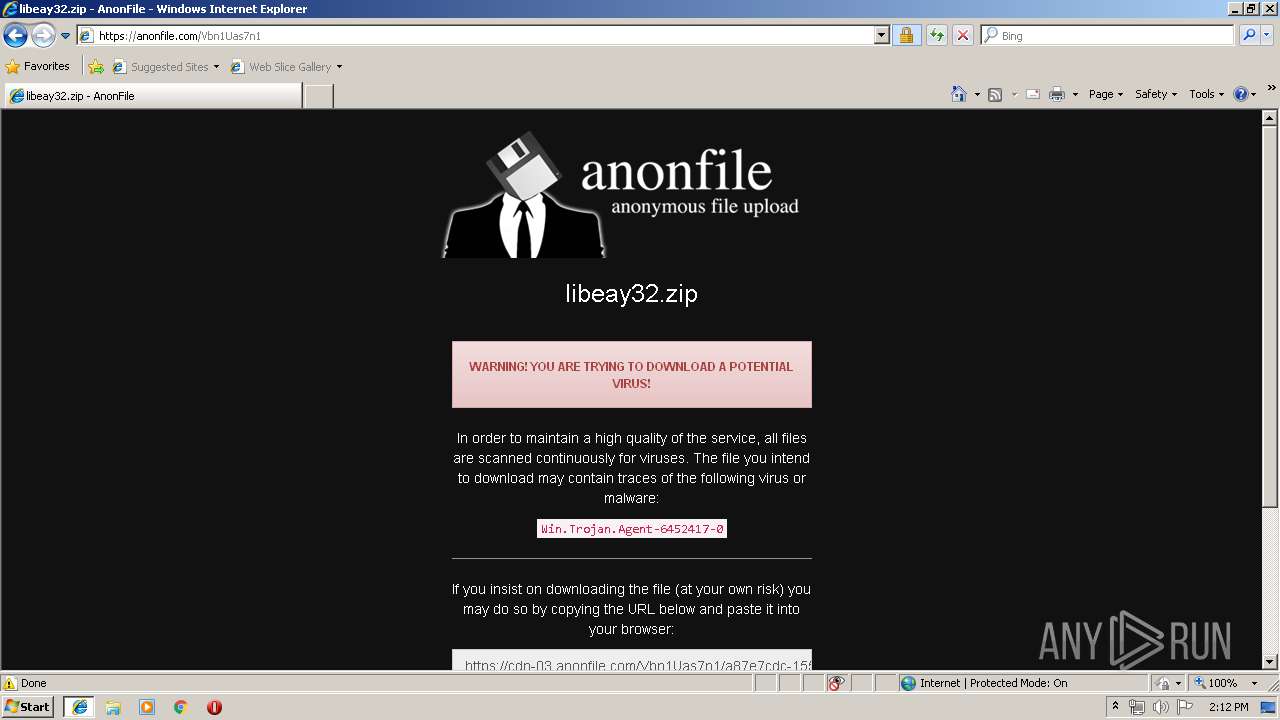
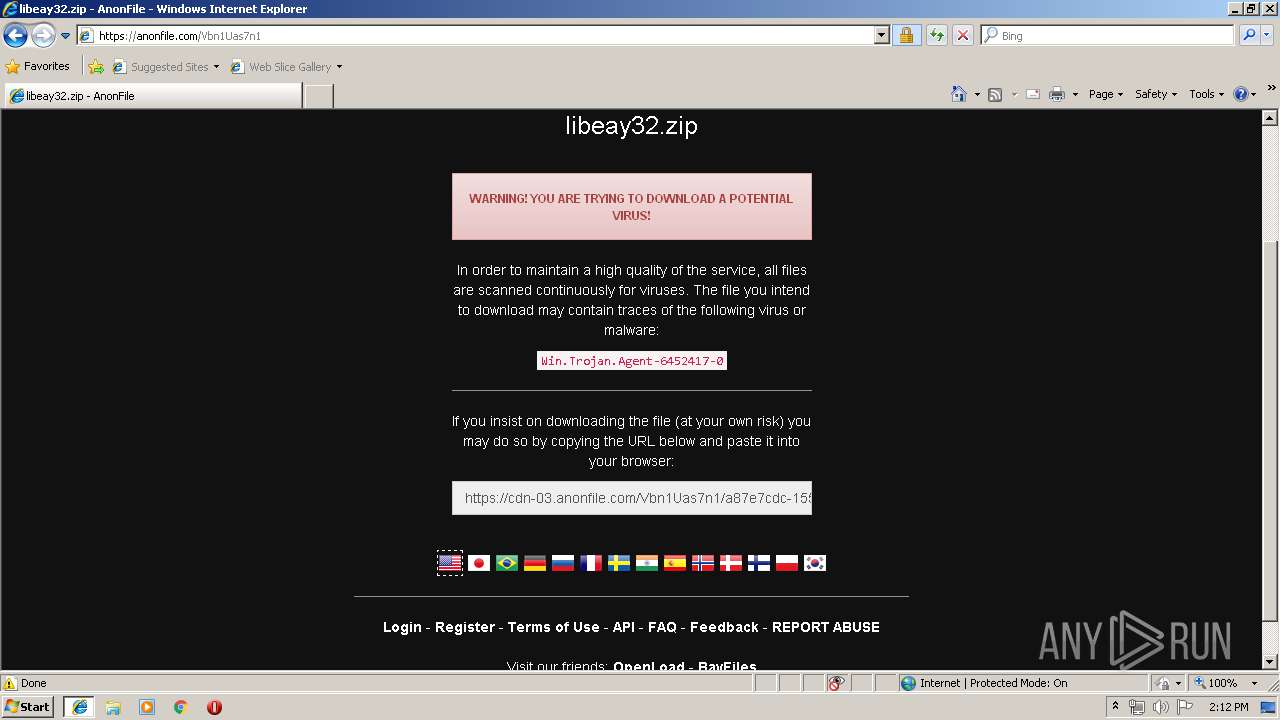
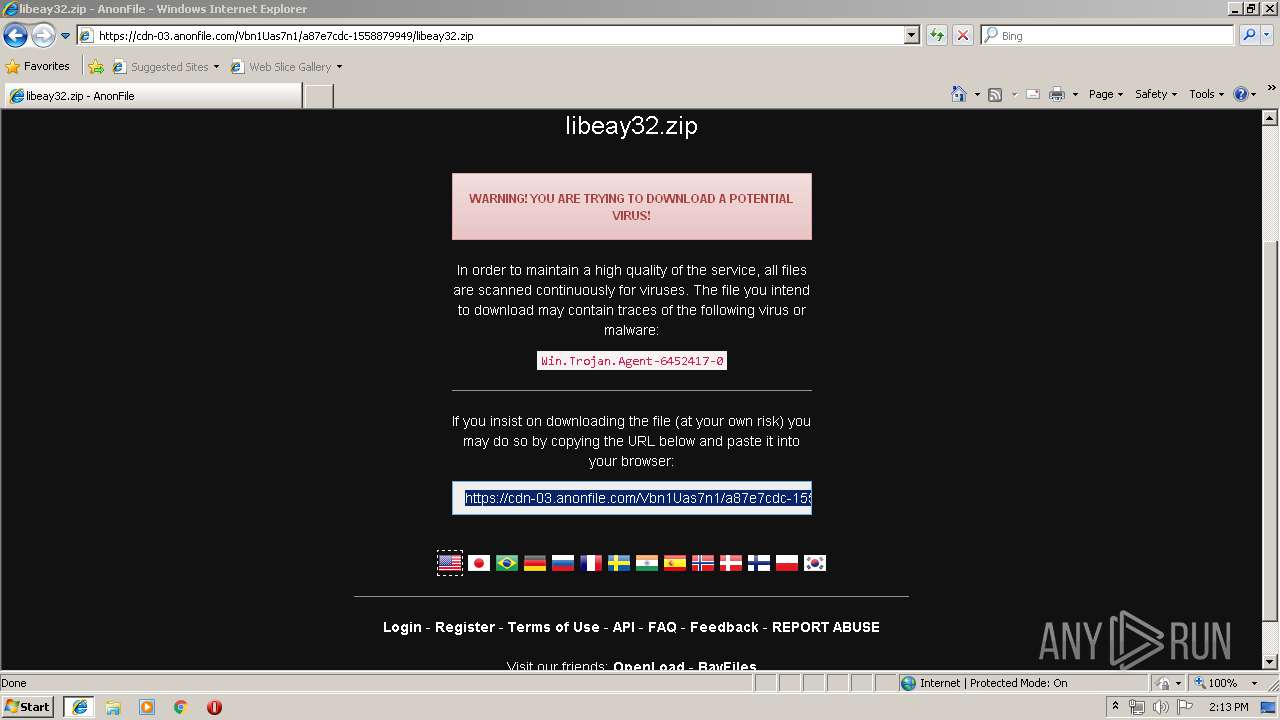
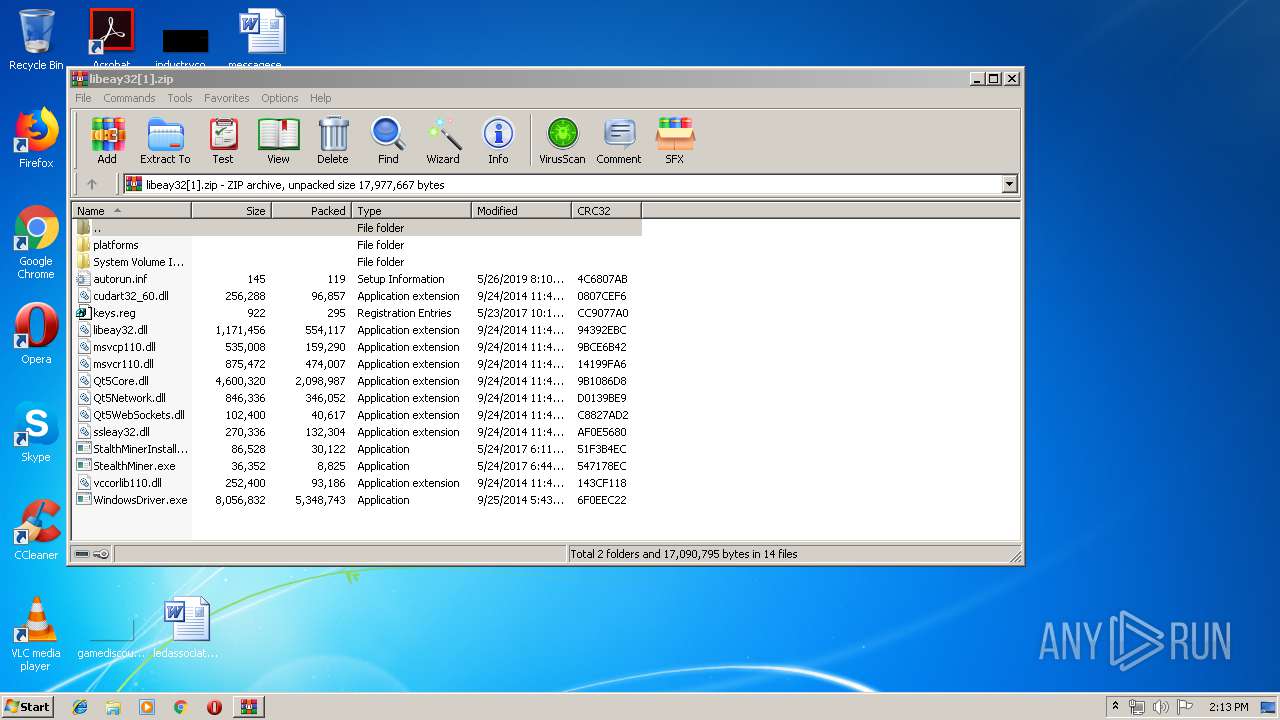
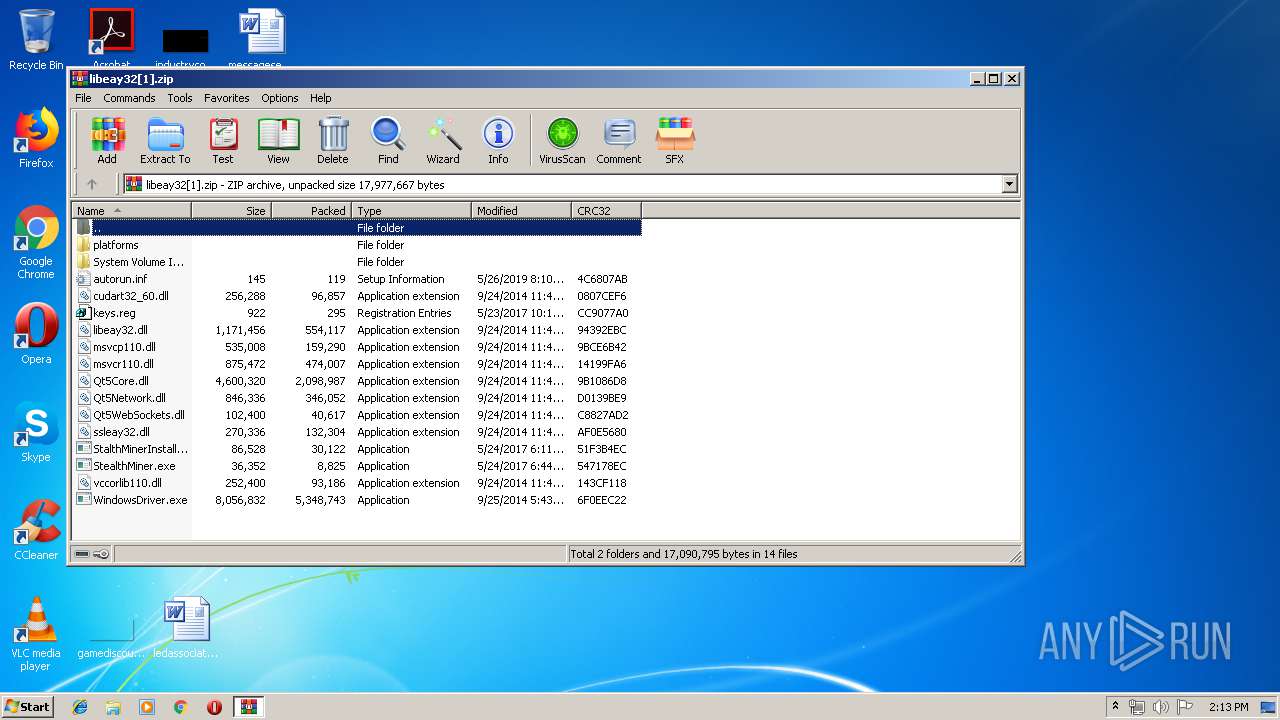
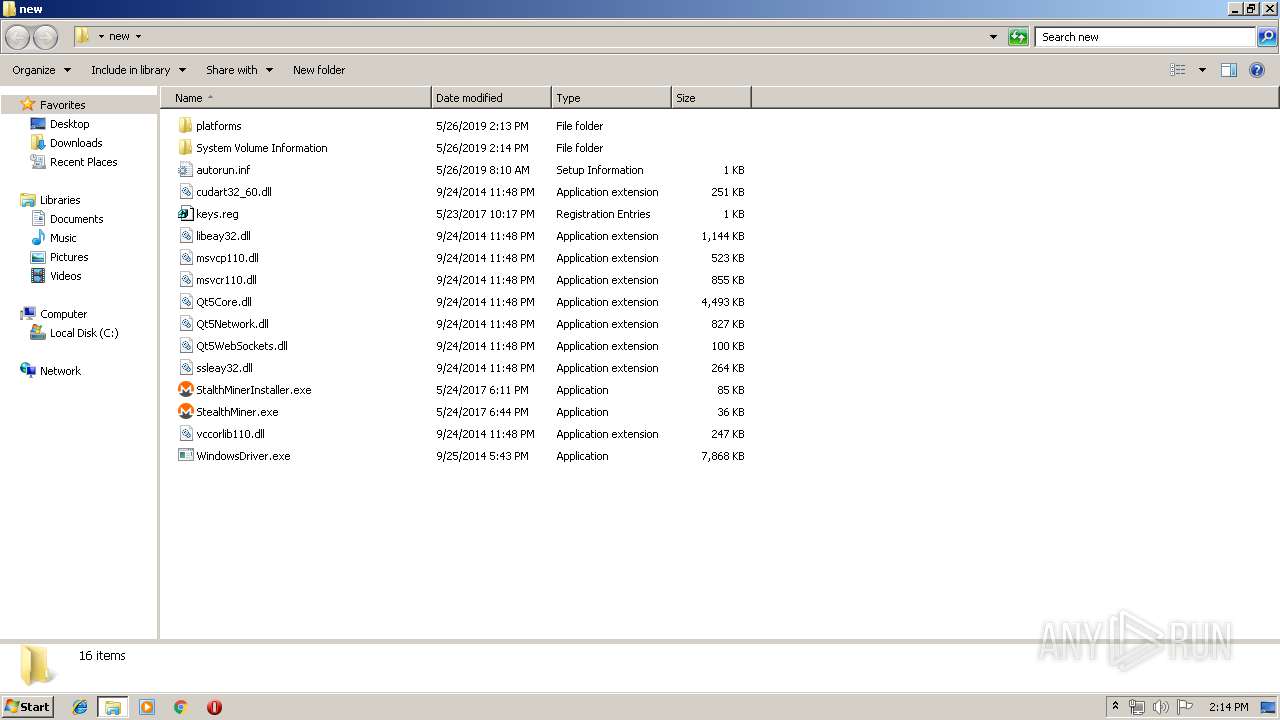
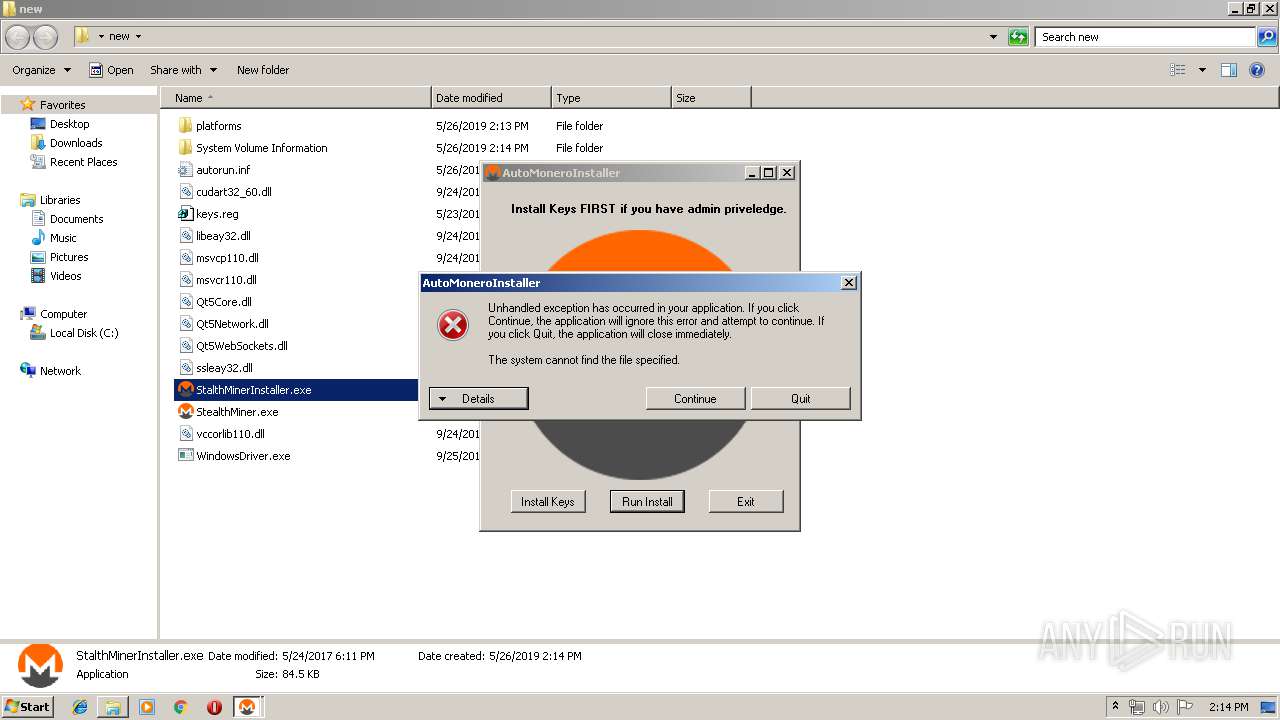
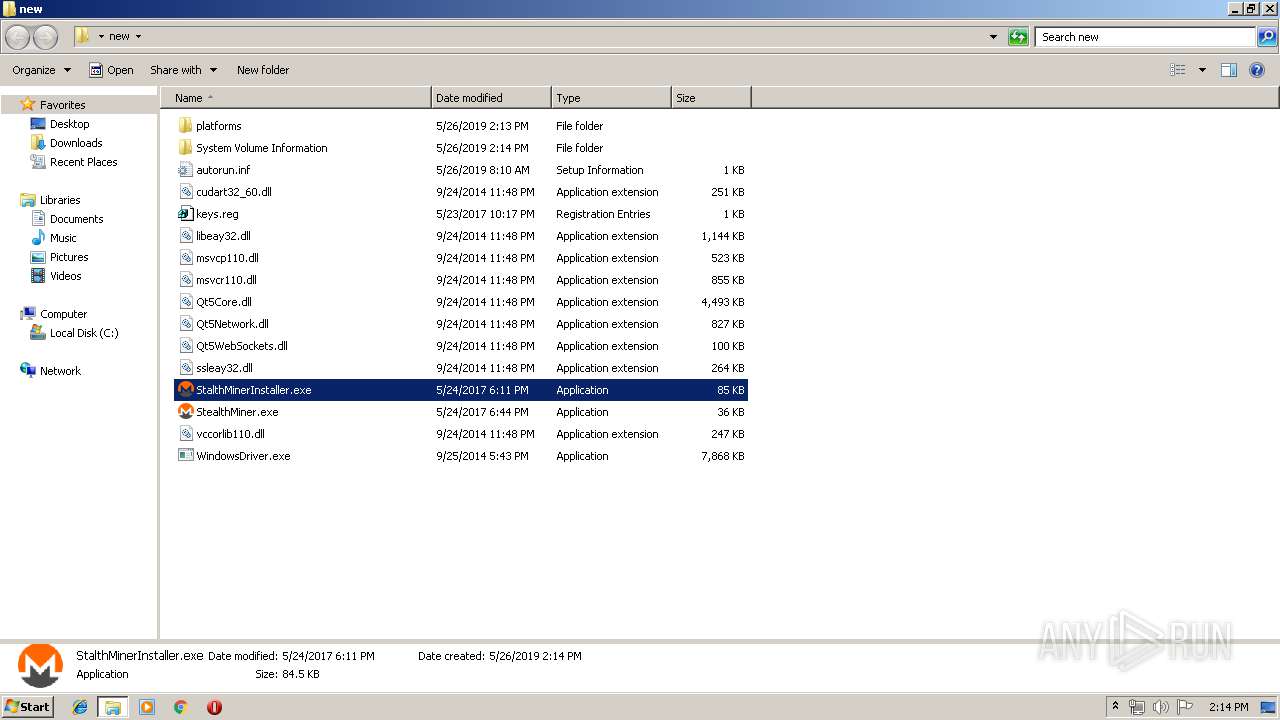
| URL: | https://anonfile.com/Vbn1Uas7n1/libeay32_zip |
| Full analysis: | https://app.any.run/tasks/269979f6-118f-43a1-b77e-ca193892eccf |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 26, 2019, 13:11:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A36D46707F132F3A9D8DCF260DC7C4AB |
| SHA1: | CF914A1DBB2DF5E7C51B489CE19F14C42E62BF5E |
| SHA256: | EF6F1C01DD2A237EA535D9E6915B5AF63438325895F03A9FDD6272B55962DE0A |
| SSDEEP: | 3:N8RGOLUwxSM1n:2gyx/1n |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2092)
- WindowsDriver.exe (PID: 2892)
- explorer.exe (PID: 2044)
- WindowsDriver.exe (PID: 2224)
- WindowsDriver.exe (PID: 1184)
Application was dropped or rewritten from another process
- StalthMinerInstaller.exe (PID: 3176)
- StealthMiner.exe (PID: 1656)
- WindowsDriver.exe (PID: 2224)
- WindowsDriver.exe (PID: 2892)
- StealthMiner.exe (PID: 2936)
- WindowsDriver.exe (PID: 1184)
Changes the autorun value in the registry
- StalthMinerInstaller.exe (PID: 3176)
MINER was detected
- WindowsDriver.exe (PID: 2892)
- WindowsDriver.exe (PID: 1184)
Connects to CnC server
- WindowsDriver.exe (PID: 2892)
- WindowsDriver.exe (PID: 1184)
SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3536)
Reads Internet Cache Settings
- explorer.exe (PID: 2044)
Starts Internet Explorer
- explorer.exe (PID: 2044)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3524)
- StalthMinerInstaller.exe (PID: 3176)
Creates files in the Windows directory
- StalthMinerInstaller.exe (PID: 3176)
Uses NETSH.EXE for network configuration
- StalthMinerInstaller.exe (PID: 3176)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 2044)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1212)
Creates files in the user directory
- iexplore.exe (PID: 3608)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3536)
- iexplore.exe (PID: 1212)
Reads internet explorer settings
- iexplore.exe (PID: 3608)
Reads Internet Cache Settings
- iexplore.exe (PID: 1212)
- iexplore.exe (PID: 3608)
Manual execution by user
- StalthMinerInstaller.exe (PID: 3176)
- StealthMiner.exe (PID: 1656)
- WindowsDriver.exe (PID: 2224)
- rundll32.exe (PID: 2660)
Reads settings of System Certificates
- iexplore.exe (PID: 1212)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3524)
- StalthMinerInstaller.exe (PID: 3176)
Changes settings of System certificates
- iexplore.exe (PID: 1212)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
60
Monitored processes
16
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 980 | "C:\Windows\regedit.exe" /s keys.reg | C:\Windows\regedit.exe | StalthMinerInstaller.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1184 | "C:\Windows.000\WindowsDriver.exe" -user rogernet95@mail.com -xmr 1 | C:\Windows.000\WindowsDriver.exe | StealthMiner.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1212 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1656 | "C:\Users\admin\Desktop\new\StealthMiner.exe" | C:\Users\admin\Desktop\new\StealthMiner.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AutoMonero Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2044 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2092 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe7_ Global\UsGthrCtrlFltPipeMssGthrPipe7 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2224 | "C:\Users\admin\Desktop\new\WindowsDriver.exe" | C:\Users\admin\Desktop\new\WindowsDriver.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2660 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\new\vccorlib110.dll | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2768 | "netsh" firewall add allowedprogram C:\Windows.000\WindowsDriver.exe WindowsDriver ENABLE | C:\Windows\system32\netsh.exe | — | StalthMinerInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2892 | "C:\Windows.000\WindowsDriver.exe" -user rogernet95@mail.com -xmr 1 | C:\Windows.000\WindowsDriver.exe | StealthMiner.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 703
Read events
3 228
Write events
464
Delete events
11
Modification events
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {DC0EA203-7FB7-11E9-A370-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (1212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307050000001A000D000C0007001102 | |||
Executable files
26
Suspicious files
18
Text files
57
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1212 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\0IS738PD\libeay32_zip[1].txt | — | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\8FML5DRE\anonfile[1].css | text | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\VCRO5FBT\shermore_info[1] | text | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YYHVCEQR\d3ud741uvs727m_cloudfront_net[1] | text | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\0IS738PD\libeay32_zip[1].htm | html | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\0IS738PD\js[1] | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
56
DNS requests
17
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3608 | iexplore.exe | GET | 200 | 52.85.188.145:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
3608 | iexplore.exe | GET | 200 | 67.27.159.126:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.1 Kb | whitelisted |
3608 | iexplore.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.1 Kb | whitelisted |
3608 | iexplore.exe | GET | 200 | 52.85.188.246:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
1212 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1212 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3608 | iexplore.exe | 194.32.146.60:443 | anonfile.com | — | — | unknown |
3608 | iexplore.exe | 104.18.38.148:443 | shermore.info | Cloudflare Inc | US | shared |
3608 | iexplore.exe | 23.111.8.154:443 | oss.maxcdn.com | netDNA | US | unknown |
3608 | iexplore.exe | 216.58.208.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
3608 | iexplore.exe | 172.217.16.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3608 | iexplore.exe | 52.200.52.74:443 | relandssymphoking.info | Amazon.com, Inc. | US | unknown |
3608 | iexplore.exe | 52.85.188.145:80 | x.ss2.us | Amazon.com, Inc. | US | unknown |
3608 | iexplore.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
1212 | iexplore.exe | 194.32.146.60:443 | anonfile.com | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
anonfile.com |
| whitelisted |
vjs.zencdn.net |
| whitelisted |
oss.maxcdn.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
shermore.info |
| whitelisted |
d3ud741uvs727m.cloudfront.net |
| whitelisted |
www.google-analytics.com |
| whitelisted |
relandssymphoking.info |
| unknown |
x.ss2.us |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2892 | WindowsDriver.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2892 | WindowsDriver.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2892 | WindowsDriver.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
1184 | WindowsDriver.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|