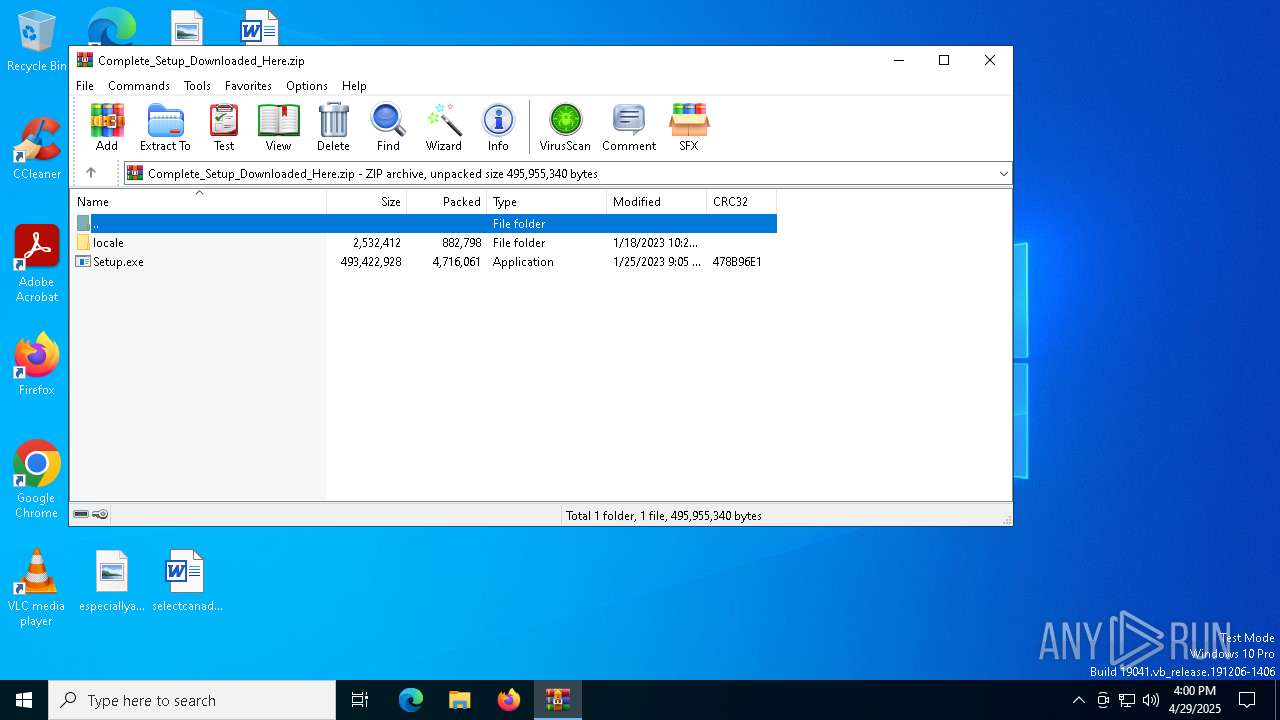
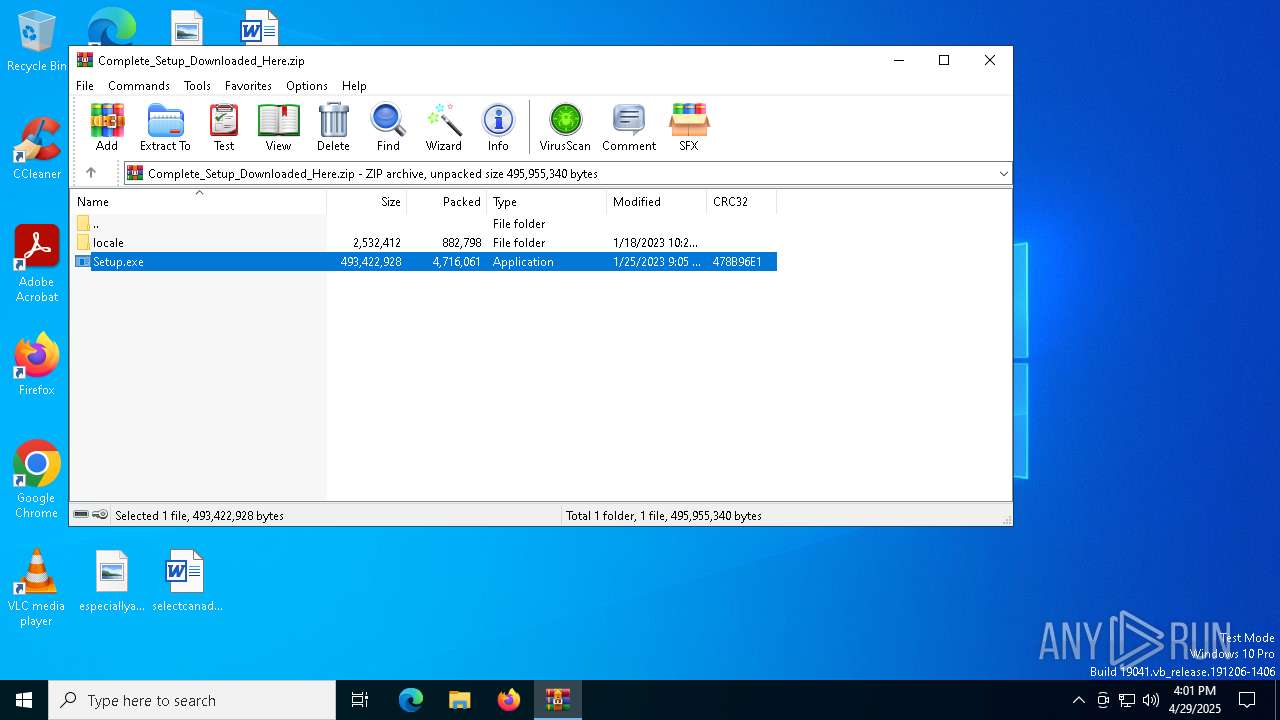
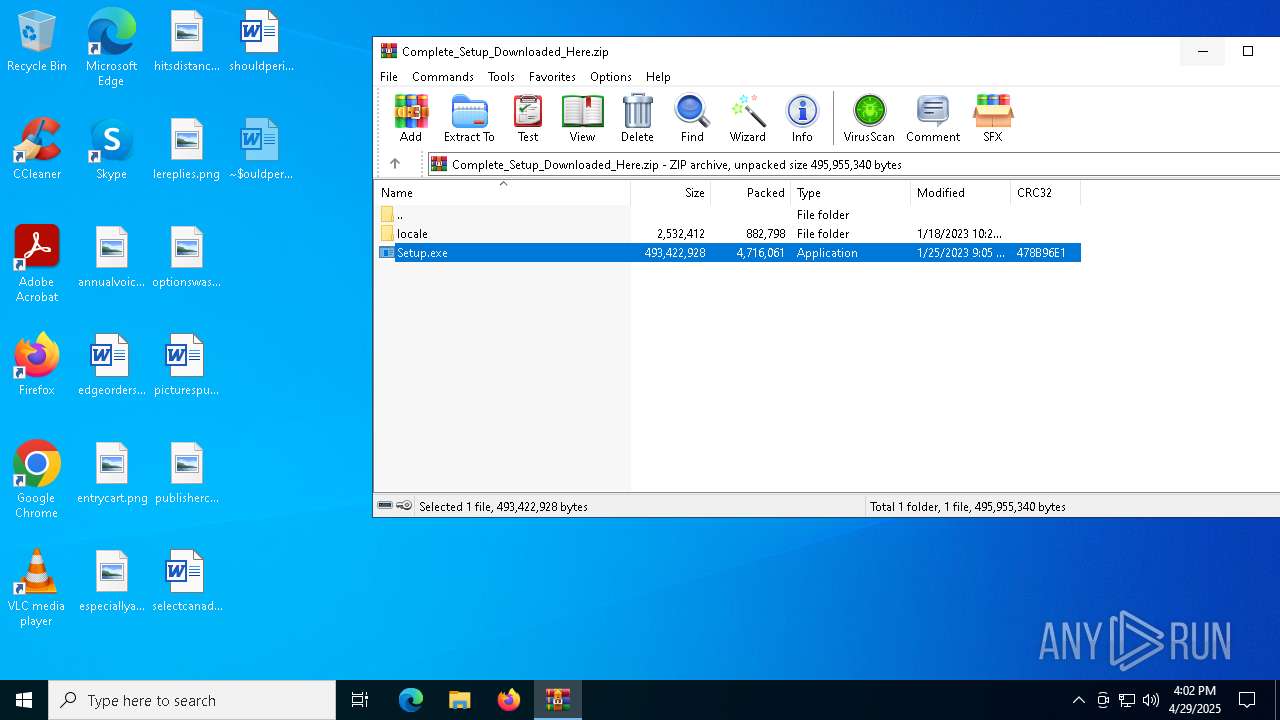
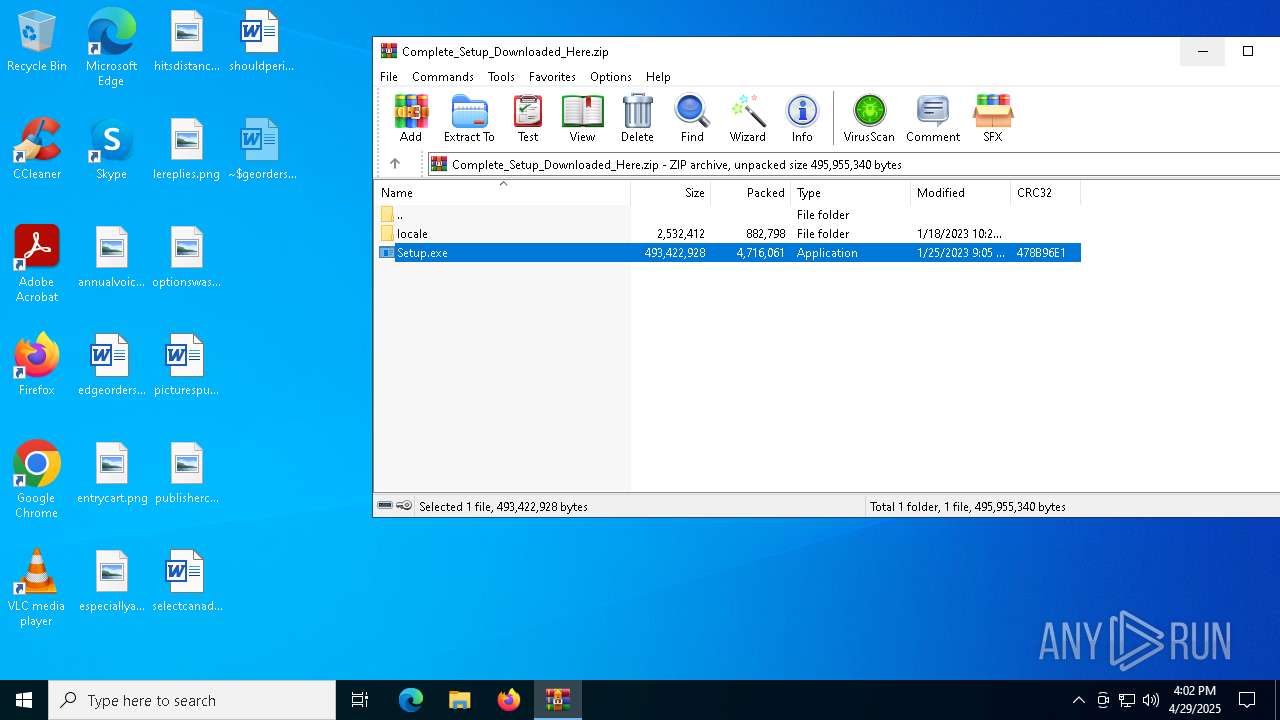
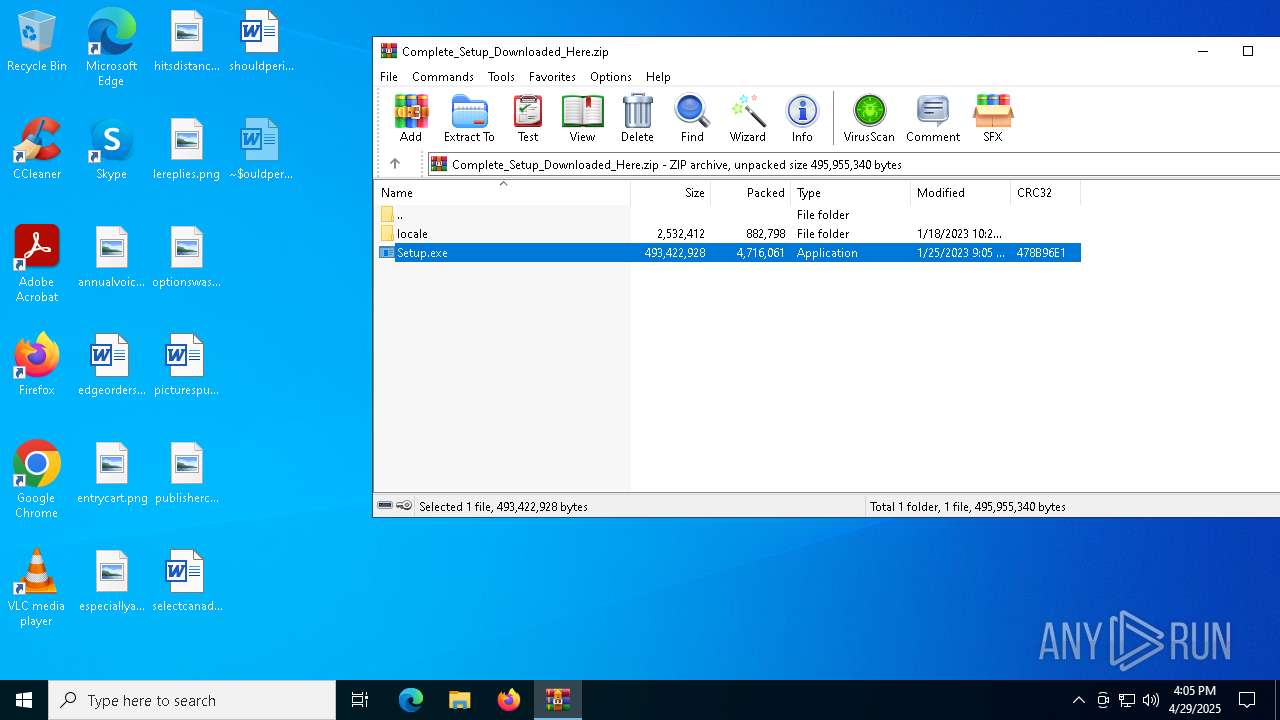
| File name: | Complete_Setup_Downloaded_Here.zip |
| Full analysis: | https://app.any.run/tasks/747c487f-05ff-4574-9d86-b5f184023769 |
| Verdict: | Malicious activity |
| Threats: | Arkei is a stealer type malware capable of collecting passwords, autosaved forms, cryptocurrency wallet credentials, and files. |
| Analysis date: | April 29, 2025, 16:00:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 6998E77840646F5575DE5B2AC0632E46 |
| SHA1: | B9DB57E91977AD0194B471BE1E2F70FDD49584AE |
| SHA256: | EF033B17034D3480EE0C076F699DA819C48E82558299EB6247C678E0195694FE |
| SSDEEP: | 98304:tmyP1HL2KNEDR3hDAiYSZdcv/j0Y0Fod4UmG+Km0syB7P/CGNRSvKOHnJ2rutZpt:RLvIulHSb |
MALICIOUS
ARKEI has been detected (YARA)
- Setup.exe (PID: 8096)
VIDAR has been detected (YARA)
- Setup.exe (PID: 8096)
SUSPICIOUS
Reads the BIOS version
- Setup.exe (PID: 8096)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7404)
- Setup.exe (PID: 8096)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Setup.exe (PID: 8096)
Multiple wallet extension IDs have been found
- Setup.exe (PID: 8096)
Connects to the server without a host name
- Setup.exe (PID: 8096)
INFO
Checks supported languages
- Setup.exe (PID: 8096)
Reads the machine GUID from the registry
- Setup.exe (PID: 8096)
Reads the computer name
- Setup.exe (PID: 8096)
Manual execution by a user
- WINWORD.EXE (PID: 8156)
- WINWORD.EXE (PID: 7788)
- WINWORD.EXE (PID: 632)
- WINWORD.EXE (PID: 2692)
- WINWORD.EXE (PID: 864)
- mspaint.exe (PID: 7308)
Reads the software policy settings
- Setup.exe (PID: 8096)
- slui.exe (PID: 7592)
Checks proxy server information
- Setup.exe (PID: 8096)
Creates files or folders in the user directory
- Setup.exe (PID: 8096)
Mpress packer has been detected
- Setup.exe (PID: 8096)
Themida protector has been detected
- Setup.exe (PID: 8096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:01:18 15:59:10 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | locale/ |
Total processes
159
Monitored processes
17
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\shouldperiod.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\edgeorders.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "965EBCAC-ECD5-4382-BC13-302D379B4AE1" "1BCE1B01-C7F1-40A3-8074-2FC3F339841B" "632" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "85FDAF1A-5DFA-4542-B3DF-DCAE9C8C4761" "F27A878B-7A29-4280-8FF8-0A9F59C4286F" "8156" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 2692 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\shouldperiod.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3768 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "CCE2DF58-0B86-417A-8F41-EC9B91E61328" "24395DE8-E399-4F5B-BFE7-8619CB33C2D7" "2692" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 5332 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "FA40D13C-DD8A-45E2-A1AF-2DCAE021D515" "DC43F5CD-9FAA-4AE6-A38C-375A9D749C4C" "864" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 6072 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.1973\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.1973\Setup.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Corel Corporation Integrity Level: MEDIUM Description: PerfectFit Object Browse ActiveX Controls Module Version: 19.0.0.325 Modules
| |||||||||||||||
| 7308 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\entrycart.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
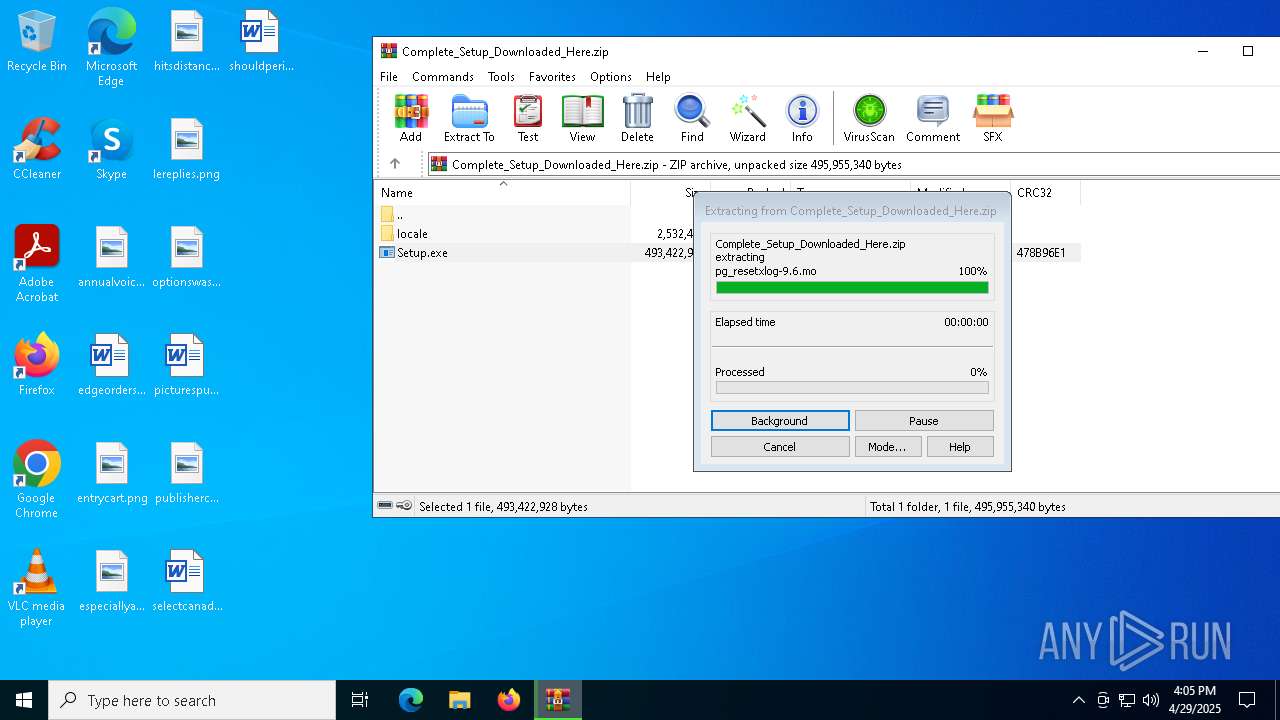
| 7404 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Complete_Setup_Downloaded_Here.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
45 642
Read events
44 876
Write events
660
Delete events
106
Modification events
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Complete_Setup_Downloaded_Here.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8096) Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8096) Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
25
Suspicious files
539
Text files
30
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\ecpglib-9.6.mo | binary | |
MD5:0FE321ADFEC0A8B140526382E99337C1 | SHA256:F6A42F0D7C12F5E341E23D4322E354F3C6FE35338932B3635E4D34AA1F030886 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\initdb-9.6.mo | binary | |
MD5:71211E2B1ACFF7A38E4C092194FC4CA7 | SHA256:D7322C18AD790A51401CF73EFECC1DF4DF5F81025A8A84BCBB7145E6EF36F614 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\pg_controldata-9.6.mo | binary | |
MD5:5664FD10C6FBA10BD71B3F02FC82B431 | SHA256:EB72ADF024F840468AEC21108A51BC3621C46A7DE27DA012411920D6A6F4AEA6 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\pg_ctl-9.6.mo | binary | |
MD5:AE61C63D421102B7CB218F464FE3633D | SHA256:48E40F6896C8B72F62FAC7748127E930075A3270C2EBB72DDB7C7335BEF1DEE7 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\libpq-9.6.mo | binary | |
MD5:5D44CE3324B8F50609FB0F7F15E7A248 | SHA256:ED3A02B350A064C4163144B0621827285AD93C096EDB3FBCB5FD9D7EFA250C15 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\pg_dump-9.6.mo | binary | |
MD5:7AA87C68FA16150FF3411541968B46FB | SHA256:C594C9DC593A5DCFFF0721B4CF37500A931FF87CF6DED247CC55DC647BA1F3A1 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\plperl-9.6.mo | binary | |
MD5:A8D917F66455CEAC64BE47B1FAF6F84F | SHA256:04E2E08F205066BA805A1FCA873C342C9B2E5202E51A617906B158D5053E1EA2 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\pg_resetxlog-9.6.mo | binary | |
MD5:0A7A53254CD4BCC98252ACC26EDE57D5 | SHA256:1A8B5A16B2A182F4B09A612FD58B531962A6DCA29B24BB275DB2C781CC088A9F | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\pg_config-9.6.mo | binary | |
MD5:F3B3A11F8756CBE97F2190C554D914E6 | SHA256:B269586FBD90597279F5EFC9021C1E99ED965048AD455EFF6529179BDEA629D0 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7404.27723\locale\cs\plpgsql-9.6.mo | binary | |
MD5:FEFDC017F62A48DAB43B01D6B1F2DC2C | SHA256:F43C36CF0BDEF38ADBF93473F96A946CAD5B92D9A7EDCF8D7B855B6045B54B6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
118
DNS requests
20
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.25.102.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 184.25.102.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8096 | Setup.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | — | — | whitelisted |
8096 | Setup.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | unknown | — | — | whitelisted |
8096 | Setup.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQDytgE3K904Dg%3D%3D | unknown | — | — | whitelisted |
8096 | Setup.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | unknown | — | — | whitelisted |
8096 | Setup.exe | GET | — | 157.90.148.112:80 | http://157.90.148.112/15 | unknown | — | — | unknown |
8156 | WINWORD.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.25.102.141:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
2104 | svchost.exe | 184.25.102.141:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
2104 | svchost.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8096 | Setup.exe | 149.154.167.99:443 | t.me | Telegram Messenger Inc | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
t.me |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
steamcommunity.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8096 | Setup.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
8096 | Setup.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
8096 | Setup.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |