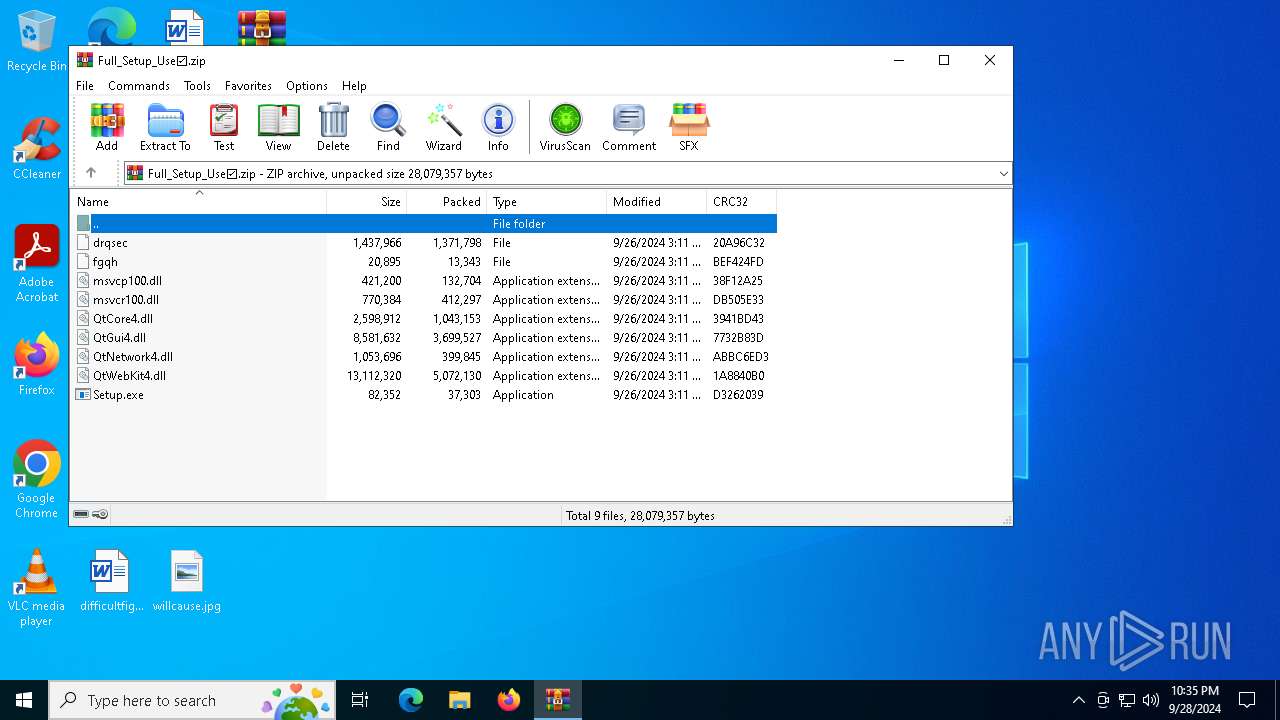
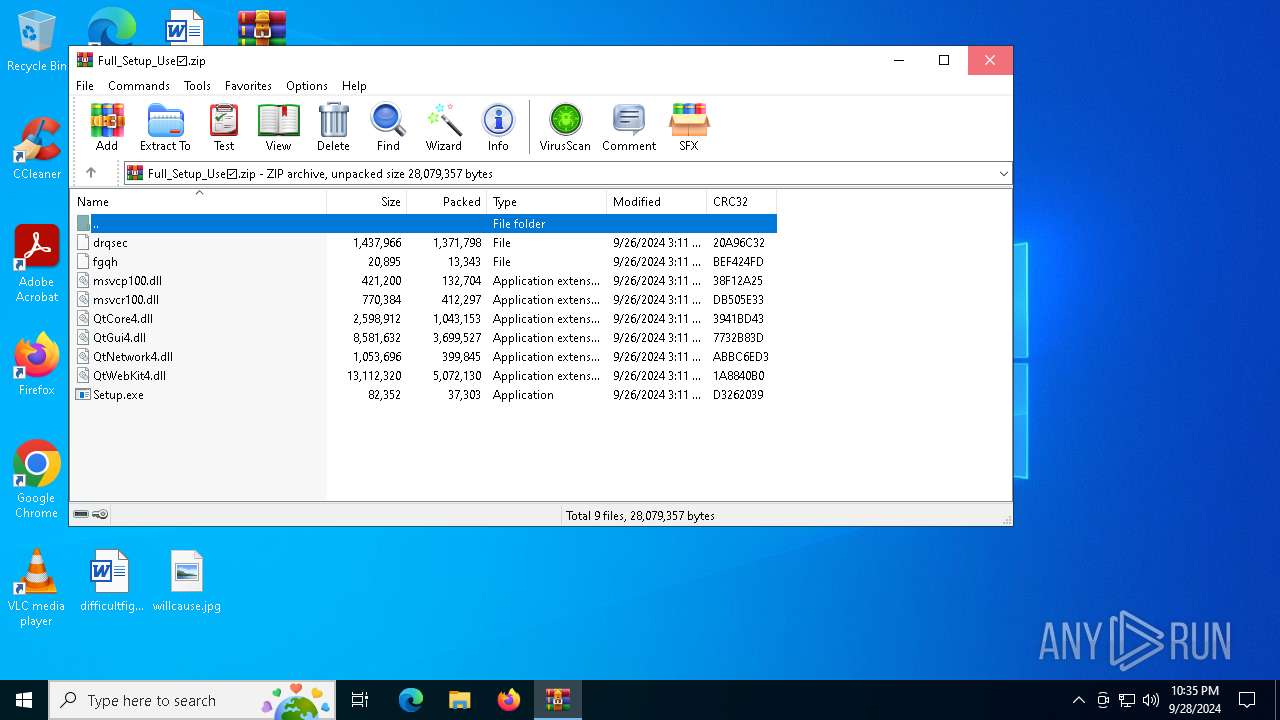
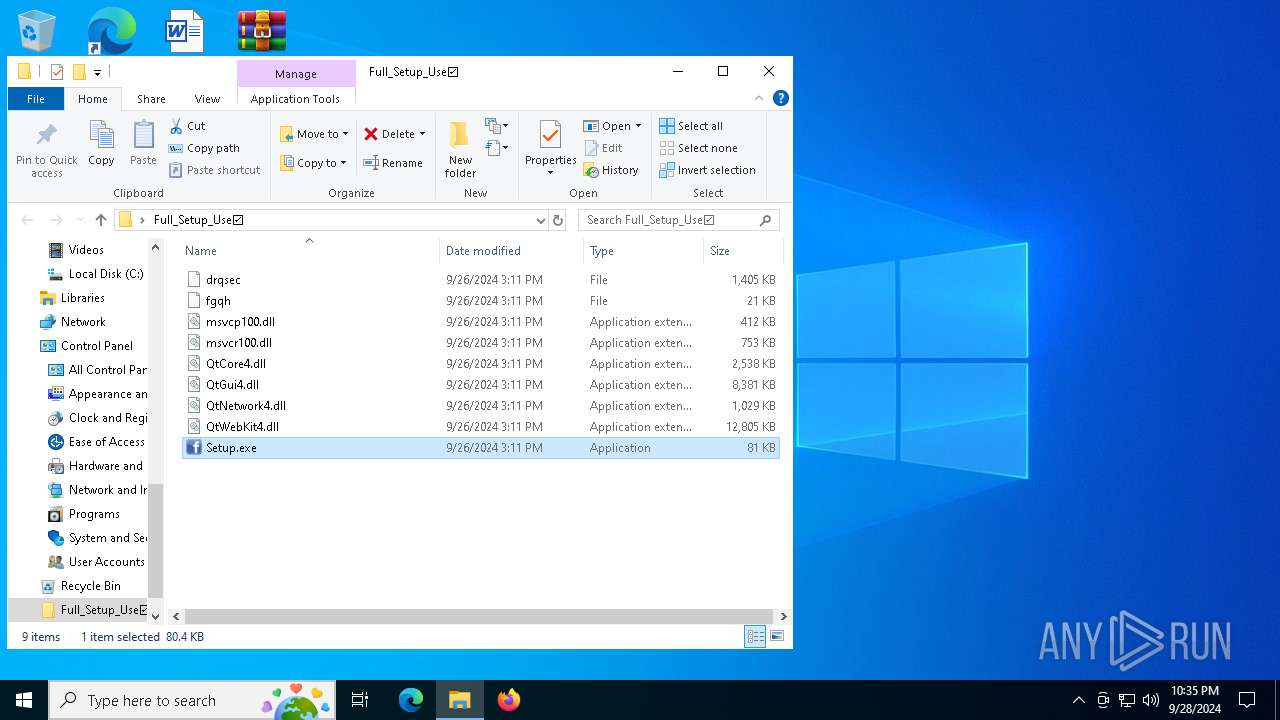
| File name: | Full_Setup_Use☑.zip |
| Full analysis: | https://app.any.run/tasks/97021a92-6022-413a-a55d-0d3da9cb2e1d |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 28, 2024, 22:35:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 09D0B75A77985D0AEB416CEABD0CEF38 |
| SHA1: | 7F8234B7196D65AC93B147EC17DF71EB5BEF3C6A |
| SHA256: | EFCC9D478BAB1C5A8DB0BDC105E7540532AFFA1C27FB93EABDF7D27BC4A44F57 |
| SSDEEP: | 98304:LSzOBjH09RmJr6YCz1F3nkHCL6Kdq7onWQqLMiCB8BstWHJXWOtlUySJh4Inf8Xw:i/MRV8abscy3hFSMYs |
MALICIOUS
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2256)
- Launcher.exe (PID: 832)
Bypass execution policy to execute commands
- powershell.exe (PID: 4976)
Connects to the CnC server
- svchost.exe (PID: 2256)
Changes powershell execution policy (Bypass)
- Launcher.exe (PID: 832)
Stealers network behavior
- Launcher.exe (PID: 832)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- Launcher.exe (PID: 832)
- svchost.exe (PID: 2256)
The process executes Powershell scripts
- Launcher.exe (PID: 832)
Starts POWERSHELL.EXE for commands execution
- Launcher.exe (PID: 832)
Process drops legitimate windows executable
- WinRAR.exe (PID: 884)
- Setup.exe (PID: 5436)
The process drops C-runtime libraries
- WinRAR.exe (PID: 884)
- Setup.exe (PID: 5436)
Executable content was dropped or overwritten
- Setup.exe (PID: 5436)
- more.com (PID: 2080)
Starts application with an unusual extension
- Setup.exe (PID: 5436)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 884)
Manual execution by a user
- Setup.exe (PID: 5436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:09:26 17:11:00 |
| ZipCRC: | 0xd3262039 |
| ZipCompressedSize: | 37303 |
| ZipUncompressedSize: | 82352 |
| ZipFileName: | Setup.exe |
Total processes
145
Monitored processes
12
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 832 | C:\Users\admin\AppData\Local\Temp\Launcher.exe | C:\Users\admin\AppData\Local\Temp\Launcher.exe | more.com | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.9.13 Modules
| |||||||||||||||
| 884 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Full_Setup_Use☑.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1020 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1504 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3384 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4172 | C:\Users\admin\AppData\Roaming\Ebnscan\MAKGAPAXDXFUKDQAJKJG\StrCmp.exe | C:\Users\admin\AppData\Roaming\Ebnscan\MAKGAPAXDXFUKDQAJKJG\StrCmp.exe | — | Setup.exe | |||||||||||
User: admin Company: aaa Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
10 881
Read events
10 848
Write events
20
Delete events
13
Modification events
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Full_Setup_Use☑.zip | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
15
Suspicious files
6
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2080 | more.com | C:\Users\admin\AppData\Local\Temp\jlbusxglb | — | |
MD5:— | SHA256:— | |||
| 884 | WinRAR.exe | C:\Users\admin\Desktop\Full_Setup_Use☑\QtGui4.dll | executable | |
MD5:831BA3A8C9D9916BDF82E07A3E8338CC | SHA256:D2C8C8B6CC783E4C00A5EF3365457D776DFC1205A346B676915E39D434F5A52D | |||
| 884 | WinRAR.exe | C:\Users\admin\Desktop\Full_Setup_Use☑\msvcp100.dll | executable | |
MD5:03E9314004F504A14A61C3D364B62F66 | SHA256:A3BA6421991241BEA9C8334B62C3088F8F131AB906C3CC52113945D05016A35F | |||
| 884 | WinRAR.exe | C:\Users\admin\Desktop\Full_Setup_Use☑\fgqh | binary | |
MD5:1D3BF701CABCA78EFBFAFE580C096A7C | SHA256:25870AEDDB4AA79F2C06B8E82DD33B7AC234243F7CEEC4F58ECB6FCE697C90F7 | |||
| 884 | WinRAR.exe | C:\Users\admin\Desktop\Full_Setup_Use☑\QtNetwork4.dll | executable | |
MD5:8A2E025FD3DDD56C8E4F63416E46E2EC | SHA256:52AE07D1D6A467283055A3512D655B6A43A42767024E57279784701206D97003 | |||
| 5436 | Setup.exe | C:\Users\admin\AppData\Roaming\Ebnscan\msvcr100.dll | executable | |
MD5:67EC459E42D3081DD8FD34356F7CAFC1 | SHA256:1221A09484964A6F38AF5E34EE292B9AFEFCCB3DC6E55435FD3AAF7C235D9067 | |||
| 884 | WinRAR.exe | C:\Users\admin\Desktop\Full_Setup_Use☑\msvcr100.dll | executable | |
MD5:67EC459E42D3081DD8FD34356F7CAFC1 | SHA256:1221A09484964A6F38AF5E34EE292B9AFEFCCB3DC6E55435FD3AAF7C235D9067 | |||
| 5436 | Setup.exe | C:\Users\admin\AppData\Roaming\Ebnscan\QtNetwork4.dll | executable | |
MD5:8A2E025FD3DDD56C8E4F63416E46E2EC | SHA256:52AE07D1D6A467283055A3512D655B6A43A42767024E57279784701206D97003 | |||
| 5436 | Setup.exe | C:\Users\admin\AppData\Roaming\Ebnscan\drqsec | abr | |
MD5:A1B321CB827F7E441D474BC6CAFAB0F5 | SHA256:1DAA5E427EDDB24B76889CC16CD2FE6A9F0B65C127994506B7584C41E683935D | |||
| 5436 | Setup.exe | C:\Users\admin\AppData\Roaming\Ebnscan\QtGui4.dll | executable | |
MD5:831BA3A8C9D9916BDF82E07A3E8338CC | SHA256:D2C8C8B6CC783E4C00A5EF3365457D776DFC1205A346B676915E39D434F5A52D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
72
DNS requests
25
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2280 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5664 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3688 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3852 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3688 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2280 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5664 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.213.170.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6664 | svchost.exe | 23.213.170.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5664 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
google.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (gutterydhowi .shop) |
832 | Launcher.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (gutterydhowi .shop in TLS SNI) |
832 | Launcher.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
832 | Launcher.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (gutterydhowi .shop in TLS SNI) |
832 | Launcher.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (gutterydhowi .shop in TLS SNI) |
832 | Launcher.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (gutterydhowi .shop in TLS SNI) |
832 | Launcher.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (gutterydhowi .shop in TLS SNI) |
832 | Launcher.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (gutterydhowi .shop in TLS SNI) |
2256 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
832 | Launcher.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |