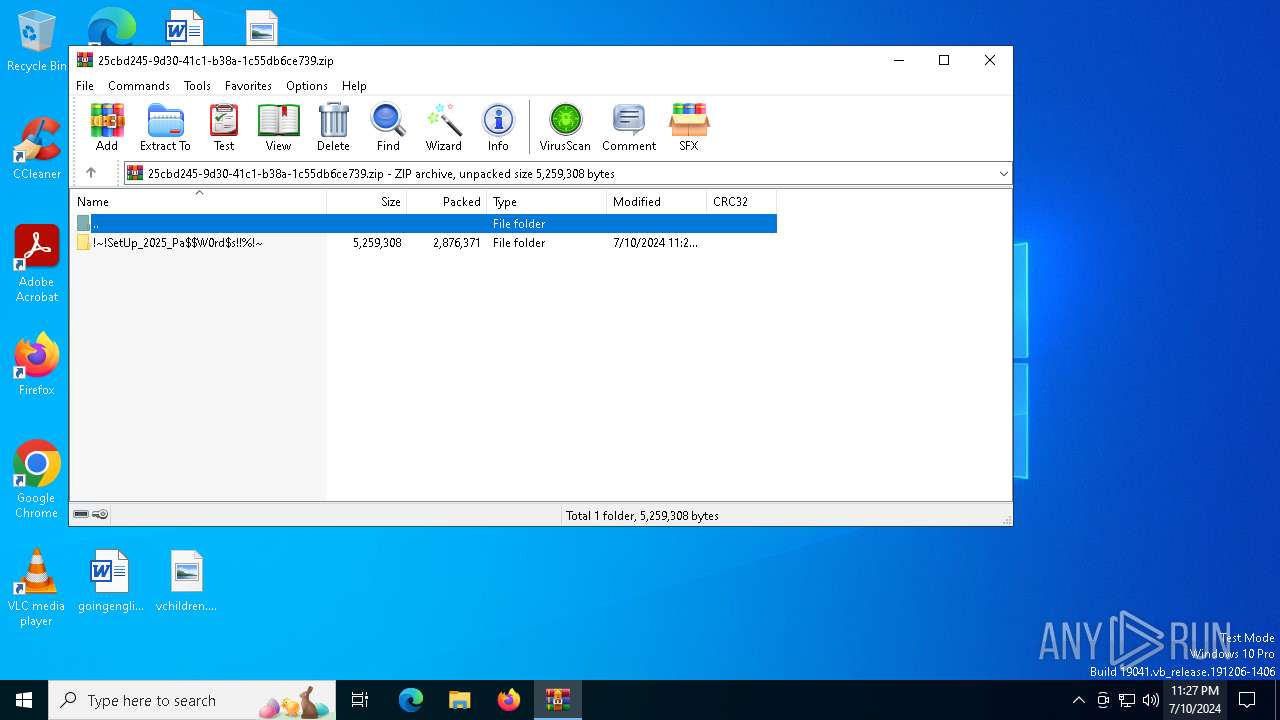
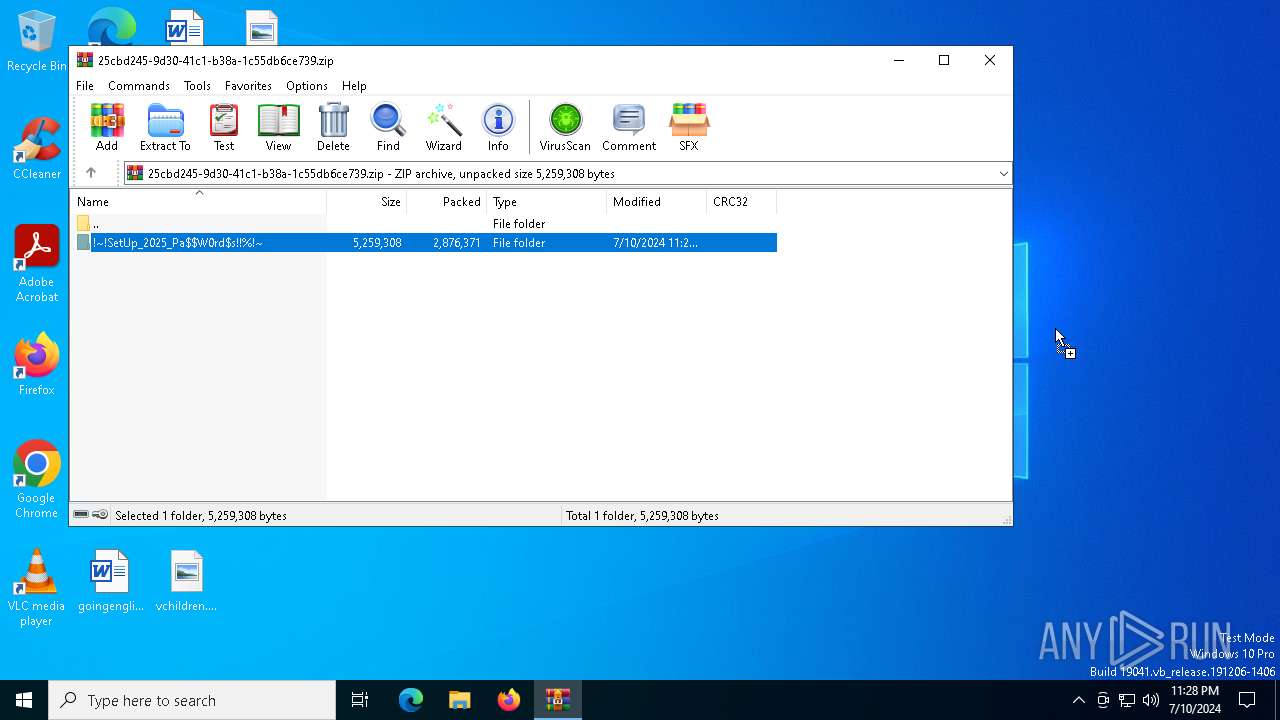
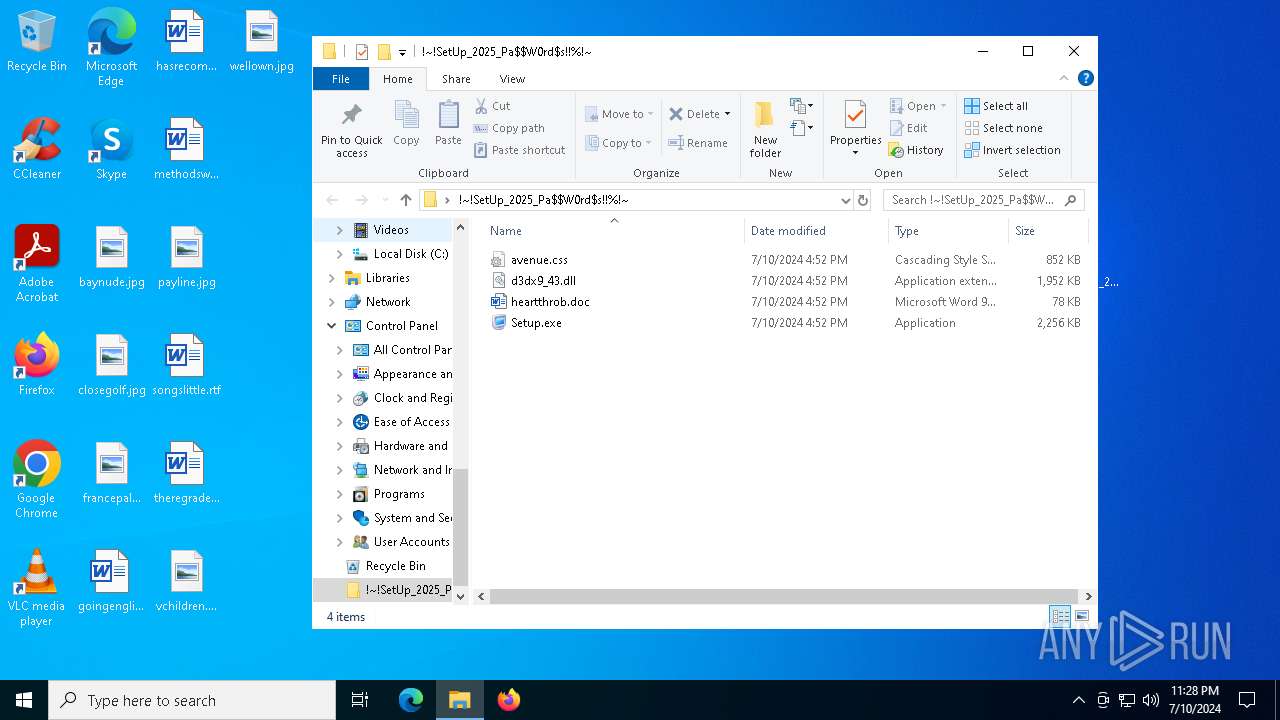
| File name: | !~!SetUp_2025_Pa$W0rd$s!!%!~.zip |
| Full analysis: | https://app.any.run/tasks/25cbd245-9d30-41c1-b38a-1c55db6ce739 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | July 10, 2024, 23:27:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 0BCEB88AED8C6BB2F5D20C050AF530B3 |
| SHA1: | 6EC563E2CC84BD115CA4C325F25860D9C7A57149 |
| SHA256: | EDEF6777BE8DBB15748BCF1332C0A7E49E5D8B8793FF23CCFB41DA2D3FF1C0CC |
| SSDEEP: | 98304:cDHO/pJ5SiENUUiB1YHbpYieHWSOQsEZbOq8fvNpF0aC3N3DMIh+JA1TzCBgbT9D:zg6 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4164)
- Setup.exe (PID: 2704)
- more.com (PID: 752)
LUMMA has been detected (SURICATA)
- SearchIndexer.exe (PID: 6392)
LUMMA has been detected (YARA)
- SearchIndexer.exe (PID: 6392)
HIJACKLOADER has been detected (YARA)
- SearchIndexer.exe (PID: 6392)
- TraceFmt.exe (PID: 6172)
- SearchIndexer.exe (PID: 4372)
- more.com (PID: 752)
Actions looks like stealing of personal data
- SearchIndexer.exe (PID: 6392)
AMADEY has been detected (YARA)
- SearchIndexer.exe (PID: 4372)
Connects to the CnC server
- SearchIndexer.exe (PID: 4372)
AMADEY has been detected (SURICATA)
- SearchIndexer.exe (PID: 4372)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4164)
- Setup.exe (PID: 2704)
- more.com (PID: 752)
Searches for installed software
- SearchIndexer.exe (PID: 6392)
Executable content was dropped or overwritten
- SearchIndexer.exe (PID: 6392)
- Setup.exe (PID: 2704)
- more.com (PID: 752)
Starts application with an unusual extension
- Setup.exe (PID: 2704)
- 69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe (PID: 5236)
- 5D57C09NDIXS9EN7C9D3P.exe (PID: 6824)
Contacting a server suspected of hosting an CnC
- SearchIndexer.exe (PID: 4372)
Starts a Microsoft application from unusual location
- TraceFmt.exe (PID: 6172)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4164)
Checks supported languages
- Setup.exe (PID: 2704)
- more.com (PID: 6380)
- more.com (PID: 752)
- 5D57C09NDIXS9EN7C9D3P.exe (PID: 6824)
- more.com (PID: 3624)
- 69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe (PID: 5236)
- TraceFmt.exe (PID: 6172)
Create files in a temporary directory
- Setup.exe (PID: 2704)
- more.com (PID: 6380)
- SearchIndexer.exe (PID: 6392)
- 69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe (PID: 5236)
- 5D57C09NDIXS9EN7C9D3P.exe (PID: 6824)
- more.com (PID: 752)
- more.com (PID: 3624)
Reads the computer name
- more.com (PID: 6380)
- Setup.exe (PID: 2704)
- more.com (PID: 752)
- 69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe (PID: 5236)
- 5D57C09NDIXS9EN7C9D3P.exe (PID: 6824)
- more.com (PID: 3624)
- TraceFmt.exe (PID: 6172)
Drops the executable file immediately after the start
- SearchIndexer.exe (PID: 6392)
Manual execution by a user
- Setup.exe (PID: 2704)
Creates files or folders in the user directory
- Setup.exe (PID: 2704)
Reads the software policy settings
- SearchIndexer.exe (PID: 6392)
Checks proxy server information
- SearchIndexer.exe (PID: 4372)
Reads security settings of Internet Explorer
- SearchIndexer.exe (PID: 4372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(6392) SearchIndexer.exe
C2 (9)answerrsdo.shop
bouncedgowp.shop
bittercoldzzdwu.shop
radiationnopp.shop
benchillppwo.shop
bargainnykwo.shop
bannngwko.shop
affecthorsedpo.shop
publicitttyps.shop
Amadey
(PID) Process(4372) SearchIndexer.exe
C2downloaddining.com
Strings (123)Content-Disposition: form-data; name="data"; filename="
ar:
/k
DefaultSettings.XResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
abcdefghijklmnopqrstuvwxyz0123456789-_
random
Norton
rb
sd:
Doctor Web
2022
\0000
id:
#
kernel32.dll
.jpg
AVAST Software
"taskkill /f /im "
/h9fmdW7/index.php
lv:
S-%lu-
shutdown -s -t 0
&& Exit"
e0
ProgramData\
\
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
dm:
pc:
av:
st=s
Kaspersky Lab
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
Avira
Startup
exe
|
+++
http://
-unicode-
2016
Programs
\App
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
og:
vs:
/h9fmdW6/index.php
rundll32
d1
un:
AVG
Bitdefender
Content-Type: application/x-www-form-urlencoded
-%lu
"
Content-Type: application/octet-stream
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
VideoID
cmd
cred.dll
<c>
ComputerName
Sophos
GetNativeSystemInfo
Hkbsse.exe
/h9fmdW5/index.php
------
Content-Type: multipart/form-data; boundary=----
Panda Security
" && timeout 1 && del
clip.dll
:::
https://
zip
/quiet
2019
POST
SYSTEM\ControlSet001\Services\BasicDisplay\Video
GET
CurrentBuild
------
f184b295cd
bi:
e2
ProductName
"
360TotalSecurity
Powershell.exe
ESET
DefaultSettings.YResolution
4.31
%-lu
downloaddining2.com
downloaddining3.com
cmd /C RMDIR /s/q
%USERPROFILE%
ps1
dll
/Plugins/
" && ren
<d>
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
cred.dll|clip.dll|
downloaddining.com
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
Comodo
msi
&&
Main
wb
rundll32.exe
Rem
os:
shell32.dll
--
WinDefender
?scr=1
0123456789
e1
-executionpolicy remotesigned -File "
=
r=
&unit=
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:07:11 01:20:14 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | !~!SetUp_2025_Pa$W0rd$s!!%!~/ |
Total processes
149
Monitored processes
14
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 648 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | 69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
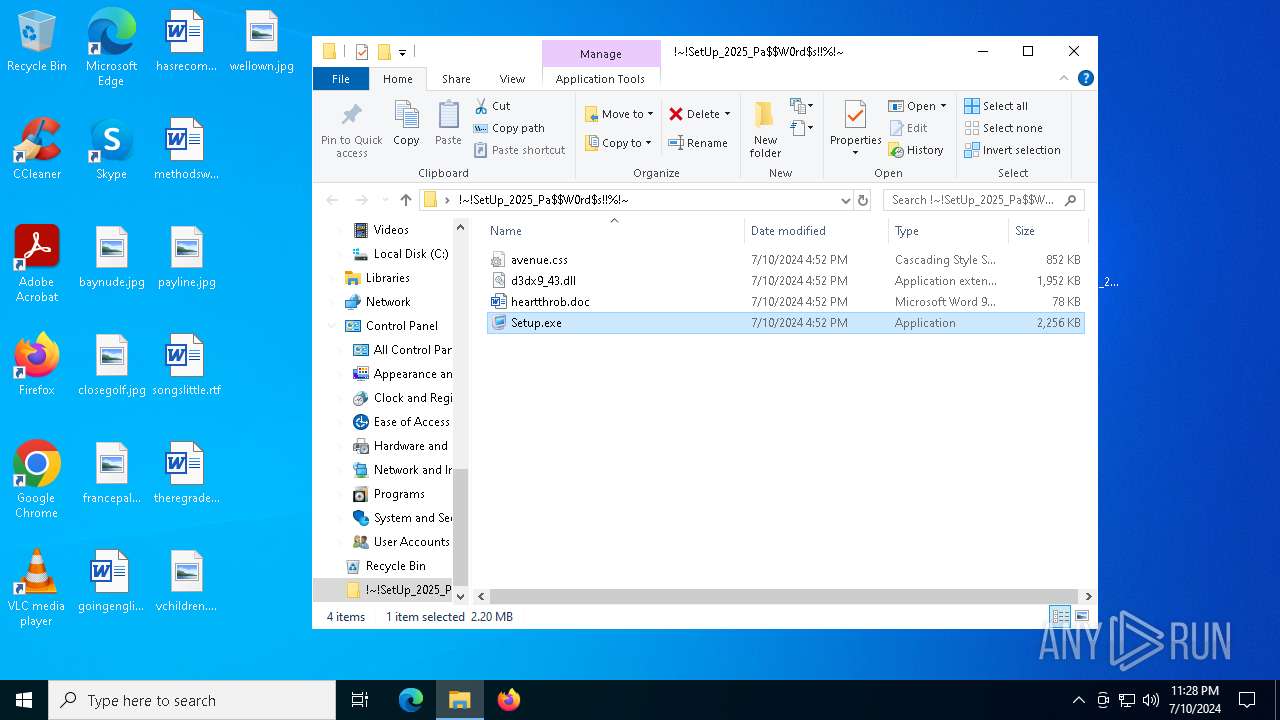
| 2704 | "C:\Users\admin\Desktop\!~!SetUp_2025_Pa$W0rd$s!!%!~\Setup.exe" | C:\Users\admin\Desktop\!~!SetUp_2025_Pa$W0rd$s!!%!~\Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3624 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | 5D57C09NDIXS9EN7C9D3P.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\25cbd245-9d30-41c1-b38a-1c55db6ce739.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4264 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4372 | C:\WINDOWS\SysWOW64\SearchIndexer.exe | C:\Windows\SysWOW64\SearchIndexer.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Indexer Version: 7.0.19041.3758 (WinBuild.160101.0800) Modules
Amadey(PID) Process(4372) SearchIndexer.exe C2downloaddining.com Strings (123)Content-Disposition: form-data; name="data"; filename=" ar: /k DefaultSettings.XResolution SOFTWARE\Microsoft\Windows NT\CurrentVersion abcdefghijklmnopqrstuvwxyz0123456789-_ random Norton rb sd: Doctor Web 2022 \0000 id: # kernel32.dll .jpg AVAST Software "taskkill /f /im " /h9fmdW7/index.php lv: S-%lu- shutdown -s -t 0 && Exit" e0 ProgramData\ \ SOFTWARE\Microsoft\Windows\CurrentVersion\Run dm: pc: av: st=s Kaspersky Lab SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\ Avira Startup exe | +++ http:// -unicode- 2016 Programs \App SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders og: vs: /h9fmdW6/index.php rundll32 d1 un: AVG Bitdefender Content-Type: application/x-www-form-urlencoded -%lu "
Content-Type: application/octet-stream SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName VideoID cmd cred.dll <c> ComputerName Sophos GetNativeSystemInfo Hkbsse.exe /h9fmdW5/index.php ------ Content-Type: multipart/form-data; boundary=---- Panda Security " && timeout 1 && del clip.dll ::: https:// zip /quiet 2019 POST SYSTEM\ControlSet001\Services\BasicDisplay\Video GET CurrentBuild ------ f184b295cd bi: e2 ProductName " 360TotalSecurity Powershell.exe ESET DefaultSettings.YResolution 4.31 %-lu downloaddining2.com downloaddining3.com cmd /C RMDIR /s/q %USERPROFILE% ps1 dll /Plugins/ " && ren <d> SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce cred.dll|clip.dll| downloaddining.com SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders Comodo msi && Main wb rundll32.exe Rem os: shell32.dll -- WinDefender ?scr=1 0123456789 e1 -executionpolicy remotesigned -File " = r= &unit= | |||||||||||||||
| 5236 | "C:\Users\admin\AppData\Local\Temp\69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe" | C:\Users\admin\AppData\Local\Temp\69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Vitaliy Levchenko Software Integrity Level: MEDIUM Description: Icons from File Exit code: 1 Version: 5.1.1.16 Modules
| |||||||||||||||
| 6172 | C:\Users\admin\AppData\Local\Temp\TraceFmt.exe | C:\Users\admin\AppData\Local\Temp\TraceFmt.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Format Message traces to text Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
7 057
Read events
7 027
Write events
30
Delete events
0
Modification events
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\25cbd245-9d30-41c1-b38a-1c55db6ce739.zip | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
6
Suspicious files
8
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6380 | more.com | C:\Users\admin\AppData\Local\Temp\jcbjebcwqbgfge | — | |
MD5:— | SHA256:— | |||
| 752 | more.com | C:\Users\admin\AppData\Local\Temp\cqia | — | |
MD5:— | SHA256:— | |||
| 3624 | more.com | C:\Users\admin\AppData\Local\Temp\ockuffw | — | |
MD5:— | SHA256:— | |||
| 4164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4164.40707\!~!SetUp_2025_Pa$W0rd$s!!%!~\d3dx9_43.dll | executable | |
MD5:520899C7DE9DF32FC7878EEA4DF08A72 | SHA256:0820FDAFEF37CB7FA1AE83D8B1F7C3839C61B6744426831D15C4561468A2E234 | |||
| 2704 | Setup.exe | C:\Users\admin\AppData\Roaming\Piriform\d3dx9_43.dll | executable | |
MD5:520899C7DE9DF32FC7878EEA4DF08A72 | SHA256:0820FDAFEF37CB7FA1AE83D8B1F7C3839C61B6744426831D15C4561468A2E234 | |||
| 2704 | Setup.exe | C:\Users\admin\AppData\Roaming\Piriform\heartthrob.doc | binary | |
MD5:42E6685956CE07BDFE900B44DFDA8555 | SHA256:7F4DC10F712C2D0D4AE5F24E3DEFB4FCBEB1B38A7DD357A7473F954ABE8FAF0D | |||
| 2704 | Setup.exe | C:\Users\admin\AppData\Local\Temp\9b50bf8d | binary | |
MD5:E063020E582AFBA80B04F5F4536E8A94 | SHA256:7FBB10638D4EB44A69DA280B5408A6B84E809CA076A57F26454AC484B43558A6 | |||
| 4164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4164.40707\!~!SetUp_2025_Pa$W0rd$s!!%!~\heartthrob.doc | binary | |
MD5:42E6685956CE07BDFE900B44DFDA8555 | SHA256:7F4DC10F712C2D0D4AE5F24E3DEFB4FCBEB1B38A7DD357A7473F954ABE8FAF0D | |||
| 5236 | 69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe | C:\Users\admin\AppData\Local\Temp\a83416bf | binary | |
MD5:2D89DE7201301ECF1ACB5F760831B62D | SHA256:3339E588643D3E4294C01F3E5E235B9CB3320B1B362820C0371A11D346F0DCFA | |||
| 5236 | 69KCWI9GAC9GWBGP6YQVF78T9XC8A94.exe | C:\Users\admin\AppData\Local\Temp\a7fc8203 | image | |
MD5:75C9ACF117D5752844559D04D8ED42B0 | SHA256:63F235D28E8AE6F68006132ED07A5875E18184DCB8706634B1061B28540245FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
89
DNS requests
27
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4392 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4392 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4372 | SearchIndexer.exe | POST | 404 | 188.114.96.3:80 | http://downloaddining2.com/h9fmdW6/index.php | unknown | — | — | unknown |
4372 | SearchIndexer.exe | POST | 404 | 172.67.208.139:80 | http://downloaddining3.com/h9fmdW7/index.php | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
7084 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
5332 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3992 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
8 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1832 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2476 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4656 | SearchApp.exe | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4392 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
4392 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6392 | SearchIndexer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
4372 | SearchIndexer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
4372 | SearchIndexer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
4372 | SearchIndexer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
1 ETPRO signatures available at the full report