| File name: | f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe |
| Full analysis: | https://app.any.run/tasks/0fbbb5b2-af75-440a-809d-657a8f6e6ee4 |
| Verdict: | Malicious activity |
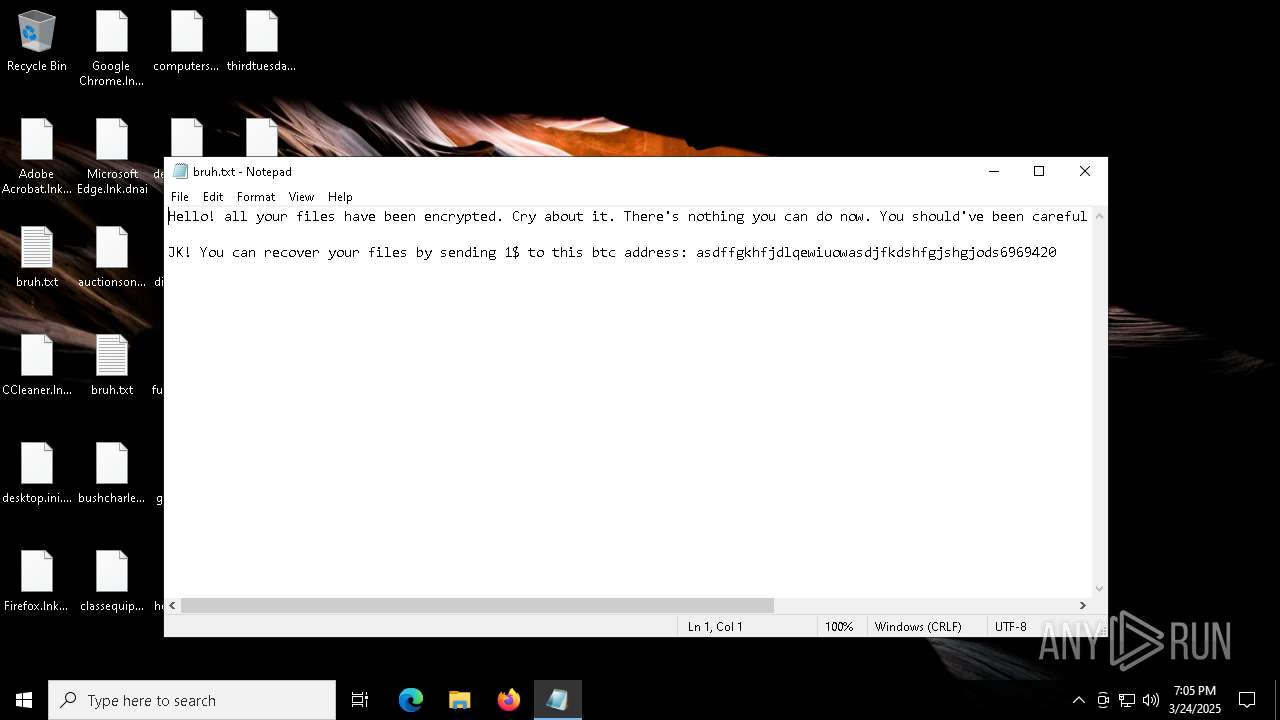
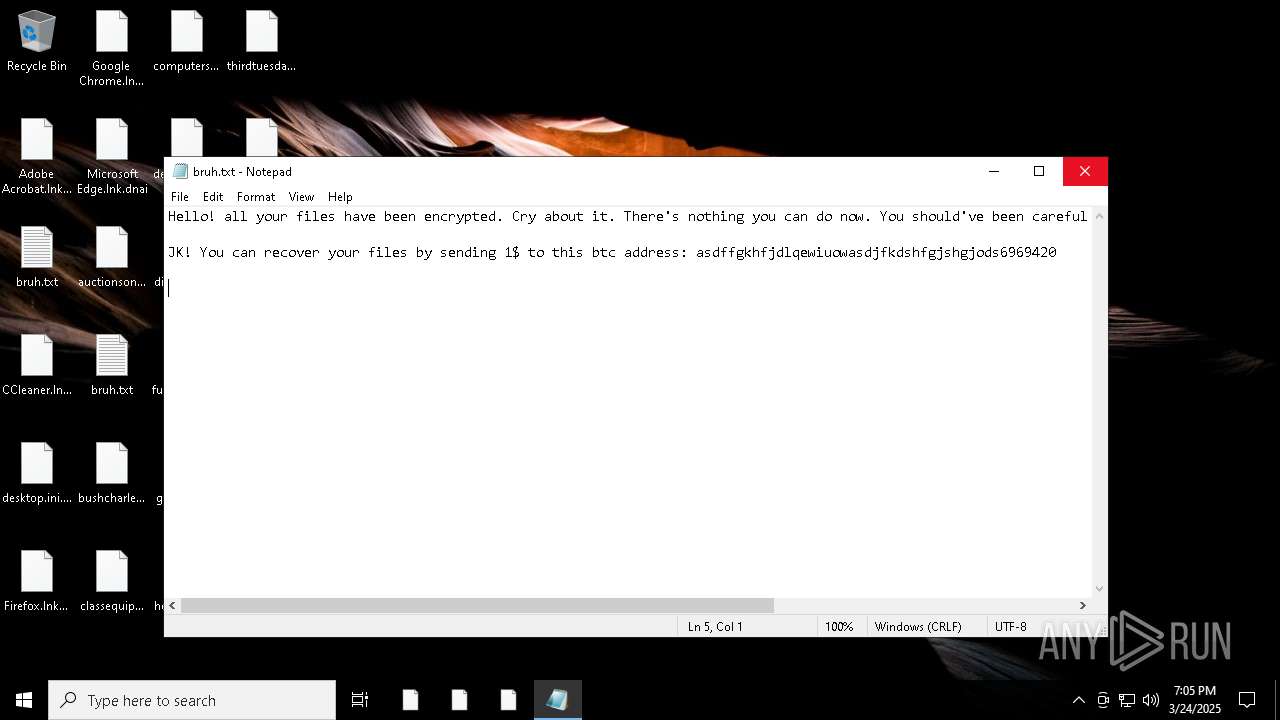
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | March 24, 2025, 19:04:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | D3C77A381D509DB6785A4D23B15D79D5 |
| SHA1: | 1B8031147C9084068A013A7230B2ADEDF8A03FEF |
| SHA256: | F0B4CC9CA7207386FA06793A0FD2DD2B2D5A0EE019AF0A7AFBEB5B1665AF4271 |
| SSDEEP: | 24576:3qQl+ulA8Msy1byaVJW9uyb/is+9qi/8EnTx4tTlR:3qa+uBy1bHVJomsMqqfFKx |
MALICIOUS
RANSOMWARE has been detected
- windowsdefender.exe (PID: 7588)
Actions looks like stealing of personal data
- windowsdefender.exe (PID: 7588)
Create files in the Startup directory
- windowsdefender.exe (PID: 7588)
CHAOS has been detected (YARA)
- windowsdefender.exe (PID: 7588)
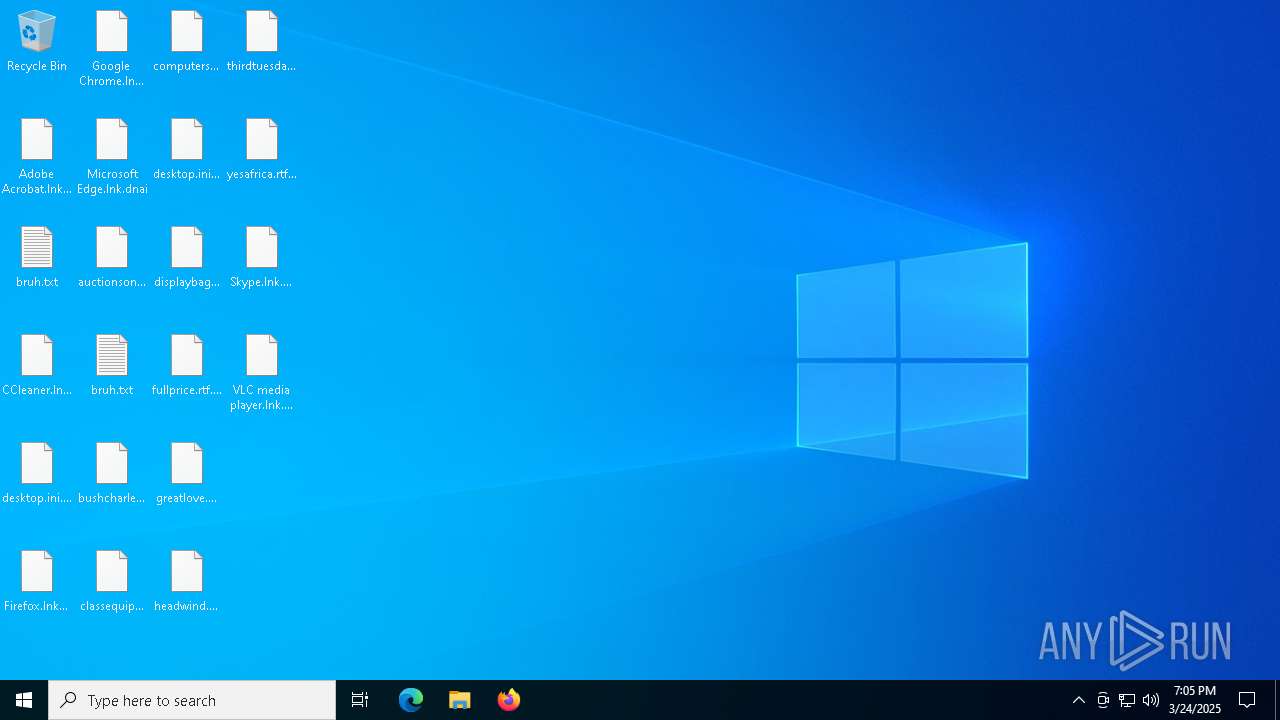
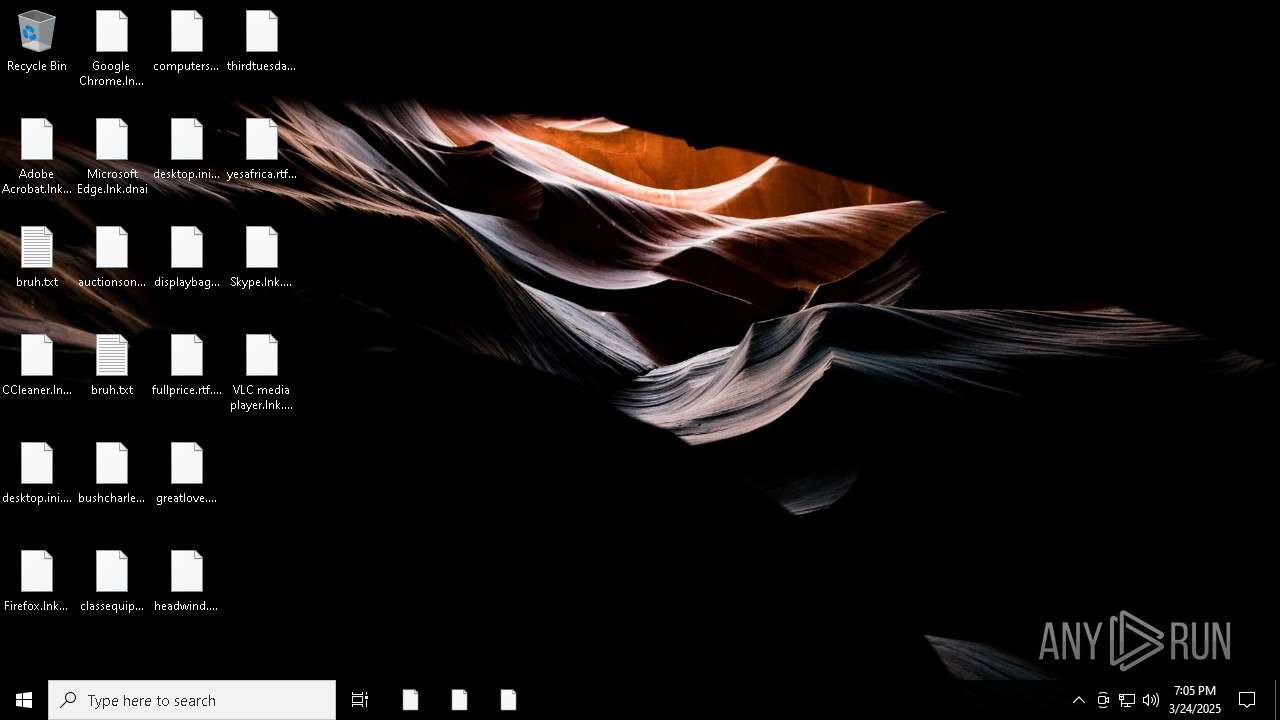
Renames files like ransomware
- windowsdefender.exe (PID: 7588)
Deletes shadow copies
- cmd.exe (PID: 7272)
- cmd.exe (PID: 7532)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 3304)
SUSPICIOUS
Executable content was dropped or overwritten
- f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe (PID: 7316)
Reads security settings of Internet Explorer
- f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe (PID: 7316)
- windowsdefender.exe (PID: 7588)
Reads the date of Windows installation
- f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe (PID: 7316)
- windowsdefender.exe (PID: 7588)
Starts itself from another location
- f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe (PID: 7316)
Found regular expressions for crypto-addresses (YARA)
- windowsdefender.exe (PID: 7588)
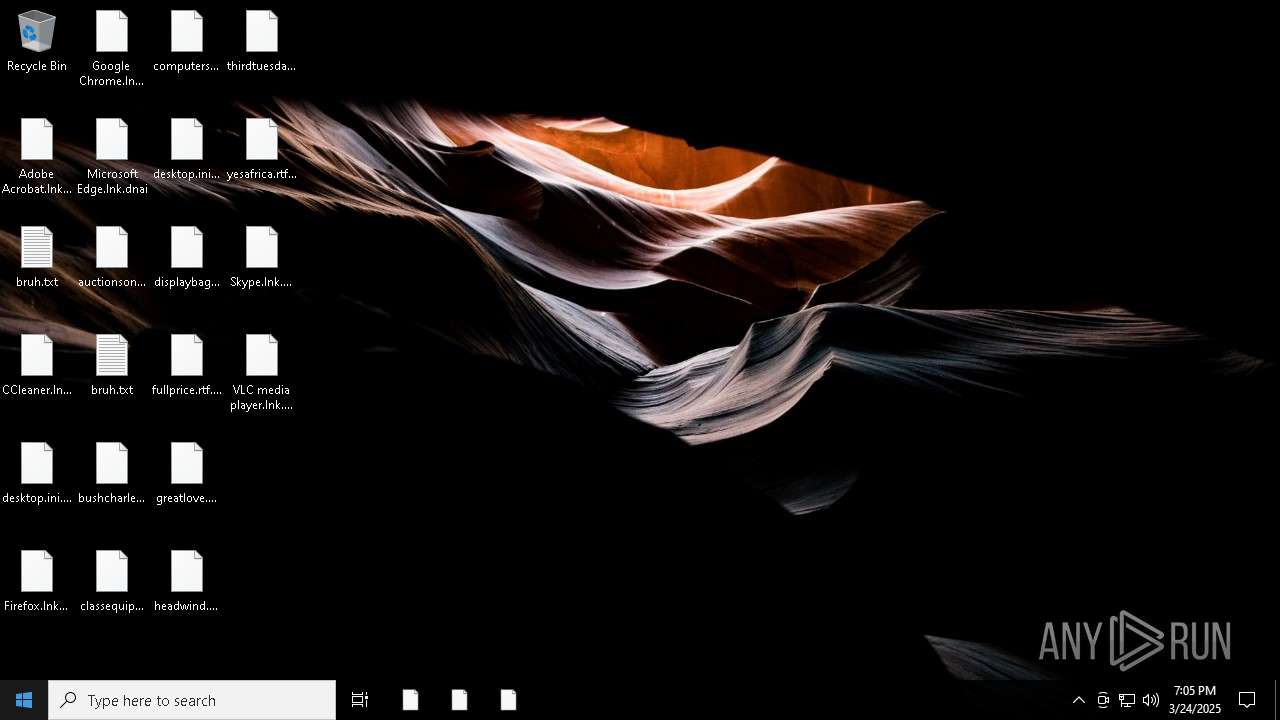
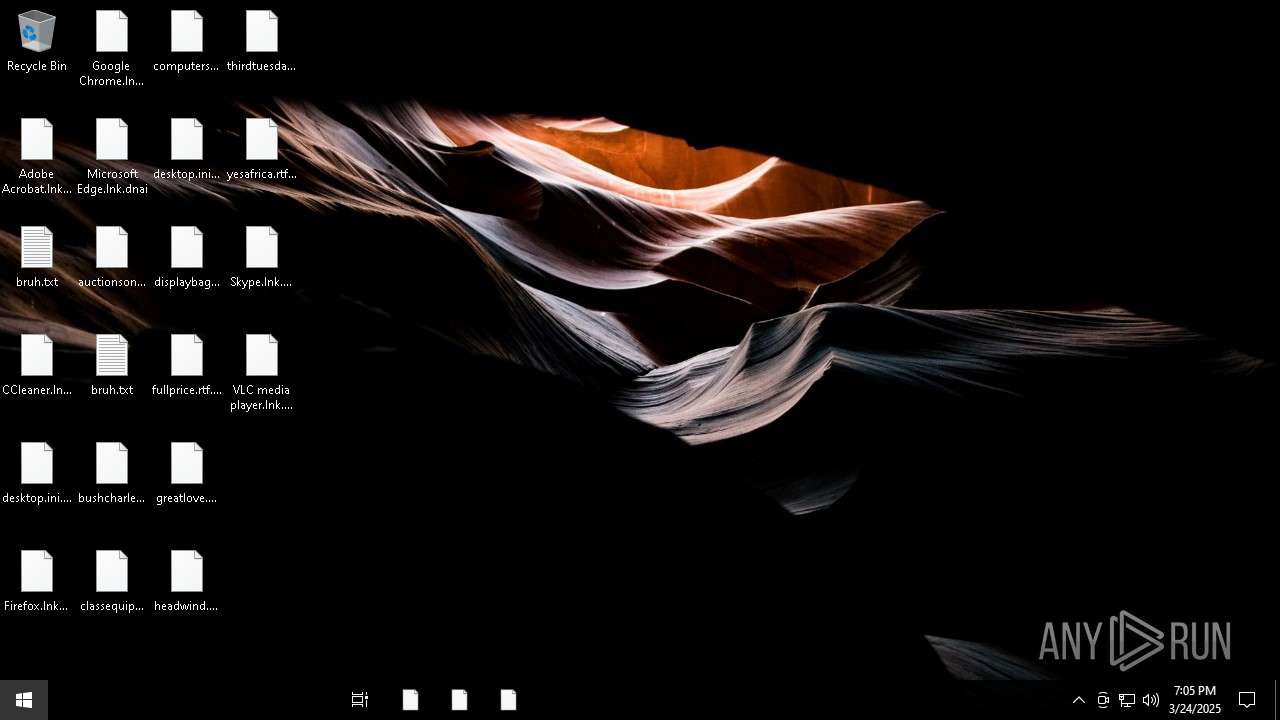
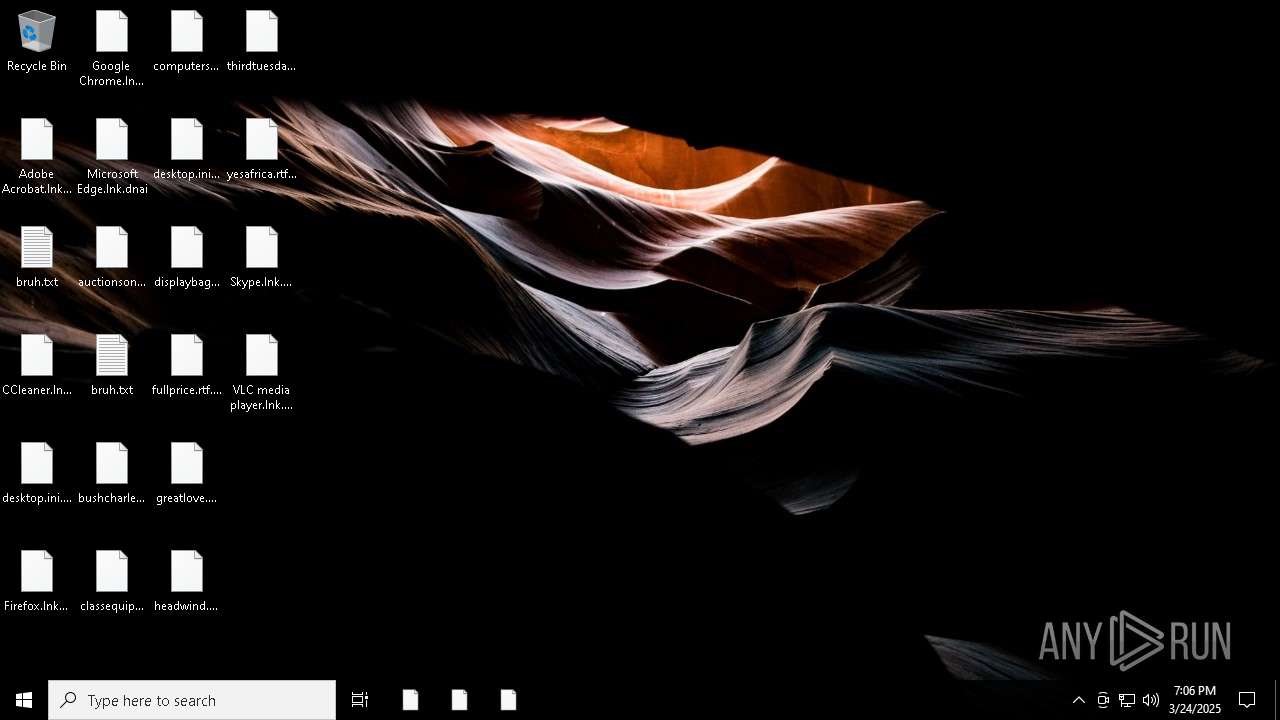
Write to the desktop.ini file (may be used to cloak folders)
- windowsdefender.exe (PID: 7588)
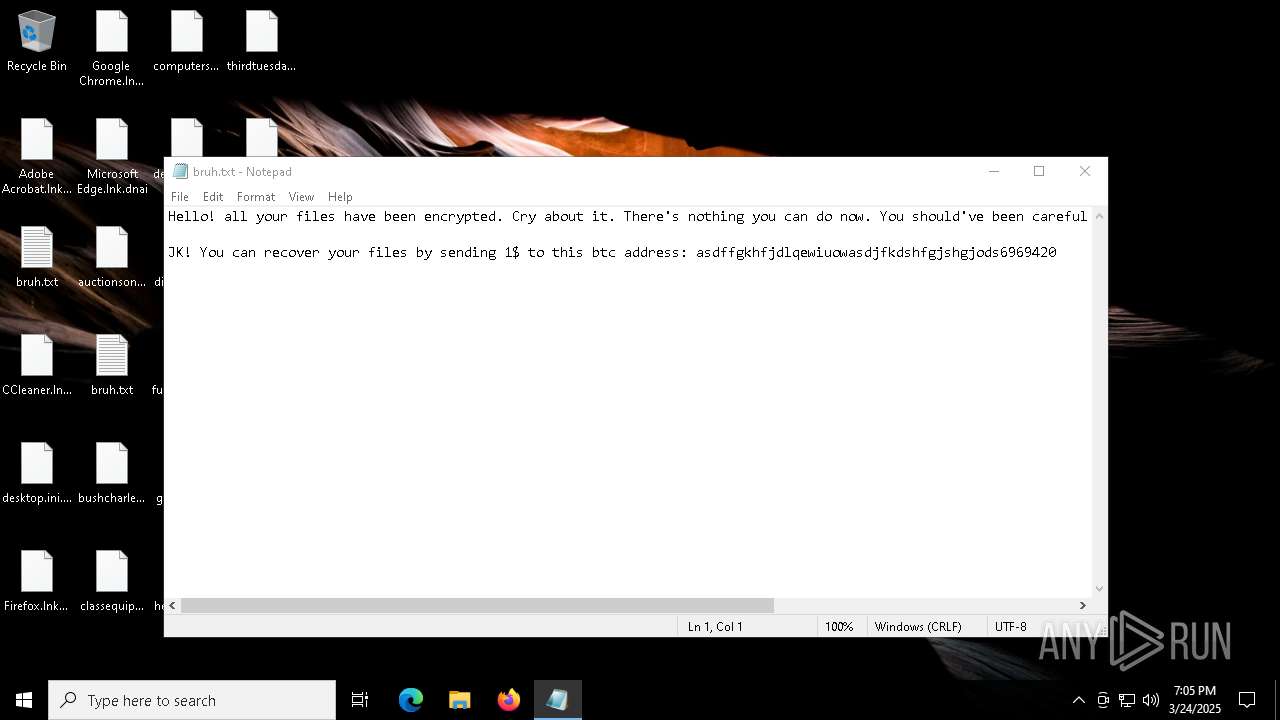
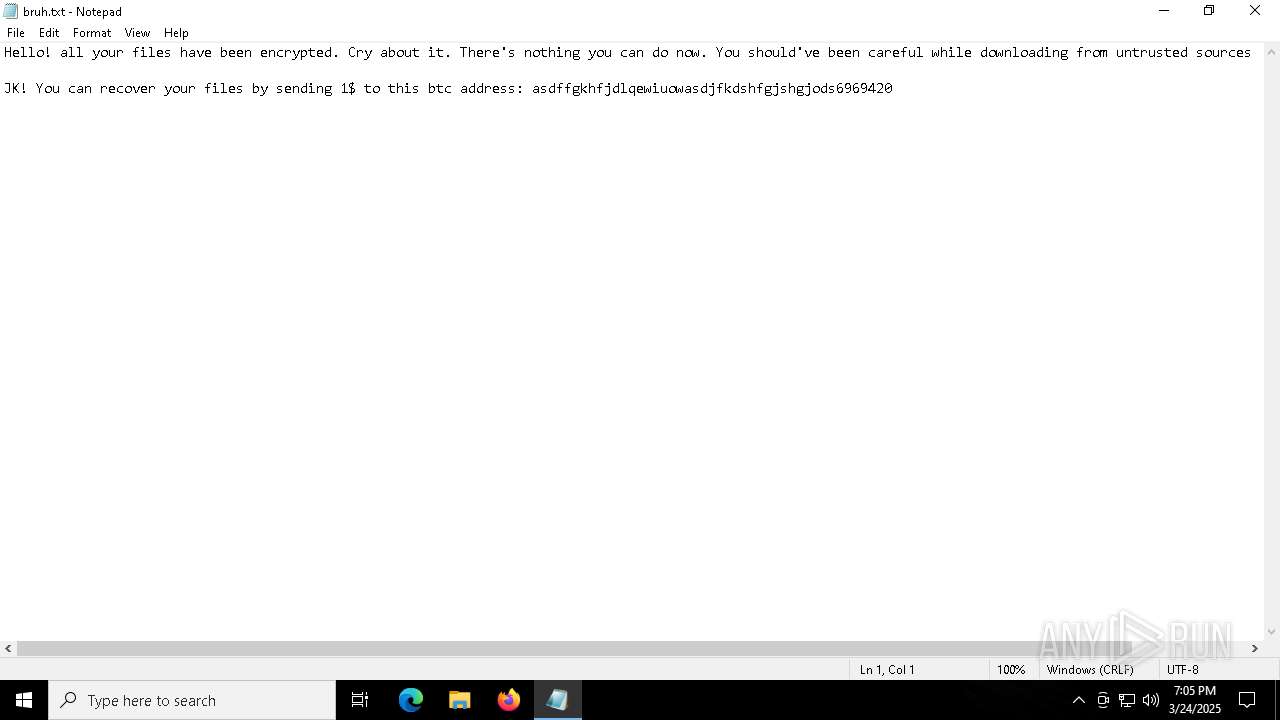
Start notepad (likely ransomware note)
- windowsdefender.exe (PID: 7588)
Executes as Windows Service
- vds.exe (PID: 7716)
- wbengine.exe (PID: 6724)
- VSSVC.exe (PID: 5608)
Starts CMD.EXE for commands execution
- windowsdefender.exe (PID: 7588)
INFO
Creates files or folders in the user directory
- f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe (PID: 7316)
- windowsdefender.exe (PID: 7588)
- Cortana.exe (PID: 5048)
- SystemSettingsBroker.exe (PID: 5720)
Reads the computer name
- f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe (PID: 7316)
- windowsdefender.exe (PID: 7588)
Checks supported languages
- f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe (PID: 7316)
- windowsdefender.exe (PID: 7588)
Process checks computer location settings
- f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe (PID: 7316)
- windowsdefender.exe (PID: 7588)
Reads the machine GUID from the registry
- windowsdefender.exe (PID: 7588)
- Cortana.exe (PID: 5048)
Autorun file from Startup directory
- windowsdefender.exe (PID: 7588)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4040)
Create files in a temporary directory
- windowsdefender.exe (PID: 7588)
Reads the software policy settings
- Cortana.exe (PID: 5048)
- slui.exe (PID: 7416)
Manual execution by a user
- chrome.exe (PID: 4120)
Application launched itself
- chrome.exe (PID: 4120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:10:02 12:26:45+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2489856 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x261d8e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | goliath.exe |
| LegalCopyright: | |
| OriginalFileName: | goliath.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
184
Monitored processes
40
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3704 --field-trial-handle=1944,i,9366329436913905309,2231821994013676335,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4588 --field-trial-handle=1944,i,9366329436913905309,2231821994013676335,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2312 --field-trial-handle=1944,i,9366329436913905309,2231821994013676335,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3196 --field-trial-handle=1944,i,9366329436913905309,2231821994013676335,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2852 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\bruh.txt | C:\Windows\System32\notepad.exe | — | windowsdefender.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3304 | "C:\Windows\System32\cmd.exe" /C bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no | C:\Windows\System32\cmd.exe | — | windowsdefender.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3364 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5164 --field-trial-handle=1944,i,9366329436913905309,2231821994013676335,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4040 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4428 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 056
Read events
10 996
Write events
40
Delete events
20
Modification events
| (PID) Process: | (7540) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{a5a30fa2-3d06-4e9f-b5f4-a01df9d1fcba}\Elements\24000001 |
| Operation: | write | Name: | Element |
Value: {5b970157-8568-11eb-b45c-806e6f6e6963} | |||
| (PID) Process: | (7540) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{a5a30fa2-3d06-4e9f-b5f4-a01df9d1fcba}\Elements\25000004 |
| Operation: | write | Name: | Element |
Value: 0000000000000000 | |||
| (PID) Process: | (7540) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{7bcdbaa8-85a9-11eb-90a8-9a9b76358421}\Elements\250000e0 |
| Operation: | write | Name: | Element |
Value: 0100000000000000 | |||
| (PID) Process: | (7512) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7512) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (7512) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7512) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (7512) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7512) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (7512) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
79
Text files
655
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7588 | windowsdefender.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\windowsdefender.url | binary | |
MD5:056573A2C47DCEE5092EACE3A8CCA873 | SHA256:D266A53B2EE0A190E8ACF84AFBD9B8426FECF80A5108D88F28FA042AE8151D8A | |||
| 7316 | f0b4cc9ca7207386fa06793a0fd2dd2b2d5a0ee019af0a7afbeb5b1665af4271.exe | C:\Users\admin\AppData\Roaming\windowsdefender.exe | executable | |
MD5:D3C77A381D509DB6785A4D23B15D79D5 | SHA256:F0B4CC9CA7207386FA06793A0FD2DD2B2D5A0EE019AF0A7AFBEB5B1665AF4271 | |||
| 7588 | windowsdefender.exe | C:\Users\admin\Desktop\computersshoes.rtf.2hzp | text | |
MD5:81A27CEEF65A8812765977C8BD5C938D | SHA256:68FFD0B7ECF081515119EEEFE78AFC17CDF54FB535D58C420CDFB285083B8556 | |||
| 7588 | windowsdefender.exe | C:\Users\admin\Desktop\desktop.ini | text | |
MD5:743747EB8C5C8FBFA21EC7C764D399B0 | SHA256:6D2F48984855635DA3923686CEC9046F1CE455C64508E2BC2341E04981DA74BB | |||
| 7588 | windowsdefender.exe | C:\Users\admin\Desktop\displaybag.rtf.vagn | text | |
MD5:906A4FB064FA91C86607F4934686D92B | SHA256:F651CF2B1539ED7D0259797B37A06BE199015CC96FF6ABD90B0247CC51A9E8DC | |||
| 7588 | windowsdefender.exe | C:\Users\admin\Desktop\greatlove.png.4bt9 | text | |
MD5:77E3F816D0BFADE9C38970613E42602E | SHA256:F28C3CFBB0D80E485DC39AB781675087CC1DEEA17C9A424BC1884F0E64E7879B | |||
| 7588 | windowsdefender.exe | C:\Users\admin\Desktop\displaybag.rtf | text | |
MD5:906A4FB064FA91C86607F4934686D92B | SHA256:F651CF2B1539ED7D0259797B37A06BE199015CC96FF6ABD90B0247CC51A9E8DC | |||
| 7588 | windowsdefender.exe | C:\Users\admin\Desktop\greatlove.png | text | |
MD5:77E3F816D0BFADE9C38970613E42602E | SHA256:F28C3CFBB0D80E485DC39AB781675087CC1DEEA17C9A424BC1884F0E64E7879B | |||
| 7588 | windowsdefender.exe | C:\Users\admin\Desktop\computersshoes.rtf | text | |
MD5:81A27CEEF65A8812765977C8BD5C938D | SHA256:68FFD0B7ECF081515119EEEFE78AFC17CDF54FB535D58C420CDFB285083B8556 | |||
| 7588 | windowsdefender.exe | C:\Users\admin\Desktop\headwind.png | text | |
MD5:3816BC7A5AA50A3FFE605E3945664EFC | SHA256:67A9A5E1C2A8A4B771FB65265DB5AAAF2F37202B2389F267519D8BF03AF041B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
51
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7852 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5204 | SIHClient.exe | GET | 200 | 92.123.22.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5204 | SIHClient.exe | GET | 200 | 92.123.22.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5048 | Cortana.exe | GET | 200 | 23.53.40.192:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5048 | Cortana.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7852 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |