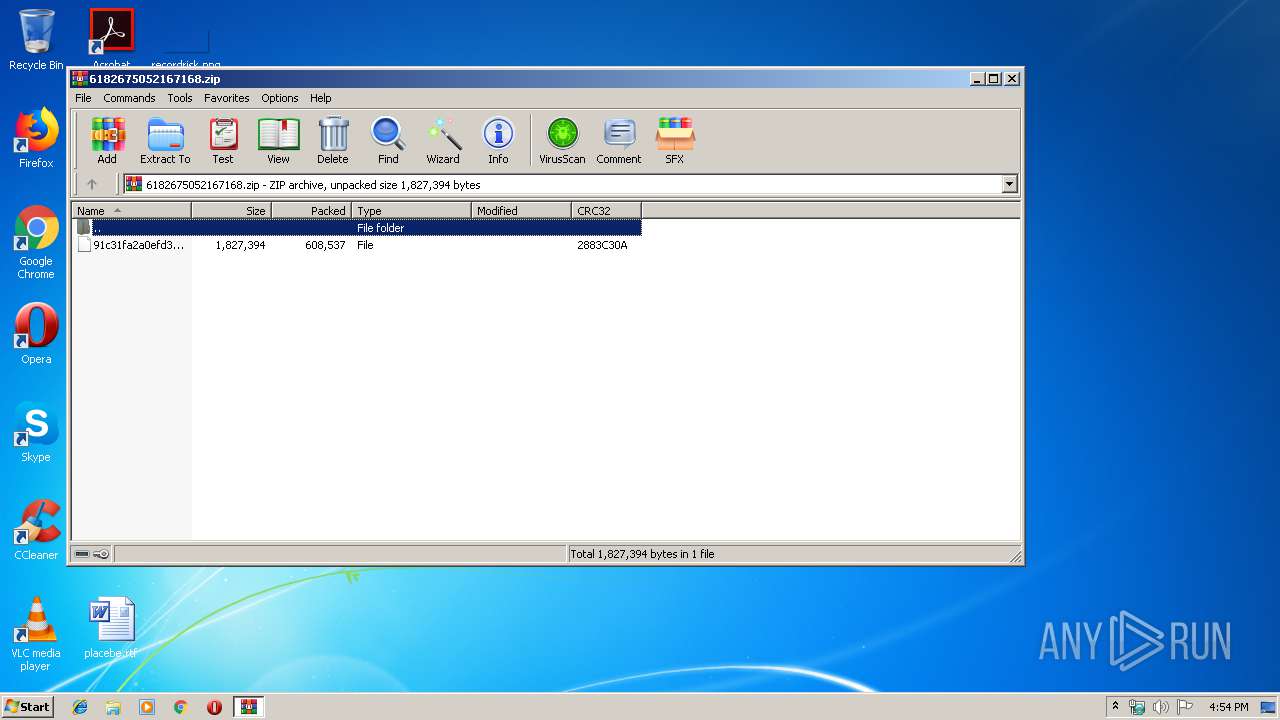
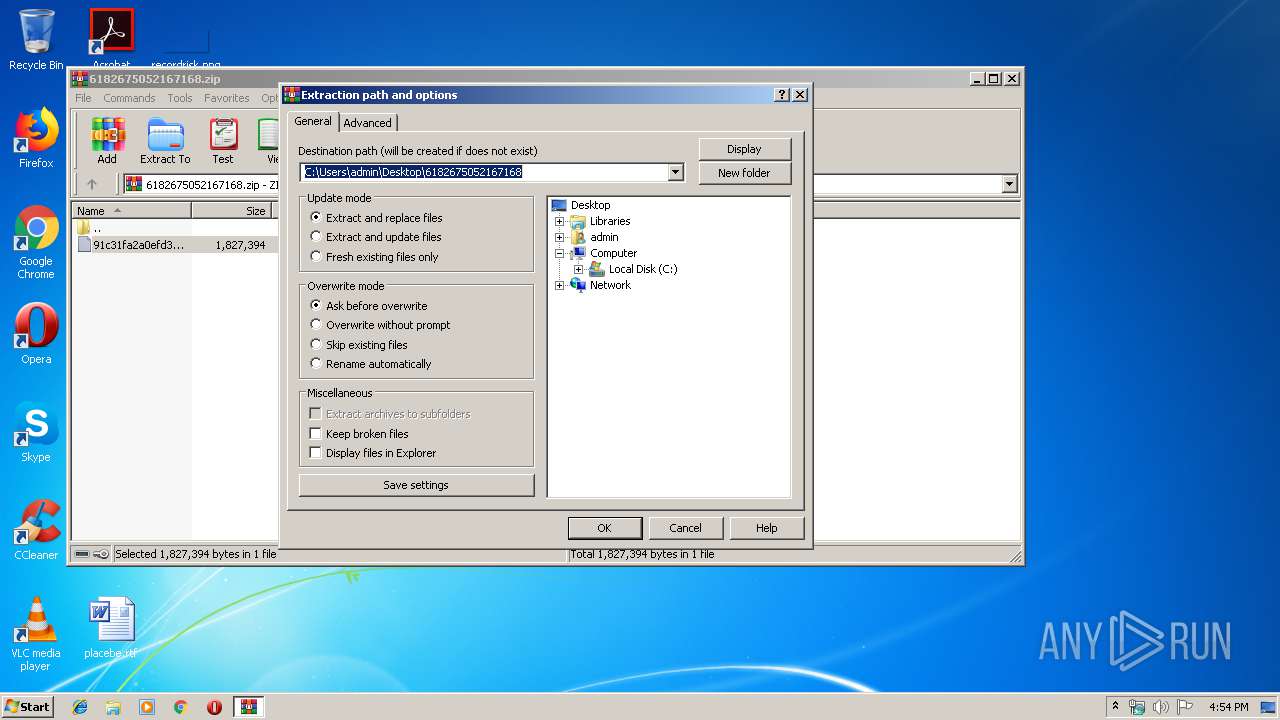
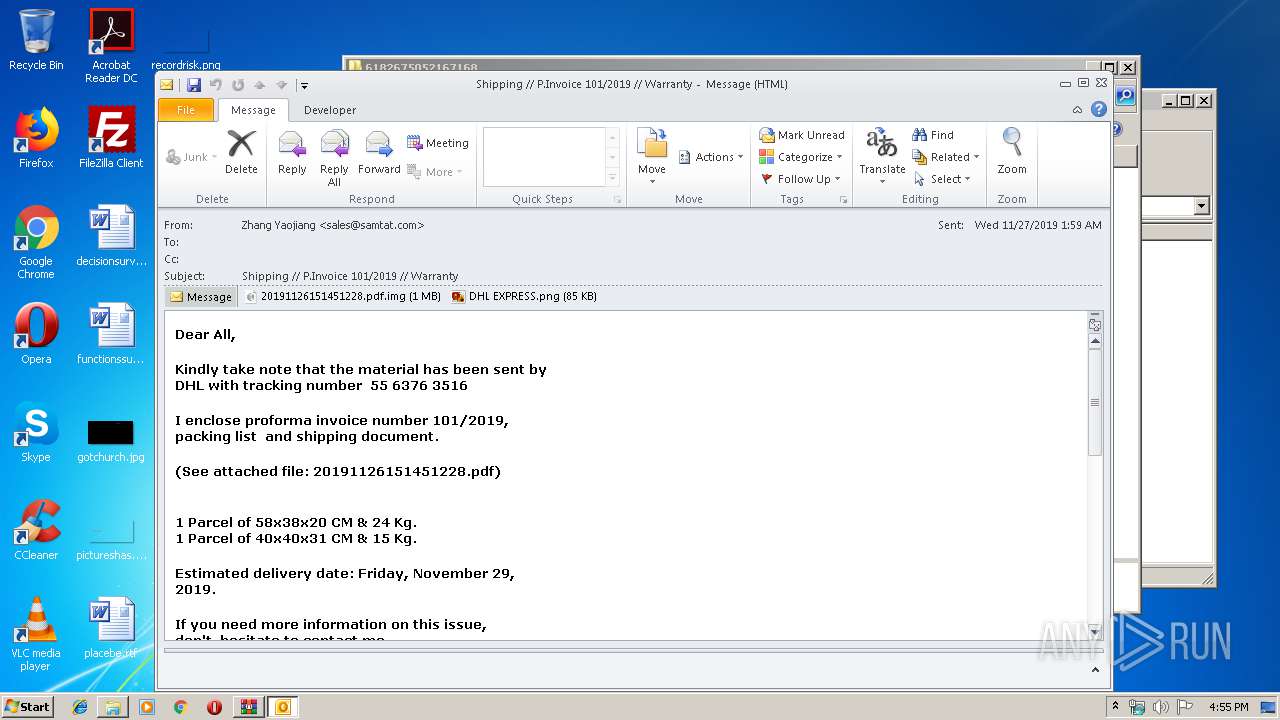
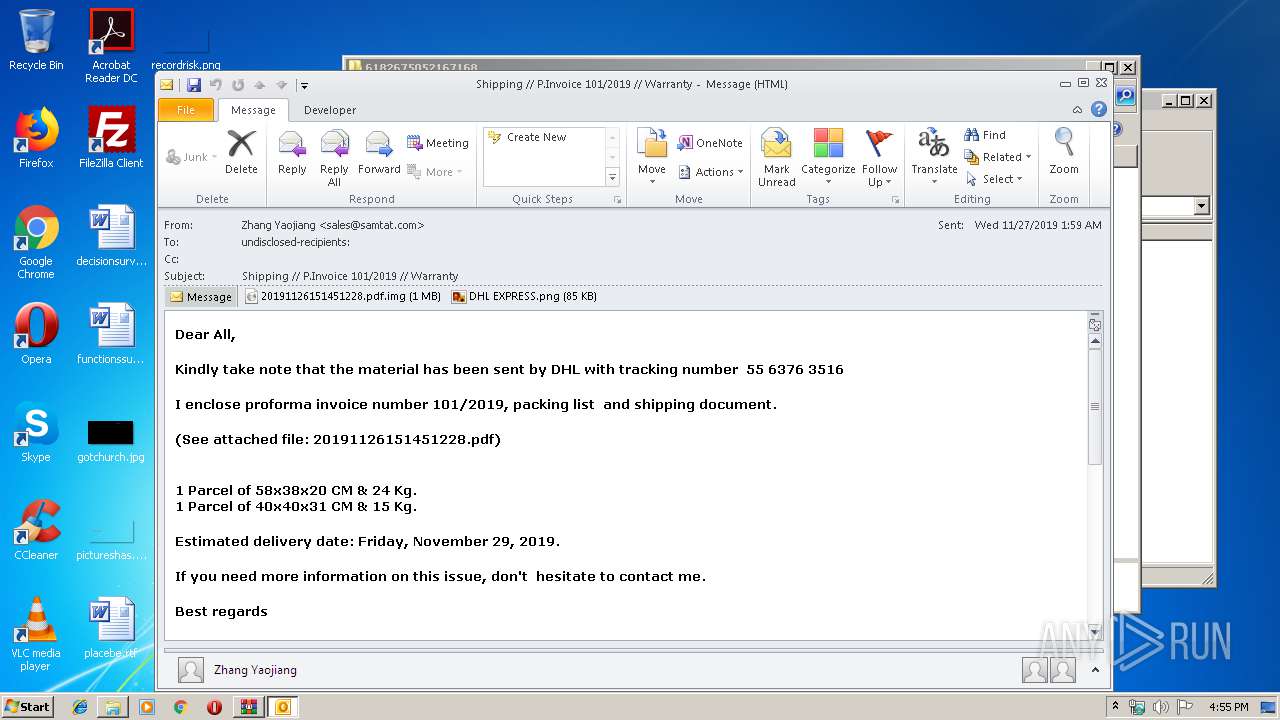
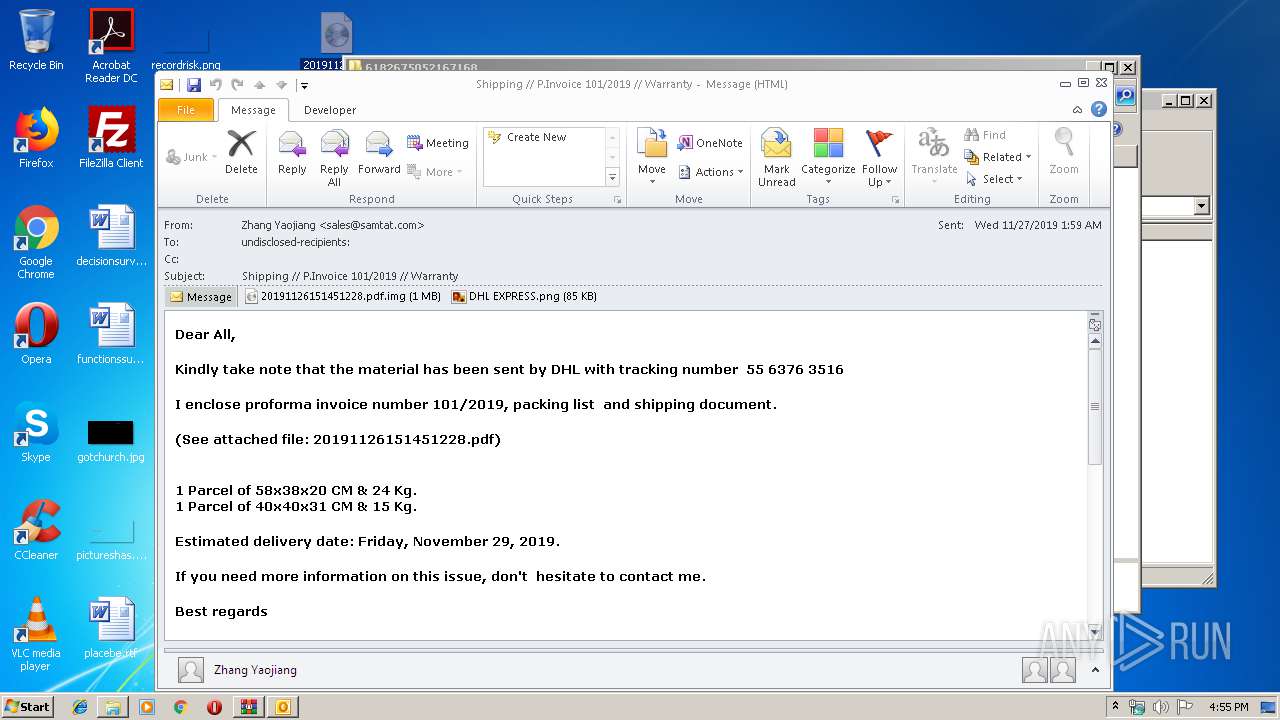
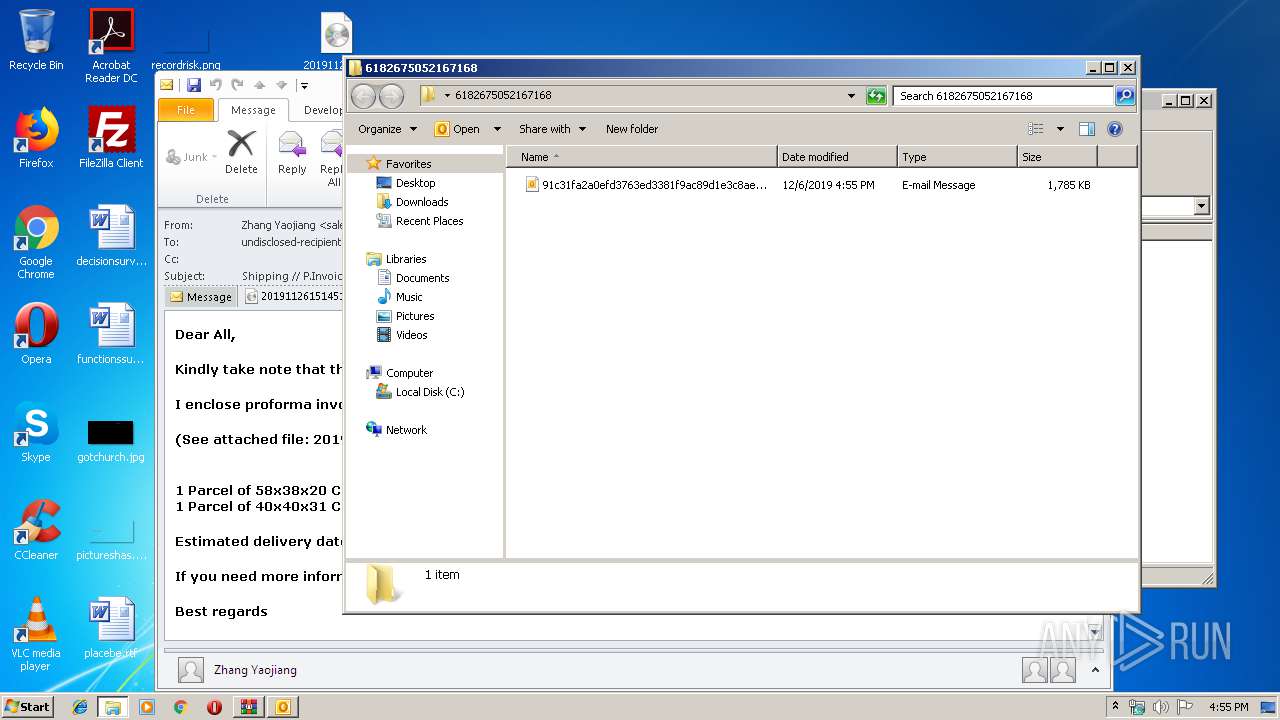
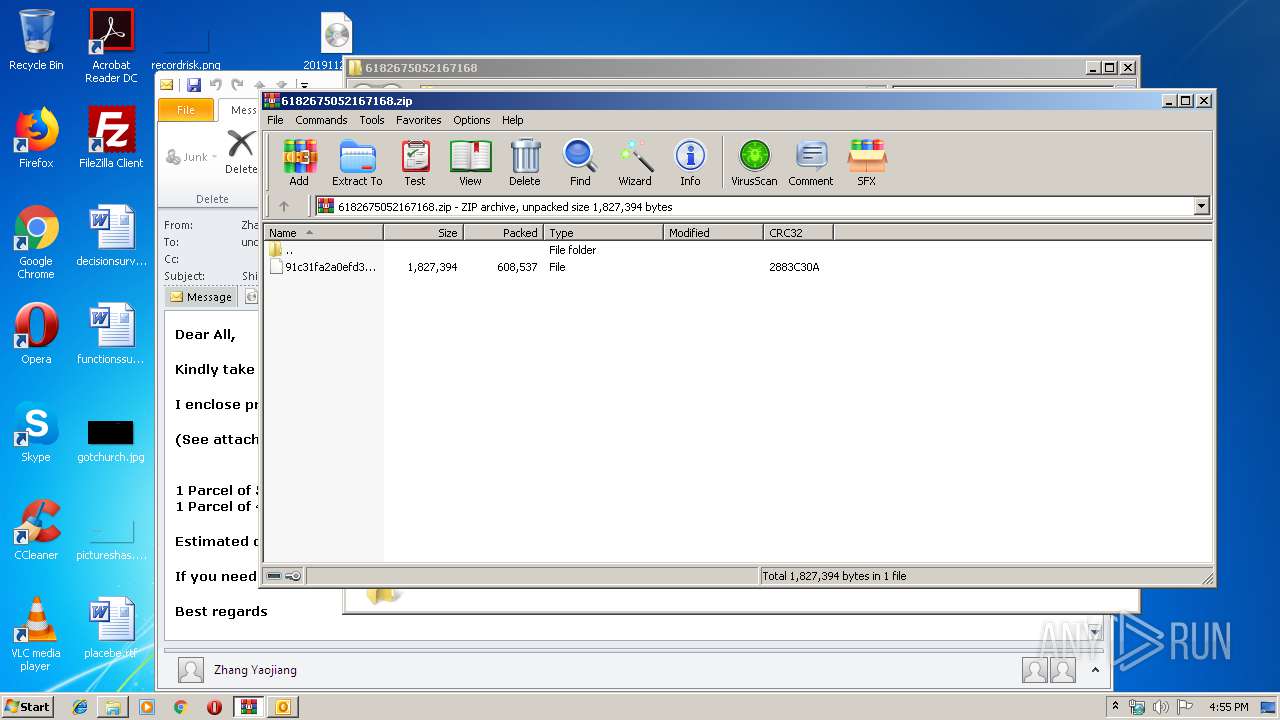
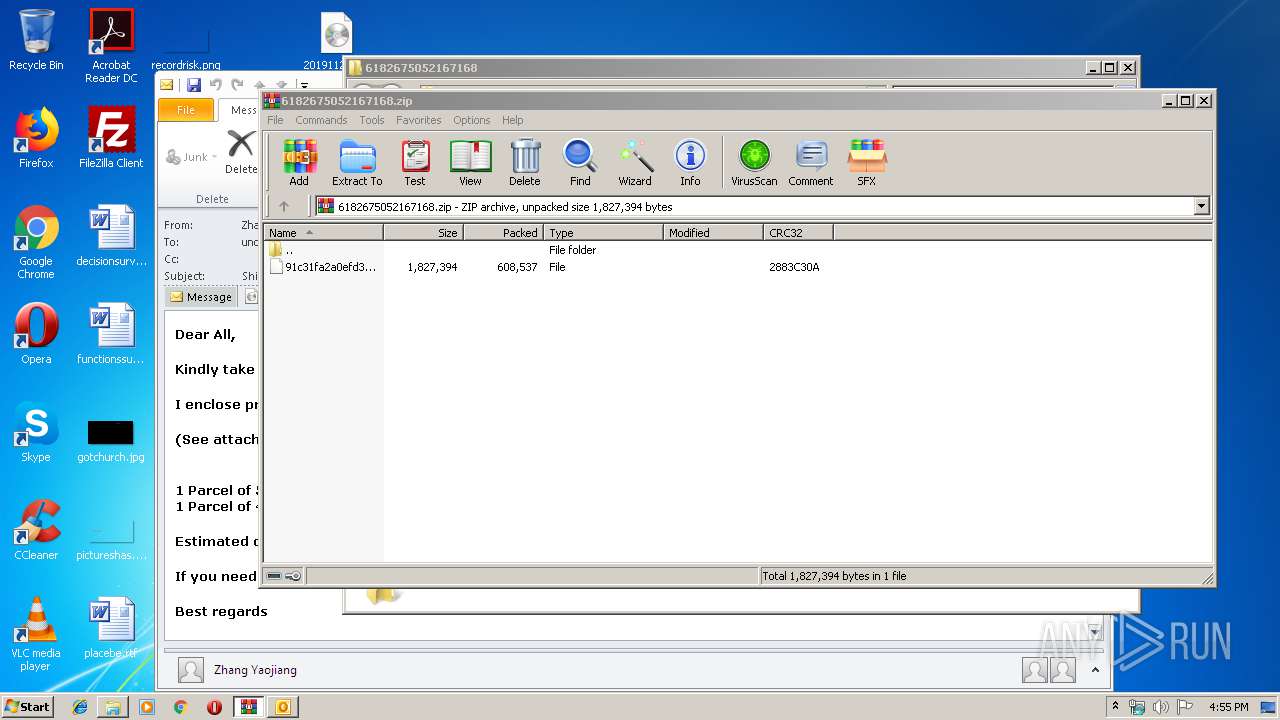
| File name: | 6182675052167168.zip |
| Full analysis: | https://app.any.run/tasks/64c5725f-ef27-433a-b80a-e278c1551874 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | December 06, 2019, 16:54:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D3C9853EC960A8E422E87118EB8E93A3 |
| SHA1: | EEB1A8DD827B2A77655C977CD03416BA1A2D0829 |
| SHA256: | F40DB9870302DA73BC149A9E0047C150E97E2D2414AC51FD376C007884A649E8 |
| SSDEEP: | 12288:e9yacjMNf6fzGhXsZJesdo3xr9hC381FBPf86iR1OHRyRaeAqLH:e9ya6rfzu1sda5hrF4eYRa9qLH |
MALICIOUS
Application was dropped or rewritten from another process
- Hdduvn2lWgw6Tw7.exe (PID: 1820)
- Hdduvn2lWgw6Tw7.exe (PID: 2816)
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
Changes the autorun value in the registry
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
AGENTTESLA was detected
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
Actions looks like stealing of personal data
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2092)
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1516)
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2092)
Application launched itself
- Hdduvn2lWgw6Tw7.exe (PID: 2816)
- WinRAR.exe (PID: 1880)
Reads the cookies of Mozilla Firefox
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
Reads the cookies of Google Chrome
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
Checks for external IP
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
Connects to SMTP port
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
INFO
Manual execution by user
- Hdduvn2lWgw6Tw7.exe (PID: 1820)
- OUTLOOK.EXE (PID: 2092)
Reads settings of System Certificates
- Hdduvn2lWgw6Tw7.exe (PID: 1976)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2092)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 1880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x2883c30a |
| ZipCompressedSize: | 608537 |
| ZipUncompressedSize: | 1827394 |
| ZipFileName: | 91c31fa2a0efd3763ed3381f9ac89d1e3c8ae70c5b6dae4efe0b225ec323144b |
Total processes
49
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
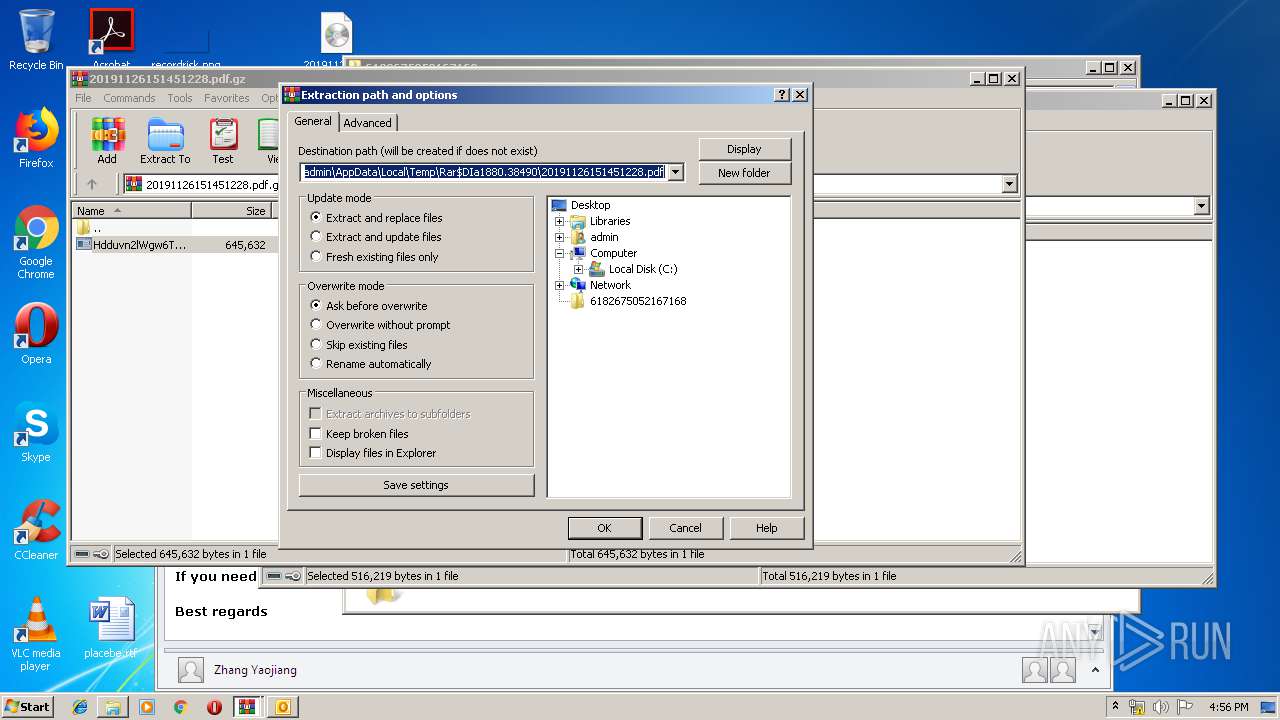
| 1516 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa1880.38490\20191126151451228.pdf.gz | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\Desktop\Hdduvn2lWgw6Tw7.exe" | C:\Users\admin\Desktop\Hdduvn2lWgw6Tw7.exe | — | explorer.exe | |||||||||||
User: admin Company: Salan S. Al-Ani Integrity Level: MEDIUM Description: Data Grid View Printer App Exit code: 4294967295 Version: 2.2.6.0 Modules
| |||||||||||||||
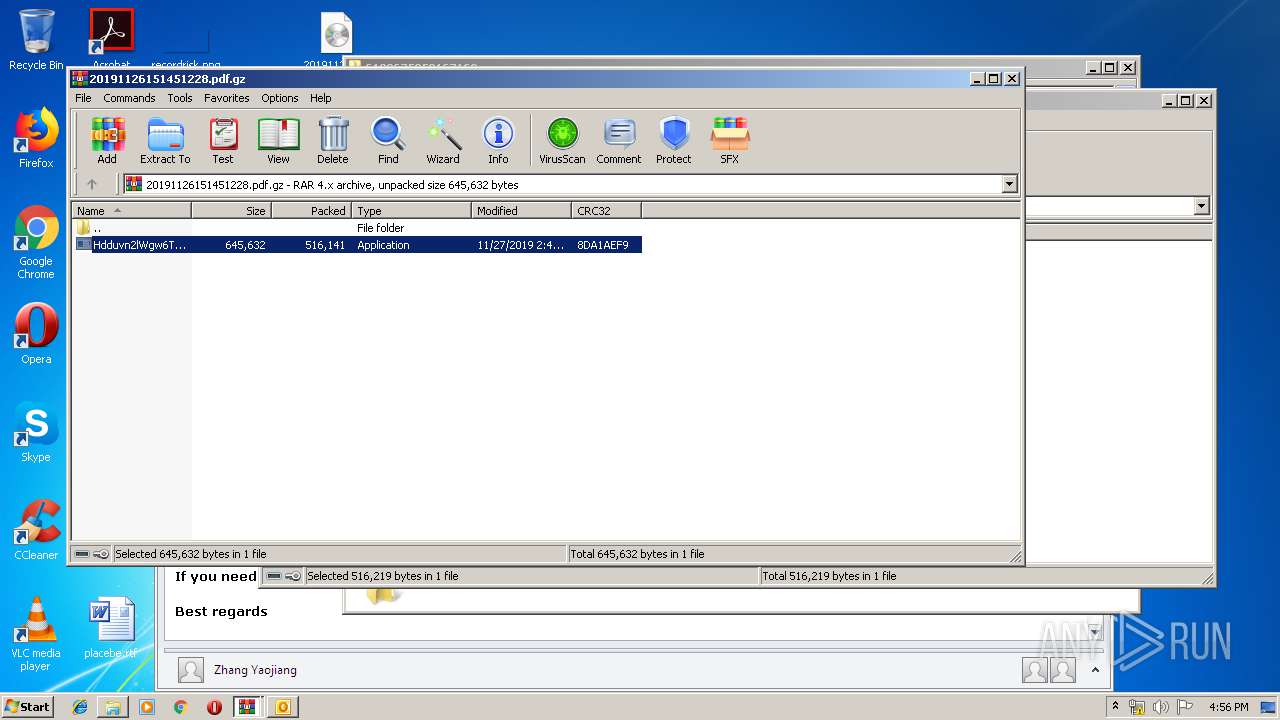
| 1880 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\6182675052167168.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1976 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1516.39528\Hdduvn2lWgw6Tw7.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1516.39528\Hdduvn2lWgw6Tw7.exe | Hdduvn2lWgw6Tw7.exe | ||||||||||||
User: admin Company: Salan S. Al-Ani Integrity Level: MEDIUM Description: Data Grid View Printer App Exit code: 0 Version: 2.2.6.0 Modules
| |||||||||||||||
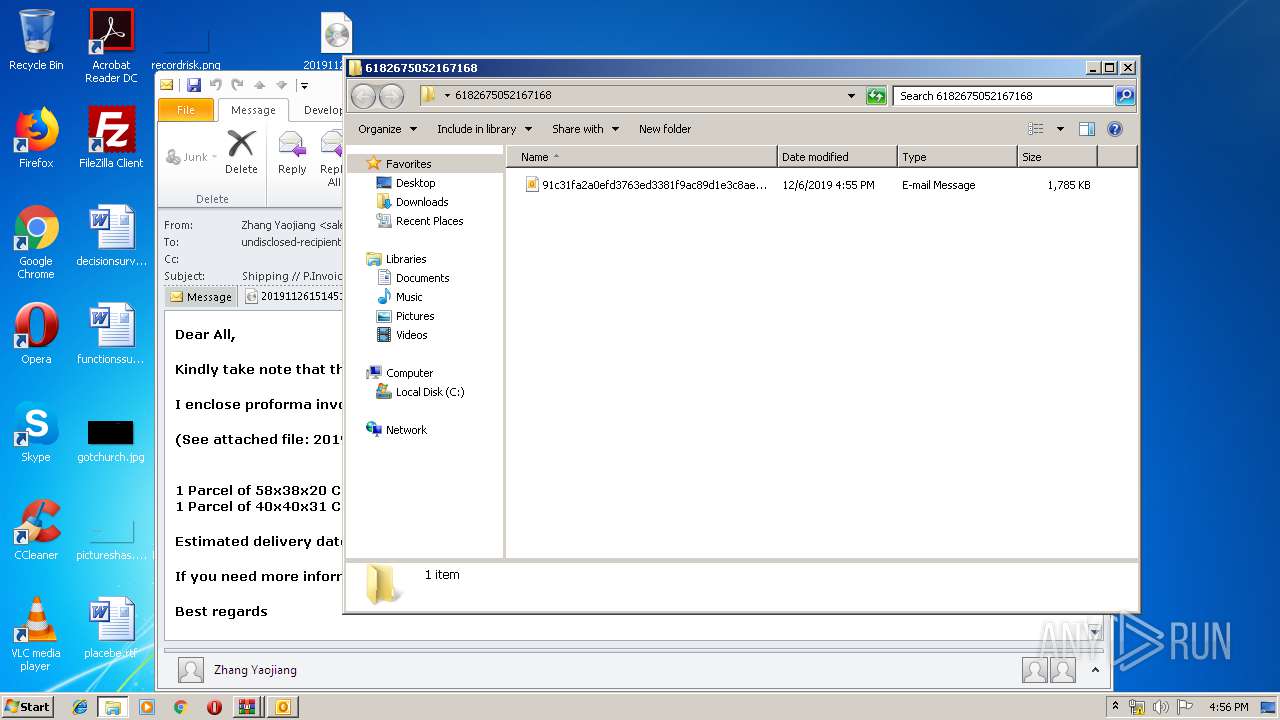
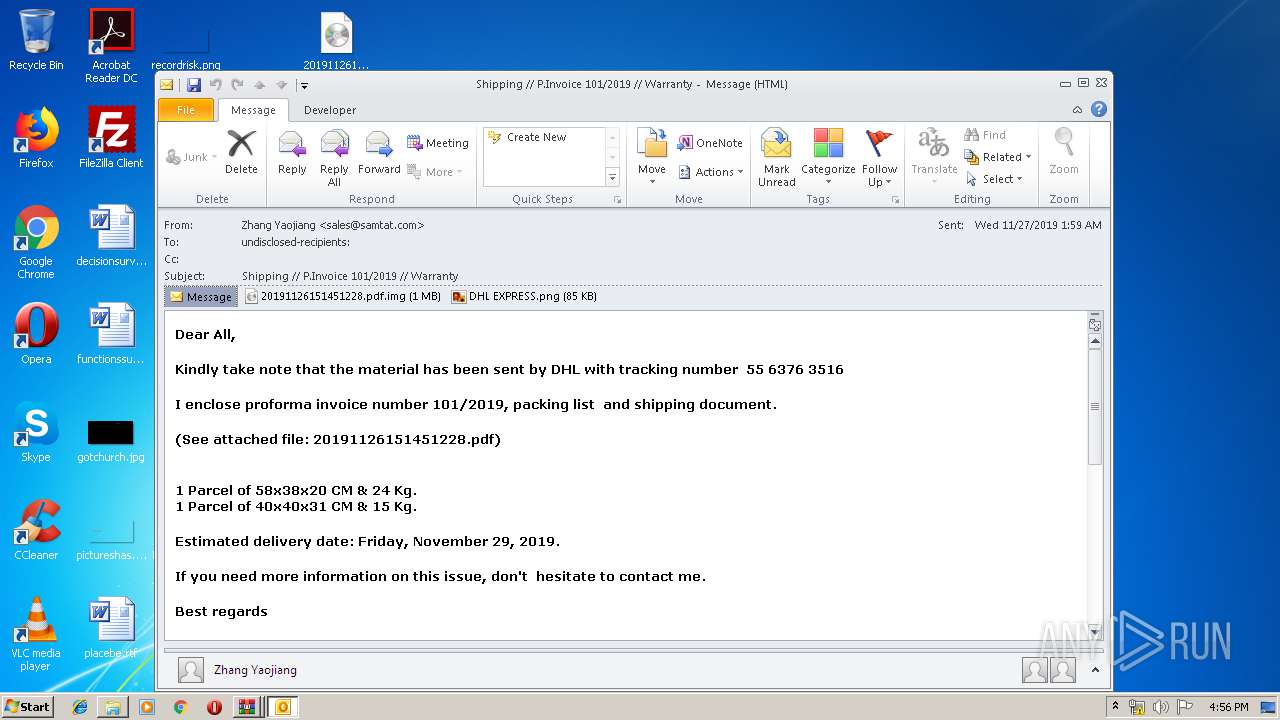
| 2092 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\6182675052167168\91c31fa2a0efd3763ed3381f9ac89d1e3c8ae70c5b6dae4efe0b225ec323144b.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2816 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1516.39528\Hdduvn2lWgw6Tw7.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1516.39528\Hdduvn2lWgw6Tw7.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Salan S. Al-Ani Integrity Level: MEDIUM Description: Data Grid View Printer App Exit code: 0 Version: 2.2.6.0 Modules
| |||||||||||||||
Total events
2 728
Read events
2 020
Write events
688
Delete events
20
Modification events
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\6182675052167168.zip | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\6182675052167168 | |||
| (PID) Process: | (1880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
3
Suspicious files
2
Text files
28
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2092 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR3F7F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2092 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp4194.tmp | — | |
MD5:— | SHA256:— | |||
| 1976 | Hdduvn2lWgw6Tw7.exe | C:\Users\admin\AppData\Roaming\fkv1u1ql.2lf\Chrome\Default\Cookies | — | |
MD5:— | SHA256:— | |||
| 1976 | Hdduvn2lWgw6Tw7.exe | C:\Users\admin\AppData\Roaming\fkv1u1ql.2lf\Firefox\Profiles\qldyz51w.default\cookies.sqlite | — | |
MD5:— | SHA256:— | |||
| 2092 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2092 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\44BDDWVS\20191126151451228 pdf.img | gmc | |
MD5:— | SHA256:— | |||
| 2092 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{B414DDFD-3A4A-4866-8786-F01061CDA9F1}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:7D80C0A7E3849818695EAF4989186A3C | SHA256:72DC527D78A8E99331409803811CC2D287E812C008A1C869A6AEA69D7A44B597 | |||
| 1880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1880.38490\20191126151451228.pdf.gz | compressed | |
MD5:— | SHA256:— | |||
| 1976 | Hdduvn2lWgw6Tw7.exe | C:\Users\admin\AppData\Roaming\MyApp\MyApp.exe | executable | |
MD5:— | SHA256:— | |||
| 2092 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_2F71466E639C884DB9D63E559FDB2091.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
3
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1976 | Hdduvn2lWgw6Tw7.exe | GET | 200 | 34.196.181.158:80 | http://checkip.amazonaws.com/ | US | text | 13 b | malicious |
2092 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1976 | Hdduvn2lWgw6Tw7.exe | 34.196.181.158:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
2092 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
1976 | Hdduvn2lWgw6Tw7.exe | 198.54.122.60:587 | mail.privateemail.com | Namecheap, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
checkip.amazonaws.com |
| malicious |
mail.privateemail.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1976 | Hdduvn2lWgw6Tw7.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
1976 | Hdduvn2lWgw6Tw7.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
1976 | Hdduvn2lWgw6Tw7.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3 ETPRO signatures available at the full report