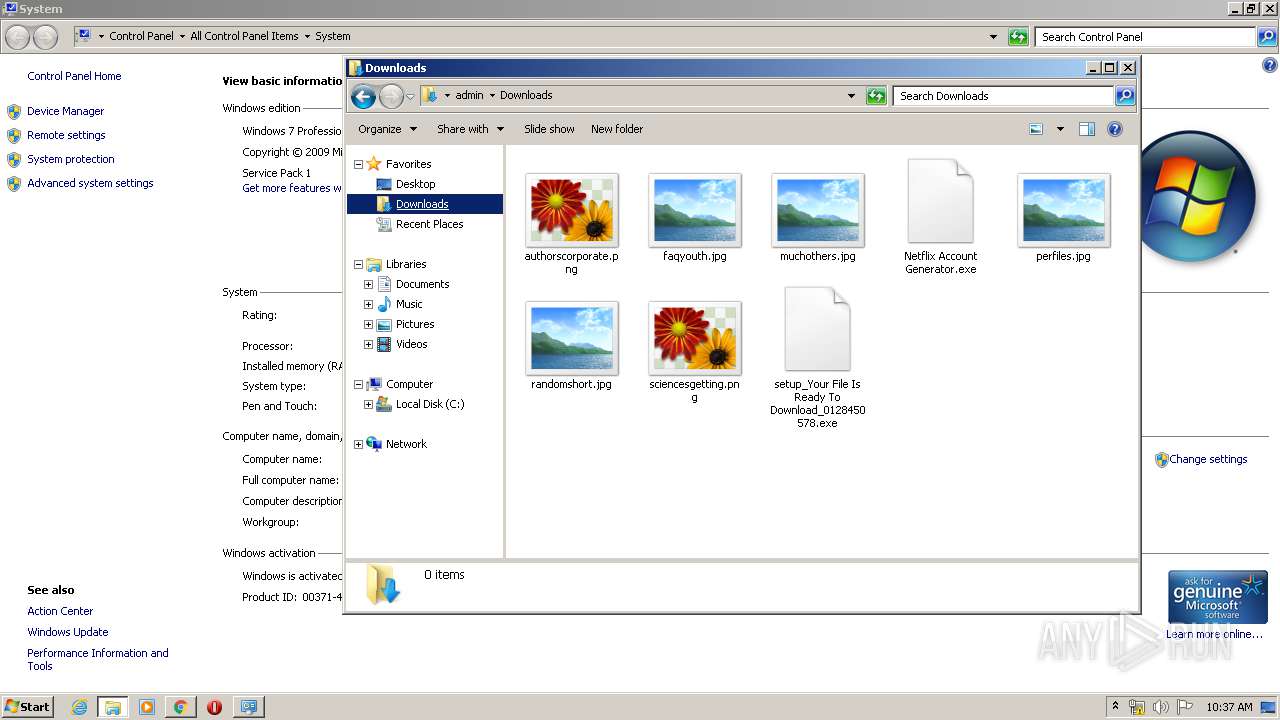
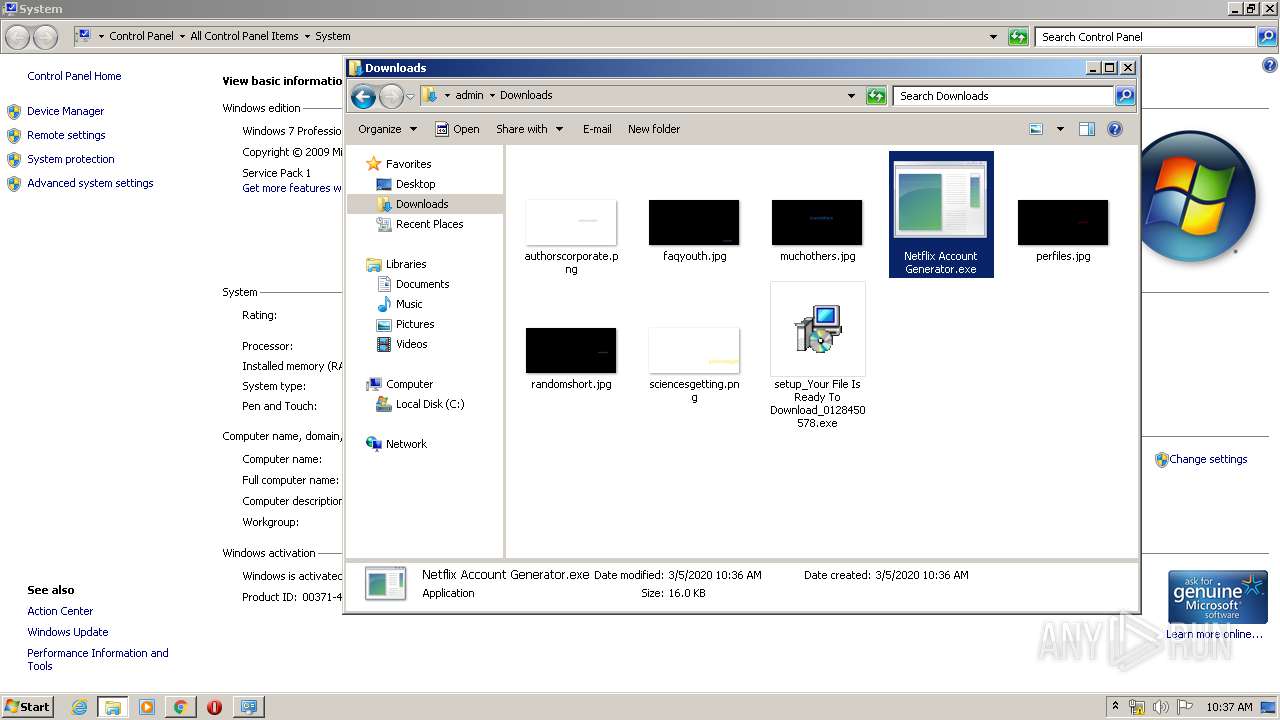
| URL: | https://anonfile.com/VbIe41e2o4/Netflix_Account_Generator_exe |
| Full analysis: | https://app.any.run/tasks/e5425a20-36b9-4ce2-b84a-0b489e755f54 |
| Verdict: | Malicious activity |
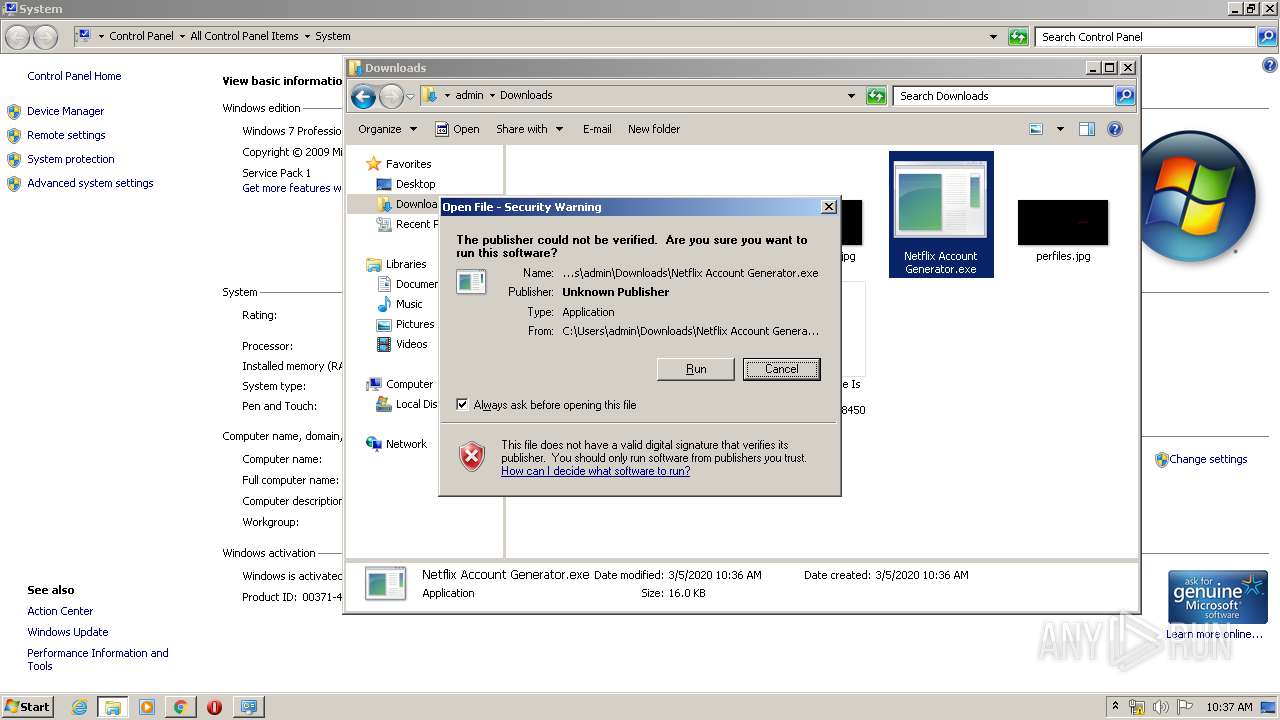
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | March 05, 2020, 10:35:25 |
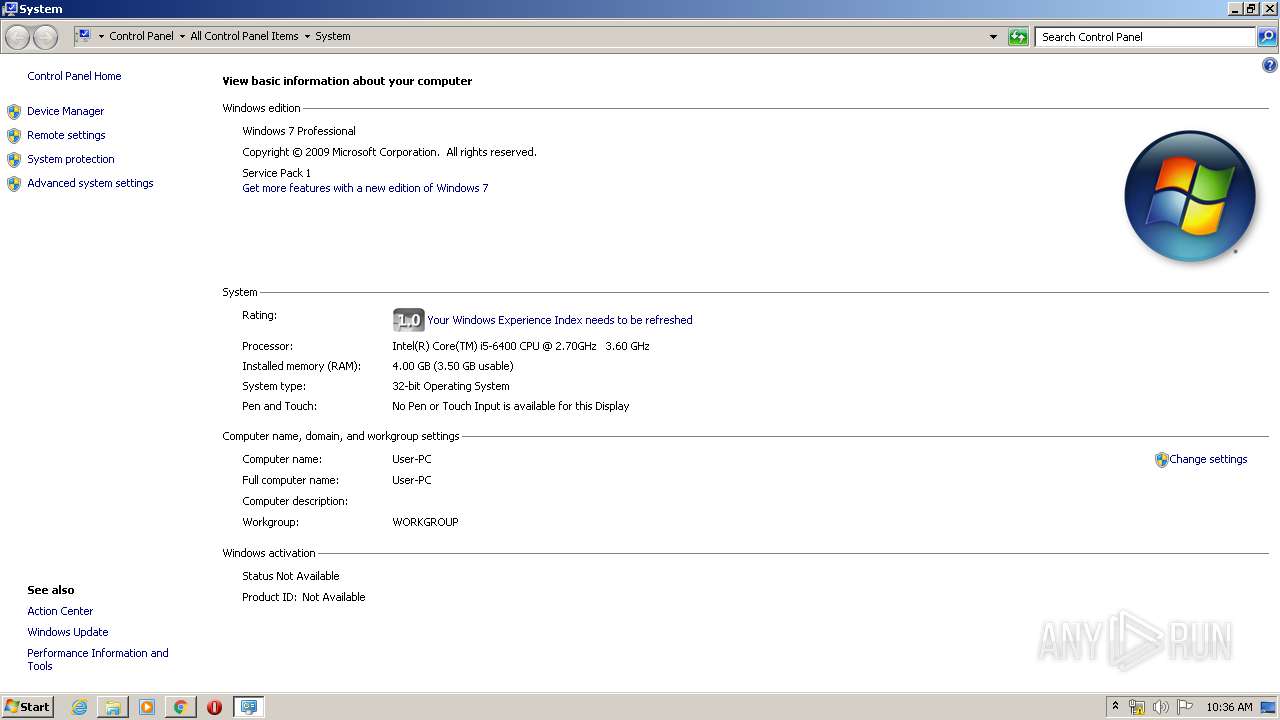
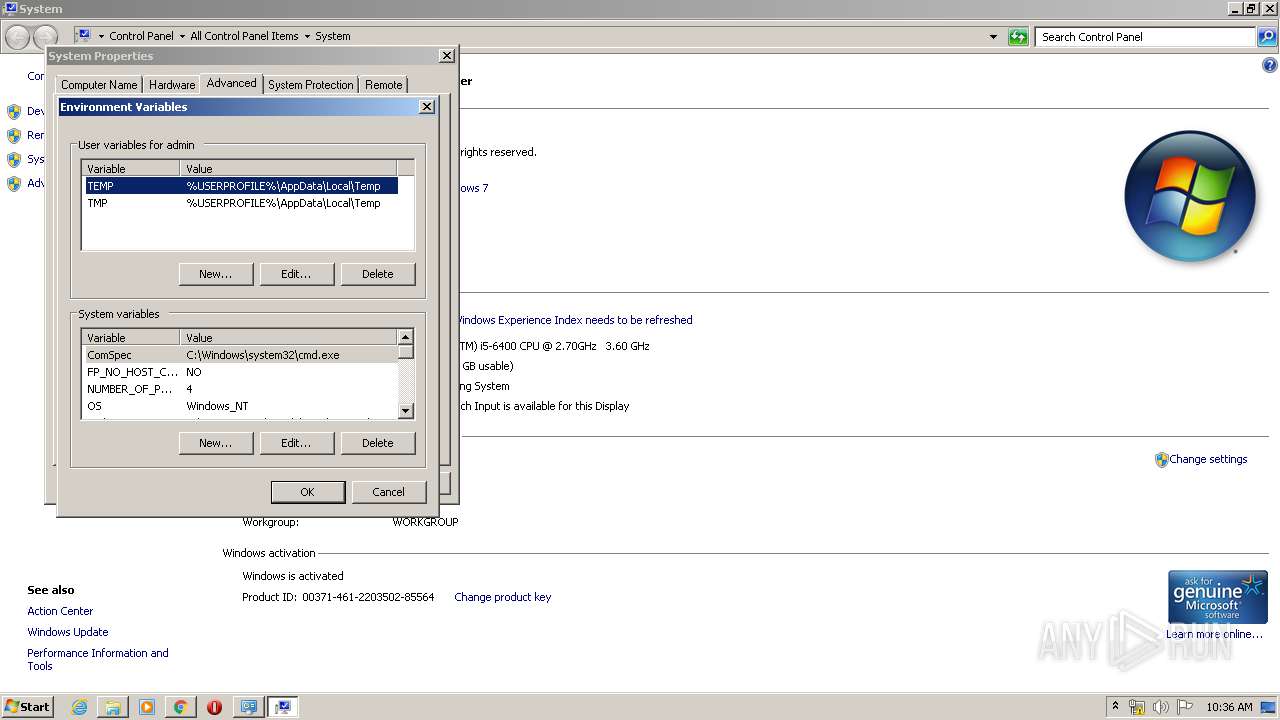
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | F1BA4D1CBA1915AA7EF0F93163290977 |
| SHA1: | D40E245DDF3C9EC320C72744521EBAD15EDF04D5 |
| SHA256: | F41ED02CD9DEF3BD35FEC54CE4391DC4D4103E3DBD6141DD3A06AEB0D29C66A8 |
| SSDEEP: | 3:N8RGOstAdFPGG/ROubCn:2gDydBNMuen |
MALICIOUS
Downloads executable files from the Internet
- chrome.exe (PID: 1392)
Application was dropped or rewritten from another process
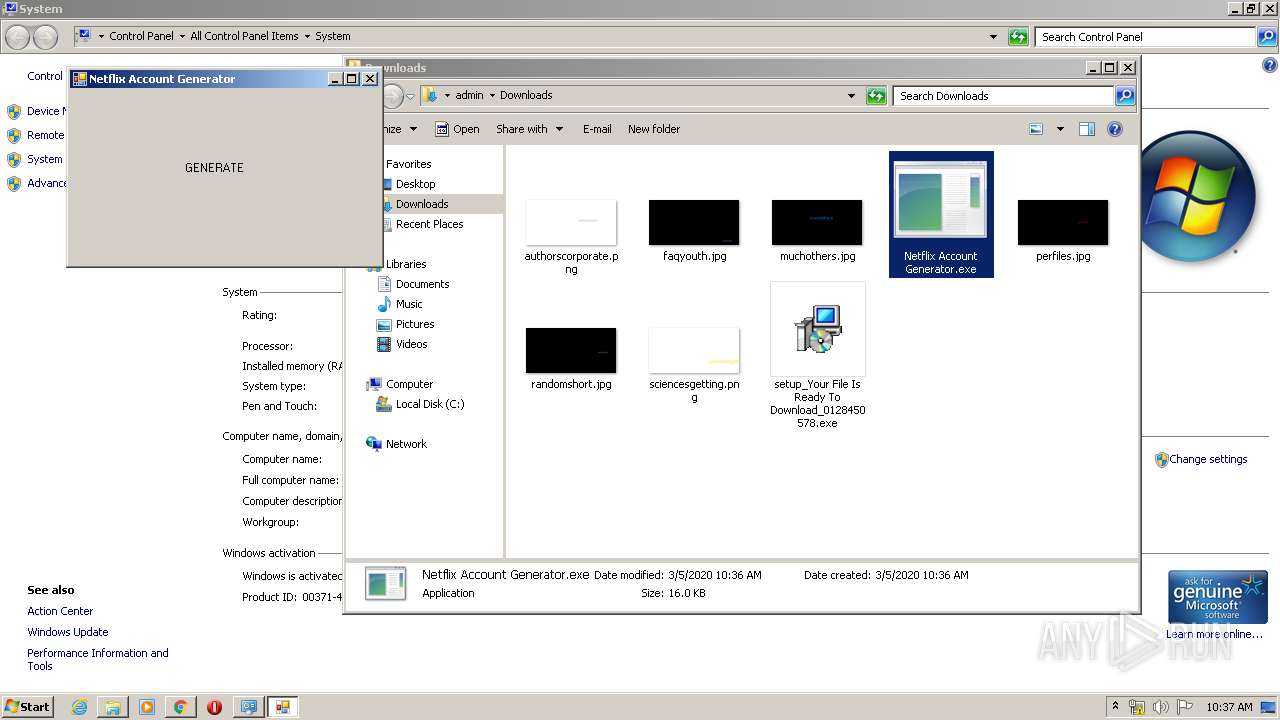
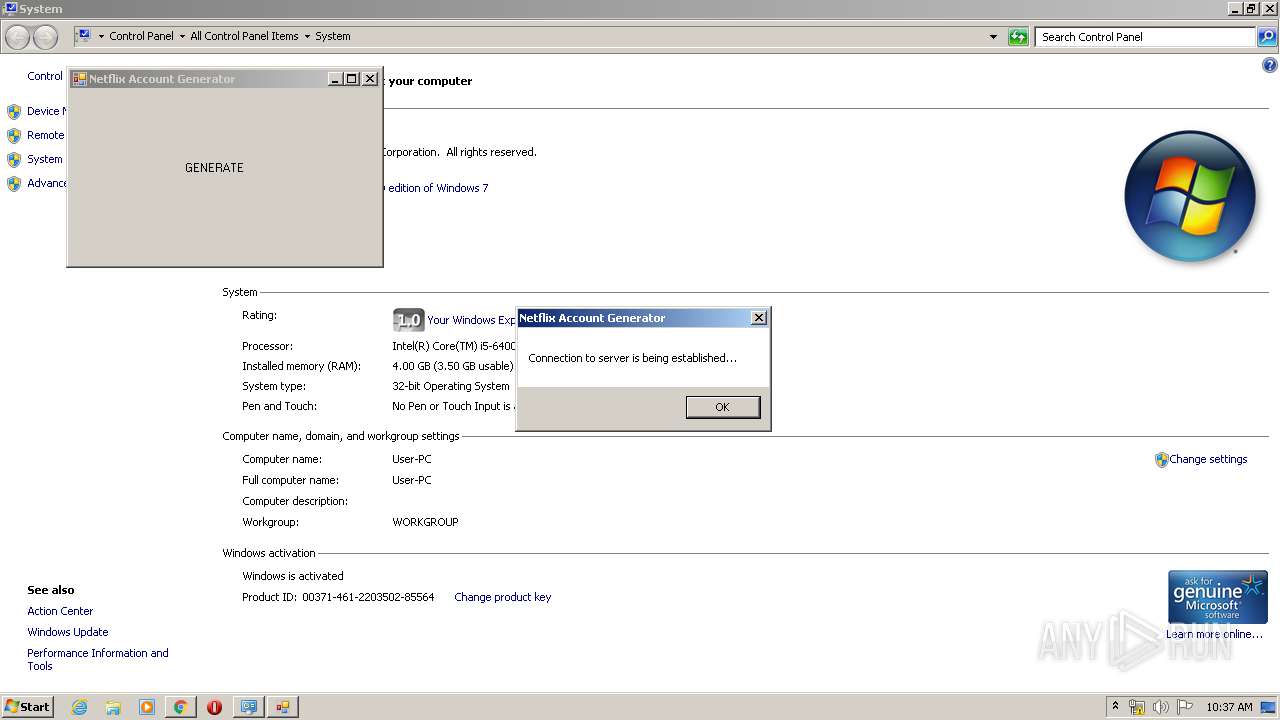
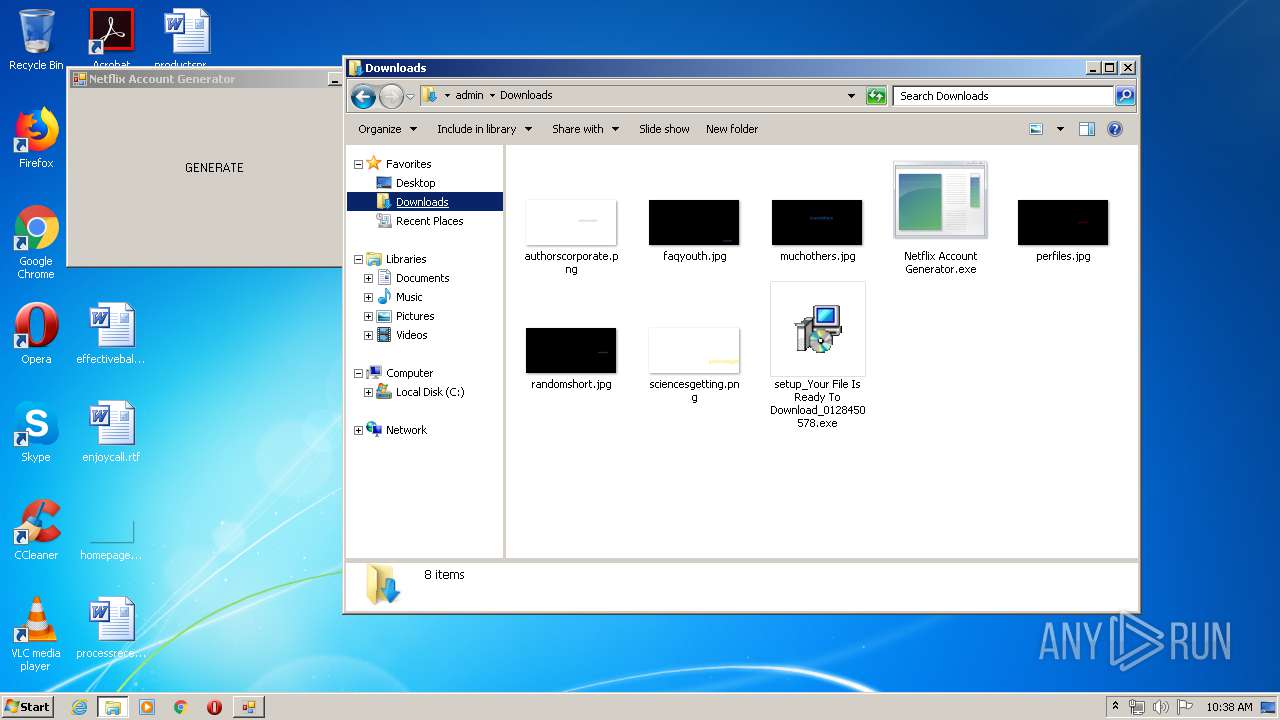
- Netflix Account Generator.exe (PID: 3820)
- lawnmower.exe (PID: 3672)
Actions looks like stealing of personal data
- vbc.exe (PID: 3096)
HAWKEYE was detected
- lawnmower.exe (PID: 3672)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3272)
Creates files in the user directory
- Netflix Account Generator.exe (PID: 3820)
- lawnmower.exe (PID: 3672)
Executable content was dropped or overwritten
- chrome.exe (PID: 3272)
- Netflix Account Generator.exe (PID: 3820)
- chrome.exe (PID: 1392)
Checks for external IP
- lawnmower.exe (PID: 3672)
Connects to SMTP port
- lawnmower.exe (PID: 3672)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 2308)
Executes scripts
- lawnmower.exe (PID: 3672)
INFO
Application launched itself
- chrome.exe (PID: 3272)
Reads the hosts file
- chrome.exe (PID: 1392)
- chrome.exe (PID: 3272)
Manual execution by user
- control.exe (PID: 2888)
- Netflix Account Generator.exe (PID: 3820)
- explorer.exe (PID: 3064)
- systempropertiesadvanced.exe (PID: 3316)
- systempropertiesadvanced.exe (PID: 2956)
- explorer.exe (PID: 1564)
Reads Internet Cache Settings
- chrome.exe (PID: 3272)
Reads settings of System Certificates
- chrome.exe (PID: 1392)
- chrome.exe (PID: 3272)
- lawnmower.exe (PID: 3672)
Creates files in the user directory
- chrome.exe (PID: 3272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
92
Monitored processes
48
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,1001029464361440216,2248630948709696884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8886105469335559868 --mojo-platform-channel-handle=3632 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,1001029464361440216,2248630948709696884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4873874691239487083 --mojo-platform-channel-handle=4252 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,1001029464361440216,2248630948709696884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=18369935251416502076 --mojo-platform-channel-handle=4728 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1044,1001029464361440216,2248630948709696884,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=2349236501386599943 --mojo-platform-channel-handle=4604 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,1001029464361440216,2248630948709696884,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16218165656329531375 --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4564 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,1001029464361440216,2248630948709696884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=11687521686999072191 --mojo-platform-channel-handle=1564 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1564 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,1001029464361440216,2248630948709696884,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4410178072708318868 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3068 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2308 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holderwb.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | lawnmower.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 2316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,1001029464361440216,2248630948709696884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7438294057605123086 --mojo-platform-channel-handle=3892 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 765
Read events
1 571
Write events
170
Delete events
24
Modification events
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3272-13227878136522750 |
Value: 259 | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (3272) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
8
Suspicious files
59
Text files
269
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E60D5F8-CC8.pma | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\07608b20-ee7b-4e05-957b-ce0b3a42c5b0.tmp | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RFa65d6a.TMP | text | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFa65d0c.TMP | text | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa65e83.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
66
DNS requests
41
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3672 | lawnmower.exe | GET | 301 | 104.16.155.36:80 | http://whatismyipaddress.com/ | US | — | — | shared |
1392 | chrome.exe | GET | 200 | 143.204.101.79:80 | http://www.pepestes.com/4twejyp4%3E6hd9/setup_Your%20File%20Is%20Ready%20To%20Download.exe | US | executable | 2.93 Mb | malicious |
1392 | chrome.exe | GET | 302 | 216.58.210.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 509 b | whitelisted |
1392 | chrome.exe | GET | 302 | 52.214.251.189:80 | http://trk.yarndestruction.club/aff_r?offer_id=194&aff_id=1000&url=https%3A%2F%2Fd1ujltfh043bem.cloudfront.net%2Fi%2Findex.php%3Fch%3D102f2b0dd0322da4ca12704dbd9685%26t%3DYour%2520File%2520Is%2520Ready%2520To%2520Download&urlauth=282161769347176488362835140765 | IE | html | 314 b | suspicious |
1392 | chrome.exe | GET | 200 | 143.204.101.43:80 | http://care.stoneglove.xyz/fit/Your%20File%20Is%20Ready%20To%20Download/2230164319949921988/714041/ | US | html | 6.66 Kb | suspicious |
1392 | chrome.exe | GET | 302 | 52.214.251.189:80 | http://trk.yarndestruction.club/aff_c?source=9945&offer_id=194&aff_id=1000&aff_sub=2230164319949921988&aff_sub2=714041&aff_sub3=&aff_sub4=browser&aff_sub5=9945&aff_unique1=&aff_unique2=&aff_unique3=&name=Your%20File%20Is%20Ready%20To%20Download&url= | IE | html | 425 b | suspicious |
1392 | chrome.exe | GET | 302 | 216.58.210.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 514 b | whitelisted |
1392 | chrome.exe | GET | 200 | 143.204.101.94:80 | http://arm.deskocean.xyz/cbcccb6dd340b032125f2da01d3241086275/ | US | html | 2.96 Kb | malicious |
1392 | chrome.exe | GET | 200 | 74.125.4.203:80 | http://r5---sn-aigzrner.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mip=185.192.69.26&mm=28&mn=sn-aigzrner&ms=nvh&mt=1583404456&mv=m&mvi=4&pl=24&shardbypass=yes | US | crx | 293 Kb | whitelisted |
1392 | chrome.exe | GET | 404 | 143.204.101.43:80 | http://care.stoneglove.xyz/favicon.ico | US | html | 571 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1392 | chrome.exe | 104.31.87.73:443 | anonfile.com | Cloudflare Inc | US | unknown |
1392 | chrome.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
1392 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1392 | chrome.exe | 216.58.208.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
1392 | chrome.exe | 143.204.98.51:443 | d3ud741uvs727m.cloudfront.net | — | US | malicious |
1392 | chrome.exe | 104.18.10.142:443 | singlyglobalti.info | Cloudflare Inc | US | unknown |
1392 | chrome.exe | 172.217.18.13:443 | — | Google Inc. | US | whitelisted |
1392 | chrome.exe | 34.227.211.119:443 | nedconstance.info | Amazon.com, Inc. | US | unknown |
1392 | chrome.exe | 104.24.99.165:443 | feenotifyfriends.info | Cloudflare Inc | US | shared |
1392 | chrome.exe | 52.72.152.124:443 | teachievedim.site | Amazon.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
anonfile.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
vjs.zencdn.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
shermore.info |
| whitelisted |
d3ud741uvs727m.cloudfront.net |
| whitelisted |
www.google-analytics.com |
| whitelisted |
singlyglobalti.info |
| shared |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1392 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1392 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1392 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1392 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1392 | chrome.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3672 | lawnmower.exe | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
3672 | lawnmower.exe | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
3672 | lawnmower.exe | A Network Trojan was detected | SPYWARE [PTsecurity] HawkEye / Predator Pain (IP Chck) |
3672 | lawnmower.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3 ETPRO signatures available at the full report