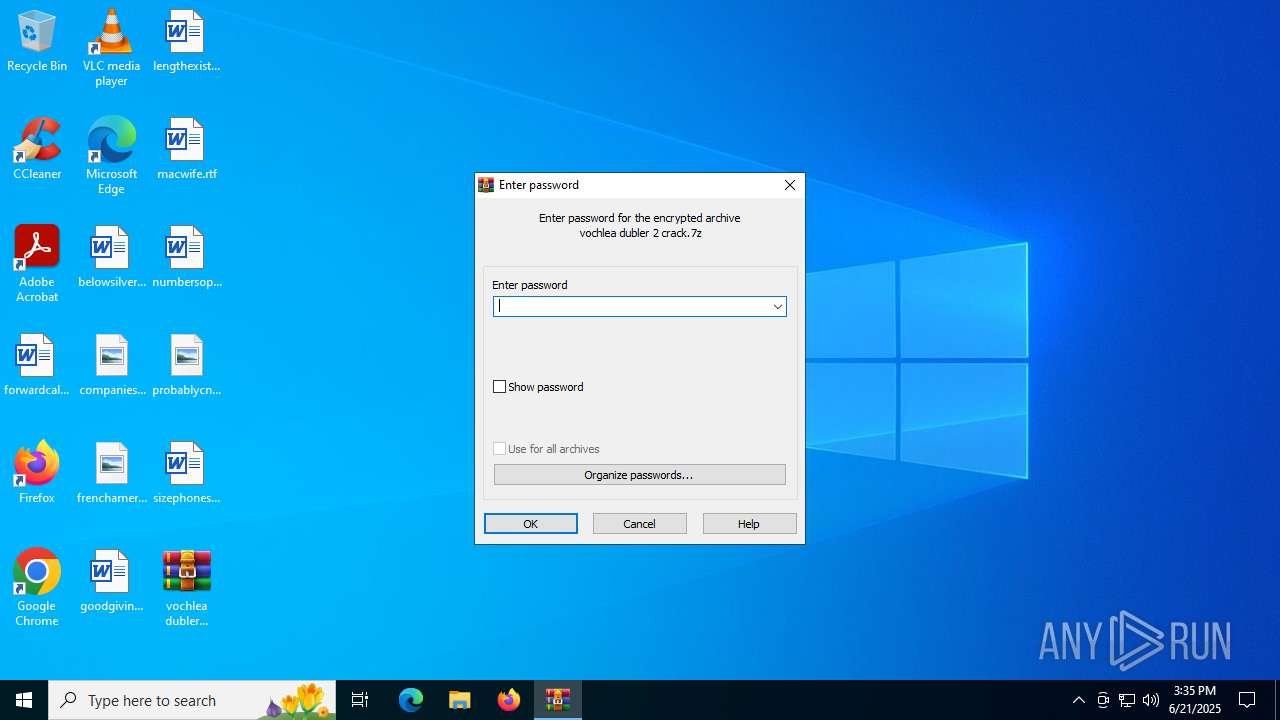
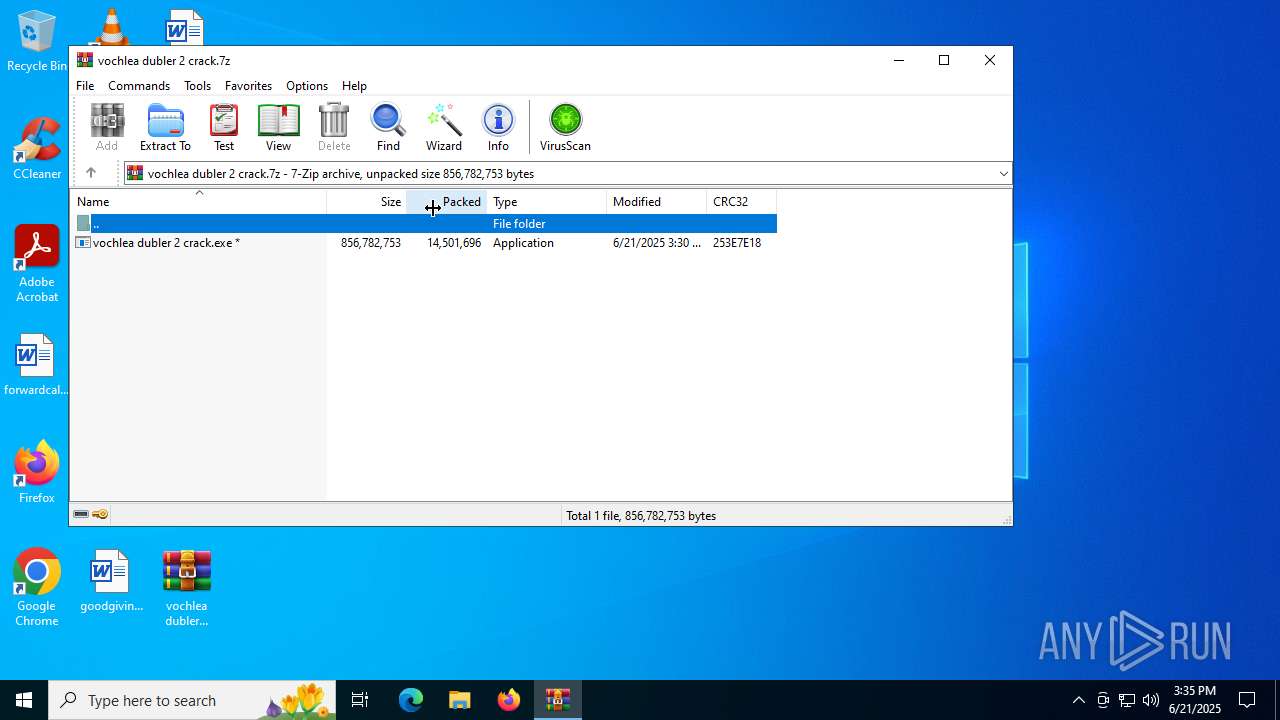
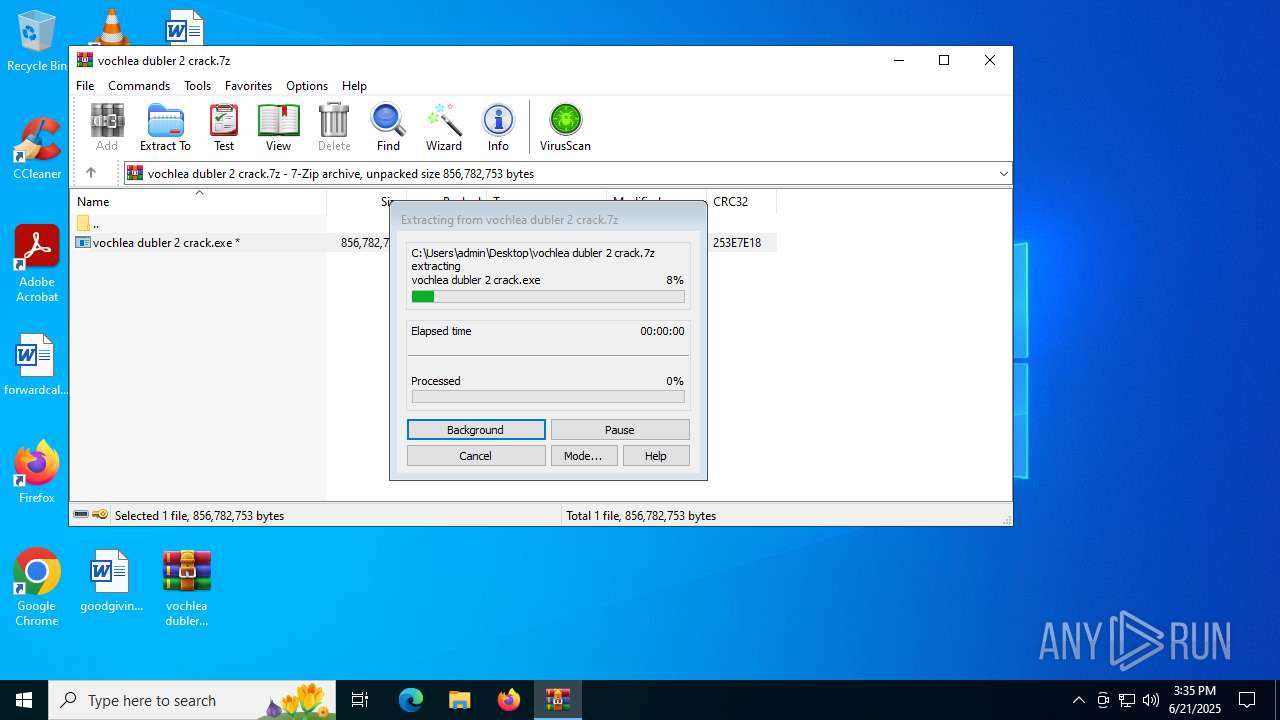
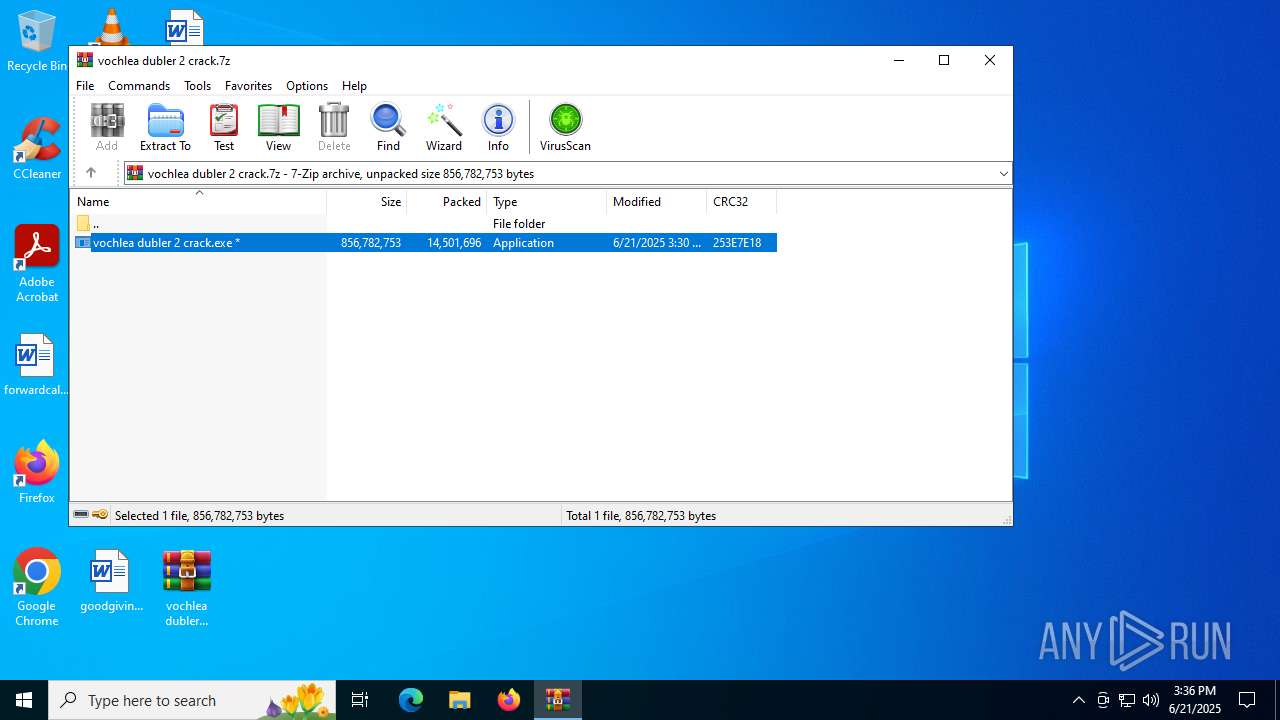
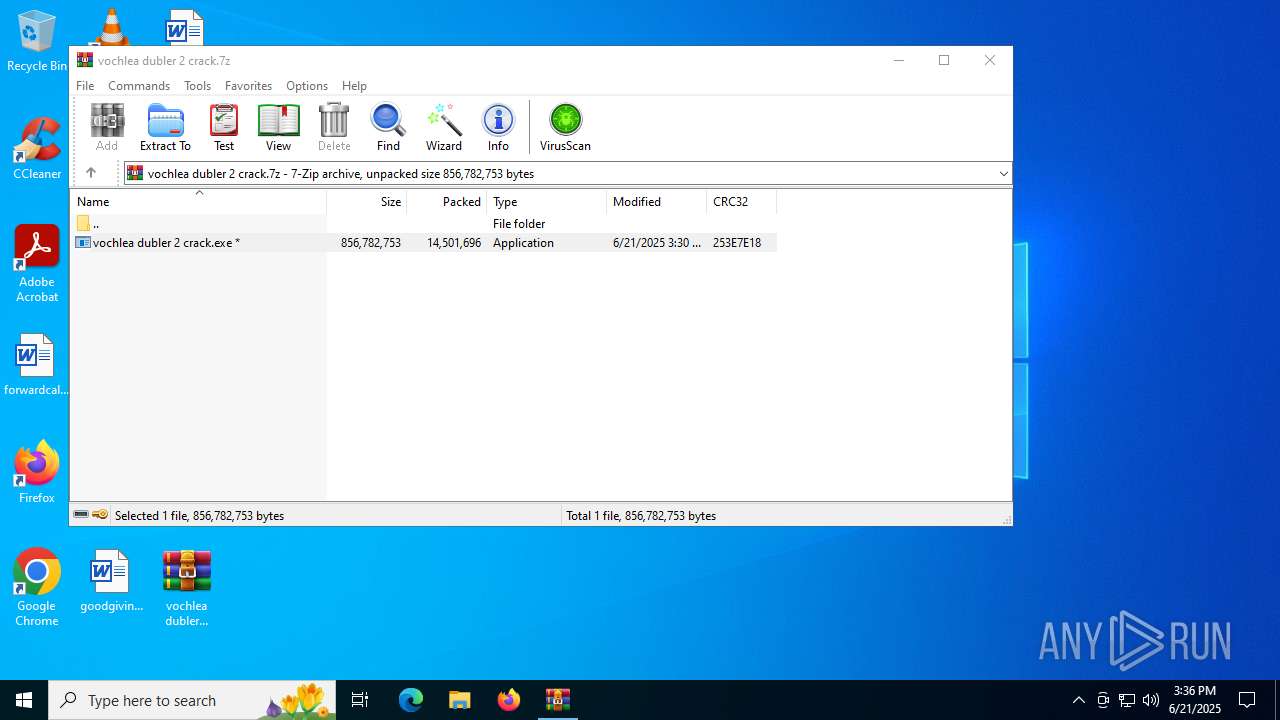
| File name: | vochlea dubler 2 crack.7z |
| Full analysis: | https://app.any.run/tasks/8469f7c0-0bee-4728-9307-7b6de288b90a |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | June 21, 2025, 15:35:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C7C7B34A4D2E8708DBACC2C5E585BBE8 |
| SHA1: | E57D6AFEA7B08E0554354D9958E45CDADF0B0C79 |
| SHA256: | EFF0EBA32DCA58B7828F36AB0B62F725CE1EB52F393DA8415EFD81CFBC2A9F9A |
| SSDEEP: | 98304:oMSArjdjN8nT6mUpdRWX+zrXOkHV7QDnexZhHxb+1W92uyBW4TbythOAIGd+sbF6:rl8pr7zX7esPxuXdHwu2wSOxE |
MALICIOUS
AutoIt loader has been detected (YARA)
- Moscow.com (PID: 6368)
LUMMA mutex has been found
- Moscow.com (PID: 6368)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6652)
- vochlea dubler 2 crack.exe (PID: 5556)
Executing commands from a ".bat" file
- vochlea dubler 2 crack.exe (PID: 5556)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7132)
Starts application with an unusual extension
- cmd.exe (PID: 7132)
Starts the AutoIt3 executable file
- cmd.exe (PID: 7132)
The executable file from the user directory is run by the CMD process
- Moscow.com (PID: 6368)
There is functionality for taking screenshot (YARA)
- Moscow.com (PID: 6368)
- vochlea dubler 2 crack.exe (PID: 5556)
Searches for installed software
- Moscow.com (PID: 6368)
Starts CMD.EXE for commands execution
- vochlea dubler 2 crack.exe (PID: 5556)
Get information on the list of running processes
- cmd.exe (PID: 7132)
INFO
Reads the computer name
- vochlea dubler 2 crack.exe (PID: 5556)
- extrac32.exe (PID: 6408)
- Moscow.com (PID: 6368)
Checks supported languages
- vochlea dubler 2 crack.exe (PID: 5556)
- Moscow.com (PID: 6368)
- extrac32.exe (PID: 6408)
Create files in a temporary directory
- extrac32.exe (PID: 6408)
- vochlea dubler 2 crack.exe (PID: 5556)
Reads mouse settings
- Moscow.com (PID: 6368)
Reads the software policy settings
- Moscow.com (PID: 6368)
- slui.exe (PID: 6732)
Checks proxy server information
- slui.exe (PID: 6732)
Reads the machine GUID from the registry
- Moscow.com (PID: 6368)
Process checks computer location settings
- vochlea dubler 2 crack.exe (PID: 5556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
147
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1212 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2160 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | choice /d n /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3672 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3740 | findstr "bdservicehost SophosHealth AvastUI AVGUI nsWscSvc ekrn" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5556 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6652.46531\vochlea dubler 2 crack.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6652.46531\vochlea dubler 2 crack.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6368 | Moscow.com K | C:\Users\admin\AppData\Local\Temp\448887\Moscow.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 6408 | extrac32 /Y Play.wp5 *.* | C:\Windows\SysWOW64\extrac32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6652 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\vochlea dubler 2 crack.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 950
Read events
5 941
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\vochlea dubler 2 crack.7z | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
20
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6652.46531\vochlea dubler 2 crack.exe | — | |
MD5:— | SHA256:— | |||
| 5556 | vochlea dubler 2 crack.exe | C:\Users\admin\AppData\Local\Temp\Mysql.wp5 | text | |
MD5:D700E104BB88001FEA6F66ECAD07BFA0 | SHA256:CE9911C4A639B88BB349F2E1E94D6A426F185BBA641B93EF93922D74E2ED387B | |||
| 5556 | vochlea dubler 2 crack.exe | C:\Users\admin\AppData\Local\Temp\Play.wp5 | compressed | |
MD5:4CCD8111EB03D462E4FA5C5D63CC8320 | SHA256:35EFC15A41CF54A51703711E0B117B1899E4698BED1A4FDAE638EBB7A3A190E0 | |||
| 5556 | vochlea dubler 2 crack.exe | C:\Users\admin\AppData\Local\Temp\Romania.wp5 | binary | |
MD5:1C989744272C401FBE8468D529100519 | SHA256:AEA644F6996780EF8D50228BD65222E0030034863401A204569A4277426BA411 | |||
| 6408 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Investors | binary | |
MD5:994020C7CAFA74B2ADD8507DE1952C63 | SHA256:D07EC16D3B6CB05590A7496B857D9D999A55E4D43CCDAB2482F193C52E01106D | |||
| 5556 | vochlea dubler 2 crack.exe | C:\Users\admin\AppData\Local\Temp\Lock.wp5 | binary | |
MD5:660F010E32A964AAB16B3603BB304728 | SHA256:B317BC29236CDB3E16BF83425840C9006397C7FC5BD0D47F21F0F1294E73FA2E | |||
| 6408 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Thanksgiving | binary | |
MD5:AC49E31B98A61C138D06870E270D3D92 | SHA256:9FD2AD4E3A67E8EEA6702F97D4A7B3642960000B0716EC911FFF167909FE36EF | |||
| 5556 | vochlea dubler 2 crack.exe | C:\Users\admin\AppData\Local\Temp\Authorization.wp5 | binary | |
MD5:DFDA57CEBDC25778F4B1E5317797009C | SHA256:8CCCD4C1FDB91FC1E16156191C52CDF9173B5722AF57AA3DB4A9063303E27615 | |||
| 6408 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Analyze | binary | |
MD5:037936BEDAA0FC900806062895F81007 | SHA256:16A9D5559DDEFBB5A084892F9879D5BE1F7859FD783670BE893D5701120816A2 | |||
| 6408 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Balls | binary | |
MD5:1C333E54BD6B076B66BE9F996ED576A9 | SHA256:AE9BBBF305C9153487093E9D0AA0A034C1EDB273A12798EE5A742FBCA19719CB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
26
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.25.50.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4520 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4520 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5012 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3876 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.25.50.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4520 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
wbVyRvhbyvEZbMqYihltOWNp.wbVyRvhbyvEZbMqYihltOWNp |
| unknown |
client.wns.windows.com |
| whitelisted |