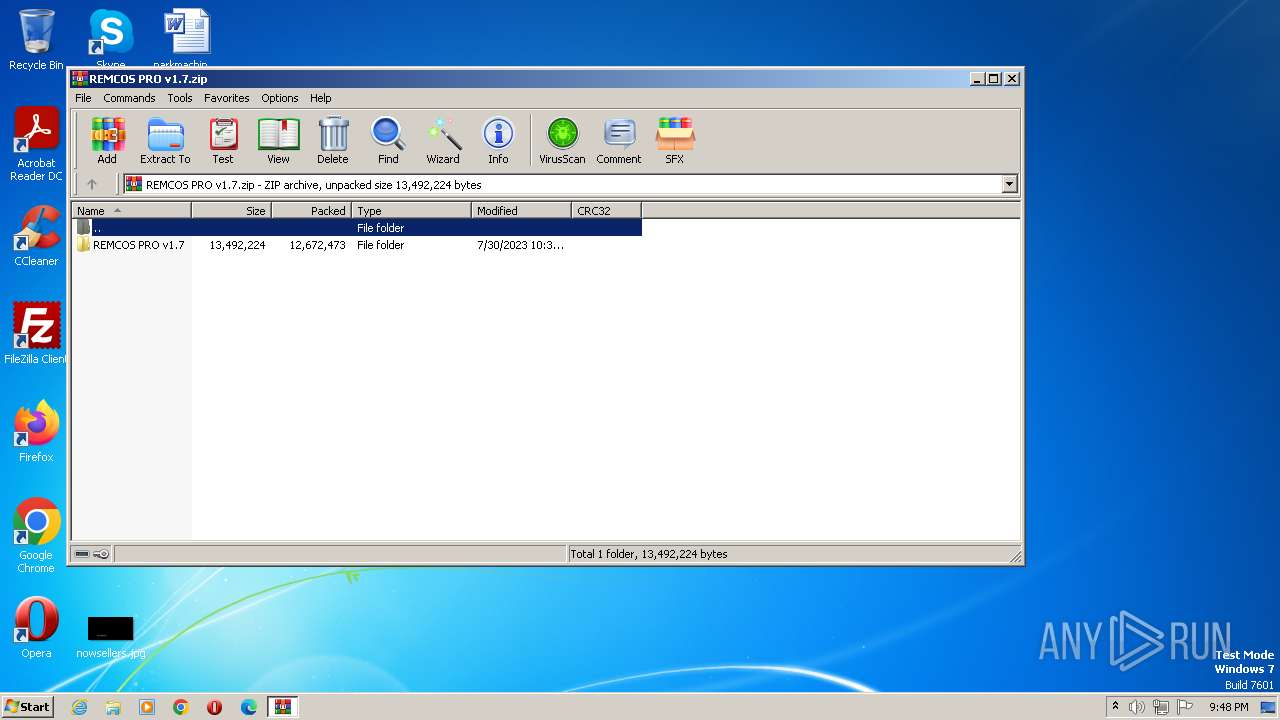
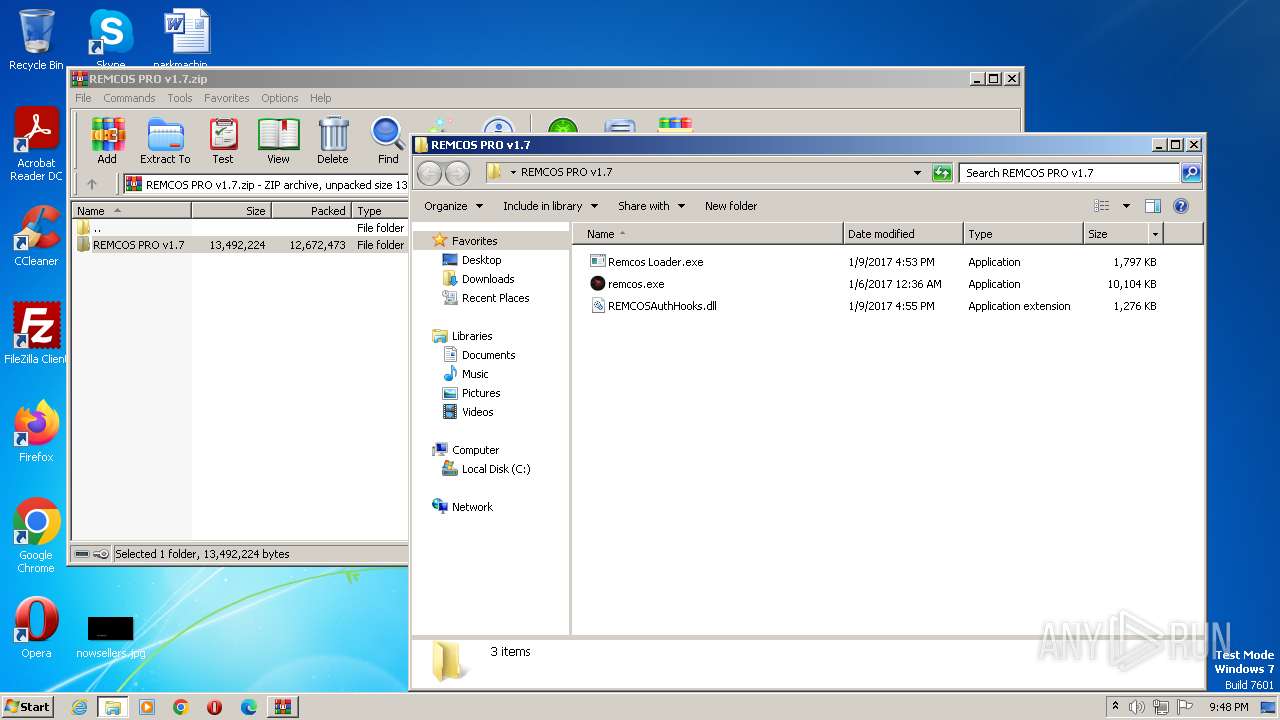
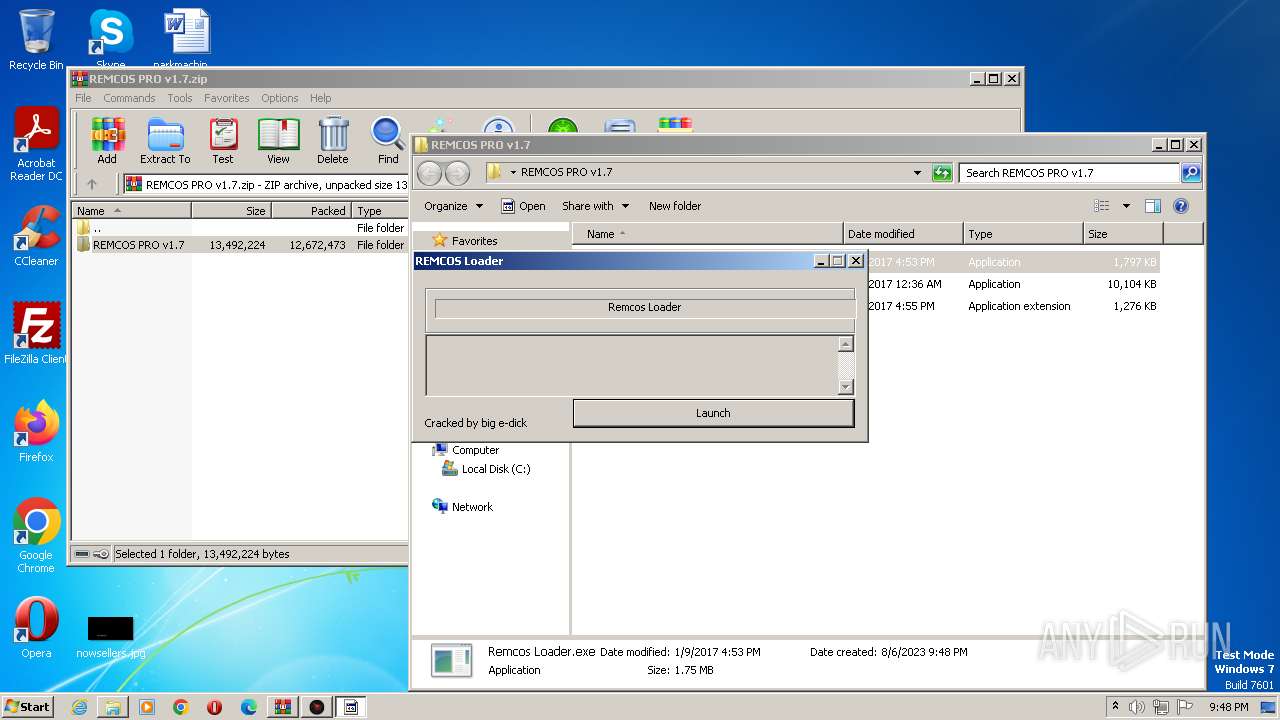
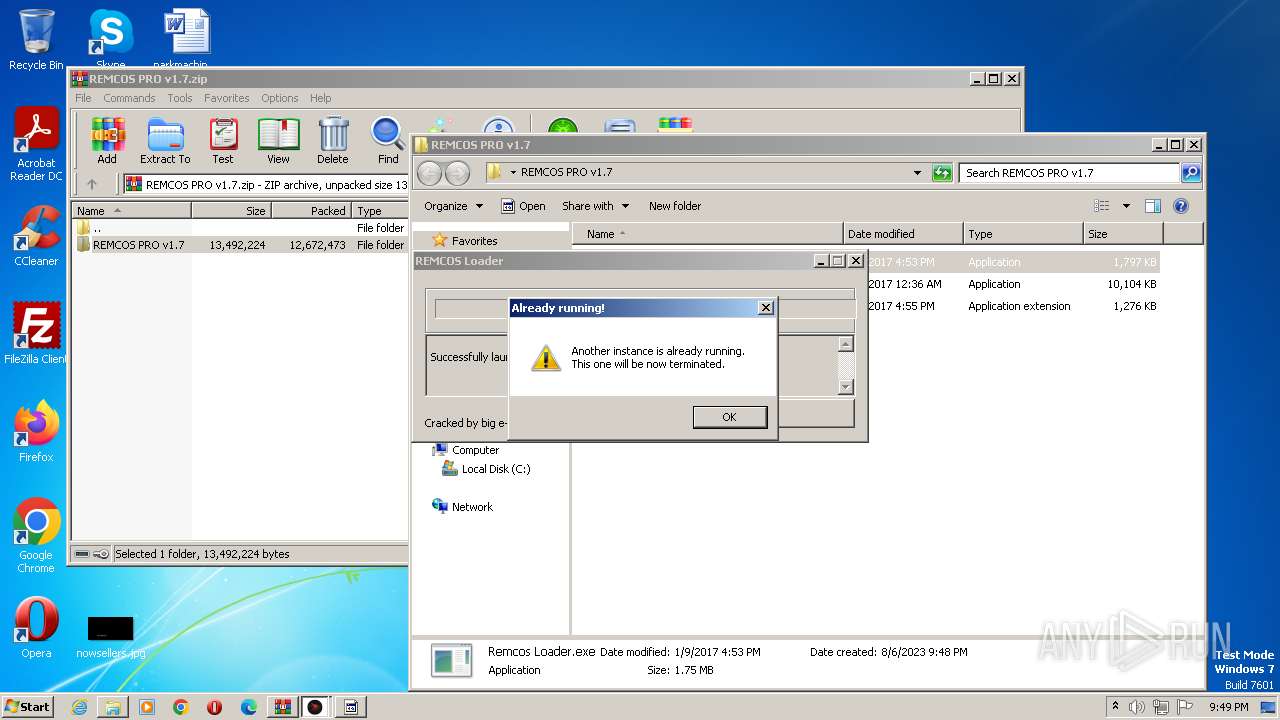
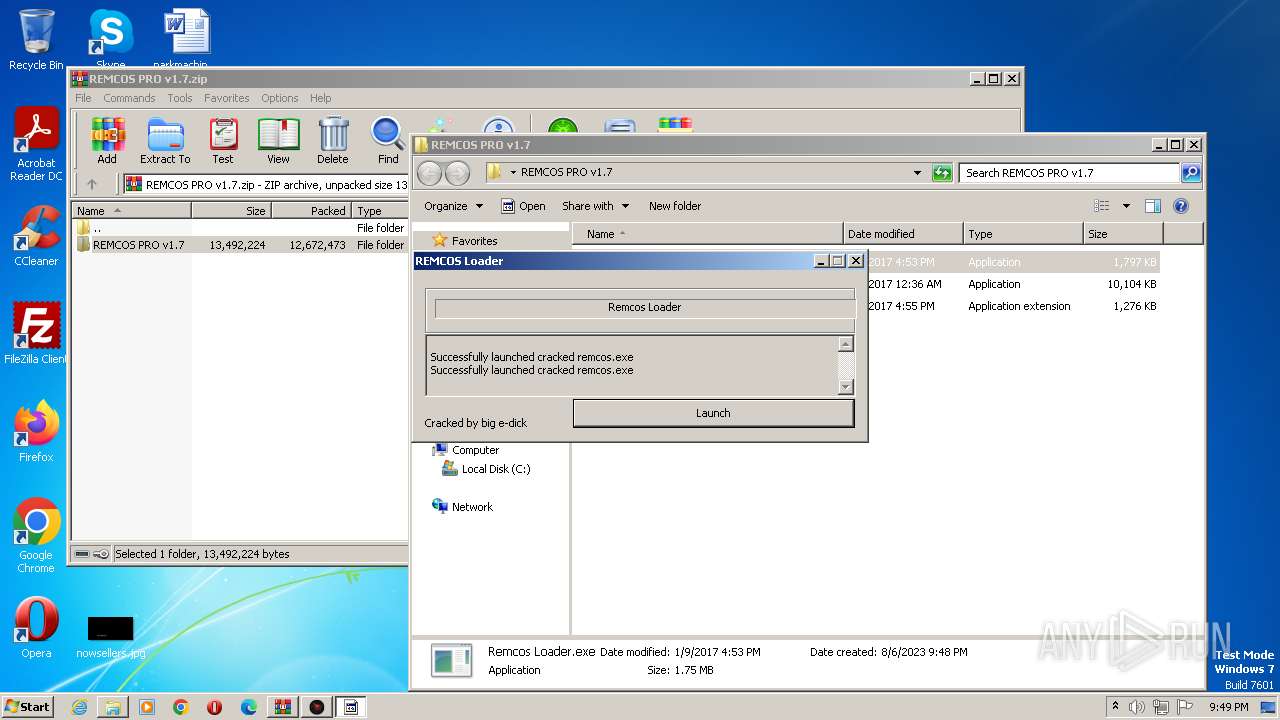
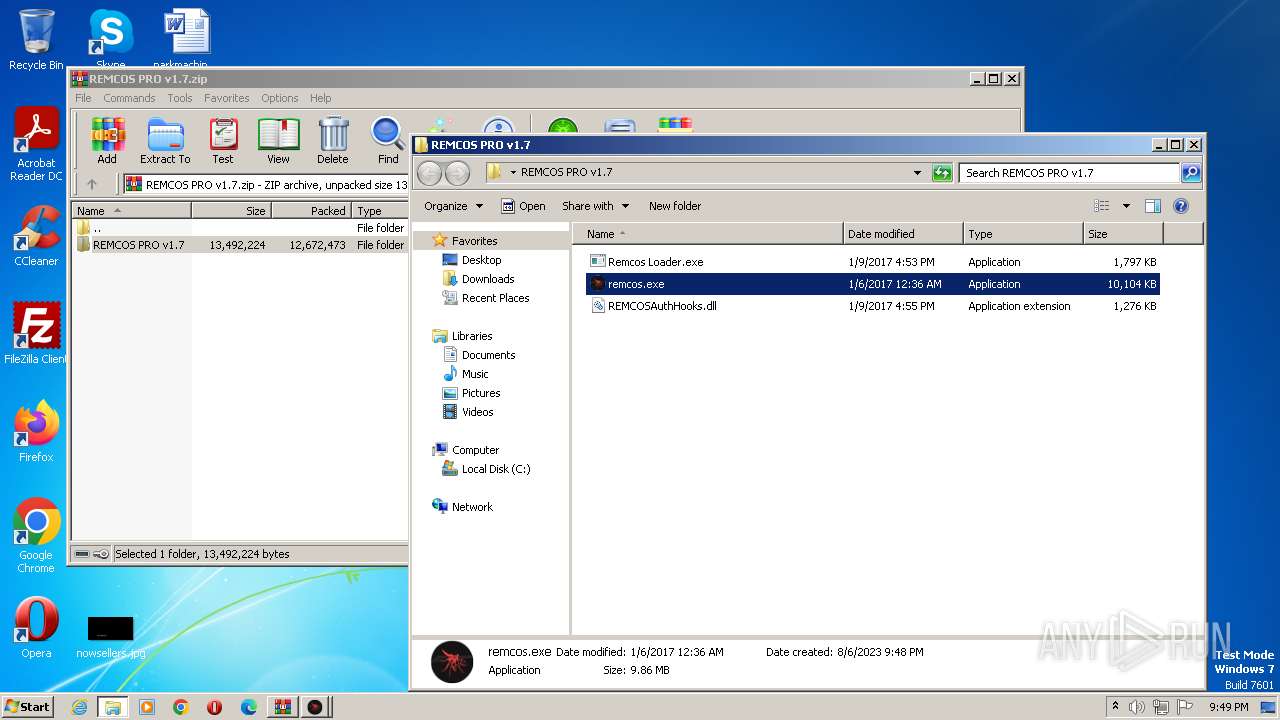
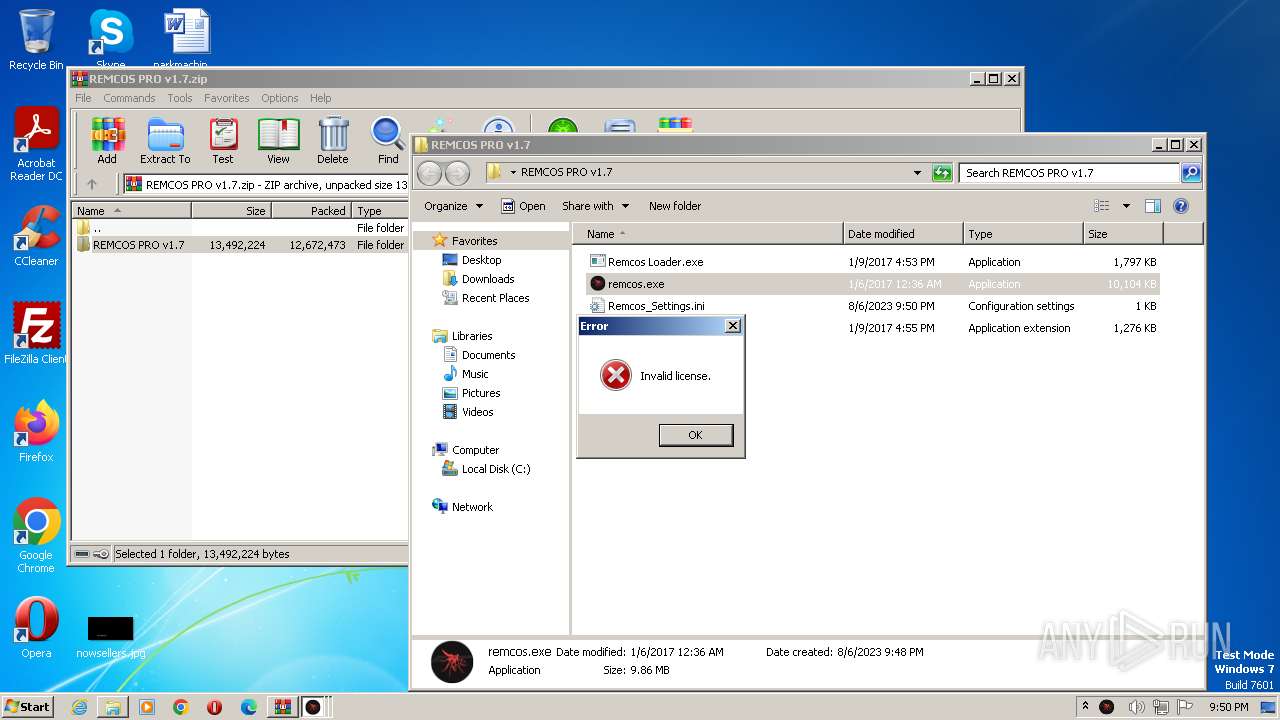
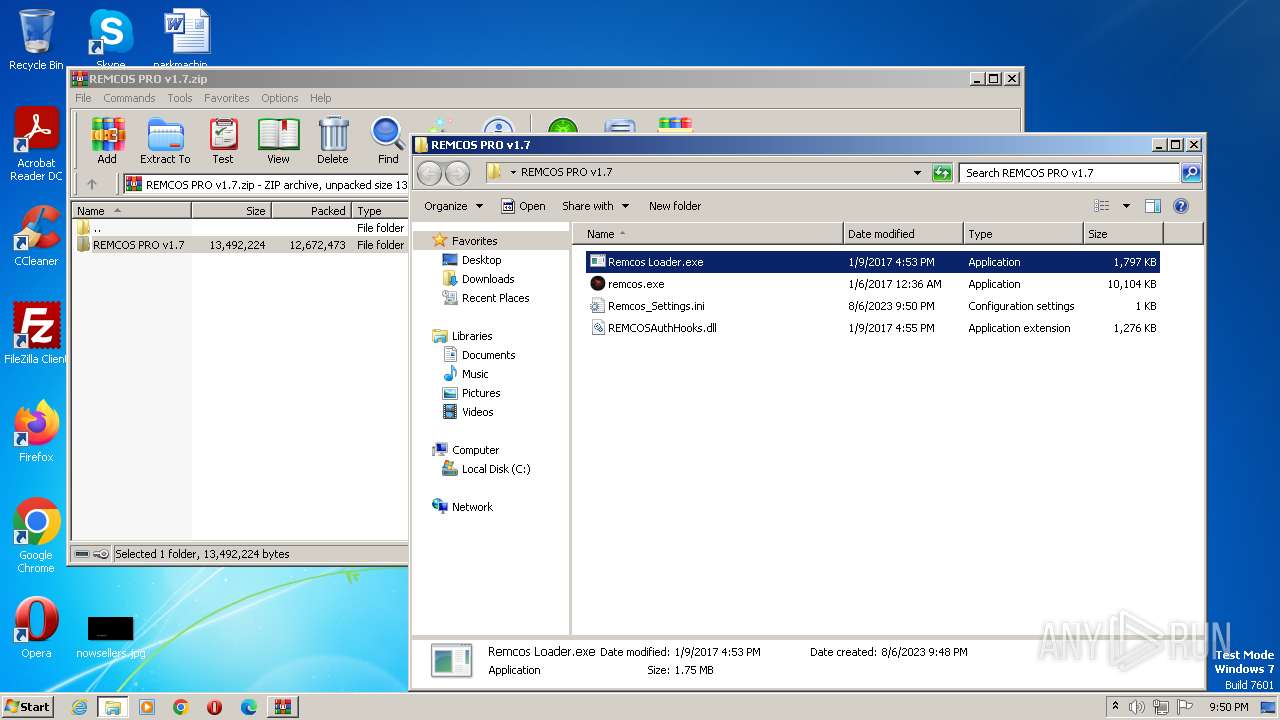
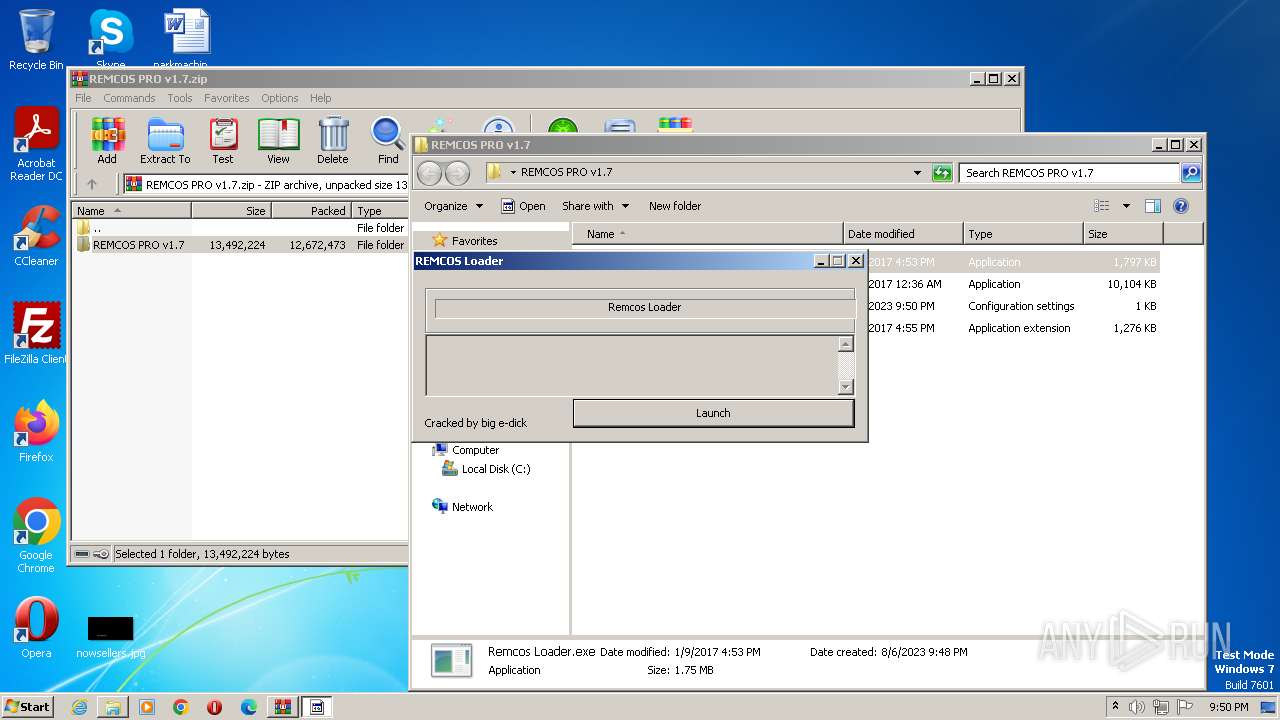
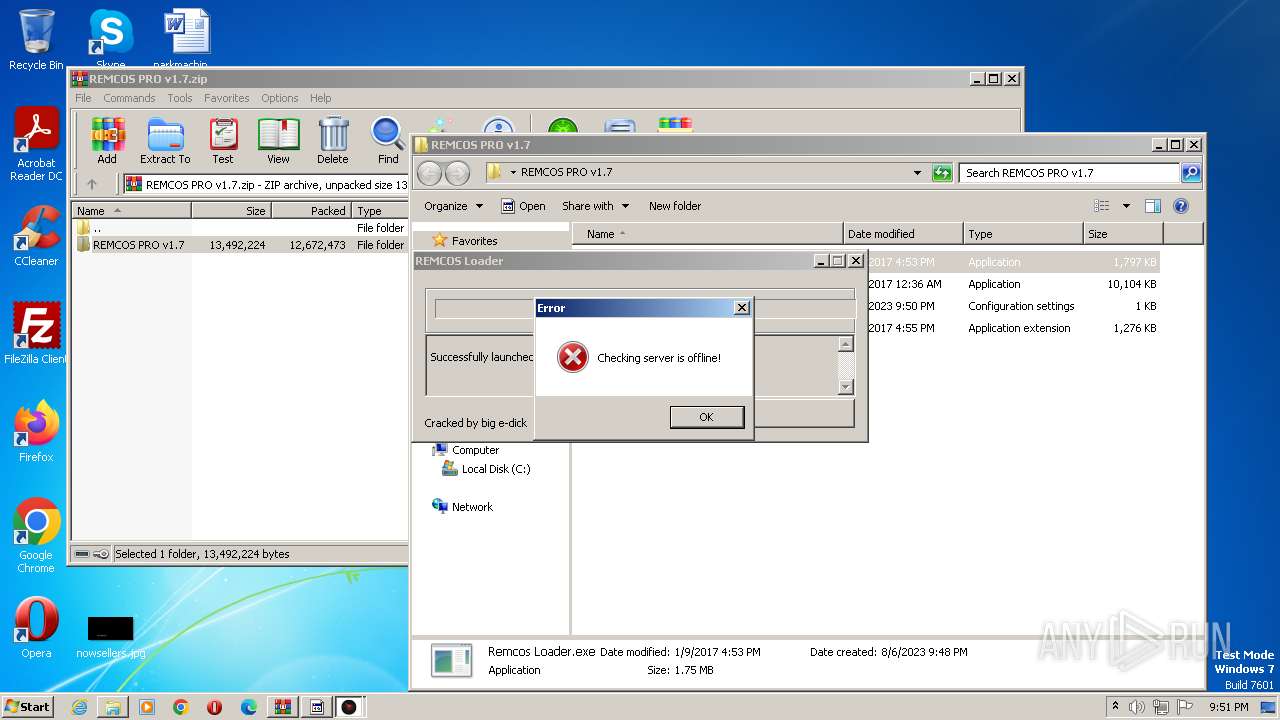
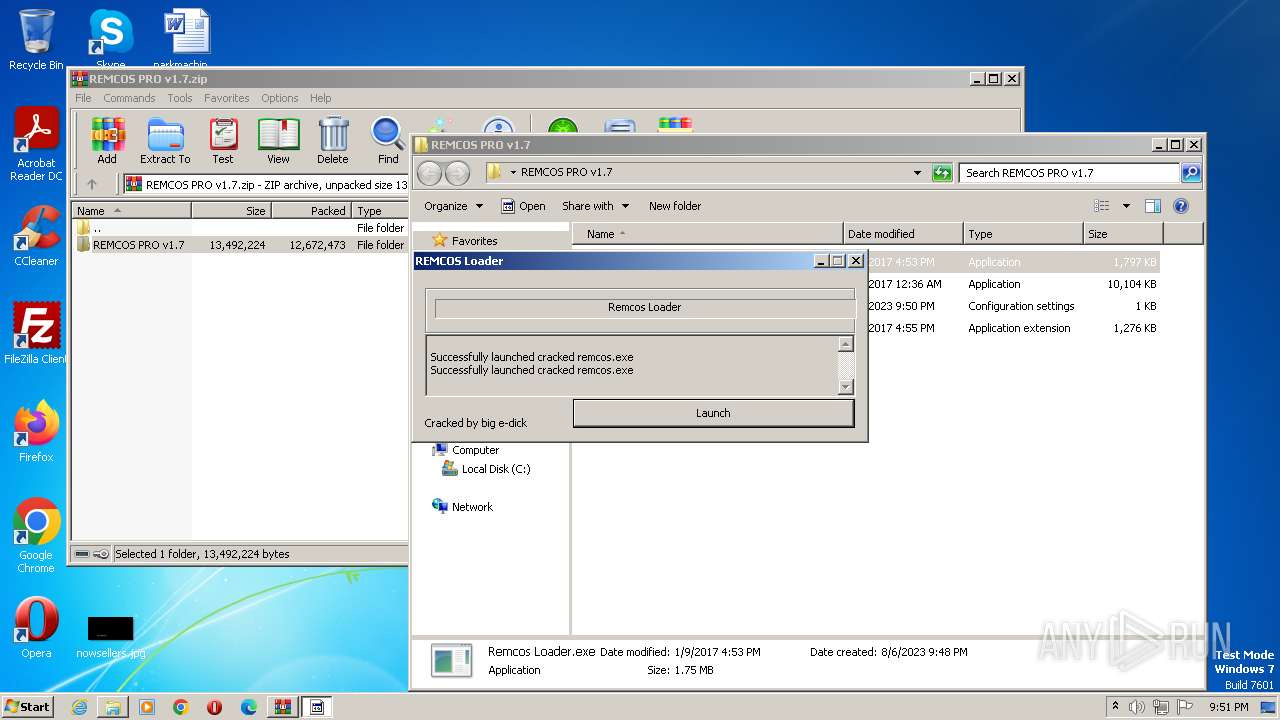
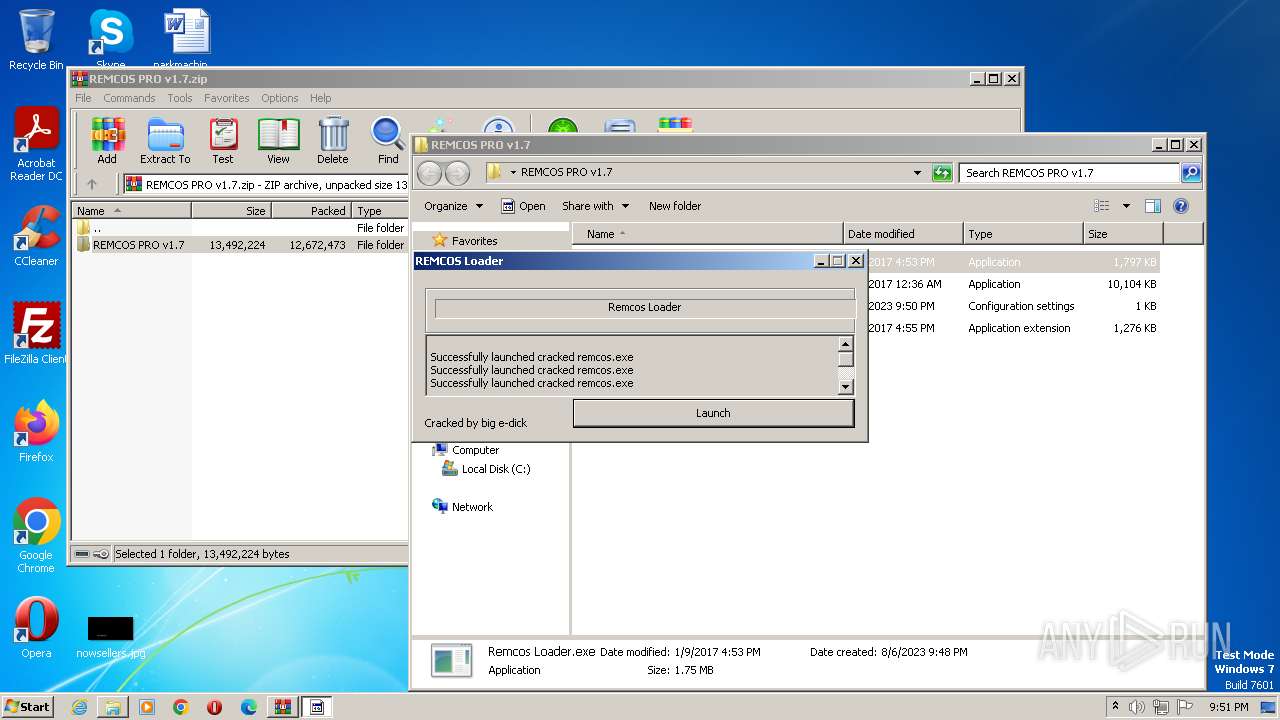
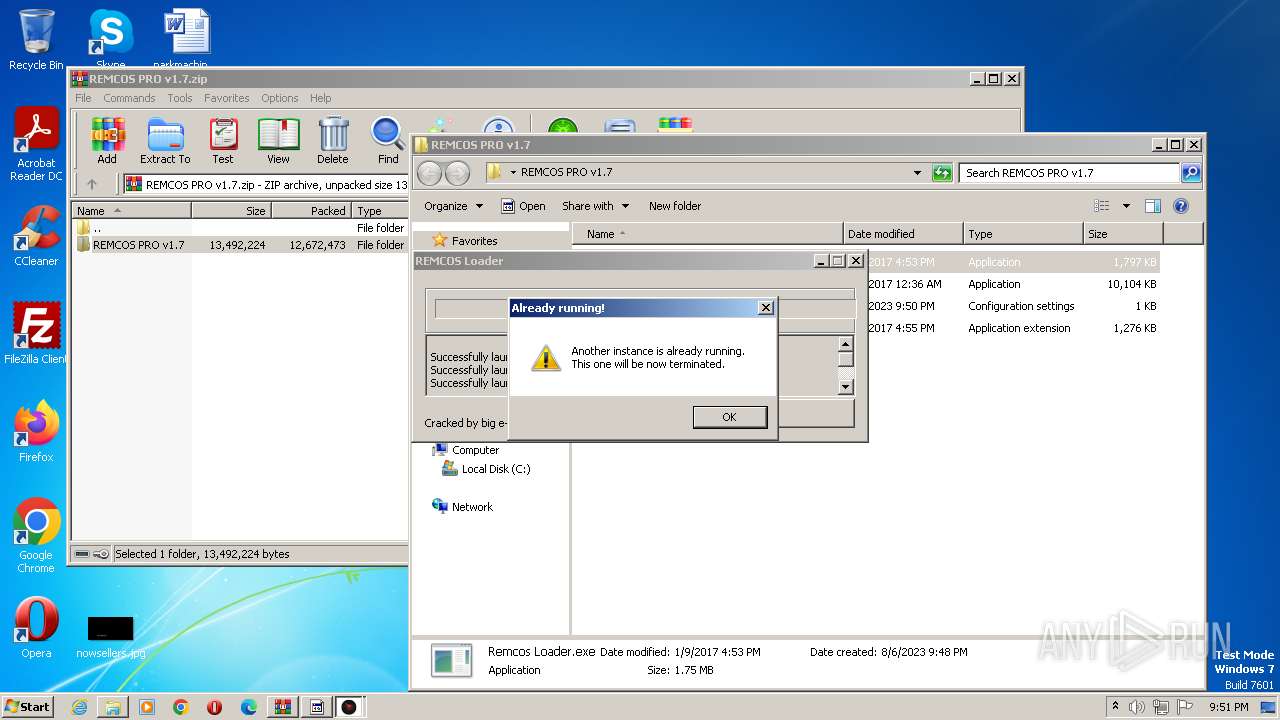
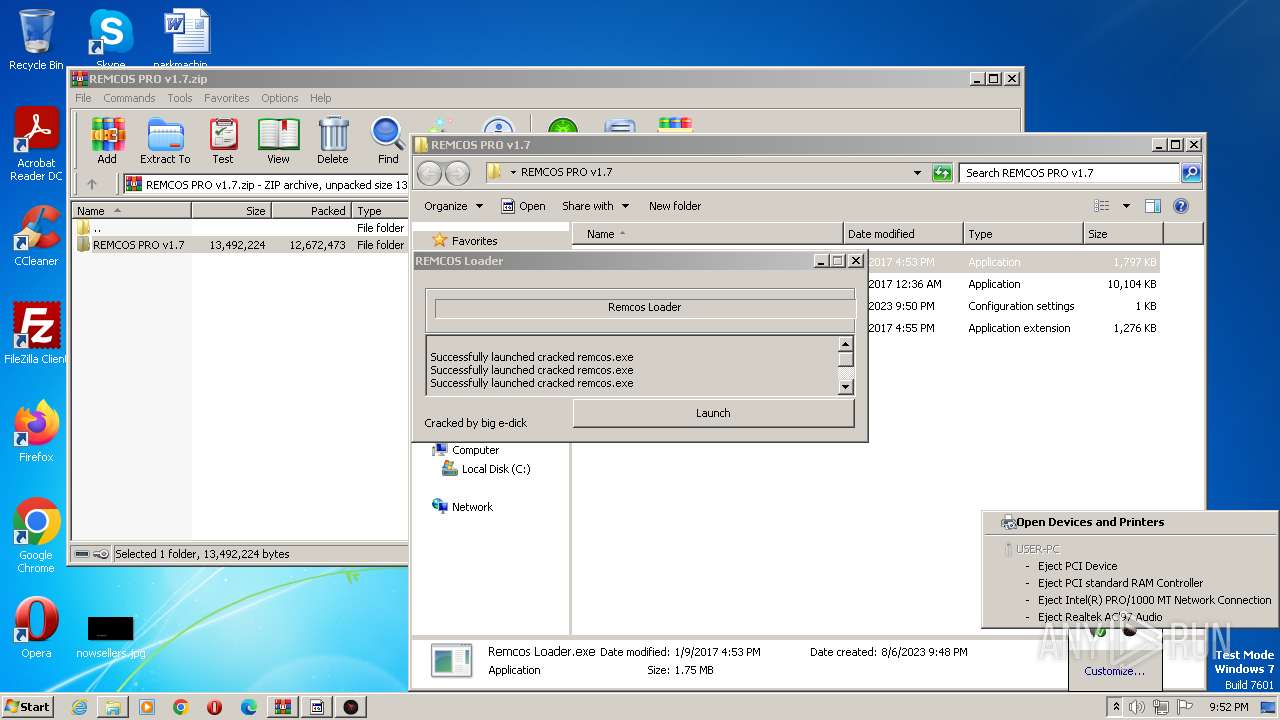
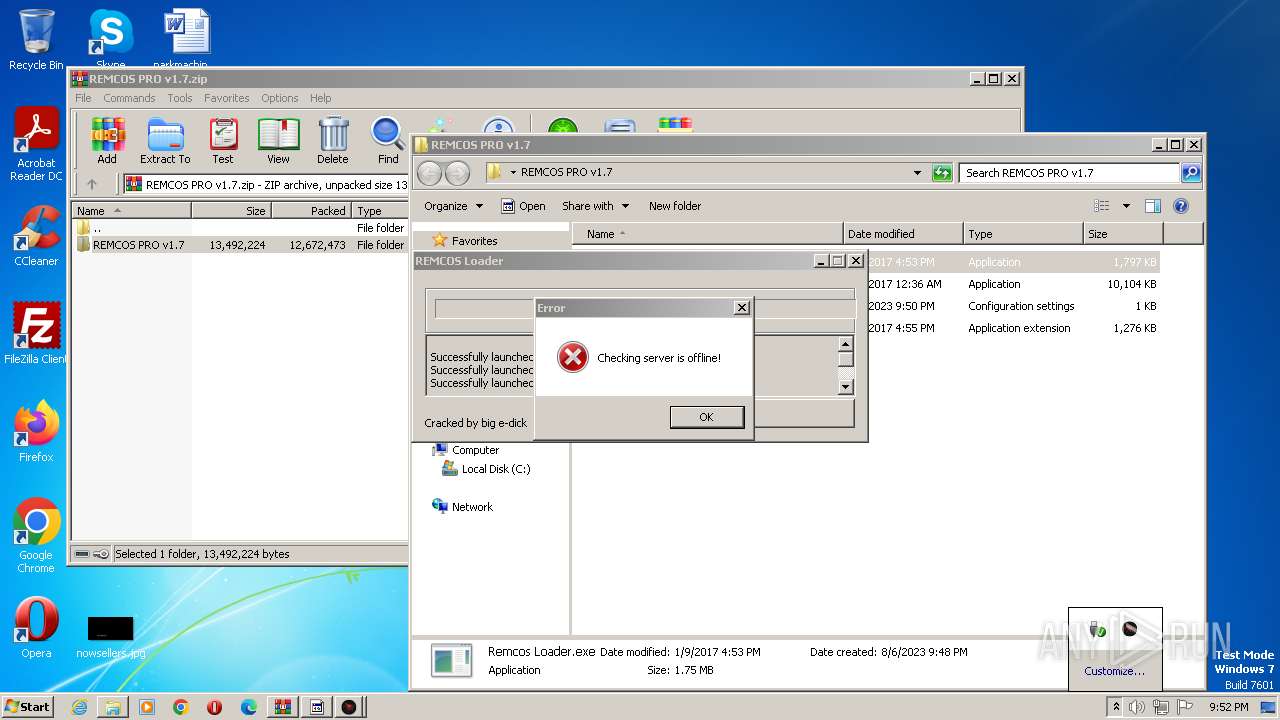
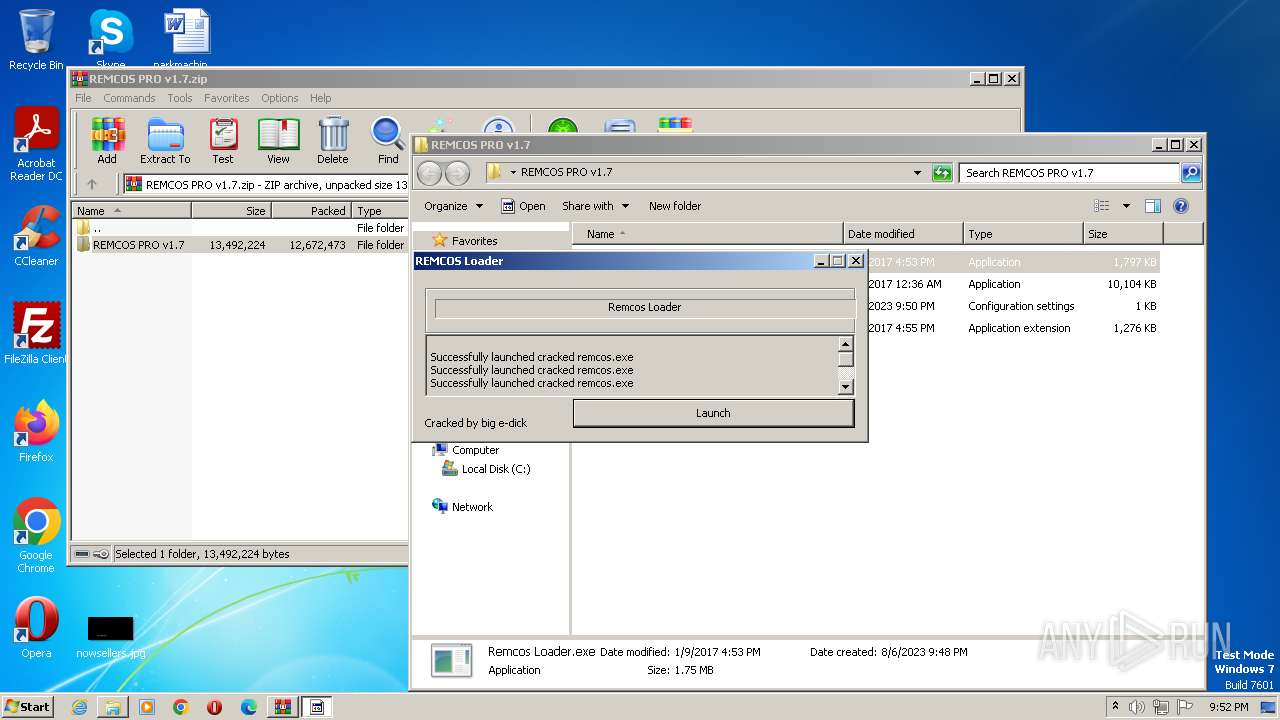
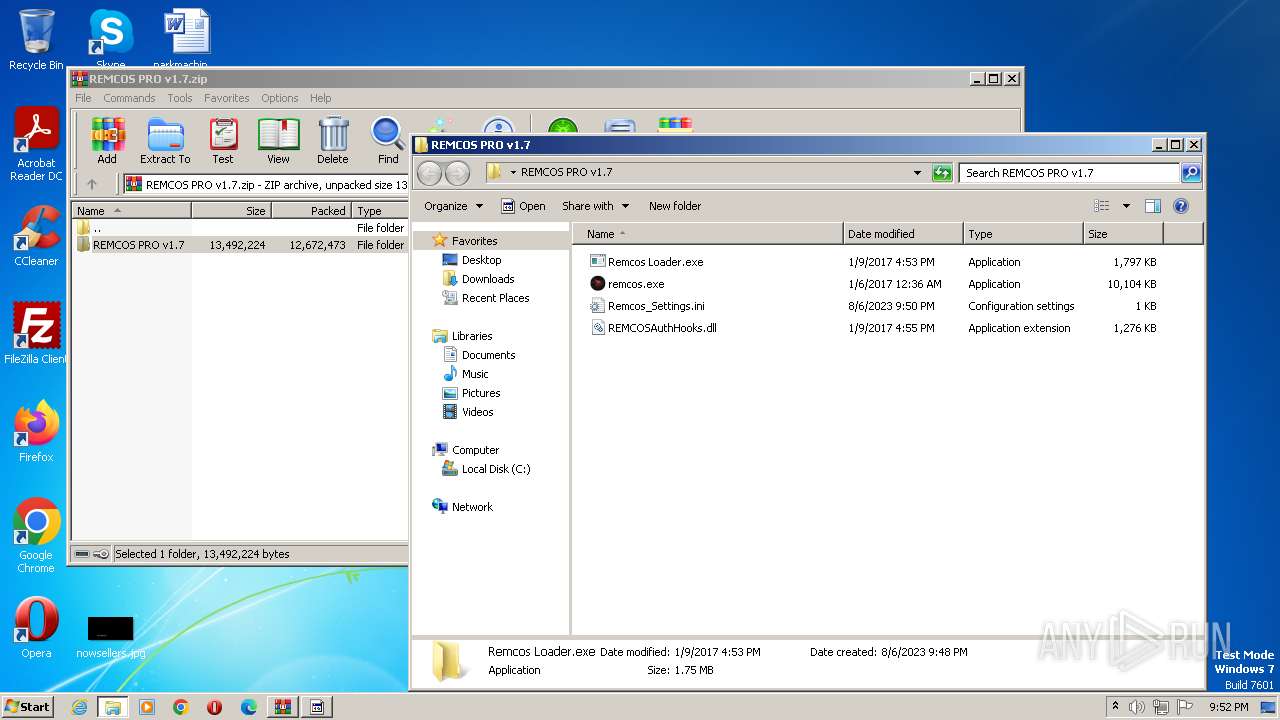
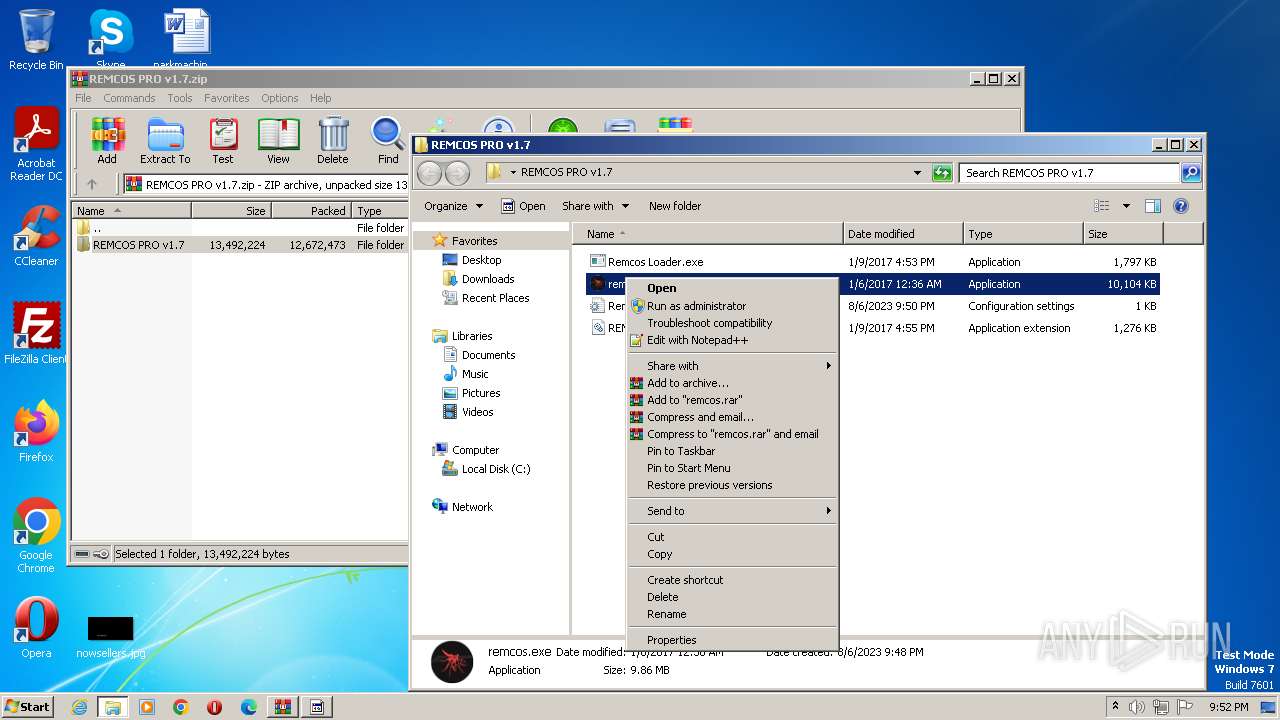
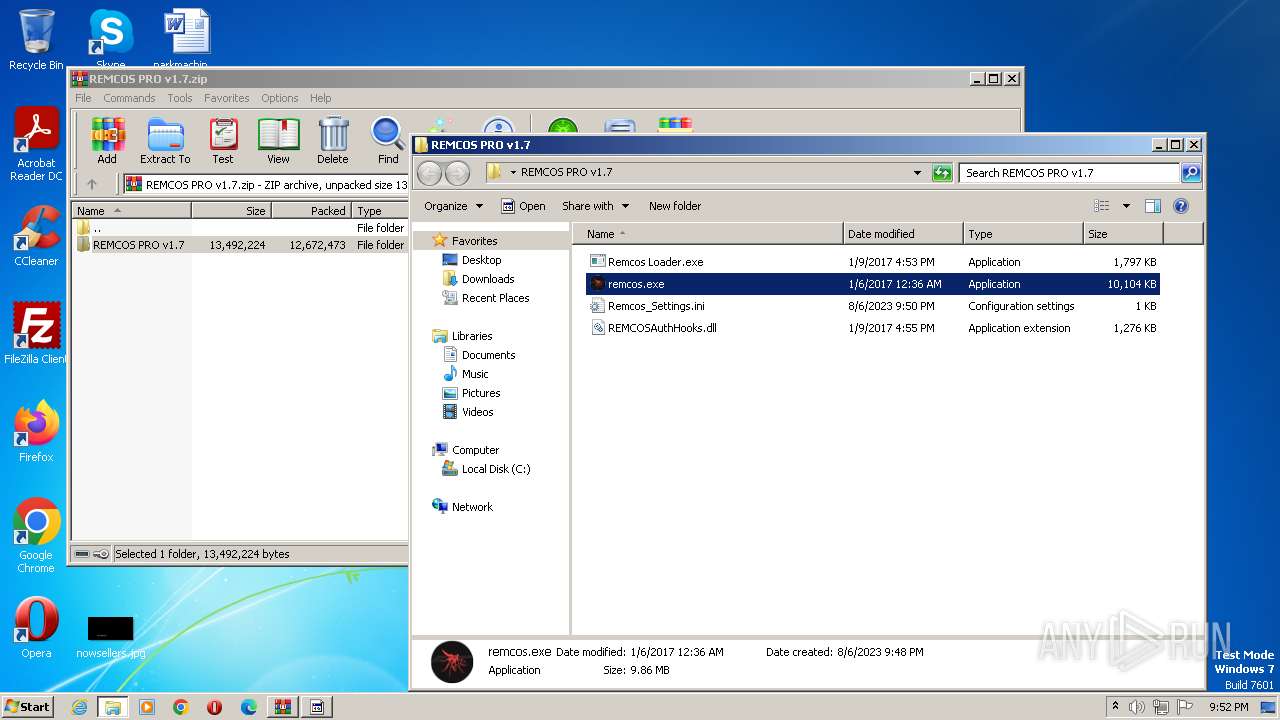
| File name: | REMCOS PRO v1.7.zip |
| Full analysis: | https://app.any.run/tasks/0e8967a1-83da-4914-85bb-f6ef2b824ad5 |
| Verdict: | Malicious activity |
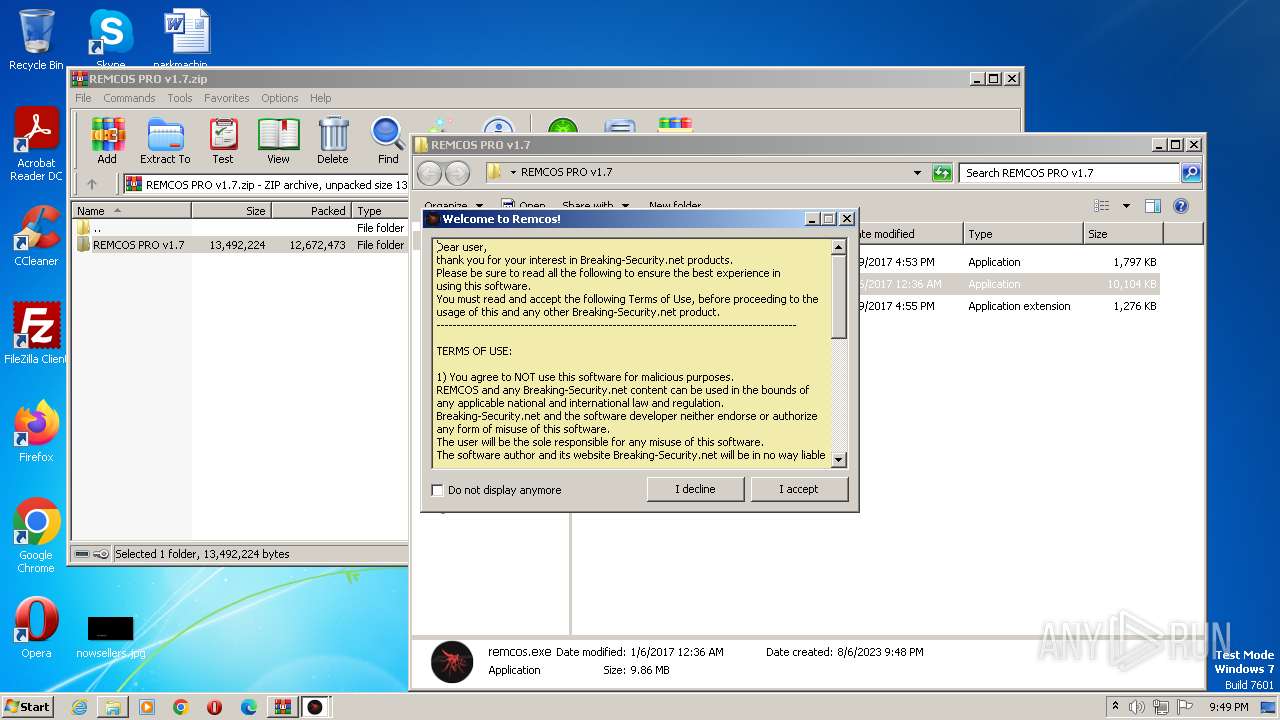
| Threats: | Remcos is a commercially distributed remote administration and surveillance tool that has been widely observed in unauthorized deployments, where threat actors use it to perform remote actions on compromised machines. It is actively maintained by its vendor, with new versions and feature updates released on a frequent, near-monthly basis. |
| Analysis date: | August 06, 2023, 20:48:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 45B214724869A4B6BE1C77FA60A1F07E |
| SHA1: | F6C8ECB2F72D2F45790827C188C0F6AD03DEB061 |
| SHA256: | F1BF89997A9485FCFD257DAF62096FF0AF93787A365A04E911BBFF4A7EBB5918 |
| SSDEEP: | 393216:sa4KHfmupIMuEC1GDibEVFWd8ciGKNpBdrZ:sa4KHfmu22C1YZVFWeb |
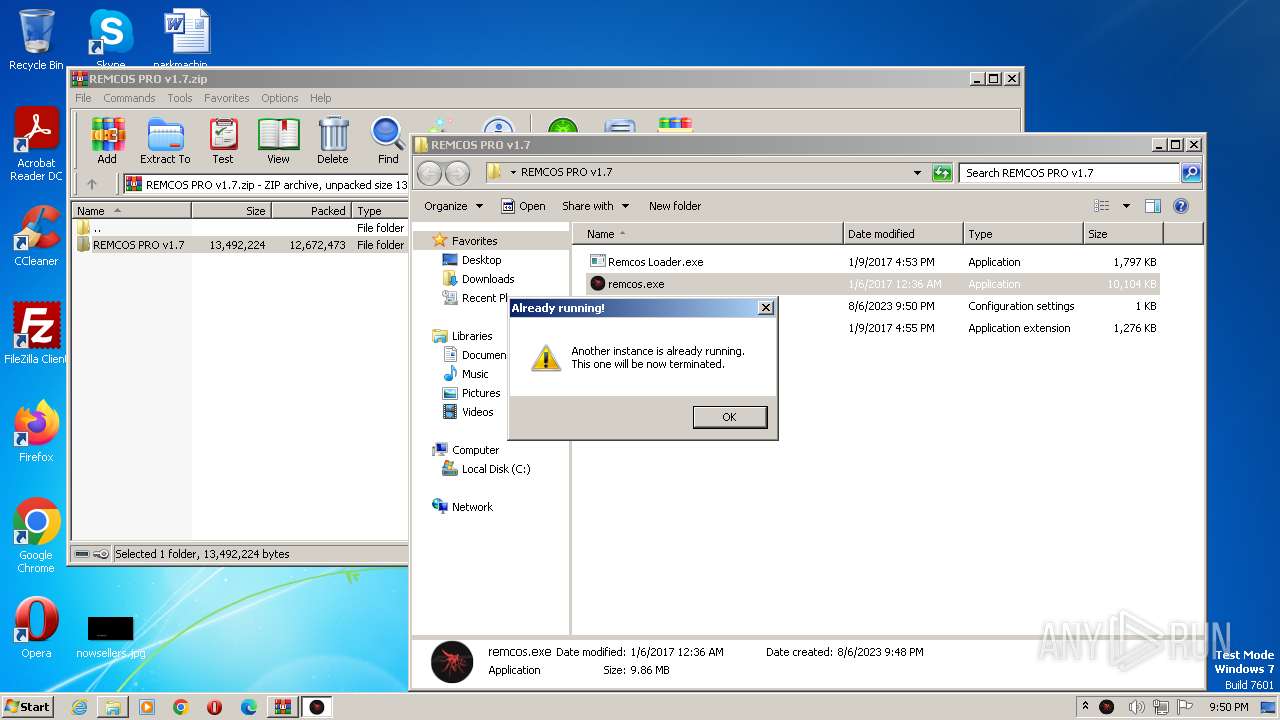
MALICIOUS
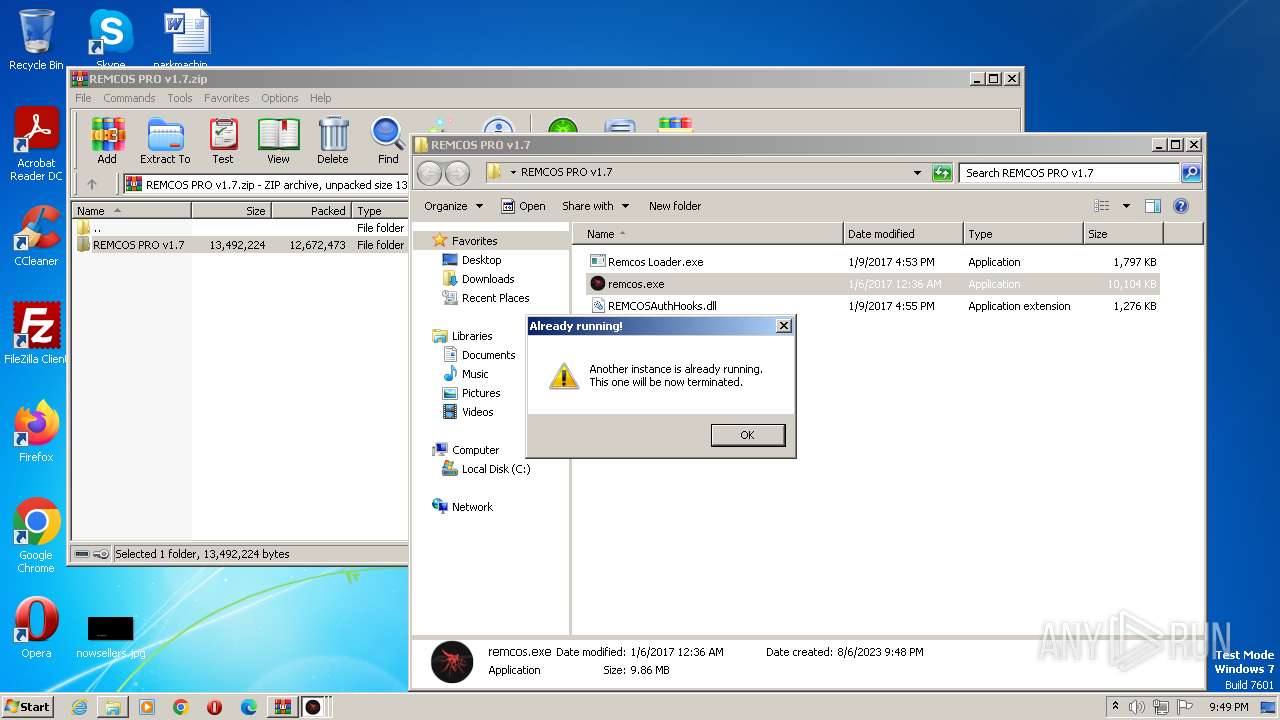
Application was dropped or rewritten from another process
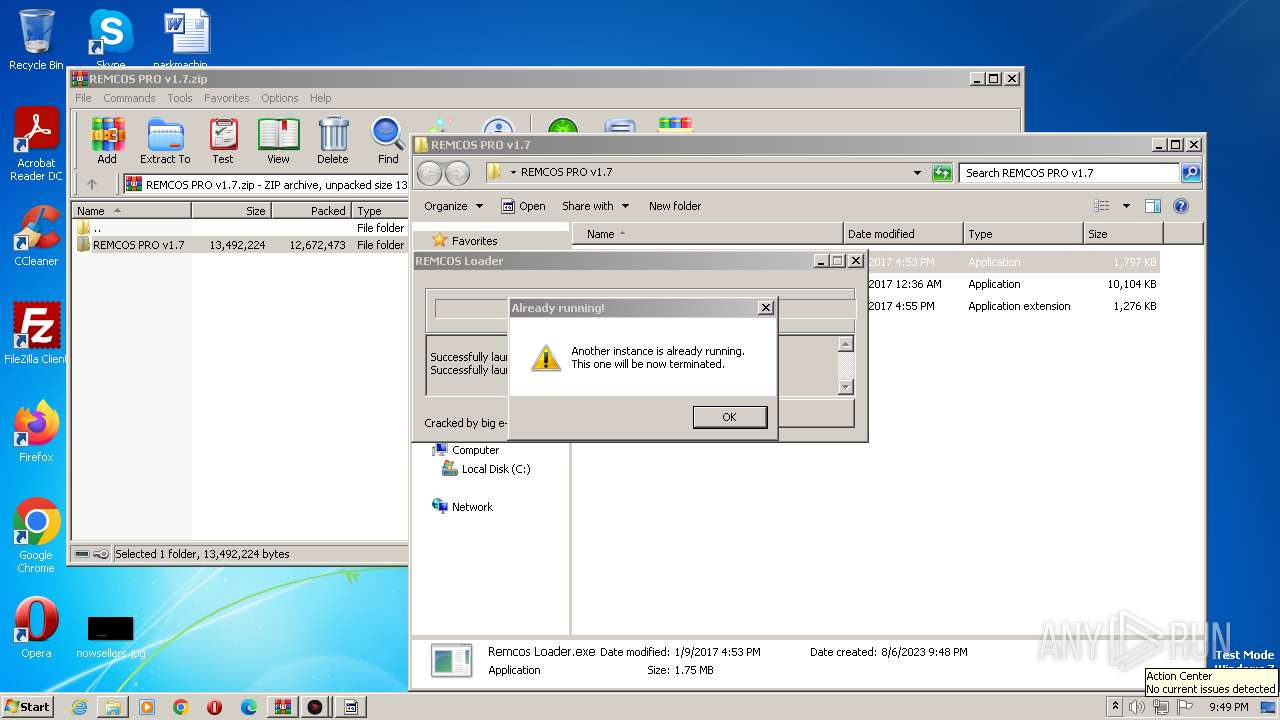
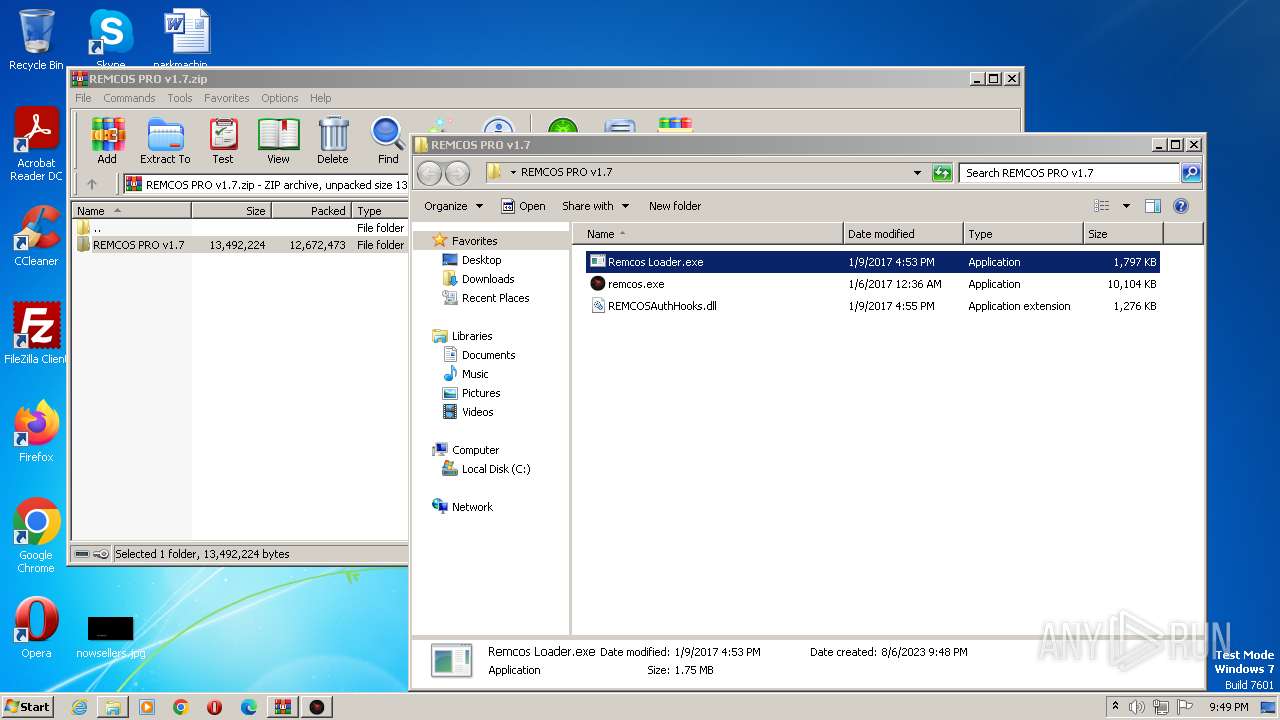
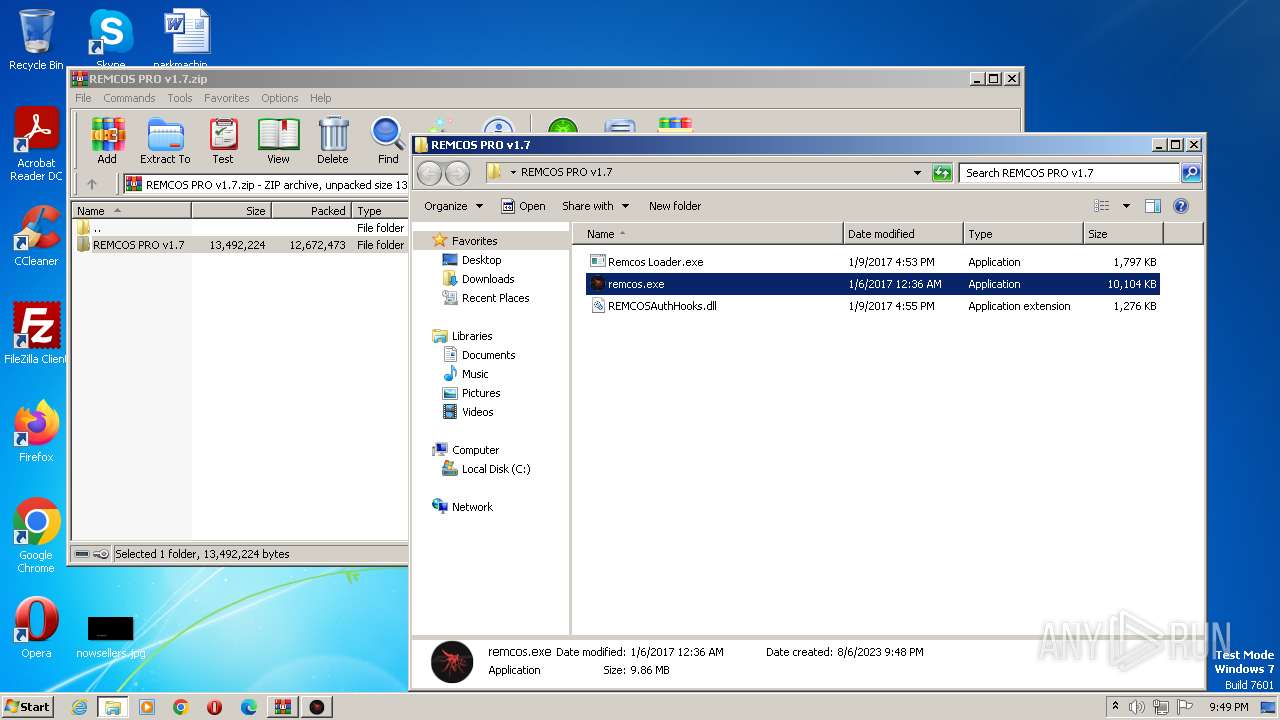
- remcos.exe (PID: 2032)
- Remcos Loader.exe (PID: 1688)
- remcos.exe (PID: 2728)
- remcos.exe (PID: 3548)
- remcos.exe (PID: 1896)
- remcos.exe (PID: 3424)
- remcos.exe (PID: 2452)
- Remcos Loader.exe (PID: 3992)
- remcos.exe (PID: 280)
- remcos.exe (PID: 3900)
- remcos.exe (PID: 2228)
- remcos.exe (PID: 1880)
- remcos.exe (PID: 3592)
- remcos.exe (PID: 3440)
- Remcos Loader.exe (PID: 3444)
- Remcos Loader.exe (PID: 1816)
- remcos.exe (PID: 1412)
Loads dropped or rewritten executable
- remcos.exe (PID: 2728)
- remcos.exe (PID: 1896)
- remcos.exe (PID: 2452)
- remcos.exe (PID: 2228)
- remcos.exe (PID: 1880)
- remcos.exe (PID: 3592)
- remcos.exe (PID: 280)
- remcos.exe (PID: 3900)
- remcos.exe (PID: 1412)
Runs injected code in another process
- remcos.exe (PID: 2728)
- remcos.exe (PID: 1896)
- remcos.exe (PID: 2452)
- remcos.exe (PID: 3592)
- remcos.exe (PID: 1880)
- remcos.exe (PID: 3900)
- remcos.exe (PID: 2228)
- remcos.exe (PID: 280)
- remcos.exe (PID: 1412)
REMCOS detected by memory dumps
- remcos.exe (PID: 2728)
- remcos.exe (PID: 2032)
- remcos.exe (PID: 1896)
- remcos.exe (PID: 2452)
- remcos.exe (PID: 3548)
- remcos.exe (PID: 280)
- remcos.exe (PID: 2228)
- remcos.exe (PID: 3440)
- remcos.exe (PID: 1412)
Application was injected by another process
- explorer.exe (PID: 1404)
SUSPICIOUS
Reads the Internet Settings
- remcos.exe (PID: 2452)
- remcos.exe (PID: 2032)
- remcos.exe (PID: 3592)
- remcos.exe (PID: 3440)
INFO
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3184)
- remcos.exe (PID: 2032)
- remcos.exe (PID: 3440)
Reads the computer name
- wmpnscfg.exe (PID: 3184)
- remcos.exe (PID: 2032)
- remcos.exe (PID: 2728)
- remcos.exe (PID: 1896)
- remcos.exe (PID: 3424)
- remcos.exe (PID: 3548)
- remcos.exe (PID: 2452)
- remcos.exe (PID: 3592)
- remcos.exe (PID: 1880)
- remcos.exe (PID: 2228)
- remcos.exe (PID: 280)
- remcos.exe (PID: 3900)
- remcos.exe (PID: 3440)
- remcos.exe (PID: 1412)
Checks supported languages
- remcos.exe (PID: 2032)
- Remcos Loader.exe (PID: 1688)
- wmpnscfg.exe (PID: 3184)
- remcos.exe (PID: 2728)
- remcos.exe (PID: 3548)
- remcos.exe (PID: 3424)
- remcos.exe (PID: 1896)
- Remcos Loader.exe (PID: 3992)
- remcos.exe (PID: 2452)
- remcos.exe (PID: 2228)
- remcos.exe (PID: 1880)
- remcos.exe (PID: 3592)
- remcos.exe (PID: 280)
- remcos.exe (PID: 3900)
- Remcos Loader.exe (PID: 3444)
- Remcos Loader.exe (PID: 1816)
- remcos.exe (PID: 3440)
- remcos.exe (PID: 1412)
The process checks LSA protection
- wmpnscfg.exe (PID: 3184)
- remcos.exe (PID: 2032)
- DeviceDisplayObjectProvider.exe (PID: 4056)
- DeviceDisplayObjectProvider.exe (PID: 3092)
- remcos.exe (PID: 3440)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3356)
Manual execution by a user
- remcos.exe (PID: 2032)
- Remcos Loader.exe (PID: 1688)
- remcos.exe (PID: 3548)
- remcos.exe (PID: 3424)
- Remcos Loader.exe (PID: 3992)
- Remcos Loader.exe (PID: 3444)
- Remcos Loader.exe (PID: 1816)
- remcos.exe (PID: 3440)
Checks proxy server information
- remcos.exe (PID: 2452)
- remcos.exe (PID: 2032)
- remcos.exe (PID: 3592)
- remcos.exe (PID: 3440)
Creates files or folders in the user directory
- remcos.exe (PID: 2032)
- DeviceDisplayObjectProvider.exe (PID: 4056)
- DeviceDisplayObjectProvider.exe (PID: 3092)
- remcos.exe (PID: 3440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | REMCOS PRO v1.7/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2023:07:30 01:32:50 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
65
Monitored processes
23
Malicious processes
18
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
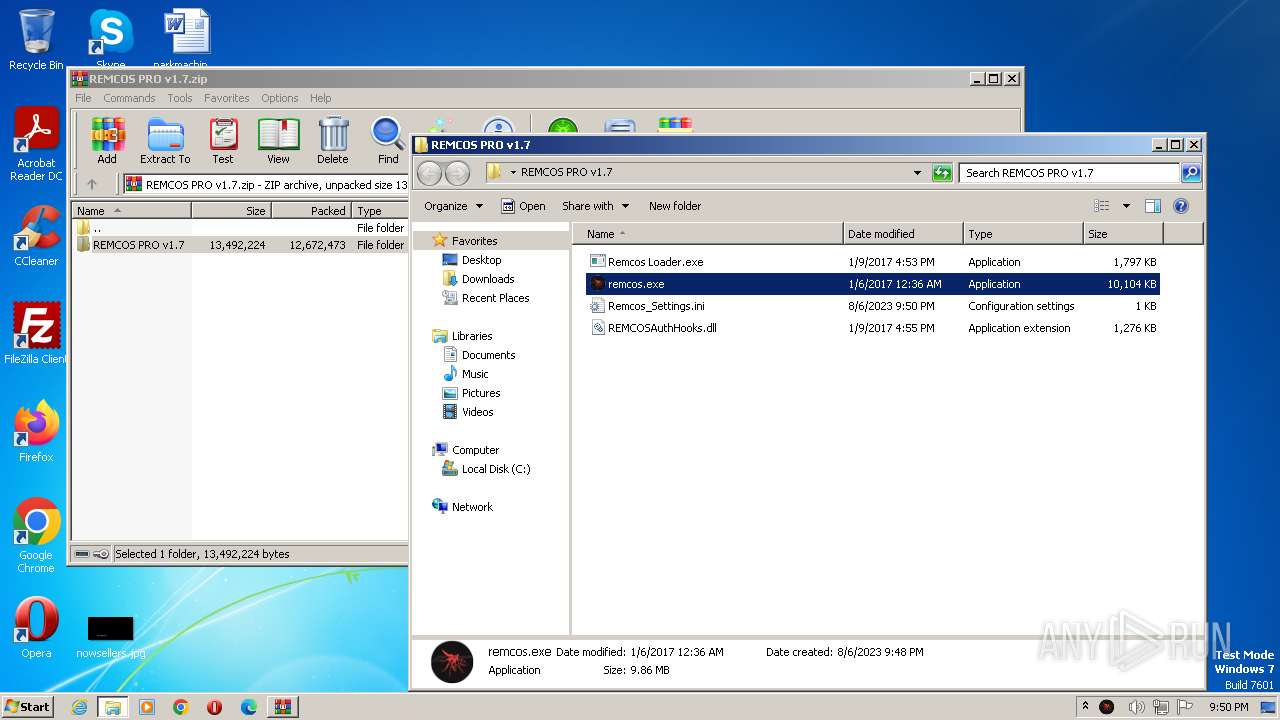
| 280 | "C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe" | C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe | Remcos Loader.exe | ||||||||||||
User: admin Company: Breaking-Security.net Integrity Level: MEDIUM Description: REMCOS Remote Control & Surveillance Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 1404 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1412 | "C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe" | C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe | Remcos Loader.exe | ||||||||||||
User: admin Company: Breaking-Security.net Integrity Level: MEDIUM Description: REMCOS Remote Control & Surveillance Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 1688 | "C:\Users\admin\Desktop\REMCOS PRO v1.7\Remcos Loader.exe" | C:\Users\admin\Desktop\REMCOS PRO v1.7\Remcos Loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1816 | "C:\Users\admin\Desktop\REMCOS PRO v1.7\Remcos Loader.exe" | C:\Users\admin\Desktop\REMCOS PRO v1.7\Remcos Loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1880 | "C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe" | C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe | — | Remcos Loader.exe | |||||||||||
User: admin Company: Breaking-Security.net Integrity Level: MEDIUM Description: REMCOS Remote Control & Surveillance Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 1896 | "C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe" | C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe | Remcos Loader.exe | ||||||||||||
User: admin Company: Breaking-Security.net Integrity Level: MEDIUM Description: REMCOS Remote Control & Surveillance Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 2032 | "C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe" | C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe | explorer.exe | ||||||||||||
User: admin Company: Breaking-Security.net Integrity Level: MEDIUM Description: REMCOS Remote Control & Surveillance Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 2228 | "C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe" | C:\Users\admin\Desktop\REMCOS PRO v1.7\remcos.exe | Remcos Loader.exe | ||||||||||||
User: admin Company: Breaking-Security.net Integrity Level: MEDIUM Description: REMCOS Remote Control & Surveillance Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 2276 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
9 007
Read events
8 753
Write events
250
Delete events
4
Modification events
| (PID) Process: | (1404) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3184) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{9152F4E6-D55D-4295-8ACE-2686B2DBB2BC}\{266B0E72-096F-40B5-8FF6-F2205AF5CFF3} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3184) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{9152F4E6-D55D-4295-8ACE-2686B2DBB2BC} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3184) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{6AF3C5A1-DF1E-4D81-B19B-32DEC9A0837E} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1404) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000F6D6788197A75D498472ACE88906AC8D000000000200000000001066000000010000200000009E878810DB7ADAA62BFF5B2995C9135391587830D7B78763BAF891A8E326C1D2000000000E8000000002000020000000708BCEE11BAED4DDD5A3536C5255C2A3EF209C73E80BF0C5975934919F66066C3000000061005E5889DC4149BCED257BF4BA4C21CB59685E22EC16EF02A95B0CEABEBA93FBB032CCA687E18A4BDEBA6F726F319C40000000F064E3528192B7C6D193DF6C50758DA37C0621234E8F51940EC6686BA8A09CA3B94552BD897D898E633AF8A1B24303E938BA186E293CEDBB46D515585CB43CE0 | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1404) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
Executable files
3
Suspicious files
8
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2032 | remcos.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\gettime[1].htm | html | |
MD5:8B6C8BDE52726F7A1E9C0CFB33DFB25C | SHA256:F103C4551AE05A56752D76DD565B8A5B2B309095DD9CF0668DEC8DC65D3C3D02 | |||
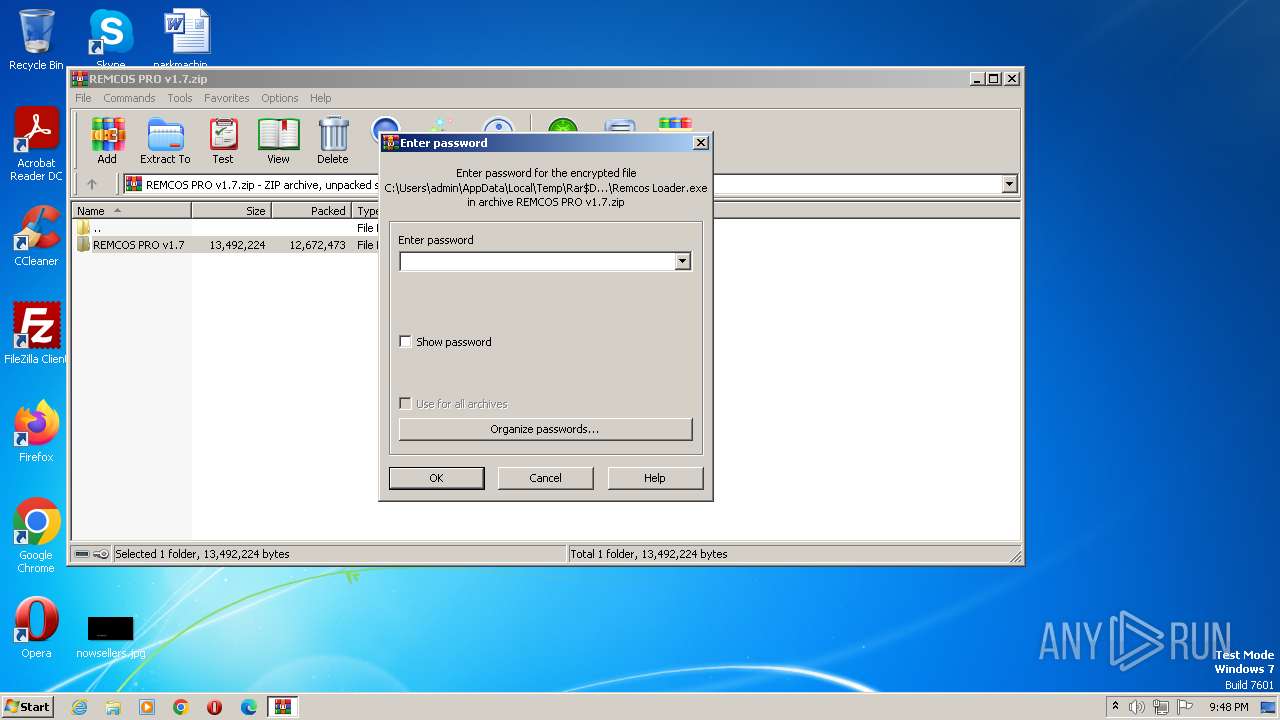
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3356.40685\REMCOS PRO v1.7\Remcos Loader.exe | executable | |
MD5:75792B5B38EDD028D13EEF62C0D828E6 | SHA256:B7F82678830C34DB745A16D5551386F15FF28FDA563F10C6903F6471A58E243E | |||
| 4056 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Microsoft\Device Metadata\dmrc.idx | binary | |
MD5:E57CAAC56ED179DDD7131EDE8B5FEBD6 | SHA256:07B55C0174554303E9C27F2A183EE4167826A61CC667625E871AC0743D04FAF5 | |||
| 2032 | remcos.exe | C:\Users\admin\Desktop\REMCOS PRO v1.7\Remcos_Settings.ini | text | |
MD5:902927C48D191E30067D84A53158E2BA | SHA256:B408602C7D2107D819B18D47CBC196A307AB6435BBC819173F300E76573E616C | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3356.40685\REMCOS PRO v1.7\remcos.exe | executable | |
MD5:ED1E424EA6F625968A334377E8AC629F | SHA256:1E5375B400F68C422804703390489B2CF3968C2A8BCCB0B5B3C55FE1D2E3C991 | |||
| 4056 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Microsoft\Device Metadata\dmrc.idx.2 | binary | |
MD5:E57CAAC56ED179DDD7131EDE8B5FEBD6 | SHA256:07B55C0174554303E9C27F2A183EE4167826A61CC667625E871AC0743D04FAF5 | |||
| 2032 | remcos.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\OnlineCheck_MT[1].htm | html | |
MD5:490F5FCA1618088A11B09F026FAFFD49 | SHA256:CC44CCDB5B245F170DB899B133B151D484077F8BB9F67698141C6722830F58AC | |||
| 3092 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Microsoft\Device Metadata\dmrc.idx.2 | binary | |
MD5:E57CAAC56ED179DDD7131EDE8B5FEBD6 | SHA256:07B55C0174554303E9C27F2A183EE4167826A61CC667625E871AC0743D04FAF5 | |||
| 3092 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Microsoft\Device Metadata\dmrc.idx | binary | |
MD5:E57CAAC56ED179DDD7131EDE8B5FEBD6 | SHA256:07B55C0174554303E9C27F2A183EE4167826A61CC667625E871AC0743D04FAF5 | |||
| 3440 | remcos.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\OnlineCheck_MT[1].htm | html | |
MD5:F51CCFB39F0758B9A21FBB2C35280187 | SHA256:516FE777618FB197DCB3A450221DBFE368E9FAE4C099261EEF4C77E75634515A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3440 | remcos.exe | GET | 200 | 185.53.178.52:80 | http://breakingsec01.co.nf/REMCOS/OnlineCheck_MT.php?LIC=B48612E8E5DA6C12EBC97A0B8168E577906CAB508A4A722EEBEE5215F0A524B6 | DE | html | 15.6 Kb | malicious |
2032 | remcos.exe | GET | 200 | 185.53.178.52:80 | http://breakingsec01.co.nf/REMCOS/gettime.php | DE | html | 15.5 Kb | malicious |
2032 | remcos.exe | GET | 200 | 185.53.178.52:80 | http://breakingsec01.co.nf/REMCOS/OnlineCheck_MT.php?LIC=BE8A18ECDFCE6A1AD1994C078358D3AE9385C28085479B49919E16DBF68C2CB4 | DE | html | 15.6 Kb | malicious |
3440 | remcos.exe | GET | 200 | 185.53.178.52:80 | http://breakingsec01.co.nf/REMCOS/gettime.php | DE | html | 15.6 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2032 | remcos.exe | 185.53.178.52:80 | breakingsec01.co.nf | Team Internet AG | DE | malicious |
2452 | remcos.exe | 142.250.186.68:80 | www.google.com | GOOGLE | US | whitelisted |
3592 | remcos.exe | 142.250.186.68:80 | www.google.com | GOOGLE | US | whitelisted |
3440 | remcos.exe | 185.53.178.52:80 | breakingsec01.co.nf | Team Internet AG | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
breakingsec01.co.nf |
| unknown |
www.google.com |
| malicious |
dns.msftncsi.com |
| shared |