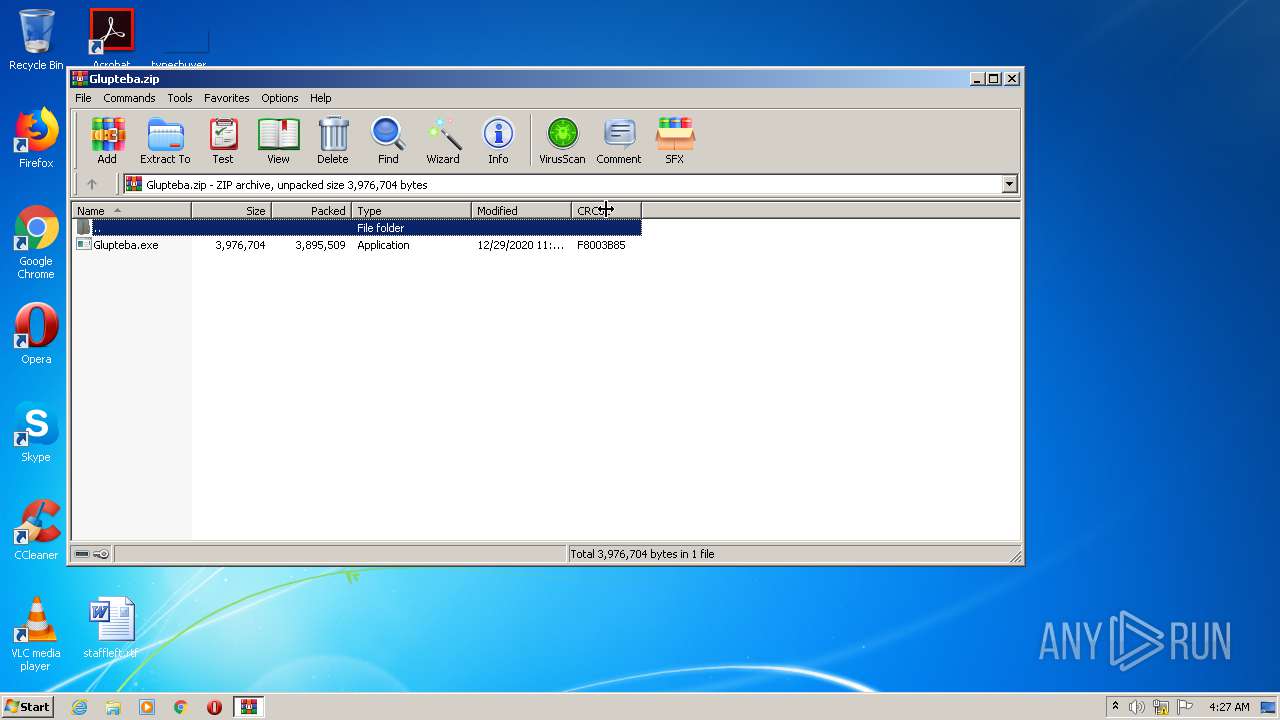
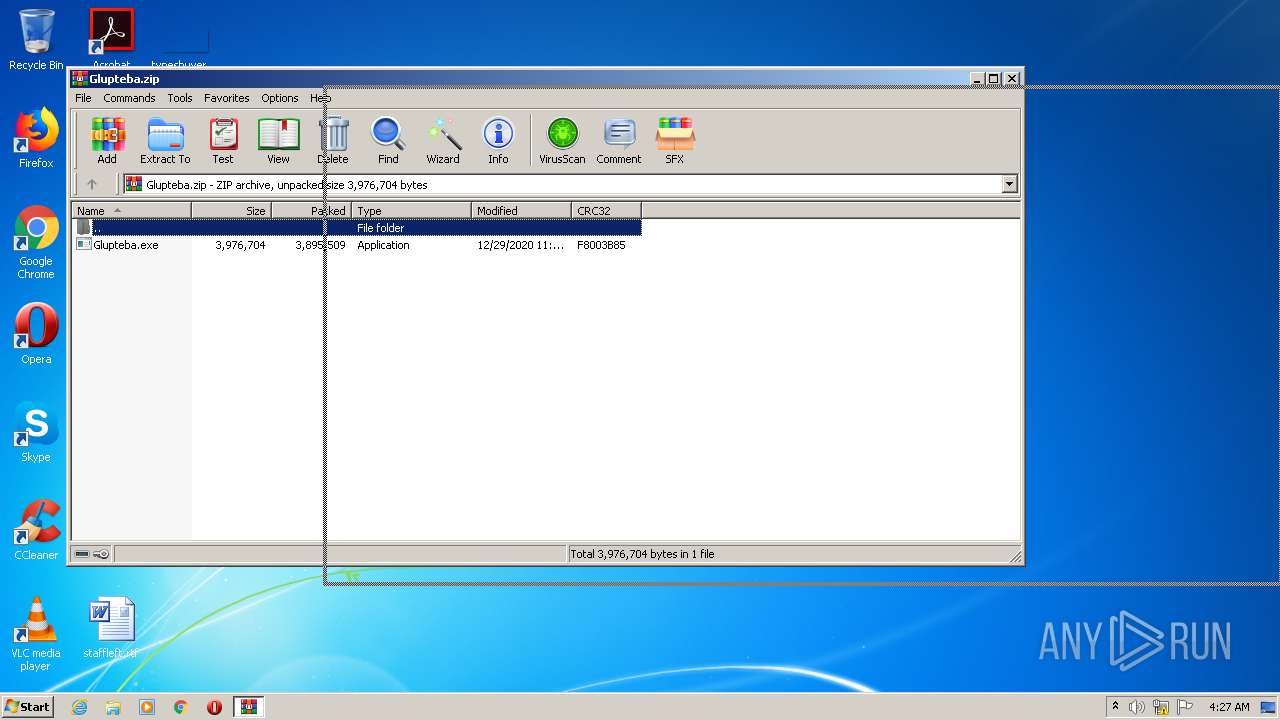
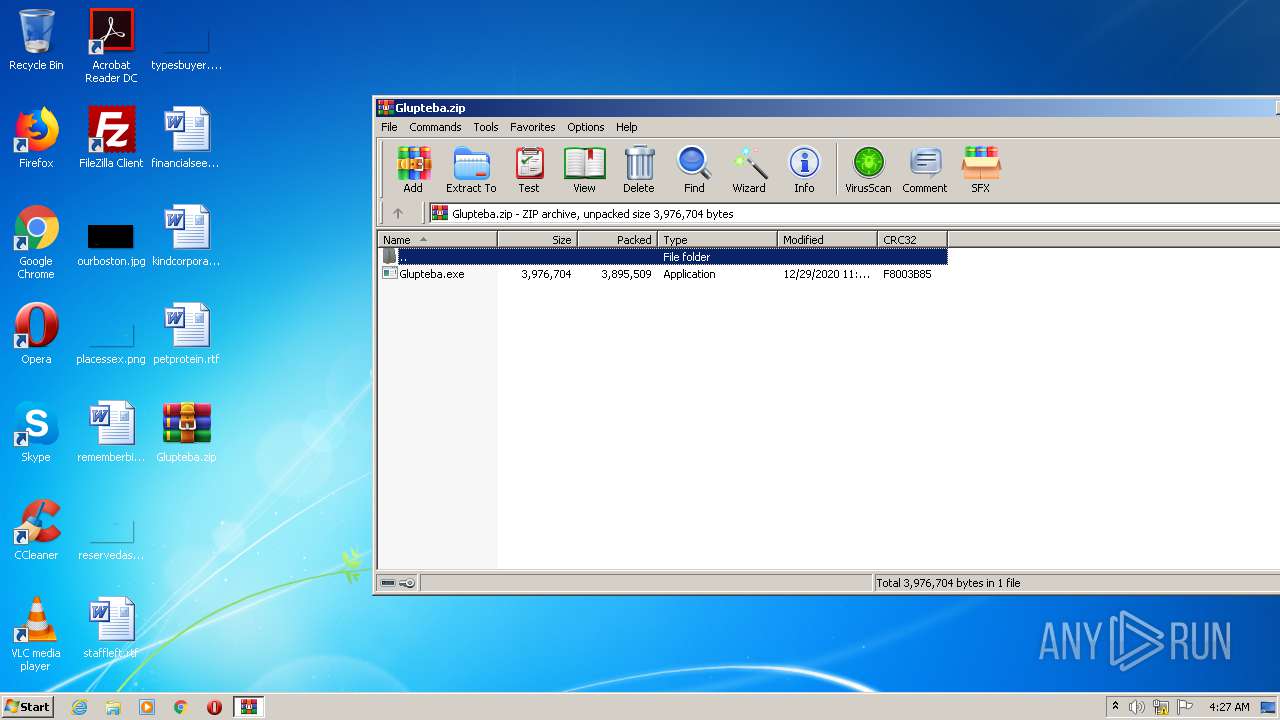
| File name: | Glupteba.zip |
| Full analysis: | https://app.any.run/tasks/d543b0c1-fd5d-441f-852b-a5a6b53b9d58 |
| Verdict: | Malicious activity |
| Threats: | Glupteba is a loader with information-stealing and traffic routing functionality. It is designed primarily to install other viruses on infected PCs but can do much more than that. In addition, it is being constantly updated, making this virus one to watch out for. |
| Analysis date: | December 31, 2020, 04:26:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 069A4B681A50AC8E07B3E7603872929C |
| SHA1: | 0B72E05CA5C71D1770EA4A9CE038C14FAA6ECD0C |
| SHA256: | F2C6C968A10B42BF5B97A6BFE6AEA692AC2BAFDABED63FE9A1CA456A246BA1A4 |
| SSDEEP: | 98304:2KFaXyIOmhjwazi8xpbsxQOSq73iG2x4nG2Bk6H6Z7+YVbI+Fs:2caXfcUieNqd73iFKnXk6H6oYm |
MALICIOUS
Application was dropped or rewritten from another process
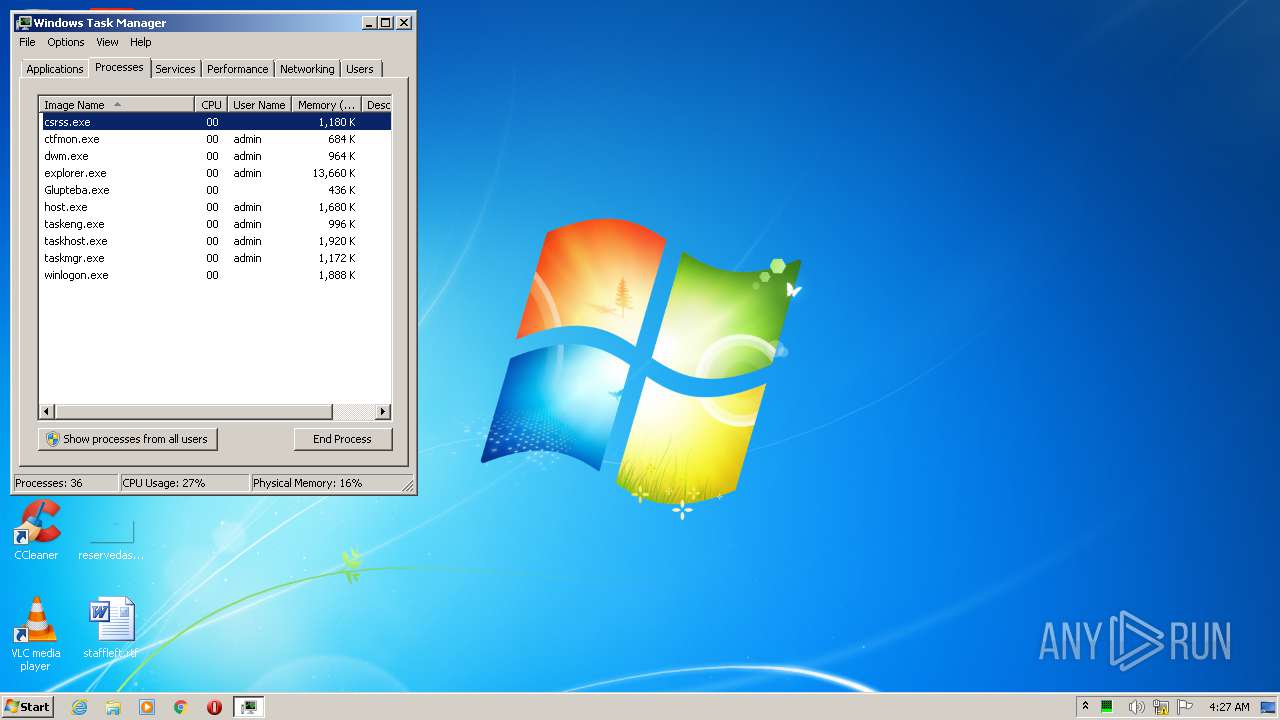
- Glupteba.exe (PID: 2888)
- Glupteba.exe (PID: 3184)
- Glupteba.exe (PID: 3100)
- csrss.exe (PID: 956)
- windefender.exe (PID: 2900)
- windefender.exe (PID: 2824)
Known privilege escalation attack
- Glupteba.exe (PID: 2888)
Modifies exclusions in Windows Defender
- Glupteba.exe (PID: 3100)
GLUPTEBA was detected
- Glupteba.exe (PID: 3100)
Changes the autorun value in the registry
- Glupteba.exe (PID: 3100)
Uses Task Scheduler to autorun other applications
- csrss.exe (PID: 956)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3492)
- schtasks.exe (PID: 2088)
Changes settings of System certificates
- csrss.exe (PID: 956)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2796)
- Glupteba.exe (PID: 3100)
- csrss.exe (PID: 956)
Changes default file association
- Glupteba.exe (PID: 2888)
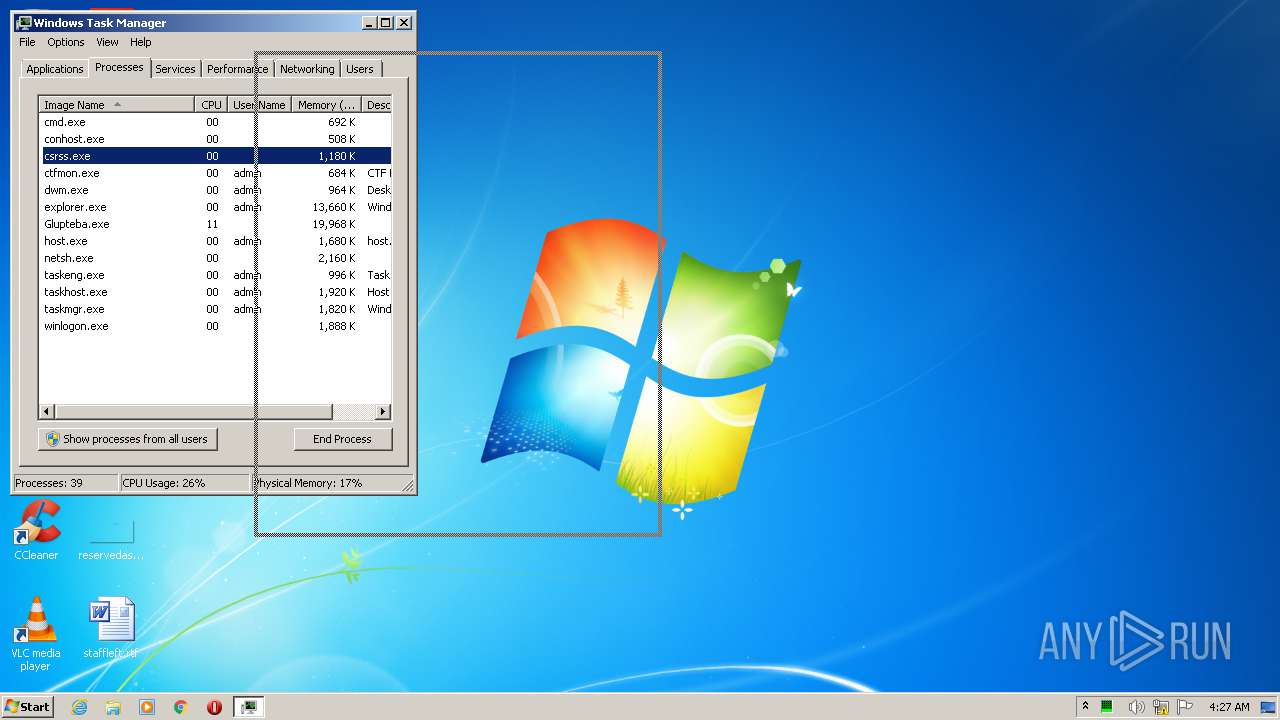
Starts CMD.EXE for commands execution
- Glupteba.exe (PID: 2888)
- Glupteba.exe (PID: 3100)
- windefender.exe (PID: 2900)
- csrss.exe (PID: 956)
Application launched itself
- Glupteba.exe (PID: 3184)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 2952)
- cmd.exe (PID: 3472)
Creates files in the Windows directory
- Glupteba.exe (PID: 3100)
- csrss.exe (PID: 956)
Starts itself from another location
- Glupteba.exe (PID: 3100)
Starts SC.EXE for service management
- cmd.exe (PID: 3852)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 2652)
- cmd.exe (PID: 3220)
Creates files in the driver directory
- csrss.exe (PID: 956)
Drops a file that was compiled in debug mode
- csrss.exe (PID: 956)
Adds / modifies Windows certificates
- csrss.exe (PID: 956)
Drops a file with too old compile date
- csrss.exe (PID: 956)
Executed as Windows Service
- windefender.exe (PID: 2824)
Searches for installed software
- csrss.exe (PID: 956)
INFO
Manual execution by user
- Glupteba.exe (PID: 2888)
- taskmgr.exe (PID: 1720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:12:29 19:34:07 |
| ZipCRC: | 0xf8003b85 |
| ZipCompressedSize: | 3895509 |
| ZipUncompressedSize: | 3976704 |
| ZipFileName: | Glupteba.exe |
Total processes
77
Monitored processes
26
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | CompMgmtLauncher | C:\Windows\system32\CompMgmtLauncher.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Computer Management Snapin Launcher Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 956 | C:\Windows\rss\csrss.exe "" | C:\Windows\rss\csrss.exe | Glupteba.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1120 | "C:\Windows\system32\CompMgmtLauncher.exe" | C:\Windows\system32\CompMgmtLauncher.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Computer Management Snapin Launcher Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1692 | netsh advfirewall firewall add rule name="CloudNet" dir=in action=allow program="C:\Users\admin\AppData\Roaming\bbeba99f3f92\bbeba99f3f92\bbeba99f3f92.exe" enable=yes | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1720 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1764 | netsh advfirewall firewall add rule name="csrss" dir=in action=allow program="C:\Windows\rss\csrss.exe" enable=yes | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1856 | sc sdset WinmonFS D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPLOCRSDRCWDWO;;;BA)(D;;WPDT;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD) | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | sc sdset WinmonProcessMonitor D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPLOCRSDRCWDWO;;;BA)(D;;WPDT;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD) | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2088 | schtasks /CREATE /SC ONLOGON /RL HIGHEST /TR "C:\Windows\rss\csrss.exe" /TN csrss /F | C:\Windows\system32\schtasks.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2652 | cmd.exe /C sc sdset WinmonFS D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPLOCRSDRCWDWO;;;BA)(D;;WPDT;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD) | C:\Windows\system32\cmd.exe | — | csrss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 097
Read events
1 706
Write events
389
Delete events
2
Modification events
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Glupteba.zip | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFD500000066000000950400005B020000 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
6
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2796.16914\Glupteba.exe | executable | |
MD5:— | SHA256:— | |||
| 3100 | Glupteba.exe | C:\Windows\rss\csrss.exe | executable | |
MD5:— | SHA256:— | |||
| 956 | csrss.exe | C:\Windows\windefender.exe | executable | |
MD5:— | SHA256:— | |||
| 956 | csrss.exe | C:\Windows\System32\drivers\Winmon.sys | executable | |
MD5:4EF0C39E632279D7B3672D2EFC071E5B | SHA256:889FB266C4C01BB4EF67635249C8DAEB641FC86CE62FC280B34BEEC415FB6129 | |||
| 956 | csrss.exe | C:\Windows\System32\drivers\WinmonProcessMonitor.sys | executable | |
MD5:622FD523A87CB55BE0B676A70C64E8F8 | SHA256:F609C6656A0C451DAFA5173DF0CD848F7CB7F22C4F150F8D16716C12593DE66C | |||
| 956 | csrss.exe | C:\Windows\System32\drivers\WinmonFS.sys | executable | |
MD5:0D3A8D67CD969C6E096B4D29E910DD9E | SHA256:EB0BE2AC3833C843214A55B14C31125A7B600D5272BDF322C4871F42627576E4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
956 | csrss.exe | 104.18.56.109:443 | 10gamestop.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
35d2acd6-c29a-4926-a1a4-e1dd2c07c17f.server4.deepsound.live |
| unknown |
10gamestop.com |
| malicious |