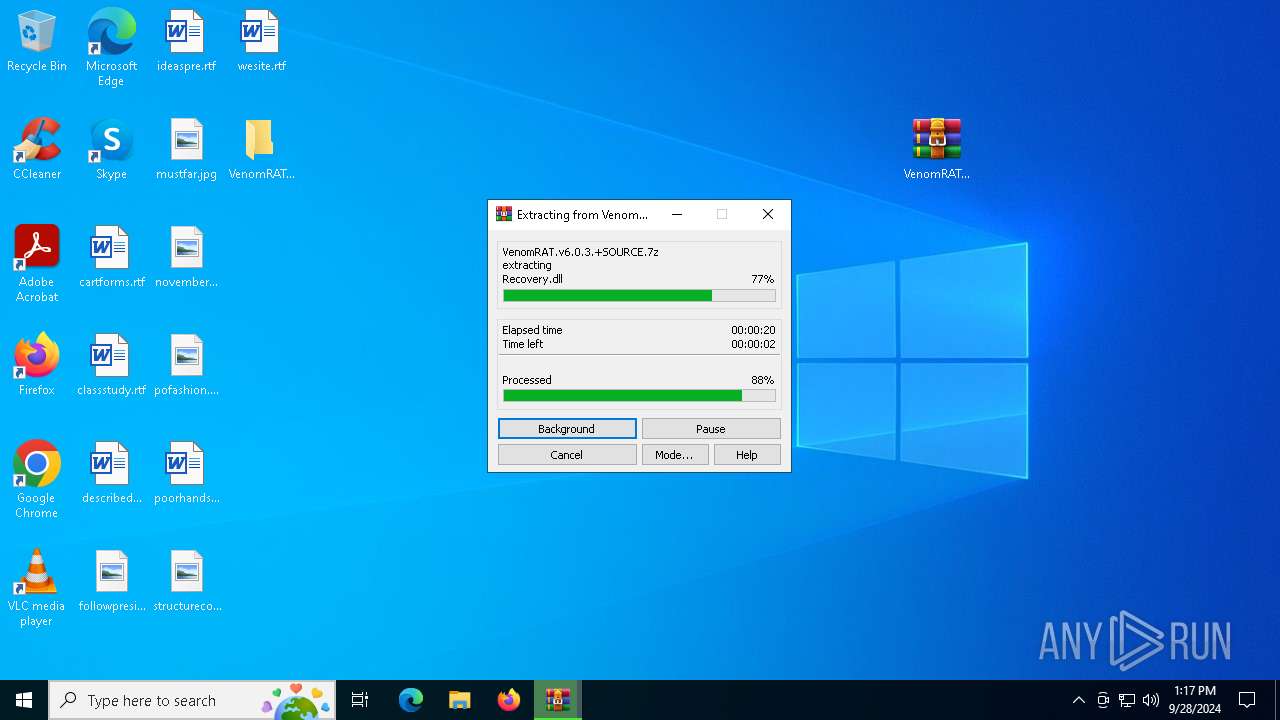
| URL: | https://gofile.io/d/vJypj7 |
| Full analysis: | https://app.any.run/tasks/a728b98c-b8aa-40e4-91e3-7cbbf871837d |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | September 28, 2024, 13:16:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B2D2AE529BB35A3DBB01EEE43F6DA62B |
| SHA1: | C1D1DA7FAD6D74BC740C40DB6400AFF5A2805768 |
| SHA256: | EF5C7B8610A101EFD3F67A68AB768E5C12EB7DA237FE003EFF348AF028C7B93C |
| SSDEEP: | 3:N8rxL1Zn:2Zn |
MALICIOUS
ASYNCRAT has been detected (YARA)
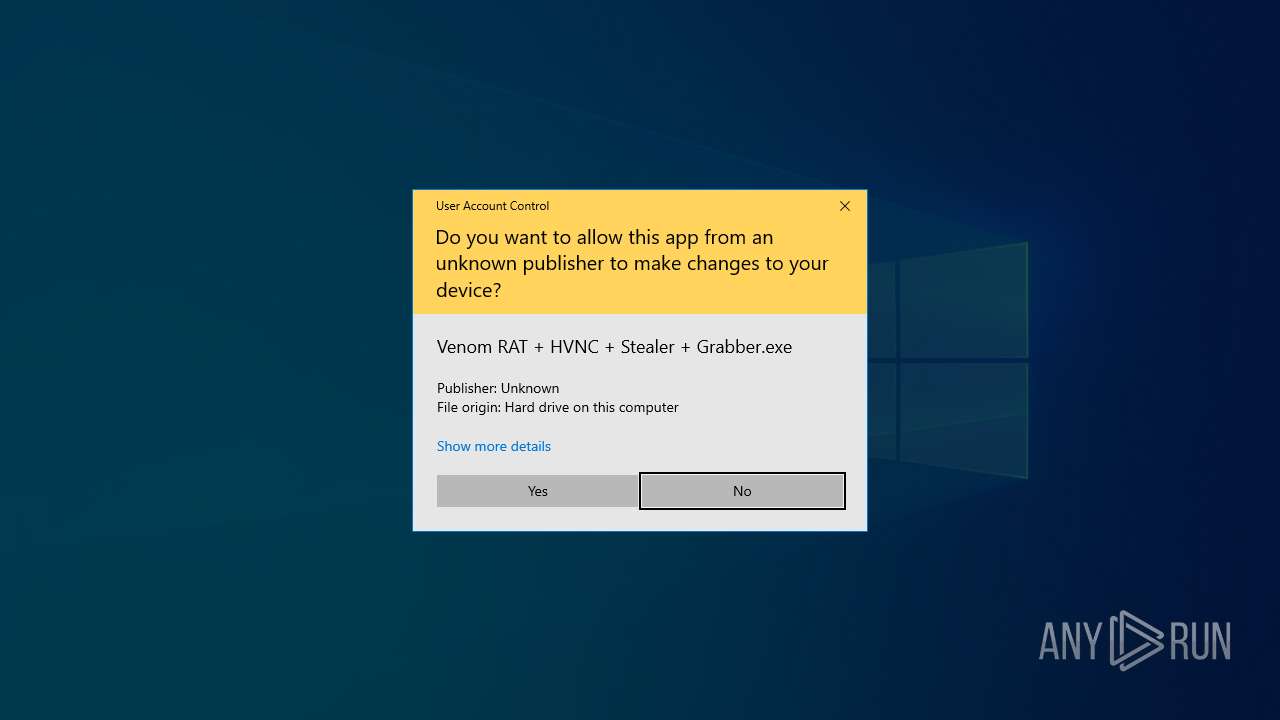
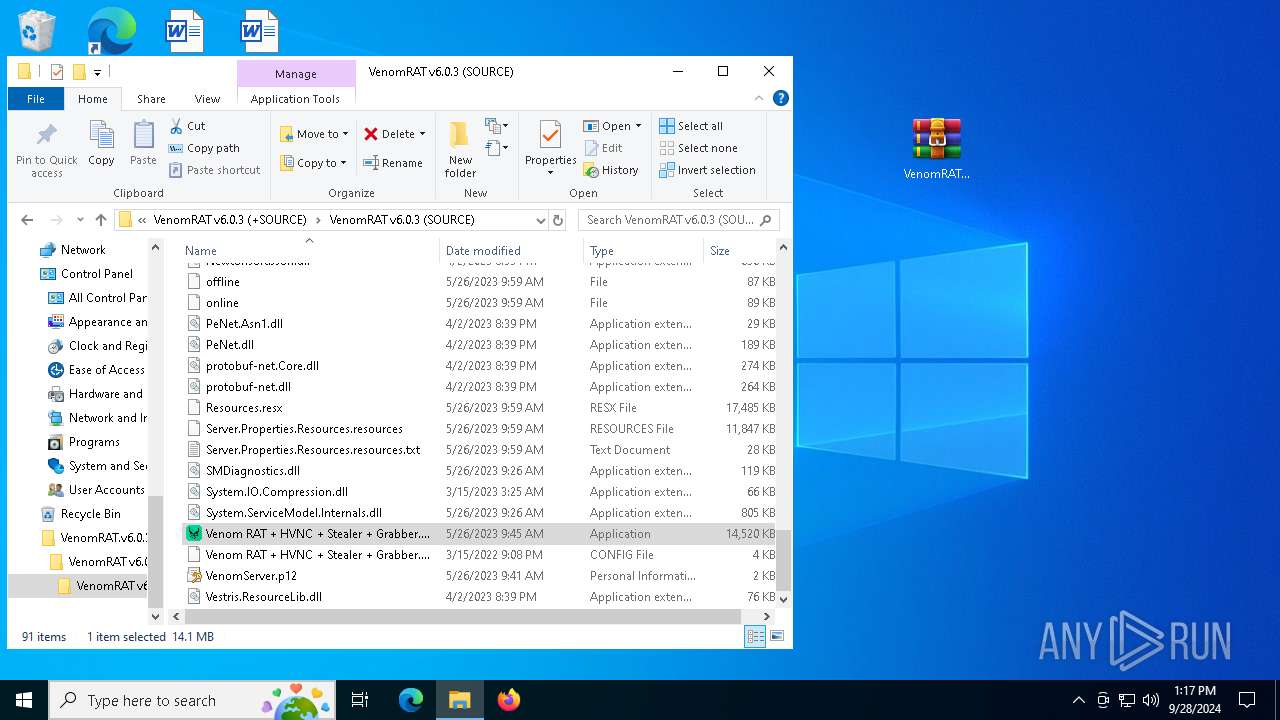
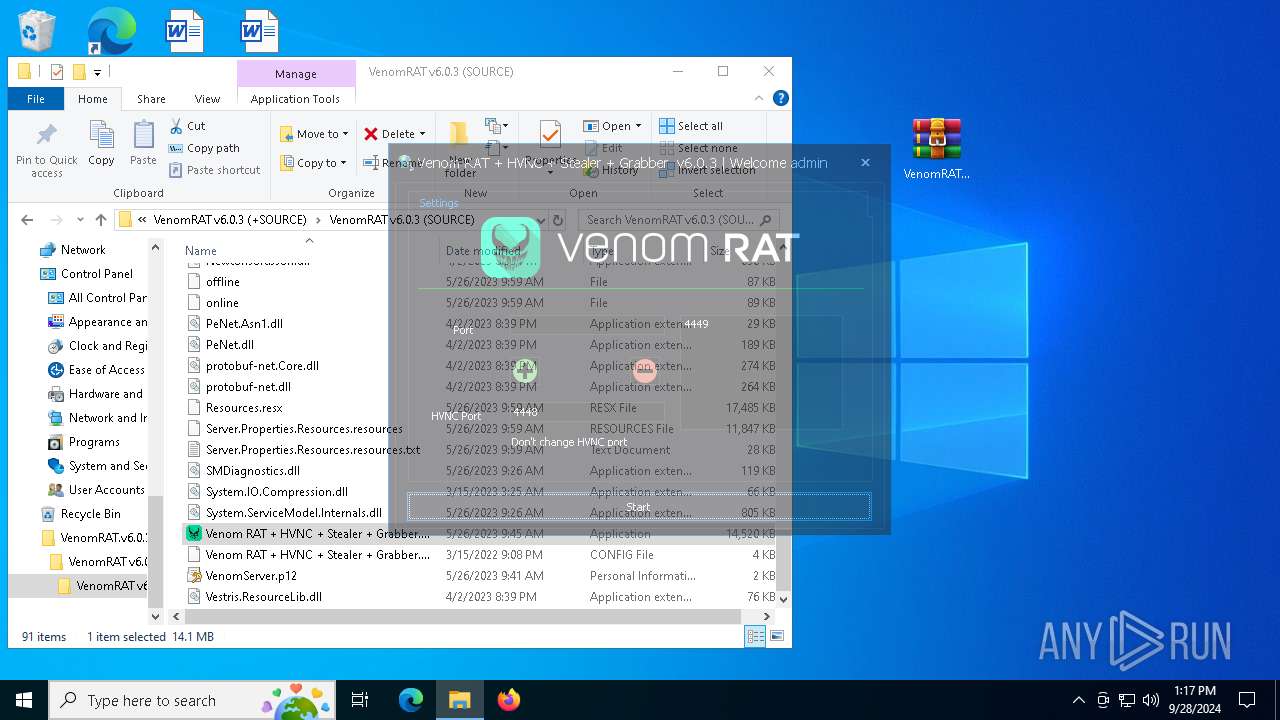
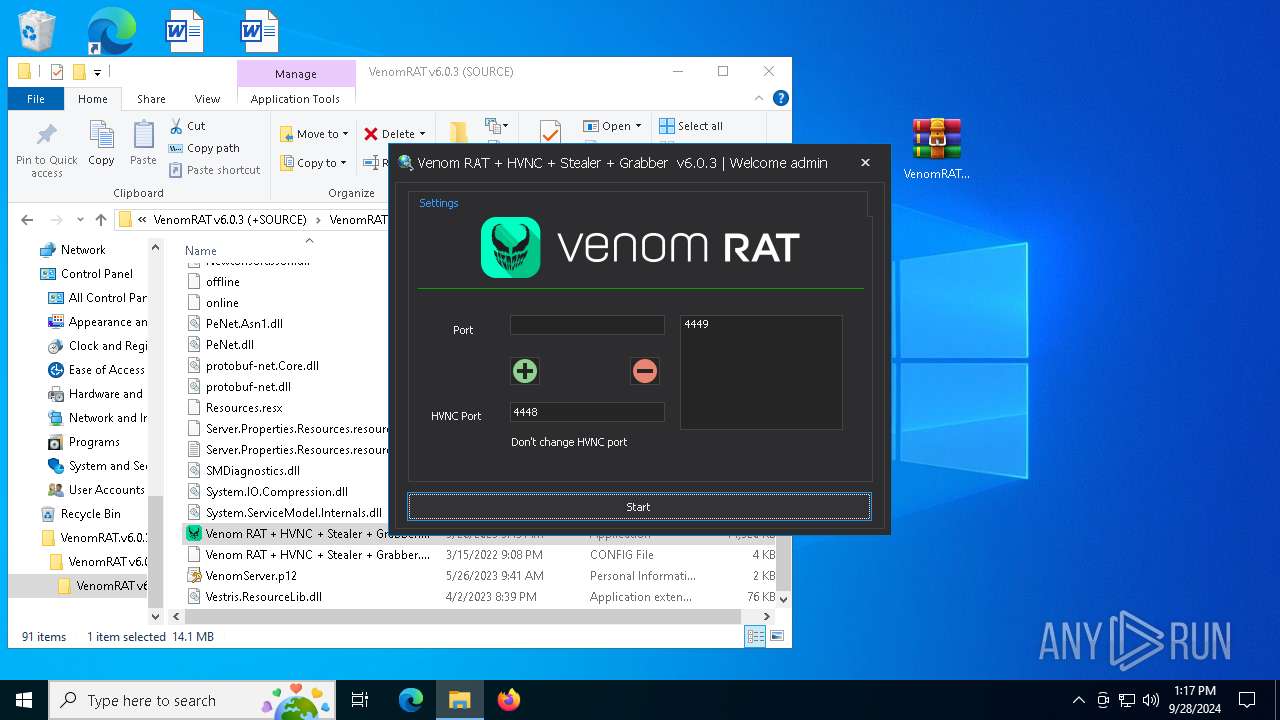
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 5140)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 2384)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6368)
Possible usage of Discord/Telegram API has been detected (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 5140)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 2384)
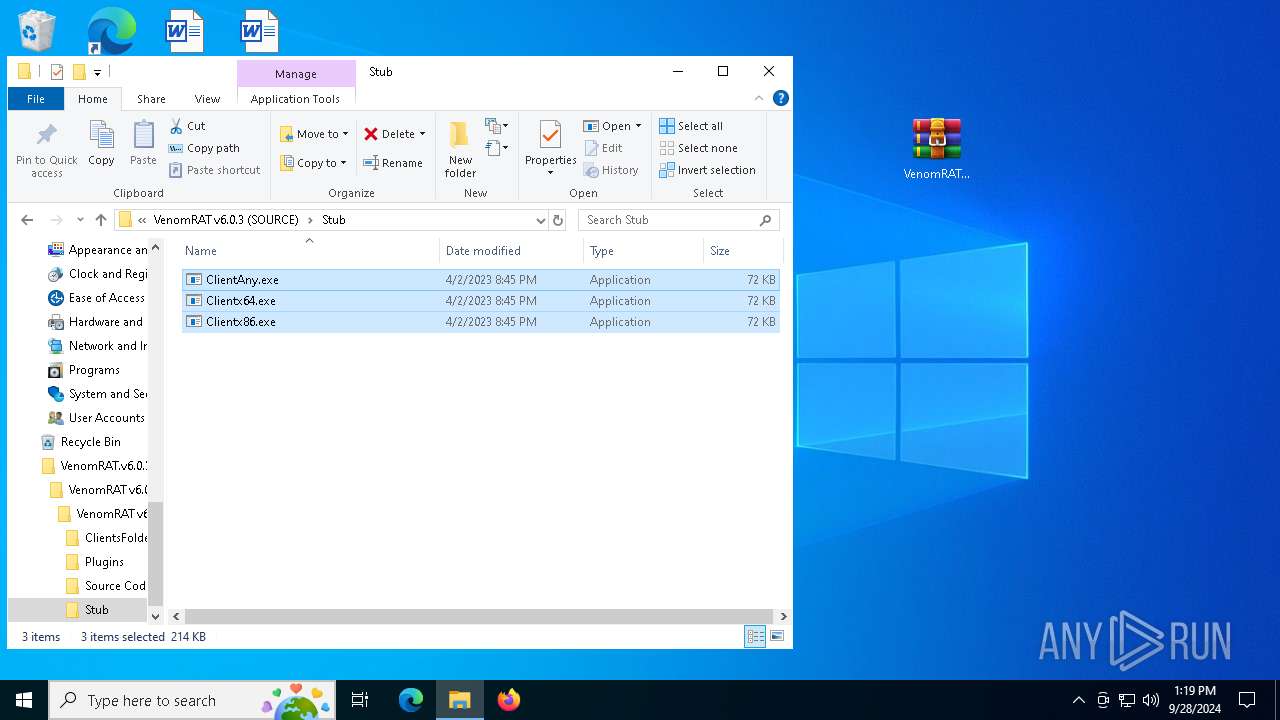
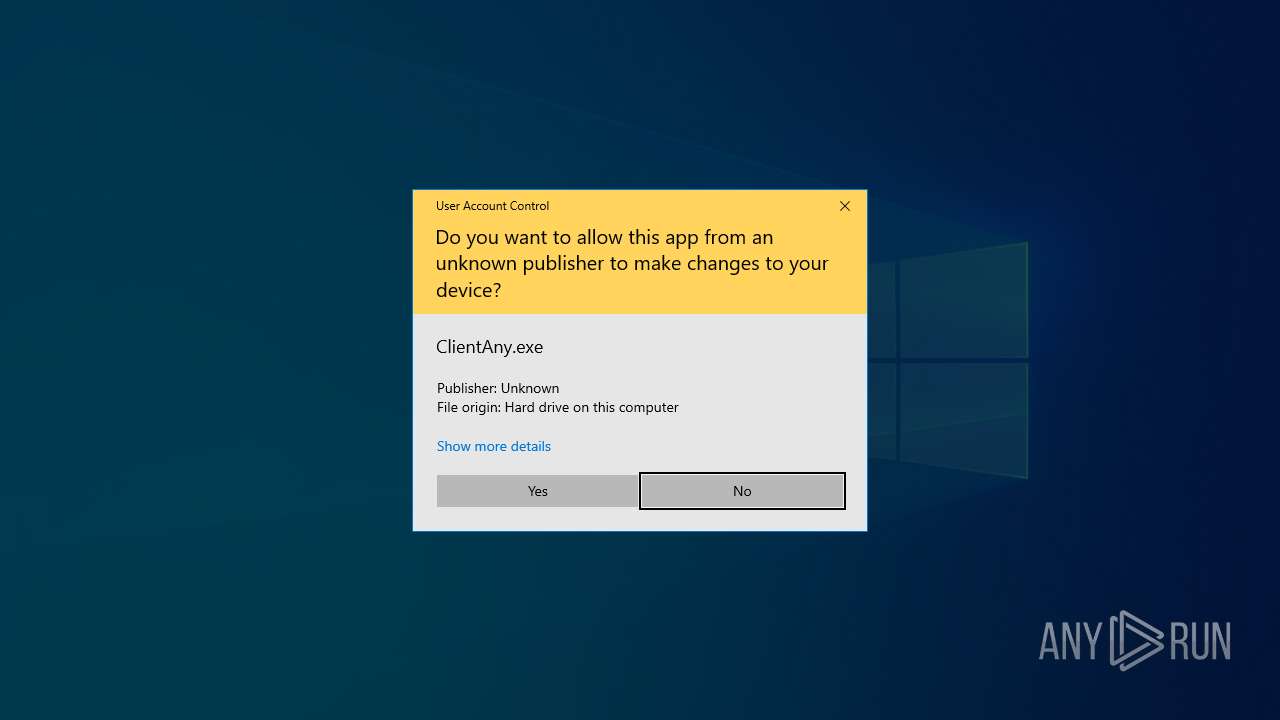
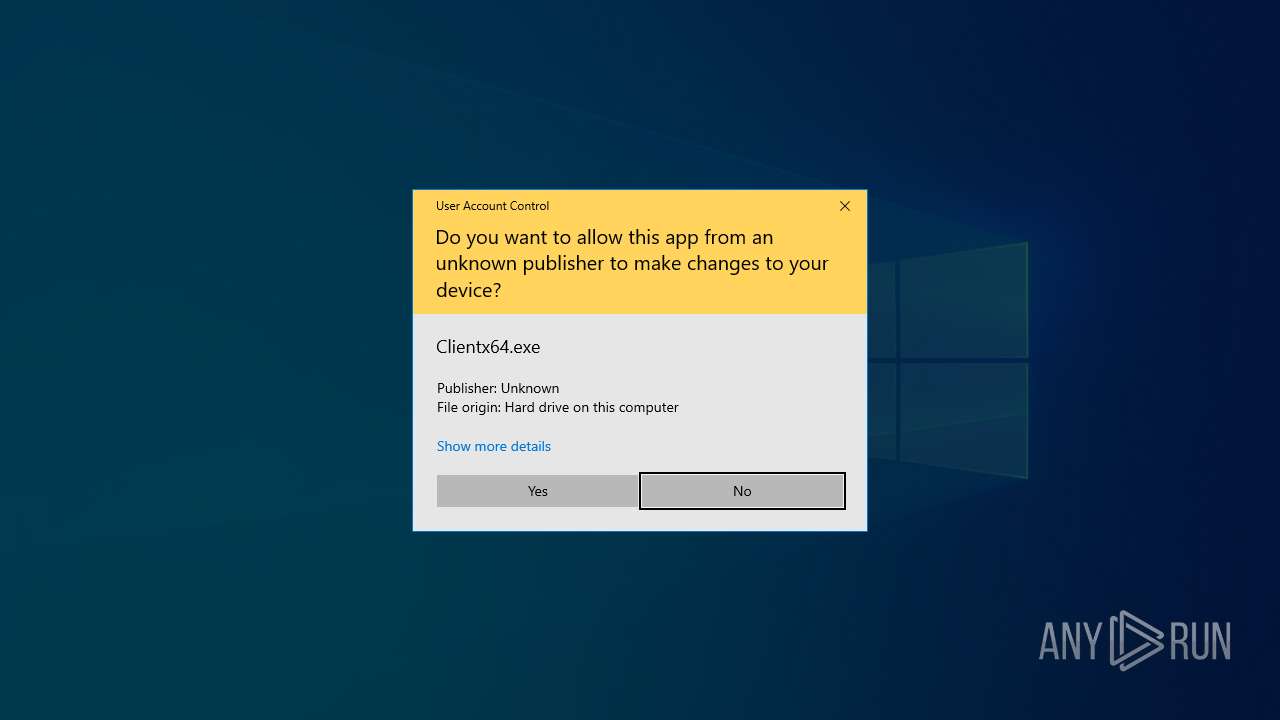
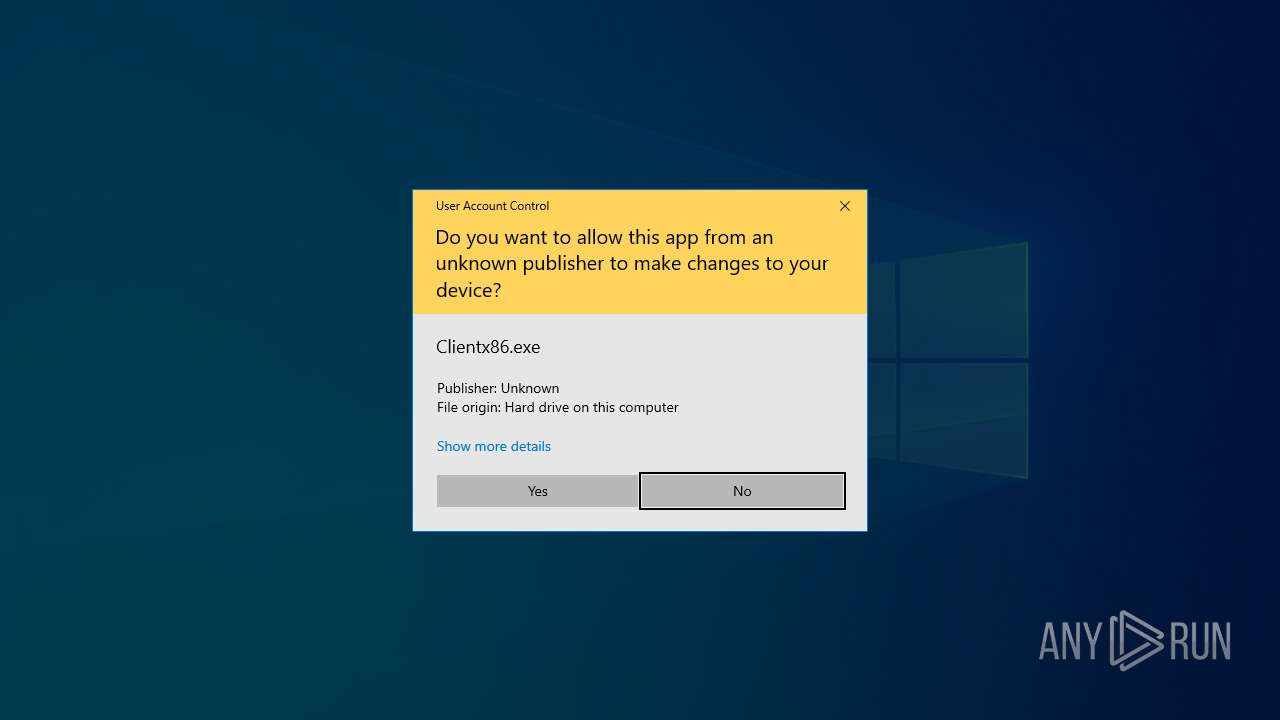
Executes application which crashes
- Clientx86.exe (PID: 7620)
- ClientAny.exe (PID: 7652)
- Clientx64.exe (PID: 5984)
There is functionality for taking screenshot (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 5140)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 2384)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6368)
Themida protector has been detected
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 5140)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 2384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Processunknown
Telegram-Tokens (1)5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Telegram-Info-Links
5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Get info about bothttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getMe
Get incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getUpdates
Get webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook?drop_pending_updates=true
Discord-Webhook-Tokens (1)1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Discord-Info-Links
1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Get Webhook Infohttps://discord.com/api/webhooks/1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
(PID) Processunknown
Telegram-Tokens (1)5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Telegram-Info-Links
5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Get info about bothttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getMe
Get incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getUpdates
Get webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook?drop_pending_updates=true
Discord-Webhook-Tokens (1)1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Discord-Info-Links
1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Get Webhook Infohttps://discord.com/api/webhooks/1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Total processes
168
Monitored processes
11
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
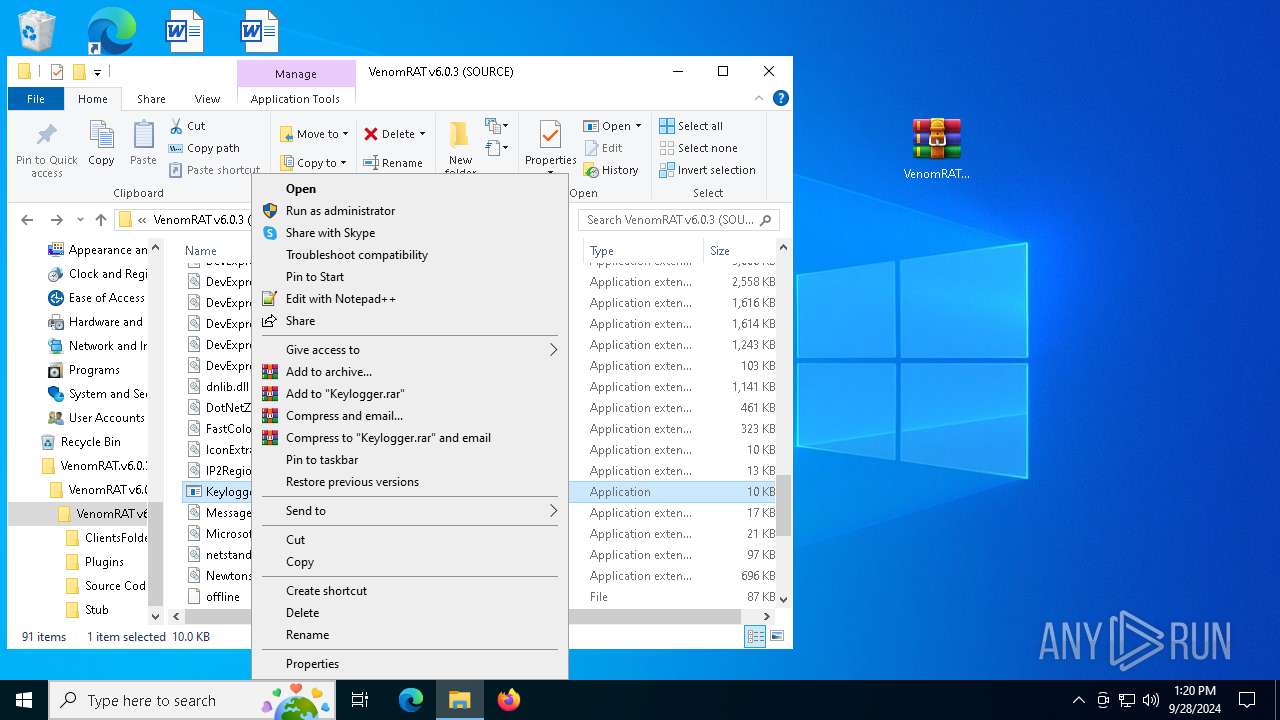
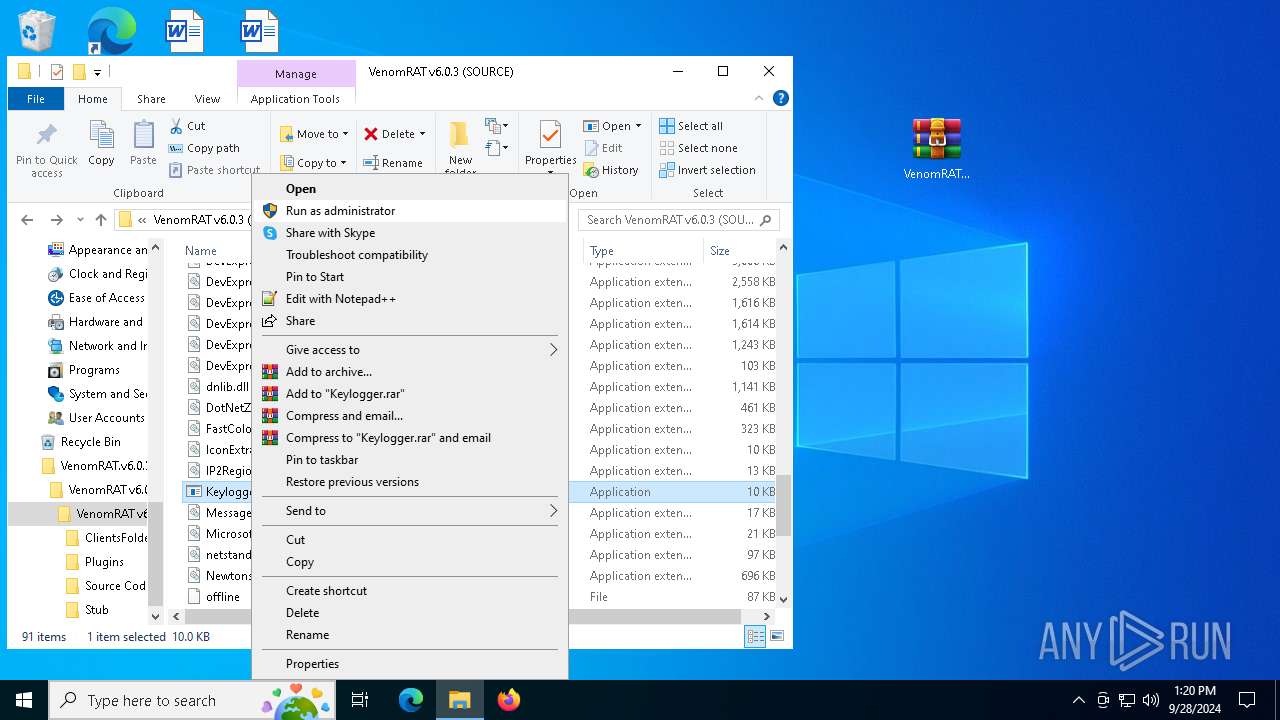
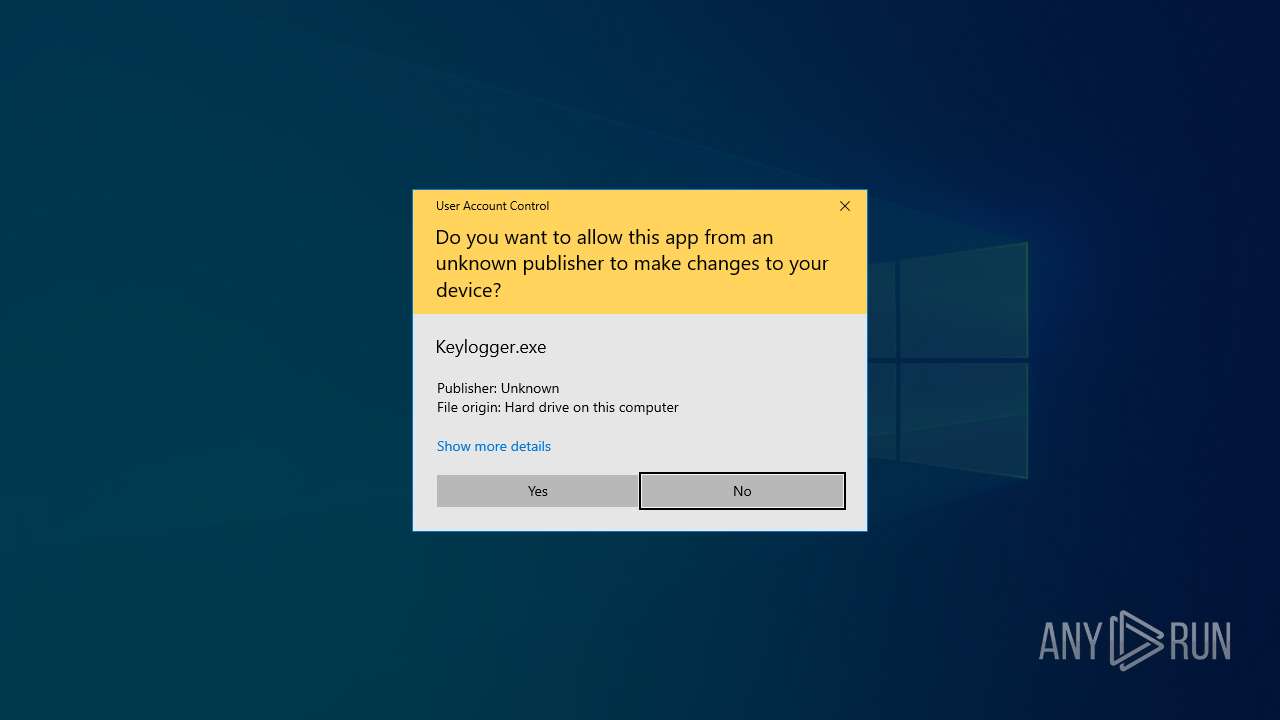
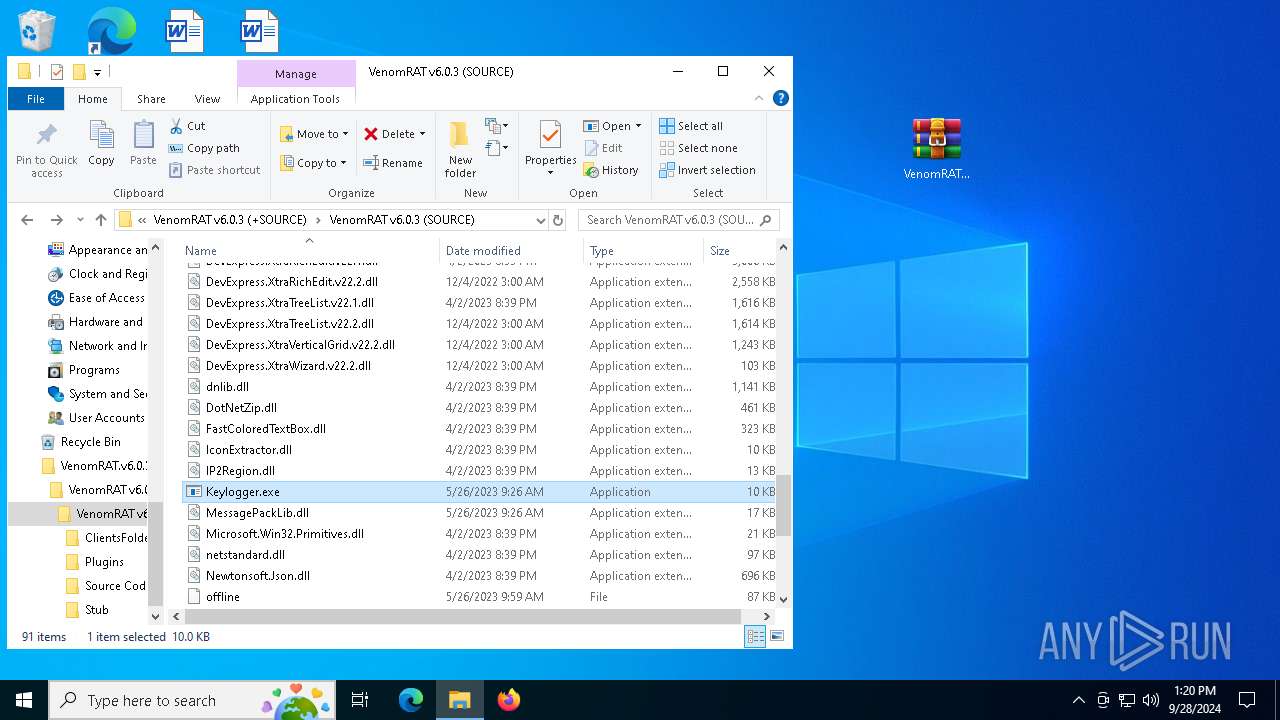
| 1148 | "C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Keylogger.exe" | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Keylogger.exe | explorer.exe | ||||||||||||
User: admin Company: Keylogger Integrity Level: HIGH Description: Keylogger Version: 1.0.0.0 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
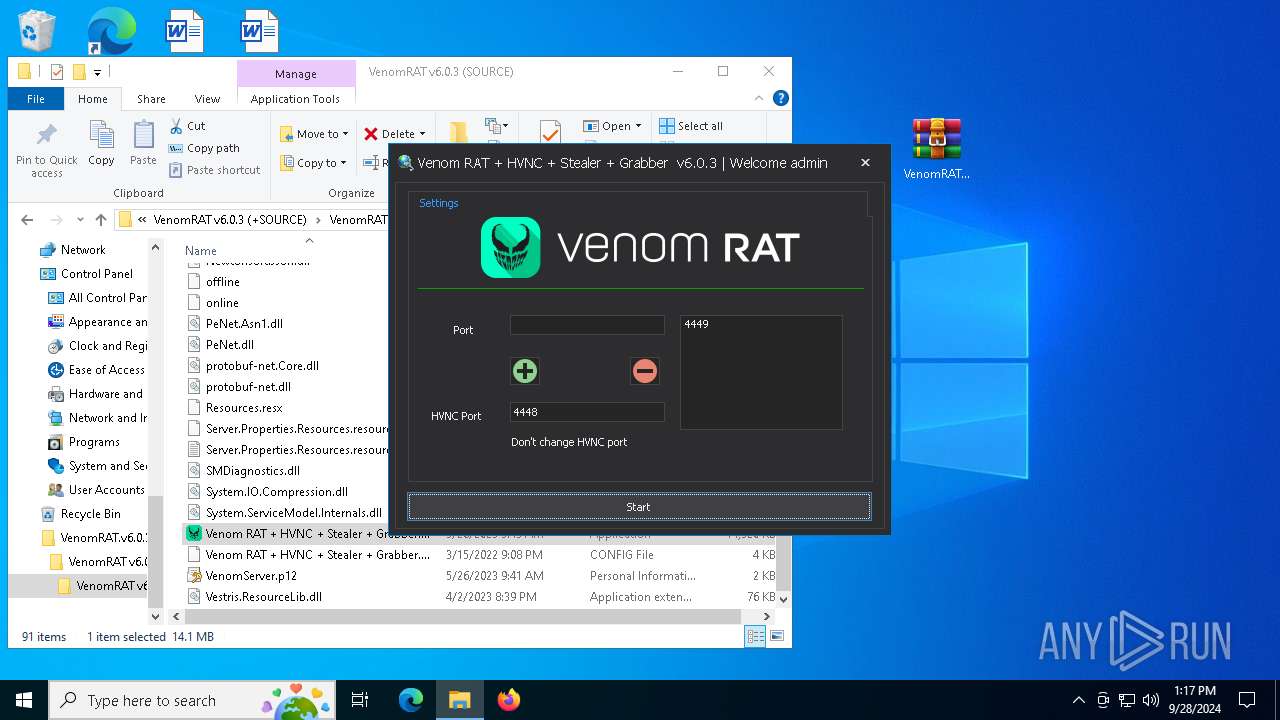
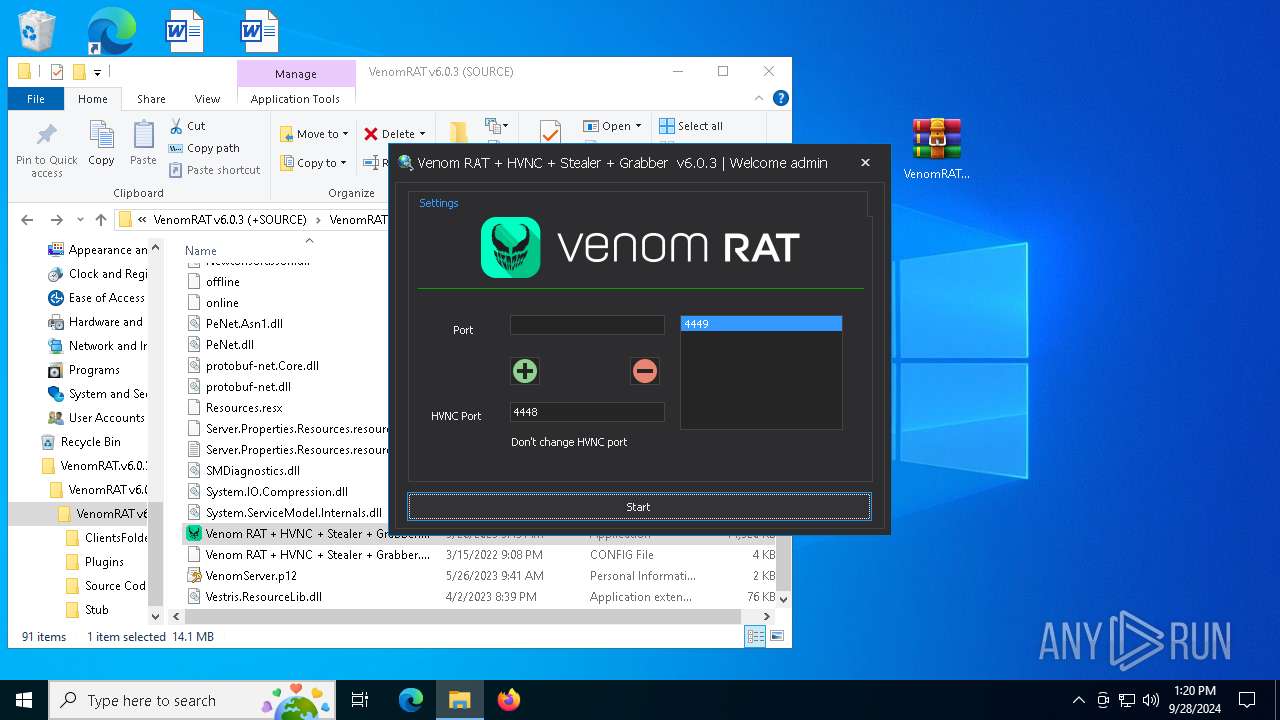
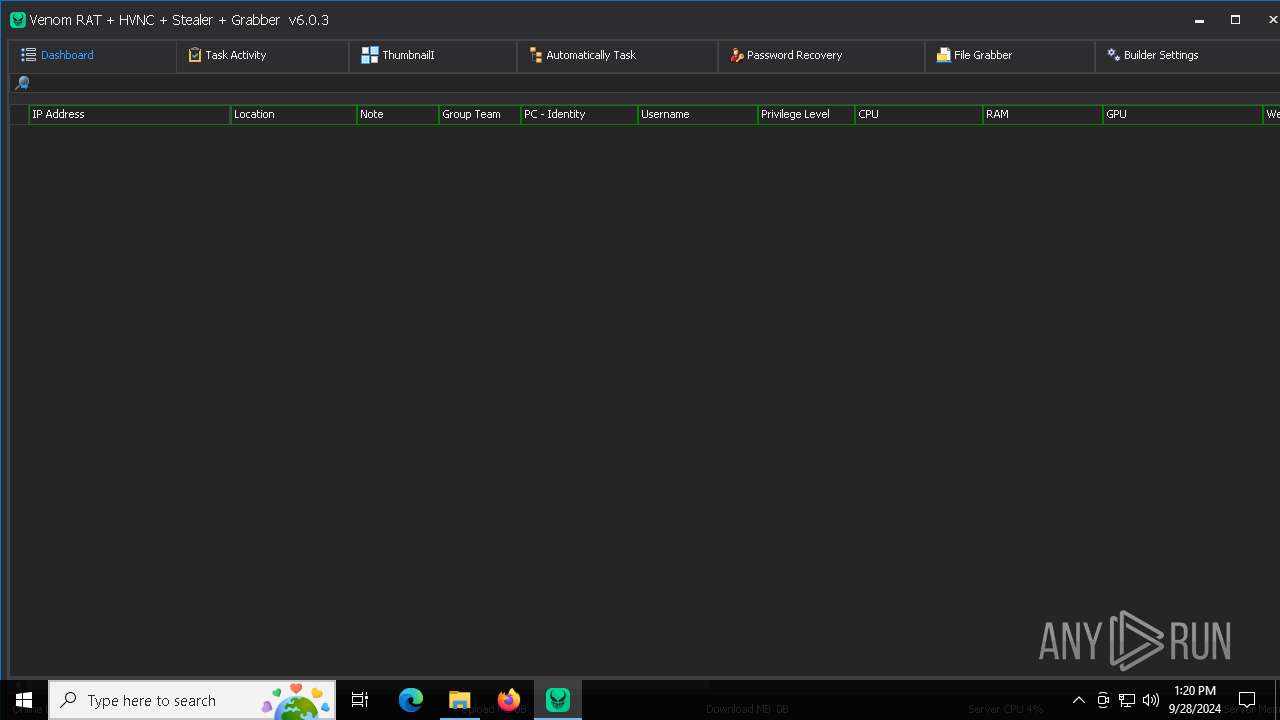
| 2384 | "C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Venom RAT + HVNC + Stealer + Grabber.exe" | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Venom RAT + HVNC + Stealer + Grabber.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: VenomRAT Version: 6.0.1 Modules
| |||||||||||||||
| 5140 | "C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Venom RAT + HVNC + Stealer + Grabber.exe" | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Venom RAT + HVNC + Stealer + Grabber.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: VenomRAT Exit code: 0 Version: 6.0.1 Modules
| |||||||||||||||
| 5500 | C:\WINDOWS\system32\WerFault.exe -u -p 7652 -s 940 | C:\Windows\System32\WerFault.exe | ClientAny.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5984 | "C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Stub\Clientx64.exe" | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Stub\Clientx64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3762504530 Version: 6.0.1 Modules
| |||||||||||||||
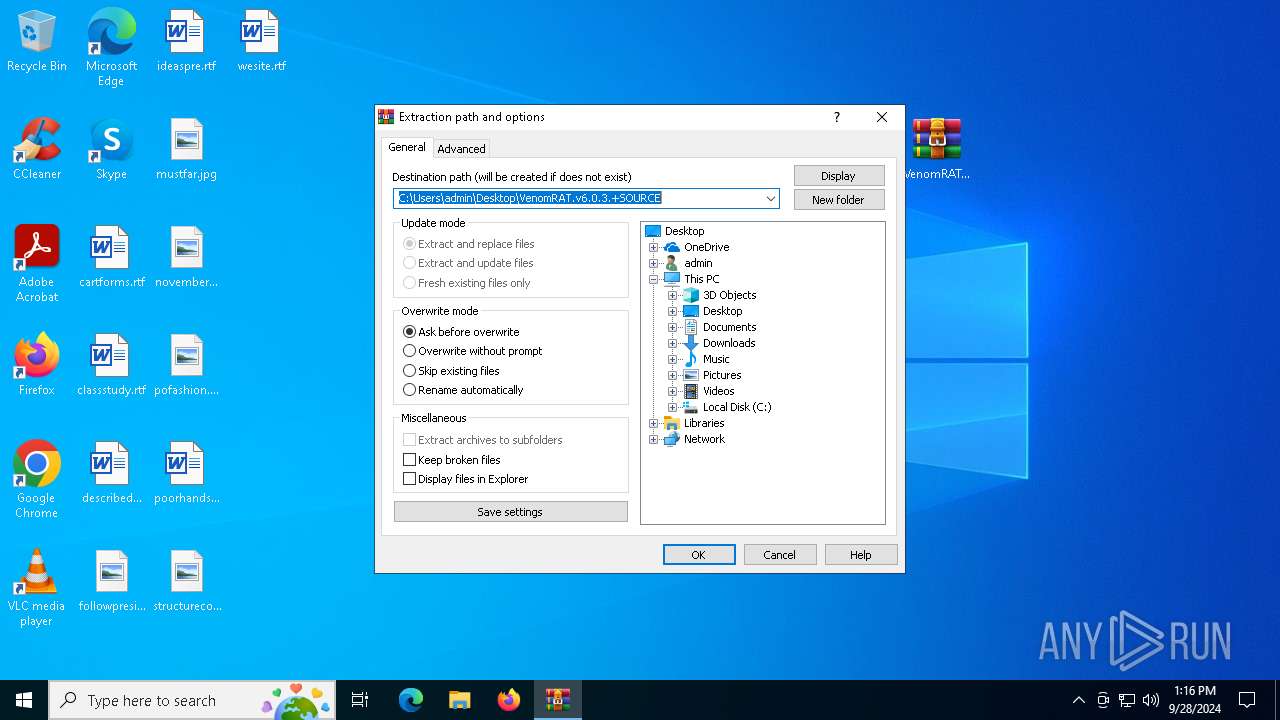
| 6368 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE.7z" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6736 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7620 -s 1004 | C:\Windows\SysWOW64\WerFault.exe | Clientx86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7256 | C:\WINDOWS\system32\WerFault.exe -u -p 5984 -s 956 | C:\Windows\System32\WerFault.exe | Clientx64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7620 | "C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Stub\Clientx86.exe" | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Stub\Clientx86.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3762504530 Version: 6.0.1 Modules
| |||||||||||||||
Total events
16 720
Read events
16 670
Write events
28
Delete events
22
Modification events
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 9 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
| (PID) Process: | (6368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 6 |
Value: | |||
Executable files
109
Suspicious files
12
Text files
166
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Plugins\ip2region.db | — | |
MD5:— | SHA256:— | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Resources.resx | — | |
MD5:— | SHA256:— | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Server.Properties.Resources.resources | — | |
MD5:— | SHA256:— | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\offline | binary | |
MD5:829C84C8F69856AABA8DFAD042BC1CF4 | SHA256:21B4173439BDCB6338D99A8F060B98426CCA95B2830B62965A72C94BC6C77236 | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\online | binary | |
MD5:4E642F0D041D6EF79D7701E599E4BBE9 | SHA256:C2CFBABF111D231FB2531B6C0759C5191FD91F767059790FF53AEF87FAB2280F | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Source Code\Algorithm\Aes256.cs | text | |
MD5:67017528F9949E89BBF199C8F330F746 | SHA256:308AA10EE89CCD2B6107276BCD054FEFB408BF2C62201B32EB4DA0DB5C340BC5 | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Plugins\Keylogger.exe.config | xml | |
MD5:8810B832F11B6E5A1AFAB929618059F2 | SHA256:68CBB1295389A1BD6B830DEBFD0A8BB0A88BEE2522304F5894C710912021194C | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Source Code\app.ico | image | |
MD5:71C699BD1EB8CF9FD981BABBF5524FC9 | SHA256:B714CAE7F66BB4E924D4E942DE68D690746FC38160476F7AA48F5CB51A02AE22 | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Source Code\Algorithm\GetHash.cs | text | |
MD5:ADAA0544A3F06D990507D8FBCC6EF55B | SHA256:B1DAA323BF8A6569992D9ABC956D29EE78CE86E522E1766DF375484B7439FB87 | |||
| 6368 | WinRAR.exe | C:\Users\admin\Desktop\VenomRAT.v6.0.3.+SOURCE\VenomRAT v6.0.3 (+SOURCE)\VenomRAT v6.0.3 (SOURCE)\Source Code\Forms\FormDownloadFile.cs | text | |
MD5:C446C2BE3B44FB3C3CAA99095FF5DAC9 | SHA256:1682080EB428A04A33499A78F66200D1913C8978747FA72514D6663047AEC0E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
80
DNS requests
85
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/s/wr3/XjA | unknown | — | — | whitelisted |
— | — | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | — | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
— | — | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
6304 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6304 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
4516 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7108 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6776 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 45.112.123.126:443 | gofile.io | AMAZON-02 | SG | whitelisted |
— | — | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
— | — | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
— | — | 184.24.77.79:80 | r10.o.lencr.org | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
gofile.io |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |