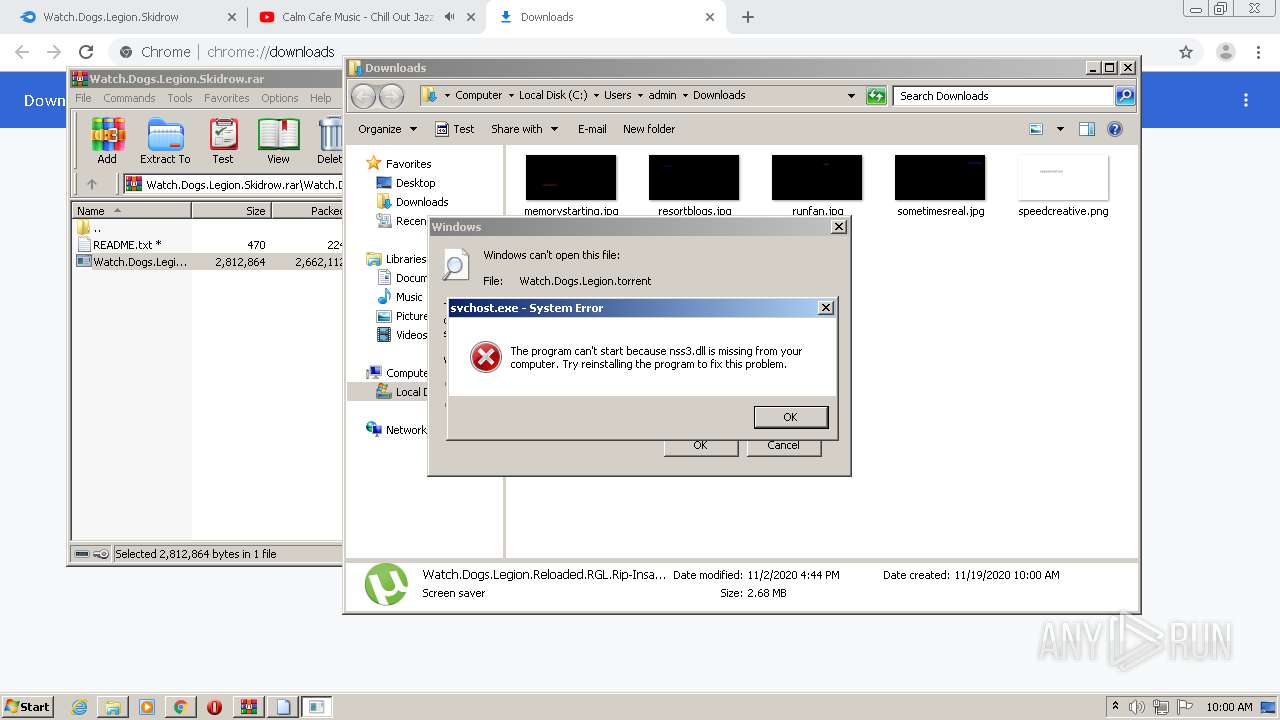
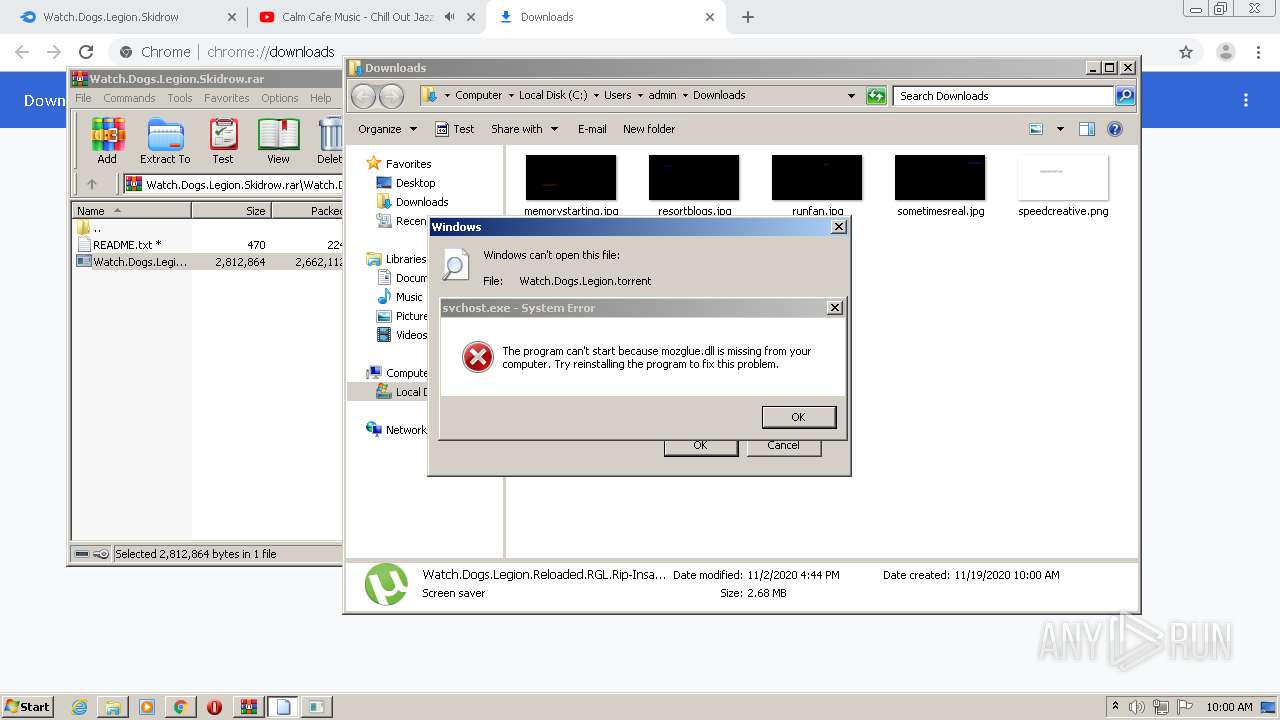
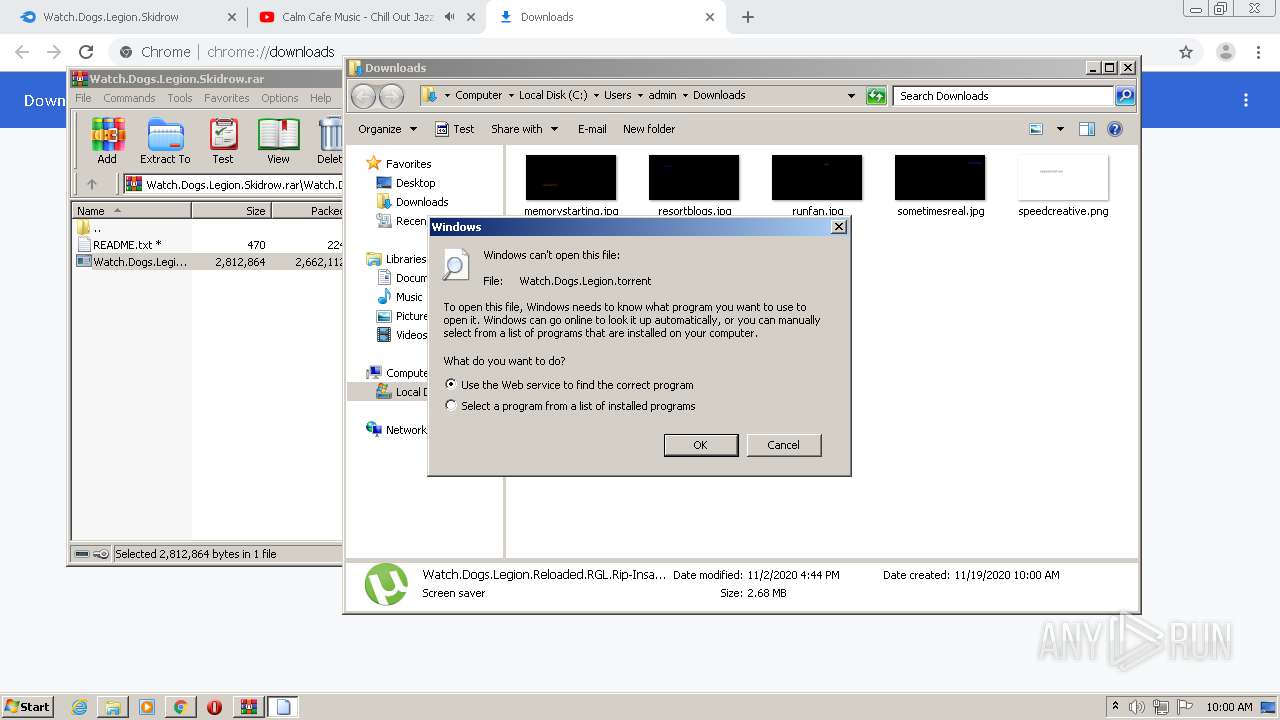
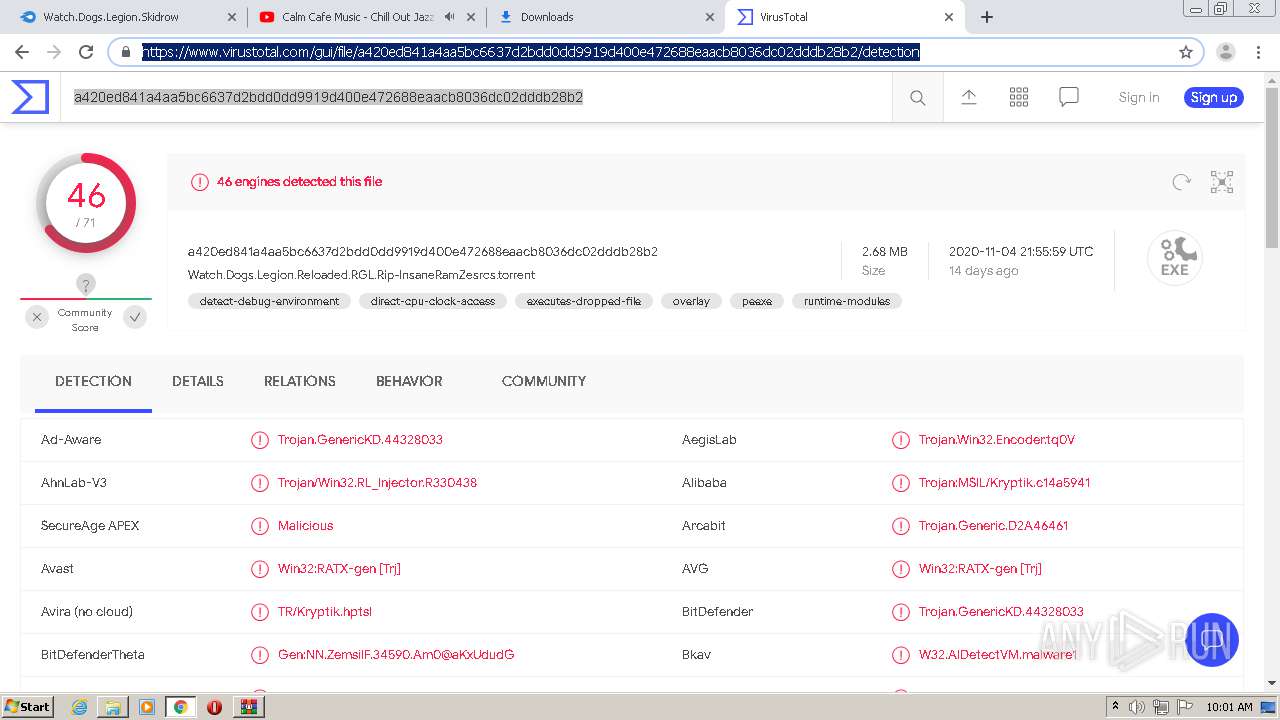
| URL: | https://www.mediafire.com/file/jcju444h3aqh44h/Watch.Dogs.Legion.Skidrow.rar/file |
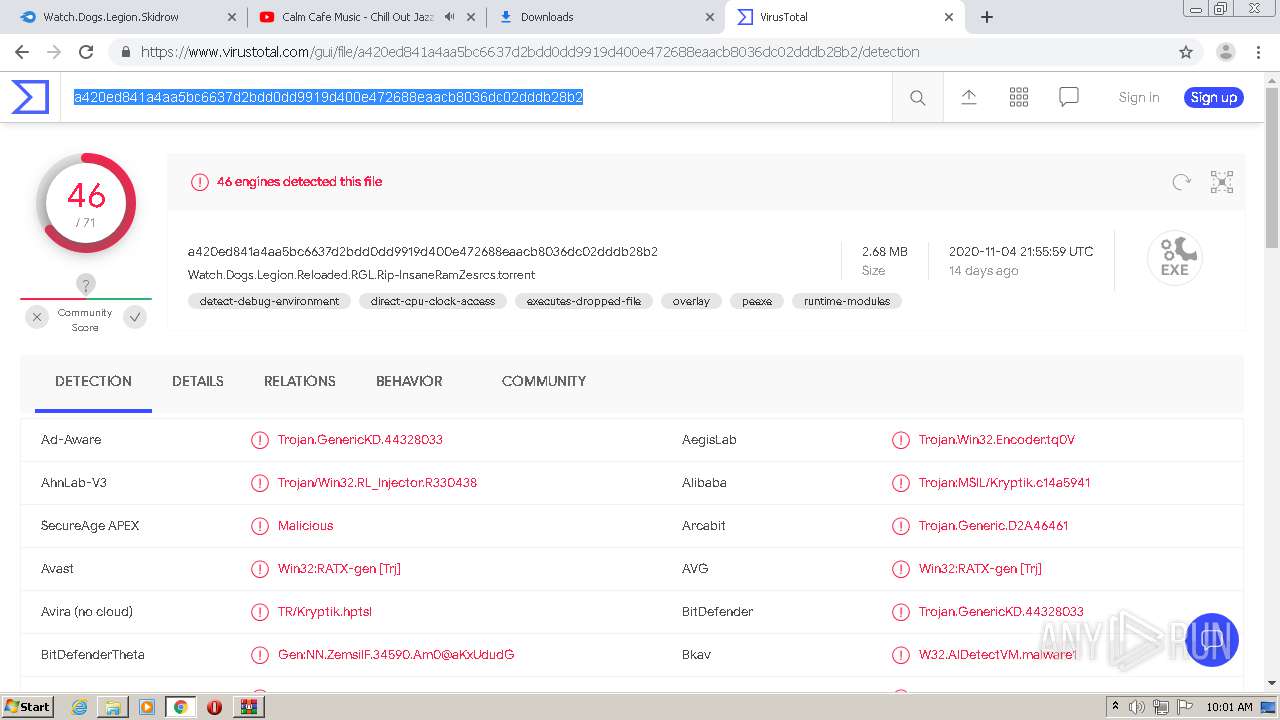
| Full analysis: | https://app.any.run/tasks/a7958080-65cb-4b68-89fd-8d20a662771e |
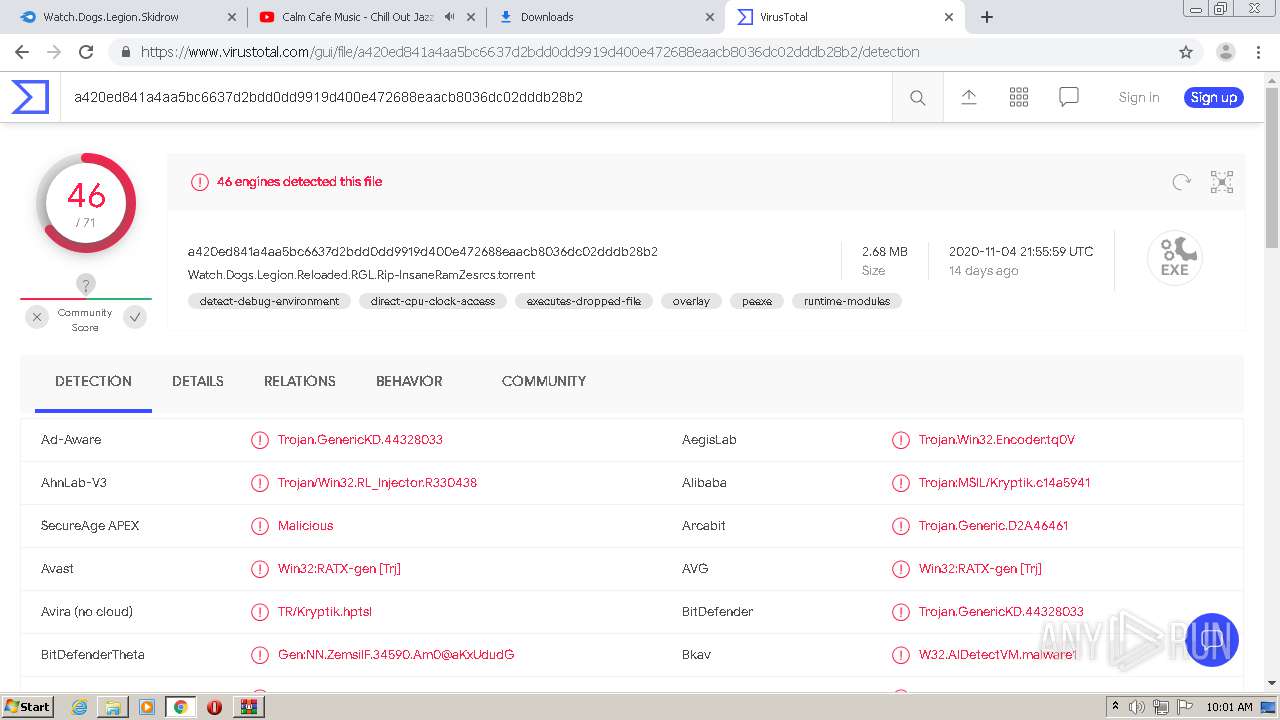
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | November 19, 2020, 09:57:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | DA930277E08E45AA3A0C48F964A673C8 |
| SHA1: | 125684DFAD77E902D7441E32AE6E08F94E73FDD9 |
| SHA256: | F55BDBAD4947868A4815FCFE66DDC2289FA525085F274B2C66B8FB25087DD5A7 |
| SSDEEP: | 3:N8DSLw3eGUodgNLhWpMP1UPA:2OLw3eG6LsMcA |
MALICIOUS
Application was dropped or rewritten from another process
- WatchDogsBE.exe (PID: 3228)
- WatchDogsBE.exe (PID: 3104)
- Watch.Dogs.Legion.Reloaded.RGL.Rip-InsaneRamZestnerrot.scr (PID: 2920)
- WatchDogsCrack.exe (PID: 3988)
- WatchDogsCrack.exe (PID: 2012)
- WatchDogsBE.exe (PID: 2320)
- svchost.exe (PID: 3456)
- svchost.exe (PID: 2836)
Runs injected code in another process
- WatchDogsCrack.exe (PID: 3988)
Application was injected by another process
- explorer.exe (PID: 292)
PHORPIEX was detected
- WatchDogsCrack.exe (PID: 3988)
MINER was detected
- wuapp.exe (PID: 2488)
- wuapp.exe (PID: 2900)
- wuapp.exe (PID: 976)
Changes the autorun value in the registry
- WatchDogsBE.exe (PID: 3104)
Connects to CnC server
- wuapp.exe (PID: 2488)
- wuapp.exe (PID: 2900)
- wuapp.exe (PID: 976)
Writes to a start menu file
- wscript.exe (PID: 908)
SUSPICIOUS
Creates files in the user directory
- explorer.exe (PID: 292)
- WatchDogsBE.exe (PID: 3104)
- WatchDogsBE.exe (PID: 2320)
- wscript.exe (PID: 908)
Uses RUNDLL32.EXE to load library
- Watch.Dogs.Legion.Reloaded.RGL.Rip-InsaneRamZestnerrot.scr (PID: 2920)
Starts application with an unusual extension
- explorer.exe (PID: 292)
Application launched itself
- WatchDogsCrack.exe (PID: 2012)
- WatchDogsBE.exe (PID: 3228)
- WatchDogsBE.exe (PID: 3104)
- svchost.exe (PID: 3456)
Executable content was dropped or overwritten
- WatchDogsBE.exe (PID: 3228)
- WatchDogsCrack.exe (PID: 2012)
- Watch.Dogs.Legion.Reloaded.RGL.Rip-InsaneRamZestnerrot.scr (PID: 2920)
- WatchDogsCrack.exe (PID: 3988)
- svchost.exe (PID: 3456)
- WatchDogsBE.exe (PID: 3104)
Reads Internet Cache Settings
- WatchDogsCrack.exe (PID: 3988)
Creates files in the program directory
- WatchDogsCrack.exe (PID: 3988)
Creates executable files which already exist in Windows
- WatchDogsBE.exe (PID: 3104)
Starts itself from another location
- WatchDogsBE.exe (PID: 2320)
Starts CMD.EXE for commands execution
- WatchDogsCrack.exe (PID: 3988)
Loads DLL from Mozilla Firefox
- svchost.exe (PID: 2836)
Executes scripts
- cmd.exe (PID: 3008)
INFO
Reads the hosts file
- chrome.exe (PID: 1952)
- chrome.exe (PID: 2544)
Reads settings of System Certificates
- chrome.exe (PID: 1952)
Manual execution by user
- WinRAR.exe (PID: 2716)
- Watch.Dogs.Legion.Reloaded.RGL.Rip-InsaneRamZestnerrot.scr (PID: 2920)
Application launched itself
- chrome.exe (PID: 2544)
Reads Internet Cache Settings
- chrome.exe (PID: 2544)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
111
Monitored processes
71
Malicious processes
13
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1000,4302535587188076086,7979628363982899736,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9163632149912792695 --mojo-platform-channel-handle=1016 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 292 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,4302535587188076086,7979628363982899736,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16030370173753142368 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3816 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,4302535587188076086,7979628363982899736,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11301715935069445340 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2356 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,4302535587188076086,7979628363982899736,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17241902661476069406 --renderer-client-id=37 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5084 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,4302535587188076086,7979628363982899736,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5099379737684845852 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3612 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,4302535587188076086,7979628363982899736,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9308604765540729766 --renderer-client-id=21 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2320 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 728 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,4302535587188076086,7979628363982899736,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7520507024819987273 --renderer-client-id=43 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5232 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 908 | WScript "C:\ProgramData\TeweWPfIfY\r.vbs" | C:\Windows\system32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 976 | "C:\Windows\System32\wuapp.exe" -c "C:\ProgramData\TeweWPfIfY\cfgi" | C:\Windows\System32\wuapp.exe | WatchDogsCrack.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Update Application Launcher Exit code: 0 Version: 7.5.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
4 727
Read events
4 307
Write events
414
Delete events
6
Modification events
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2248) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2544-13250253464096875 |
Value: 259 | |||
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2544) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
8
Suspicious files
145
Text files
2 659
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FB64199-9F0.pma | — | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\1e15cc8f-b6e1-42f6-9420-a8f19ae1c1e5.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF127e9e.TMP | text | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT~RF127f98.TMP | text | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old~RF127fe6.TMP | text | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF1281ab.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
199
DNS requests
133
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1952 | chrome.exe | GET | 304 | 8.253.204.121:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
1952 | chrome.exe | GET | 304 | 8.253.204.121:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | — | — | whitelisted |
1952 | chrome.exe | GET | 200 | 8.253.204.121:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
1952 | chrome.exe | GET | 304 | 8.253.204.121:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
3988 | WatchDogsCrack.exe | GET | 200 | 45.82.72.148:80 | http://45.82.72.148/update.txt | unknown | text | 1.70 Kb | malicious |
1952 | chrome.exe | GET | 304 | 8.253.204.121:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
1952 | chrome.exe | GET | 304 | 8.253.204.121:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1952 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
1952 | chrome.exe | 173.194.67.95:443 | safebrowsing.googleapis.com | Google Inc. | US | unknown |
1952 | chrome.exe | 216.58.206.8:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
1952 | chrome.exe | 172.217.21.206:443 | clients1.google.com | Google Inc. | US | whitelisted |
1952 | chrome.exe | 172.217.16.174:443 | fundingchoicesmessages.google.com | Google Inc. | US | whitelisted |
1952 | chrome.exe | 185.33.221.14:443 | ib.adnxs.com | AppNexus, Inc | — | unknown |
1952 | chrome.exe | 104.17.166.186:443 | c.adsco.re | Cloudflare Inc | US | shared |
1952 | chrome.exe | 104.19.214.37:443 | cdn.otnolatrnup.com | Cloudflare Inc | US | shared |
— | — | 185.64.189.112:443 | hbopenbid.pubmatic.com | PubMatic, Inc. | GB | unknown |
1952 | chrome.exe | 104.16.68.69:443 | dmx.districtm.io | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediafire.com |
| shared |
accounts.google.com |
| shared |
fundingchoicesmessages.google.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
translate.google.com |
| whitelisted |
c.aaxads.com |
| whitelisted |
static.mediafire.com |
| shared |
cdn.otnolatrnup.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1952 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
1952 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
3988 | WatchDogsCrack.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Phorpiex |
2488 | wuapp.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2488 | wuapp.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
2488 | wuapp.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
5 ETPRO signatures available at the full report