| File name: | mssql.exe |
| Full analysis: | https://app.any.run/tasks/ebdb1d0a-2688-4908-a44c-017fbca4db3e |
| Verdict: | Malicious activity |
| Threats: | Mallox is a ransomware strain that emerged in 2021, known for its ability to encrypt files and target database servers using vulnerabilities like RDP. Often distributed through phishing campaigns and exploiting exposed SQL servers, it locks victims' data and demands a ransom. Mallox operates as a Ransomware-as-a-Service (RaaS), making it accessible to affiliates who use it to conduct attacks. |
| Analysis date: | June 15, 2025, 12:10:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 68A6333D3775F2AED498FC71773A99D9 |
| SHA1: | 50DA1229D57937D4349E764320BB536322726E3C |
| SHA256: | F45D853AABDB7AABB567671AEAAC5C1D1287C5EB25D13F27CF4523341A36F6F3 |
| SSDEEP: | 49152:jwAzRc9KsHsd5zi8AsYNtRTgJrQKPWjbLVveIX1vLcqd8VWU7rS8Q7nGxOn9lEiJ:jDRKKsvNtRTQrjPg5veSuVW0rUzGxOnJ |
MALICIOUS
MALLOX mutex has been found
- grpconv.exe (PID: 1044)
RANSOMWARE has been detected
- grpconv.exe (PID: 1044)
SUSPICIOUS
Connects to the server without a host name
- grpconv.exe (PID: 1044)
There is functionality for capture public ip (YARA)
- grpconv.exe (PID: 1044)
Checks for external IP
- grpconv.exe (PID: 1044)
INFO
Creates files in the program directory
- grpconv.exe (PID: 1044)
Checks supported languages
- mssql.exe (PID: 5616)
Create files in a temporary directory
- grpconv.exe (PID: 1044)
Creates files or folders in the user directory
- grpconv.exe (PID: 1044)
Manual execution by a user
- notepad.exe (PID: 5060)
Reads the software policy settings
- slui.exe (PID: 4040)
Checks proxy server information
- slui.exe (PID: 4040)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:28 20:19:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 486912 |
| InitializedDataSize: | 796160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x53cf8 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
141
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1044 | "C:\Windows\System32\grpconv.exe" | C:\Windows\System32\grpconv.exe | mssql.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Progman Group Converter Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5060 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\FILE RECOVERY.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5616 | "C:\Users\admin\AppData\Local\Temp\mssql.exe" | C:\Users\admin\AppData\Local\Temp\mssql.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 321
Read events
2 321
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
24
Text files
558
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
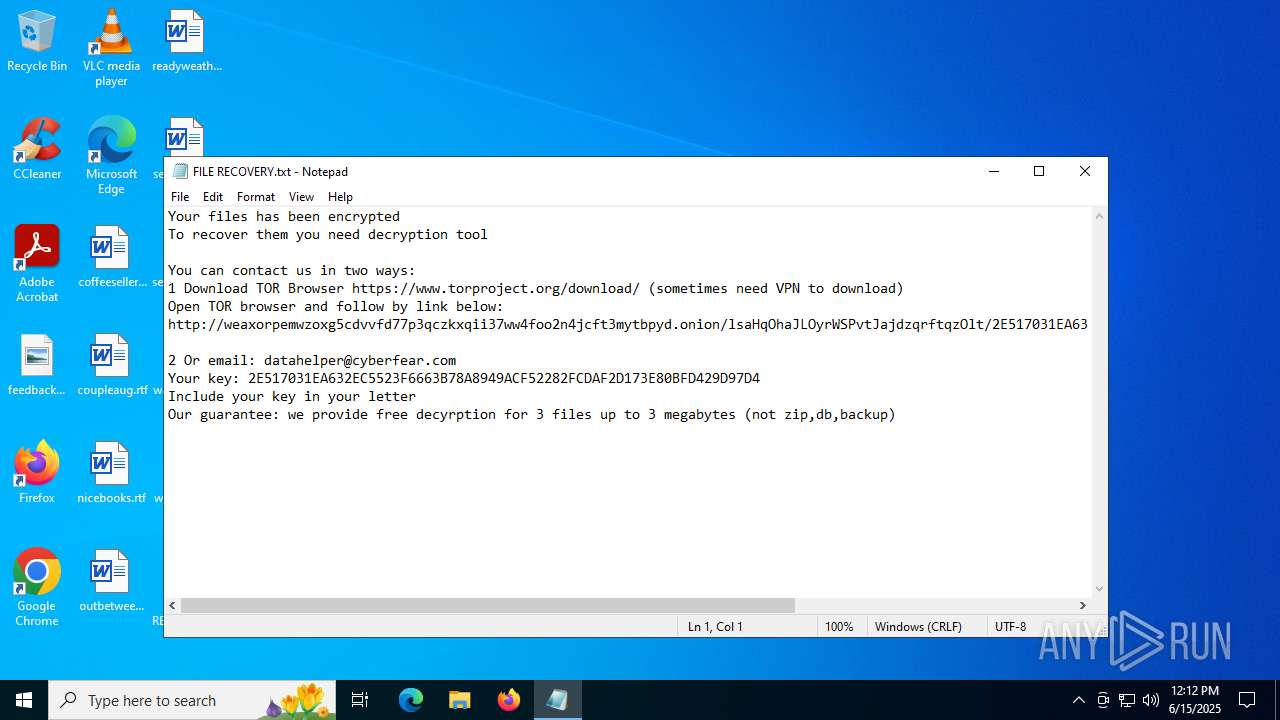
| 1044 | grpconv.exe | C:\Users\admin\Desktop\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\core\linux-x64\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\core\win-x86\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\x64\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\Documents\Outlook Files\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\core\osx-x64\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\Documents\OneNote Notebooks\My Notebook\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\core\win-x64\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\x86\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
| 1044 | grpconv.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\FILE RECOVERY.txt | text | |
MD5:DB5DF5788EC272B42D3DE45F2E9DE07E | SHA256:1CCCF70C21082BC79059CA71FBA82F7EB2B224A2CE563A0562F0C05894DCCDBC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
29
DNS requests
18
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1044 | grpconv.exe | GET | 200 | 104.26.12.205:80 | http://api.ipify.org/ | unknown | — | — | malicious |
1044 | grpconv.exe | POST | 200 | 193.143.1.153:80 | http://193.143.1.153/Ujdu8jjooue/biweax.php | unknown | — | — | unknown |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1132 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1132 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1336 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6232 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1044 | grpconv.exe | 104.26.12.205:80 | api.ipify.org | CLOUDFLARENET | US | shared |
1044 | grpconv.exe | 193.143.1.153:80 | — | LLC Baxet | RU | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1336 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1336 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
api.ipify.org |
| shared |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1044 | grpconv.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
1044 | grpconv.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
2200 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1044 | grpconv.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 41 |
1044 | grpconv.exe | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
1044 | grpconv.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |