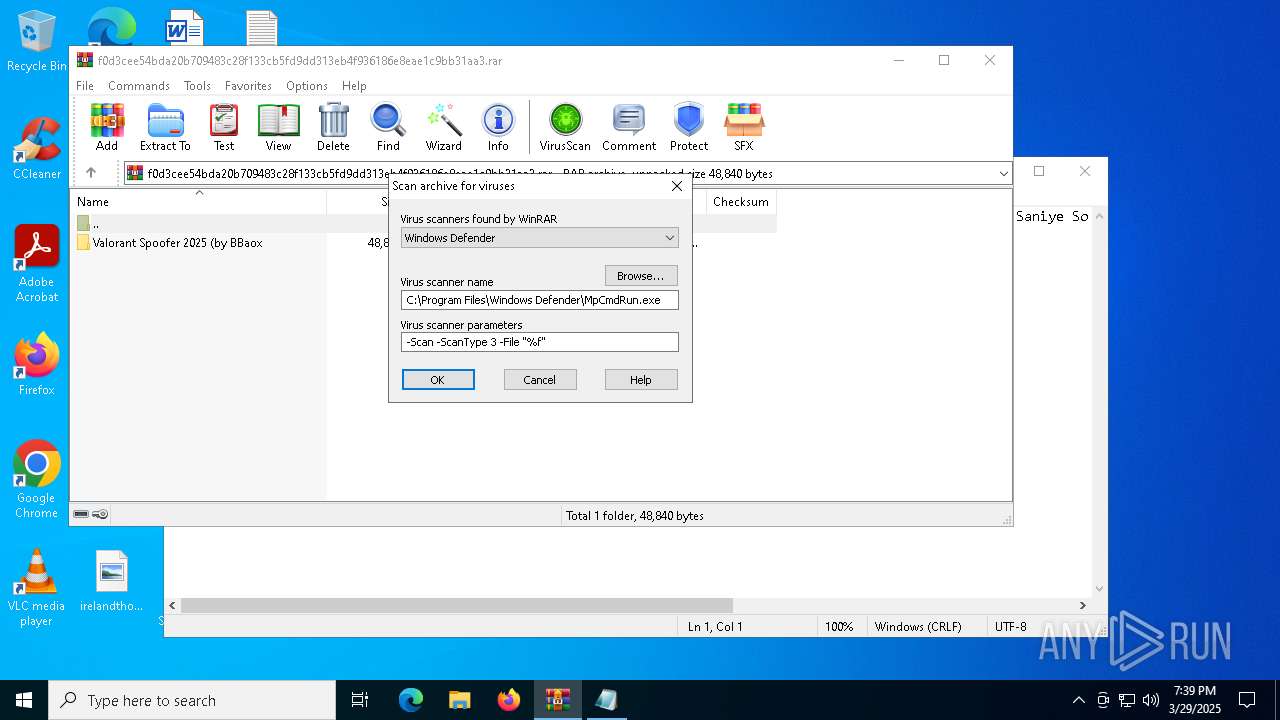
| File name: | f0d3cee54bda20b709483c28f133cb5fd9dd313eb4f936186e8eae1c9bb31aa3 |
| Full analysis: | https://app.any.run/tasks/34e11d55-6c34-4cef-bec5-caf971f7c3a0 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 29, 2025, 19:39:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BDF04DD451F7CB06C2BAADAB9712A543 |
| SHA1: | 40CA5061D63D7744A76C3B1FE2AEFCD42B2A8B09 |
| SHA256: | F0D3CEE54BDA20B709483C28F133CB5FD9DD313EB4F936186E8EAE1C9BB31AA3 |
| SSDEEP: | 384:axuAwmm24LU6kNzfPa2fggYBOfrPdy4tv5l/ovF2zrDBmgPMhqpB84npga+WQsUg:f+4LwZfPvfgg7fr1yQSF2XVHPZCsUg |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7436)
ASYNCRAT has been detected (MUTEX)
- Valorant Spoofer (by BBaox).exe (PID: 7560)
- Valorant Spoofer.exe (PID: 7720)
Changes the autorun value in the registry
- Valorant Spoofer (by BBaox).exe (PID: 7560)
ASYNCRAT has been detected (YARA)
- Valorant Spoofer.exe (PID: 7720)
SUSPICIOUS
Executing commands from a ".bat" file
- Valorant Spoofer (by BBaox).exe (PID: 7560)
- WinRAR.exe (PID: 7436)
Starts CMD.EXE for commands execution
- Valorant Spoofer (by BBaox).exe (PID: 7560)
- WinRAR.exe (PID: 7436)
Executable content was dropped or overwritten
- Valorant Spoofer (by BBaox).exe (PID: 7560)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7640)
The executable file from the user directory is run by the CMD process
- Valorant Spoofer.exe (PID: 7720)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7436)
INFO
Create files in a temporary directory
- Valorant Spoofer (by BBaox).exe (PID: 7560)
- MpCmdRun.exe (PID: 8104)
Reads the computer name
- Valorant Spoofer (by BBaox).exe (PID: 7560)
- Valorant Spoofer.exe (PID: 7720)
- MpCmdRun.exe (PID: 8104)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7596)
Manual execution by a user
- Valorant Spoofer (by BBaox).exe (PID: 7560)
- notepad.exe (PID: 7596)
Checks supported languages
- Valorant Spoofer (by BBaox).exe (PID: 7560)
- Valorant Spoofer.exe (PID: 7720)
- MpCmdRun.exe (PID: 8104)
Reads the machine GUID from the registry
- Valorant Spoofer (by BBaox).exe (PID: 7560)
- Valorant Spoofer.exe (PID: 7720)
Checks proxy server information
- slui.exe (PID: 8184)
Reads the software policy settings
- slui.exe (PID: 8184)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(7720) Valorant Spoofer.exe
C2 (1)127.0.0.1
Ports (2)1604
1600
Version0.5.7B
BotnetDefault
Options
AutoRuntrue
MutexAsyncMutex_6SI8OkPnk
InstallFolder%Temp%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPtwLv/OLlVAytP9mGlrkzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjUwMjEzMTEzNTUzWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIQyH0/kc3iYSq9VLxeuIGNB9RTzmw7fmyJTD+EdiPIH4PhlJU1DTxbljsPEyE29v8ugGv+8lPGl...
Server_SignatureQwFCEbBynLZQFB5sujOBoibu1ylmWzTUrDUYibGq5+TFkpqDDpM0GzUuoLj802yqUg5YH4LDqliekGuhceao7cu+3pdHvDOpQvqHaJSQuT54/Ax1IU4HELfSVLhwPQqfvvW9AMkXgC2uguDNGq30SE2qI7VaBU76By1wmcpwO45d5sxt6QdM4sa7Iu4l6PoPOBEBPjUTbyacLk5+rdLbyWi+ze0qXm3zcTSNZO/wk9guicfOhrs5SApV+2LHLZHx5wK/1c26R5MacUMZ9iHbDAYWOpd/EDGZEMSlZ8mKyeAW...
Keys
AESb7828007f363b214a1ae7587ba754bb0505178a4a5e8e19d6292ddc07b5af854
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 164 |
| UncompressedSize: | 200 |
| OperatingSystem: | Win32 |
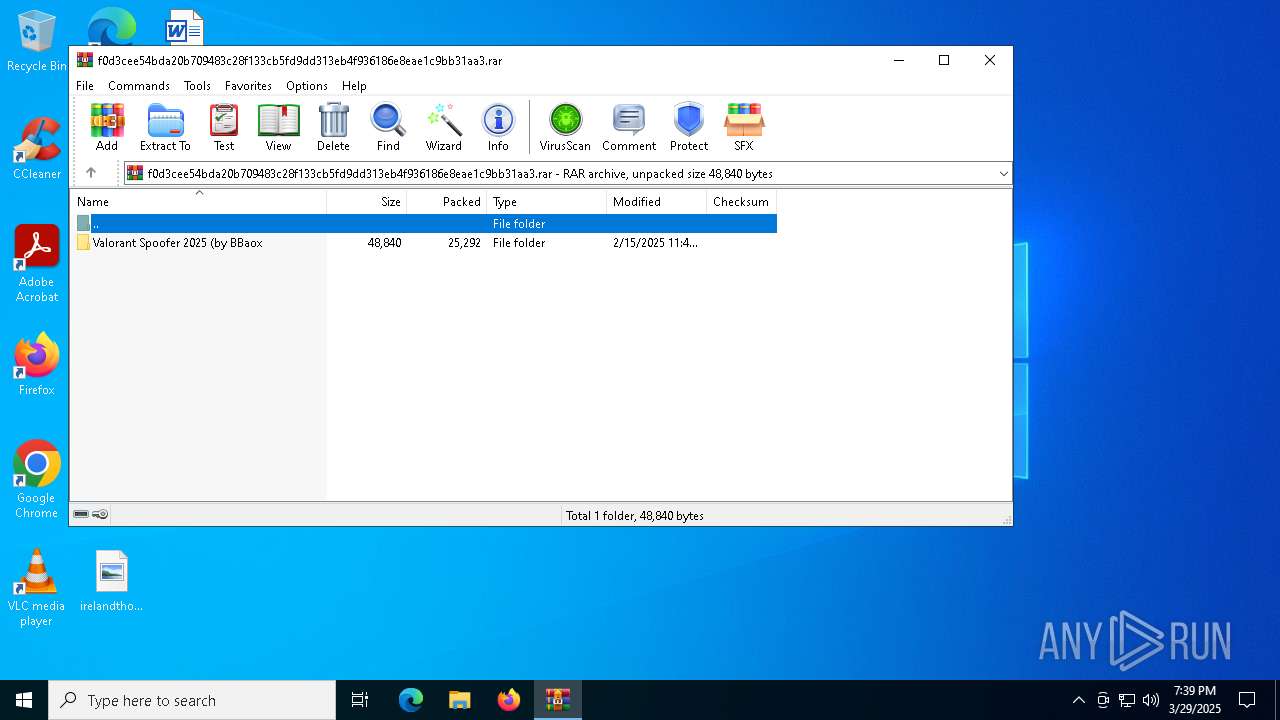
| ArchivedFileName: | Valorant Spoofer 2025 (by BBaox/oku beni.txt |
Total processes
132
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7436 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\f0d3cee54bda20b709483c28f133cb5fd9dd313eb4f936186e8eae1c9bb31aa3.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7560 | "C:\Users\admin\Desktop\Valorant Spoofer (by BBaox).exe" | C:\Users\admin\Desktop\Valorant Spoofer (by BBaox).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 7596 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\oku beni.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7640 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmpE0EC.tmp.bat"" | C:\Windows\SysWOW64\cmd.exe | — | Valorant Spoofer (by BBaox).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7648 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7696 | timeout 3 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7720 | "C:\Users\admin\AppData\Local\Temp\Valorant Spoofer.exe" | C:\Users\admin\AppData\Local\Temp\Valorant Spoofer.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 0.0.0.0 Modules
AsyncRat(PID) Process(7720) Valorant Spoofer.exe C2 (1)127.0.0.1 Ports (2)1604 1600 Version0.5.7B BotnetDefault Options AutoRuntrue MutexAsyncMutex_6SI8OkPnk InstallFolder%Temp% BSoDfalse AntiVMfalse Certificates Cert1MIIE8jCCAtqgAwIBAgIQAPtwLv/OLlVAytP9mGlrkzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjUwMjEzMTEzNTUzWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIQyH0/kc3iYSq9VLxeuIGNB9RTzmw7fmyJTD+EdiPIH4PhlJU1DTxbljsPEyE29v8ugGv+8lPGl... Server_SignatureQwFCEbBynLZQFB5sujOBoibu1ylmWzTUrDUYibGq5+TFkpqDDpM0GzUuoLj802yqUg5YH4LDqliekGuhceao7cu+3pdHvDOpQvqHaJSQuT54/Ax1IU4HELfSVLhwPQqfvvW9AMkXgC2uguDNGq30SE2qI7VaBU76By1wmcpwO45d5sxt6QdM4sa7Iu4l6PoPOBEBPjUTbyacLk5+rdLbyWi+ze0qXm3zcTSNZO/wk9guicfOhrs5SApV+2LHLZHx5wK/1c26R5MacUMZ9iHbDAYWOpd/EDGZEMSlZ8mKyeAW... Keys AESb7828007f363b214a1ae7587ba754bb0505178a4a5e8e19d6292ddc07b5af854 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 8044 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7436.964\Rar$Scan26907.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8104 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7436.964" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 631
Read events
5 621
Write events
10
Delete events
0
Modification events
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\f0d3cee54bda20b709483c28f133cb5fd9dd313eb4f936186e8eae1c9bb31aa3.rar | |||
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7560) Valorant Spoofer (by BBaox).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Valorant Spoofer |
Value: "C:\Users\admin\AppData\Local\Temp\Valorant Spoofer.exe" | |||
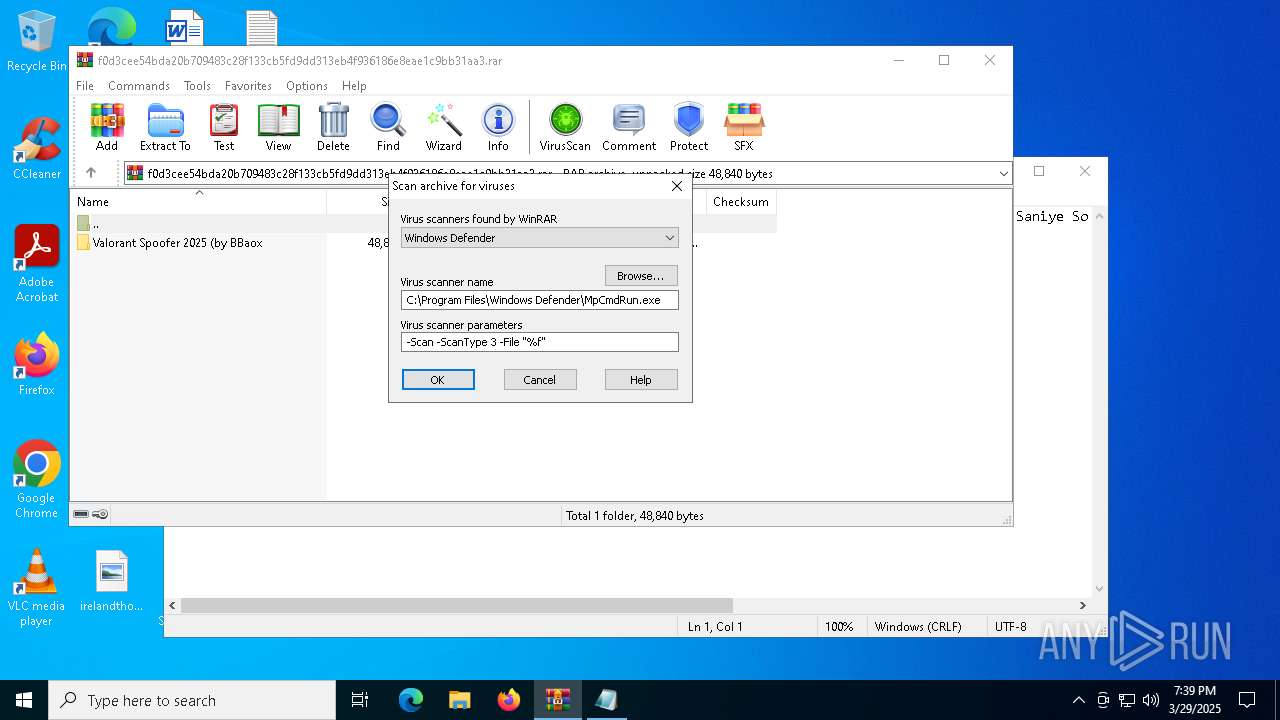
| (PID) Process: | (7436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
2
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7560 | Valorant Spoofer (by BBaox).exe | C:\Users\admin\AppData\Local\Temp\Valorant Spoofer.exe | executable | |
MD5:FD64259B217827EBBE114699E9194BA7 | SHA256:68FB8F06592B84297FC6ADF794044E693BC8CA655502D7C661A5A00128DD37B4 | |||
| 7436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7436.964\Rar$Scan26907.bat | text | |
MD5:2F06A65E13BAEBEE6AA88F35355DBDCC | SHA256:4853533E74D1FC5E220A386489B54557A051C6BA4C7B3A70229C58AE0C343BFF | |||
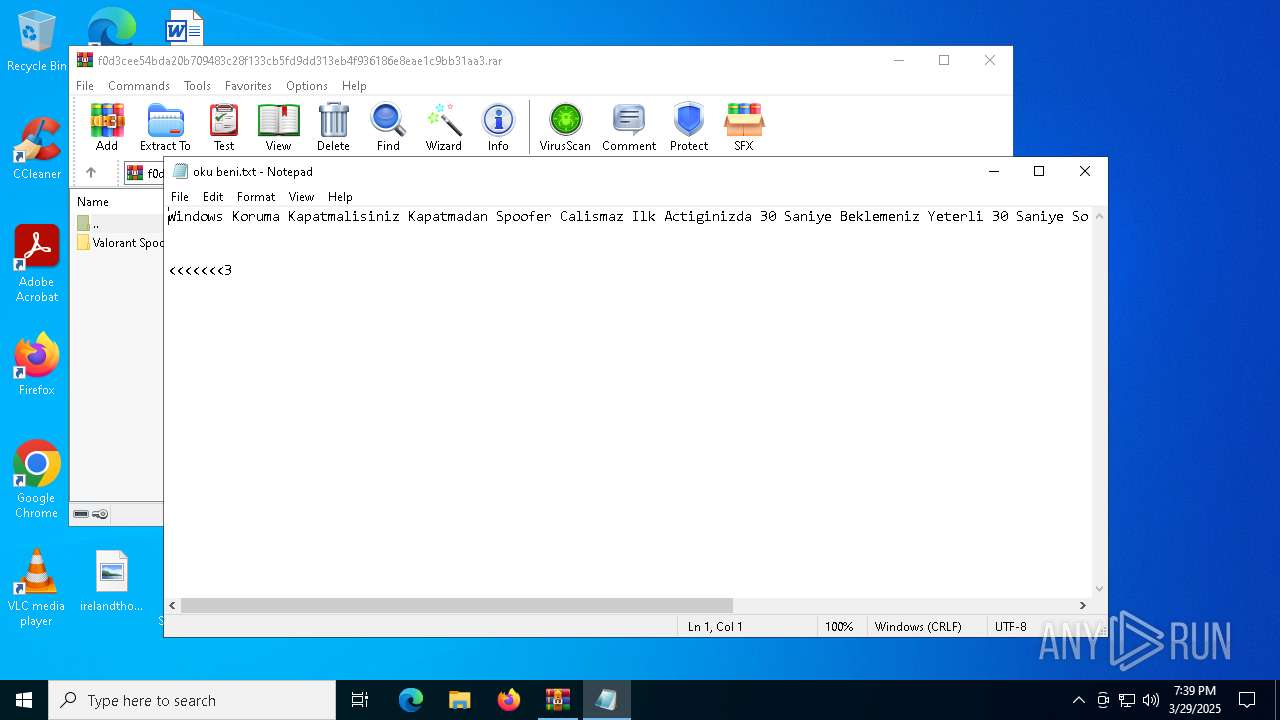
| 7436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7436.964\f0d3cee54bda20b709483c28f133cb5fd9dd313eb4f936186e8eae1c9bb31aa3.rar\Valorant Spoofer 2025 (by BBaox\oku beni.txt | text | |
MD5:435906694882D3CB2CE0B2FB75714802 | SHA256:63275E4DE7217FC0438BA5B89388A31DC4D1D57FE387A305FB9522006D881182 | |||
| 8104 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:3F16F939EE74DA8FAF71A7E825446E95 | SHA256:68BE70B09286291E383983FD25B18D4CEAA14F5F0F1A0CB6A9F64AABCA11E304 | |||
| 7436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7436.964\f0d3cee54bda20b709483c28f133cb5fd9dd313eb4f936186e8eae1c9bb31aa3.rar\Valorant Spoofer 2025 (by BBaox\Valorant Spoofer (by BBaox).exe | executable | |
MD5:FD64259B217827EBBE114699E9194BA7 | SHA256:68FB8F06592B84297FC6ADF794044E693BC8CA655502D7C661A5A00128DD37B4 | |||
| 7560 | Valorant Spoofer (by BBaox).exe | C:\Users\admin\AppData\Local\Temp\tmpE0EC.tmp.bat | text | |
MD5:C592016F08490EC9F82FA3EC59F6C751 | SHA256:BF17CEAD924D0E34E1EC8B1C6ED6FB6D787317EE8C018544E8B636D7C1F34B71 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
42
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
7872 | SIHClient.exe | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.242.39.171:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
7872 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
7872 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7872 | SIHClient.exe | 23.48.23.138:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7872 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7872 | SIHClient.exe | 52.165.164.15:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7292 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |