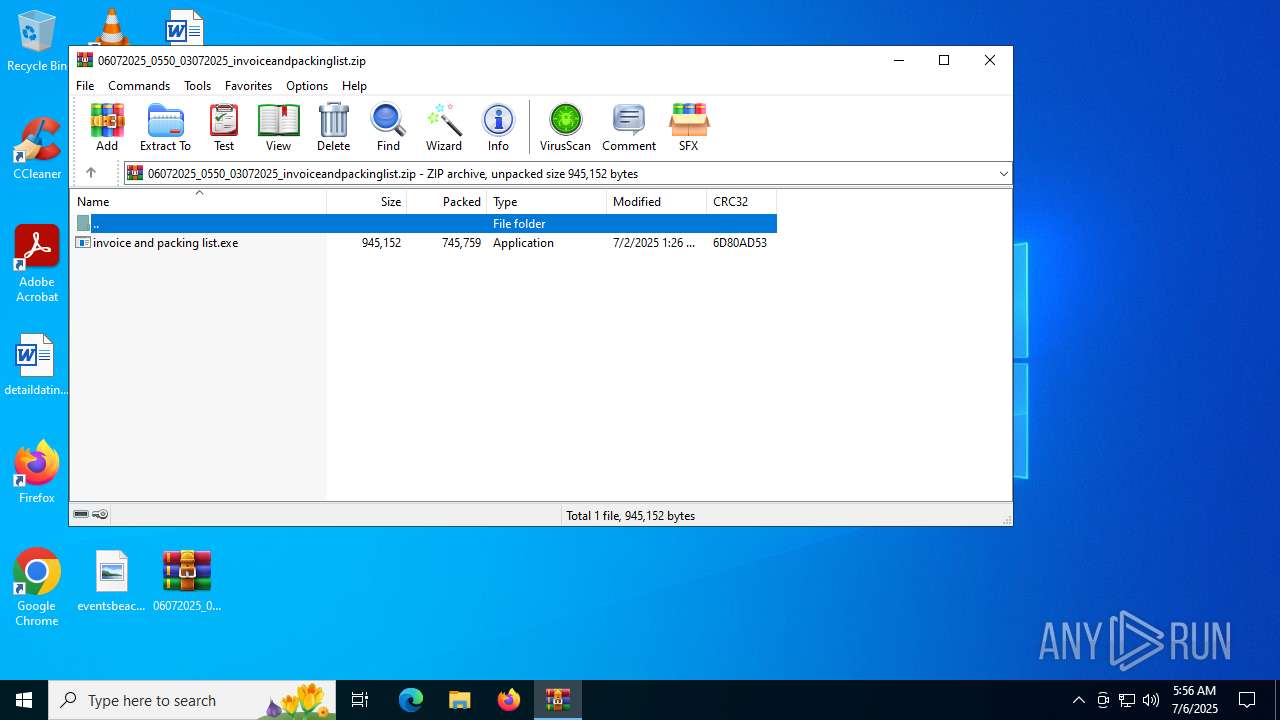
| File name: | 06072025_0550_03072025_invoiceandpackinglist.zip |
| Full analysis: | https://app.any.run/tasks/e09ed9a5-b0d3-49c8-8baf-fdeeefb8184d |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | July 06, 2025, 05:56:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C672E9B0C3D96974B0564D3E76084756 |
| SHA1: | 2A11D33B63F9CACC28A42F9E50554B1E7ED85E08 |
| SHA256: | F516B5EC80C3C35546D488896A1A119A26F0B6193B511A235DA3F1D2DBCC87C8 |
| SSDEEP: | 24576:UUAHRdQTnijaeP1G9+gAn0P4GIEMHYoa8LBDe6lxhbvt6YLQKc8EwVylK/jbLvqs:3AHRdQTnijaeP1G9+gAn0P4GIEMHYoau |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7080)
FORMBOOK has been detected (YARA)
- dialer.exe (PID: 6796)
Connects to the CnC server
- WinRAR.exe (PID: 7080)
FORMBOOK has been detected (SURICATA)
- WinRAR.exe (PID: 7080)
Actions looks like stealing of personal data
- dialer.exe (PID: 6796)
SUSPICIOUS
Application launched itself
- invoice and packing list.exe (PID: 6016)
Contacting a server suspected of hosting an CnC
- WinRAR.exe (PID: 7080)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7080)
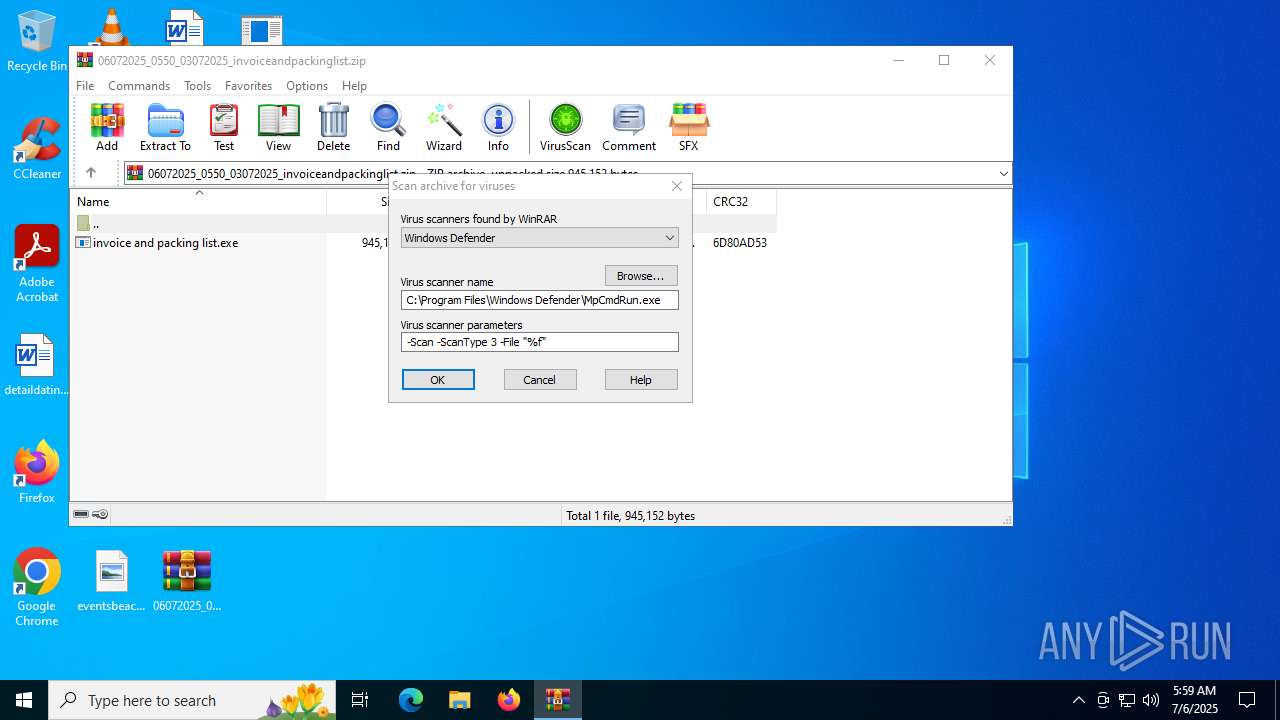
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7080)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7080)
INFO
Checks supported languages
- invoice and packing list.exe (PID: 6016)
- invoice and packing list.exe (PID: 1156)
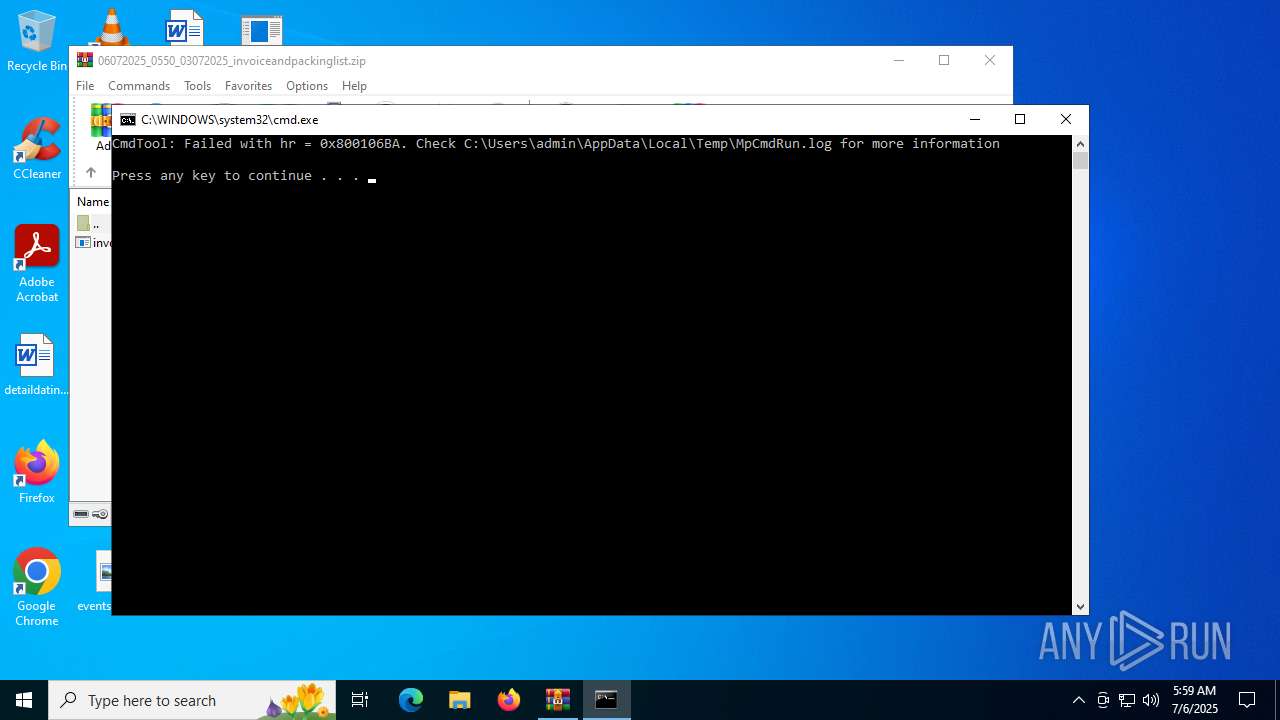
- MpCmdRun.exe (PID: 4844)
.NET Reactor protector has been detected
- invoice and packing list.exe (PID: 6016)
Reads the machine GUID from the registry
- invoice and packing list.exe (PID: 6016)
Manual execution by a user
- invoice and packing list.exe (PID: 6016)
Reads the computer name
- invoice and packing list.exe (PID: 6016)
- MpCmdRun.exe (PID: 4844)
Create files in a temporary directory
- dialer.exe (PID: 6796)
- MpCmdRun.exe (PID: 4844)
Reads security settings of Internet Explorer
- dialer.exe (PID: 6796)
Checks proxy server information
- slui.exe (PID: 3392)
Reads the software policy settings
- slui.exe (PID: 3392)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:02 01:26:30 |
| ZipCRC: | 0x6d80ad53 |
| ZipCompressedSize: | 745759 |
| ZipUncompressedSize: | 945152 |
| ZipFileName: | invoice and packing list.exe |
Total processes
141
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Users\admin\Desktop\invoice and packing list.exe" | C:\Users\admin\Desktop\invoice and packing list.exe | — | invoice and packing list.exe | |||||||||||
User: admin Company: FlexTech Fitness Solutions Integrity Level: MEDIUM Description: IronPulse Fitness Manager Exit code: 4294967295 Version: 4.7.2025.182 Modules
| |||||||||||||||
| 1156 | "C:\Users\admin\Desktop\invoice and packing list.exe" | C:\Users\admin\Desktop\invoice and packing list.exe | — | invoice and packing list.exe | |||||||||||
User: admin Company: FlexTech Fitness Solutions Integrity Level: MEDIUM Description: IronPulse Fitness Manager Exit code: 0 Version: 4.7.2025.182 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3392 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4312 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7080.37175" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5340 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7080.37175\Rar$Scan144835.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6016 | "C:\Users\admin\Desktop\invoice and packing list.exe" | C:\Users\admin\Desktop\invoice and packing list.exe | — | explorer.exe | |||||||||||
User: admin Company: FlexTech Fitness Solutions Integrity Level: MEDIUM Description: IronPulse Fitness Manager Exit code: 0 Version: 4.7.2025.182 Modules
| |||||||||||||||
| 6704 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | dialer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 6796 | "C:\Windows\SysWOW64\dialer.exe" | C:\Windows\SysWOW64\dialer.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Phone Dialer Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 173
Read events
8 159
Write events
14
Delete events
0
Modification events
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\06072025_0550_03072025_invoiceandpackinglist.zip | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7080.37175\06072025_0550_03072025_invoiceandpackinglist.zip\invoice and packing list.exe | executable | |
MD5:A773122356235222E62E119AC92666BC | SHA256:F33C9123DF28592B1E7855BCD9A32F1080AD1CDC54629EDD987A1B6738FB21D1 | |||
| 6796 | dialer.exe | C:\Users\admin\AppData\Local\Temp\F2J637-0 | binary | |
MD5:A45465CDCDC6CB30C8906F3DA4EC114C | SHA256:4412319EF944EBCCA9581CBACB1D4E1DC614C348D1DFC5D2FAAAAD863D300209 | |||
| 4844 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:6719798B7066F6AA01D6C274F119895D | SHA256:92F5C51F61317878C28FC9195583B9EC63493D86D24C08C96F52AFD54DC86513 | |||
| 7080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7080.37175\Rar$Scan144835.bat | text | |
MD5:76E997643A770903F6953401AB38B111 | SHA256:350A5365CBE23AB681D8AA0B7ABEE7E7A6ABA5846F00B9A36731A33B7F7FFD99 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
45
DNS requests
11
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5172 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
7080 | WinRAR.exe | GET | 200 | 13.248.169.48:80 | http://www.oufi.xyz/qcj1/?B5n=Dcd7tIf7&cp=TmHKNPIBlq9yD/ywazp5M+niSzu11BiiEtWTz7zmxoC8S05qp5OM/F3kWjS35eFcbxfS5d6dphYX6OYl8hWDx0Af6BeporhNnIcdwcfrLH1QYqBxIL2qk8wf5qondRLr1Y7/Xbo= | unknown | — | — | malicious |
7080 | WinRAR.exe | POST | 308 | 52.210.99.253:80 | http://www.jobzella.com/lb3g/ | unknown | — | — | whitelisted |
7080 | WinRAR.exe | POST | 308 | 52.210.99.253:80 | http://www.jobzella.com/lb3g/ | unknown | — | — | whitelisted |
7080 | WinRAR.exe | GET | 308 | 52.210.99.253:80 | http://www.jobzella.com/lb3g/?cp=1ZTy/Jnaz1epPNkSTvKK6G8bp4L0fjj8N0HWLD3ehT1ezelIC6zpkdLafFnyE0TBHVoitS9gimJrwZX70cxrTHT+TAK7HgMCagCK8oEDrclyh8egcl/bKVfSGTHyOOfwjZMyBPM=&B5n=Dcd7tIf7 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5172 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5172 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.oufi.xyz |
| malicious |
www.jobzella.com |
| whitelisted |
www.igeam.net |
| malicious |
www.qilux.site |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7080 | WinRAR.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
7080 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
7080 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
7080 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
7080 | WinRAR.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
7080 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
7080 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
7080 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
7080 | WinRAR.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
7080 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |