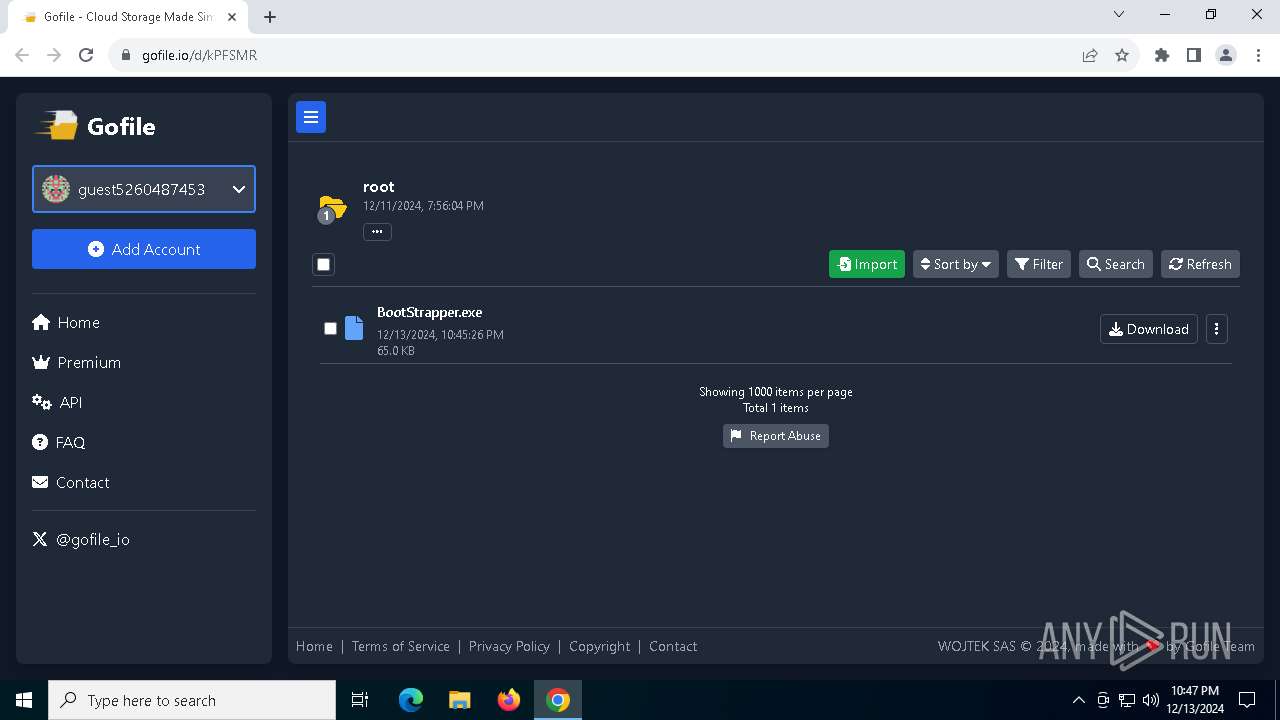
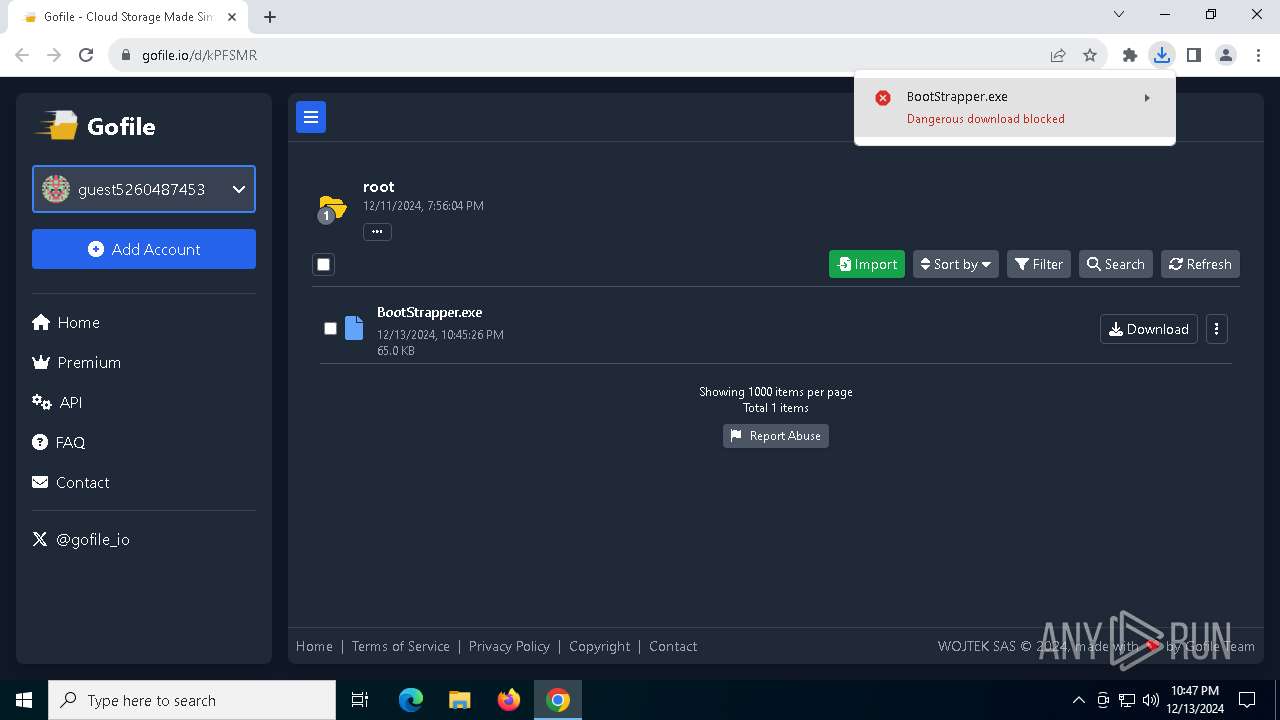
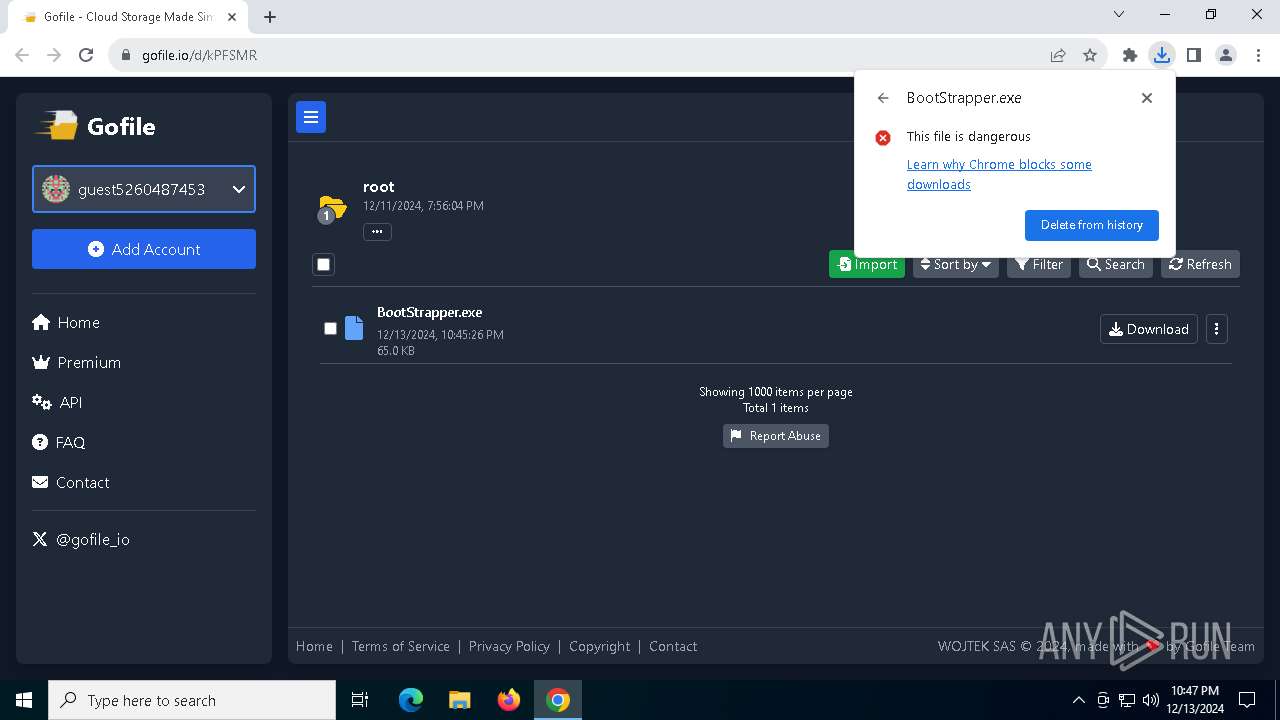
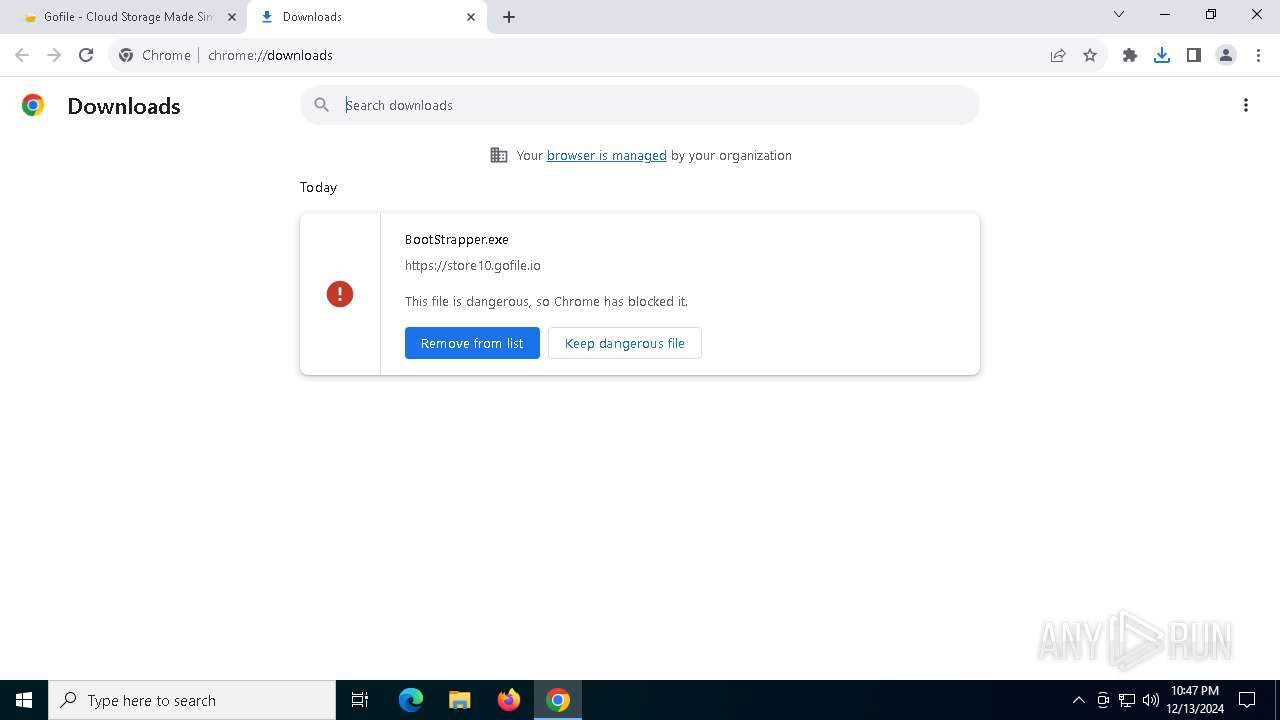
| URL: | https://gofile.io/d/kPFSMR |
| Full analysis: | https://app.any.run/tasks/e9d8d96e-693a-45cc-8343-92b0f543f8de |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 13, 2024, 22:46:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8473BE099FEE3689C880558F90D640A2 |
| SHA1: | F175D10AC34E92B61F3B26321427630B9D01D9FA |
| SHA256: | F1C5E0CF1F667243B26A80A5EC3623C80D33EAE76232A08541435403F6231CE3 |
| SSDEEP: | 3:N8rxL1m:2ZE |
MALICIOUS
ASYNCRAT has been detected (YARA)
- bsod.exe (PID: 2928)
Changes the autorun value in the registry
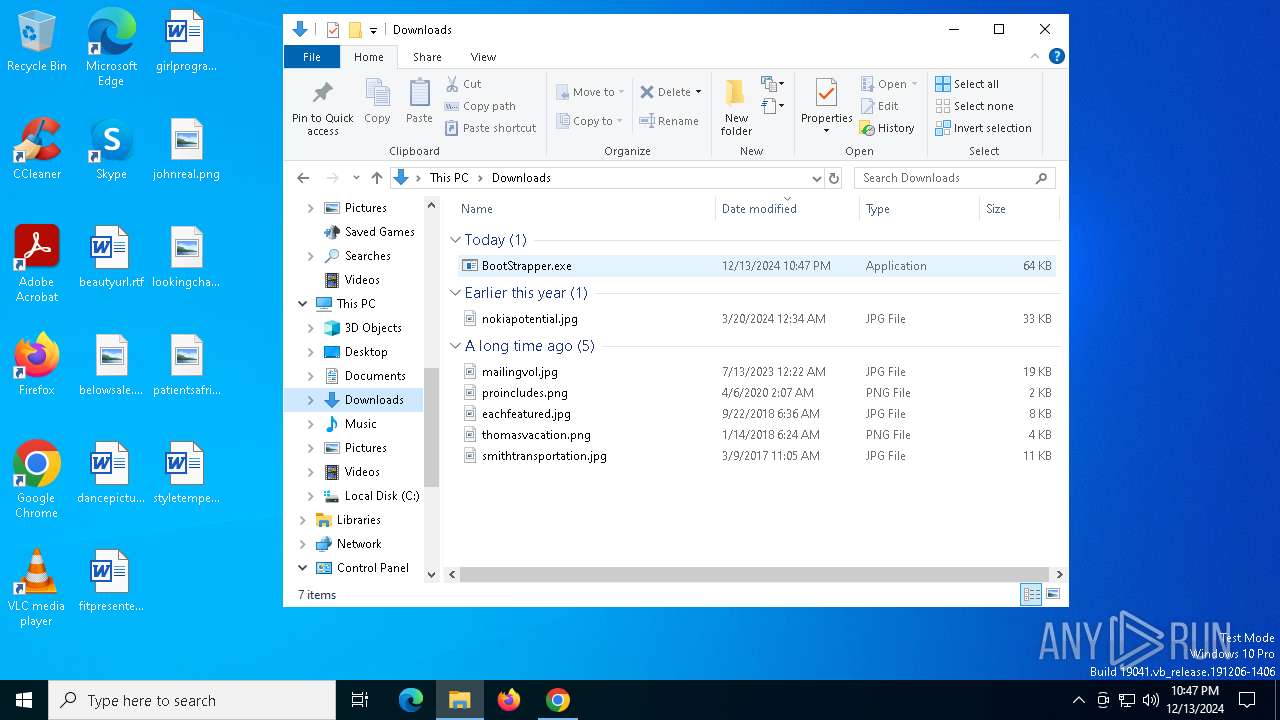
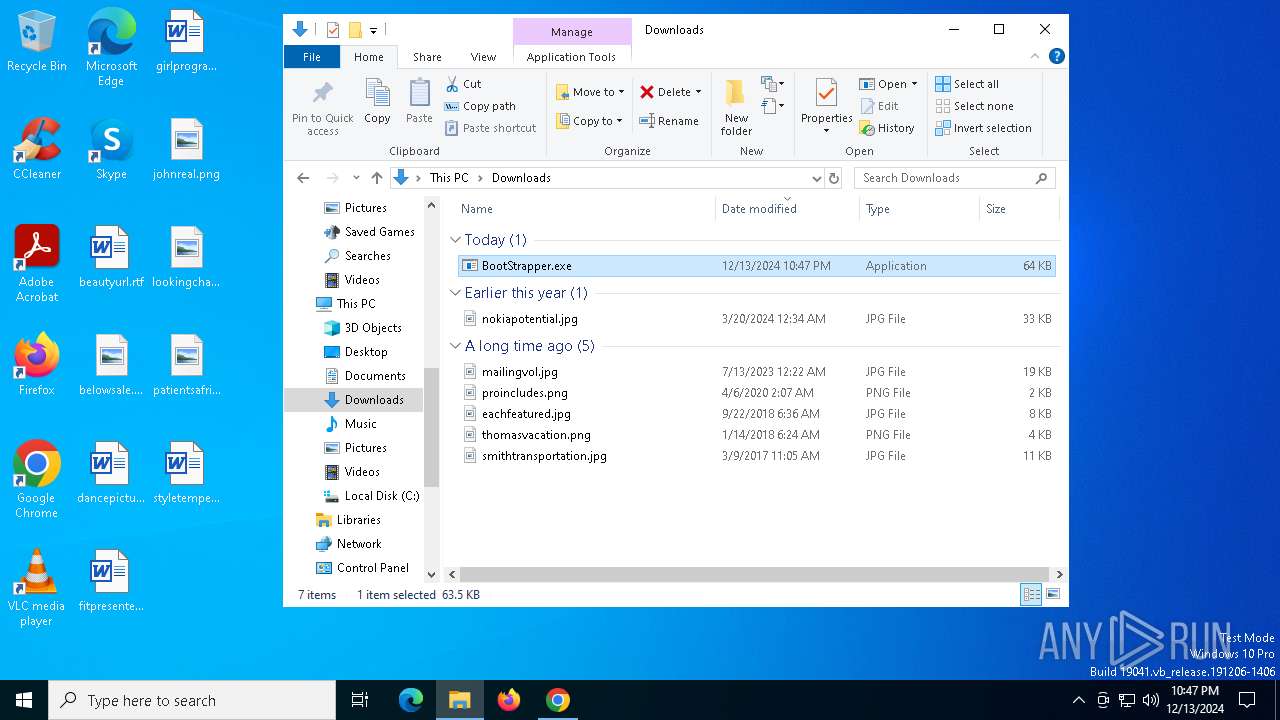
- BootStrapper.exe (PID: 8172)
SUSPICIOUS
Executing commands from a ".bat" file
- BootStrapper.exe (PID: 8172)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6936)
Starts CMD.EXE for commands execution
- BootStrapper.exe (PID: 8172)
Executable content was dropped or overwritten
- BootStrapper.exe (PID: 8172)
The executable file from the user directory is run by the CMD process
- bsod.exe (PID: 2928)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2192)
INFO
The process uses the downloaded file
- chrome.exe (PID: 8064)
- chrome.exe (PID: 6568)
Executable content was dropped or overwritten
- chrome.exe (PID: 6568)
- chrome.exe (PID: 6492)
Create files in a temporary directory
- BootStrapper.exe (PID: 8172)
Checks supported languages
- BootStrapper.exe (PID: 8172)
- bsod.exe (PID: 2928)
- BootStrapper.exe (PID: 2672)
Creates files or folders in the user directory
- BootStrapper.exe (PID: 8172)
Reads the computer name
- bsod.exe (PID: 2928)
- BootStrapper.exe (PID: 8172)
- BootStrapper.exe (PID: 2672)
Reads the machine GUID from the registry
- BootStrapper.exe (PID: 8172)
- bsod.exe (PID: 2928)
- BootStrapper.exe (PID: 2672)
Application launched itself
- chrome.exe (PID: 6568)
The sample compiled with english language support
- chrome.exe (PID: 6492)
Manual execution by a user
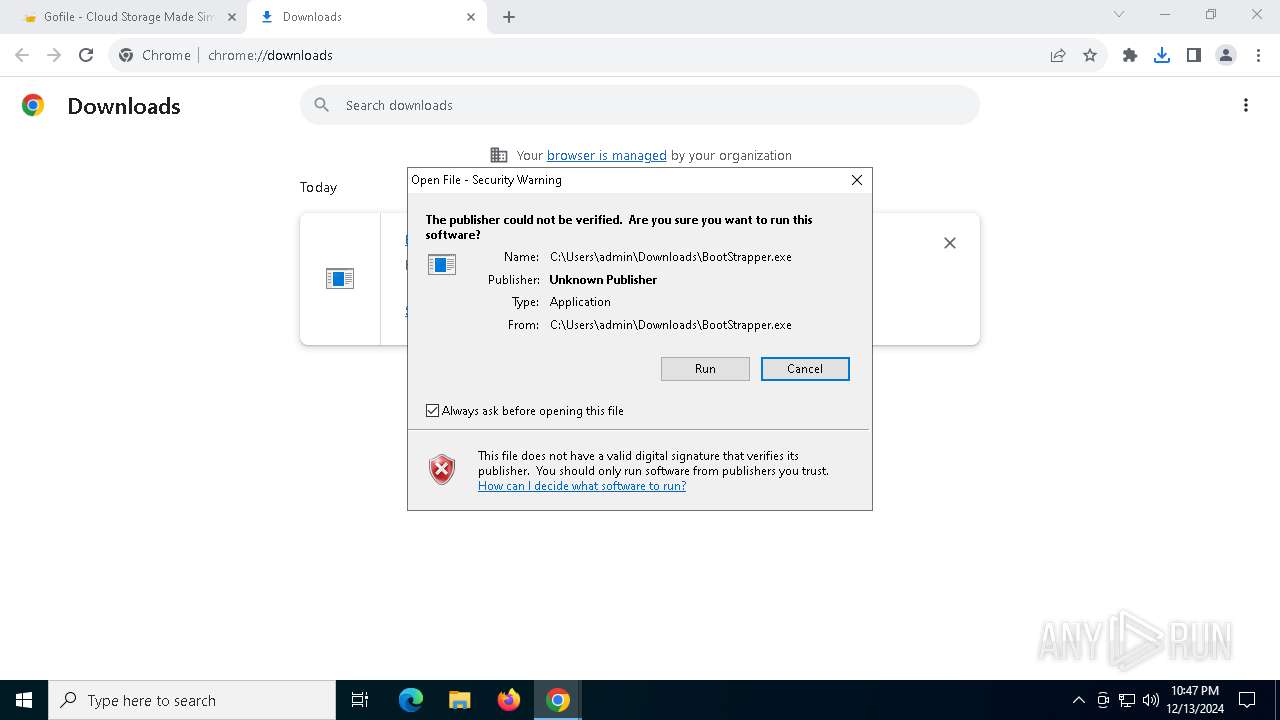
- BootStrapper.exe (PID: 2672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(2928) bsod.exe
C2 (2)127.0.0.1
specteded-40824.portmap.host
Ports (1)23
Version
Options
AutoRuntrue
Mutex杰NΗV勒艾LGoe斯تI吾开O
InstallFolder%AppData%
Certificates
Cert1MIICKTCCAZKgAwIBAgIVAJONBgQFqzpa7jdy8WsNyOY5blW/MA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjQwMzAzMTMxNjMzWhcNMzQxMjExMTMxNjMzWjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA...
Server_SignatureMMlFig7K1xdeoQUeTyMlipZQJOmHiTdPiYLRoE9yK1IVVdEMV2375PPrPaHrSEQxAIlkvy8XO4txhLJiBo67ABOSCgDHDLsLWXh5wmi4RwQ5cyUoCThNR4xnBCbFrj73OqWM827nWu1eVOOiXNtddpPkfvJ1aJeJP6hHfdq59zc=
Keys
AESceca6d8b132693bed433a414e754087ffa1aaa46ae75eea5da0eb5db085b3ac8
SaltDcRatByqwqdanchun
Total processes
156
Monitored processes
26
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\Downloads\BootStrapper.exe" | C:\Users\admin\Downloads\BootStrapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 3.6.0.0 Modules
| |||||||||||||||
| 2928 | "C:\Users\admin\AppData\Roaming\bsod.exe" | C:\Users\admin\AppData\Roaming\bsod.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 3.6.0.0 Modules
AsyncRat(PID) Process(2928) bsod.exe C2 (2)127.0.0.1 specteded-40824.portmap.host Ports (1)23 Version Options AutoRuntrue Mutex杰NΗV勒艾LGoe斯تI吾开O InstallFolder%AppData% Certificates Cert1MIICKTCCAZKgAwIBAgIVAJONBgQFqzpa7jdy8WsNyOY5blW/MA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjQwMzAzMTMxNjMzWhcNMzQxMjExMTMxNjMzWjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA... Server_SignatureMMlFig7K1xdeoQUeTyMlipZQJOmHiTdPiYLRoE9yK1IVVdEMV2375PPrPaHrSEQxAIlkvy8XO4txhLJiBo67ABOSCgDHDLsLWXh5wmi4RwQ5cyUoCThNR4xnBCbFrj73OqWM827nWu1eVOOiXNtddpPkfvJ1aJeJP6hHfdq59zc= Keys AESceca6d8b132693bed433a414e754087ffa1aaa46ae75eea5da0eb5db085b3ac8 SaltDcRatByqwqdanchun | |||||||||||||||
| 4308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=4180 --field-trial-handle=1872,i,5569542526515326972,12293255005065253961,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6168 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6252 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=856 --field-trial-handle=1872,i,5569542526515326972,12293255005065253961,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3584 --field-trial-handle=1872,i,5569542526515326972,12293255005065253961,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://gofile.io/d/kPFSMR" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ff8182adc40,0x7ff8182adc4c,0x7ff8182adc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
5 890
Read events
5 864
Write events
20
Delete events
6
Modification events
| (PID) Process: | (6568) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6568) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6568) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6568) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6568) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (8064) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000076DD38F4B04DDB01 | |||
| (PID) Process: | (8172) BootStrapper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | bsod |
Value: "C:\Users\admin\AppData\Roaming\bsod.exe" | |||
| (PID) Process: | (6568) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (6568) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (6568) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
Executable files
7
Suspicious files
64
Text files
23
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF136b9e.TMP | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF136b9e.TMP | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF136bae.TMP | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF136bae.TMP | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF136bae.TMP | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF136bbd.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
83
DNS requests
45
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6348 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6348 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7128 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5792 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acovj2efvkczd7qv7e6pmyxdosta_20241128.702116459.14/obedbbhbpmojnkanicioggnmelmoomoc_20241128.702116459.14_all_ENUS500000_mly4hgx432i2at3mf2t2m6amrq.crx3 | unknown | — | — | whitelisted |
5792 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acovj2efvkczd7qv7e6pmyxdosta_20241128.702116459.14/obedbbhbpmojnkanicioggnmelmoomoc_20241128.702116459.14_all_ENUS500000_mly4hgx432i2at3mf2t2m6amrq.crx3 | unknown | — | — | whitelisted |
5792 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acovj2efvkczd7qv7e6pmyxdosta_20241128.702116459.14/obedbbhbpmojnkanicioggnmelmoomoc_20241128.702116459.14_all_ENUS500000_mly4hgx432i2at3mf2t2m6amrq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3508 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3508 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
gofile.io |
| whitelisted |
accounts.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6904 | chrome.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6904 | chrome.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6904 | chrome.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
6904 | chrome.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6904 | chrome.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6904 | chrome.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6904 | chrome.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
6904 | chrome.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
6904 | chrome.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
6904 | chrome.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |