| File name: | payroll.docx.exe |
| Full analysis: | https://app.any.run/tasks/94a346ca-c717-4593-ab83-c14a5ca0df80 |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | August 17, 2024, 11:33:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 9B746C7D207122FDD040B8003BF1A535 |
| SHA1: | 59C1CF766FCFDB2542947A43466AC1A8F7D04A46 |
| SHA256: | F2CF1D12365B1880325E9A6E2CE4315F96D33B5CADB815398870D7D49B58F9BB |
| SSDEEP: | 1536:OIxL0u7FfOMEgl8CwRidsssssssssIiBKPxeDLNbjebcTcV:B/9zdsssssssssZB3PNbjKcTcV |
MALICIOUS
Starts CMD.EXE for self-deleting
- payroll.docx.exe (PID: 6408)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6700)
Renames files like ransomware
- payroll.docx.exe (PID: 5944)
ETERNITY has been detected (YARA)
- payroll.docx.exe (PID: 6788)
- payroll.docx.exe (PID: 5944)
SUSPICIOUS
Drops the executable file immediately after the start
- payroll.docx.exe (PID: 6408)
Reads security settings of Internet Explorer
- payroll.docx.exe (PID: 6408)
Reads the date of Windows installation
- payroll.docx.exe (PID: 6408)
Executable content was dropped or overwritten
- payroll.docx.exe (PID: 6408)
The executable file from the user directory is run by the CMD process
- payroll.docx.exe (PID: 5944)
Starts application with an unusual extension
- cmd.exe (PID: 6700)
Starts CMD.EXE for commands execution
- payroll.docx.exe (PID: 6408)
The process executes via Task Scheduler
- payroll.docx.exe (PID: 6788)
INFO
Reads the computer name
- payroll.docx.exe (PID: 6408)
- payroll.docx.exe (PID: 5944)
- payroll.docx.exe (PID: 6788)
Checks supported languages
- payroll.docx.exe (PID: 6408)
- chcp.com (PID: 6768)
- payroll.docx.exe (PID: 5944)
- payroll.docx.exe (PID: 6788)
Reads the machine GUID from the registry
- payroll.docx.exe (PID: 6408)
- payroll.docx.exe (PID: 5944)
- payroll.docx.exe (PID: 6788)
Changes the display of characters in the console
- chcp.com (PID: 6768)
Process checks computer location settings
- payroll.docx.exe (PID: 6408)
Creates files or folders in the user directory
- payroll.docx.exe (PID: 6408)
Checks proxy server information
- payroll.docx.exe (PID: 5944)
- payroll.docx.exe (PID: 6788)
Reads Environment values
- payroll.docx.exe (PID: 5944)
- payroll.docx.exe (PID: 6788)
Disables trace logs
- payroll.docx.exe (PID: 5944)
- payroll.docx.exe (PID: 6788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Eternity
(PID) Process(5944) payroll.docx.exe
Strings (95)ServiceHub
/C chcp 65001 &&
ping 127.0.0.1 &&
schtasks /create /tn "{0}" /sc MINUTE /tr "{1}" /rl {2} /f &&
LIMITED
HIGHEST
DEL /F /S /Q /A "{0}" &&
cmd.exe
uk
Glory to Ukraine!
Blocked
Locked
Unlocked
Software
TimeLeft
Software
TimeLeft
Data deleted
Time Left:
{0}
dd\:hh\:mm\:ss
Please specify key file path
Please select private key (not public)
Invalid key
Failed decrypt:
Error
Data decrypted!
Success!
Select private key file
key Files|*.rsa
Arial
textBoxPrivateKeyPath
Yu Gothic UI
buttonDecrypt
Decrypt
Yu Gothic UI
labelEncryptionKey
Private key file:
Yu Gothic UI
textBoxDescription
Sample text
labelTitle
Eternity Ransomware
Yu Gothic UI
buttonExit
panelControls
Yu Gothic UI
buttonMinimize
-
Yu Gothic UI
buttonBrowsePrivateKeyFile
. . .
Yu Gothic UI
labelTimeLeft
Time Left:
--.--.--.--
pictureBoxEncryptionState
MainForm
Eternity
0
Firefox
<RSAKeyValue><Modulus>uMahuum2IaH1q+tvXCG01qfv2gNuPX8BRT2ErT5c4C2MNnttJS5+l4sAPF1MYlrAKHXNy01sIsGcB+R/Q68hOxjt20Uke14+EZl9W2CJhkzsH9MFzwYgmncJjWiK53S9m52K+zrRUNm65WQvTJ7XIy7flFs2hG3auEOeGV/Tf2MdaXVXdZcbg1M37RVew7uXjAjsBIhuLc6MnJs5XTx1OKeAMOAl046vYeW6ePagUOV3hRJaE8K639mkFDXlKjV4ZvTIyqyLI/49ze1KId9mNd...
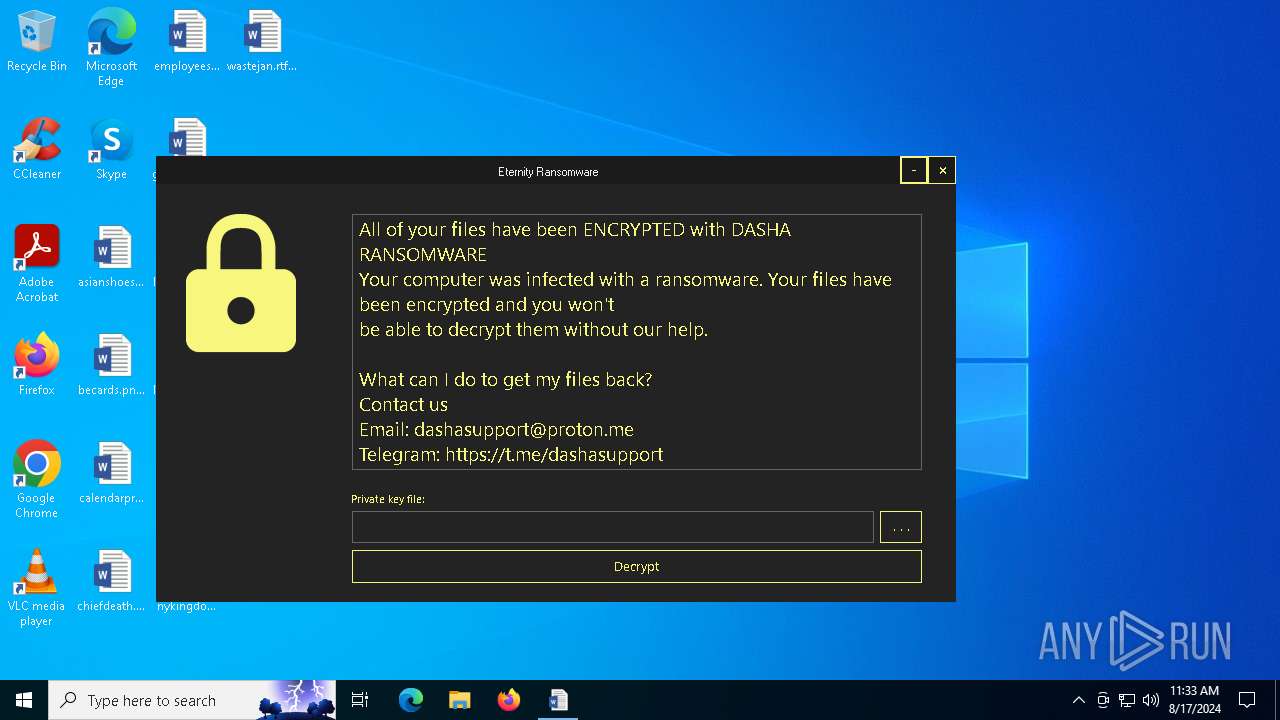
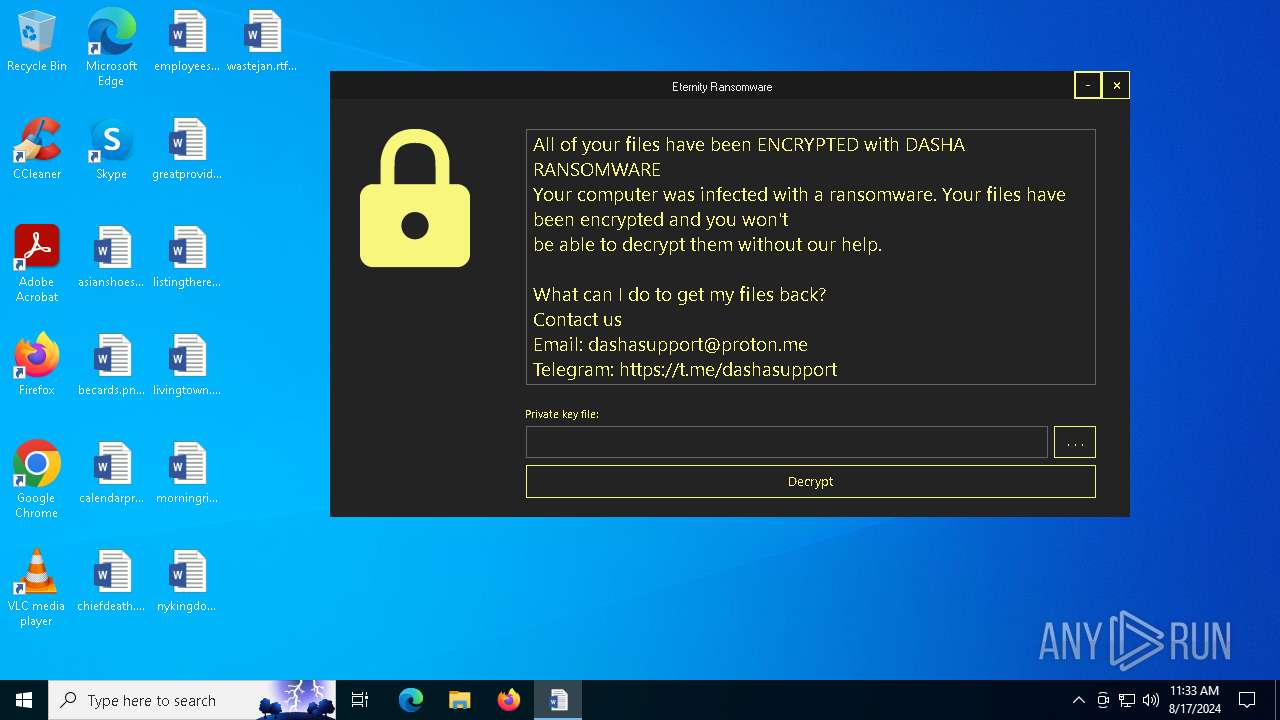
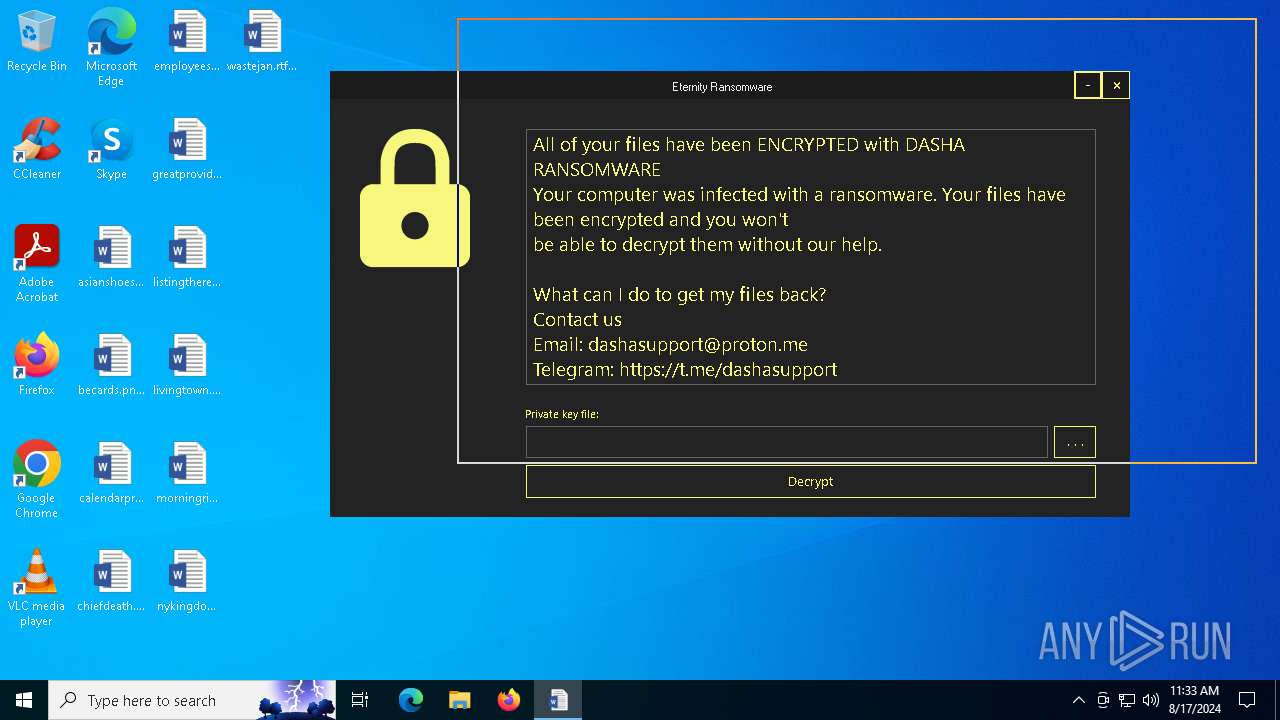
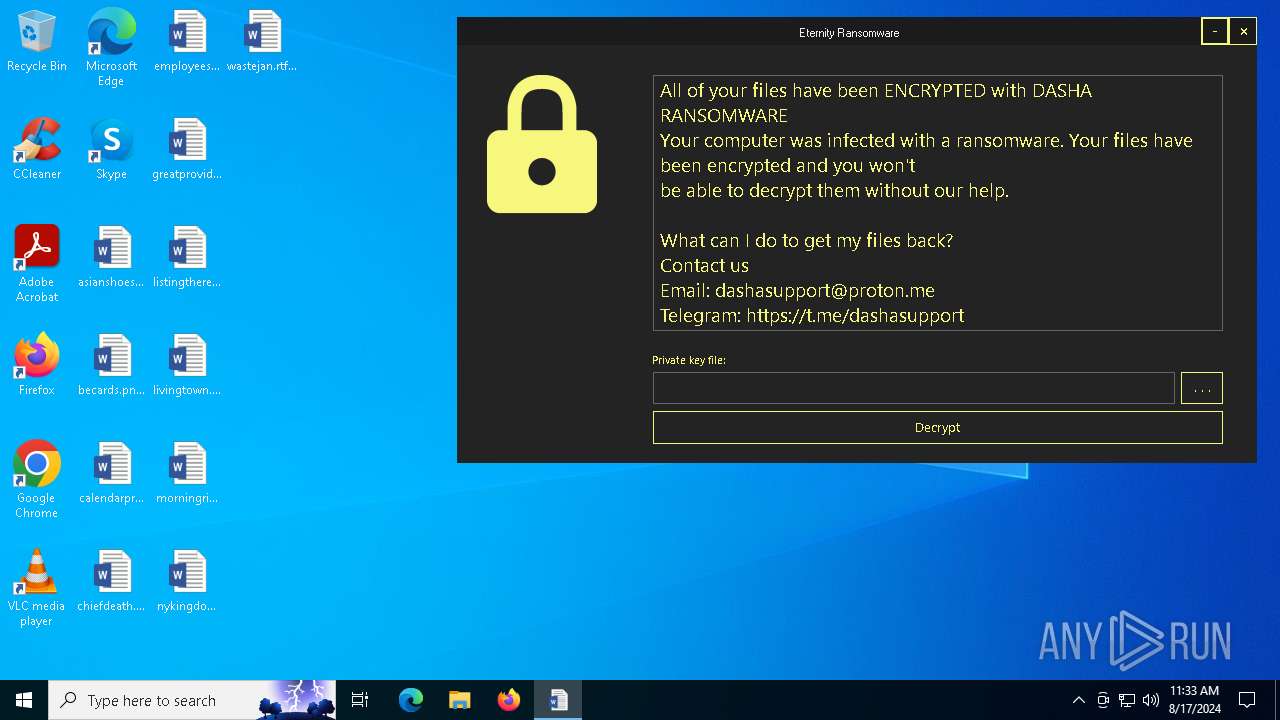
All of your files have been ENCRYPTED with DASHA RANSOMWARE
Your computer was infected with a ransomware. Your files have been encrypted and you won't
be able to decrypt them without our help.
What can I do to get my files back?
Contact us
Email: dashasupport@proton.me
Telegram: https://t.me...
https://satid-gob.mx/dasha.jpeg
.png .jpg .psd .wav .avi .mp3 .mp4 .jpeg .php .xlsm .dat .php
.txt .xls .doc .rtf .ppt .pdf .sql .docx .html .py .dll .iso .xml .bin
.pem .der .kbd .zip .rar .7z .zip .json .jar .mdb .docm .apk .msi
db key src source project pass coin bank info wallet secret security backup log phrase report reco...
.ecrp
ngrhlkskvz
*
Software
cmd.exe
/C chcp 65001 && ping 127.0.0.1 && DEL /F /S /Q /A "{0}"
[EncryptFile] {0}
RSA private key required to decrypt credentials!
[DecryptFile] {0}
USERPROFILE
Downloads
DropBox
OneDrive
Software
EncryptedKeys
Software
Classes
shell\open\command
%1
\\.\root\default
systemrestore
sequencenumber
cmd.exe
/C chcp 65001 && vssadmin delete shadows /all /quiet
wallpaper.bmp
Control Panel\Desktop
WallpaperStyle
TileWallpaper
Eternity.Properties.Resources
(PID) Process(6788) payroll.docx.exe
Strings (95)ServiceHub
/C chcp 65001 &&
ping 127.0.0.1 &&
schtasks /create /tn "{0}" /sc MINUTE /tr "{1}" /rl {2} /f &&
LIMITED
HIGHEST
DEL /F /S /Q /A "{0}" &&
cmd.exe
uk
Glory to Ukraine!
Blocked
Locked
Unlocked
Software
TimeLeft
Software
TimeLeft
Data deleted
Time Left:
{0}
dd\:hh\:mm\:ss
Please specify key file path
Please select private key (not public)
Invalid key
Failed decrypt:
Error
Data decrypted!
Success!
Select private key file
key Files|*.rsa
Arial
textBoxPrivateKeyPath
Yu Gothic UI
buttonDecrypt
Decrypt
Yu Gothic UI
labelEncryptionKey
Private key file:
Yu Gothic UI
textBoxDescription
Sample text
labelTitle
Eternity Ransomware
Yu Gothic UI
buttonExit
panelControls
Yu Gothic UI
buttonMinimize
-
Yu Gothic UI
buttonBrowsePrivateKeyFile
. . .
Yu Gothic UI
labelTimeLeft
Time Left:
--.--.--.--
pictureBoxEncryptionState
MainForm
Eternity
0
Firefox
<RSAKeyValue><Modulus>uMahuum2IaH1q+tvXCG01qfv2gNuPX8BRT2ErT5c4C2MNnttJS5+l4sAPF1MYlrAKHXNy01sIsGcB+R/Q68hOxjt20Uke14+EZl9W2CJhkzsH9MFzwYgmncJjWiK53S9m52K+zrRUNm65WQvTJ7XIy7flFs2hG3auEOeGV/Tf2MdaXVXdZcbg1M37RVew7uXjAjsBIhuLc6MnJs5XTx1OKeAMOAl046vYeW6ePagUOV3hRJaE8K639mkFDXlKjV4ZvTIyqyLI/49ze1KId9mNd...
All of your files have been ENCRYPTED with DASHA RANSOMWARE
Your computer was infected with a ransomware. Your files have been encrypted and you won't
be able to decrypt them without our help.
What can I do to get my files back?
Contact us
Email: dashasupport@proton.me
Telegram: https://t.me...
https://satid-gob.mx/dasha.jpeg
.png .jpg .psd .wav .avi .mp3 .mp4 .jpeg .php .xlsm .dat .php
.txt .xls .doc .rtf .ppt .pdf .sql .docx .html .py .dll .iso .xml .bin
.pem .der .kbd .zip .rar .7z .zip .json .jar .mdb .docm .apk .msi
db key src source project pass coin bank info wallet secret security backup log phrase report reco...
.ecrp
ngrhlkskvz
*
Software
cmd.exe
/C chcp 65001 && ping 127.0.0.1 && DEL /F /S /Q /A "{0}"
[EncryptFile] {0}
RSA private key required to decrypt credentials!
[DecryptFile] {0}
USERPROFILE
Downloads
DropBox
OneDrive
Software
EncryptedKeys
Software
Classes
shell\open\command
%1
\\.\root\default
systemrestore
sequencenumber
cmd.exe
/C chcp 65001 && vssadmin delete shadows /all /quiet
wallpaper.bmp
Control Panel\Desktop
WallpaperStyle
TileWallpaper
Eternity.Properties.Resources
TRiD
| .exe | | | Win64 Executable (generic) (49.4) |
|---|---|---|
| .scr | | | Windows screen saver (23.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (11.7) |
| .exe | | | Win32 Executable (generic) (8) |
| .exe | | | Generic Win/DOS Executable (3.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2103:10:13 03:19:28+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 91648 |
| InitializedDataSize: | 19456 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1851e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Windows Security Services |
| FileVersion: | 1.0.0.4 |
| InternalName: | Eternity.exe |
| LegalCopyright: | Copyright © Microsoft 2021 |
| LegalTrademarks: | - |
| OriginalFileName: | Eternity.exe |
| ProductName: | Windows Security Services |
| ProductVersion: | 1.0.0.4 |
| AssemblyVersion: | 1.0.0.4 |
Total processes
136
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2476 | schtasks /create /tn "payroll.docx" /sc MINUTE /tr "C:\Users\admin\AppData\Local\ServiceHub\payroll.docx.exe" /rl LIMITED /f | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5944 | "C:\Users\admin\AppData\Local\ServiceHub\payroll.docx.exe" | C:\Users\admin\AppData\Local\ServiceHub\payroll.docx.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Windows Security Services Version: 1.0.0.4 Modules
Eternity(PID) Process(5944) payroll.docx.exe Strings (95)ServiceHub /C chcp 65001 && ping 127.0.0.1 && schtasks /create /tn "{0}" /sc MINUTE /tr "{1}" /rl {2} /f && LIMITED HIGHEST DEL /F /S /Q /A "{0}" && cmd.exe uk Glory to Ukraine! Blocked Locked Unlocked Software TimeLeft Software TimeLeft Data deleted Time Left:
{0} dd\:hh\:mm\:ss Please specify key file path Please select private key (not public) Invalid key Failed decrypt: Error Data decrypted! Success! Select private key file key Files|*.rsa Arial textBoxPrivateKeyPath Yu Gothic UI buttonDecrypt Decrypt Yu Gothic UI labelEncryptionKey Private key file: Yu Gothic UI textBoxDescription Sample text labelTitle Eternity Ransomware Yu Gothic UI buttonExit panelControls Yu Gothic UI buttonMinimize - Yu Gothic UI buttonBrowsePrivateKeyFile . . . Yu Gothic UI labelTimeLeft Time Left:
--.--.--.-- pictureBoxEncryptionState MainForm Eternity 0 Firefox <RSAKeyValue><Modulus>uMahuum2IaH1q+tvXCG01qfv2gNuPX8BRT2ErT5c4C2MNnttJS5+l4sAPF1MYlrAKHXNy01sIsGcB+R/Q68hOxjt20Uke14+EZl9W2CJhkzsH9MFzwYgmncJjWiK53S9m52K+zrRUNm65WQvTJ7XIy7flFs2hG3auEOeGV/Tf2MdaXVXdZcbg1M37RVew7uXjAjsBIhuLc6MnJs5XTx1OKeAMOAl046vYeW6ePagUOV3hRJaE8K639mkFDXlKjV4ZvTIyqyLI/49ze1KId9mNd... All of your files have been ENCRYPTED with DASHA RANSOMWARE
Your computer was infected with a ransomware. Your files have been encrypted and you won't
be able to decrypt them without our help.
What can I do to get my files back?
Contact us
Email: dashasupport@proton.me
Telegram: https://t.me... https://satid-gob.mx/dasha.jpeg .png .jpg .psd .wav .avi .mp3 .mp4 .jpeg .php .xlsm .dat .php
.txt .xls .doc .rtf .ppt .pdf .sql .docx .html .py .dll .iso .xml .bin
.pem .der .kbd .zip .rar .7z .zip .json .jar .mdb .docm .apk .msi
db key src source project pass coin bank info wallet secret security backup log phrase report reco... .ecrp ngrhlkskvz * Software cmd.exe /C chcp 65001 && ping 127.0.0.1 && DEL /F /S /Q /A "{0}" [EncryptFile] {0} RSA private key required to decrypt credentials! [DecryptFile] {0} USERPROFILE Downloads DropBox OneDrive Software EncryptedKeys Software Classes shell\open\command %1 \\.\root\default systemrestore sequencenumber cmd.exe /C chcp 65001 && vssadmin delete shadows /all /quiet wallpaper.bmp Control Panel\Desktop WallpaperStyle TileWallpaper Eternity.Properties.Resources | |||||||||||||||
| 6408 | "C:\Users\admin\AppData\Local\Temp\payroll.docx.exe" | C:\Users\admin\AppData\Local\Temp\payroll.docx.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Windows Security Services Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 6700 | "C:\Windows\System32\cmd.exe" /C chcp 65001 && ping 127.0.0.1 && schtasks /create /tn "payroll.docx" /sc MINUTE /tr "C:\Users\admin\AppData\Local\ServiceHub\payroll.docx.exe" /rl LIMITED /f && DEL /F /S /Q /A "C:\Users\admin\AppData\Local\Temp\payroll.docx.exe" &&START "" "C:\Users\admin\AppData\Local\ServiceHub\payroll.docx.exe" | C:\Windows\SysWOW64\cmd.exe | — | payroll.docx.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6768 | chcp 65001 | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | ping 127.0.0.1 | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | "C:\Users\admin\AppData\Local\ServiceHub\payroll.docx.exe" | C:\Users\admin\AppData\Local\ServiceHub\payroll.docx.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Windows Security Services Exit code: 0 Version: 1.0.0.4 Modules
Eternity(PID) Process(6788) payroll.docx.exe Strings (95)ServiceHub /C chcp 65001 && ping 127.0.0.1 && schtasks /create /tn "{0}" /sc MINUTE /tr "{1}" /rl {2} /f && LIMITED HIGHEST DEL /F /S /Q /A "{0}" && cmd.exe uk Glory to Ukraine! Blocked Locked Unlocked Software TimeLeft Software TimeLeft Data deleted Time Left:
{0} dd\:hh\:mm\:ss Please specify key file path Please select private key (not public) Invalid key Failed decrypt: Error Data decrypted! Success! Select private key file key Files|*.rsa Arial textBoxPrivateKeyPath Yu Gothic UI buttonDecrypt Decrypt Yu Gothic UI labelEncryptionKey Private key file: Yu Gothic UI textBoxDescription Sample text labelTitle Eternity Ransomware Yu Gothic UI buttonExit panelControls Yu Gothic UI buttonMinimize - Yu Gothic UI buttonBrowsePrivateKeyFile . . . Yu Gothic UI labelTimeLeft Time Left:
--.--.--.-- pictureBoxEncryptionState MainForm Eternity 0 Firefox <RSAKeyValue><Modulus>uMahuum2IaH1q+tvXCG01qfv2gNuPX8BRT2ErT5c4C2MNnttJS5+l4sAPF1MYlrAKHXNy01sIsGcB+R/Q68hOxjt20Uke14+EZl9W2CJhkzsH9MFzwYgmncJjWiK53S9m52K+zrRUNm65WQvTJ7XIy7flFs2hG3auEOeGV/Tf2MdaXVXdZcbg1M37RVew7uXjAjsBIhuLc6MnJs5XTx1OKeAMOAl046vYeW6ePagUOV3hRJaE8K639mkFDXlKjV4ZvTIyqyLI/49ze1KId9mNd... All of your files have been ENCRYPTED with DASHA RANSOMWARE
Your computer was infected with a ransomware. Your files have been encrypted and you won't
be able to decrypt them without our help.
What can I do to get my files back?
Contact us
Email: dashasupport@proton.me
Telegram: https://t.me... https://satid-gob.mx/dasha.jpeg .png .jpg .psd .wav .avi .mp3 .mp4 .jpeg .php .xlsm .dat .php
.txt .xls .doc .rtf .ppt .pdf .sql .docx .html .py .dll .iso .xml .bin
.pem .der .kbd .zip .rar .7z .zip .json .jar .mdb .docm .apk .msi
db key src source project pass coin bank info wallet secret security backup log phrase report reco... .ecrp ngrhlkskvz * Software cmd.exe /C chcp 65001 && ping 127.0.0.1 && DEL /F /S /Q /A "{0}" [EncryptFile] {0} RSA private key required to decrypt credentials! [DecryptFile] {0} USERPROFILE Downloads DropBox OneDrive Software EncryptedKeys Software Classes shell\open\command %1 \\.\root\default systemrestore sequencenumber cmd.exe /C chcp 65001 && vssadmin delete shadows /all /quiet wallpaper.bmp Control Panel\Desktop WallpaperStyle TileWallpaper Eternity.Properties.Resources | |||||||||||||||
Total events
3 609
Read events
3 581
Write events
28
Delete events
0
Modification events
| (PID) Process: | (6408) payroll.docx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Firefox\EncryptedKeys |
| Operation: | write | Name: | 0 |
Value: ACFE52D628E4CAA7CE126AE58DED3248A0B1BEC984FD252C2ED4BA6B3AD8B23AB39B64310383EDCD4614FAEFFAE32D7DE302A19EF95DF3AE32777937EBF098FB252FDEE68A5DD4EB2ACB52768D7ADE3B869633E73663EB5B78263E3348973DD283FF8B658CB3E0CD7C9C82336667CC3BA6472097FFF911D9F3653865E32FD4EBD414C4C3A47C5747AAB2E3DF2237B0F8068A75E8B17FF4EDBB365F5F169A079CBC61AE9740BB7E36EFC5CADEC8F21B5BDF71F57CC68FC6E7C6F951B4E07375017E90F5349D3903092AC8B4C37D17F9C0C6939B0986674CF4239AA933125004360BA3538167784B0110D2CE70EA4ED78E94D59EB5300D07634A7BBFB0854A8254 | |||
| (PID) Process: | (6408) payroll.docx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6408) payroll.docx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6408) payroll.docx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6408) payroll.docx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5944) payroll.docx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Firefox\EncryptedKeys |
| Operation: | write | Name: | 1 |
Value: 732640C7FE8B9AA9C443CCBE0E9C0AF72A6A921F59E3953DF6D579C6530F571CE99756EA10BCD34073C9B0275682109844D51F9154B4B5B627FF10CC7317EE52778F42FB32CD2A48857AF0A1522A46F9066098E13E57EE2AC9D2C02FDFB74A09C5D66039F570A88D200325CBE920C8DC19E3062ACA990620EE497B2E62D158680B66415F8B1C81B207DAFDED2B625BEC2ADBFAB0DBD0067AB62E6650EE9E67FDECDC98AA7AD3AFC57E765172CE5434A0314D07D1707700839DDC41B2270620D0300463954543F129EF3CDF5D0ED39A249DBEFDD4CDEA36526B2658BC8C3D092CB009268B27C923E4BF2F685B4E82E90670B7F8BA24E856B35EE4F5E2F0099738 | |||
| (PID) Process: | (5944) payroll.docx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 93 | |||
| (PID) Process: | (5944) payroll.docx.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5944) payroll.docx.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\payroll_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5944) payroll.docx.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\payroll_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
1
Suspicious files
18
Text files
0
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\accommodationdc.jpg.ecrp | pi2 | |
MD5:A1FCAEB07C8B2666D1FB8C5B2647371D | SHA256:98FF1B3047390EC62260EFF8FC96685CB877397F852462C3981C56FFBFB21819 | |||
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\computerurl.png.ecrp | pi2 | |
MD5:83949317199D72CF9B21FF2F6F3B7A03 | SHA256:FBF7F46D52C9CC93F9612A10D16C4779B471A2435D9E52E16049750D5F6FE7D3 | |||
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\computerurl.png | pi2 | |
MD5:83949317199D72CF9B21FF2F6F3B7A03 | SHA256:FBF7F46D52C9CC93F9612A10D16C4779B471A2435D9E52E16049750D5F6FE7D3 | |||
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\limitedworking.png | pi2 | |
MD5:7FC8C92C0FE8E904842A8D8EEB2E03FA | SHA256:6B50EEFC2B5F3BBBFD28E230672137A30836131B10443F21947AC36C7071B774 | |||
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\limitedworking.png.ecrp | binary | |
MD5:7FC8C92C0FE8E904842A8D8EEB2E03FA | SHA256:6B50EEFC2B5F3BBBFD28E230672137A30836131B10443F21947AC36C7071B774 | |||
| 6408 | payroll.docx.exe | C:\Users\admin\AppData\Local\ServiceHub\payroll.docx.exe | executable | |
MD5:9B746C7D207122FDD040B8003BF1A535 | SHA256:F2CF1D12365B1880325E9A6E2CE4315F96D33B5CADB815398870D7D49B58F9BB | |||
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\accommodationdc.jpg | binary | |
MD5:A1FCAEB07C8B2666D1FB8C5B2647371D | SHA256:98FF1B3047390EC62260EFF8FC96685CB877397F852462C3981C56FFBFB21819 | |||
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\shotst.jpg | pi2 | |
MD5:88E25A0215187101B1EE6ECB274D107D | SHA256:BF3353B7FC320B73926AE83C3E560B74D91E64201920E41B7F5B5AD61616CA77 | |||
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\familyjan.png.ecrp | pi2 | |
MD5:B8CF04C09E0B2E530F8993EA0E796015 | SHA256:E3E0DC87E6D0ABC58E23635A505908E65ABB7E4C91B8A1332E4F5758F3F46C32 | |||
| 5944 | payroll.docx.exe | C:\Users\admin\Pictures\dealwithout.png.ecrp | binary | |
MD5:3555F913DA25E6259D8DAB86B8DBB506 | SHA256:3875FB158645FC3A845A69DB8736A04985E8072564DE2EC0938C44C0AE8BD750 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
45
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3376 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6492 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6520 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4664 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 104.126.37.160:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5924 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5924 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
satid-gob.mx |
| unknown |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |