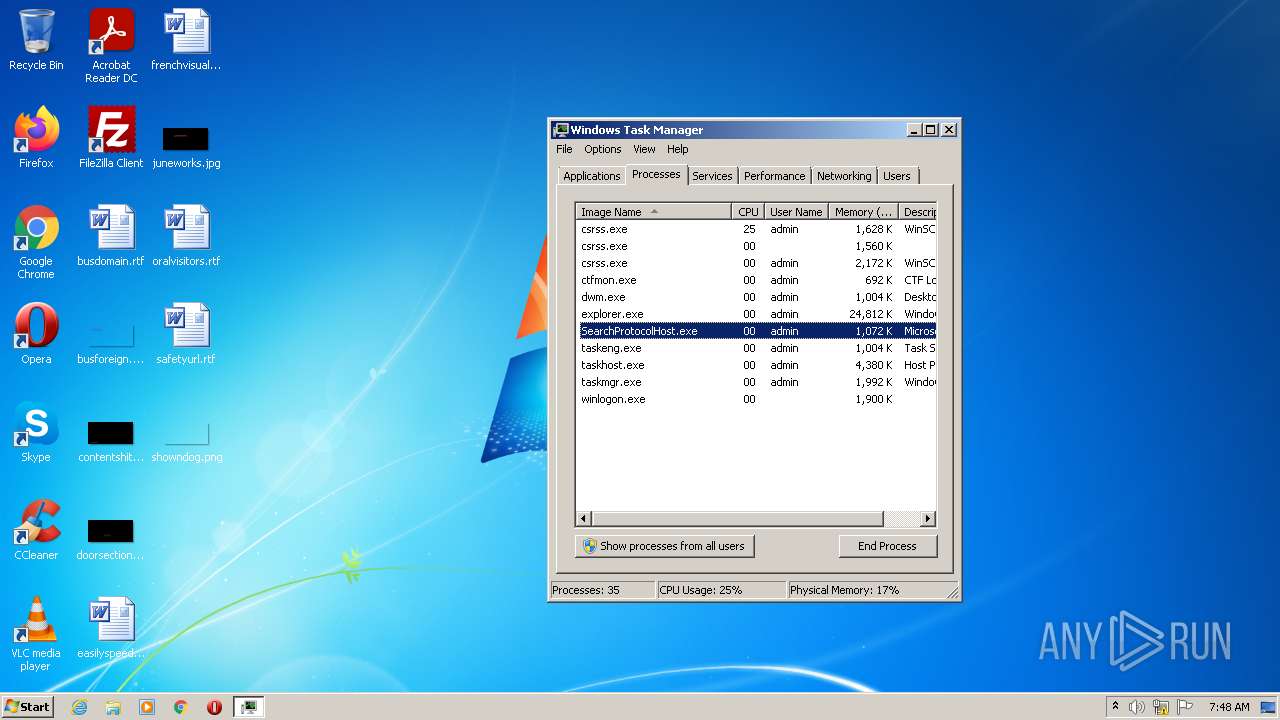
| File name: | Set-up.exe |
| Full analysis: | https://app.any.run/tasks/b8c1b05c-840c-4404-9f3b-bd99ead6f62f |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | May 21, 2022, 06:45:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
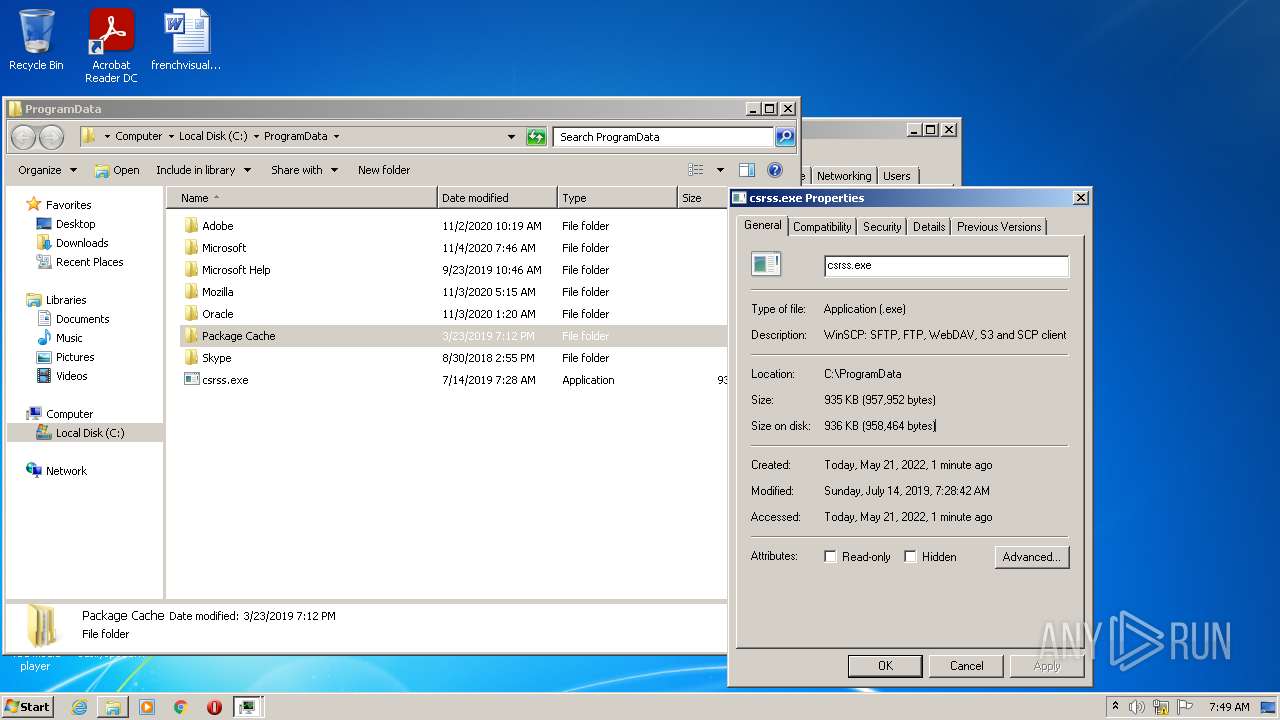
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 76C1DE0FE401C5203492CACF1F70713A |
| SHA1: | 07F06894960BB202CF6A54D5A1B56E879BCA03BB |
| SHA256: | F551D90C542E9D4FDBBE23F0E78DDA7B0B5C230F106291F41866E9D02C23F918 |
| SSDEEP: | 49152:pAI+leWJWXNsSVDqA79TKnkjXeeSgadOq0oCtFV:pAI+leKNSxqZkj1Sgrqux |
MALICIOUS
Drops executable file immediately after starts
- Set-up.exe (PID: 3760)
- svchost.exe (PID: 400)
- cmd.exe (PID: 2100)
- DllHost.exe (PID: 2612)
- cmd.exe (PID: 3180)
- DllHost.exe (PID: 3456)
Application was dropped or rewritten from another process
- svchost.exe (PID: 400)
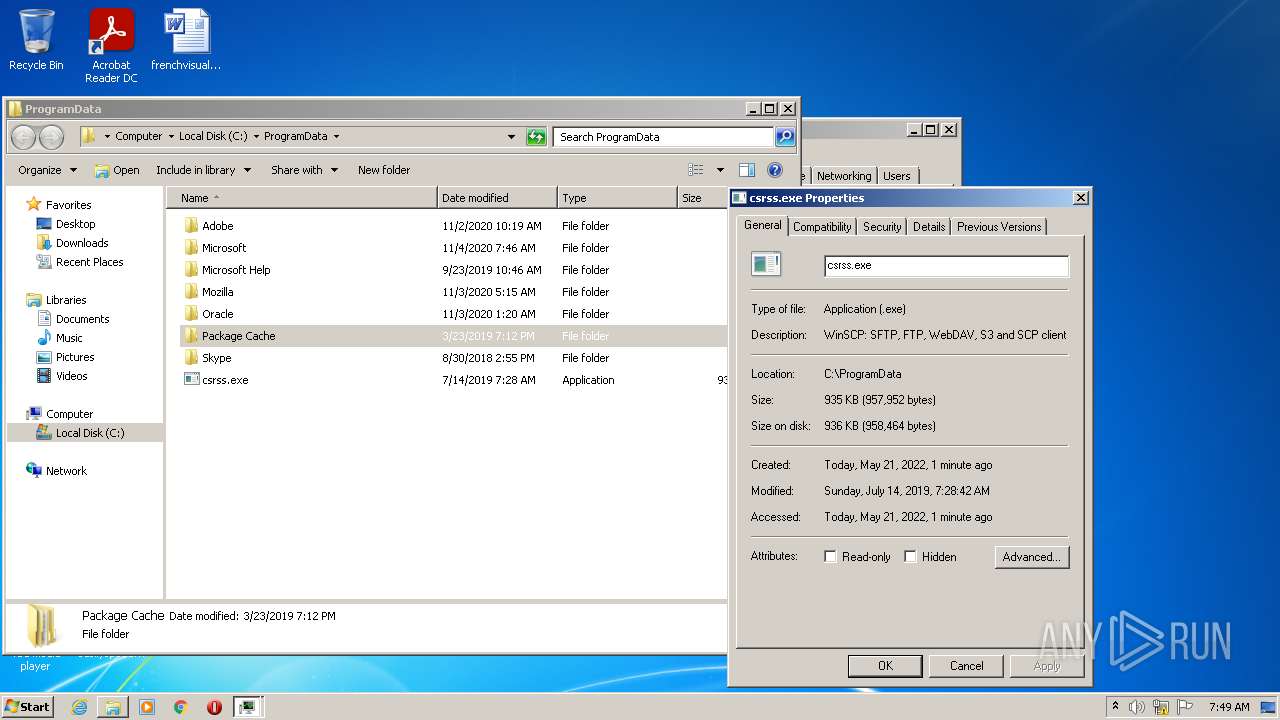
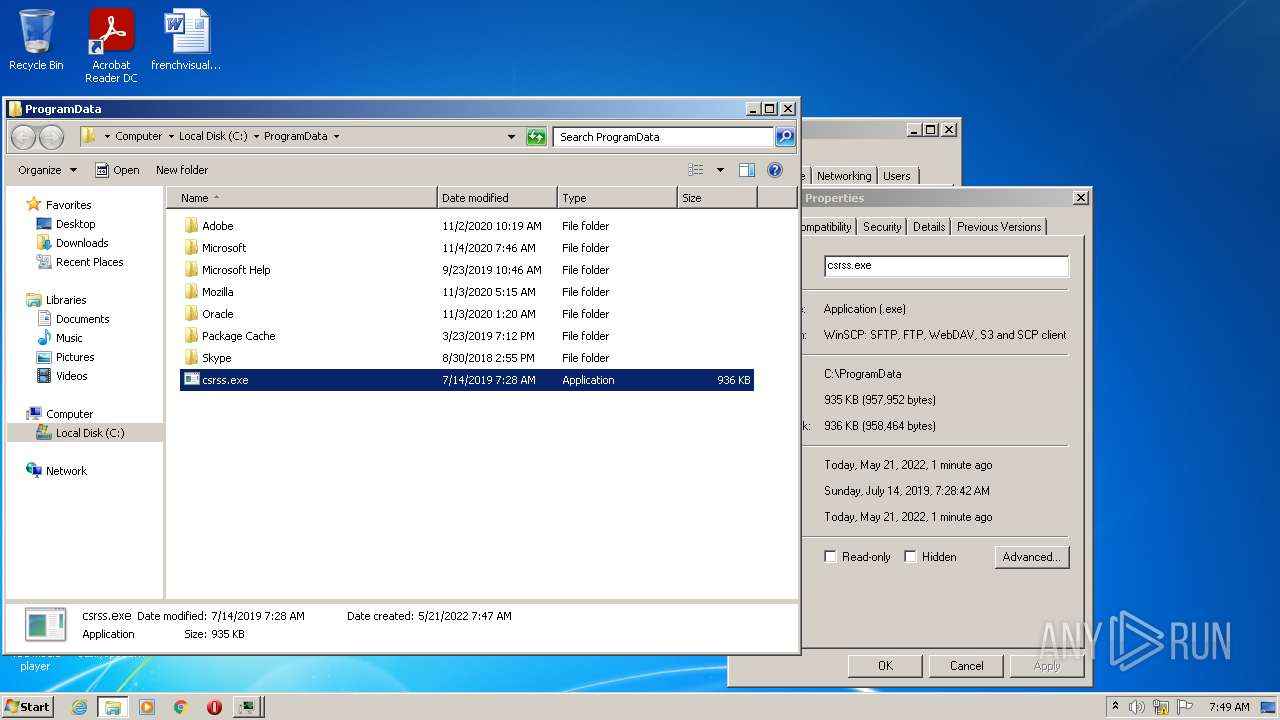
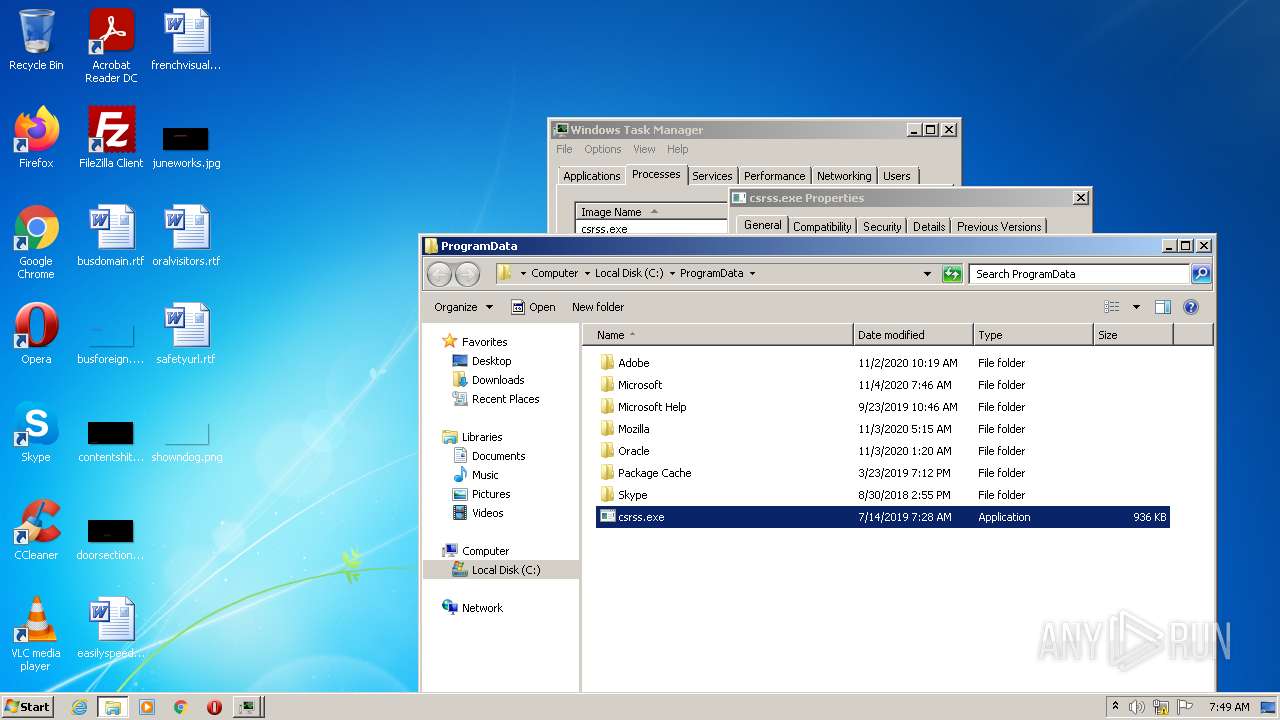
- csrss.exe (PID: 3608)
- csrss.exe (PID: 280)
- csrss.exe (PID: 2672)
- csrss.exe (PID: 3516)
- csrss.exe (PID: 1828)
- csrss.exe (PID: 1072)
- csrss.exe (PID: 3688)
- svchost.exe (PID: 3564)
Runs injected code in another process
- csrss.exe (PID: 3608)
- csrss.exe (PID: 280)
- csrss.exe (PID: 2672)
- csrss.exe (PID: 3516)
Application was injected by another process
- Explorer.EXE (PID: 1376)
AVEMARIA was detected
- csrss.exe (PID: 280)
- csrss.exe (PID: 3516)
Runs app for hidden code execution
- csrss.exe (PID: 280)
- csrss.exe (PID: 3516)
Loads dropped or rewritten executable
- dism.exe (PID: 1156)
- dism.exe (PID: 3292)
SUSPICIOUS
Checks supported languages
- Set-up.exe (PID: 3760)
- svchost.exe (PID: 400)
- Set-up.exe (PID: 3924)
- powershell.exe (PID: 2776)
- csrss.exe (PID: 3608)
- powershell.exe (PID: 604)
- csrss.exe (PID: 280)
- cmd.exe (PID: 2100)
- csrss.exe (PID: 2672)
- csrss.exe (PID: 3516)
- cmd.exe (PID: 3180)
- powershell.exe (PID: 2596)
- csrss.exe (PID: 1828)
- csrss.exe (PID: 1072)
- csrss.exe (PID: 3688)
- svchost.exe (PID: 3564)
Creates executable files which already exist in Windows
- Set-up.exe (PID: 3760)
Creates a directory in Program Files
- Set-up.exe (PID: 3760)
- svchost.exe (PID: 400)
Changes IE settings (feature browser emulation)
- Set-up.exe (PID: 3924)
Creates files in the program directory
- Set-up.exe (PID: 3760)
- svchost.exe (PID: 400)
Creates a software uninstall entry
- Set-up.exe (PID: 3760)
Reads the computer name
- Set-up.exe (PID: 3760)
- Set-up.exe (PID: 3924)
- svchost.exe (PID: 400)
- csrss.exe (PID: 3608)
- powershell.exe (PID: 2776)
- powershell.exe (PID: 604)
- csrss.exe (PID: 280)
- cmd.exe (PID: 2100)
- csrss.exe (PID: 2672)
- csrss.exe (PID: 3516)
- cmd.exe (PID: 3180)
- powershell.exe (PID: 2596)
- csrss.exe (PID: 1828)
- csrss.exe (PID: 1072)
- svchost.exe (PID: 3564)
- csrss.exe (PID: 3688)
Creates files in the user directory
- Set-up.exe (PID: 3760)
- Explorer.EXE (PID: 1376)
Executable content was dropped or overwritten
- Set-up.exe (PID: 3760)
- svchost.exe (PID: 400)
- cmd.exe (PID: 2100)
- DllHost.exe (PID: 2612)
- cmd.exe (PID: 3180)
- DllHost.exe (PID: 3456)
Drops a file with a compile date too recent
- Set-up.exe (PID: 3760)
- svchost.exe (PID: 400)
- cmd.exe (PID: 2100)
- DllHost.exe (PID: 2612)
- cmd.exe (PID: 3180)
- DllHost.exe (PID: 3456)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1376)
- taskmgr.exe (PID: 3860)
Executes PowerShell scripts
- svchost.exe (PID: 400)
- csrss.exe (PID: 3608)
- csrss.exe (PID: 2672)
Starts itself from another location
- svchost.exe (PID: 400)
Starts Internet Explorer
- Explorer.EXE (PID: 1376)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2704)
- iexplore.exe (PID: 2332)
Starts CMD.EXE for commands execution
- csrss.exe (PID: 280)
- csrss.exe (PID: 3516)
Executed via COM
- DllHost.exe (PID: 2612)
- DllHost.exe (PID: 1896)
- DllHost.exe (PID: 3456)
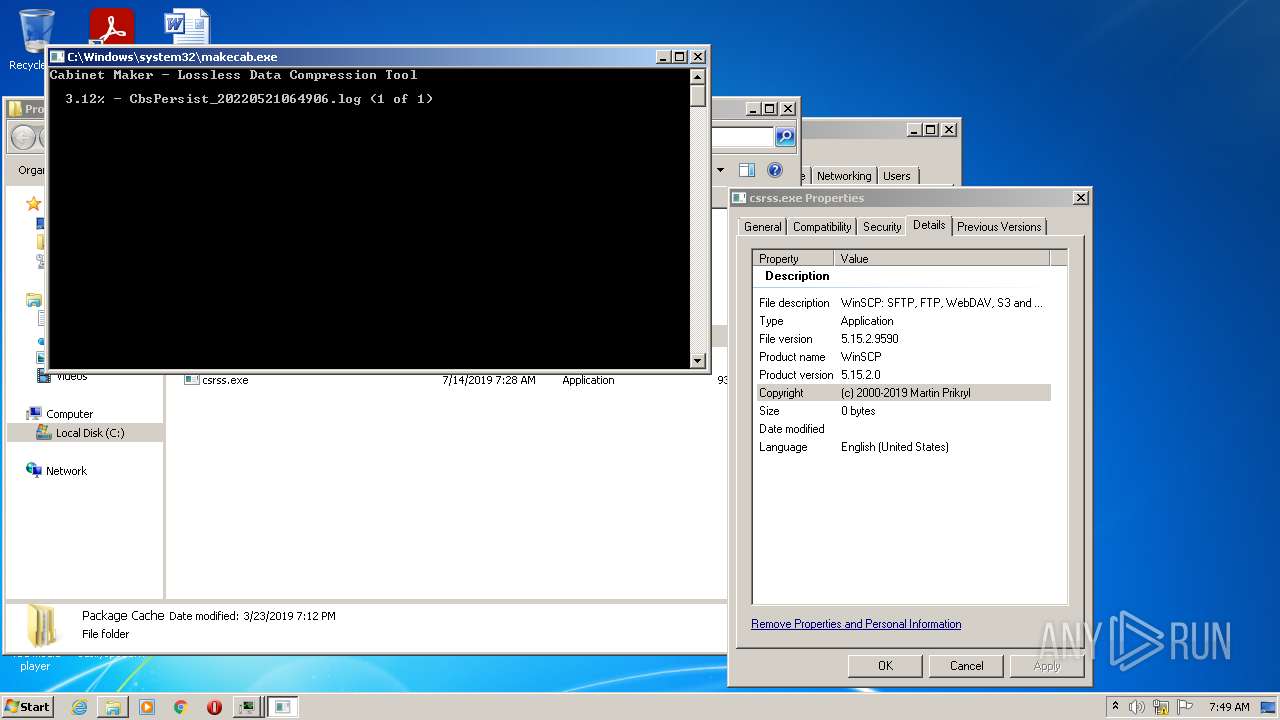
Creates files in the Windows directory
- pkgmgr.exe (PID: 3848)
- makecab.exe (PID: 4012)
INFO
Checks Windows Trust Settings
- Set-up.exe (PID: 3924)
- powershell.exe (PID: 2776)
- iexplore.exe (PID: 2208)
- powershell.exe (PID: 604)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 2332)
- powershell.exe (PID: 2596)
Reads settings of System Certificates
- Set-up.exe (PID: 3924)
- powershell.exe (PID: 2776)
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 3796)
- powershell.exe (PID: 604)
- iexplore.exe (PID: 2332)
- powershell.exe (PID: 2596)
Manual execution by user
- WINWORD.EXE (PID: 1408)
- taskmgr.exe (PID: 3860)
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 3796)
- csrss.exe (PID: 280)
- csrss.exe (PID: 3516)
- csrss.exe (PID: 1072)
- csrss.exe (PID: 3688)
- svchost.exe (PID: 3564)
Reads Microsoft Office registry keys
- Explorer.EXE (PID: 1376)
- WINWORD.EXE (PID: 1408)
Creates files in the user directory
- WINWORD.EXE (PID: 1408)
- iexplore.exe (PID: 2332)
Checks supported languages
- WINWORD.EXE (PID: 1408)
- Explorer.EXE (PID: 1376)
- taskmgr.exe (PID: 3860)
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 2704)
- iexplore.exe (PID: 2332)
- iexplore.exe (PID: 3796)
- DllHost.exe (PID: 2612)
- dism.exe (PID: 1156)
- pkgmgr.exe (PID: 3848)
- makecab.exe (PID: 4012)
- DllHost.exe (PID: 1896)
- DllHost.exe (PID: 3456)
- dism.exe (PID: 3292)
- makecab.exe (PID: 3604)
- pkgmgr.exe (PID: 2416)
Reads the computer name
- WINWORD.EXE (PID: 1408)
- taskmgr.exe (PID: 3860)
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 2704)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 2332)
- DllHost.exe (PID: 2612)
- dism.exe (PID: 1156)
- DllHost.exe (PID: 1896)
- DllHost.exe (PID: 3456)
- dism.exe (PID: 3292)
Starts Microsoft Office Application
- Explorer.EXE (PID: 1376)
Application launched itself
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 3796)
Changes internet zones settings
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 3796)
Reads the date of Windows installation
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 3796)
Reads internet explorer settings
- iexplore.exe (PID: 2332)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3796)
Changes settings of System certificates
- iexplore.exe (PID: 3796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| LegalCopyright: | Adobe Inc. |
|---|---|
| FileVersion: | 4.8.2.478 |
| FileDescription: | Adobe Installer 4.8.2.478 Installation |
| CompanyName: | Adobe Inc. |
| Comments: | - |
| CharacterSet: | Windows, Latin1 |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 0.0.0.0 |
| FileVersionNumber: | 4.8.2.478 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x25468 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 94720 |
| CodeSize: | 148992 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | Adobe Inc. |
| FileDescription: | Adobe Installer 4.8.2.478 Installation |
| FileVersion: | 4.8.2.478 |
| LegalCopyright: | Adobe Inc. |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x000244CC | 0x00024600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59443 |
DATA | 0x00026000 | 0x00002894 | 0x00002A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.79376 |
BSS | 0x00029000 | 0x000010F5 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0002B000 | 0x00001798 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.88555 |
.tls | 0x0002D000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0002E000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.204488 |
.reloc | 0x0002F000 | 0x00001884 | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.58665 |
.rsrc | 0x00031000 | 0x00011228 | 0x00011400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 4.4827 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.93923 | 886 | UNKNOWN | Russian - Russia | RT_MANIFEST |
50 | 4.35889 | 67624 | UNKNOWN | UNKNOWN | RT_ICON |
DVCLAL | 4 | 16 | UNKNOWN | UNKNOWN | RT_RCDATA |
PACKAGEINFO | 5.28362 | 272 | UNKNOWN | UNKNOWN | RT_RCDATA |
MAINICON | 2.01924 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
advapi32.dll |
cabinet.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
winmm.dll |
Total processes
98
Monitored processes
35
Malicious processes
10
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\ProgramData\csrss.exe" | C:\ProgramData\csrss.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 400 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | Set-up.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 604 | powershell Add-MpPreference -ExclusionPath C:\ | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1072 | "C:\ProgramData\csrss.exe" | C:\ProgramData\csrss.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1156 | "C:\Windows\system32\dism.exe" /online /norestart /apply-unattend:"C:\Users\admin\AppData\Local\Temp\ellocnak.xml" | C:\Windows\system32\dism.exe | — | pkgmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1376 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1408 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\safetyurl.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1828 | "C:\ProgramData\csrss.exe" | C:\ProgramData\csrss.exe | dism.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1896 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2100 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | csrss.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
66 624
Read events
63 607
Write events
2 872
Delete events
145
Modification events
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Installer 4.8.2.478 | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | DisplayVersion |
Value: 4.8.2.478 | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | VersionMajor |
Value: 4 | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | VersionMinor |
Value: 8 | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | Publisher |
Value: Adobe Inc. | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Adobe Inc.\Adobe Installer\Uninstall.exe | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Adobe Inc.\Adobe Installer\Uninstall.exe | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Adobe Inc.\Adobe Installer\ | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | InstallSource |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (3760) Set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Adobe Installer 4.8.2.478 |
| Operation: | write | Name: | InstallDate |
Value: 20220521 | |||
Executable files
8
Suspicious files
31
Text files
11
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR697A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3760 | Set-up.exe | C:\Users\admin\AppData\Local\Temp\$inst\temp_0.tmp | compressed | |
MD5:— | SHA256:— | |||
| 3760 | Set-up.exe | C:\Program Files\Adobe Inc\Adobe Installer\Uninstall.ini | ini | |
MD5:— | SHA256:— | |||
| 1376 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\a7bd71699cd38d1c.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 1376 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 3760 | Set-up.exe | C:\Program Files\Adobe Inc\Adobe Installer\Set-up.exe | executable | |
MD5:— | SHA256:— | |||
| 1376 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\safetyurl.rtf.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3760 | Set-up.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:B7D1941132F5B23B0CF8868B0C556F87 | SHA256:FDC1E685156902BDC98DAFA83D13C08C0CD2EC816A5ACD3598615F290F5239F0 | |||
| 3760 | Set-up.exe | C:\Users\admin\AppData\Local\Temp\$inst\2.tmp | compressed | |
MD5:8708699D2C73BED30A0A08D80F96D6D7 | SHA256:A32E0A83001D2C5D41649063217923DAC167809CAB50EC5784078E41C9EC0F0F | |||
| 3924 | Set-up.exe | C:\Users\admin\AppData\Local\Temp\CreativeCloud\ACC\AdobeDownload\HDInstaller.log | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
40
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2332 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2332 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEG3aTvFLTYzNCmxS2fUJutw%3D | US | der | 471 b | whitelisted |
2208 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2332 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2332 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFsL8ccV6MRJElibH7RYju4%3D | US | der | 471 b | whitelisted |
3796 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2332 | iexplore.exe | GET | 301 | 142.250.185.142:80 | http://google.com/ | US | html | 219 b | malicious |
2332 | iexplore.exe | GET | 302 | 142.250.186.100:80 | http://www.google.com/ | US | html | 231 b | malicious |
2332 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDExSUZ712qmxLhqE9UUaDV | US | der | 472 b | whitelisted |
2208 | iexplore.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6ba41c051313144d | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3796 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2332 | iexplore.exe | 142.250.185.142:80 | google.com | Google Inc. | US | whitelisted |
2332 | iexplore.exe | 142.250.186.100:80 | www.google.com | Google Inc. | US | whitelisted |
2332 | iexplore.exe | 142.250.186.100:443 | www.google.com | Google Inc. | US | whitelisted |
2332 | iexplore.exe | 142.250.185.67:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2332 | iexplore.exe | 142.250.186.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2332 | iexplore.exe | 172.217.23.110:443 | clients1.google.com | Google Inc. | US | whitelisted |
3608 | csrss.exe | 142.250.185.142:80 | google.com | Google Inc. | US | whitelisted |
2208 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2208 | iexplore.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
mangomanga.ddns.net |
| unknown |
www.google.com |
| malicious |
ocsp.pki.goog |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |