| File name: | Memehax.zip |
| Full analysis: | https://app.any.run/tasks/4a647917-b99f-4b3a-bcd9-f95120b673e2 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | June 22, 2019, 12:09:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 04F3235986E5C35DFF3B1F5E8F51B1FC |
| SHA1: | 88619AAB227A62AF9E5E024FCBF8D86A788A61B6 |
| SHA256: | F1E85442D2085FC6C6561EB212FB8791CE15EB6A84BFB07A933191AAEABE1090 |
| SSDEEP: | 393216:eRX/qSi7FQ6kmTTwa8n5w5LTpmQkm9407+K:eVyaHmIacoLt7kDW |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 4012)
Drops/Copies Quasar RAT executable
- Free Robux Generator.exe (PID: 3464)
- WindowsDefender.exe (PID: 2056)
Application was dropped or rewritten from another process
- WindowsDefender.exe (PID: 2056)
- WindowsDefender.exe (PID: 3424)
Uses Task Scheduler to autorun other applications
- WindowsDefender.exe (PID: 2056)
- WindowsDefender.exe (PID: 3424)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 1784)
- schtasks.exe (PID: 408)
QUASAR was detected
- WindowsDefender.exe (PID: 2056)
- WindowsDefender.exe (PID: 3424)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2156)
- Free Robux Generator.exe (PID: 3464)
- WindowsDefender.exe (PID: 2056)
Creates files in the program directory
- dw20.exe (PID: 3412)
Creates files in the user directory
- WindowsDefender.exe (PID: 2056)
- WindowsDefender.exe (PID: 3424)
Starts itself from another location
- WindowsDefender.exe (PID: 2056)
Checks for external IP
- WindowsDefender.exe (PID: 2056)
- WindowsDefender.exe (PID: 3424)
INFO
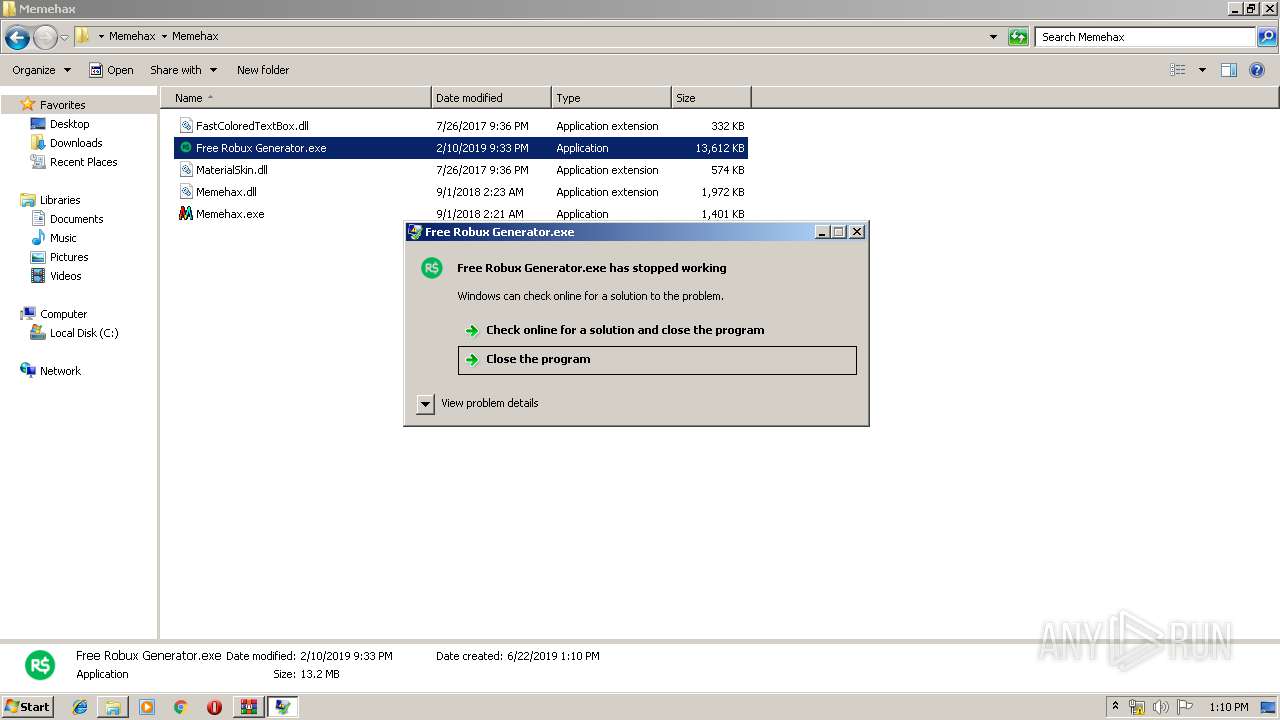
Application was crashed
- Free Robux Generator.exe (PID: 3464)
Manual execution by user
- Free Robux Generator.exe (PID: 3464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:02:10 21:44:23 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Memehax/Memehax/ |
Total processes
45
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 408 | "schtasks" /create /tn "Windows Defender" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\Windows Defender\WindowsDefender.exe" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | WindowsDefender.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | "schtasks" /create /tn "Windows Defender" /sc ONLOGON /tr "C:\Users\admin\AppData\Local\Temp\WindowsDefender.exe" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | WindowsDefender.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | "C:\Users\admin\AppData\Local\Temp\WindowsDefender.exe" | C:\Users\admin\AppData\Local\Temp\WindowsDefender.exe | Free Robux Generator.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2156 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Memehax.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3412 | dw20.exe -x -s 660 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | — | Free Robux Generator.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 3424 | "C:\Users\admin\AppData\Roaming\Windows Defender\WindowsDefender.exe" | C:\Users\admin\AppData\Roaming\Windows Defender\WindowsDefender.exe | WindowsDefender.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\Desktop\Memehax\Memehax\Free Robux Generator.exe" | C:\Users\admin\Desktop\Memehax\Memehax\Free Robux Generator.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 3762507597 Version: 0.0.0.0 Modules
| |||||||||||||||
| 4012 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 213
Read events
1 189
Write events
24
Delete events
0
Modification events
| (PID) Process: | (2156) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2156) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2156) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2156) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Memehax.zip | |||
| (PID) Process: | (2156) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2156) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2156) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2156) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3464) Free Robux Generator.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3464) Free Robux Generator.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
4
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2156.41959\Memehax\Memehax\Free Robux Generator.exe | — | |
MD5:— | SHA256:— | |||
| 2156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2156.41959\Memehax\Memehax\MaterialSkin.dll | — | |
MD5:— | SHA256:— | |||
| 2156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2156.41959\Memehax\Memehax\Memehax.dll | — | |
MD5:— | SHA256:— | |||
| 2156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2156.41959\Memehax\Memehax\Memehax.exe | — | |
MD5:— | SHA256:— | |||
| 2056 | WindowsDefender.exe | C:\Users\admin\AppData\Roaming\Windows Defender\WindowsDefender.exe | executable | |
MD5:— | SHA256:— | |||
| 3412 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_free robux gener_d1b8e818f047355b9267fb8577a2fa18a1cb1e_0d46896c\Report.wer | binary | |
MD5:— | SHA256:— | |||
| 3424 | WindowsDefender.exe | C:\Users\admin\AppData\Roaming\logs\06-22-2019 | binary | |
MD5:— | SHA256:— | |||
| 2156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2156.41959\Memehax\Memehax\FastColoredTextBox.dll | executable | |
MD5:7D315038DA4CB77039DC315C64946E22 | SHA256:777C68C5C47CF91E18583A0FA50B556B1551898A07097F296A0811943A493FA6 | |||
| 3464 | Free Robux Generator.exe | C:\Users\admin\AppData\Local\Temp\audiodg.exe | executable | |
MD5:— | SHA256:— | |||
| 3464 | Free Robux Generator.exe | C:\Users\admin\AppData\Local\Temp\WindowsDefender.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
2
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3424 | WindowsDefender.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/ | DE | text | 266 b | malicious |
2056 | WindowsDefender.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/ | DE | text | 266 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2056 | WindowsDefender.exe | 185.194.141.58:80 | ip-api.com | netcup GmbH | DE | unknown |
3424 | WindowsDefender.exe | 185.194.141.58:80 | ip-api.com | netcup GmbH | DE | unknown |
3424 | WindowsDefender.exe | 37.228.132.165:368 | narcicist.mooo.com | Mike Kaldig | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
narcicist.mooo.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2056 | WindowsDefender.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2056 | WindowsDefender.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2056 | WindowsDefender.exe | A Network Trojan was detected | MALWARE [PTsecurity] Quasar 1.3 RAT IP Lookup ip-api.com (HTTP headeer) |
3424 | WindowsDefender.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3424 | WindowsDefender.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3424 | WindowsDefender.exe | A Network Trojan was detected | MALWARE [PTsecurity] Quasar 1.3 RAT IP Lookup ip-api.com (HTTP headeer) |
1056 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
2 ETPRO signatures available at the full report