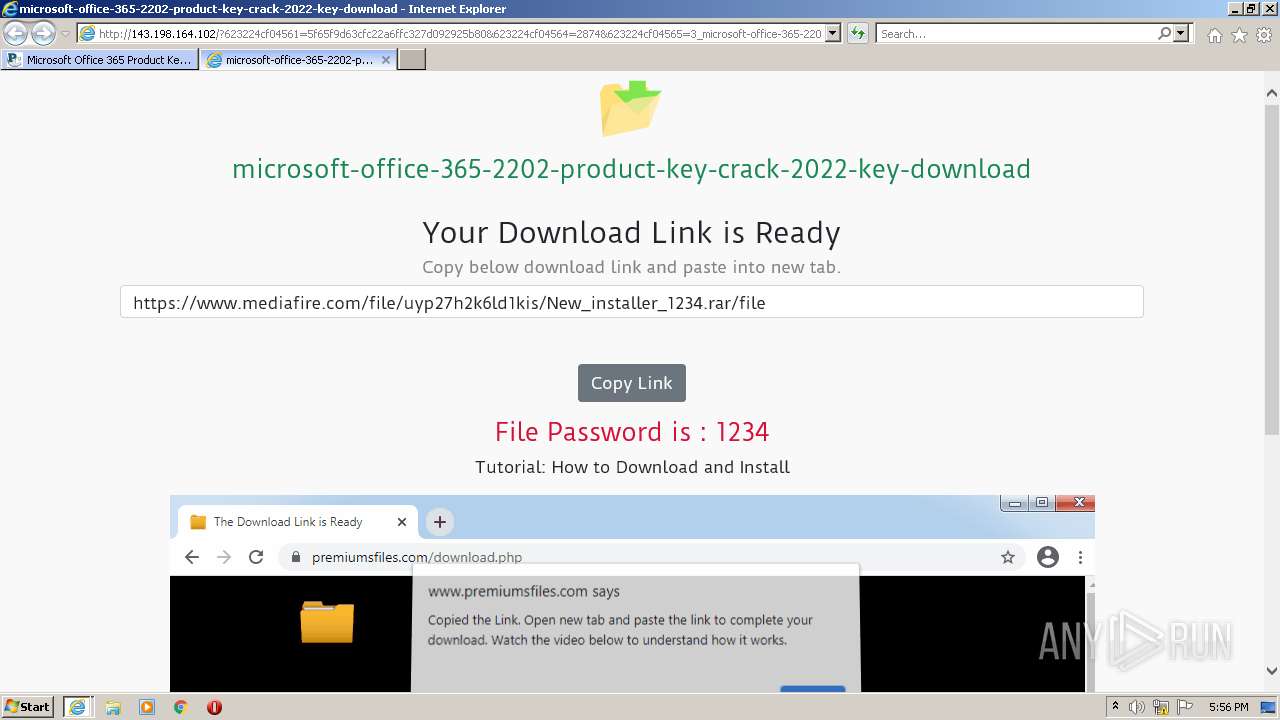
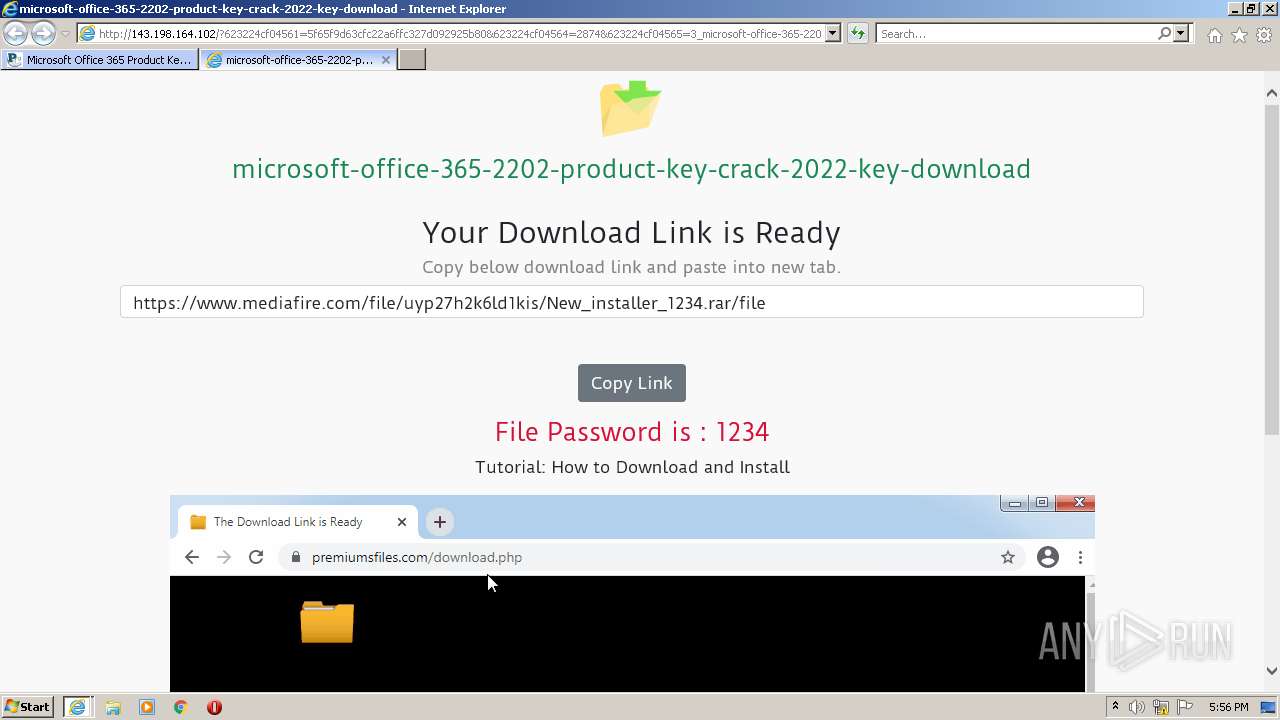
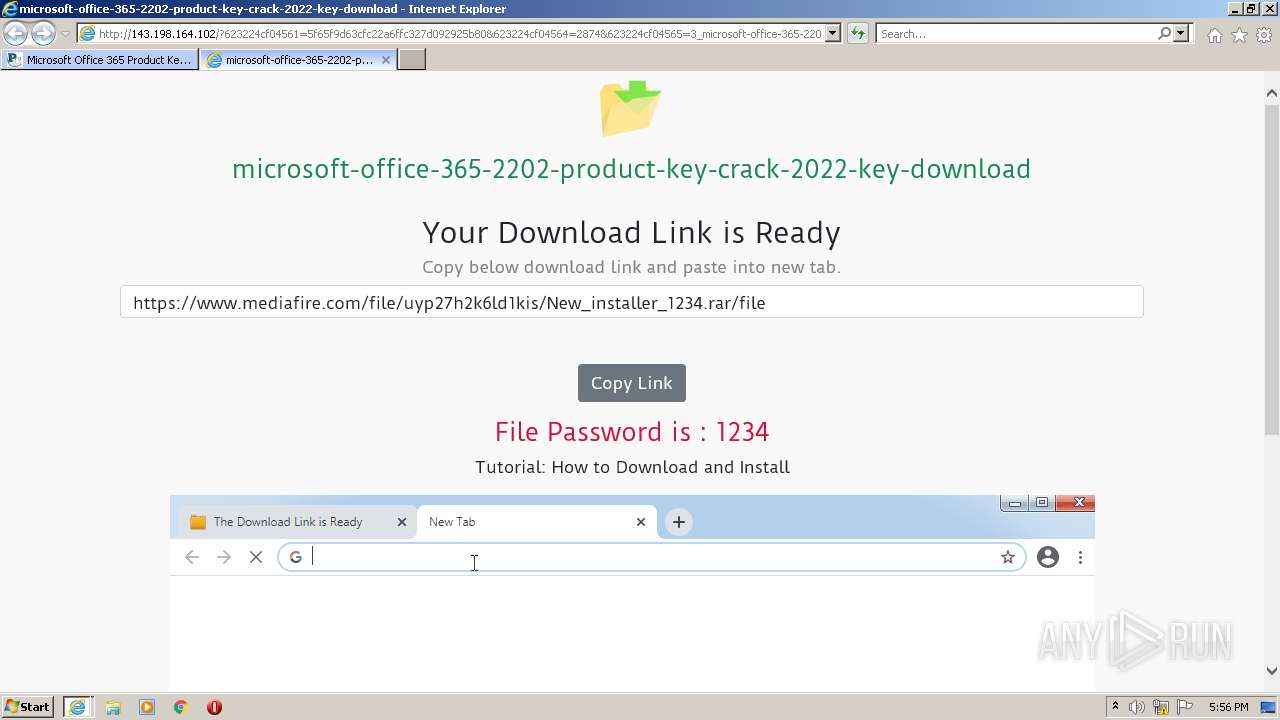
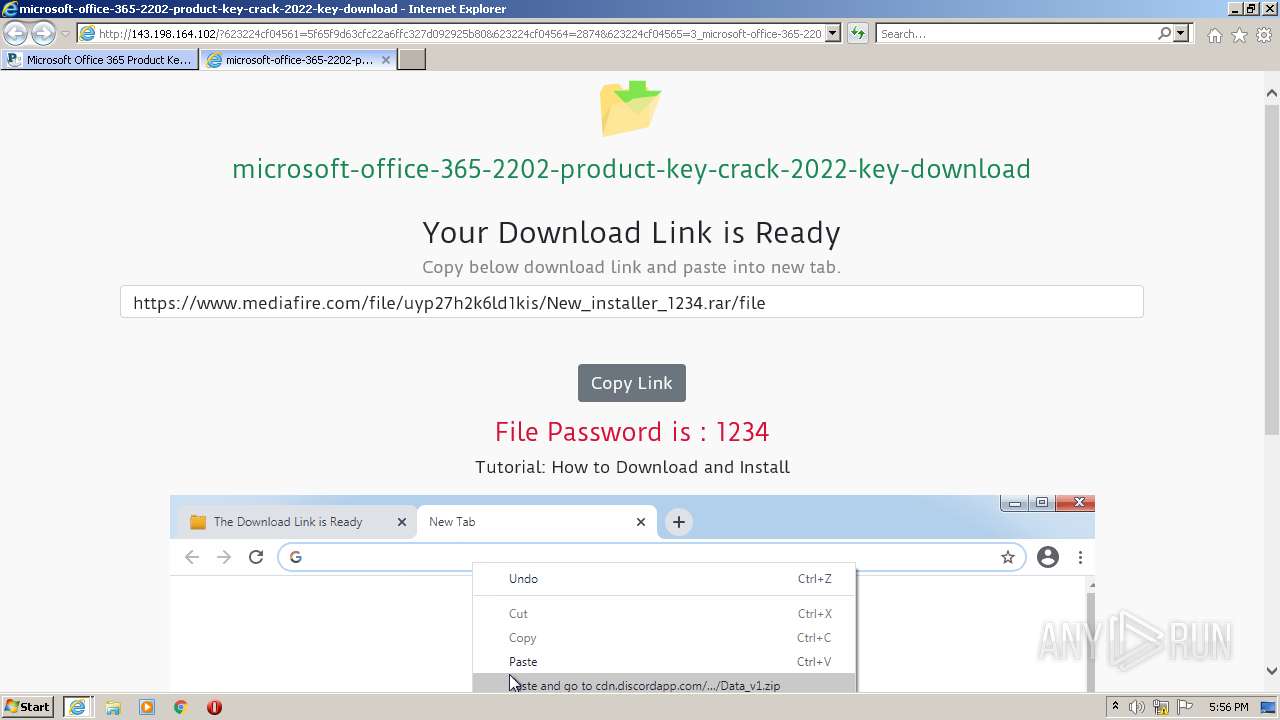
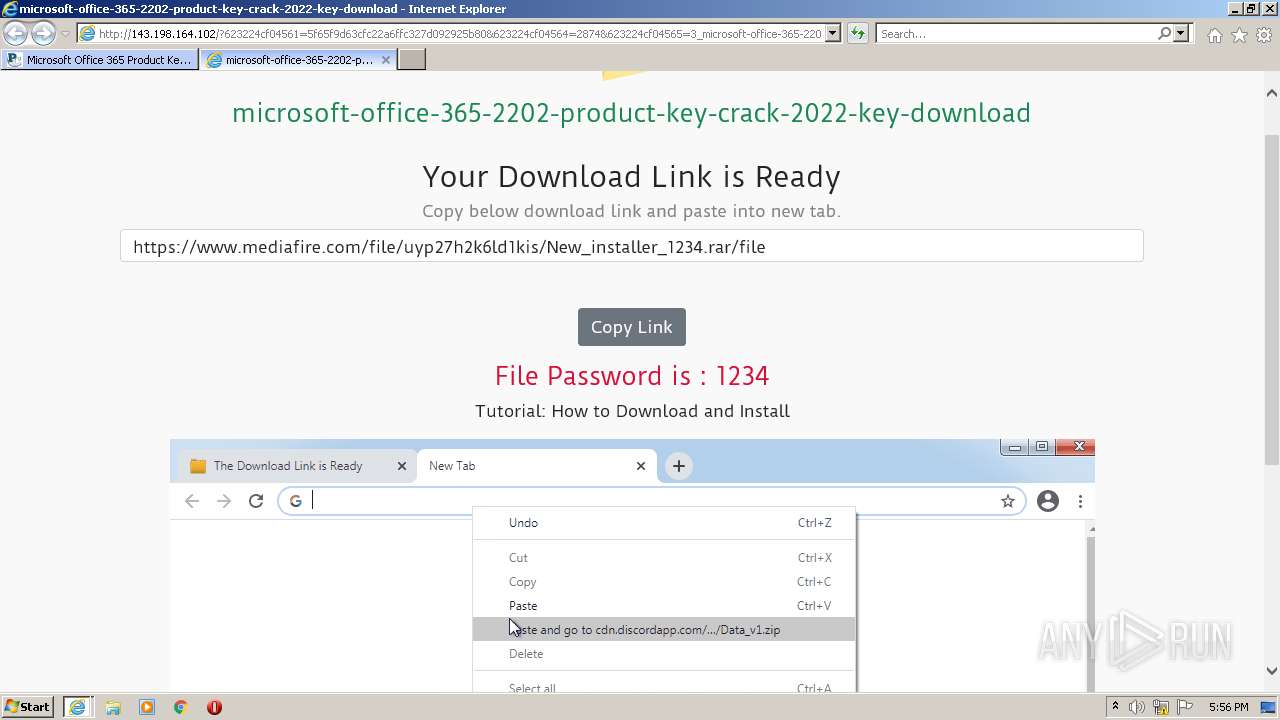
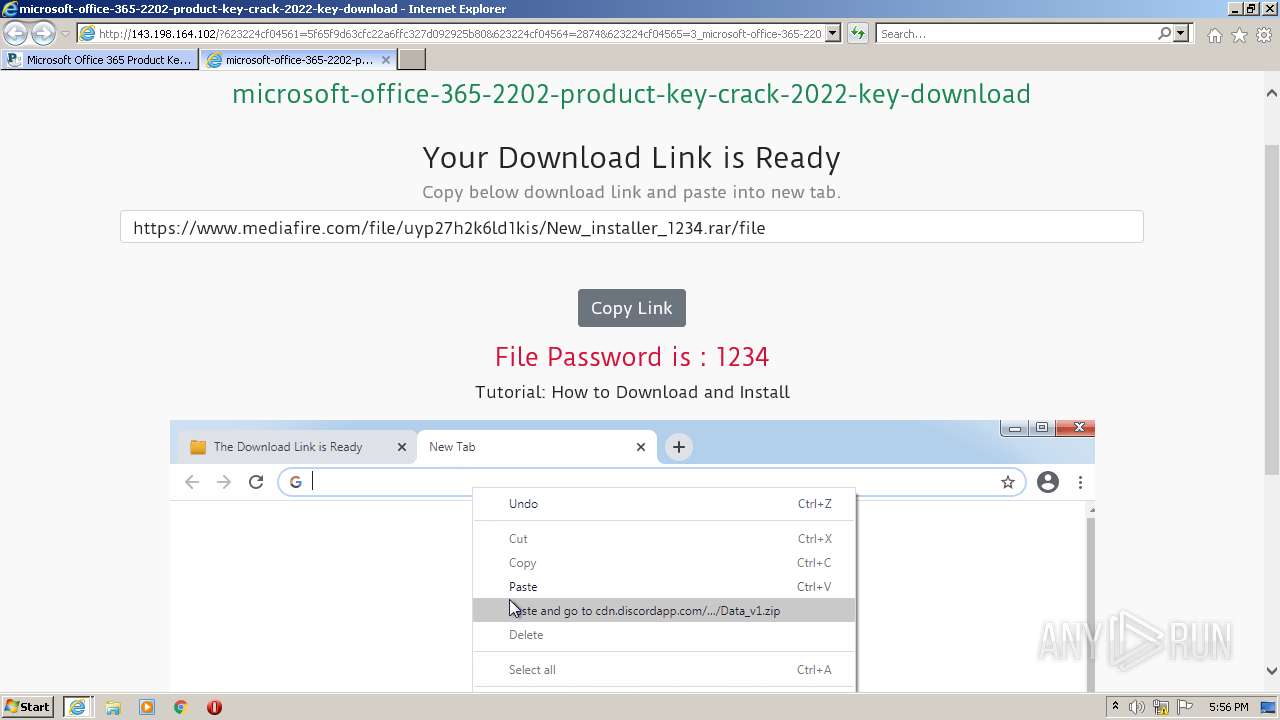
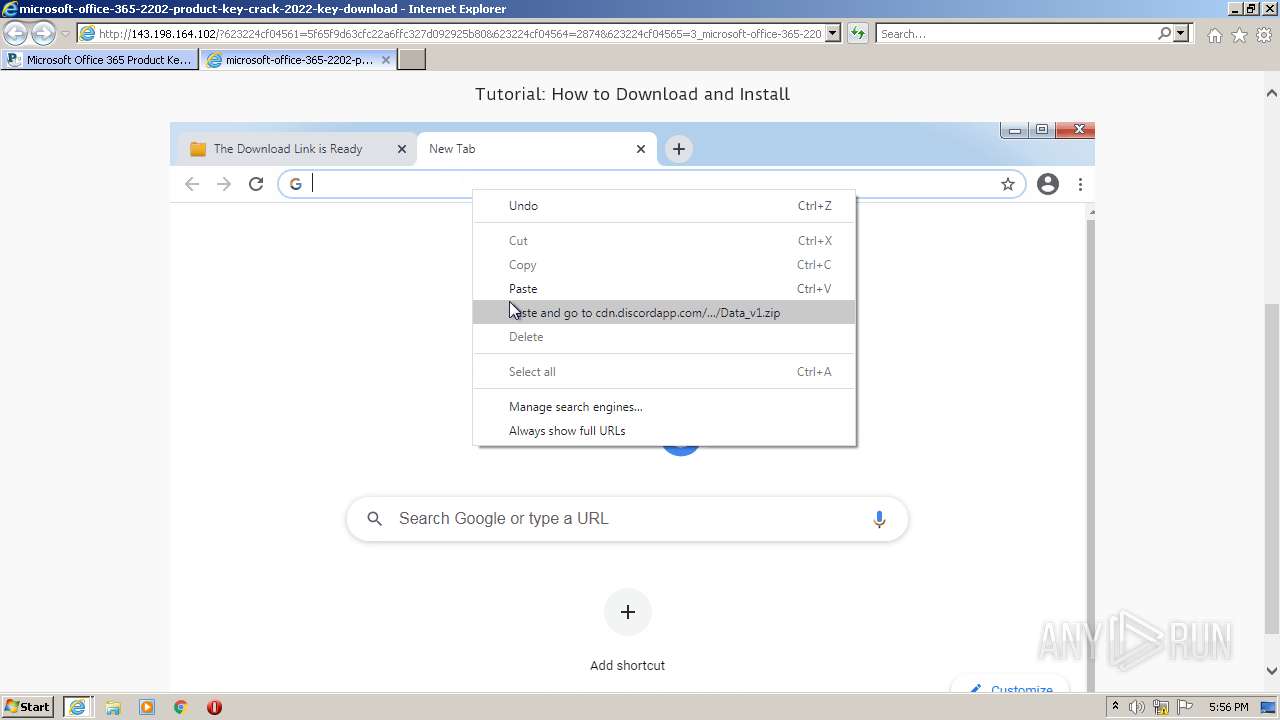
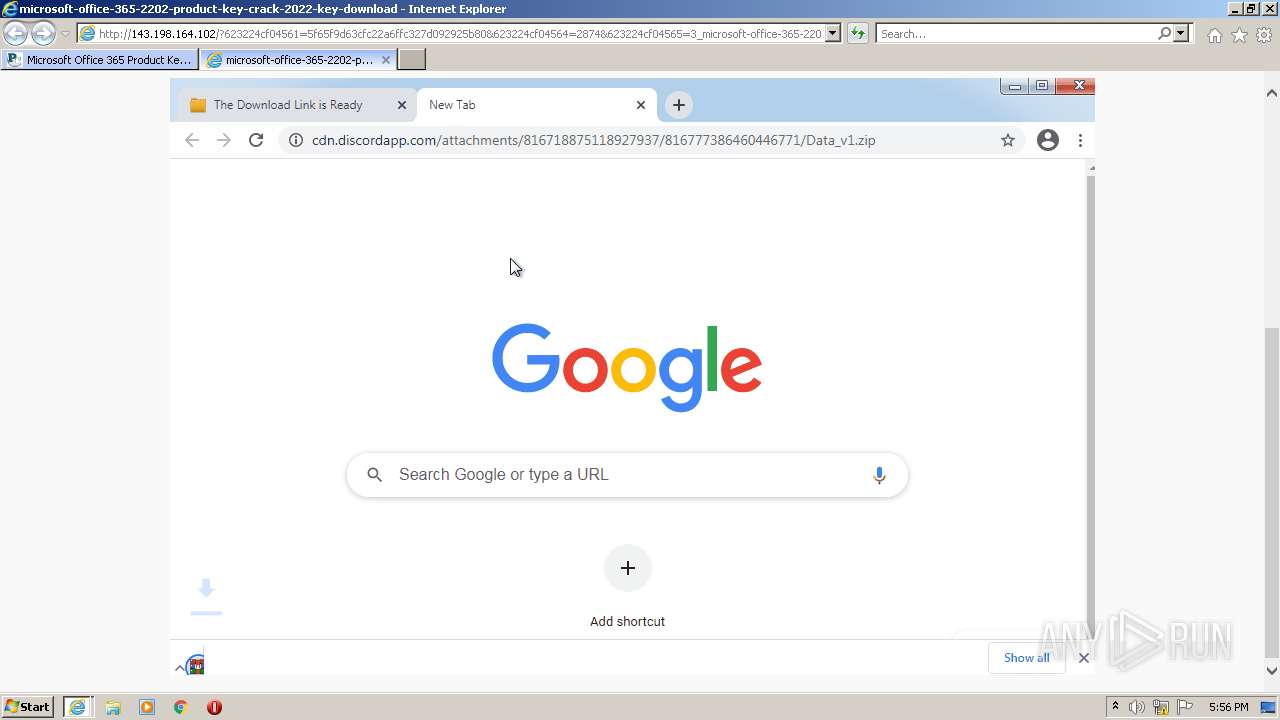
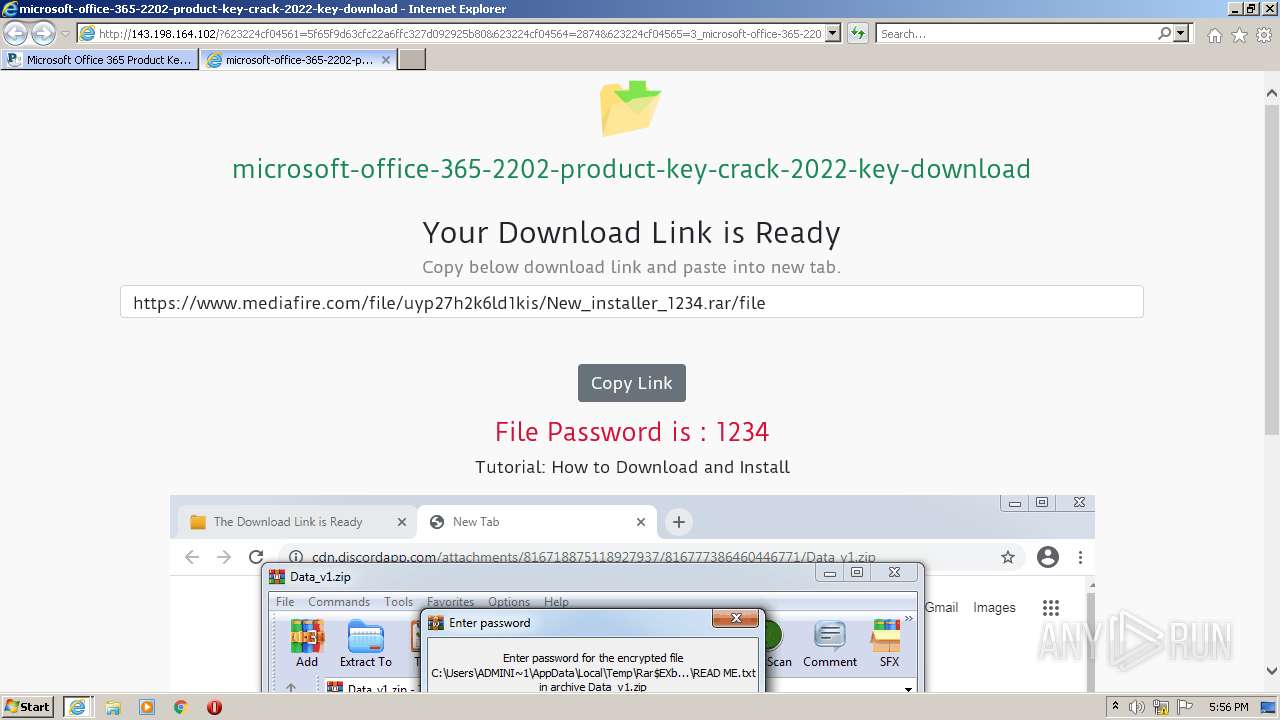
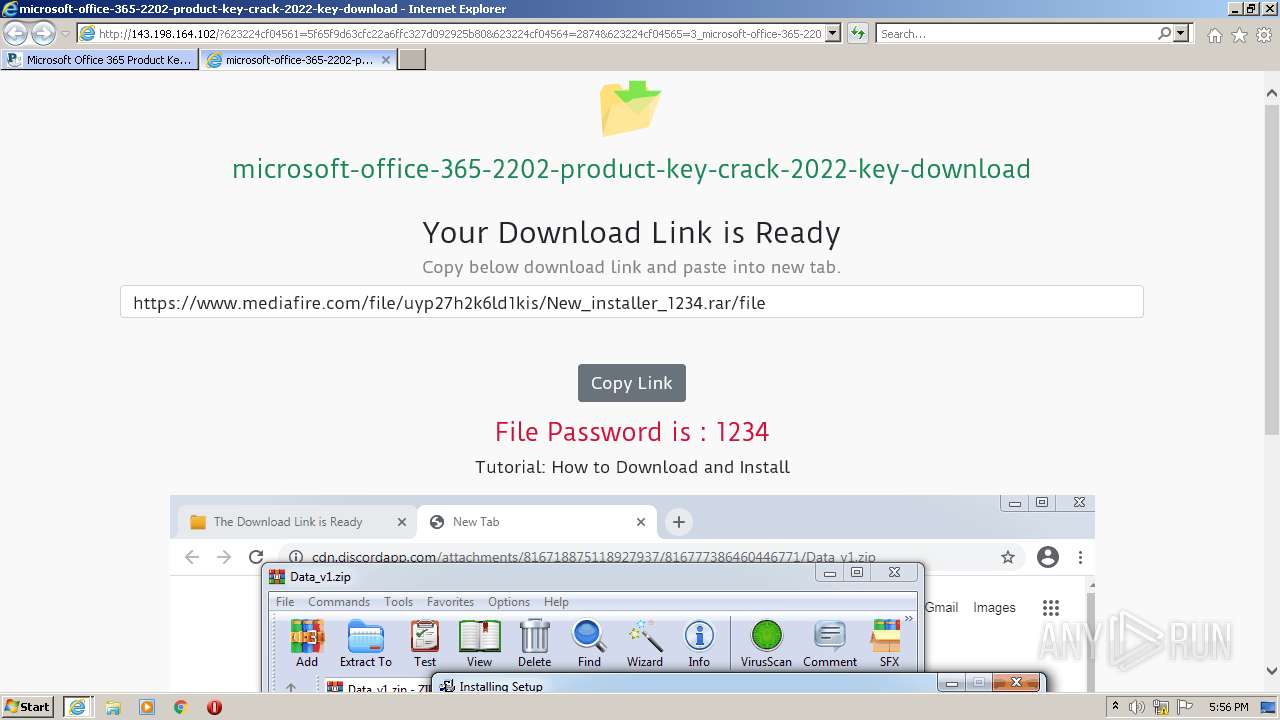
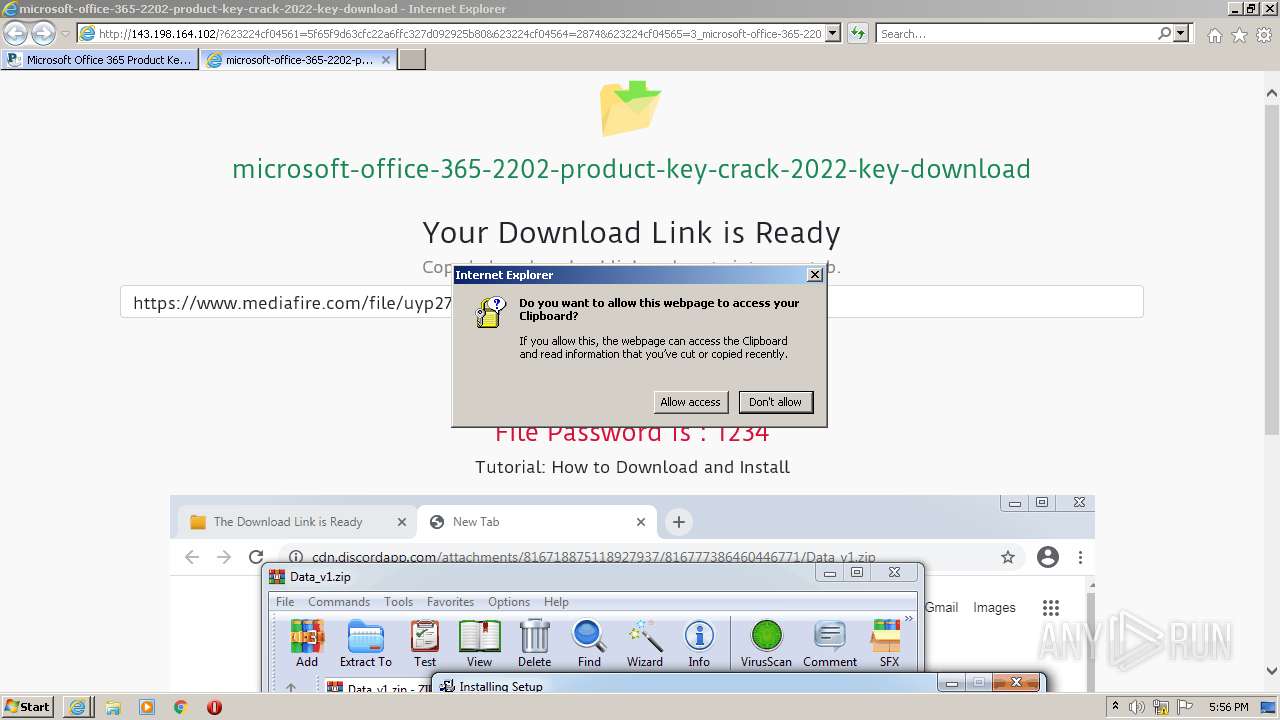
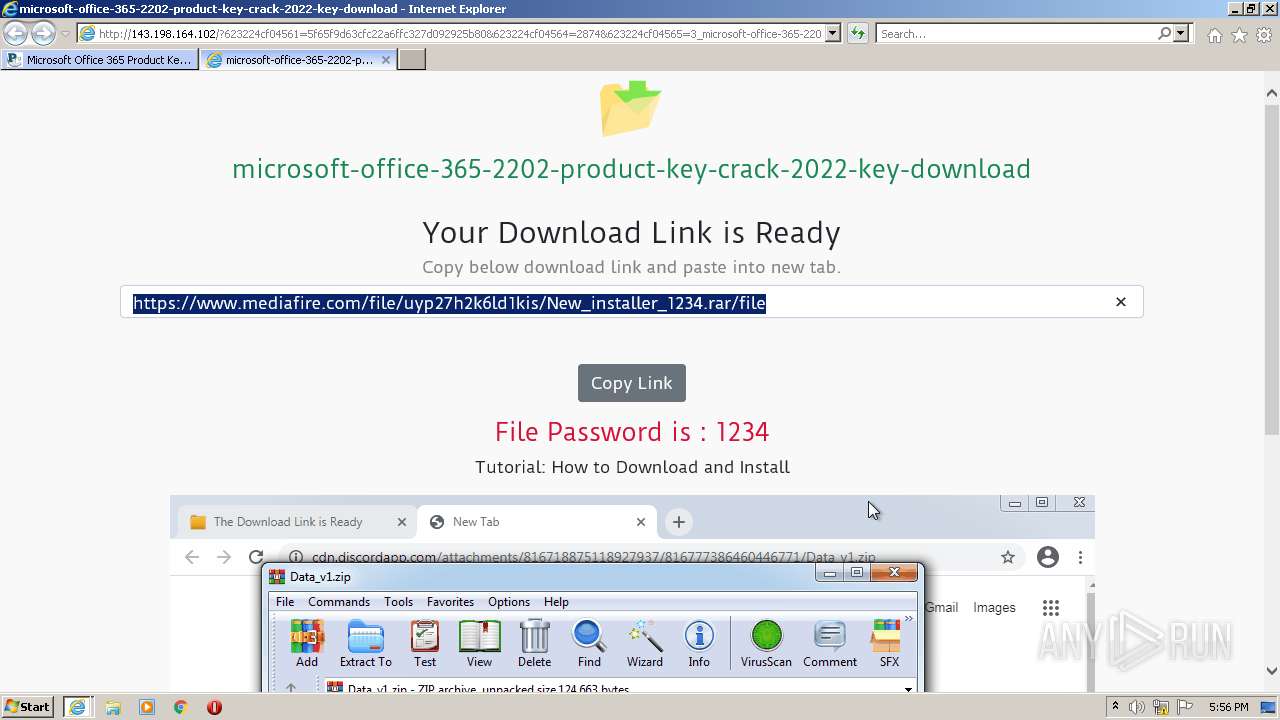
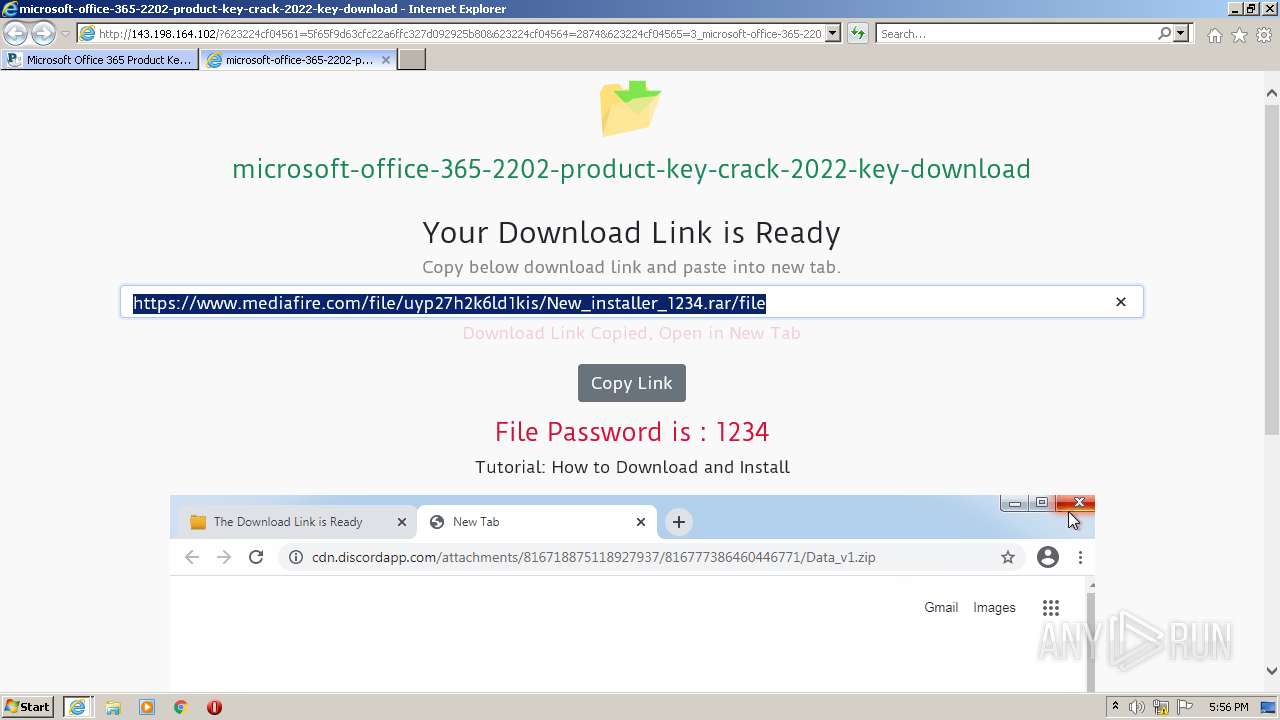
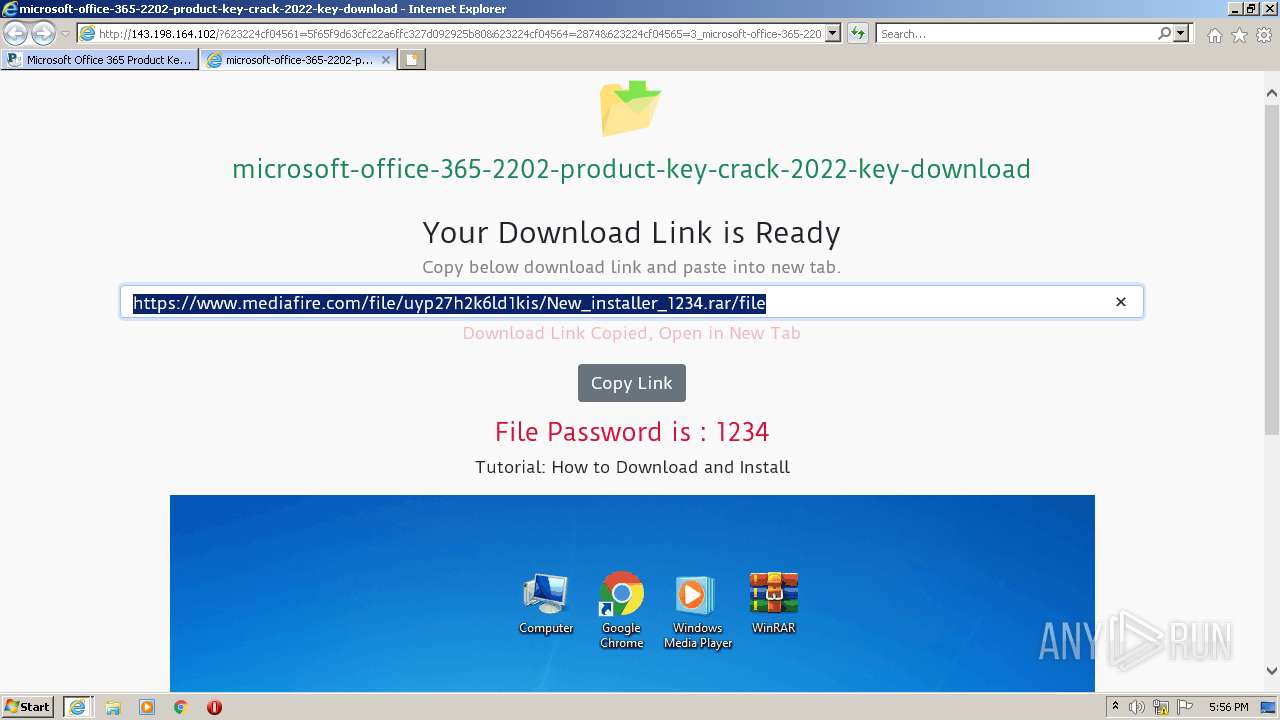
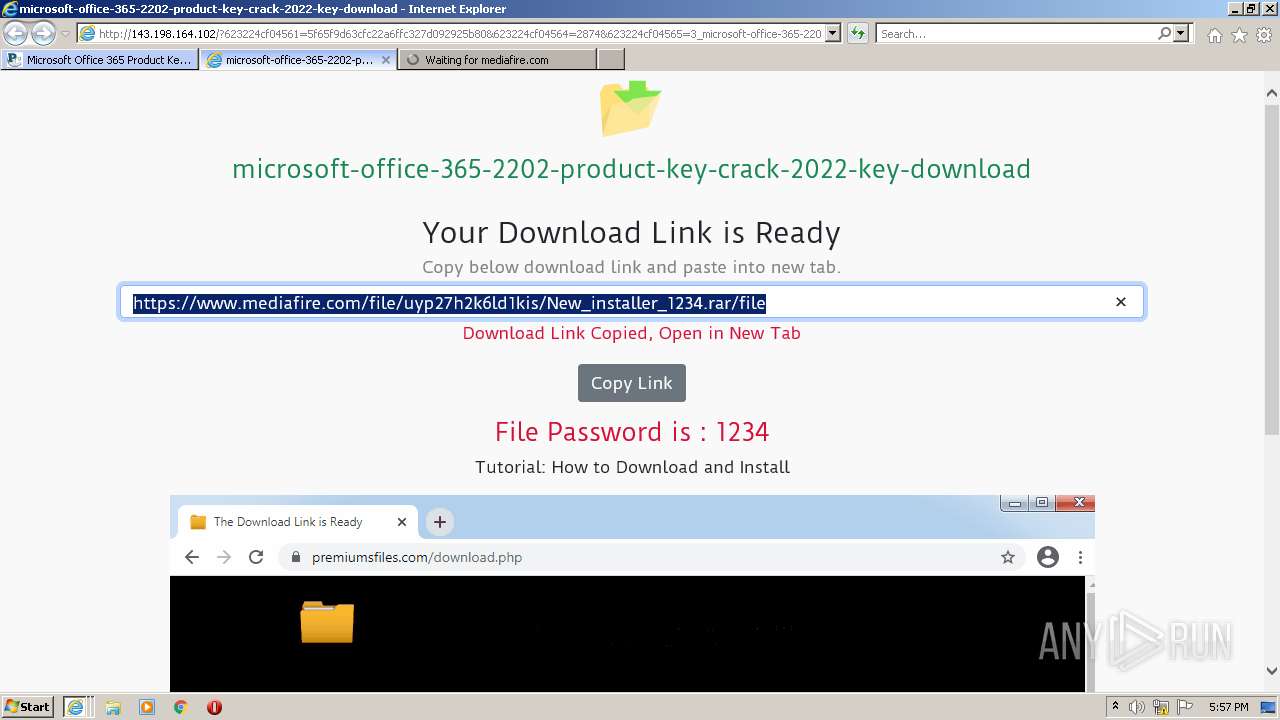
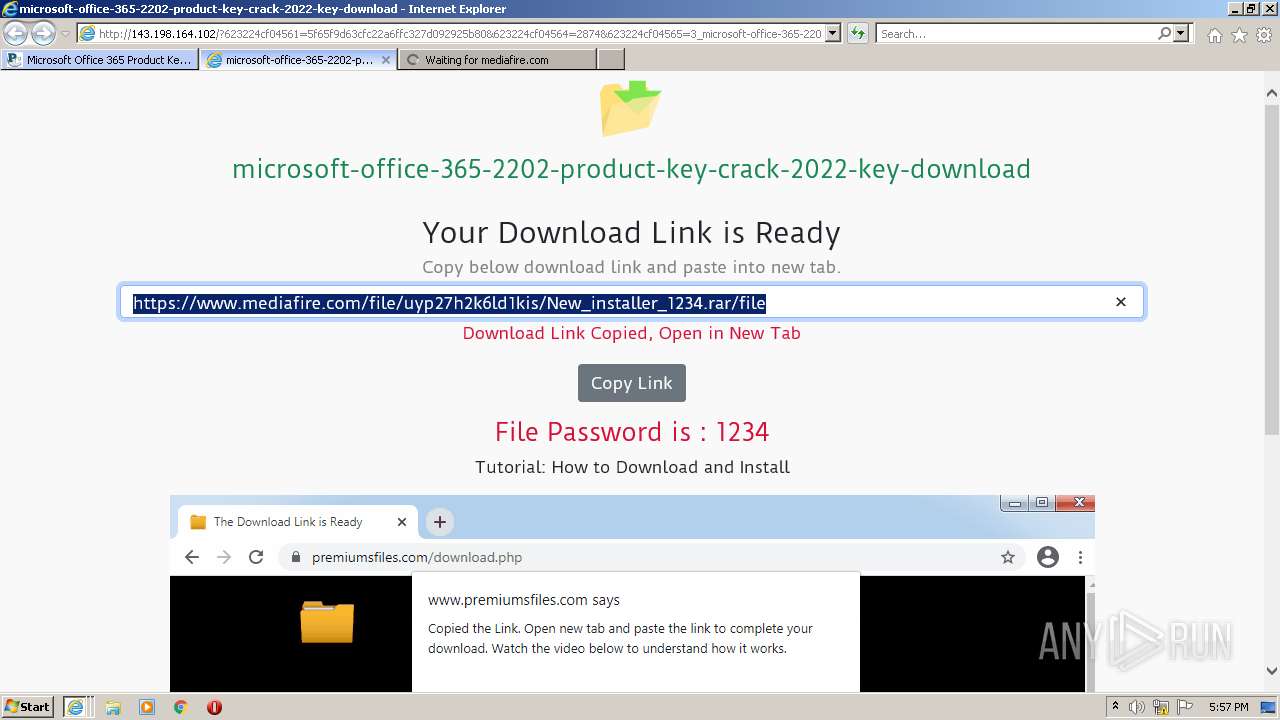
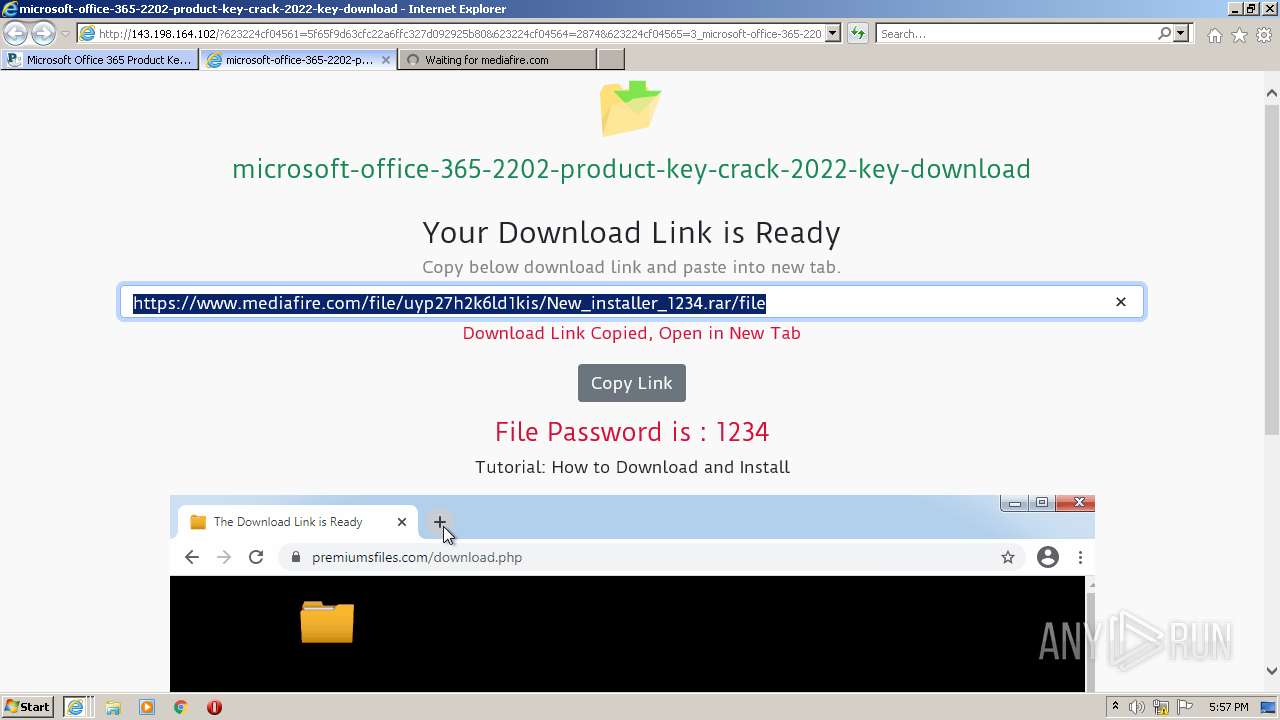
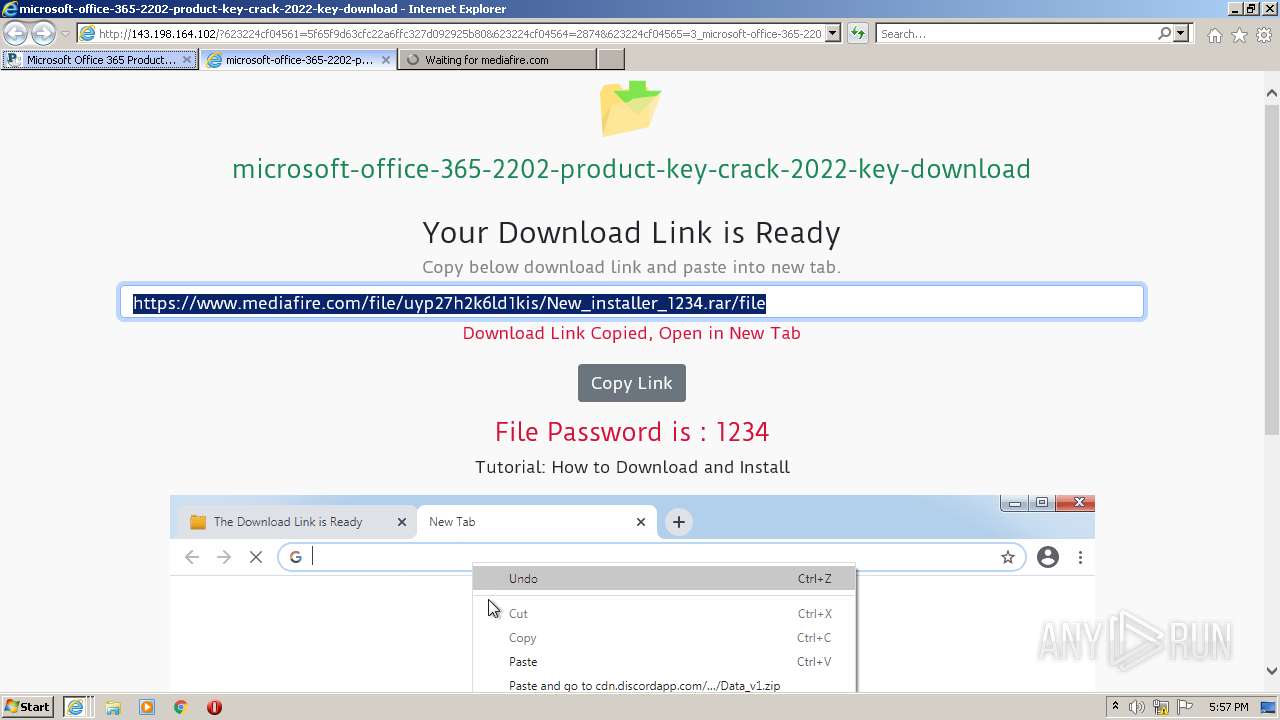
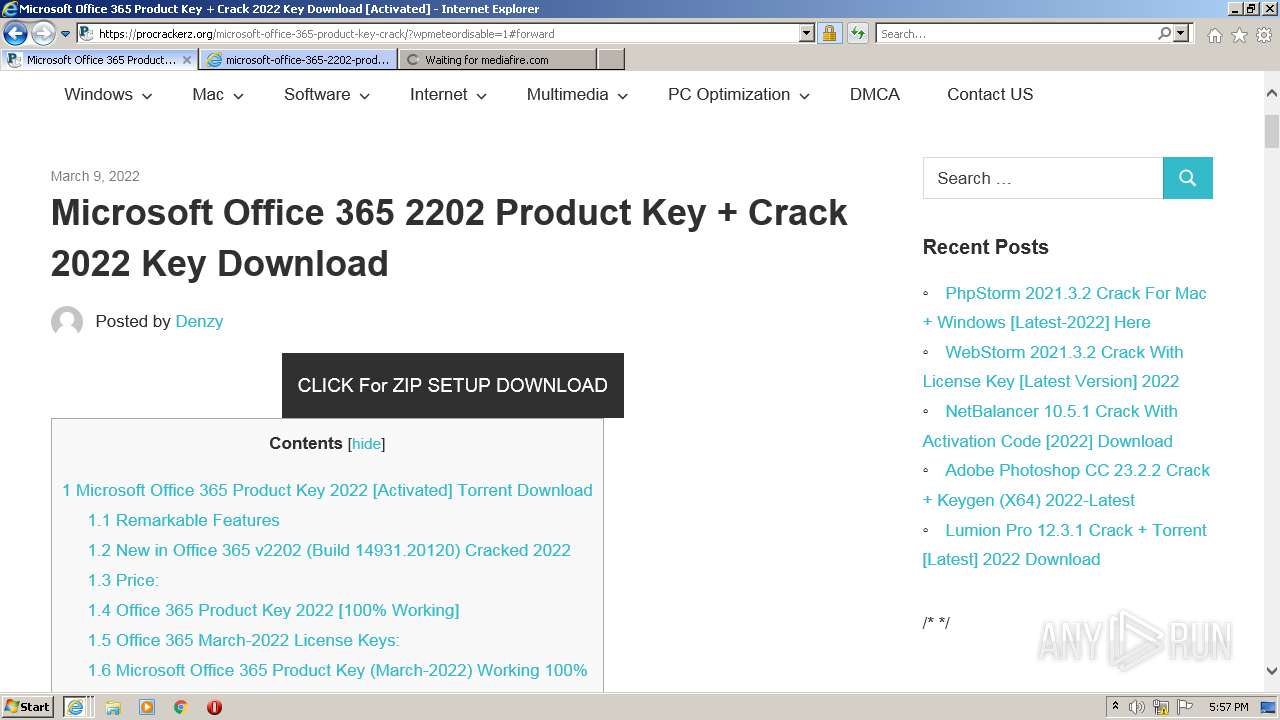
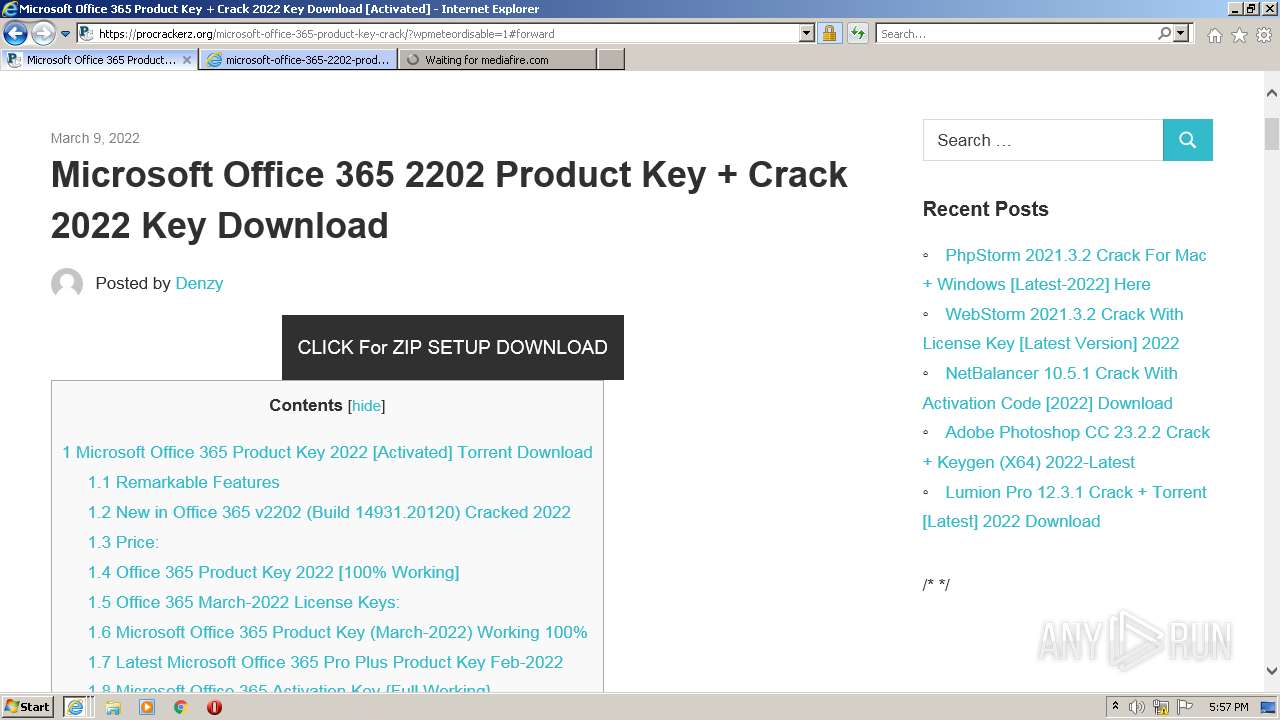
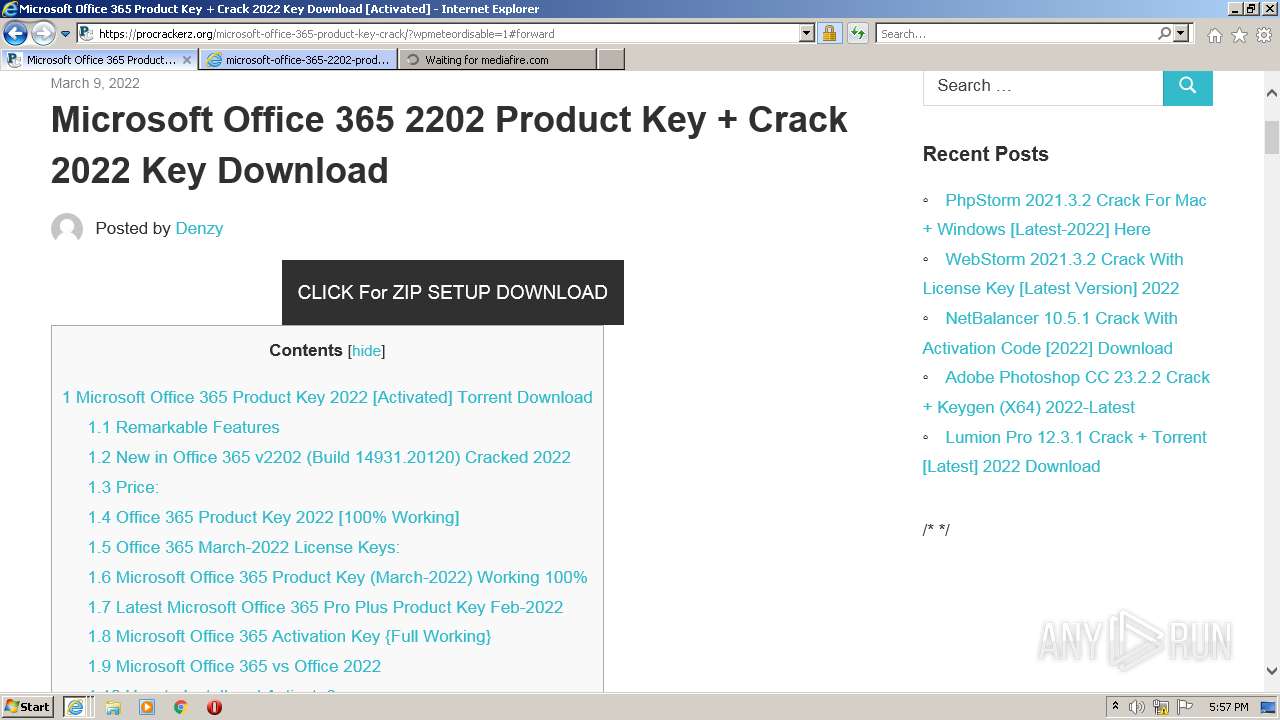
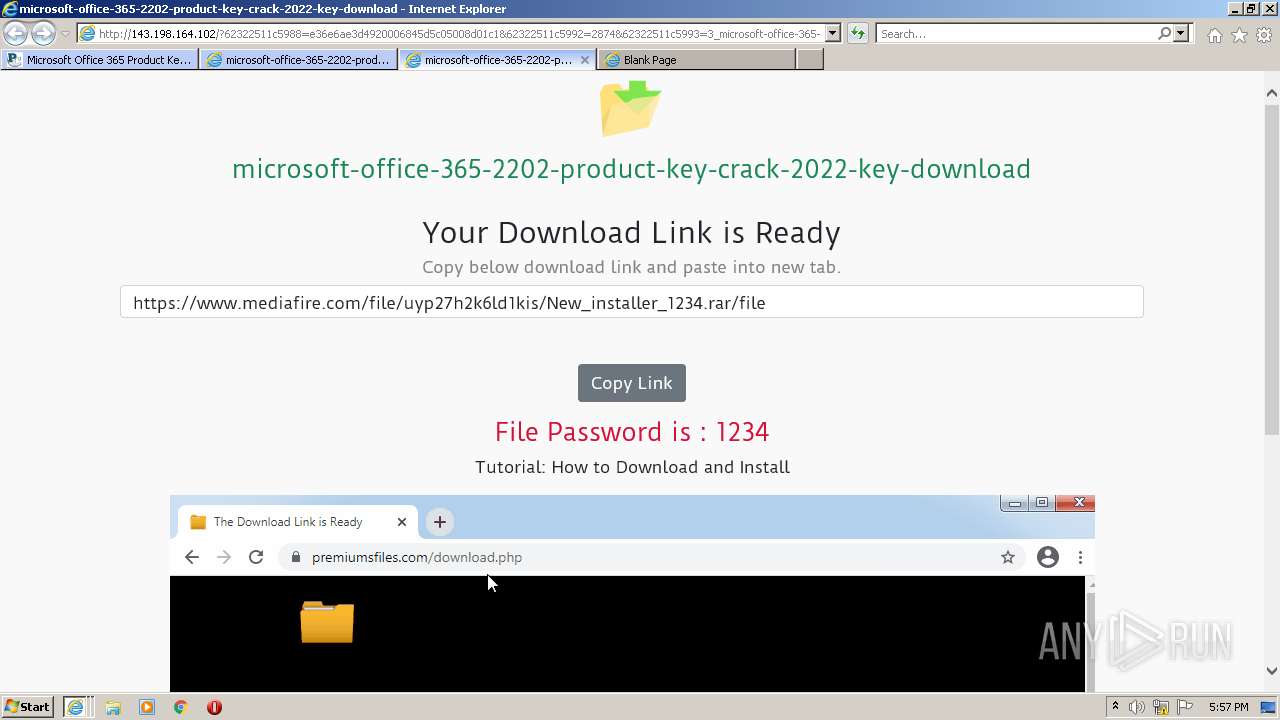
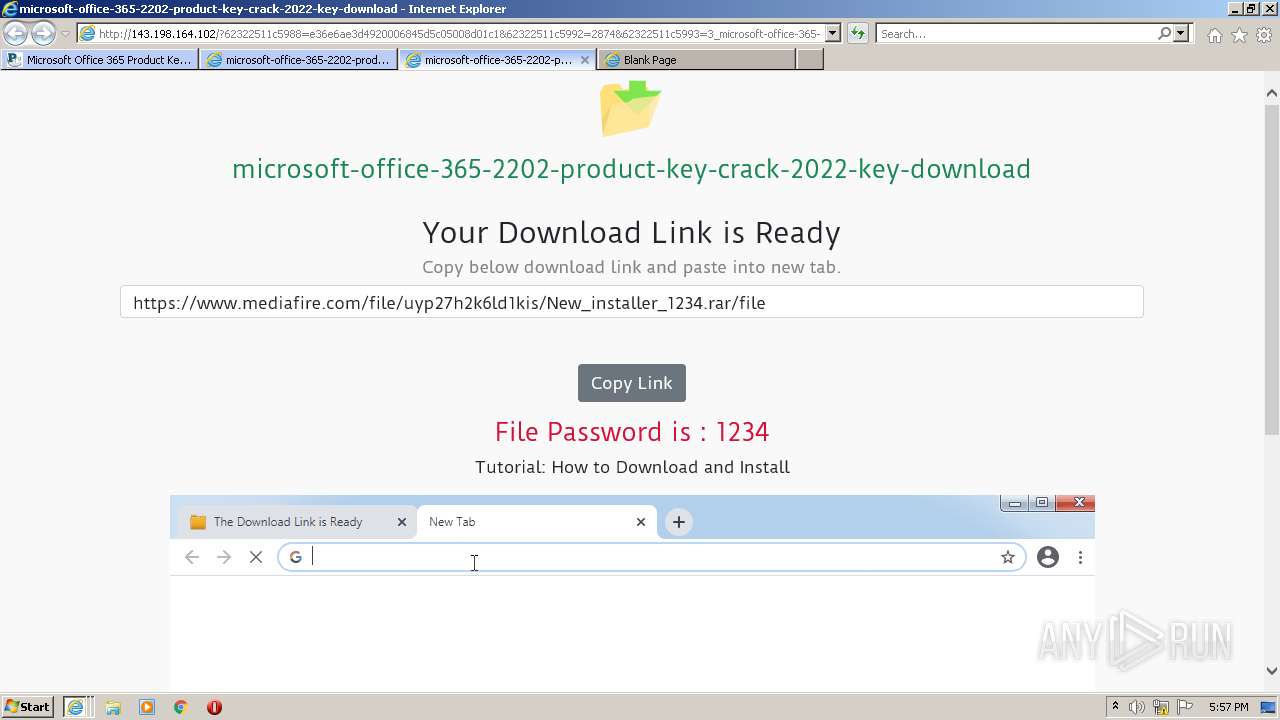
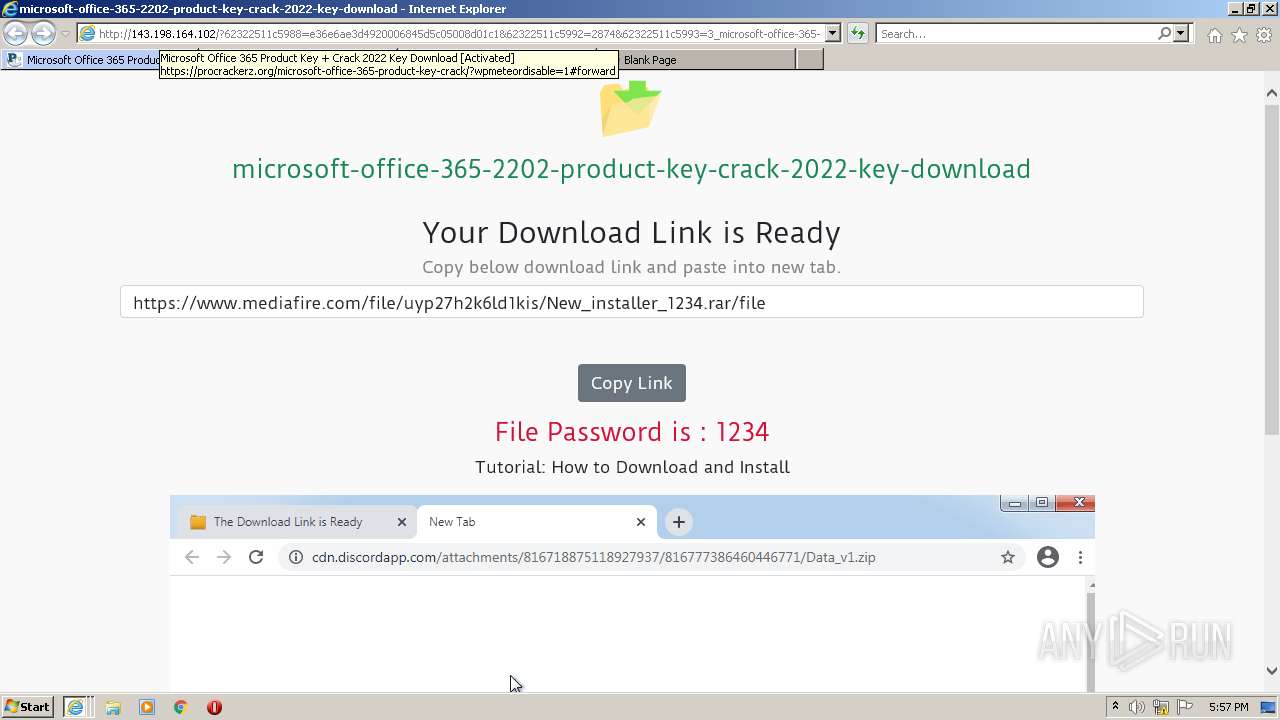
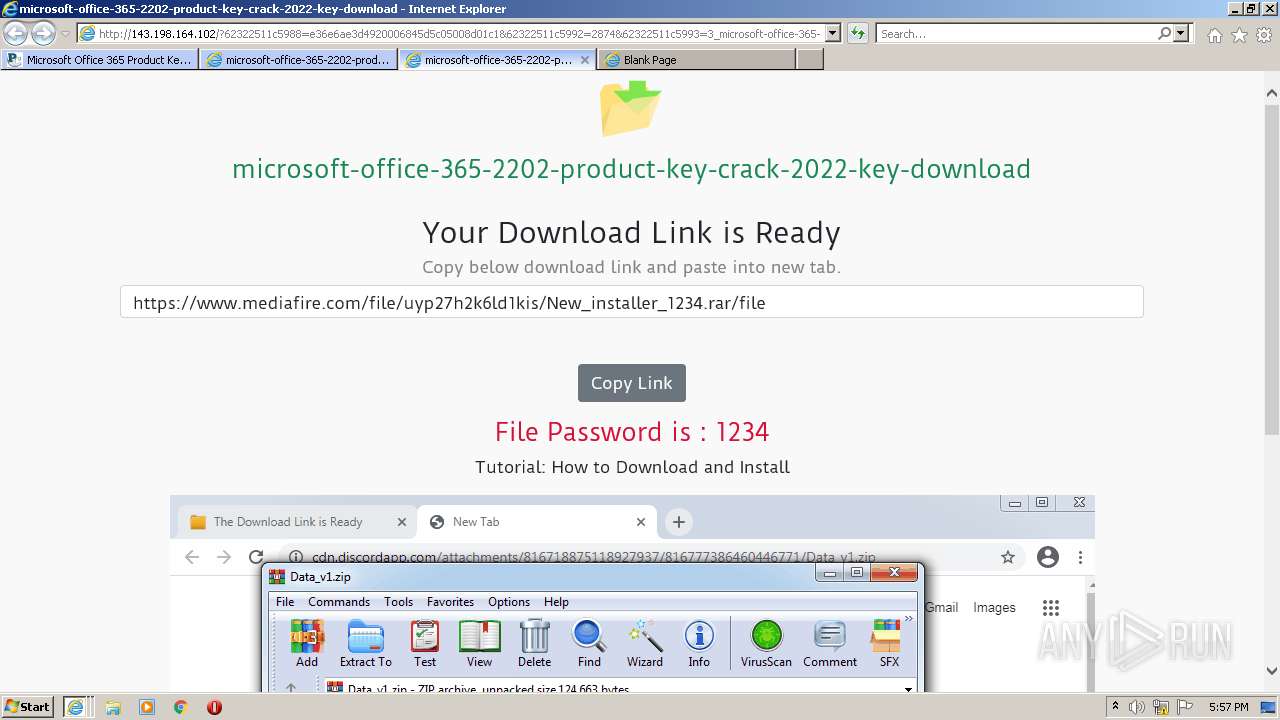
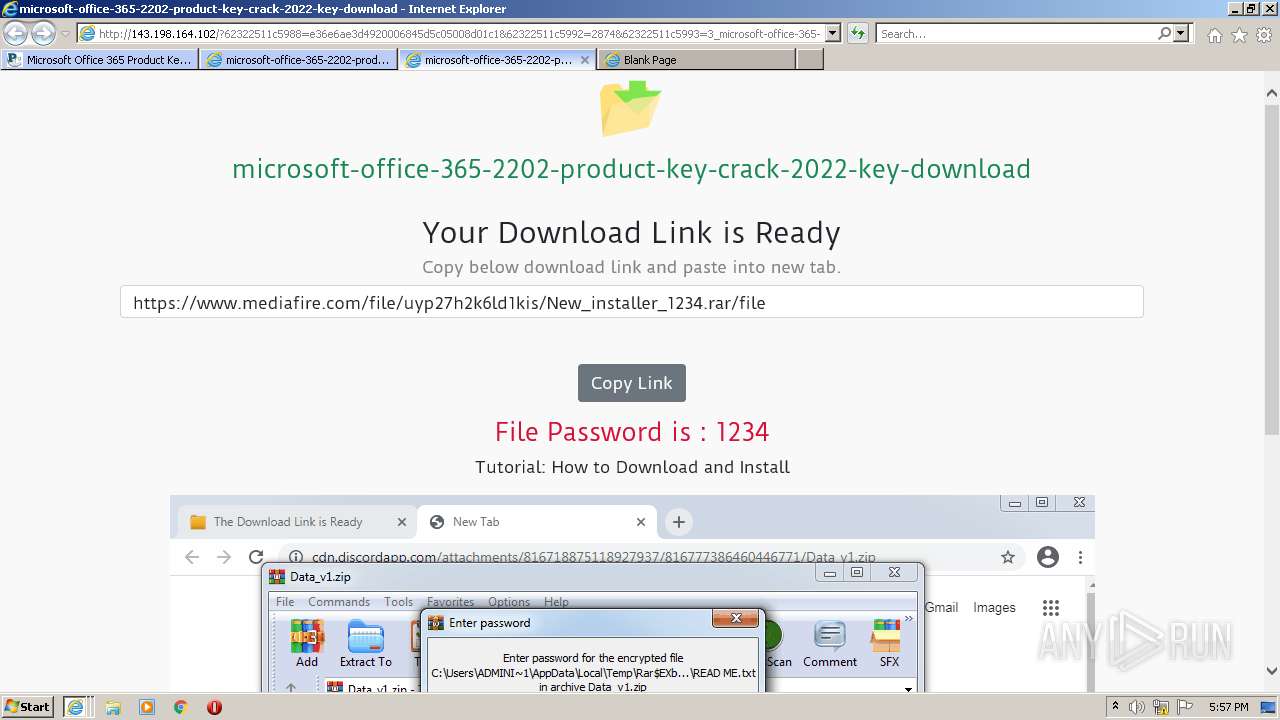
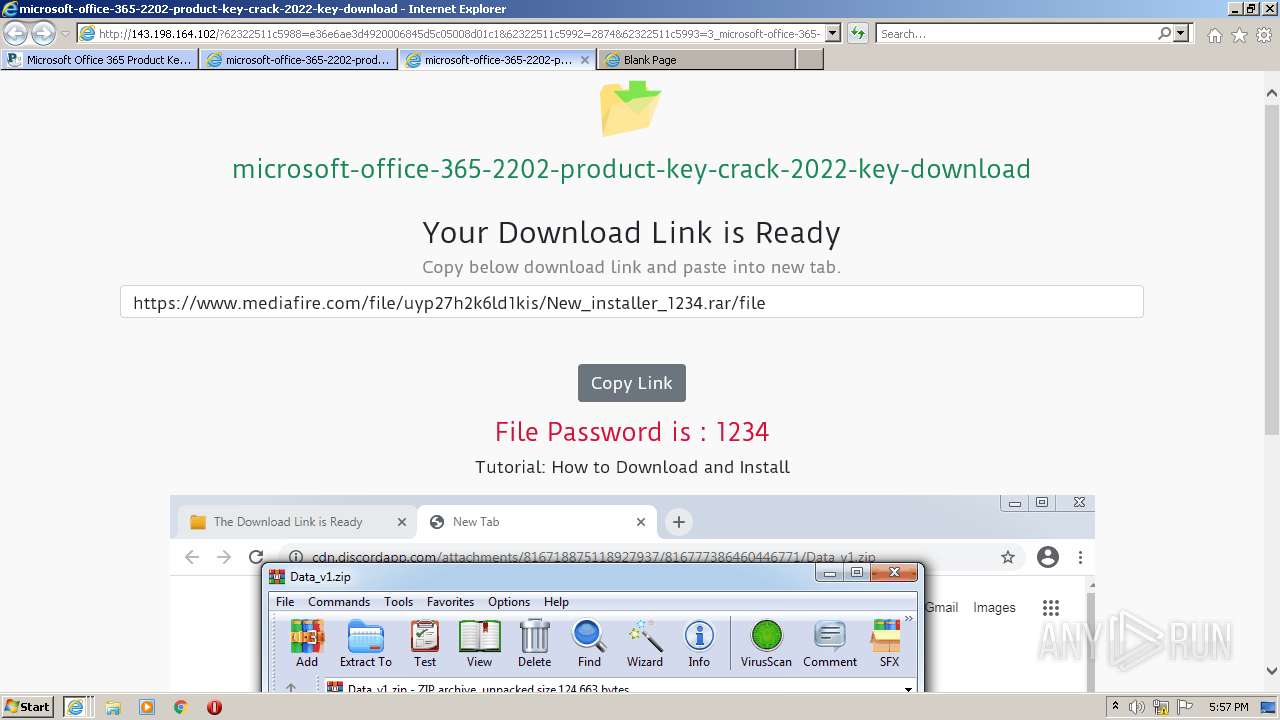
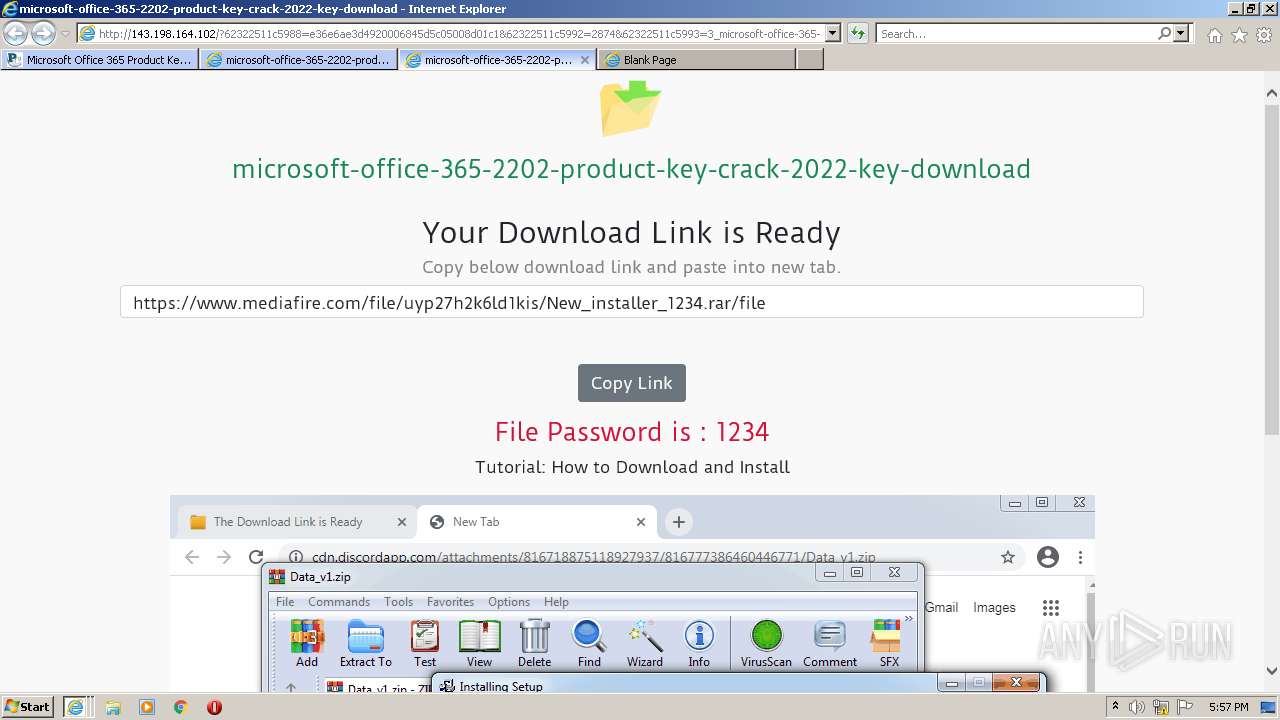
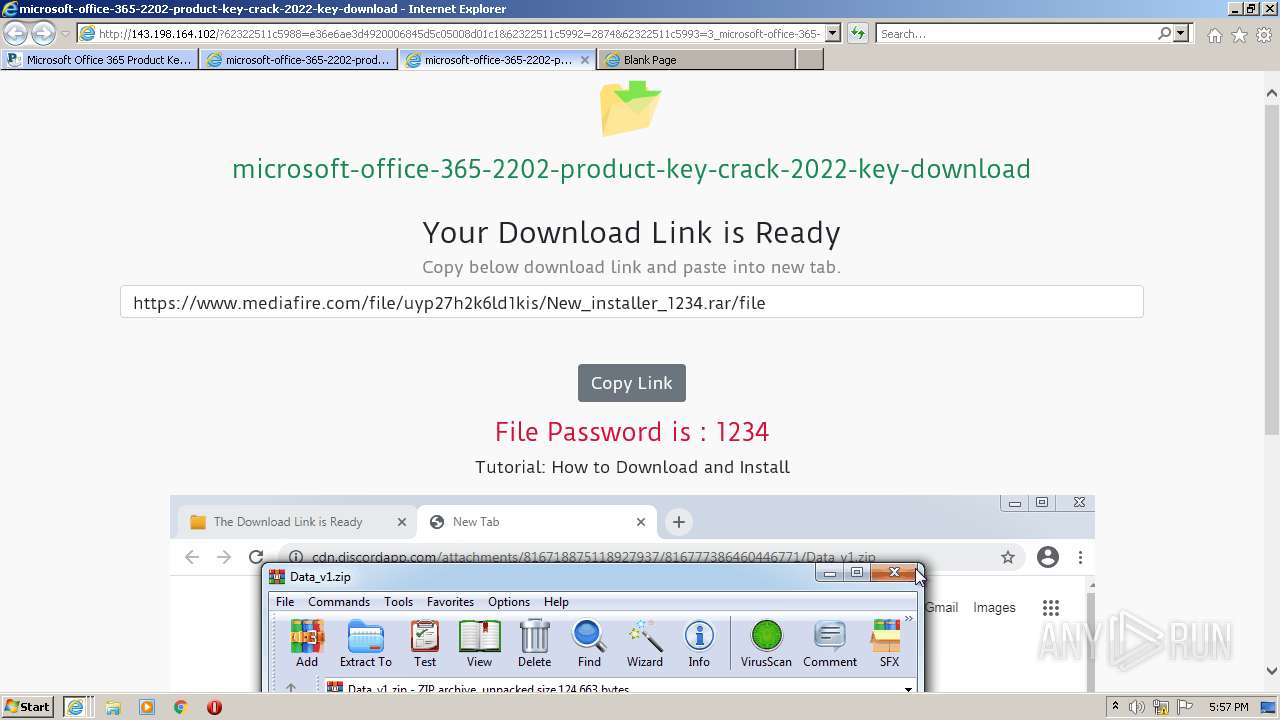
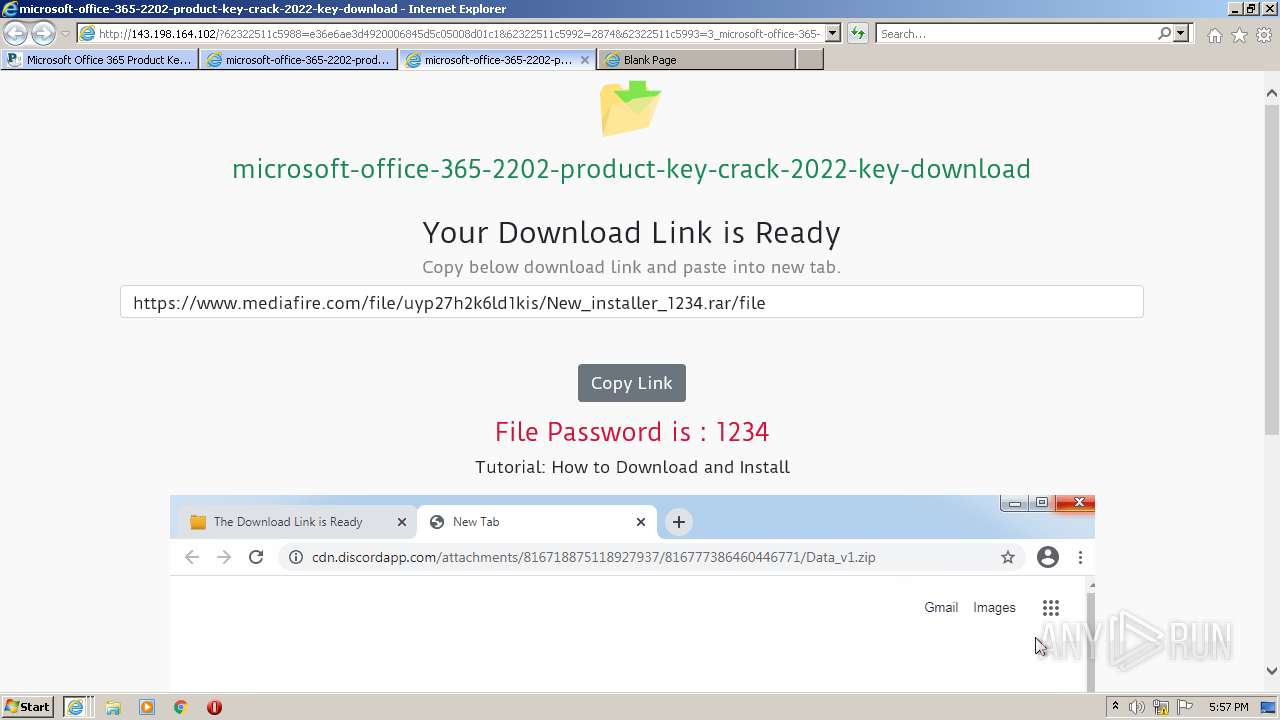
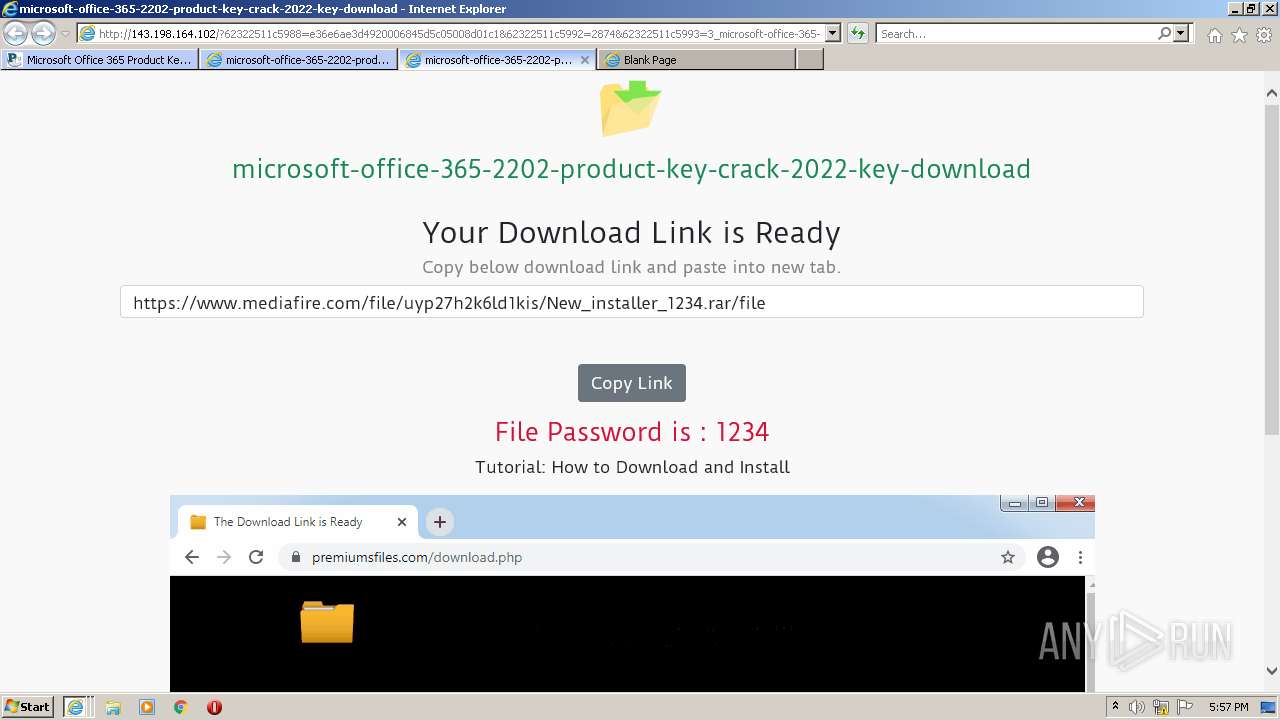
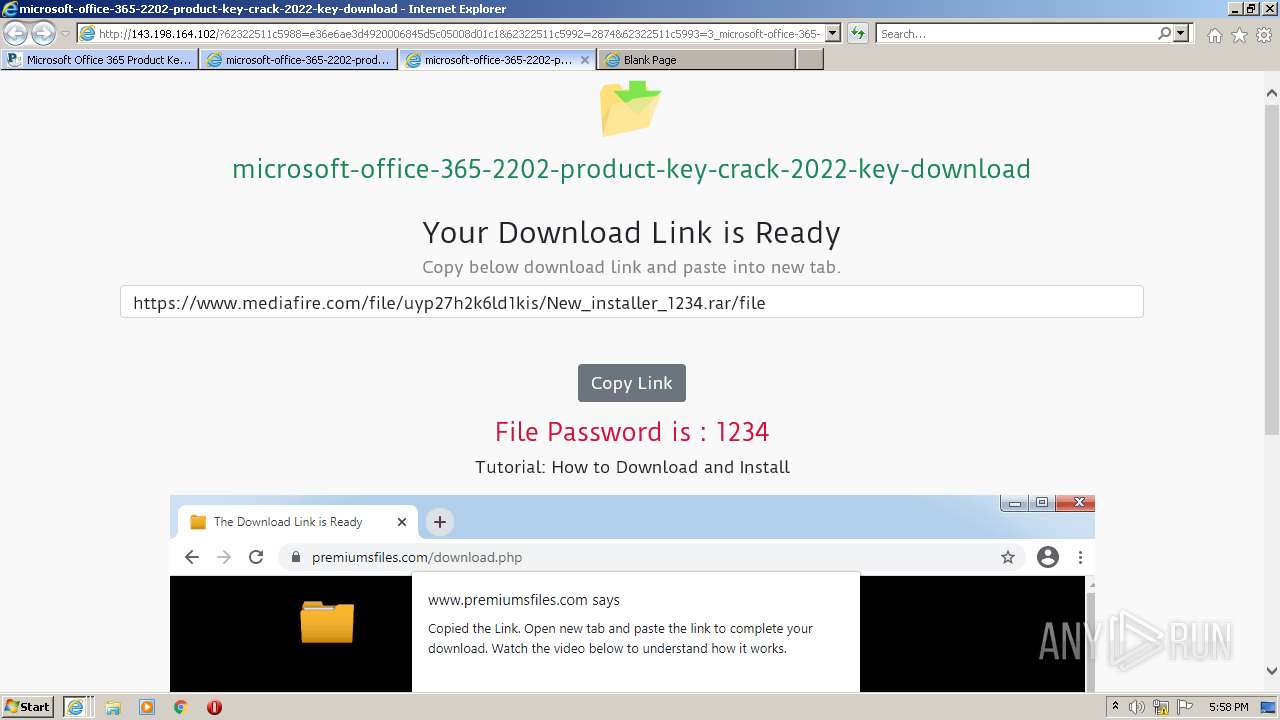
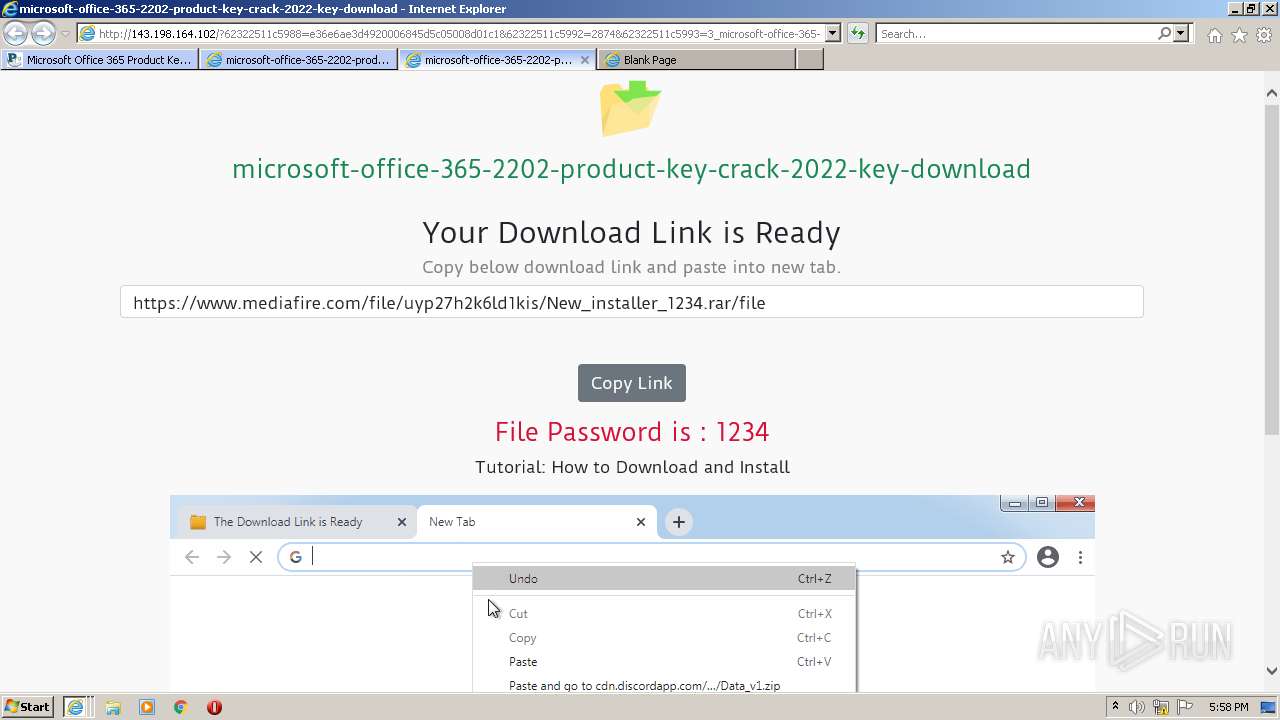
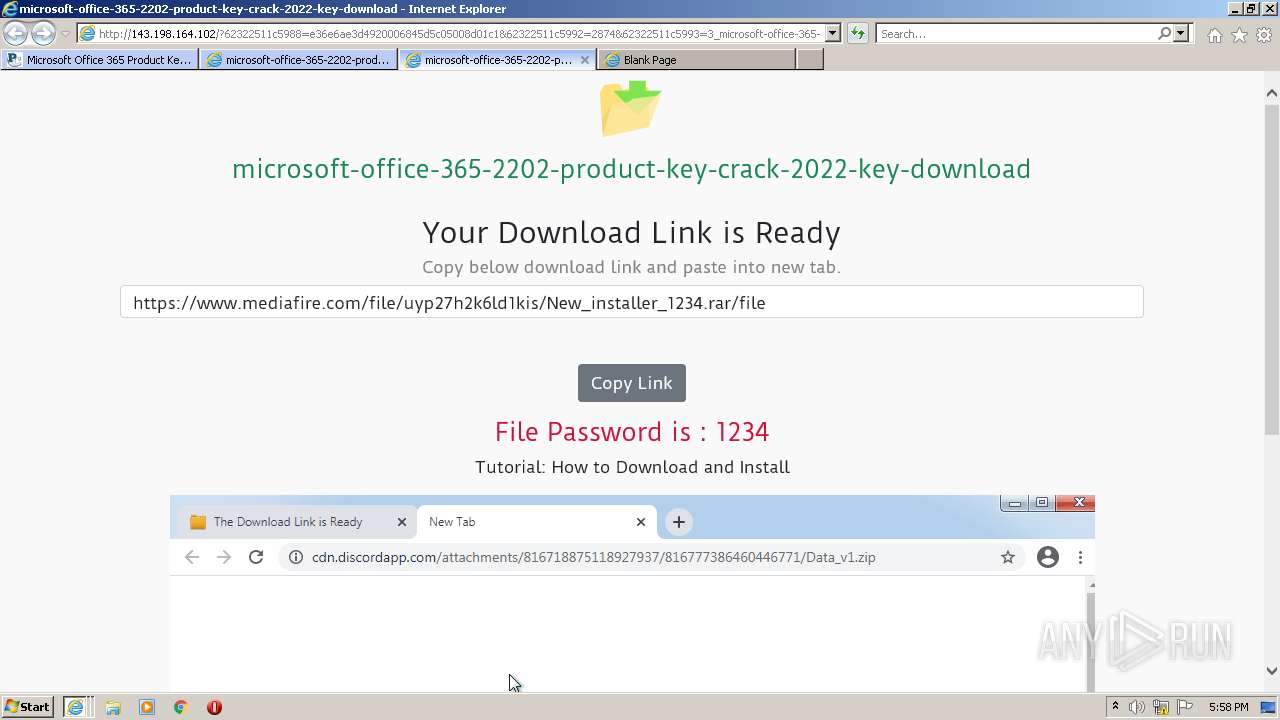
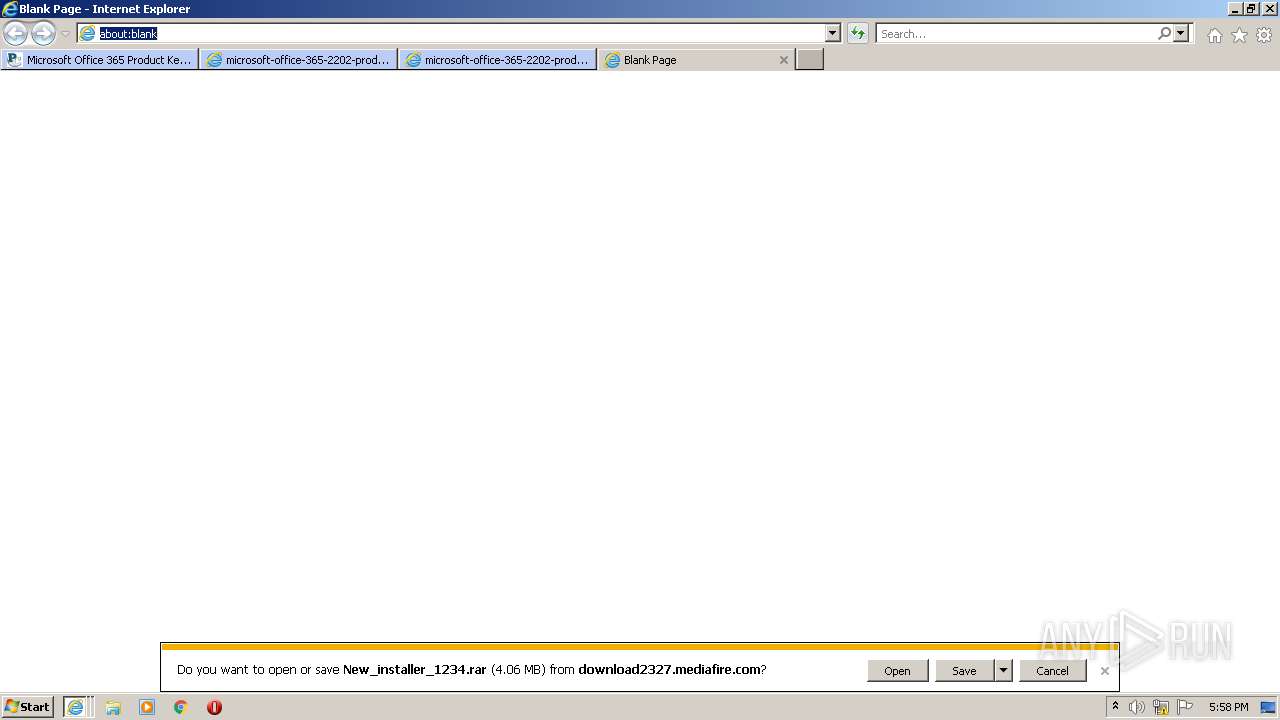
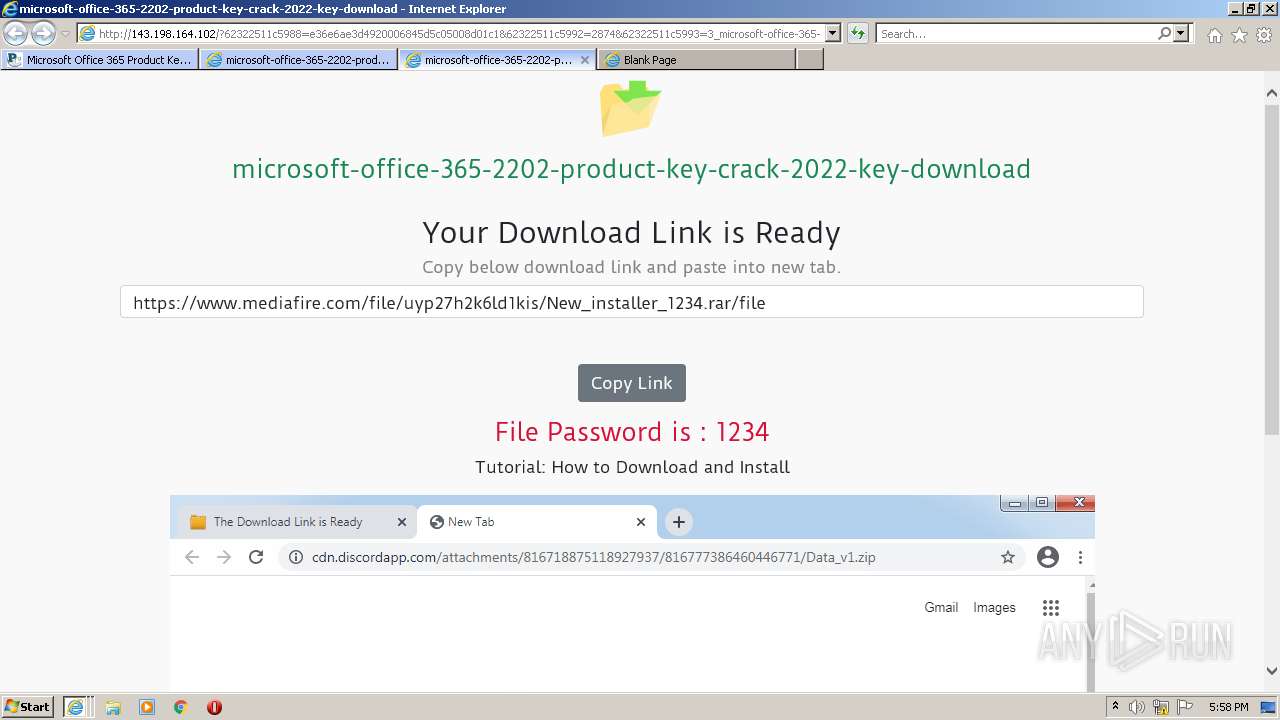
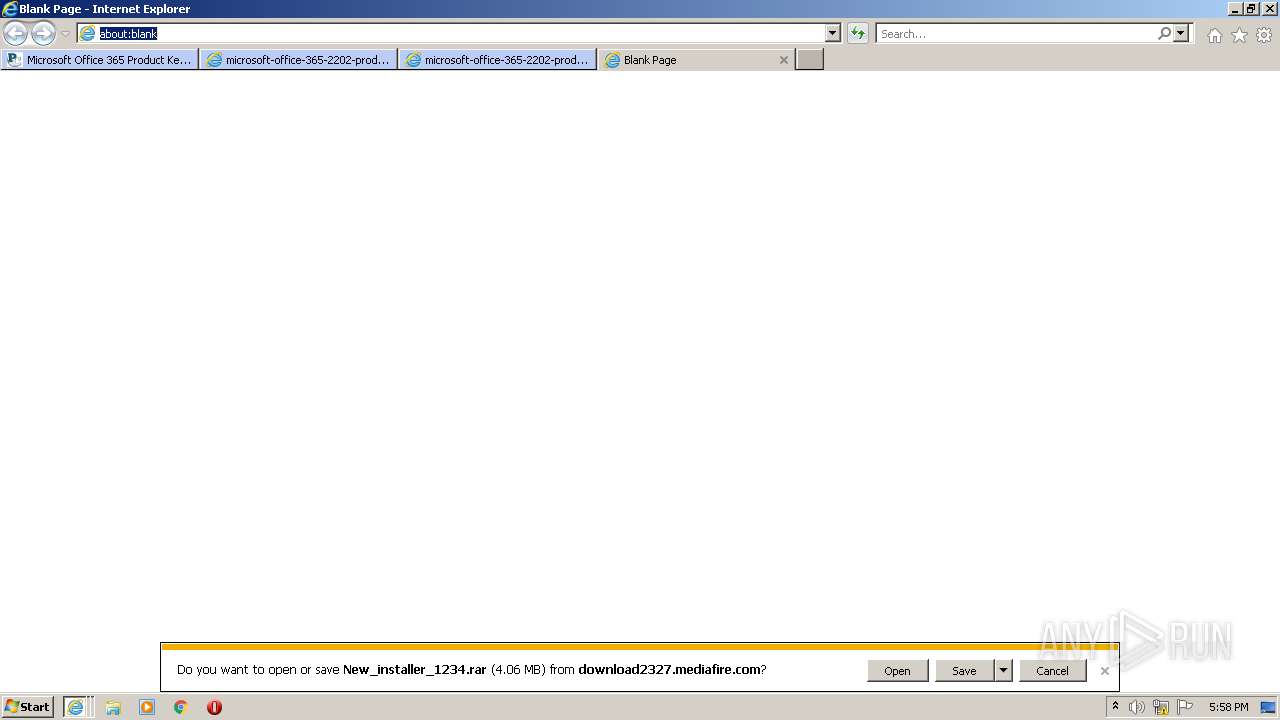
| URL: | https://procrackerz.org/microsoft-office-365-product-key-crack/#forward |
| Full analysis: | https://app.any.run/tasks/7c845ae4-d234-4d41-96ee-c957ce210011 |
| Verdict: | Malicious activity |
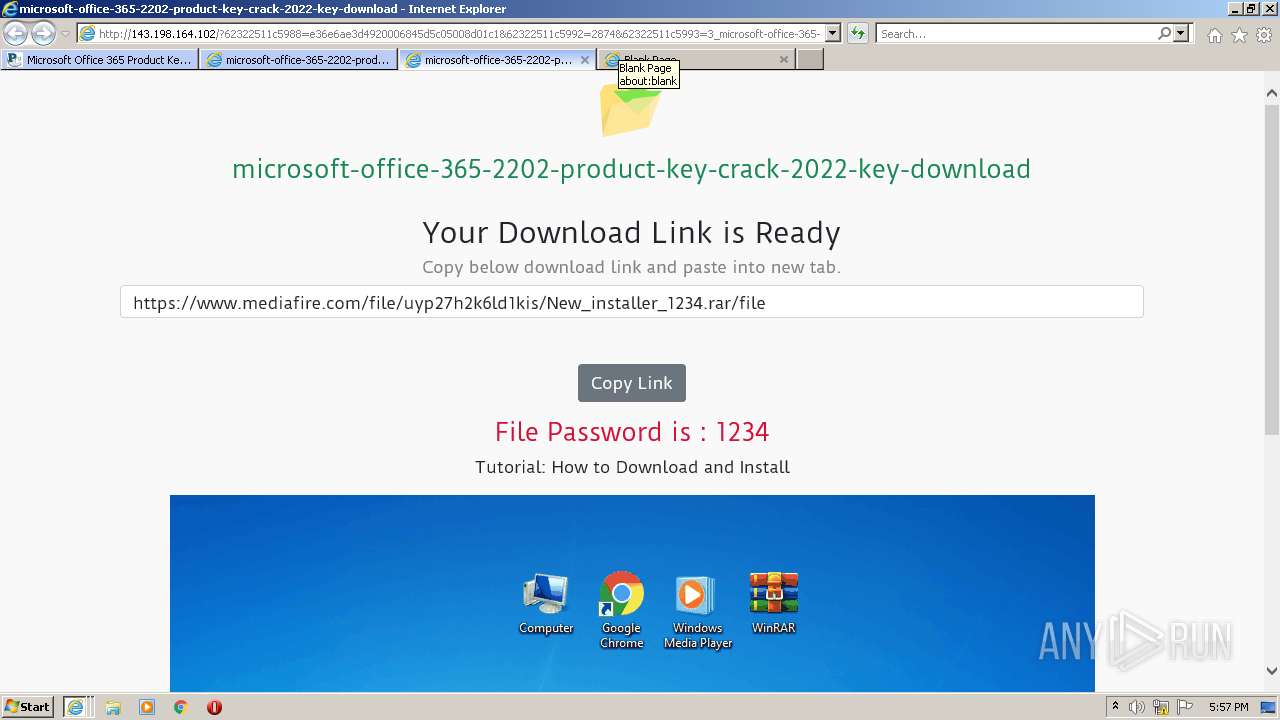
| Threats: | Raccoon is an info stealer type malware available as a Malware as a Service. It can be obtained for a subscription and costs $200 per month. Raccoon malware has already infected over 100,000 devices and became one of the most mentioned viruses on the underground forums in 2019. |
| Analysis date: | March 16, 2022, 17:55:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0248965D02AED44B6F6BF585DD075BA7 |
| SHA1: | F0C0BC42A28B1E541FB0EBBB6FB89A42B6DE8A88 |
| SHA256: | F46FB399AA9064E36CF6C7F9637AC9DA3A47B3AAFA26CBF8BE56E6764604BD78 |
| SSDEEP: | 3:N8TKG3XfLMCJYuuHk5VLGIv+n:2R3quuHkGI2 |
MALICIOUS
Application was dropped or rewritten from another process
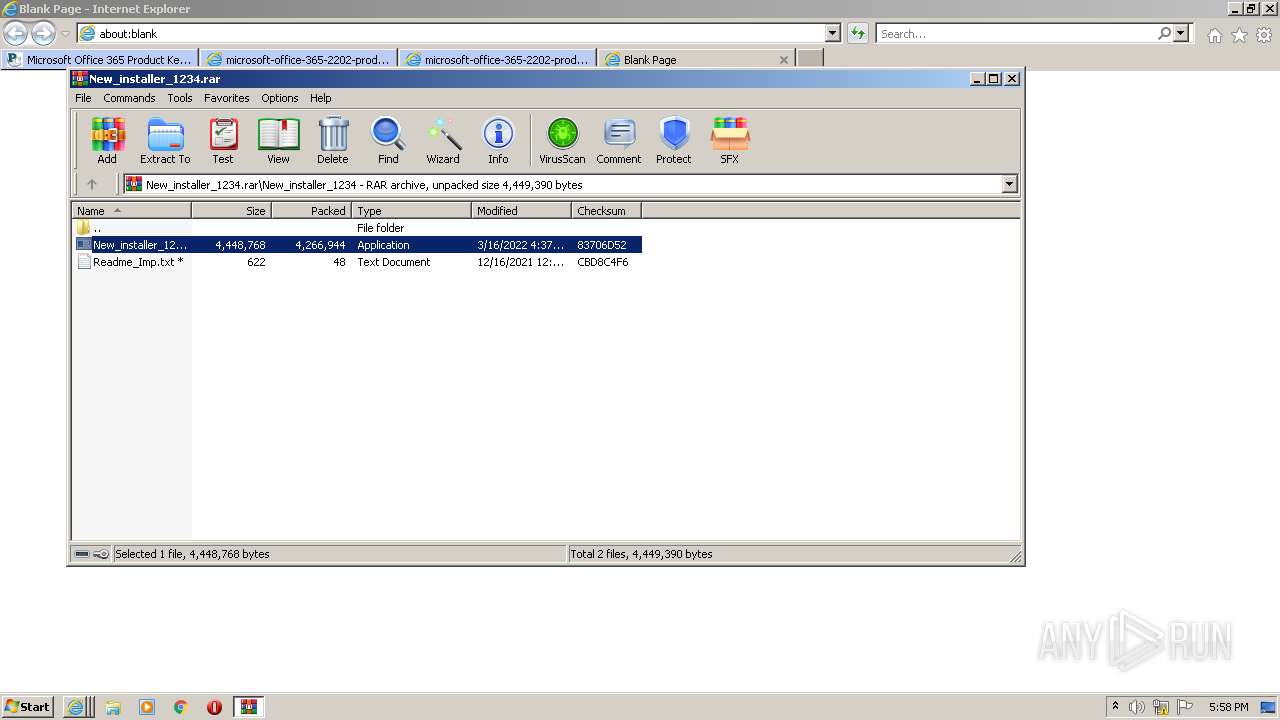
- New_installer_1234.exe (PID: 2252)
- New_installer_1234.exe (PID: 3224)
RACCOON was detected
- AppLaunch.exe (PID: 3808)
Connects to CnC server
- AppLaunch.exe (PID: 3808)
Loads dropped or rewritten executable
- AppLaunch.exe (PID: 3808)
Actions looks like stealing of personal data
- AppLaunch.exe (PID: 3808)
Stealing of credential data
- AppLaunch.exe (PID: 3808)
Steals credentials from Web Browsers
- AppLaunch.exe (PID: 3808)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3584)
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 2664)
- iexplore.exe (PID: 2848)
Reads the computer name
- WinRAR.exe (PID: 3600)
- AppLaunch.exe (PID: 3808)
Checks supported languages
- WinRAR.exe (PID: 3600)
- New_installer_1234.exe (PID: 2252)
- AppLaunch.exe (PID: 3808)
- cmd.exe (PID: 2220)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3600)
- AppLaunch.exe (PID: 3808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3600)
- AppLaunch.exe (PID: 3808)
Drops a file that was compiled in debug mode
- AppLaunch.exe (PID: 3808)
Drops a file with too old compile date
- AppLaunch.exe (PID: 3808)
Reads Environment values
- AppLaunch.exe (PID: 3808)
Starts CMD.EXE for self-deleting
- AppLaunch.exe (PID: 3808)
Starts CMD.EXE for commands execution
- AppLaunch.exe (PID: 3808)
Reads the cookies of Mozilla Firefox
- AppLaunch.exe (PID: 3808)
Searches for installed software
- AppLaunch.exe (PID: 3808)
Removes files from Windows directory
- cmd.exe (PID: 2220)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3916)
Reads the computer name
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 2848)
- iexplore.exe (PID: 3584)
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 2664)
Checks supported languages
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 2848)
- iexplore.exe (PID: 3584)
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 2664)
- timeout.exe (PID: 3756)
Checks Windows Trust Settings
- iexplore.exe (PID: 2848)
- iexplore.exe (PID: 3584)
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 2664)
Reads settings of System Certificates
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 2848)
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 2664)
- iexplore.exe (PID: 3584)
Application launched itself
- iexplore.exe (PID: 3916)
Reads internet explorer settings
- iexplore.exe (PID: 2848)
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 2664)
- iexplore.exe (PID: 3584)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3916)
Creates files in the user directory
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 3584)
Changes settings of System certificates
- iexplore.exe (PID: 3916)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
11
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2068 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3916 CREDAT:3872030 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2220 | cmd.exe /C timeout /T 10 /NOBREAK > Nul & Del /f /q "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\system32\cmd.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
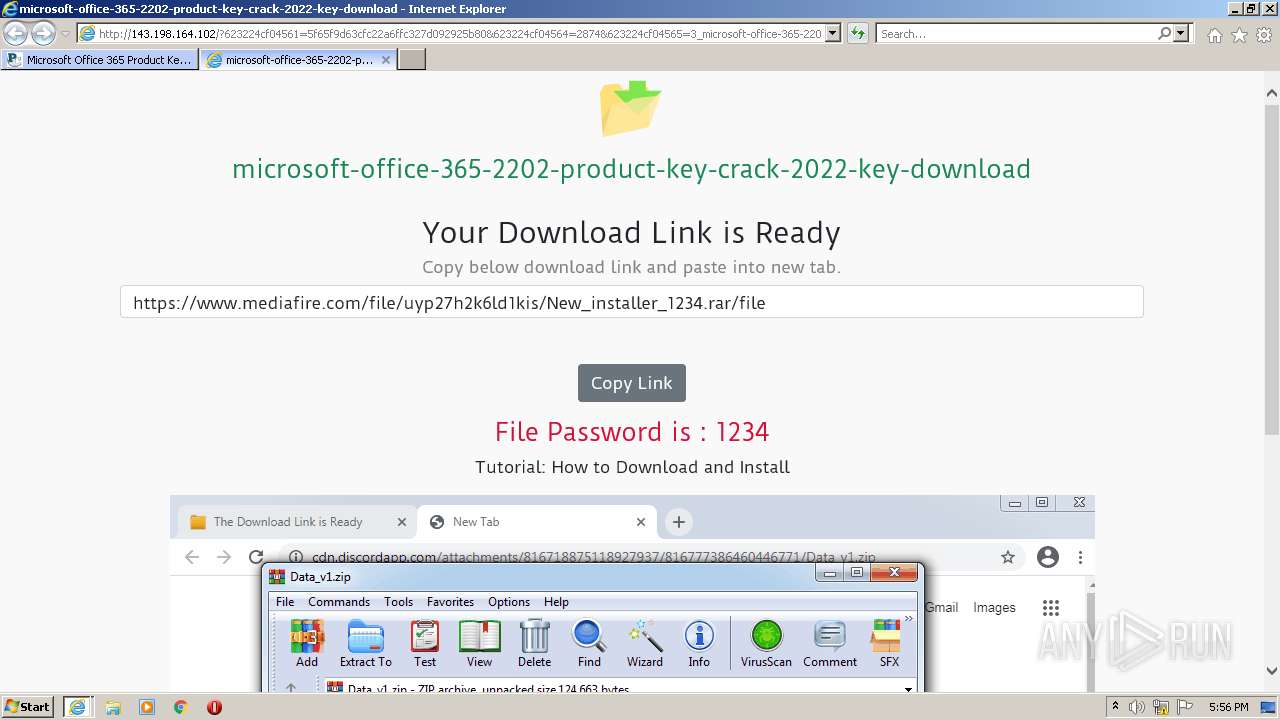
| 2252 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3600.15214\New_installer_1234\New_installer_1234.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3600.15214\New_installer_1234\New_installer_1234.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2664 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3916 CREDAT:1250580 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2848 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3916 CREDAT:4003091 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3224 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3600.15214\New_installer_1234\New_installer_1234.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3600.15214\New_installer_1234\New_installer_1234.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3584 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3916 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3600 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\New_installer_1234.rar" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3756 | timeout /T 10 /NOBREAK | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3808 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | New_installer_1234.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
Total events
35 201
Read events
34 855
Write events
338
Delete events
8
Modification events
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 374684016 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30947679 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 674842766 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30947679 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
59
Suspicious files
42
Text files
80
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\64DCC9872C5635B1B7891B30665E0558_5902CB49D5053F52437E024A0A679CC8 | der | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\64DCC9872C5635B1B7891B30665E0558_5902CB49D5053F52437E024A0A679CC8 | binary | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\microsoft-office-365-product-key-crack[1].htm | html | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BJ1SD8U7.txt | text | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8EF2PDNG.txt | text | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:— | SHA256:— | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
118
DNS requests
46
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3584 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAlzgVOtaLijaEGvkcEJMCU%3D | US | der | 471 b | whitelisted |
3584 | iexplore.exe | GET | 200 | 104.18.31.182:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
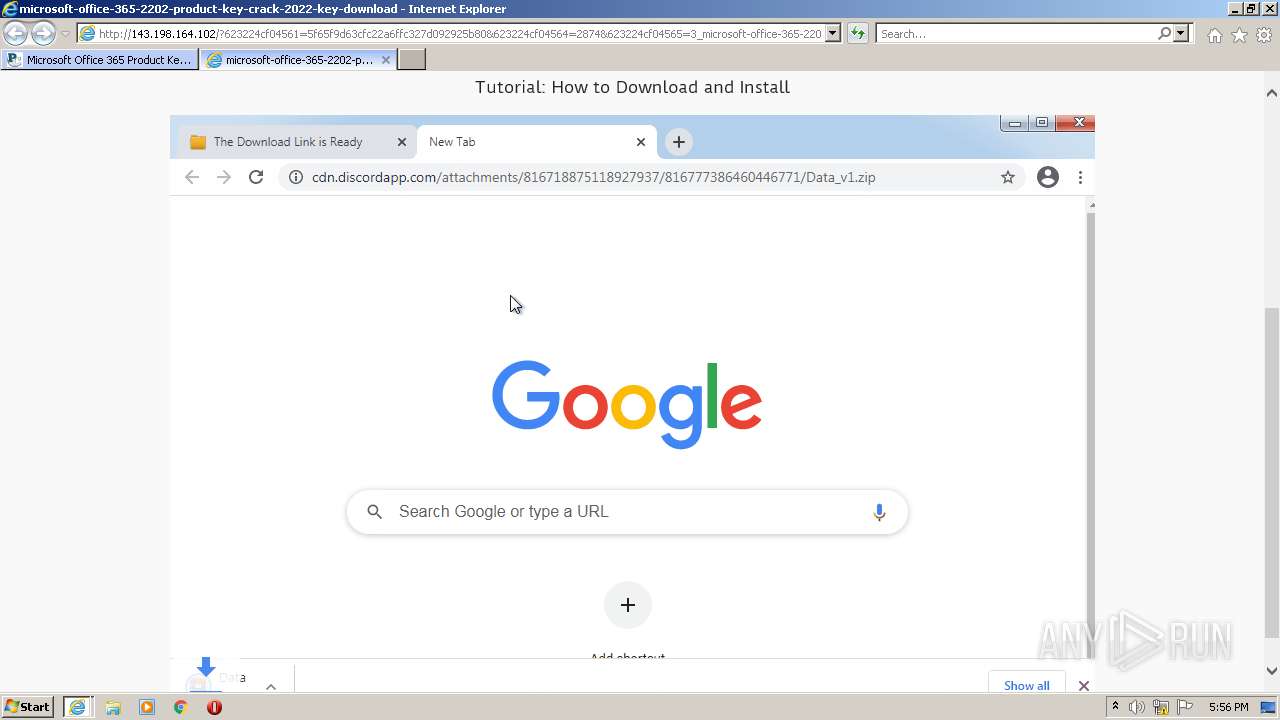
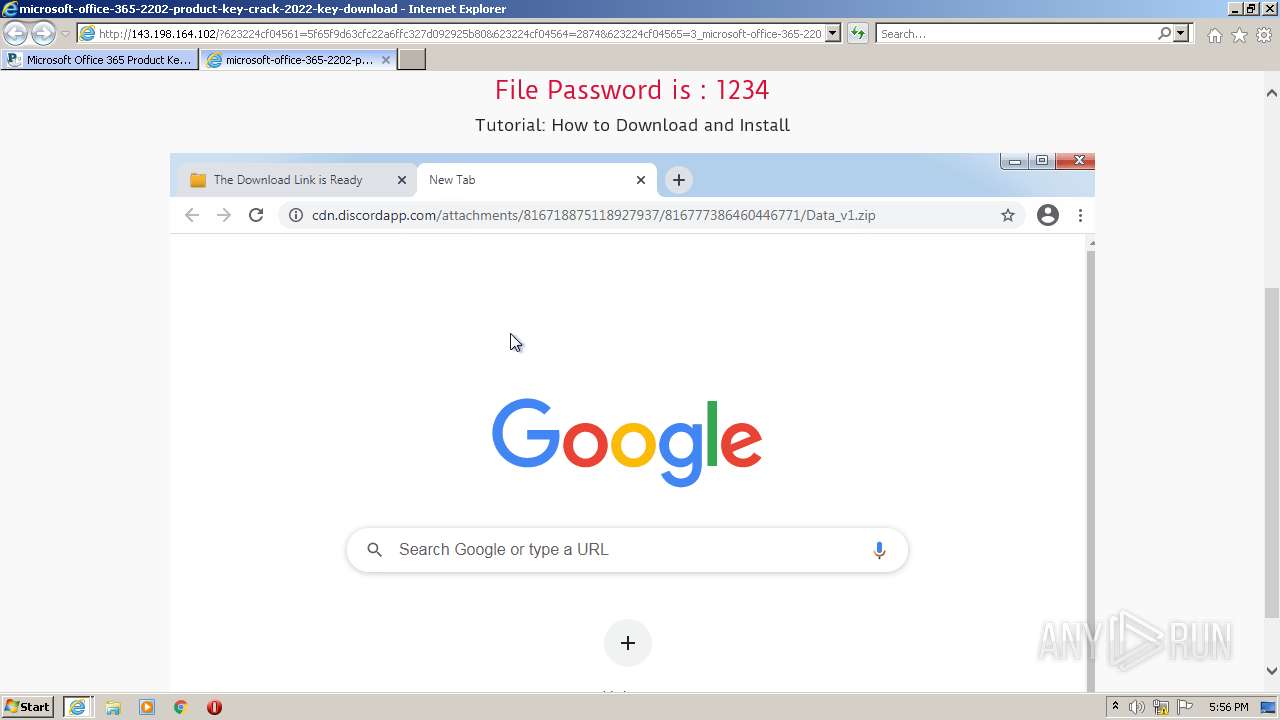
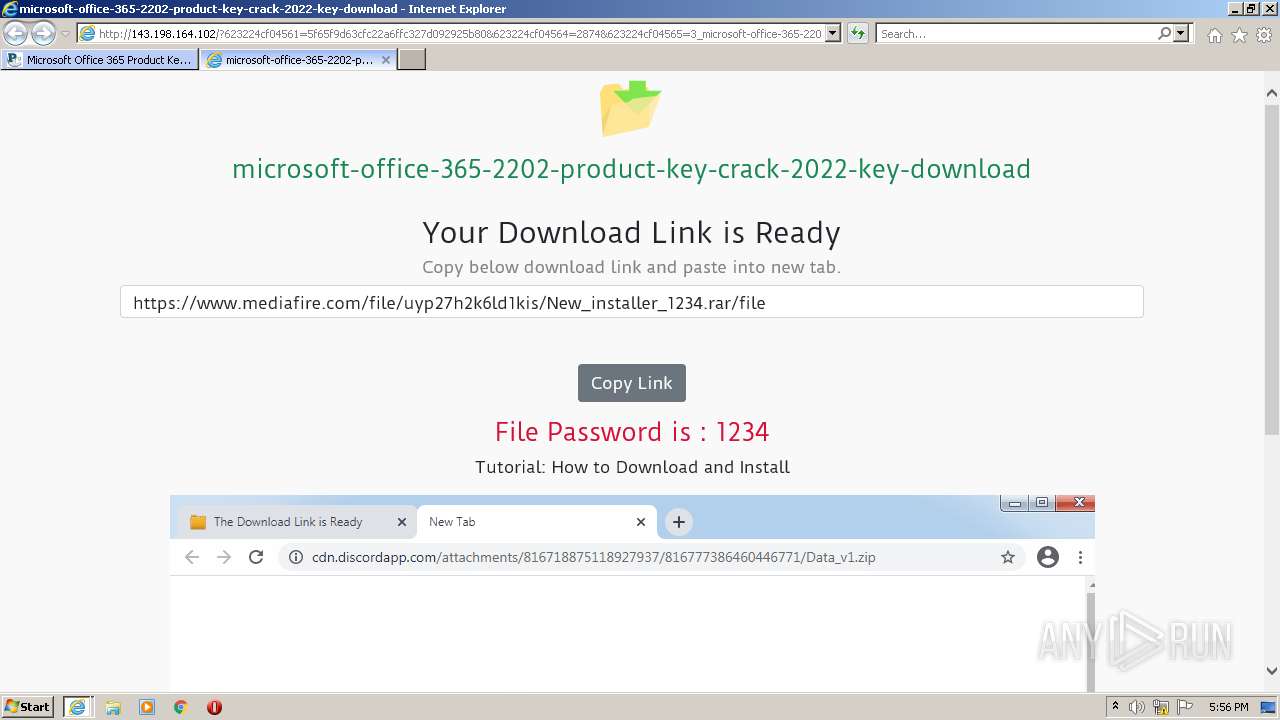
2848 | iexplore.exe | GET | 200 | 143.198.164.102:80 | http://143.198.164.102/?623224cf04561=5f65f9d63cfc22a6ffc327d092925b80&623224cf04564=2874&623224cf04565=3_microsoft-office-365-2202-product-key-crack-2022-key-download&gkss=456017&623224cf04566=3 | US | html | 1.07 Kb | unknown |
2848 | iexplore.exe | GET | 200 | 143.198.164.102:80 | http://143.198.164.102/images/thelrn.gif | US | image | 958 Kb | unknown |
2848 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDGntkWsVwfkgoAAAABOO%2F8 | US | der | 472 b | whitelisted |
2848 | iexplore.exe | GET | 200 | 2.16.186.40:80 | http://e1.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBTvkAFw3ViPKmUeIVEf3NC7b1ErqwQUWvPtK%2Fw2wjd5uVIw6lRvz1XLLqwCEgPV2P0ZoNQKWxdHZQNyFBpuQA%3D%3D | unknown | der | 346 b | whitelisted |
3584 | iexplore.exe | GET | 200 | 104.18.31.182:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3916 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2848 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2848 | iexplore.exe | GET | 200 | 23.45.105.185:80 | http://x2.c.lencr.org/ | NL | der | 299 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3916 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3584 | iexplore.exe | 173.249.25.20:443 | procrackerz.org | Contabo GmbH | US | unknown |
3916 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3916 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3584 | iexplore.exe | 192.0.77.2:443 | i0.wp.com | Automattic, Inc | US | suspicious |
3584 | iexplore.exe | 104.18.30.182:80 | ocsp.comodoca.com | Cloudflare Inc | US | suspicious |
3584 | iexplore.exe | 192.0.73.2:443 | secure.gravatar.com | Automattic, Inc | US | whitelisted |
3584 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3584 | iexplore.exe | 185.60.216.35:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
3584 | iexplore.exe | 31.13.92.14:443 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
procrackerz.org |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
i0.wp.com |
| whitelisted |
secure.gravatar.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
c0.wp.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2848 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3916 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3916 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2664 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3808 | AppLaunch.exe | A Network Trojan was detected | ET TROJAN Win32.Raccoon Stealer Checkin M6 |
3808 | AppLaunch.exe | A Network Trojan was detected | ET TROJAN Win32.Raccoon Stealer Checkin Response M5 |
3808 | AppLaunch.exe | A Network Trojan was detected | ET TROJAN Win32.Raccoon Stealer CnC Activity (dependency download) |
3808 | AppLaunch.exe | A Network Trojan was detected | ET TROJAN Win32.Raccoon Stealer CnC Activity (dependency download) |
3808 | AppLaunch.exe | A Network Trojan was detected | ET TROJAN Win32.Raccoon Stealer Data Exfil Attempt |
3808 | AppLaunch.exe | A Network Trojan was detected | ET TROJAN Suspicious Zipped Filename in Outbound POST Request (passwords.txt) M2 |
1 ETPRO signatures available at the full report