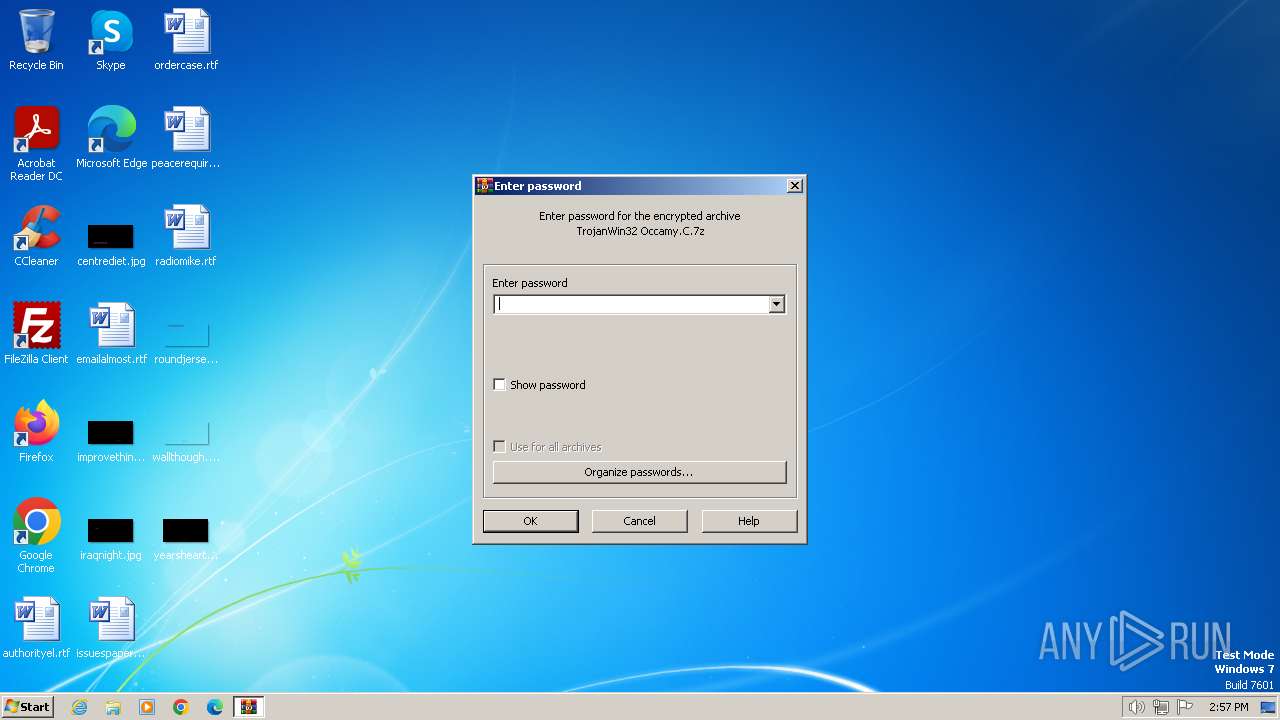
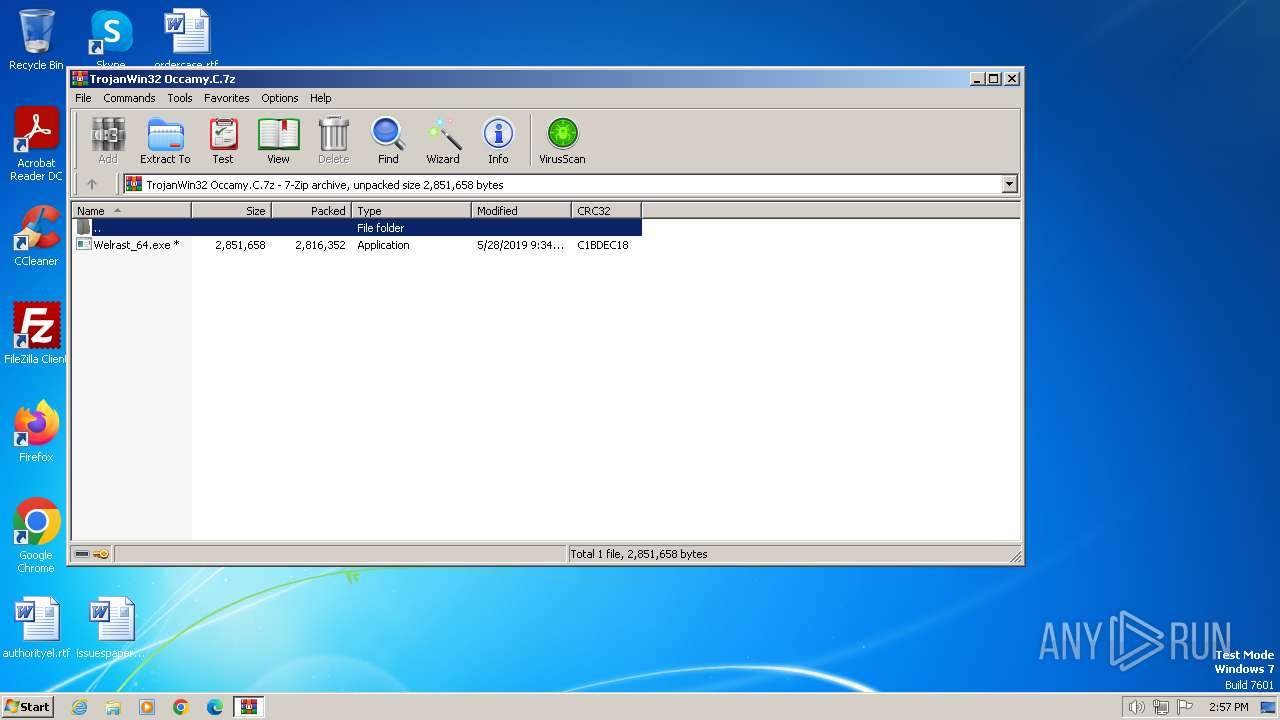
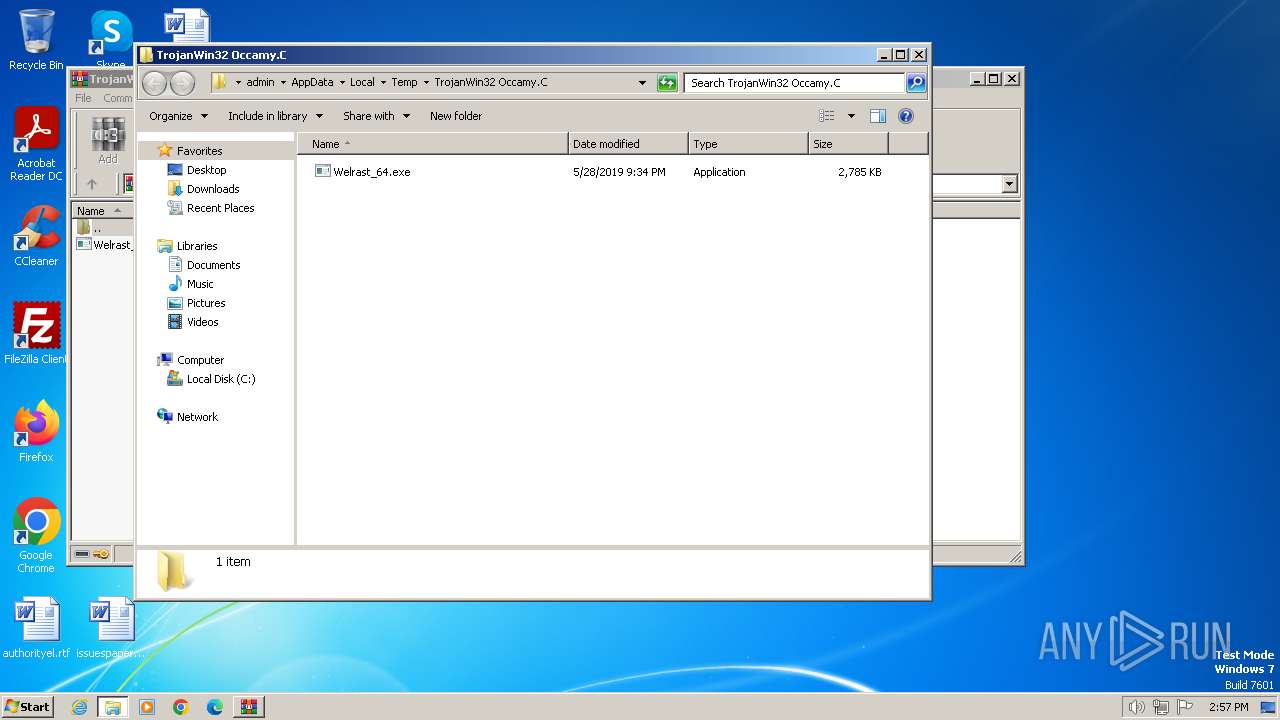
| File name: | TrojanWin32 Occamy.C.7z |
| Full analysis: | https://app.any.run/tasks/530148f5-09b2-4757-b76e-79717bd0d7a6 |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | March 02, 2024, 14:57:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 211091126642FC64ED27785B67FBBC00 |
| SHA1: | C54F732AED358EFEFF4344797ABF0789E6E55EF5 |
| SHA256: | F1ED060F21CD2C7F276ED00E16E80A55CB7ABDB4AA0D87FC7B2791607B20070F |
| SSDEEP: | 98304:xqjBDHkBoAbIUH1lkBqor9og0PmbWAtcOHjTE5um042rNIFh58py9YkYgx+y7Pgs:DAa/ |
MALICIOUS
Drops the executable file immediately after the start
- Welrast_64.exe (PID: 2964)
- fdfbvd.exe (PID: 3848)
Actions looks like stealing of personal data
- dzvsac.exe (PID: 3940)
Steals credentials
- dzvsac.exe (PID: 3940)
Steals credentials from Web Browsers
- dzvsac.exe (PID: 3940)
Application was injected by another process
- explorer.exe (PID: 1164)
Runs injected code in another process
- dascsaCV.exe (PID: 2692)
Changes the autorun value in the registry
- explorer.exe (PID: 1164)
Connects to the CnC server
- explorer.exe (PID: 1164)
- dzvsac.exe (PID: 3940)
- advasv.exe (PID: 3964)
PLUROX has been detected (SURICATA)
- explorer.exe (PID: 1164)
- advasv.exe (PID: 3964)
SUSPICIOUS
Executable content was dropped or overwritten
- Welrast_64.exe (PID: 2964)
- fdfbvd.exe (PID: 3848)
Reads the Internet Settings
- fdfbvd.exe (PID: 3848)
Reads security settings of Internet Explorer
- fdfbvd.exe (PID: 3848)
Connects to unusual port
- explorer.exe (PID: 1164)
- advasv.exe (PID: 3964)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
Checks supported languages
- Welrast_64.exe (PID: 2964)
- fdfbvd.exe (PID: 3848)
- advasv.exe (PID: 3964)
- dascsaCV.exe (PID: 2692)
- dzvsac.exe (PID: 3940)
Reads the computer name
- Welrast_64.exe (PID: 2964)
- fdfbvd.exe (PID: 3848)
- advasv.exe (PID: 3964)
- dascsaCV.exe (PID: 2692)
- dzvsac.exe (PID: 3940)
Manual execution by a user
- Welrast_64.exe (PID: 2964)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3672)
- explorer.exe (PID: 1164)
Creates files or folders in the user directory
- Welrast_64.exe (PID: 2964)
- fdfbvd.exe (PID: 3848)
- dzvsac.exe (PID: 3940)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3672)
Reads the machine GUID from the registry
- advasv.exe (PID: 3964)
- dascsaCV.exe (PID: 2692)
- dzvsac.exe (PID: 3940)
Creates files in the program directory
- explorer.exe (PID: 1164)
Reads CPU info
- advasv.exe (PID: 3964)
Application launched itself
- iexplore.exe (PID: 3684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
50
Monitored processes
10
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3684 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3684 CREDAT:3085575 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2692 | "C:\Users\admin\AppData\Roaming\dascsaCV.exe" | C:\Users\admin\AppData\Roaming\dascsaCV.exe | — | fdfbvd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2964 | "C:\Users\admin\AppData\Local\Temp\TrojanWin32 Occamy.C\Welrast_64.exe" | C:\Users\admin\AppData\Local\Temp\TrojanWin32 Occamy.C\Welrast_64.exe | explorer.exe | ||||||||||||
User: admin Company: tortoisesvn Integrity Level: MEDIUM Description: TortoisePlink Exit code: 0 Version: 2.21.31.1 Modules
| |||||||||||||||
| 3672 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TrojanWin32 Occamy.C.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3684 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3848 | "C:\Users\admin\AppData\Roaming\fdfbvd.exe" -s -ptdgndgmsratgg4hfsghsrfH | C:\Users\admin\AppData\Roaming\fdfbvd.exe | Welrast_64.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3940 | "C:\Users\admin\AppData\Roaming\dzvsac.exe" | C:\Users\admin\AppData\Roaming\dzvsac.exe | fdfbvd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3964 | "C:\Users\admin\AppData\Roaming\advasv.exe" | C:\Users\admin\AppData\Roaming\advasv.exe | fdfbvd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
53 484
Read events
53 066
Write events
296
Delete events
122
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C470000000002000000000010660000000100002000000046E6AD8122E9861F341A0D40D1FF4721F882F48A226CD1AF18D32C07BB5BC265000000000E80000000020000200000005F51F3BD434D51156926B174D5838199BC7567D084F65786F14DE6A76248A6C330000000991C275E3964C9BF40C213EBB05A6684EEEDECA74490814A6359770AF6030A648DFE663AEFE05638CBEB62035210390E400000006E8455C8EA2097D097110A79F85F205502138EA080DA4CA974376F07A11605256719588E7C87839BB9B67DC16FBD249B4710616C24B55FC8D3AAB4E8E4B3DB03 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\JvaENE\JvaENE.rkr |
Value: 000000000900000007000000F9020100000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF906CB27932B0D90100000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000D70100004C0300006EC39501440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\JvaENE\JvaENE.rkr |
Value: 000000000900000008000000F9020100000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF906CB27932B0D90100000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000D70100004D0300006EC39501440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
6
Suspicious files
55
Text files
508
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3940 | dzvsac.exe | C:\Users\admin\AppData\Local\x6u7vg5l90mj\google_chrome_default_ccdata.txt | — | |
MD5:— | SHA256:— | |||
| 3940 | dzvsac.exe | C:\Users\admin\AppData\Local\x6u7vg5l90mj\google_chrome_default_logins.txt | text | |
MD5:8CD3E621740BE01918DBD04A08733B6A | SHA256:2ED9E01F2B6C815EC72FF815CD9911195E67DAB9EEF4C40BFF7F9A878722F688 | |||
| 3848 | fdfbvd.exe | C:\Users\admin\AppData\Roaming\dascsaCV.exe | executable | |
MD5:FB00504FEC16C83EB6DB4649F3090507 | SHA256:E56FA8A40C953D96E66273BE75AC51A8213C3057233B199B18D13DBD5F0FB7C1 | |||
| 3940 | dzvsac.exe | C:\Users\admin\AppData\Local\gundyk2cjxa6.zip | compressed | |
MD5:7403EF4EE18ABDE31BA183434D359A05 | SHA256:17952F005409197450FD781D88D4C48DEEA7E59F690B6118CBA80BB687E60CBA | |||
| 3684 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:3D6FF7F4D449369B62359E6ABE98440B | SHA256:31C39443F0A7B157225EBAC8222C3E8369FBC0421341DBC2C4440B8F93AE7071 | |||
| 2964 | Welrast_64.exe | C:\Users\admin\AppData\Roaming\fdfbvd.exe | executable | |
MD5:3E1E601FDDB3E1CFCA88AB98CB974C94 | SHA256:A533C1F2705EFED579475FAAD2FD72EB3D40CE5FF653FF1588ACCF3FA450FCF2 | |||
| 3940 | dzvsac.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Web Data1 | binary | |
MD5:F47EB60CDF981C17722D0CE740129927 | SHA256:0210071DF12CA42D70DCB679926668AE072264705AC139A24F94BBC5A129DD8F | |||
| 1164 | explorer.exe | C:\ProgramData\TimeManager.exe | executable | |
MD5:F3424DD5BA8B10FDA5F523633865C320 | SHA256:23EB5A1E2C2E742F68452237EC094F53F2A82B9906C25DA99FA6B6698D66C98D | |||
| 3848 | fdfbvd.exe | C:\Users\admin\AppData\Roaming\advasv.exe | executable | |
MD5:7824383A3B8C6C18CB1E6E8758118513 | SHA256:F02F97D5E28BA69E50AB74318890D6657382FC982CE2C77A4EF326BB20495AAF | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\TrojanWin32 Occamy.C\Welrast_64.exe | executable | |
MD5:49853690EE7CBEC3703FCD75B06D7CE3 | SHA256:123423017A860591694B92EAF14EB3B633D80899C00B0D34D525469E79E6C340 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
275
DNS requests
54
Threats
197
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1560 | iexplore.exe | GET | 304 | 84.53.175.107:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c218dcb863adf7e2 | unknown | — | — | unknown |
1576 | iexplore.exe | GET | 301 | 142.250.179.142:80 | http://google.com/ | unknown | html | 219 b | unknown |
1576 | iexplore.exe | GET | 429 | 142.251.36.4:80 | http://www.google.com/sorry/index?continue=http://www.google.com/&q=EgS53GWFGLj9jK8GIjDZHHr-21eAUttGaKYrXiZvbXzs1UJzOnrEPtL6Qnki_6Ss1IvIF7u7fMKFv4gS9dQyAXJKGVNPUlJZX0FCVVNJVkVfTkVUX01FU1NBR0VaAUM | unknown | html | 2.98 Kb | unknown |
3940 | dzvsac.exe | POST | — | 46.17.44.54:80 | http://u2728516dh.ha002.t.justns.ru/landing.php | unknown | — | — | unknown |
1560 | iexplore.exe | GET | 304 | 84.53.175.107:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a6b9386cc2faab51 | unknown | — | — | unknown |
3684 | iexplore.exe | GET | 304 | 84.53.175.107:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bdfb7dc7aee5c892 | unknown | — | — | unknown |
1576 | iexplore.exe | GET | 200 | 172.217.23.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
1576 | iexplore.exe | GET | 200 | 172.217.23.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDWcu1vhm%2F7Dgq%2BMnSH3EBn | unknown | binary | 472 b | unknown |
1080 | svchost.exe | GET | 200 | 84.53.175.107:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a7cbe0941f54ddd4 | unknown | compressed | 67.5 Kb | unknown |
3684 | iexplore.exe | GET | 200 | 142.251.36.4:80 | http://www.google.com/favicon.ico | unknown | image | 1.46 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3940 | dzvsac.exe | 46.17.44.54:80 | u2728516dh.ha002.t.justns.ru | LLC Baxet | RU | unknown |
1164 | explorer.exe | 178.21.11.90:25998 | — | Domain names registrar REG.RU, Ltd | RU | unknown |
3964 | advasv.exe | 178.21.11.90:25998 | — | Domain names registrar REG.RU, Ltd | RU | unknown |
1560 | iexplore.exe | 13.107.5.80:443 | api.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3684 | iexplore.exe | 88.221.24.72:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
1560 | iexplore.exe | 84.53.175.107:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | whitelisted |
3684 | iexplore.exe | 84.53.175.107:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google-public-dns-a.google.com |
| whitelisted |
u2728516dh.ha002.t.justns.ru |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
www.google.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1164 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Plurox Backdoor CnC Checkin |
3964 | advasv.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Plurox Backdoor CnC Checkin |
3964 | advasv.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Plurox Backdoor CnC Checkin |
3964 | advasv.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Plurox Backdoor CnC Checkin |
3964 | advasv.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Plurox Backdoor CnC Checkin |
3964 | advasv.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Plurox Backdoor CnC Checkin |
1164 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Plurox Backdoor CnC Checkin |
3940 | dzvsac.exe | A Network Trojan was detected | ET HUNTING Suspicious Zipped Filename in Outbound POST Request (ccdata.txt) M2 |
3940 | dzvsac.exe | A Network Trojan was detected | ET HUNTING Suspicious Zipped Filename in Outbound POST Request (google_chrome_default_) M2 |
3964 | advasv.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Plurox Backdoor CnC Checkin |
3 ETPRO signatures available at the full report