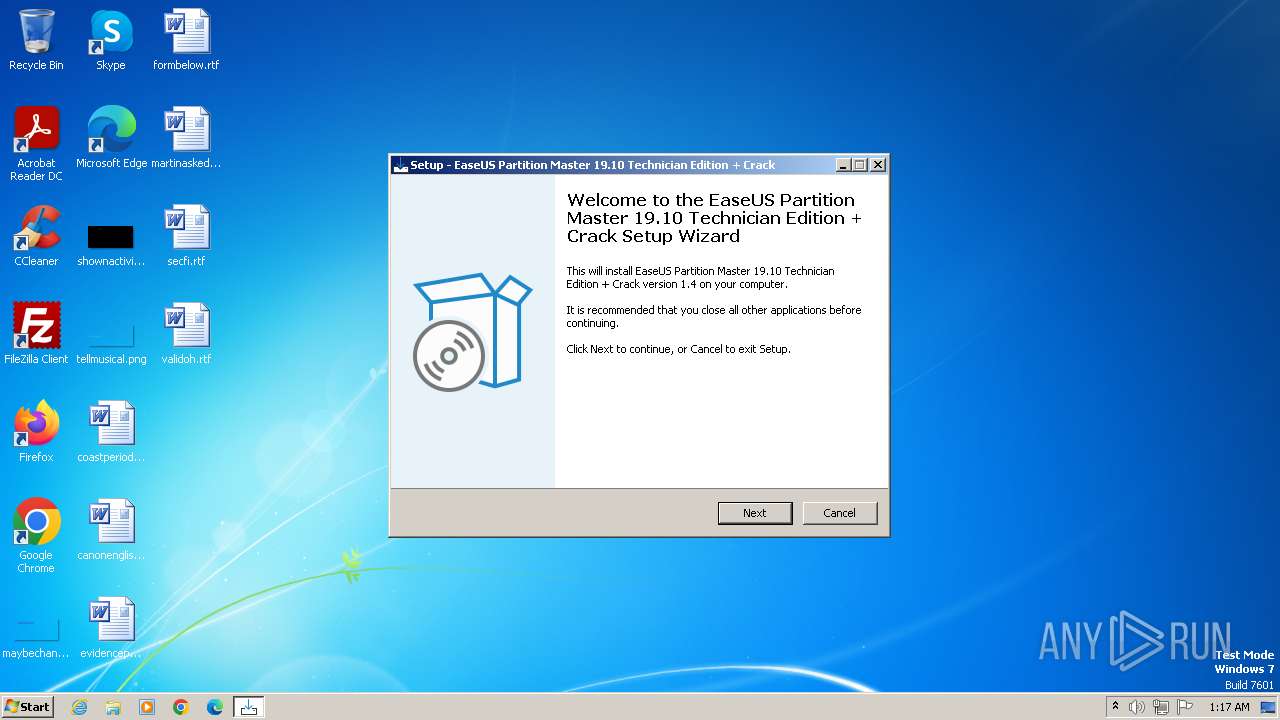
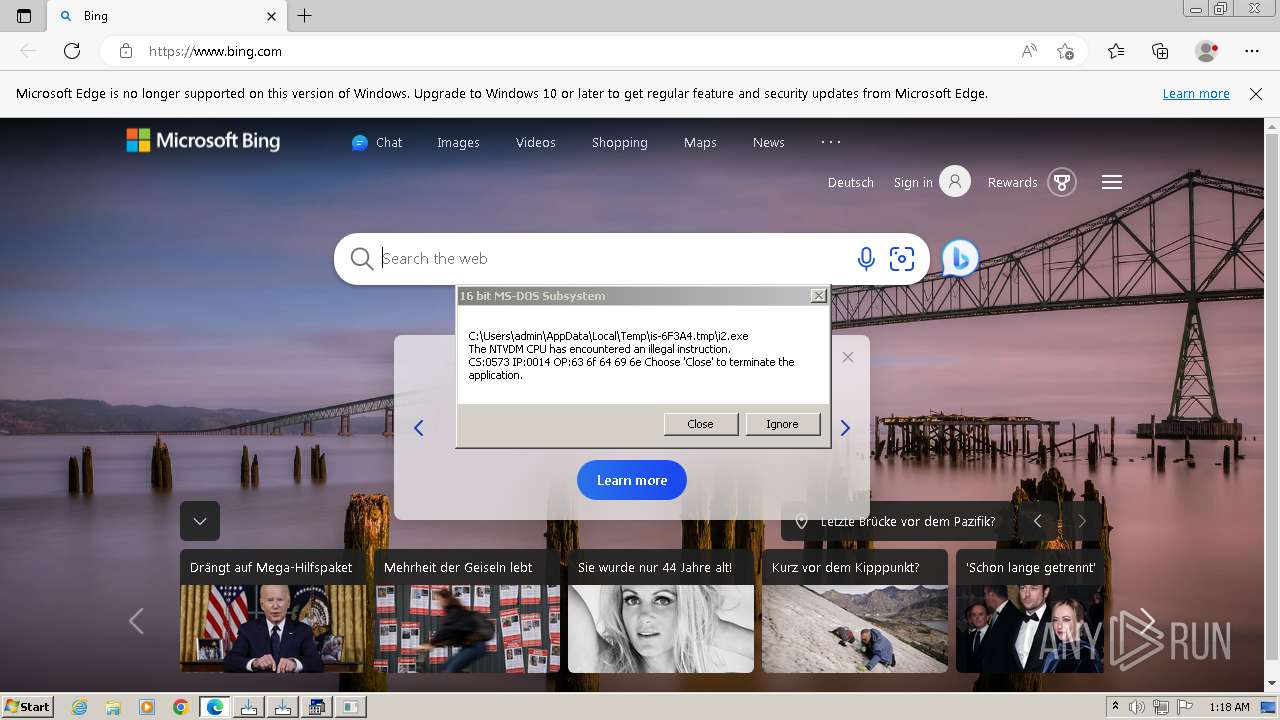
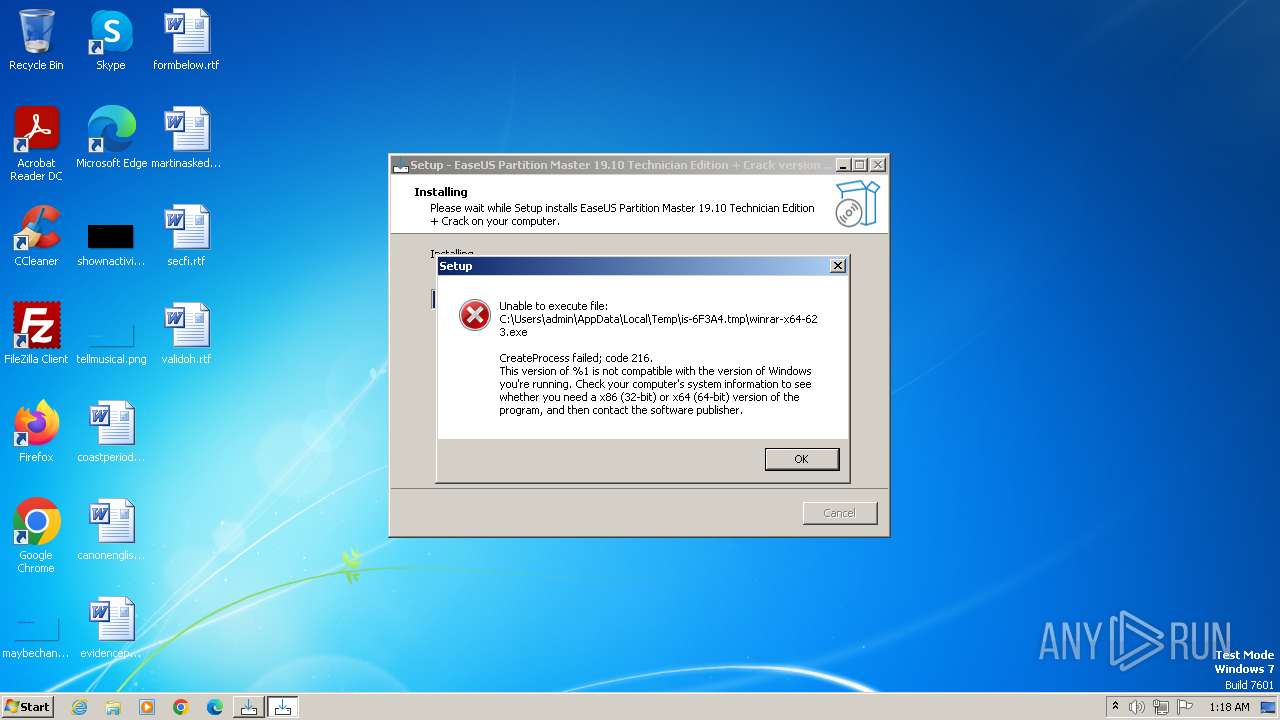
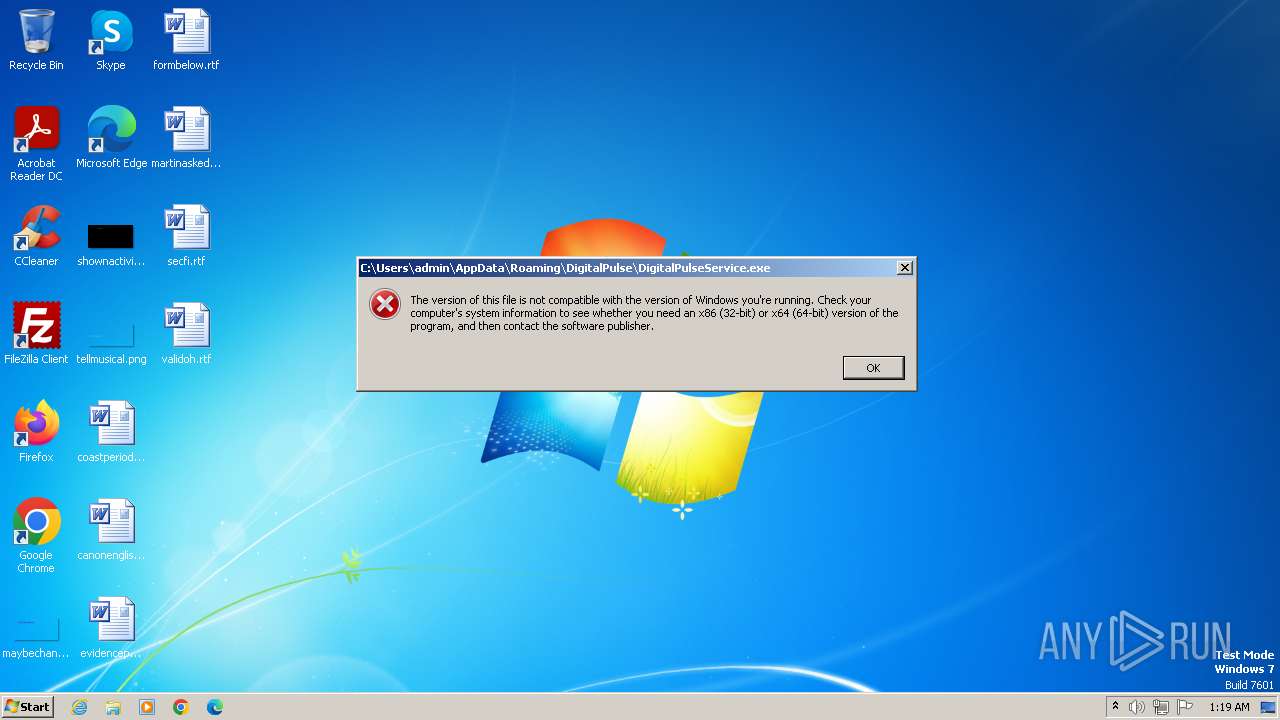
| File name: | EaseUS Partition Master 19.10 Technician Edition + Crack.exe |
| Full analysis: | https://app.any.run/tasks/db675a4d-def2-4886-9936-6f34a679fa20 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | October 22, 2023, 00:16:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 157DBF4C6E6A44C66077537B3022AD12 |
| SHA1: | ED03D8749F665E9055BE357135DD7E0286C75B96 |
| SHA256: | F1F454FCE30424BB21147879AA6CEE844E197E3752ECD67779A5BA58F5146889 |
| SSDEEP: | 98304:m+cD4dnAw23wR6LTST7l2bGjd6+5nu7/h8IxsduK9Wo1O5iuE+gT/RzSIli1PhOH:TpThlRTpThlRTpT5lRTpgWYW |
MALICIOUS
Drops the executable file immediately after the start
- EaseUS Partition Master 19.10 Technician Edition + Crack.exe (PID: 1372)
- EaseUS Partition Master 19.10 Technician Edition + Crack.exe (PID: 2900)
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 2232)
- setup.tmp (PID: 3820)
- i1.exe (PID: 948)
- i1.tmp (PID: 3004)
- i3.exe (PID: 2944)
- i3.tmp (PID: 2096)
- i4.exe (PID: 2776)
- setup.exe (PID: 2952)
- msiexec.exe (PID: 2568)
Application was dropped or rewritten from another process
- EaseUS Partition Master 19.10 Technician Edition + Crack.exe (PID: 2900)
- EaseUS Partition Master 19.10 Technician Edition + Crack.exe (PID: 1372)
- wmiprvse.exe (PID: 2464)
Loads dropped or rewritten executable
- setup.tmp (PID: 3820)
- wmiprvse.exe (PID: 2464)
- msiexec.exe (PID: 3568)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 2328)
- msiexec.exe (PID: 4024)
NETSUPPORT was detected
- wmiprvse.exe (PID: 2464)
Connects to the CnC server
- wmiprvse.exe (PID: 2464)
Uses Task Scheduler to run other applications
- i3.tmp (PID: 2096)
The DLL Hijacking
- msiexec.exe (PID: 4024)
- msiexec.exe (PID: 3568)
SUSPICIOUS
Reads the Windows owner or organization settings
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 2232)
- setup.tmp (PID: 3820)
- i1.tmp (PID: 3004)
- i3.tmp (PID: 2096)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 2568)
Reads the Internet Settings
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 2232)
- setup.tmp (PID: 3820)
- cmd.exe (PID: 3396)
- wmiprvse.exe (PID: 2464)
- msiexec.exe (PID: 3568)
- i4.exe (PID: 2776)
Checks Windows Trust Settings
- setup.tmp (PID: 3820)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 2568)
- msiexec.exe (PID: 3568)
Reads security settings of Internet Explorer
- setup.tmp (PID: 3820)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 3568)
Searches for installed software
- setup.tmp (PID: 3820)
Adds/modifies Windows certificates
- setup.exe (PID: 2952)
- setup.tmp (PID: 3820)
Reads settings of System Certificates
- setup.tmp (PID: 3820)
- i4.exe (PID: 2776)
The process drops C-runtime libraries
- i1.tmp (PID: 3004)
- expand.exe (PID: 2496)
Process drops legitimate windows executable
- i1.tmp (PID: 3004)
- expand.exe (PID: 2496)
Starts CMD.EXE for commands execution
- i1.tmp (PID: 3004)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2948)
Connects to the server without a host name
- wmiprvse.exe (PID: 2464)
Connects to unusual port
- wmiprvse.exe (PID: 2464)
Process requests binary or script from the Internet
- setup.tmp (PID: 3820)
Checks for Java to be installed
- msiexec.exe (PID: 4024)
- msiexec.exe (PID: 3568)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 3568)
The process creates files with name similar to system file names
- msiexec.exe (PID: 2568)
INFO
Checks supported languages
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 4048)
- EaseUS Partition Master 19.10 Technician Edition + Crack.exe (PID: 1372)
- EaseUS Partition Master 19.10 Technician Edition + Crack.exe (PID: 2900)
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 2232)
- setup.exe (PID: 2952)
- setup.tmp (PID: 3820)
- i1.exe (PID: 948)
- i1.tmp (PID: 3004)
- wmiprvse.exe (PID: 2464)
- i3.exe (PID: 2944)
- i3.tmp (PID: 2096)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 2568)
- msiexec.exe (PID: 4024)
- msiexec.exe (PID: 3568)
- msiexec.exe (PID: 2328)
Create files in a temporary directory
- EaseUS Partition Master 19.10 Technician Edition + Crack.exe (PID: 1372)
- EaseUS Partition Master 19.10 Technician Edition + Crack.exe (PID: 2900)
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 2232)
- setup.exe (PID: 2952)
- setup.tmp (PID: 3820)
- i1.exe (PID: 948)
- i1.tmp (PID: 3004)
- i3.exe (PID: 2944)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 2568)
Reads the computer name
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 4048)
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 2232)
- setup.tmp (PID: 3820)
- i1.tmp (PID: 3004)
- wmiprvse.exe (PID: 2464)
- i3.tmp (PID: 2096)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 2568)
- msiexec.exe (PID: 4024)
- msiexec.exe (PID: 3568)
- msiexec.exe (PID: 2328)
Application was dropped or rewritten from another process
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 2232)
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 4048)
- setup.exe (PID: 2952)
- i1.exe (PID: 948)
- i1.tmp (PID: 3004)
- i3.tmp (PID: 2096)
- i3.exe (PID: 2944)
- i4.exe (PID: 2776)
- setup.tmp (PID: 3820)
Creates files in the program directory
- EaseUS Partition Master 19.10 Technician Edition + Crack.tmp (PID: 2232)
- i1.tmp (PID: 3004)
- expand.exe (PID: 2496)
- setup.tmp (PID: 3820)
Checks proxy server information
- setup.tmp (PID: 3820)
- wmiprvse.exe (PID: 2464)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 3568)
Reads the machine GUID from the registry
- setup.tmp (PID: 3820)
- wmiprvse.exe (PID: 2464)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 2568)
- msiexec.exe (PID: 3568)
- msiexec.exe (PID: 4024)
- msiexec.exe (PID: 2328)
Creates files or folders in the user directory
- setup.tmp (PID: 3820)
- wmiprvse.exe (PID: 2464)
- i3.tmp (PID: 2096)
- i4.exe (PID: 2776)
- msiexec.exe (PID: 3568)
Drops the executable file immediately after the start
- expand.exe (PID: 2496)
Drop NetSupport executable file
- expand.exe (PID: 2496)
Application launched itself
- msedge.exe (PID: 3644)
- msedge.exe (PID: 4016)
- msiexec.exe (PID: 2568)
Manual execution by a user
- msedge.exe (PID: 4016)
Reads Environment values
- i4.exe (PID: 2776)
- msiexec.exe (PID: 3568)
- msiexec.exe (PID: 4024)
Process checks Powershell version
- msiexec.exe (PID: 4024)
- msiexec.exe (PID: 3568)
Reads Microsoft Office registry keys
- msiexec.exe (PID: 4024)
- msiexec.exe (PID: 3568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 15:54:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | EaseUS Partition Master 19.10 Technician Edition + Crack Set |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | EaseUS Partition Master 19.10 Technician Edition + Crack |
| ProductVersion: | 1.4 |
Total processes
100
Monitored processes
48
Malicious processes
17
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1548 --field-trial-handle=1288,i,4856958915022225534,4406063112171654665,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 948 | "C:\Users\admin\AppData\Local\Temp\is-6F3A4.tmp\i1.exe" /VERYSILENT /PASSWORD=NtIRVUpMK9ZD30Nf60705572 -token mtn1co3fo4gs5vwq -subid 2607 | C:\Users\admin\AppData\Local\Temp\is-6F3A4.tmp\i1.exe | — | setup.tmp | |||||||||||
User: admin Company: 81JihD4Ja3 Limited Liability Integrity Level: HIGH Description: 2a9Sevc6HX1DdgVi corp Setup Exit code: 0 Version: 7.5 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3916 --field-trial-handle=1288,i,4856958915022225534,4406063112171654665,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 980 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3780 --field-trial-handle=1288,i,4856958915022225534,4406063112171654665,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1372 | "C:\Users\admin\AppData\Local\Temp\EaseUS Partition Master 19.10 Technician Edition + Crack.exe" | C:\Users\admin\AppData\Local\Temp\EaseUS Partition Master 19.10 Technician Edition + Crack.exe | — | explorer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: EaseUS Partition Master 19.10 Technician Edition + Crack Set Exit code: 0 Version: Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1280 --field-trial-handle=1296,i,15285832328622235335,4904225662366871919,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1908 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3792 --field-trial-handle=1288,i,4856958915022225534,4406063112171654665,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1404 --field-trial-handle=1288,i,4856958915022225534,4406063112171654665,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2096 | "C:\Users\admin\AppData\Local\Temp\is-24U62.tmp\i3.tmp" /SL5="$70348,4480080,832512,C:\Users\admin\AppData\Local\Temp\is-6F3A4.tmp\i3.exe" /SP- /VERYSILENT /SUPPRESSMSGBOXES /PID=6752 /CLICKID=2607 /SOURCEID=2607 | C:\Users\admin\AppData\Local\Temp\is-24U62.tmp\i3.tmp | — | i3.exe | |||||||||||
User: admin Company: DigitalPulse, Ltd. Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2284 --field-trial-handle=1288,i,4856958915022225534,4406063112171654665,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
24 856
Read events
24 643
Write events
174
Delete events
39
Modification events
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3820) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 1900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA662000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C60B000000010000001A0000004900530052004700200052006F006F007400200058003100000014000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E1D000000010000001000000073B6876195F5D18E048510422AEF04E309000000010000000C000000300A06082B06010505070301030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E80F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F6320000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
Executable files
79
Suspicious files
152
Text files
101
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | C:\Users\admin\AppData\Local\Temp\is-O58DU.tmp\is-9P4U1.tmp | — | |
MD5:— | SHA256:— | |||
| 2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | C:\Users\admin\AppData\Local\Temp\is-O58DU.tmp\entry | — | |
MD5:— | SHA256:— | |||
| 2900 | EaseUS Partition Master 19.10 Technician Edition + Crack.exe | C:\Users\admin\AppData\Local\Temp\is-19QS7.tmp\EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | executable | |
MD5:5C83977344CF478E656642AA86DC08B7 | SHA256:8EC57CC5374D5AF0183142B8F6D71C5F6DC9AB00A873931C92BA5A271AEFD1F1 | |||
| 2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | C:\Users\admin\AppData\Local\Temp\is-O58DU.tmp\setup | text | |
MD5:4308F9C0E1CB47E9F9DDC0445BDB2DA3 | SHA256:AFC45119F588827F0958B49F09FC756C4B8A190F674523465F0F3D824FCB5430 | |||
| 2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | C:\Users\admin\AppData\Local\Temp\is-O58DU.tmp\is-D54DI.tmp | executable | |
MD5:6BD2CAC29FB16D108E8F0464A5F60826 | SHA256:E9BBBD4C1B8B321A34A2082546868C31833C6B7ADE1C2D0E449577BA0BB0BC2E | |||
| 1372 | EaseUS Partition Master 19.10 Technician Edition + Crack.exe | C:\Users\admin\AppData\Local\Temp\is-1TGE4.tmp\EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | executable | |
MD5:5C83977344CF478E656642AA86DC08B7 | SHA256:8EC57CC5374D5AF0183142B8F6D71C5F6DC9AB00A873931C92BA5A271AEFD1F1 | |||
| 2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | C:\Users\admin\AppData\Local\Temp\is-O58DU.tmp\is-HHCT0.tmp | text | |
MD5:444BCB3A3FCF8389296C49467F27E1D6 | SHA256:2689367B205C16CE32ED4200942B8B8B1E262DFC70D9BC9FBC77C49699A4F1DF | |||
| 3820 | setup.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | C:\Program Files\EaseUS Partition Master 19.10 Technician Edition + Crack\is-BEUNF.tmp | executable | |
MD5:19943A8B937379B8591B7EB6078B5D1D | SHA256:9C308A7C01CB63303B3533BF9DD69402AECB9069397D4DB34FD1F0F72488D8D6 | |||
| 3820 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-6F3A4.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
98
DNS requests
55
Threats
34
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3820 | setup.tmp | HEAD | 200 | 23.106.59.52:80 | http://www.mildstat.com/ping/?count=true&id=3gn4m2ide1 | unknown | — | — | unknown |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | GET | 200 | 188.114.96.3:80 | http://pagecellar.website/dunk.php?p=3896&t=47281277&title=RWFzZVVTIFBhcnRpdGlvbiBNYXN0ZXIgMTkuMTAgVGVjaG5pY2lhbiBFZGl0aW9uICsgQ3JhY2s= | unknown | text | 170 b | unknown |
3820 | setup.tmp | GET | 200 | 8.241.123.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?19d7f26de4e03693 | unknown | compressed | 4.66 Kb | unknown |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | GET | 200 | 188.114.96.3:80 | http://pagecellar.website/sunk.php | unknown | text | 2 b | unknown |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | GET | 200 | 188.114.97.3:80 | http://producerainstorm.xyz/pe/buildIN.php?sub=&source=3896&s1=47281277&title=RWFzZVVTIFBhcnRpdGlvbiBNYXN0ZXIgMTkuMTAgVGVjaG5pY2lhbiBFZGl0aW9uICsgQ3JhY2s%3D&ti=1697933837 | unknown | executable | 4.90 Mb | unknown |
3820 | setup.tmp | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3820 | setup.tmp | GET | 200 | 184.24.77.65:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQOSBe1Ujs4a55YMOeQC9ipbg%3D%3D | unknown | binary | 503 b | unknown |
2464 | wmiprvse.exe | POST | — | 194.38.21.22:1203 | http://194.38.21.22/fakeurl.htm | unknown | — | — | unknown |
2464 | wmiprvse.exe | POST | — | 194.38.21.22:1203 | http://194.38.21.22/fakeurl.htm | unknown | — | — | unknown |
3820 | setup.tmp | GET | 200 | 188.114.96.3:80 | http://goof.townbrass.xyz/ar.php?d=inno&r=offer_execution&rk=no&o=365&a=2607&dn=310&spot=3&t=1697933834 | unknown | text | 2 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | 188.114.96.3:80 | pagecellar.website | CLOUDFLARENET | NL | unknown |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | 188.114.97.3:80 | pagecellar.website | CLOUDFLARENET | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3820 | setup.tmp | 188.114.96.3:443 | pagecellar.website | CLOUDFLARENET | NL | unknown |
3820 | setup.tmp | 8.241.123.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3820 | setup.tmp | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
3820 | setup.tmp | 212.86.101.26:443 | www.kommelton.cloud | Zomro B.V. | NL | unknown |
3820 | setup.tmp | 184.24.77.65:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pagecellar.website |
| unknown |
producerainstorm.xyz |
| unknown |
goof.townbrass.xyz |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
www.kommelton.cloud |
| unknown |
r3.o.lencr.org |
| shared |
infrastructuresurfer.top |
| unknown |
geo.netsupportsoftware.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/TrojanDownloader Variant Activity (GET) |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | Possibly Unwanted Program Detected | ADWARE [ANY.RUN] InnoSetup Installer |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | Possibly Unwanted Program Detected | ADWARE [ANY.RUN] InnoSetup Installer |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2232 | EaseUS Partition Master 19.10 Technician Edition + Crack.tmp | Misc activity | ET INFO EXE - Served Attached HTTP |
3820 | setup.tmp | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2464 | wmiprvse.exe | Misc activity | ET INFO NetSupport Remote Admin Checkin |
2464 | wmiprvse.exe | Misc activity | ET INFO NetSupport Remote Admin Response |
11 ETPRO signatures available at the full report