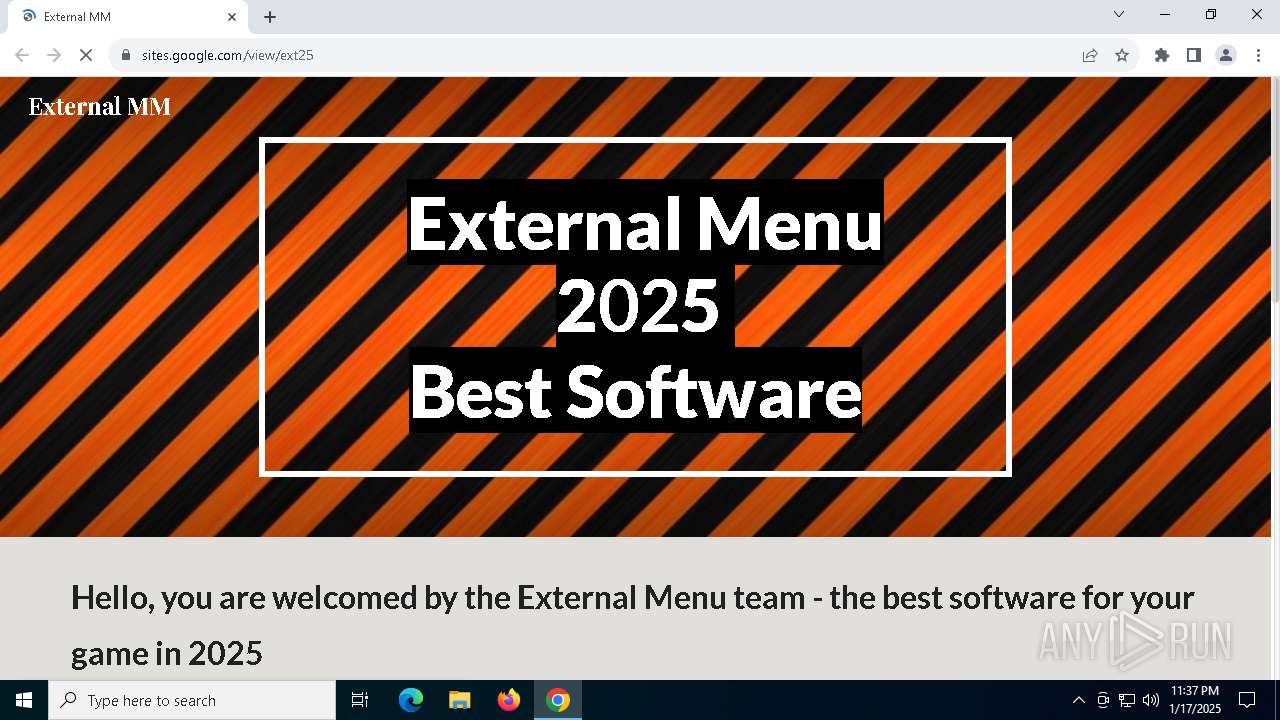
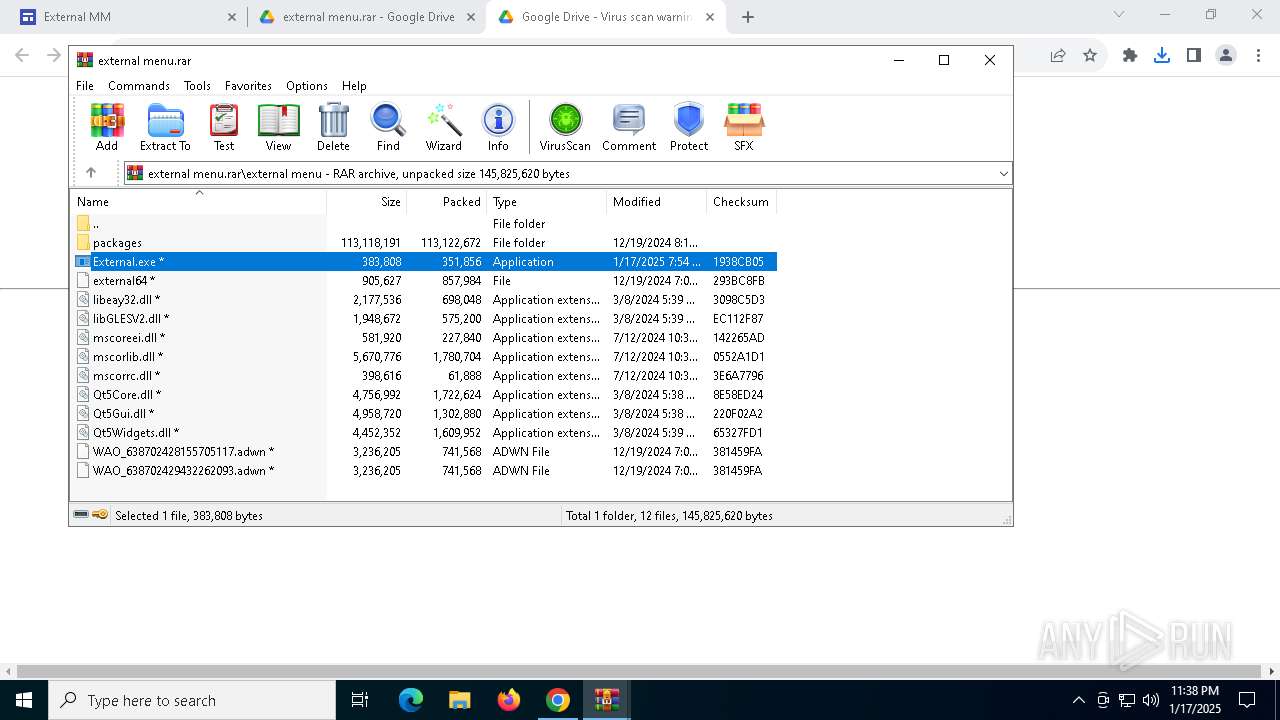
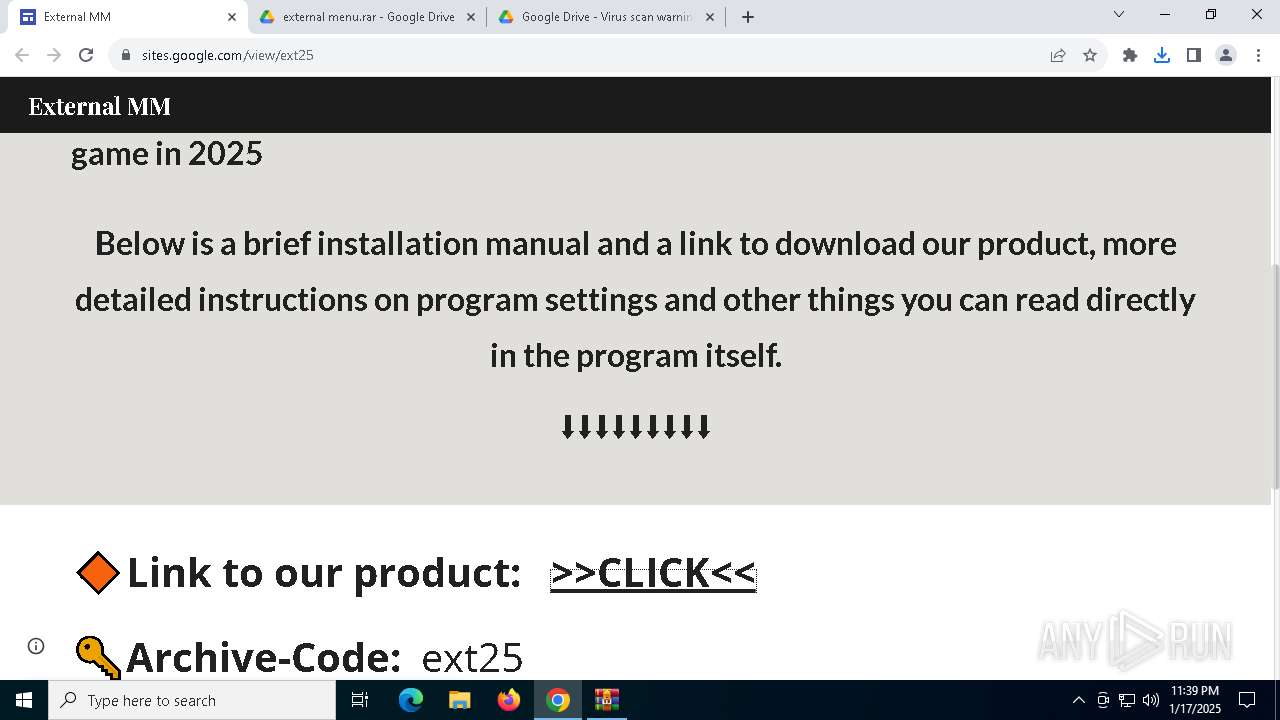
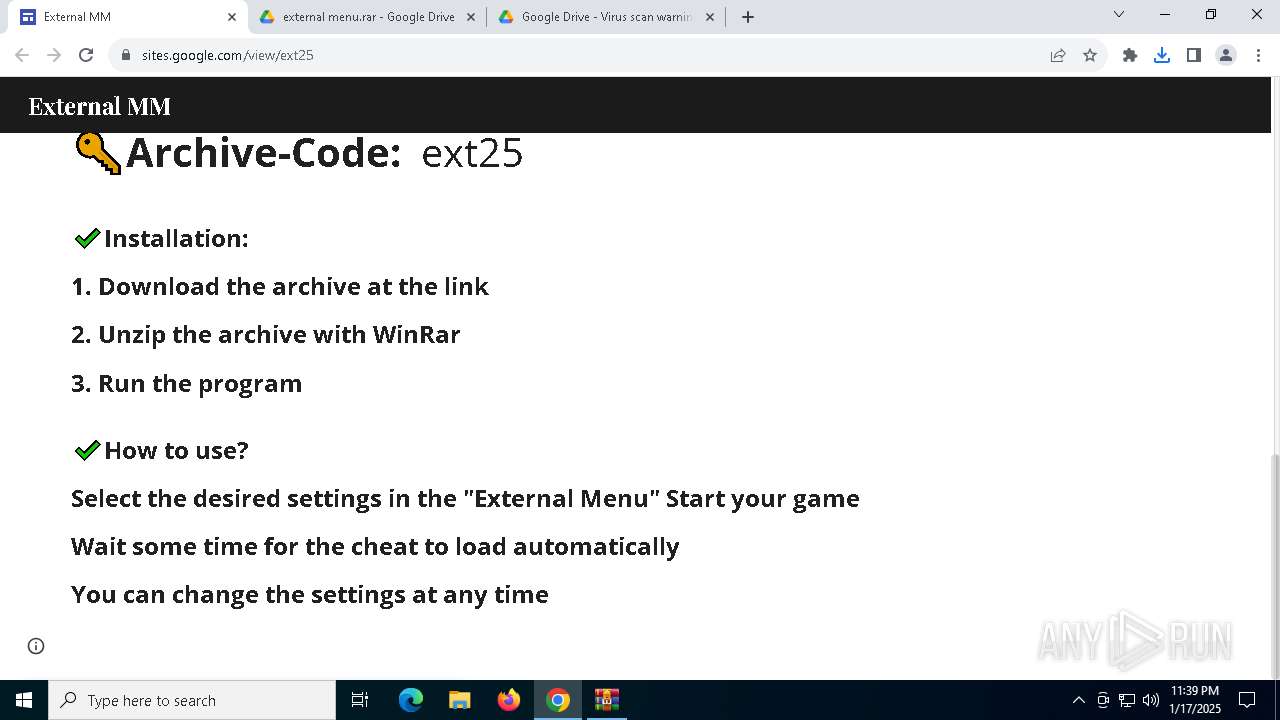
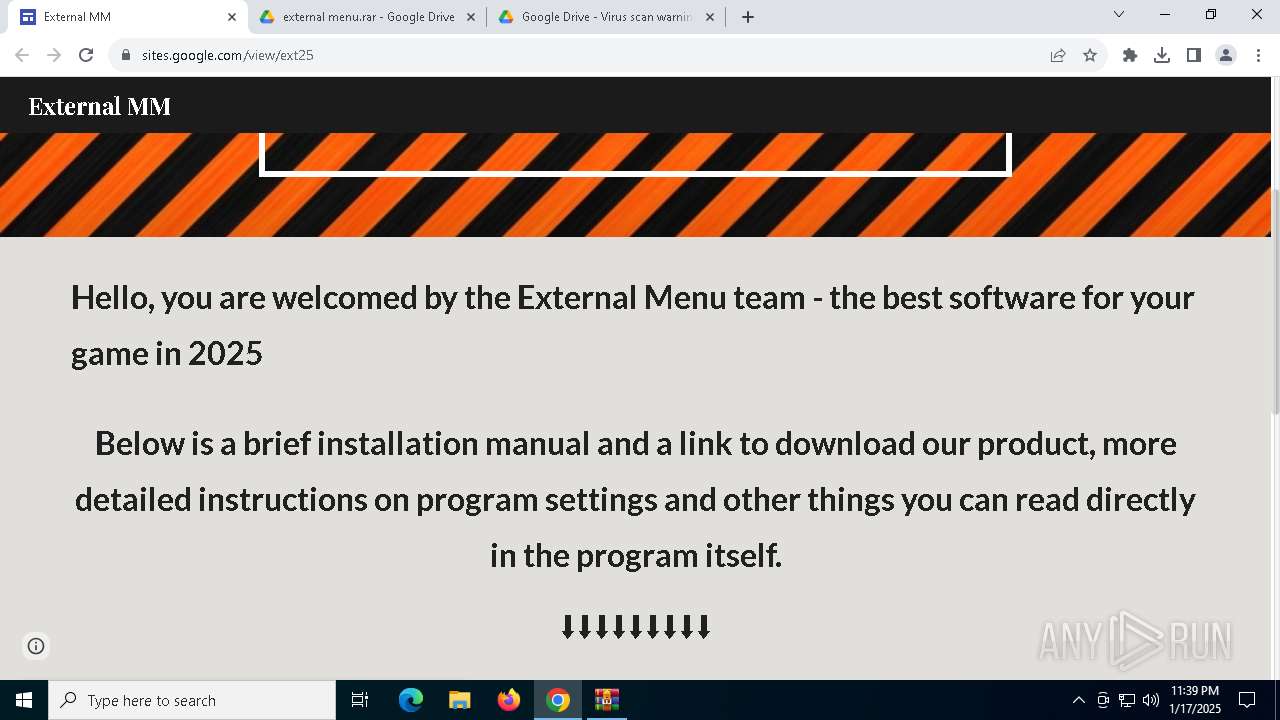
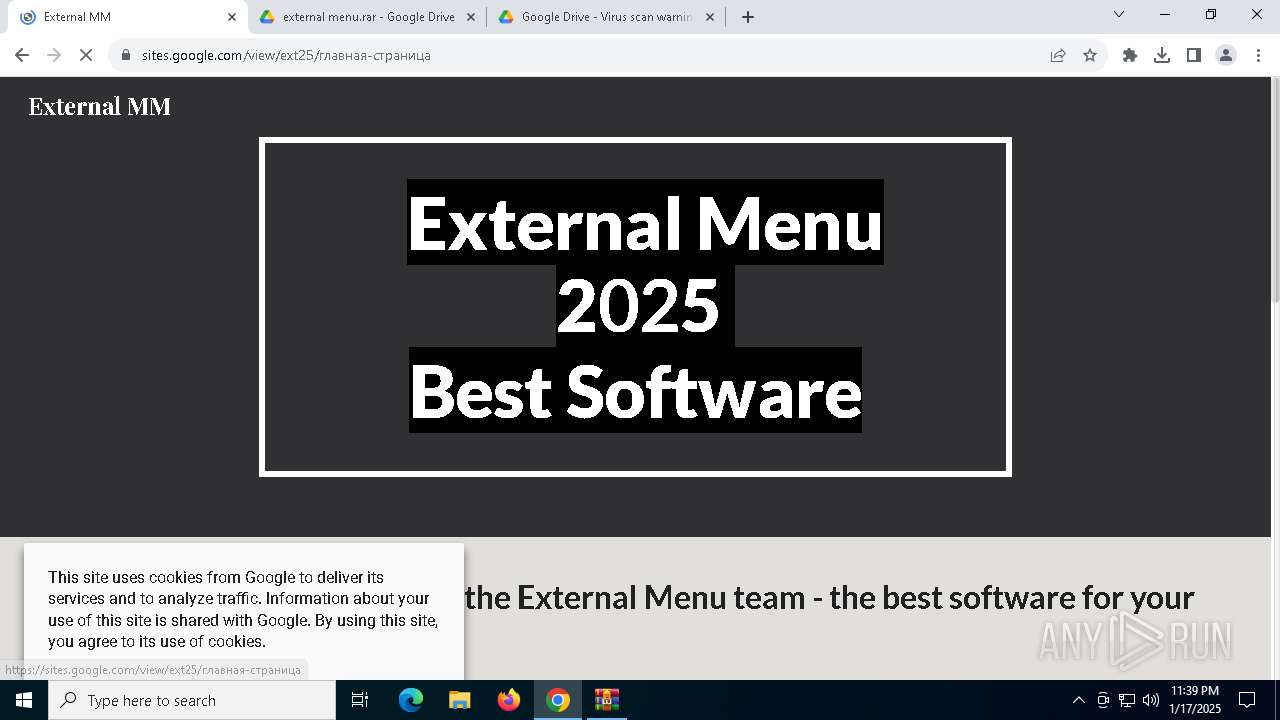
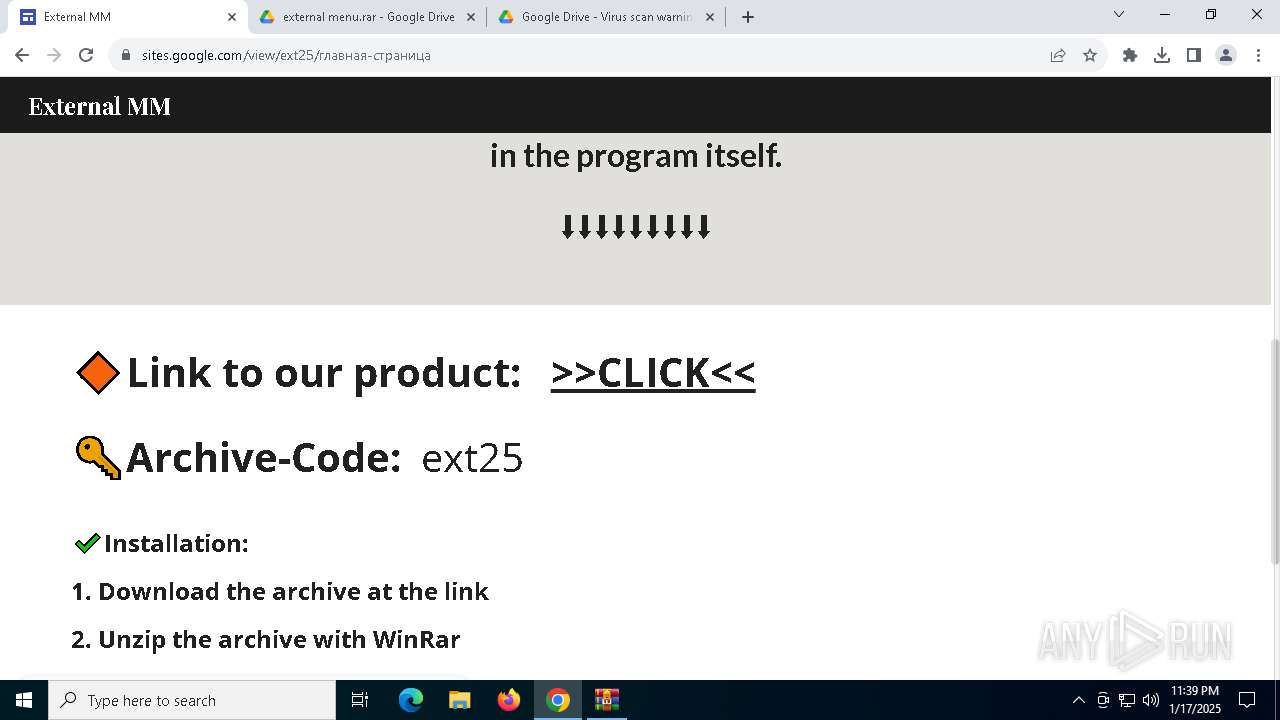
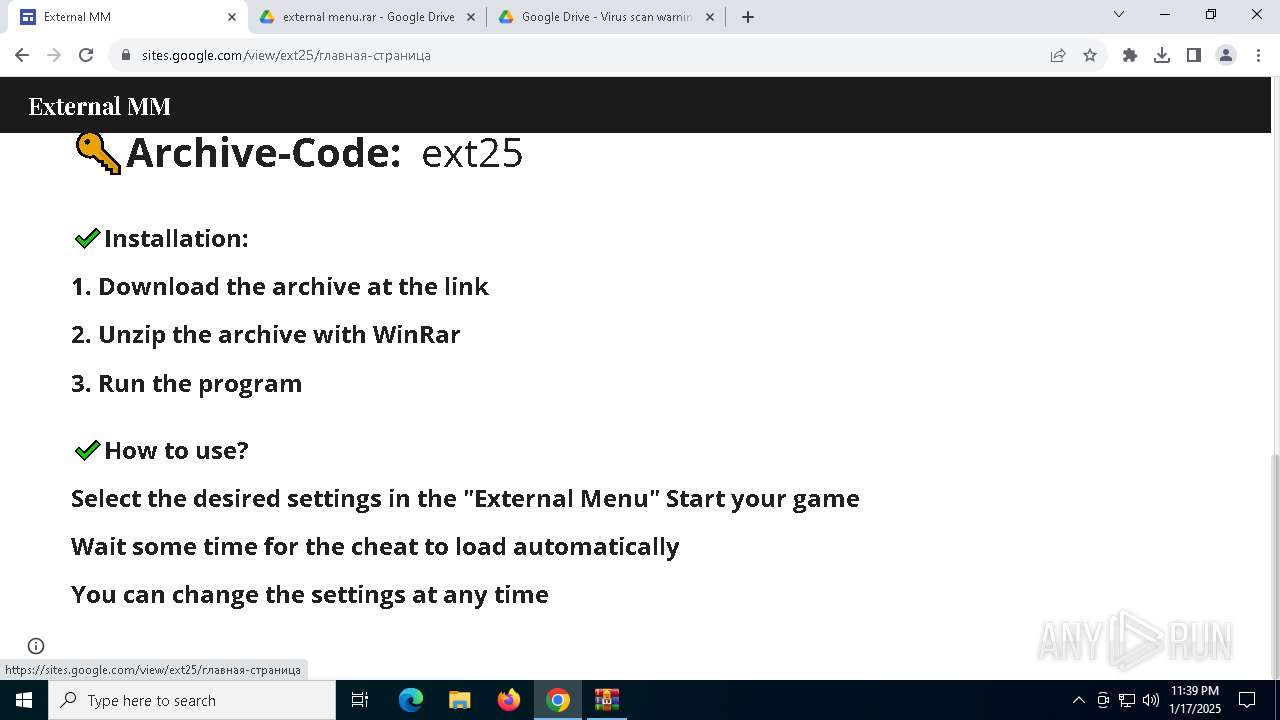
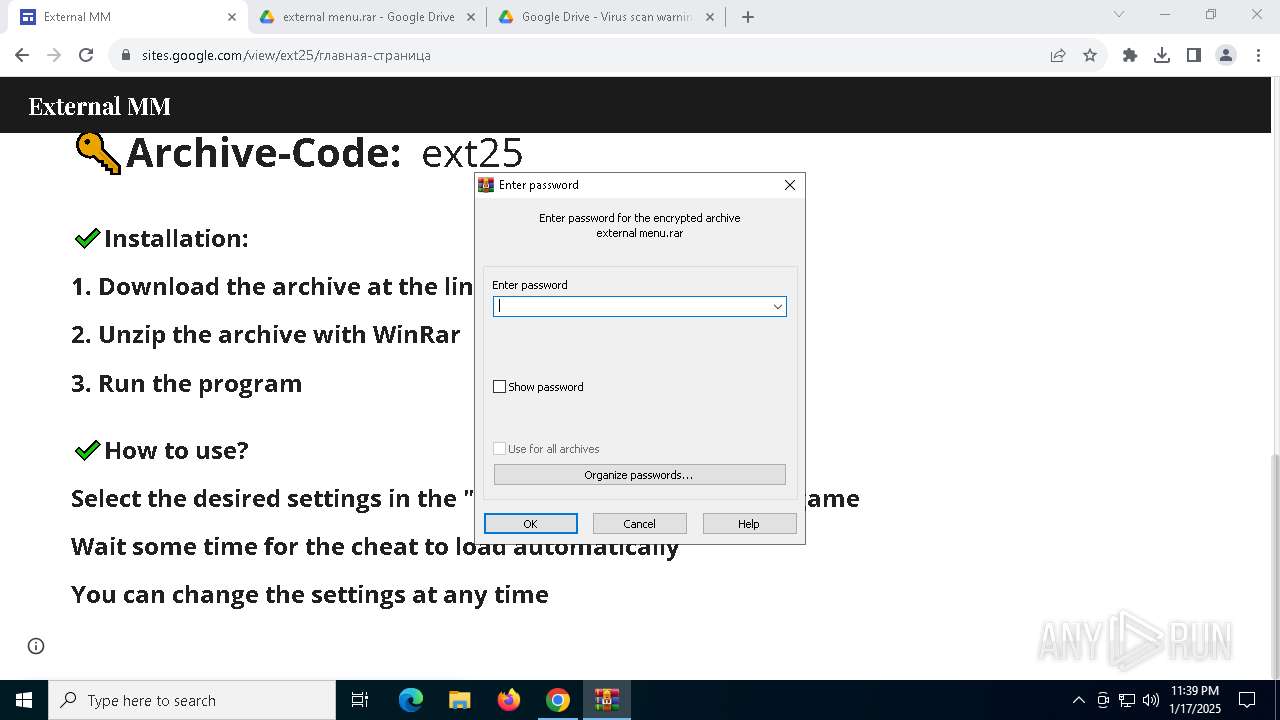
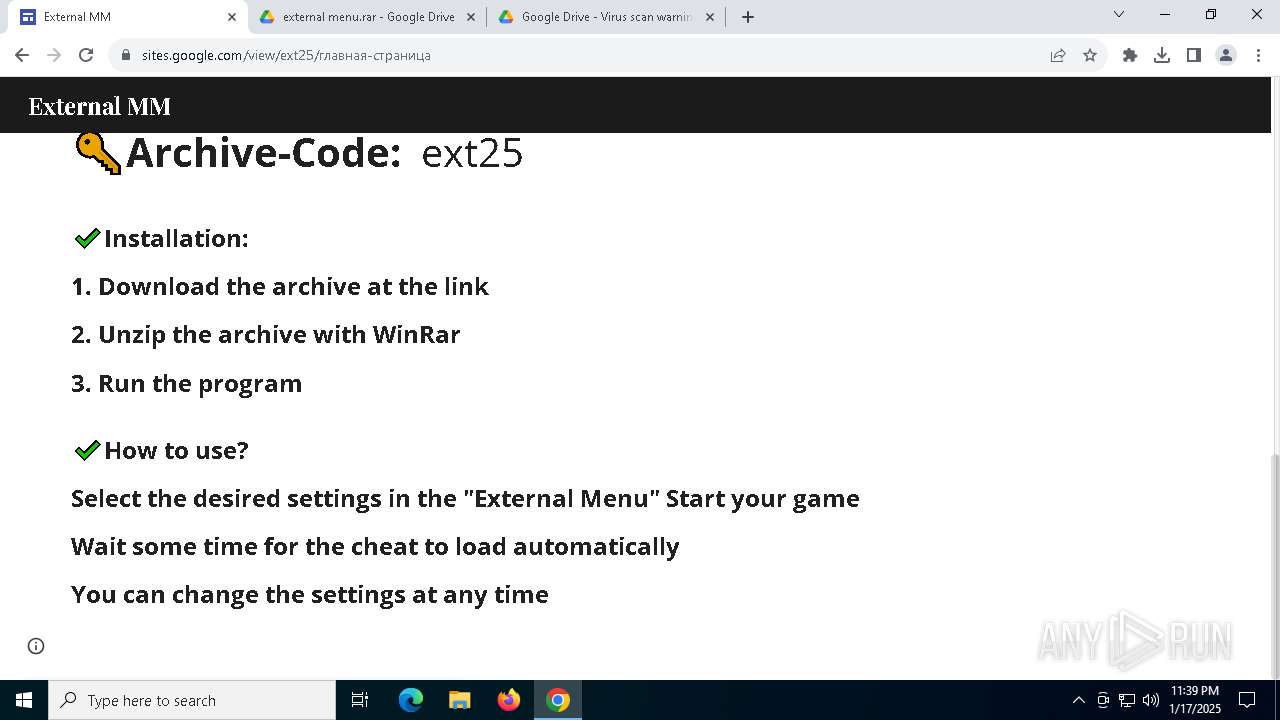
| URL: | https://sites.google.com/view/ext25 |
| Full analysis: | https://app.any.run/tasks/ffcc2b22-9fc2-4a7e-9070-dff8f32ea2e8 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 17, 2025, 23:37:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9AD331FAD3E61CC2CA0EE9A7F154D477 |
| SHA1: | 2FC0D3E9ED7CE2EEA6B80CC2D3A900B8A5D9E94A |
| SHA256: | F10133FDCA36BBB5E6ED59E0139598BF2B39D33C7C8E196CDAD0F002E01AF47E |
| SSDEEP: | 3:N8BhLJ3u1iQ:2J+J |
MALICIOUS
Executing a file with an untrusted certificate
- External.exe (PID: 3632)
- External.exe (PID: 1536)
- External.exe (PID: 2084)
- External.exe (PID: 3920)
Connects to the CnC server
- chrome.exe (PID: 6616)
LUMMA has been detected (SURICATA)
- chrome.exe (PID: 6616)
- External.exe (PID: 1536)
- External.exe (PID: 3920)
LUMMA mutex has been found
- External.exe (PID: 1536)
- External.exe (PID: 3920)
Steals credentials from Web Browsers
- External.exe (PID: 1536)
Actions looks like stealing of personal data
- External.exe (PID: 1536)
- External.exe (PID: 3920)
LUMMA has been detected (YARA)
- External.exe (PID: 1536)
- External.exe (PID: 3920)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6016)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6016)
Application launched itself
- External.exe (PID: 3632)
- External.exe (PID: 2084)
Executes application which crashes
- External.exe (PID: 3632)
- External.exe (PID: 2084)
Contacting a server suspected of hosting an CnC
- External.exe (PID: 1536)
- chrome.exe (PID: 6616)
- External.exe (PID: 3920)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6016)
There is functionality for taking screenshot (YARA)
- External.exe (PID: 1536)
- External.exe (PID: 3920)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6016)
INFO
The process uses the downloaded file
- chrome.exe (PID: 132)
- chrome.exe (PID: 6376)
- WinRAR.exe (PID: 6016)
- WinRAR.exe (PID: 876)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6376)
- OpenWith.exe (PID: 6800)
The sample compiled with english language support
- WinRAR.exe (PID: 6016)
Checks supported languages
- External.exe (PID: 3632)
- External.exe (PID: 1536)
- External.exe (PID: 3920)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6016)
Reads the software policy settings
- External.exe (PID: 1536)
- WerFault.exe (PID: 4932)
Application launched itself
- chrome.exe (PID: 6376)
Checks proxy server information
- WerFault.exe (PID: 4932)
Creates files or folders in the user directory
- WerFault.exe (PID: 4932)
- WerFault.exe (PID: 2356)
Create files in a temporary directory
- MpCmdRun.exe (PID: 6956)
.NET Reactor protector has been detected
- External.exe (PID: 1536)
- External.exe (PID: 3920)
Manual execution by a user
- WinRAR.exe (PID: 876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
166
Monitored processes
31
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5356 --field-trial-handle=1920,i,4988997467199841886,18156149130627161491,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
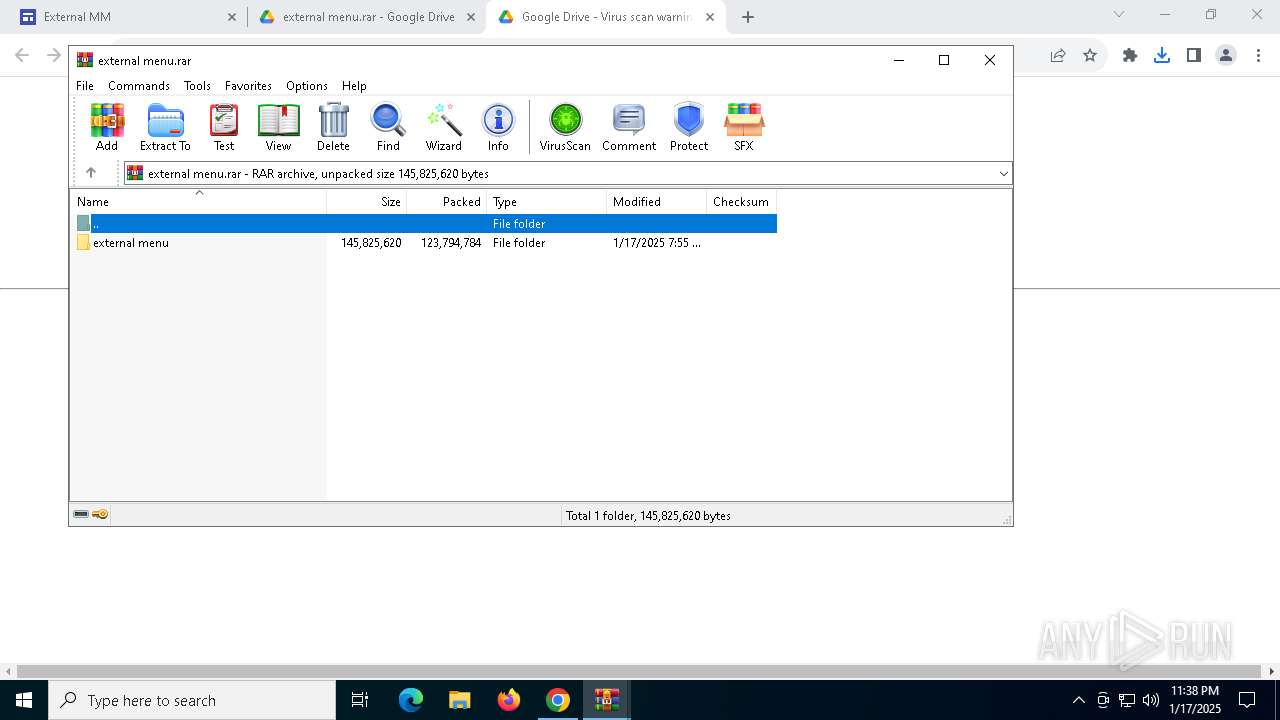
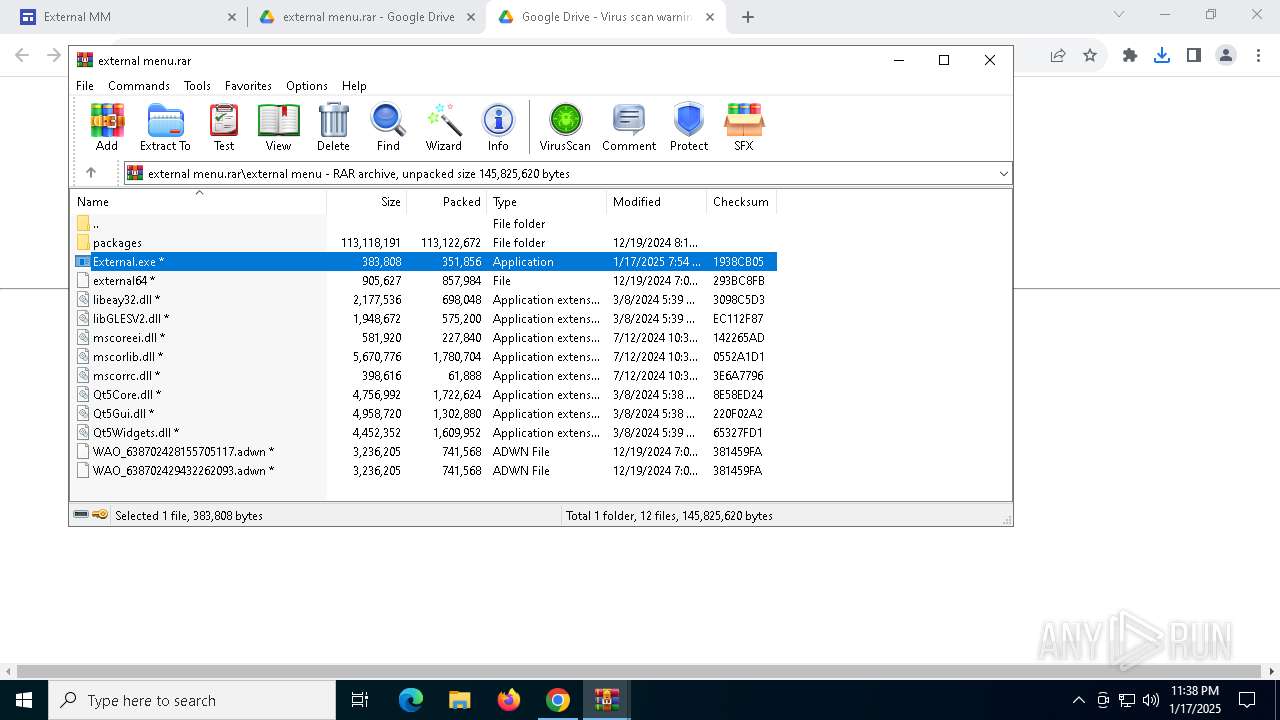
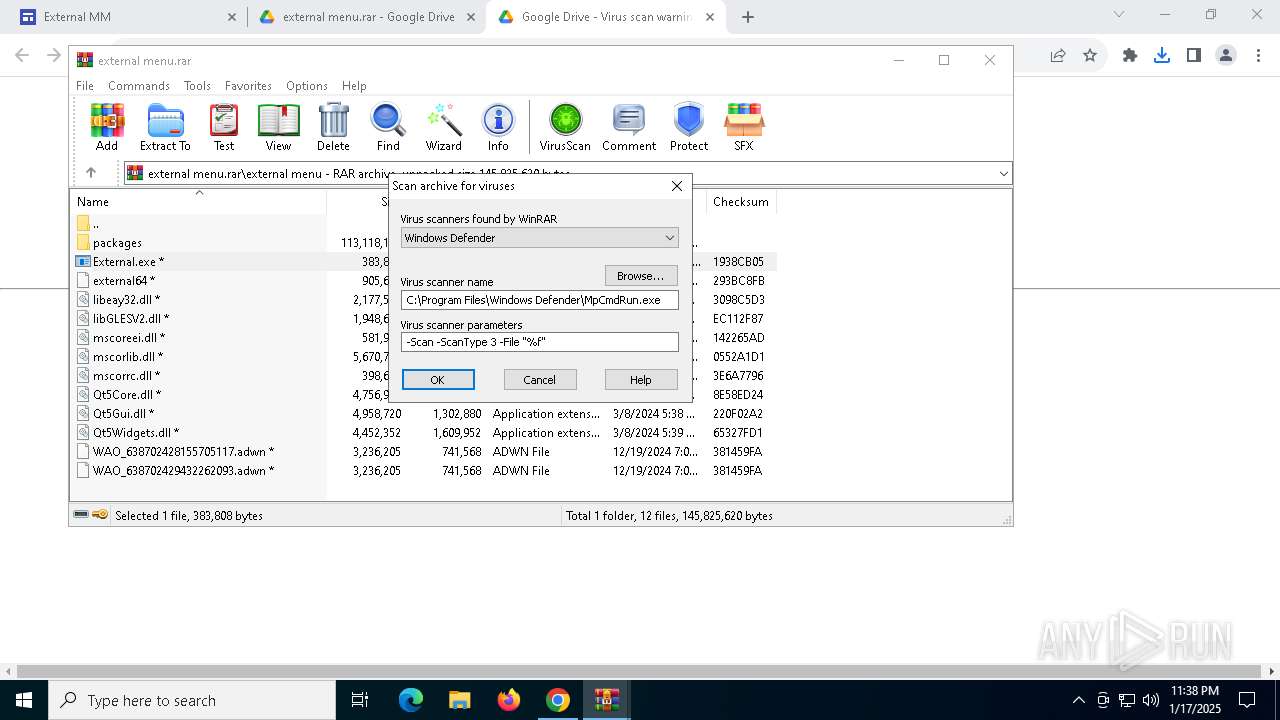
| 876 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\external menu.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=6016 --field-trial-handle=1920,i,4988997467199841886,18156149130627161491,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
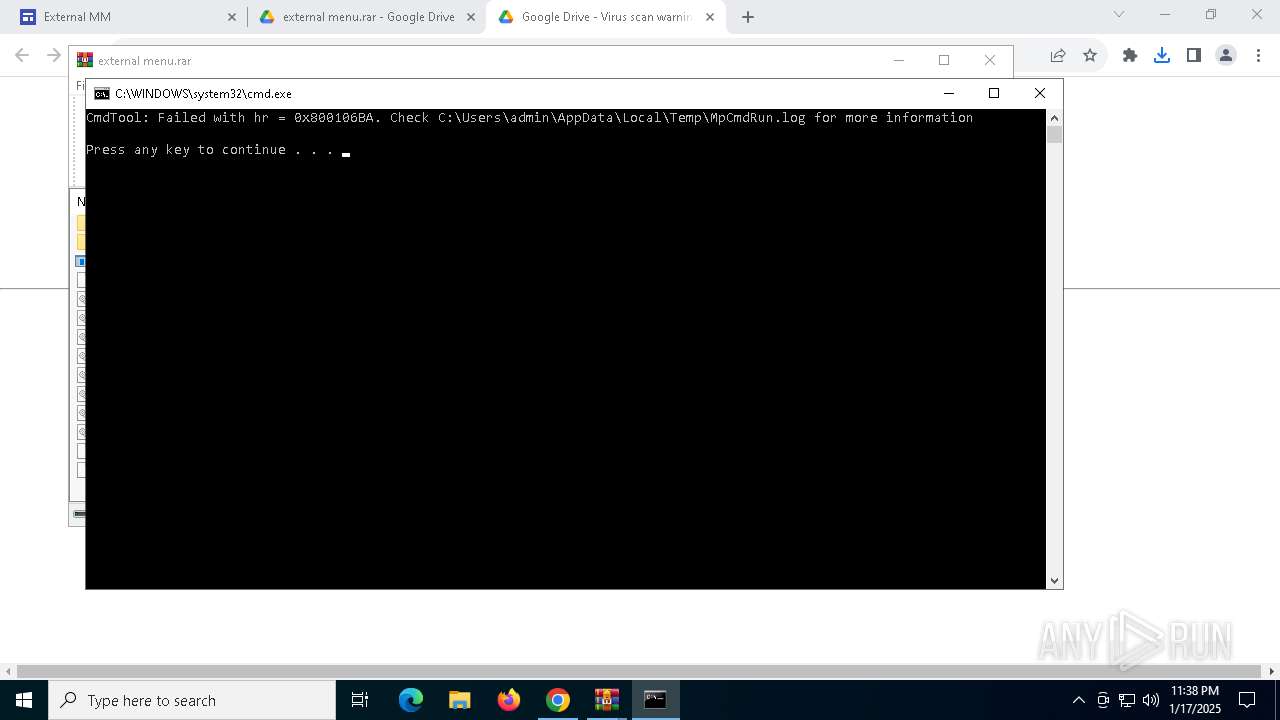
| 1216 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6016.43436\Rar$Scan36647.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
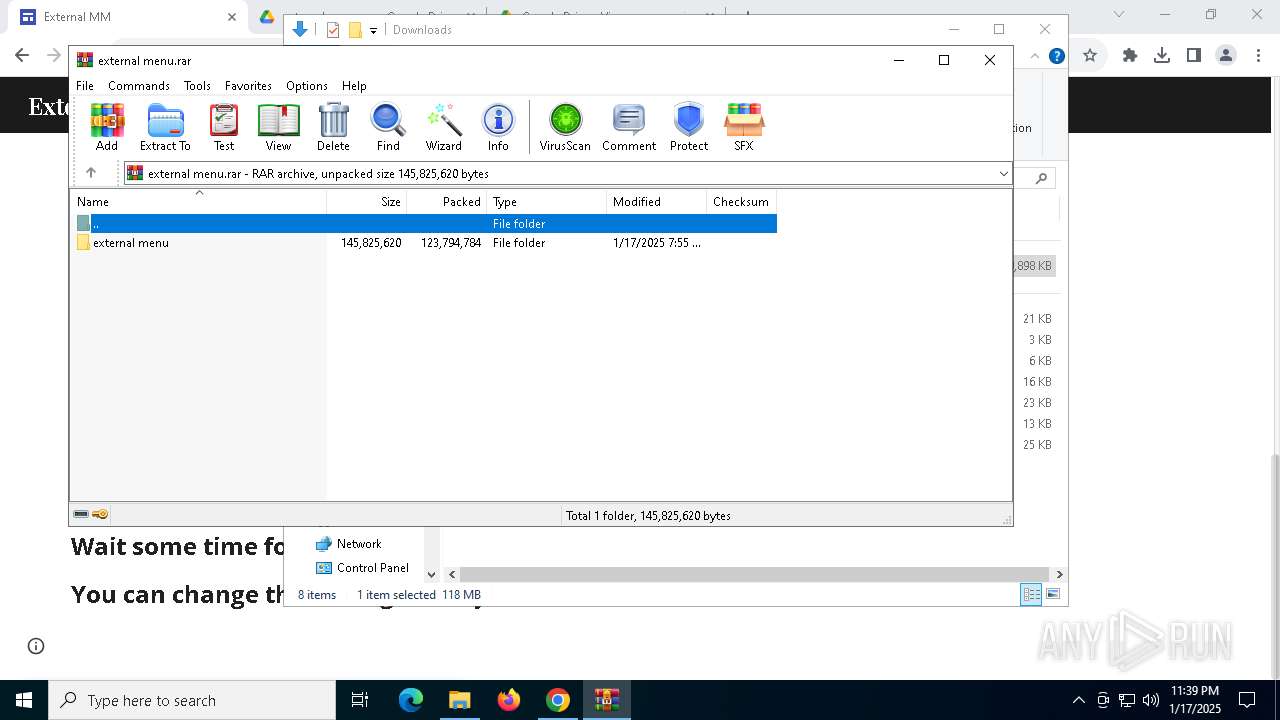
| 1536 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6016.42033\external menu\External.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6016.42033\external menu\External.exe | External.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6016.44358\external menu\External.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6016.44358\external menu\External.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226505 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=3860 --field-trial-handle=1920,i,4988997467199841886,18156149130627161491,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=1252 --field-trial-handle=1920,i,4988997467199841886,18156149130627161491,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5292 --field-trial-handle=1920,i,4988997467199841886,18156149130627161491,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2356 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2084 -s 836 | C:\Windows\SysWOW64\WerFault.exe | External.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 273
Read events
19 218
Write events
49
Delete events
6
Modification events
| (PID) Process: | (132) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000007E3079DD3869DB01 | |||
| (PID) Process: | (6376) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithProgids |
| Operation: | write | Name: | WinRAR |
Value: | |||
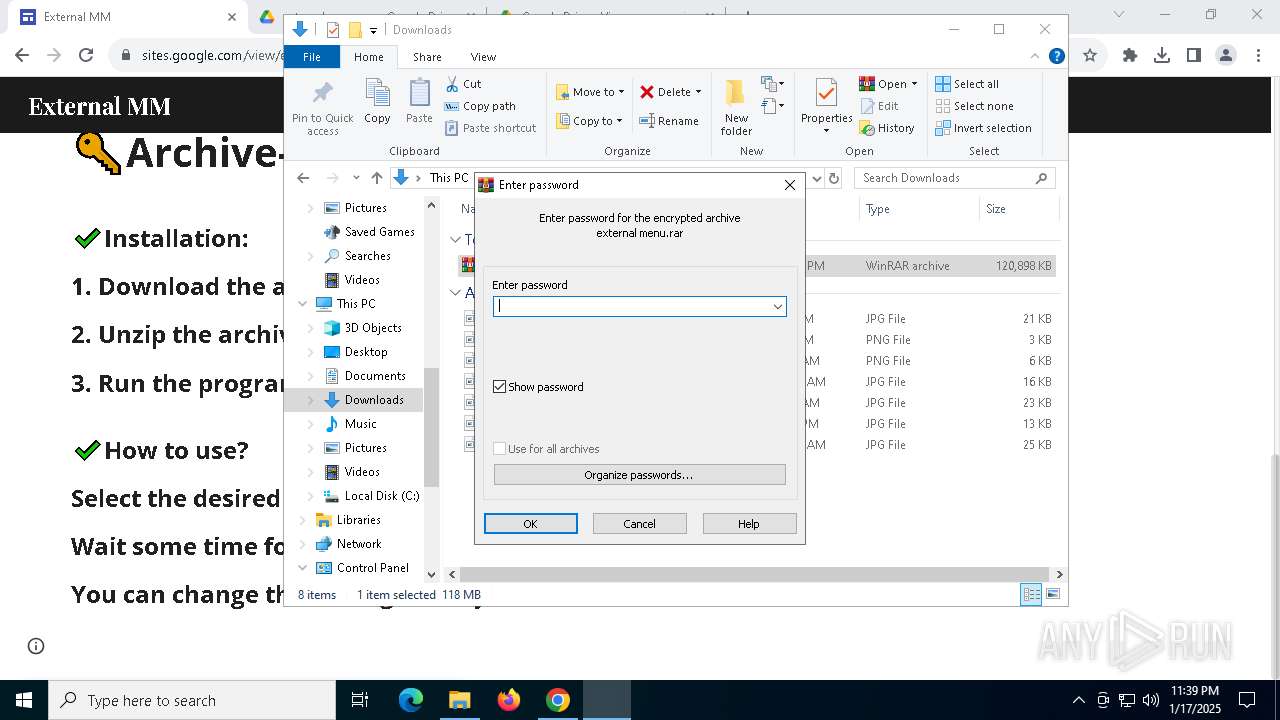
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\external menu.rar | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
30
Suspicious files
110
Text files
36
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1367b6.TMP | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF1367b6.TMP | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF1367b6.TMP | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1367c6.TMP | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1367c6.TMP | — | |
MD5:— | SHA256:— | |||
| 6376 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1367c6.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
106
DNS requests
101
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5752 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
5752 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/mvcjpd6vi4yx5whra47mpiws44_2025.1.15.1/jflhchccmppkfebkiaminageehmchikm_2025.01.15.01_all_acjwzxuclpxy2ofwrm7p6zfuof5q.crx3 | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7112 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7112 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5752 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/b5yy2kgkjogckxjqjmfsbp3mb4_1194/efniojlnjndmcbiieegkicadnoecjjef_1194_all_acn3s6x6jqixlit4cgflz4qgh6ta.crx3 | unknown | — | — | whitelisted |
6172 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 2.21.65.154:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
sites.google.com |
| whitelisted |
accounts.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6616 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (cultureddirtys .click) |
1536 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |
1536 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |
1536 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |
1536 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |
1536 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |
1536 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |
3920 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |
3920 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |
3920 | External.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cultureddirtys .click in TLS SNI) |