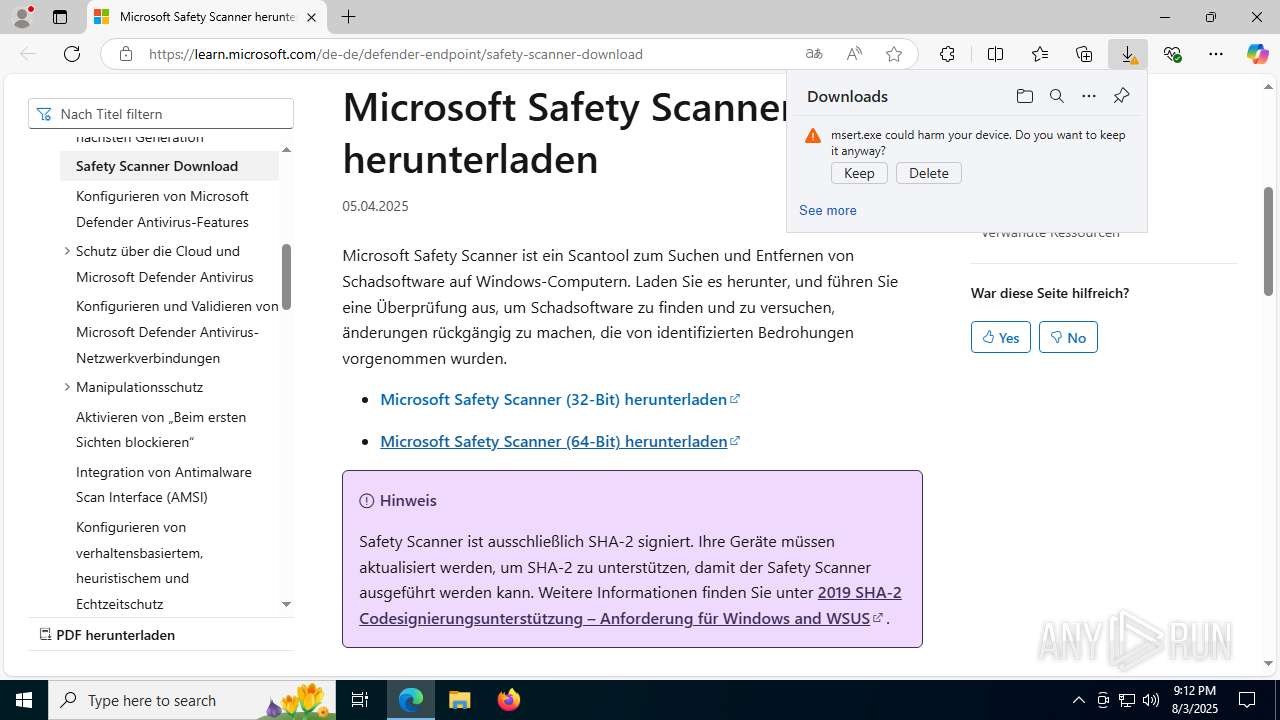
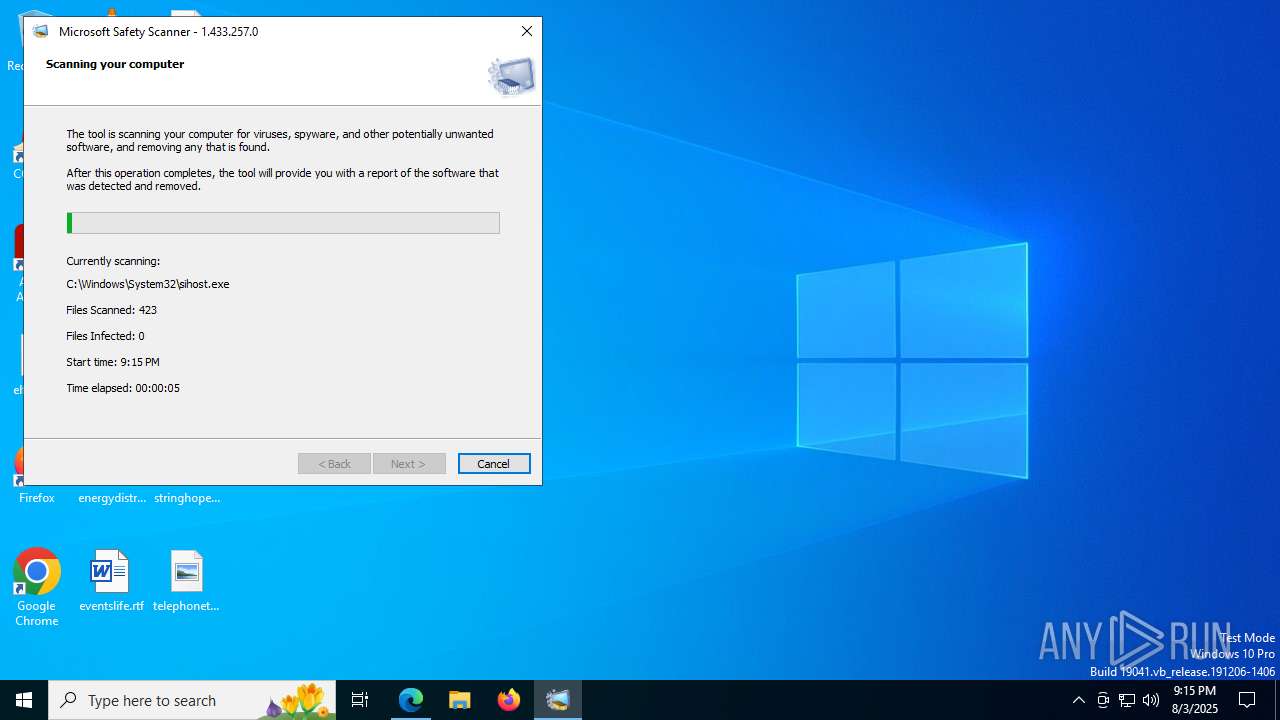
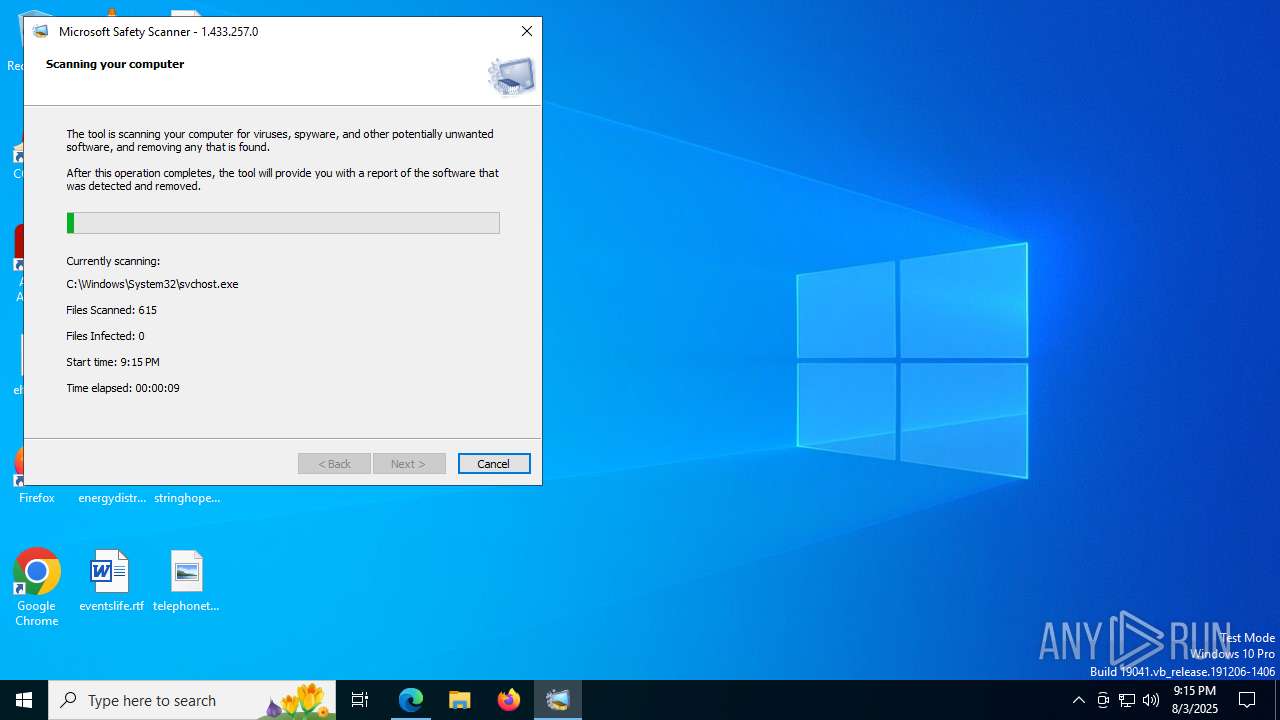
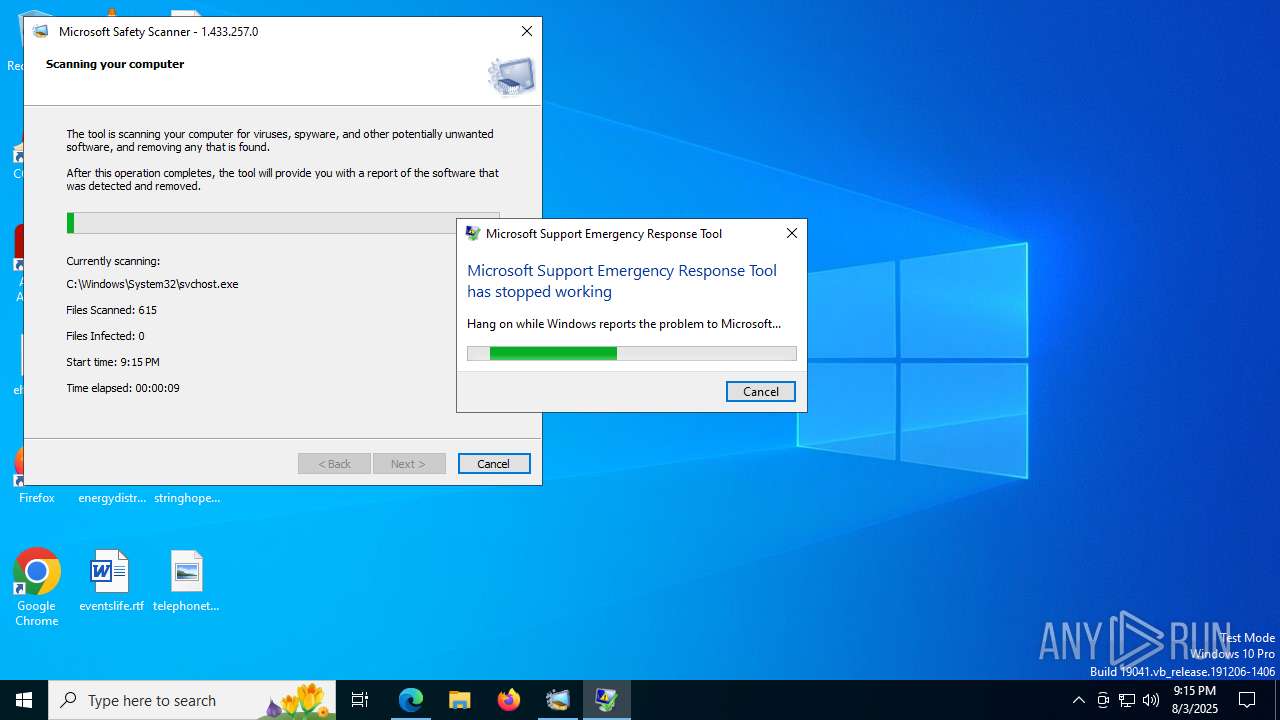
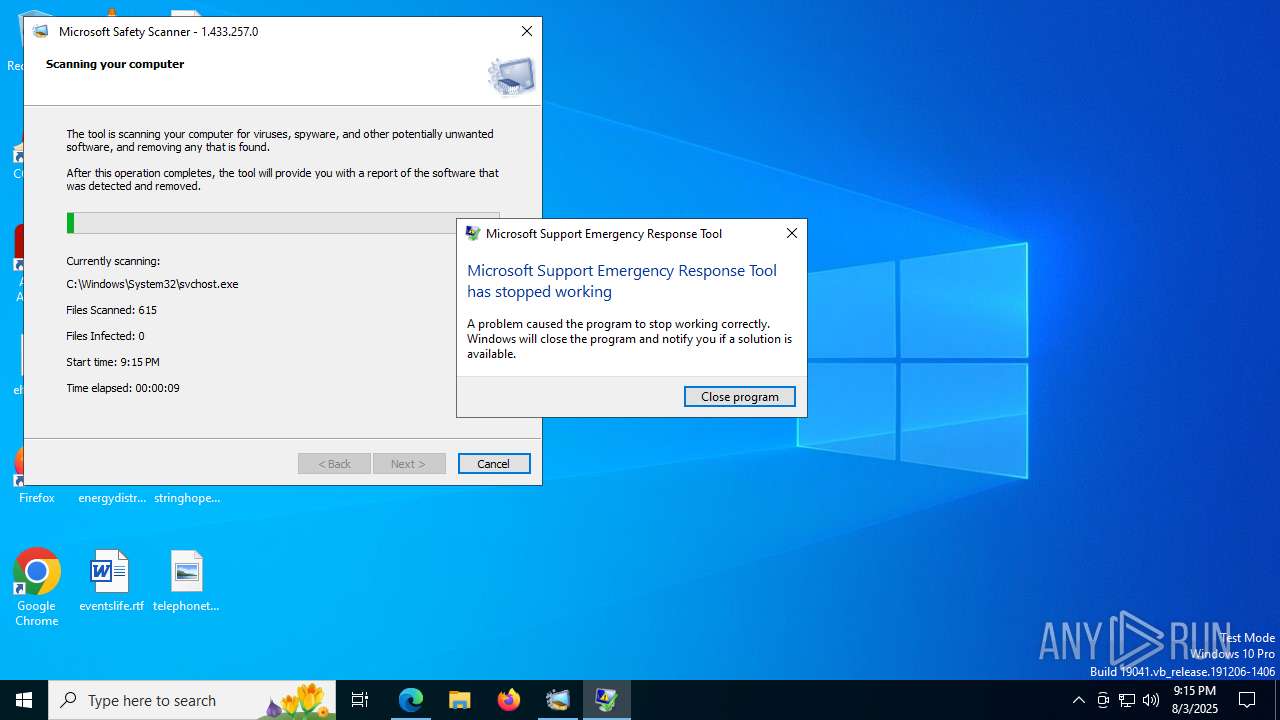
| URL: | https://learn.microsoft.com/de-de/defender-endpoint/safety-scanner-download |
| Full analysis: | https://app.any.run/tasks/ed662640-bb37-44a2-a9a1-0c5234aa312f |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | August 03, 2025, 21:12:40 |
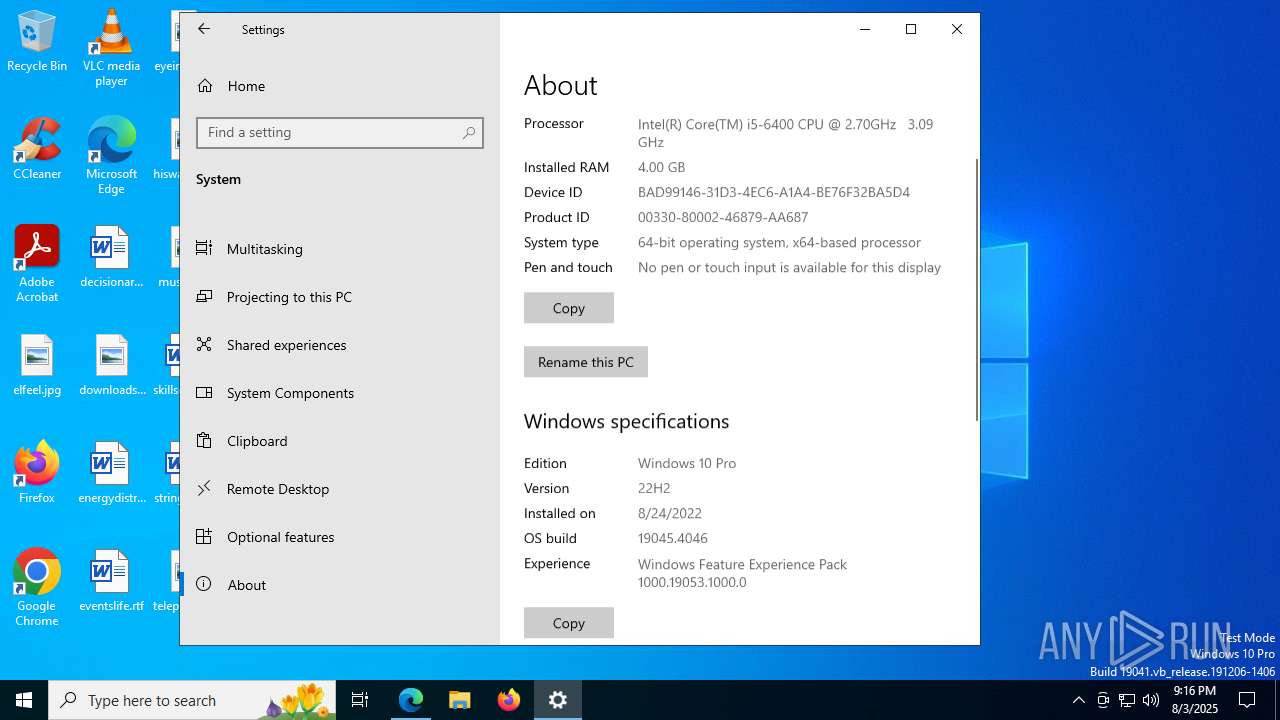
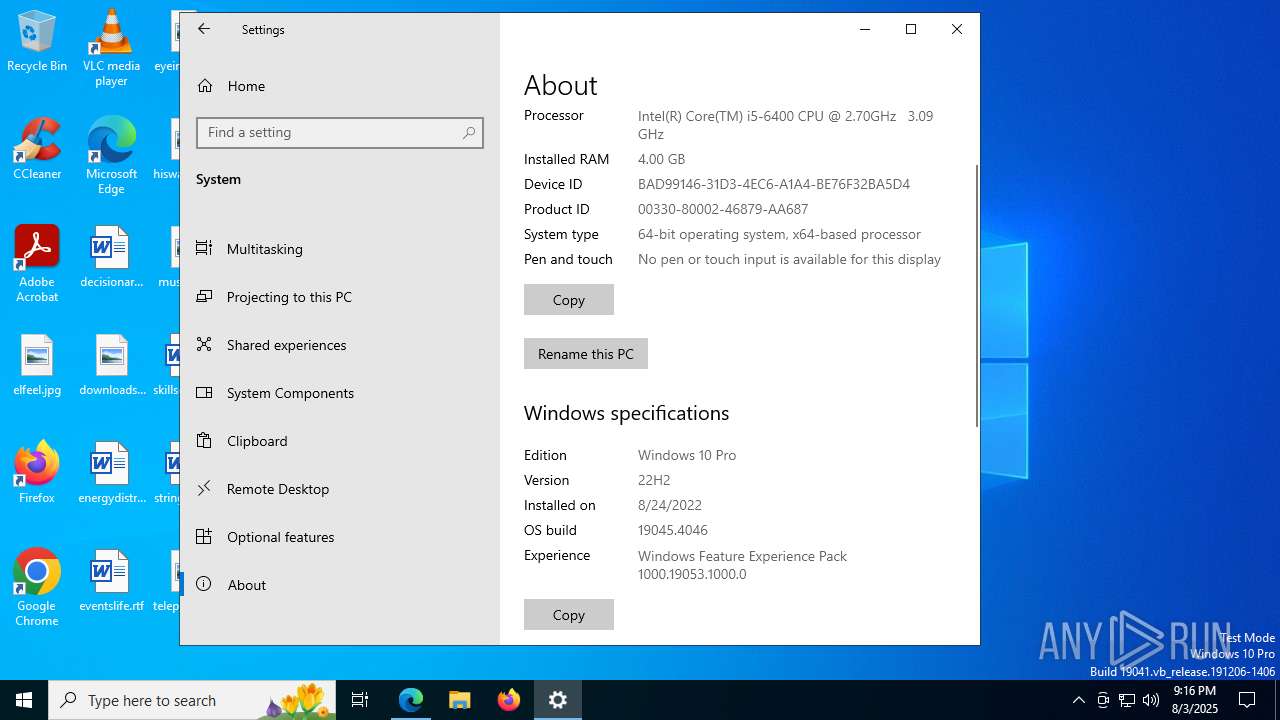
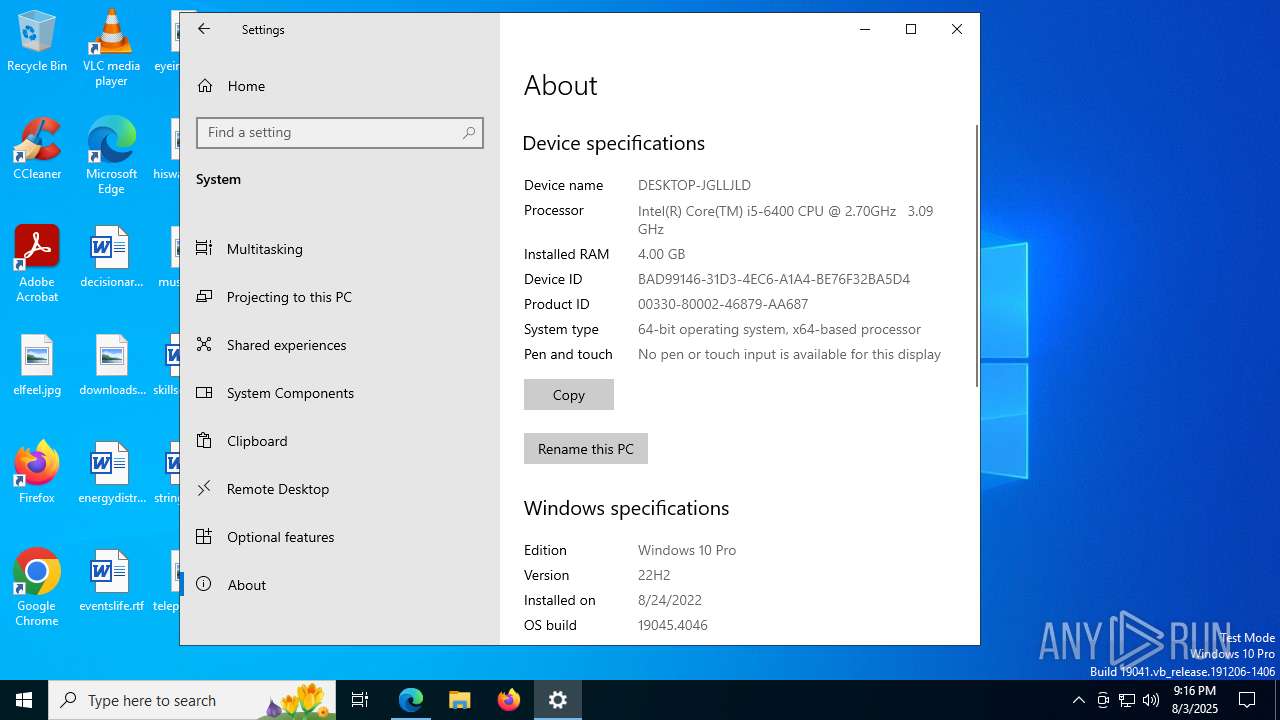
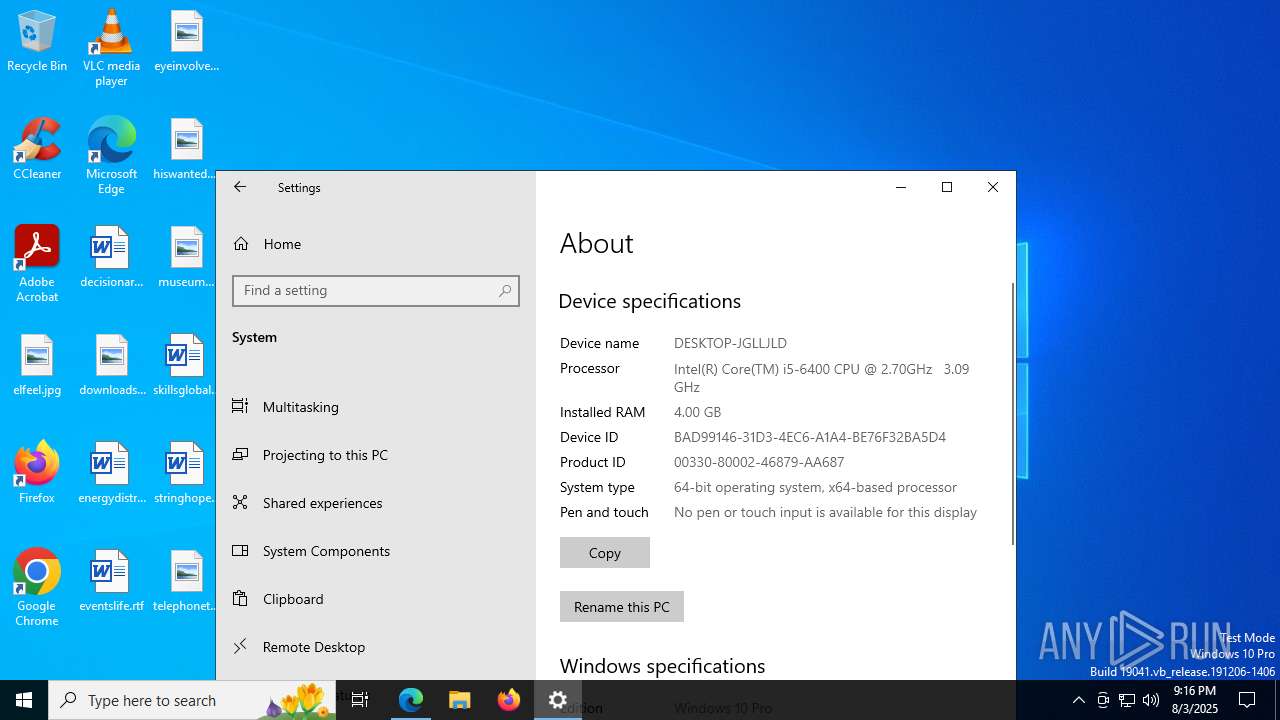
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 43A34ABC87640ED13451DCE22544E0FD |
| SHA1: | B72DB1A44026735D7488DA42B1A2D21EE786CF98 |
| SHA256: | F043BB72CA219C598D41829C941B27CE8E4093E3369BC91E7B4332D9AC7837B5 |
| SSDEEP: | 3:N8AEvTtR2IB8AL9OrN7REy2Lz:2AEvTD2UONVez |
MALICIOUS
Actions looks like stealing of personal data
- msert.exe (PID: 7792)
ATLANTIDA has been detected (YARA)
- msert.exe (PID: 7792)
MASSLOGGER has been detected (YARA)
- msert.exe (PID: 7792)
REVERSESSH has been detected (YARA)
- msert.exe (PID: 7792)
XORed URL has been found (YARA)
- msert.exe (PID: 7792)
EMMENHTAL has been detected (YARA)
- msert.exe (PID: 7792)
MIMIKATZ has been detected (YARA)
- msert.exe (PID: 7792)
Steals Growtopia credentials and data (YARA)
- msert.exe (PID: 7792)
PWDUMP has been detected (YARA)
- msert.exe (PID: 7792)
MINT has been detected (YARA)
- msert.exe (PID: 7792)
DCRAT has been detected (YARA)
- msert.exe (PID: 7792)
[YARA] DarkVision RAT is detected
- msert.exe (PID: 7792)
Steals Discord credentials and data (YARA)
- msert.exe (PID: 7792)
CRYPTBOT has been detected (YARA)
- msert.exe (PID: 7792)
LOCKBIT4 has been detected (YARA)
- msert.exe (PID: 7792)
COBALTSTRIKE has been detected (YARA)
- msert.exe (PID: 7792)
M0YV has been detected (YARA)
- msert.exe (PID: 7792)
LUMMA has been detected (YARA)
- msert.exe (PID: 7792)
SODINOKIBI has been detected (YARA)
- msert.exe (PID: 7792)
GOINJECTOR has been detected (YARA)
- msert.exe (PID: 7792)
ASYNCRAT has been detected (YARA)
- msert.exe (PID: 7792)
XMRIG has been detected (YARA)
- msert.exe (PID: 7792)
CVE-2022-30190 detected
- msert.exe (PID: 7792)
SUSPICIOUS
Reads the date of Windows installation
- msert.exe (PID: 8000)
Reads security settings of Internet Explorer
- msert.exe (PID: 8000)
- msert.exe (PID: 7792)
- ShellExperienceHost.exe (PID: 1268)
Application launched itself
- msert.exe (PID: 8000)
Executable content was dropped or overwritten
- msert.exe (PID: 7792)
Process drops legitimate windows executable
- msert.exe (PID: 7792)
The process verifies whether the antivirus software is installed
- msert.exe (PID: 7792)
Possible usage of Discord/Telegram API has been detected (YARA)
- msert.exe (PID: 7792)
There is functionality for taking screenshot (YARA)
- msert.exe (PID: 8000)
- msert.exe (PID: 7792)
Found regular expressions for crypto-addresses (YARA)
- msert.exe (PID: 7792)
Multiple wallet extension IDs have been found
- msert.exe (PID: 7792)
There is functionality for VM detection antiVM strings (YARA)
- msert.exe (PID: 7792)
MeshAgent potential remote access (YARA)
- msert.exe (PID: 7792)
Executes application which crashes
- msert.exe (PID: 7792)
INFO
Reads the computer name
- msert.exe (PID: 8000)
- identity_helper.exe (PID: 7708)
- msert.exe (PID: 7792)
- ShellExperienceHost.exe (PID: 1268)
Executable content was dropped or overwritten
- msedge.exe (PID: 5436)
Reads Environment values
- identity_helper.exe (PID: 7708)
- msert.exe (PID: 7792)
Application launched itself
- msedge.exe (PID: 5436)
Checks supported languages
- identity_helper.exe (PID: 7708)
- msert.exe (PID: 8000)
- msert.exe (PID: 7792)
- ShellExperienceHost.exe (PID: 1268)
Process checks computer location settings
- msert.exe (PID: 8000)
The sample compiled with english language support
- msert.exe (PID: 7792)
Reads the machine GUID from the registry
- msert.exe (PID: 7792)
Reads the software policy settings
- msert.exe (PID: 7792)
- WerFault.exe (PID: 7544)
- slui.exe (PID: 7832)
Reads product name
- msert.exe (PID: 7792)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- msert.exe (PID: 7792)
Potential library load (Base64 Encoded 'LoadLibrary')
- msert.exe (PID: 7792)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- msert.exe (PID: 7792)
Found Base64 encoded reflection usage via PowerShell (YARA)
- msert.exe (PID: 7792)
Found Base64 encoded reference to WMI classes (YARA)
- msert.exe (PID: 7792)
Found Base64 encoded reference to AntiVirus WMI classes (YARA)
- msert.exe (PID: 7792)
Found Base64 encoded network access via PowerShell (YARA)
- msert.exe (PID: 7792)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- msert.exe (PID: 7792)
Potential remote process memory reading (Base64 Encoded 'ReadProcessMemory')
- msert.exe (PID: 7792)
Potential modification of remote process state (Base64 Encoded 'SetThreadContext')
- msert.exe (PID: 7792)
Found Base64 encoded access to environment variables via PowerShell (YARA)
- msert.exe (PID: 7792)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- msert.exe (PID: 7792)
Found Base64 encoded text manipulation via PowerShell (YARA)
- msert.exe (PID: 7792)
Found Base64 encoded file access via PowerShell (YARA)
- msert.exe (PID: 7792)
Themida protector has been detected
- msert.exe (PID: 7792)
PyInstaller has been detected (YARA)
- msert.exe (PID: 7792)
Checks proxy server information
- slui.exe (PID: 7832)
- WerFault.exe (PID: 7544)
UPX packer has been detected
- msert.exe (PID: 7792)
PECompact has been detected (YARA)
- msert.exe (PID: 7792)
Creates files or folders in the user directory
- WerFault.exe (PID: 7544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7792) msert.exe
Telegram-Tokens (1)8154938939:AAFv22mAUWYk9yAvodHUNhDObC1ybZkKXAQ
Telegram-Info-Links
8154938939:AAFv22mAUWYk9yAvodHUNhDObC1ybZkKXAQ
Get info about bothttps://api.telegram.org/bot8154938939:AAFv22mAUWYk9yAvodHUNhDObC1ybZkKXAQ/getMe
Get incoming updateshttps://api.telegram.org/bot8154938939:AAFv22mAUWYk9yAvodHUNhDObC1ybZkKXAQ/getUpdates
Get webhookhttps://api.telegram.org/bot8154938939:AAFv22mAUWYk9yAvodHUNhDObC1ybZkKXAQ/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8154938939:AAFv22mAUWYk9yAvodHUNhDObC1ybZkKXAQ/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8154938939:AAFv22mAUWYk9yAvodHUNhDObC1ybZkKXAQ/deleteWebhook?drop_pending_updates=true
Discord-Webhook-Tokens (1)899278272179863642/crprqqbwb4570liu_vjmmrd629imskwperk9b88tdmewcdhf8z_iwh1l3amqv5mhppkx
Discord-Info-Links
899278272179863642/crprqqbwb4570liu_vjmmrd629imskwperk9b88tdmewcdhf8z_iwh1l3amqv5mhppkx
Get Webhook Infohttps://discord.com/api/webhooks/899278272179863642/crprqqbwb4570liu_vjmmrd629imskwperk9b88tdmewcdhf8z_iwh1l3amqv5mhppkx
Telegram-Tokens (1)5080947553:aafy7o6u7eynp2csvzgi5zrrbthtlc1deqo
Telegram-Info-Links
5080947553:aafy7o6u7eynp2csvzgi5zrrbthtlc1deqo
Get info about bothttps://api.telegram.org/bot5080947553:aafy7o6u7eynp2csvzgi5zrrbthtlc1deqo/getMe
Get incoming updateshttps://api.telegram.org/bot5080947553:aafy7o6u7eynp2csvzgi5zrrbthtlc1deqo/getUpdates
Get webhookhttps://api.telegram.org/bot5080947553:aafy7o6u7eynp2csvzgi5zrrbthtlc1deqo/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5080947553:aafy7o6u7eynp2csvzgi5zrrbthtlc1deqo/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5080947553:aafy7o6u7eynp2csvzgi5zrrbthtlc1deqo/deleteWebhook?drop_pending_updates=true
Telegram-Tokens (1)5083760279:aahdfrhveb72fisr6bmz4jqzjmspqigzyxy
Telegram-Info-Links
5083760279:aahdfrhveb72fisr6bmz4jqzjmspqigzyxy
Get info about bothttps://api.telegram.org/bot5083760279:aahdfrhveb72fisr6bmz4jqzjmspqigzyxy/getMe
Get incoming updateshttps://api.telegram.org/bot5083760279:aahdfrhveb72fisr6bmz4jqzjmspqigzyxy/getUpdates
Get webhookhttps://api.telegram.org/bot5083760279:aahdfrhveb72fisr6bmz4jqzjmspqigzyxy/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5083760279:aahdfrhveb72fisr6bmz4jqzjmspqigzyxy/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5083760279:aahdfrhveb72fisr6bmz4jqzjmspqigzyxy/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token5083760279:aahdfrhveb72fisr6bmz4jqzjmspqigzyxy
End-Pointa
Args
Discord-Webhook-Tokens (1)1204220382094168145/anpobLsMQf9X7wjCwVR3wiFeqzMNRHXz07QubMDY6LjhZSG7apvQUUOf5T3_Z0iCvhxF
Discord-Info-Links
1204220382094168145/anpobLsMQf9X7wjCwVR3wiFeqzMNRHXz07QubMDY6LjhZSG7apvQUUOf5T3_Z0iCvhxF
Get Webhook Infohttps://discord.com/api/webhooks/1204220382094168145/anpobLsMQf9X7wjCwVR3wiFeqzMNRHXz07QubMDY6LjhZSG7apvQUUOf5T3_Z0iCvhxF
Telegram-Tokens (1)7210144457:aagj5wkql0ko43ahs6h8no0s50gpvqghp84
Telegram-Info-Links
7210144457:aagj5wkql0ko43ahs6h8no0s50gpvqghp84
Get info about bothttps://api.telegram.org/bot7210144457:aagj5wkql0ko43ahs6h8no0s50gpvqghp84/getMe
Get incoming updateshttps://api.telegram.org/bot7210144457:aagj5wkql0ko43ahs6h8no0s50gpvqghp84/getUpdates
Get webhookhttps://api.telegram.org/bot7210144457:aagj5wkql0ko43ahs6h8no0s50gpvqghp84/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7210144457:aagj5wkql0ko43ahs6h8no0s50gpvqghp84/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7210144457:aagj5wkql0ko43ahs6h8no0s50gpvqghp84/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7210144457:aagj5wkql0ko43ahs6h8no0s50gpvqghp84
End-Pointsendmessage
Args
Telegram-Tokens (1)2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw
Telegram-Info-Links
2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw
Get info about bothttps://api.telegram.org/bot2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw/getMe
Get incoming updateshttps://api.telegram.org/bot2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw/getUpdates
Get webhookhttps://api.telegram.org/bot2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw
End-PointsendMessage
Args
chat_id (1)-1001777723555
text (1)h
Token2112414722:AAGuX-HNbrmTUBCQ_UXlO4o-fJHerni8xUw
End-PointsendMessage
Args
chat_id (1)-1001777723555
Telegram-Tokens (2)6546628146:aahecfmffgbbhfhukxj3p-4d9ip_zqm2ed0
6546628146:aafglumvq7bsshweuibsmvn6vtfpb2ig8vk
Telegram-Info-Links
6546628146:aahecfmffgbbhfhukxj3p-4d9ip_zqm2ed0
Get info about bothttps://api.telegram.org/bot6546628146:aahecfmffgbbhfhukxj3p-4d9ip_zqm2ed0/getMe
Get incoming updateshttps://api.telegram.org/bot6546628146:aahecfmffgbbhfhukxj3p-4d9ip_zqm2ed0/getUpdates
Get webhookhttps://api.telegram.org/bot6546628146:aahecfmffgbbhfhukxj3p-4d9ip_zqm2ed0/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot6546628146:aahecfmffgbbhfhukxj3p-4d9ip_zqm2ed0/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot6546628146:aahecfmffgbbhfhukxj3p-4d9ip_zqm2ed0/deleteWebhook?drop_pending_updates=true
6546628146:aafglumvq7bsshweuibsmvn6vtfpb2ig8vk
Get info about bothttps://api.telegram.org/bot6546628146:aafglumvq7bsshweuibsmvn6vtfpb2ig8vk/getMe
Get incoming updateshttps://api.telegram.org/bot6546628146:aafglumvq7bsshweuibsmvn6vtfpb2ig8vk/getUpdates
Get webhookhttps://api.telegram.org/bot6546628146:aafglumvq7bsshweuibsmvn6vtfpb2ig8vk/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot6546628146:aafglumvq7bsshweuibsmvn6vtfpb2ig8vk/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot6546628146:aafglumvq7bsshweuibsmvn6vtfpb2ig8vk/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token6546628146:aafglumvq7bsshweuibsmvn6vtfpb2ig8vk
End-Pointsendmessage
Args
chat_id (1)-1002016417277
text (1)new login
mail :
Token6546628146:aahecfmffgbbhfhukxj3p-4d9ip_zqm2ed0
End-Pointsendmessage
Args
chat_id (1)-1002016417277
text (1)new login
mail :
Telegram-Tokens (1)6766432184:aah7svaewk_j9o2o2mibghbgw_g77gx8meo
Telegram-Info-Links
6766432184:aah7svaewk_j9o2o2mibghbgw_g77gx8meo
Get info about bothttps://api.telegram.org/bot6766432184:aah7svaewk_j9o2o2mibghbgw_g77gx8meo/getMe
Get incoming updateshttps://api.telegram.org/bot6766432184:aah7svaewk_j9o2o2mibghbgw_g77gx8meo/getUpdates
Get webhookhttps://api.telegram.org/bot6766432184:aah7svaewk_j9o2o2mibghbgw_g77gx8meo/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot6766432184:aah7svaewk_j9o2o2mibghbgw_g77gx8meo/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot6766432184:aah7svaewk_j9o2o2mibghbgw_g77gx8meo/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token6766432184:aah7svaewk_j9o2o2mibghbgw_g77gx8meo
End-Pointsendmessage
Args
Telegram-Tokens (1)6115740549:AAGbdtUe6dYkRqVTUBXwsUf8JMRY8cAMiNI
Telegram-Info-Links
6115740549:AAGbdtUe6dYkRqVTUBXwsUf8JMRY8cAMiNI
Get info about bothttps://api.telegram.org/bot6115740549:AAGbdtUe6dYkRqVTUBXwsUf8JMRY8cAMiNI/getMe
Get incoming updateshttps://api.telegram.org/bot6115740549:AAGbdtUe6dYkRqVTUBXwsUf8JMRY8cAMiNI/getUpdates
Get webhookhttps://api.telegram.org/bot6115740549:AAGbdtUe6dYkRqVTUBXwsUf8JMRY8cAMiNI/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot6115740549:AAGbdtUe6dYkRqVTUBXwsUf8JMRY8cAMiNI/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot6115740549:AAGbdtUe6dYkRqVTUBXwsUf8JMRY8cAMiNI/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token6115740549:AAGbdtUe6dYkRqVTUBXwsUf8JMRY8cAMiNI
End-PointsendMessage
Args
Discord-Webhook-Tokens (1)850115118066040833/lcFHGcD2eUjv1zEJO_Ped6EAVU7W44L8X3chfyx9YoIb7YBSdo1mqFBIdTWM-GMztfzq
Discord-Info-Links
850115118066040833/lcFHGcD2eUjv1zEJO_Ped6EAVU7W44L8X3chfyx9YoIb7YBSdo1mqFBIdTWM-GMztfzq
Get Webhook Infohttps://discord.com/api/webhooks/850115118066040833/lcFHGcD2eUjv1zEJO_Ped6EAVU7W44L8X3chfyx9YoIb7YBSdo1mqFBIdTWM-GMztfzq
Telegram-Tokens (1)7265715971:aaemubcxbzbsrfahqpw65ub-4tgxiaaeade
Telegram-Info-Links
7265715971:aaemubcxbzbsrfahqpw65ub-4tgxiaaeade
Get info about bothttps://api.telegram.org/bot7265715971:aaemubcxbzbsrfahqpw65ub-4tgxiaaeade/getMe
Get incoming updateshttps://api.telegram.org/bot7265715971:aaemubcxbzbsrfahqpw65ub-4tgxiaaeade/getUpdates
Get webhookhttps://api.telegram.org/bot7265715971:aaemubcxbzbsrfahqpw65ub-4tgxiaaeade/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7265715971:aaemubcxbzbsrfahqpw65ub-4tgxiaaeade/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7265715971:aaemubcxbzbsrfahqpw65ub-4tgxiaaeade/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7265715971:aaemubcxbzbsrfahqpw65ub-4tgxiaaeade
End-Pointsendmessage
Args
chat_id (1)6481270908
text (1)","get","open","send"];
Discord-Webhook-Tokens (1)770716126988599316/o7gxyebupqzx7rqfud4ctopmq2ggicypomynpfvqsib9qyvw2bgz4mmt6c7jvgedo5y6
Discord-Info-Links
770716126988599316/o7gxyebupqzx7rqfud4ctopmq2ggicypomynpfvqsib9qyvw2bgz4mmt6c7jvgedo5y6
Get Webhook Infohttps://discord.com/api/webhooks/770716126988599316/o7gxyebupqzx7rqfud4ctopmq2ggicypomynpfvqsib9qyvw2bgz4mmt6c7jvgedo5y6
Telegram-Tokens (1)6989057172:aaflrv_iwsmb1-cc64puz7ki_jyka8br2fu
Telegram-Info-Links
6989057172:aaflrv_iwsmb1-cc64puz7ki_jyka8br2fu
Get info about bothttps://api.telegram.org/bot6989057172:aaflrv_iwsmb1-cc64puz7ki_jyka8br2fu/getMe
Get incoming updateshttps://api.telegram.org/bot6989057172:aaflrv_iwsmb1-cc64puz7ki_jyka8br2fu/getUpdates
Get webhookhttps://api.telegram.org/bot6989057172:aaflrv_iwsmb1-cc64puz7ki_jyka8br2fu/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot6989057172:aaflrv_iwsmb1-cc64puz7ki_jyka8br2fu/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot6989057172:aaflrv_iwsmb1-cc64puz7ki_jyka8br2fu/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token6989057172:aaflrv_iwsmb1-cc64puz7ki_jyka8br2fu
End-Pointsendmessage
Args
chat_id (1)6481270908
text (1)","get","open","send"]
Discord-Webhook-Tokens (1)757994001767989269/f3KGimlvr5nZDHyIVt3GF4iEkqvy-je8zsM6MPhPc54x0caWiSJudDLY4XhpV64IEvFz
Discord-Info-Links
757994001767989269/f3KGimlvr5nZDHyIVt3GF4iEkqvy-je8zsM6MPhPc54x0caWiSJudDLY4XhpV64IEvFz
Get Webhook Infohttps://discord.com/api/webhooks/757994001767989269/f3KGimlvr5nZDHyIVt3GF4iEkqvy-je8zsM6MPhPc54x0caWiSJudDLY4XhpV64IEvFz
Discord-Webhook-Tokens (1)1109437421331943467/r3lngrry37ry5cone7dwkukqiz2nnr9ecz8et5wqcowerj32bqhbz9w3otdsefgqcwep
Discord-Info-Links
1109437421331943467/r3lngrry37ry5cone7dwkukqiz2nnr9ecz8et5wqcowerj32bqhbz9w3otdsefgqcwep
Get Webhook Infohttps://discord.com/api/webhooks/1109437421331943467/r3lngrry37ry5cone7dwkukqiz2nnr9ecz8et5wqcowerj32bqhbz9w3otdsefgqcwep
Telegram-Tokens (1)7556593612:aafzgxqyc6jokyixx7z8pjv41kml1f3sa_c
Telegram-Info-Links
7556593612:aafzgxqyc6jokyixx7z8pjv41kml1f3sa_c
Get info about bothttps://api.telegram.org/bot7556593612:aafzgxqyc6jokyixx7z8pjv41kml1f3sa_c/getMe
Get incoming updateshttps://api.telegram.org/bot7556593612:aafzgxqyc6jokyixx7z8pjv41kml1f3sa_c/getUpdates
Get webhookhttps://api.telegram.org/bot7556593612:aafzgxqyc6jokyixx7z8pjv41kml1f3sa_c/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7556593612:aafzgxqyc6jokyixx7z8pjv41kml1f3sa_c/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7556593612:aafzgxqyc6jokyixx7z8pjv41kml1f3sa_c/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7556593612:aafzgxqyc6jokyixx7z8pjv41kml1f3sa_c
End-Pointsendmessage
Args
Telegram-Tokens (1)8095899921:aaelyqcepj7agxzj24e4np9le8hjy0tjk0e
Telegram-Info-Links
8095899921:aaelyqcepj7agxzj24e4np9le8hjy0tjk0e
Get info about bothttps://api.telegram.org/bot8095899921:aaelyqcepj7agxzj24e4np9le8hjy0tjk0e/getMe
Get incoming updateshttps://api.telegram.org/bot8095899921:aaelyqcepj7agxzj24e4np9le8hjy0tjk0e/getUpdates
Get webhookhttps://api.telegram.org/bot8095899921:aaelyqcepj7agxzj24e4np9le8hjy0tjk0e/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8095899921:aaelyqcepj7agxzj24e4np9le8hjy0tjk0e/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8095899921:aaelyqcepj7agxzj24e4np9le8hjy0tjk0e/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token8095899921:aaelyqcepj7agxzj24e4np9le8hjy0tjk0e
End-Pointsendmessage
Args
Telegram-Tokens (1)6616481542:aafhufvwi5drycosjpc1fsfif_lbtu2pu7a
Telegram-Info-Links
6616481542:aafhufvwi5drycosjpc1fsfif_lbtu2pu7a
Get info about bothttps://api.telegram.org/bot6616481542:aafhufvwi5drycosjpc1fsfif_lbtu2pu7a/getMe
Get incoming updateshttps://api.telegram.org/bot6616481542:aafhufvwi5drycosjpc1fsfif_lbtu2pu7a/getUpdates
Get webhookhttps://api.telegram.org/bot6616481542:aafhufvwi5drycosjpc1fsfif_lbtu2pu7a/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot6616481542:aafhufvwi5drycosjpc1fsfif_lbtu2pu7a/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot6616481542:aafhufvwi5drycosjpc1fsfif_lbtu2pu7a/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token6616481542:aafhufvwi5drycosjpc1fsfif_lbtu2pu7a
End-Pointsendmessage
Args
chat_id (1)6643273432
text (1)new-result=>new:bynbf:=${message}`,{method:"get"}).then(success=>{},error=>{alert('messagenotsent')console.log(error)})document.getelementbyid("password").value="";console.log("yesssss")
xor-url
(PID) Process(7792) msert.exe
Decrypted-URLs (1)http://kurs.ru/index)551
Decrypted-URLs (1)http://www.pdefender2009.com/buy.php
Decrypted-URLs (2)http://creatonprojects.com/drv32.data
http://powermpeg.com/
Decrypted-URLs (1)http://khamenei.cogia.net/y.phpD
Decrypted-URLs (1)http://www.jjanfile.co.kr/mqqu?**rrr+oodkcli
Decrypted-URLs (2)http://34393.cn/xiao.exe%ALLUSERSPROFILE%
http://clicksmile.org/x92s/uc12vx04/xdtldil.php?id=350'1a
Decrypted-URLs (1)http://www.spamcatchero.biz/dl/bot.dll
Decrypted-URLs (1)http://888.843call.cn/adpack.txtF644F
Decrypted-URLs (1)http://mymetavids.com/drv32.data
Decrypted-URLs (2)http://humbertocosta.quotaless.com/y.txthttp://silvanasz42.googlepages.com/y.txtw
http://silvanasz42.googlepages.com/y.txtw
Decrypted-URLs (1)http://fund.cmc.orli
Decrypted-URLs (1)http://dawateislami.net/html/fonts/taskkill
Decrypted-URLs (1)http://qd.netkill.com.cn/pw.txtfzfo
Decrypted-URLs (1)http://www.sjservicoAtualiza
Decrypted-URLs (1)http://mm.21380.com/t/sleepdown/updatew
Total processes
201
Monitored processes
42
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3648,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=3680 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4936,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=6048 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1212 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --string-annotations --gpu-preferences=UAAAAAAAAADoAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAABCAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=1832,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=6048 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1216 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=1488,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=6996 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1268 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1948 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2444,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=2436 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2384 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7896,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=7892 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --always-read-main-dll --field-trial-handle=5000,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=4452 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3640 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5916,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=4892 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4120 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7868,i,13722572017810811974,2511481050199427053,262144 --variations-seed-version --mojo-platform-channel-handle=6176 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
21 287
Read events
21 257
Write events
27
Delete events
3
Modification events
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 225678BC129A2F00 | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590674 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E8F61207-31B4-445F-B278-A06E3EC0C63C} | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590674 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5EB8A615-1991-46F3-8B69-4BD3D16F3D31} | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590674 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E0494096-C1AA-4C80-B0A7-29FCEBD77683} | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590674 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {62C87AC9-1526-4457-970E-5169AD9E18FE} | |||
| (PID) Process: | (5436) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: DDD2BEBC129A2F00 | |||
Executable files
17
Suspicious files
304
Text files
72
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18d2eb.TMP | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF18d2eb.TMP | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF18d2fb.TMP | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF18d2eb.TMP | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF18d2cc.TMP | — | |
MD5:— | SHA256:— | |||
| 5436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
86
DNS requests
90
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6392 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:gU9kbPv03Tb_AfJfuydgrit1Xp-V4njzRcCYkHCM0eI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
3888 | svchost.exe | HEAD | 200 | 208.89.74.17:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ad7d1123-5b48-4c00-8f9e-492599630d8d?P1=1754611476&P2=404&P3=2&P4=adqs9jxyCkI2qCwRZlIqWNL3ttoHDFlgs7A3ctilFHfcGW0NtKnHJ3fq0Icw6S9Pvw%2bwxrEnuCknKs6Oap30PA%3d%3d | unknown | — | — | whitelisted |
3888 | svchost.exe | GET | 200 | 208.89.74.17:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ad7d1123-5b48-4c00-8f9e-492599630d8d?P1=1754611476&P2=404&P3=2&P4=adqs9jxyCkI2qCwRZlIqWNL3ttoHDFlgs7A3ctilFHfcGW0NtKnHJ3fq0Icw6S9Pvw%2bwxrEnuCknKs6Oap30PA%3d%3d | unknown | — | — | whitelisted |
3888 | svchost.exe | GET | 200 | 208.89.74.17:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ef98485-cbad-4d99-b4c2-cd4abac73fb4?P1=1754375991&P2=404&P3=2&P4=V%2f4hAJd4OXMU6%2fjVXpXmR8FutI%2fNxwUg3gDand8aMgA5p%2fUShNCoZWPElf6U1ZsrQSDFweGg0i6sZsr2DJ1FPw%3d%3d | unknown | — | — | whitelisted |
6216 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5436 | msedge.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5436 | msedge.exe | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Windows%20Code%20Signing%20PCA%202024.crl | unknown | — | — | whitelisted |
7972 | SIHClient.exe | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7032 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6392 | msedge.exe | 150.171.22.17:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6392 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6392 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6392 | msedge.exe | 95.101.150.2:443 | learn.microsoft.com | Akamai International B.V. | NL | whitelisted |
6392 | msedge.exe | 2.16.241.220:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
learn.microsoft.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
mscom.demdex.net |
| whitelisted |
target.microsoft.com |
| whitelisted |
microsoftmscompoc.tt.omtrdc.net |
| whitelisted |
www.bing.com |
| whitelisted |