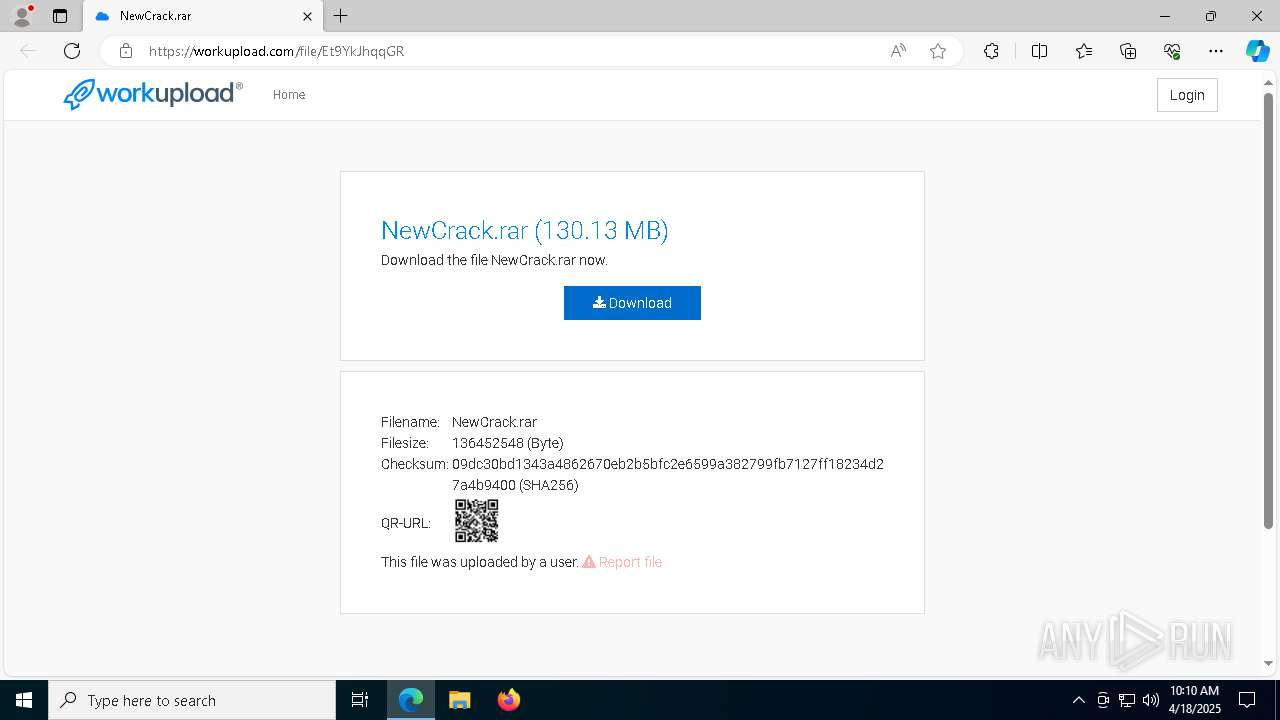
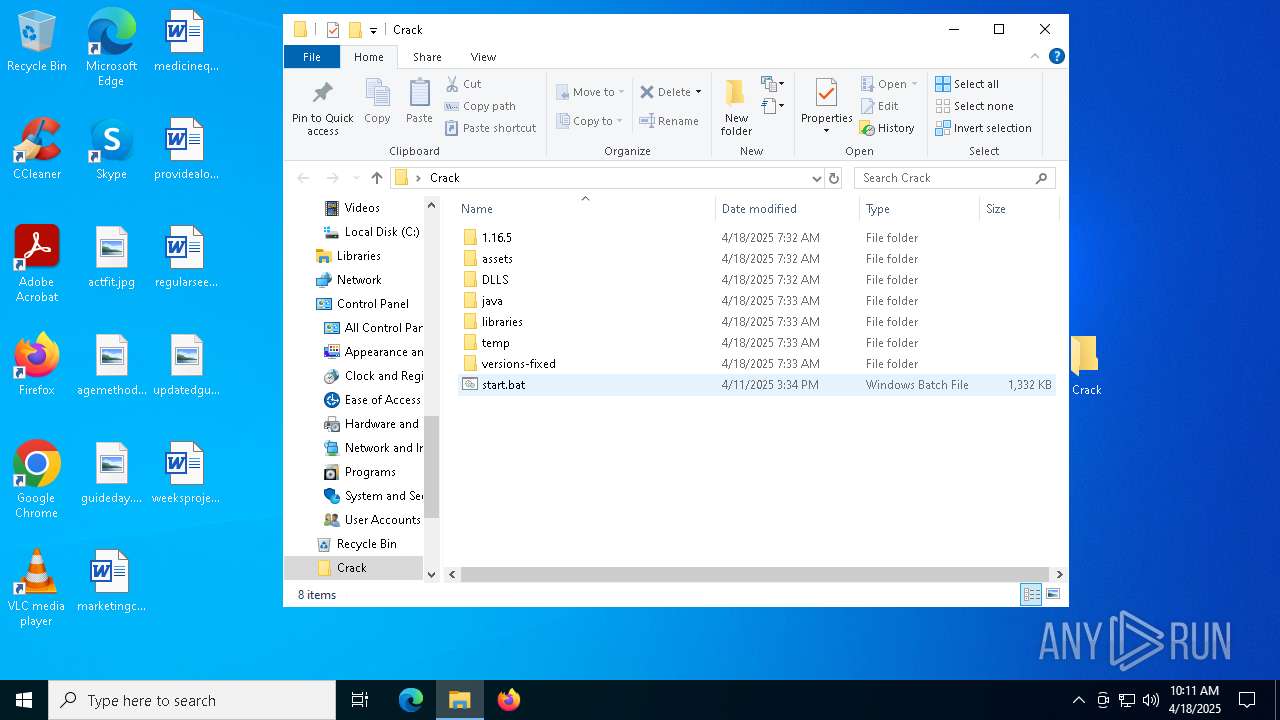
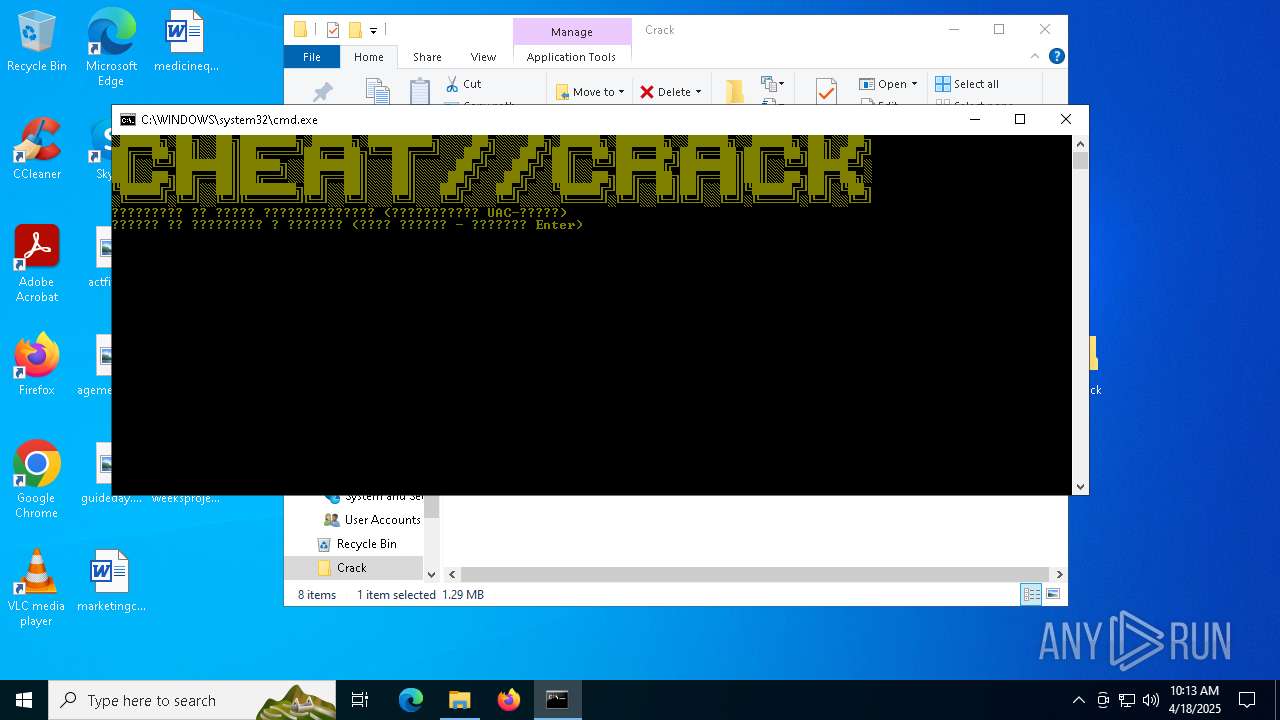
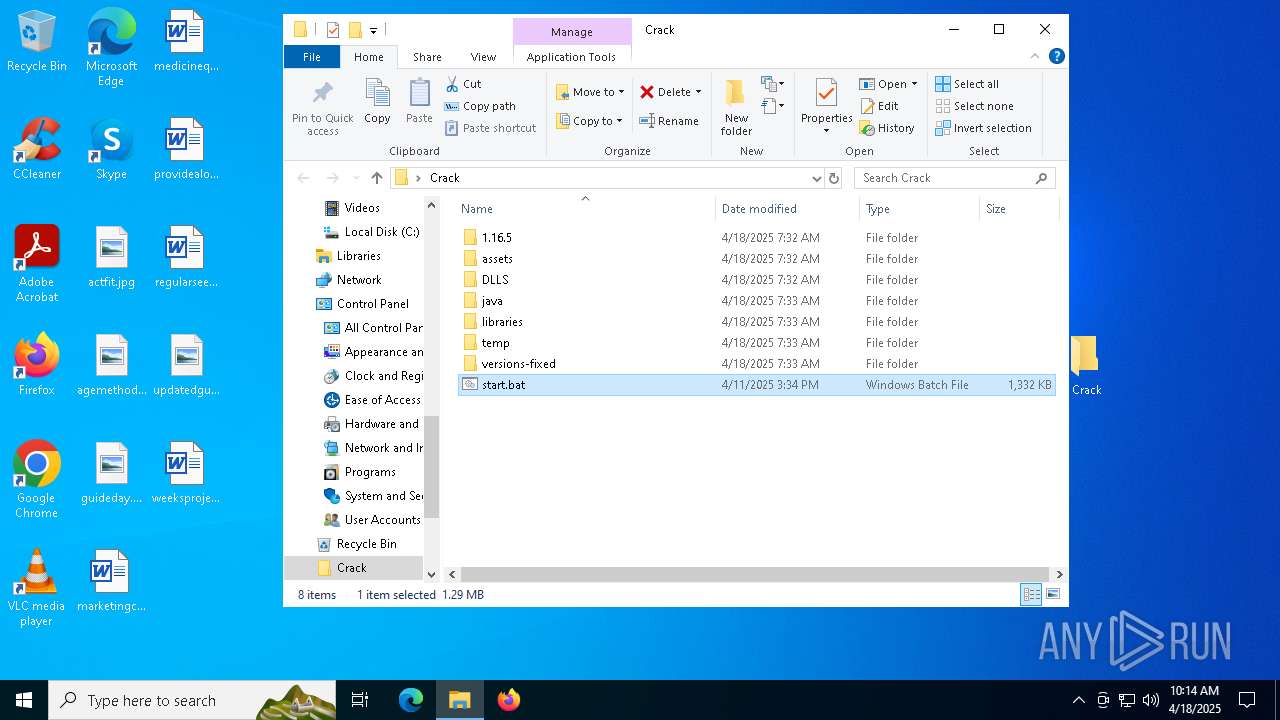
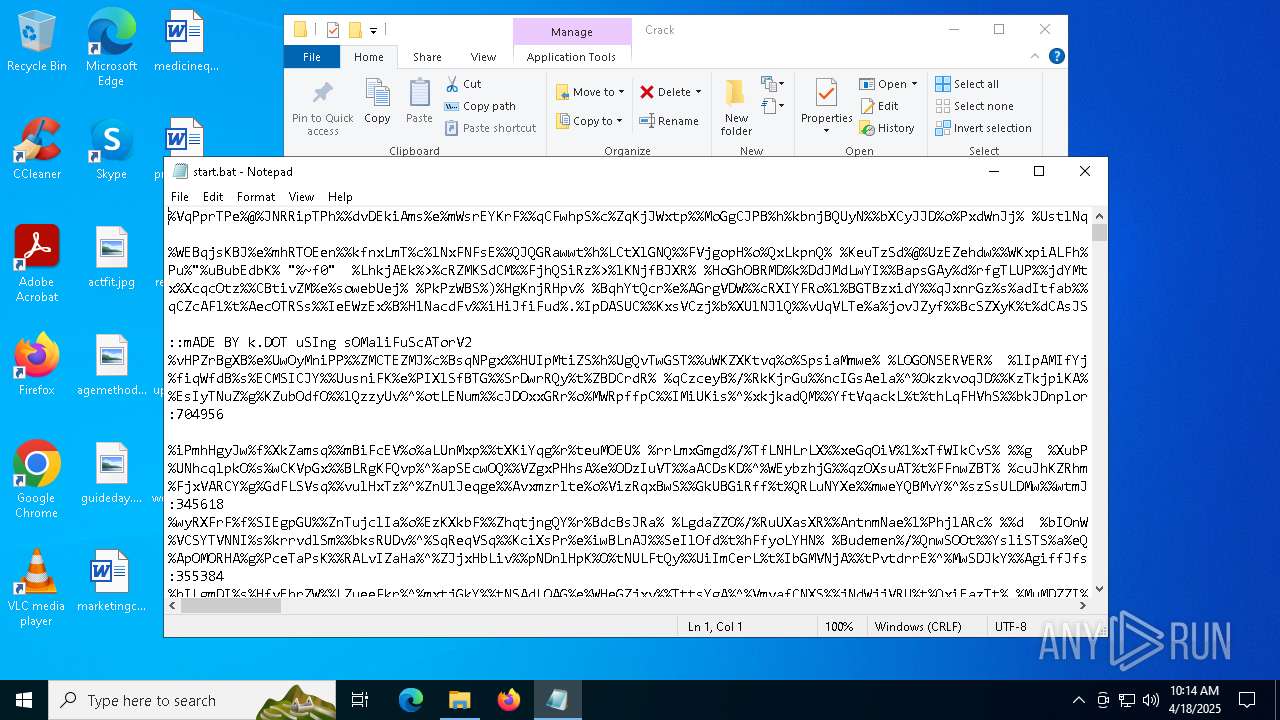
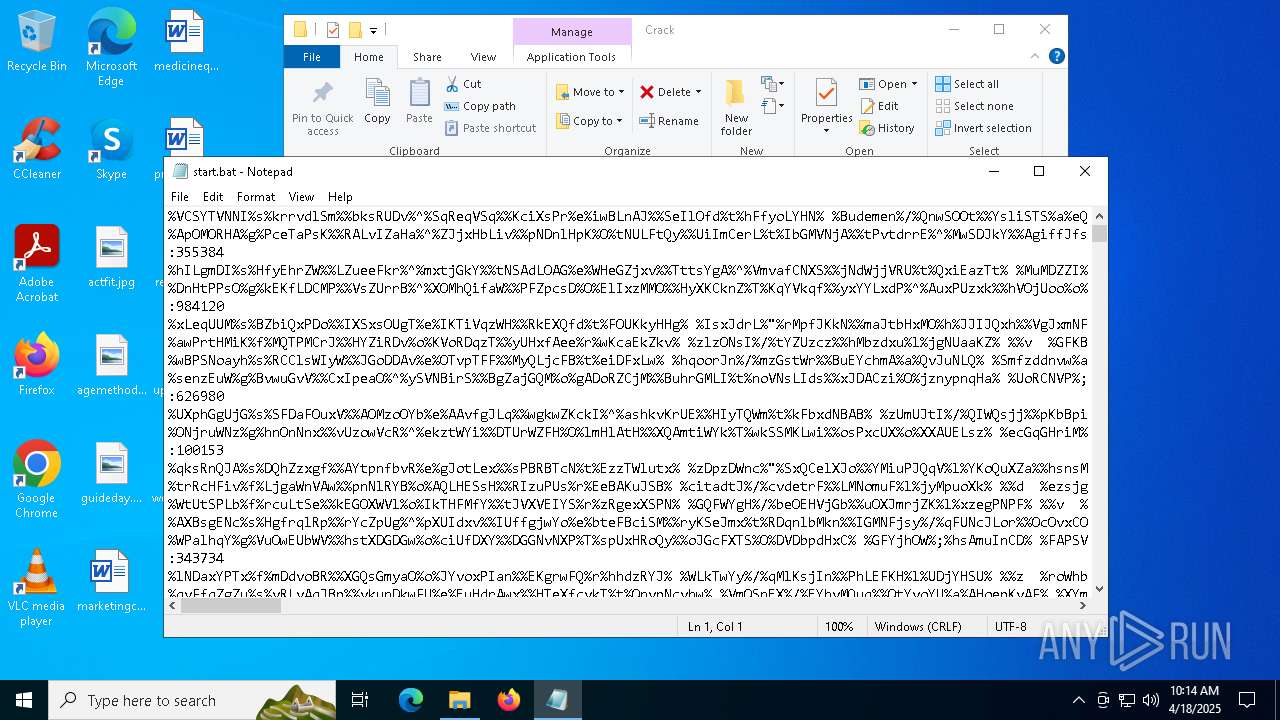
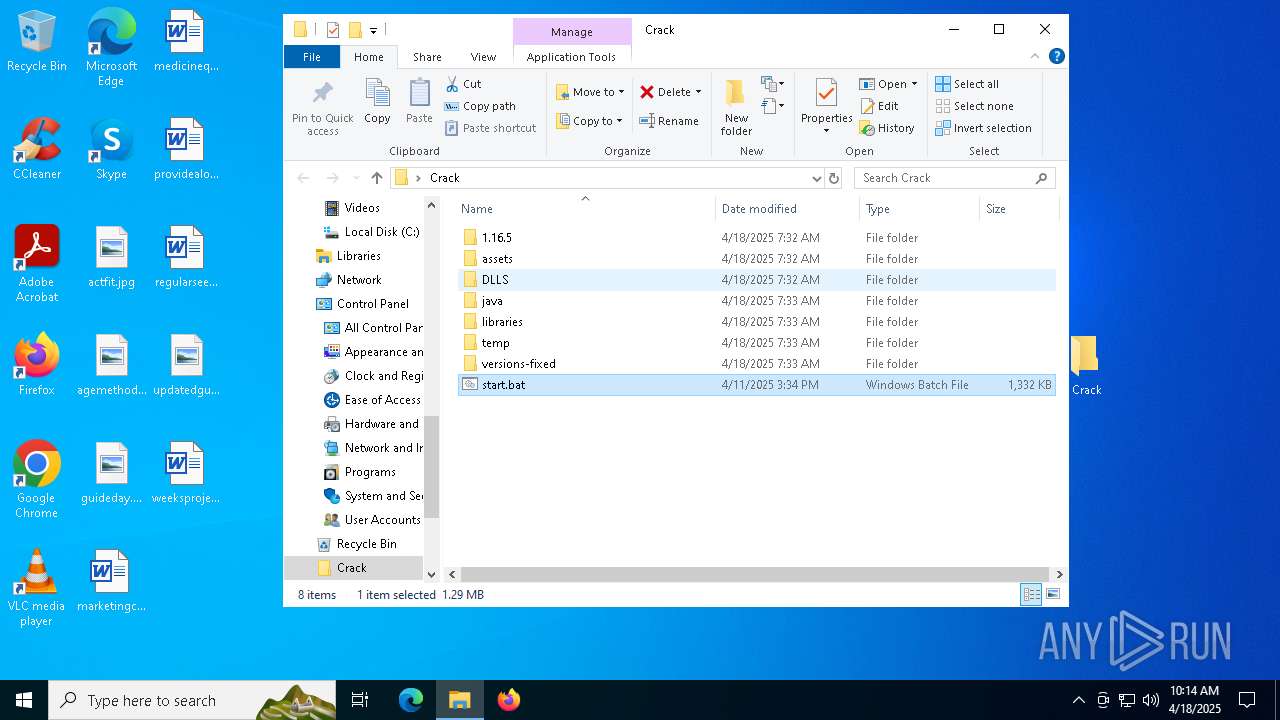
| URL: | https://workupload.com/file/Et9YkJhqqGR |
| Full analysis: | https://app.any.run/tasks/17b97e4c-18f6-4d2c-9cce-24554d2db53b |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | April 18, 2025, 10:10:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0F1C46E34145BB9B28FB992D5879692A |
| SHA1: | EB2010E178401F836478792167E117801DE88574 |
| SHA256: | ED9EABB8555B00F62C2A671F6174B11BFAF224C5580846C9967FB3B9629A01E6 |
| SSDEEP: | 3:N8bXOrZXFjU:2ithU |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 8504)
- powershell.exe (PID: 8004)
Changes Windows Defender settings
- cmd.exe (PID: 3884)
- cmd.exe (PID: 8988)
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3884)
- cmd.exe (PID: 8988)
UAC/LUA settings modification
- dllhost.exe (PID: 7580)
Downloads files via BITSADMIN.EXE
- cmd.exe (PID: 8988)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 8880)
Adds extension to the Windows Defender exclusion list
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
- cmd.exe (PID: 3884)
Vulnerable driver has been detected
- explorer.exe (PID: 2416)
Application was injected by another process
- lsass.exe (PID: 756)
- svchost.exe (PID: 468)
- svchost.exe (PID: 1260)
- svchost.exe (PID: 1252)
- svchost.exe (PID: 1044)
- svchost.exe (PID: 1232)
- svchost.exe (PID: 1352)
- svchost.exe (PID: 1288)
- svchost.exe (PID: 1416)
- svchost.exe (PID: 1444)
- svchost.exe (PID: 1552)
- svchost.exe (PID: 1524)
- svchost.exe (PID: 1772)
- svchost.exe (PID: 1652)
- svchost.exe (PID: 1784)
- svchost.exe (PID: 1792)
- svchost.exe (PID: 1904)
- svchost.exe (PID: 1892)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 2196)
- svchost.exe (PID: 2172)
- svchost.exe (PID: 2292)
- svchost.exe (PID: 2068)
- svchost.exe (PID: 2396)
- svchost.exe (PID: 2536)
- svchost.exe (PID: 2544)
- svchost.exe (PID: 2448)
- svchost.exe (PID: 2880)
- svchost.exe (PID: 2624)
- svchost.exe (PID: 2584)
- spoolsv.exe (PID: 2732)
- svchost.exe (PID: 3084)
- svchost.exe (PID: 2920)
- svchost.exe (PID: 3104)
- svchost.exe (PID: 2932)
- OfficeClickToRun.exe (PID: 3112)
- svchost.exe (PID: 3860)
- svchost.exe (PID: 3564)
- svchost.exe (PID: 4312)
- svchost.exe (PID: 4508)
- dllhost.exe (PID: 5880)
- svchost.exe (PID: 1572)
- svchost.exe (PID: 3196)
- svchost.exe (PID: 3216)
- svchost.exe (PID: 3184)
- svchost.exe (PID: 3232)
- svchost.exe (PID: 3284)
- svchost.exe (PID: 3812)
- svchost.exe (PID: 4292)
- svchost.exe (PID: 860)
- svchost.exe (PID: 6024)
- dwm.exe (PID: 6568)
- svchost.exe (PID: 4952)
- sihost.exe (PID: 4984)
- explorer.exe (PID: 5492)
- svchost.exe (PID: 4544)
- svchost.exe (PID: 6608)
- RuntimeBroker.exe (PID: 6160)
- dllhost.exe (PID: 6896)
- RuntimeBroker.exe (PID: 5368)
- ctfmon.exe (PID: 956)
- RuntimeBroker.exe (PID: 1036)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 1684)
- winlogon.exe (PID: 6648)
- uhssvc.exe (PID: 648)
- dllhost.exe (PID: 6176)
- svchost.exe (PID: 6544)
- audiodg.exe (PID: 6168)
- svchost.exe (PID: 4844)
- svchost.exe (PID: 5416)
- svchost.exe (PID: 2560)
- svchost.exe (PID: 6180)
- RuntimeBroker.exe (PID: 8128)
- WmiPrvSE.exe (PID: 8868)
- ApplicationFrameHost.exe (PID: 6952)
- svchost.exe (PID: 4684)
- UserOOBEBroker.exe (PID: 1248)
- svchost.exe (PID: 4916)
- WmiPrvSE.exe (PID: 8700)
- WmiPrvSE.exe (PID: 3620)
- svchost.exe (PID: 7560)
- svchost.exe (PID: 5304)
- taskhostw.exe (PID: 8328)
- svchost.exe (PID: 1020)
- consent.exe (PID: 8896)
- WerFault.exe (PID: 9128)
- svchost.exe (PID: 1988)
Runs injected code in another process
- dialer.exe (PID: 9108)
- dialer.exe (PID: 9140)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
Adds process to the Windows Defender exclusion list
- cmd.exe (PID: 3884)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1272)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1272)
- curl.exe (PID: 7944)
- explorerS.exe (PID: 7948)
- WerFault.exe (PID: 6248)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 5492)
- cmd.exe (PID: 4300)
- powershell.exe (PID: 8180)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- powershell.exe (PID: 8968)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 7776)
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
Executing commands from a ".bat" file
- explorer.exe (PID: 5492)
- powershell.exe (PID: 8180)
- powershell.exe (PID: 8968)
Application launched itself
- cmd.exe (PID: 4300)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 7776)
Starts application with an unusual extension
- cmd.exe (PID: 4300)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 7776)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 4300)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 7776)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 4300)
- net.exe (PID: 8004)
- cmd.exe (PID: 3884)
- net.exe (PID: 2516)
- cmd.exe (PID: 1020)
- net.exe (PID: 8956)
- cmd.exe (PID: 8988)
- net.exe (PID: 6132)
- cmd.exe (PID: 7776)
- net.exe (PID: 4380)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 4300)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 7776)
Executes script without checking the security policy
- powershell.exe (PID: 5132)
- powershell.exe (PID: 7176)
- powershell.exe (PID: 7672)
- powershell.exe (PID: 8948)
- powershell.exe (PID: 9056)
- powershell.exe (PID: 7844)
- powershell.exe (PID: 7308)
- powershell.exe (PID: 8776)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 8112)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 8080)
- powershell.exe (PID: 7636)
- powershell.exe (PID: 7988)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 8556)
- powershell.exe (PID: 4212)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 7872)
- powershell.exe (PID: 3028)
- powershell.exe (PID: 8980)
- powershell.exe (PID: 5256)
- powershell.exe (PID: 7968)
- powershell.exe (PID: 7800)
- powershell.exe (PID: 8824)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 3024)
- powershell.exe (PID: 5868)
- powershell.exe (PID: 7884)
- powershell.exe (PID: 5256)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 8372)
Starts process via Powershell
- powershell.exe (PID: 8180)
- powershell.exe (PID: 8968)
- powershell.exe (PID: 7660)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 4300)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 7776)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4300)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 7776)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4300)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 8988)
- explorerS.exe (PID: 7948)
- cmd.exe (PID: 7776)
- explorer.exe (PID: 2416)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3884)
- cmd.exe (PID: 8988)
Adds/modifies Windows certificates
- lsass.exe (PID: 756)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3884)
- cmd.exe (PID: 8988)
Executable content was dropped or overwritten
- curl.exe (PID: 5304)
- curl.exe (PID: 7688)
- curl.exe (PID: 7944)
- curl.exe (PID: 8776)
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 3884)
- cmd.exe (PID: 8988)
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
The process connected to a server suspected of theft
- Launcher.exe (PID: 7736)
- Launcher.exe (PID: 7720)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Launcher.exe (PID: 7736)
- Launcher.exe (PID: 7720)
Executes application which crashes
- start.exe (PID: 6416)
- findstr.exe (PID: 8992)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 7012)
- powershell.exe (PID: 8364)
Starts SC.EXE for service management
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
Stops a currently running service
- sc.exe (PID: 8896)
- sc.exe (PID: 7864)
- sc.exe (PID: 7732)
- sc.exe (PID: 8096)
- sc.exe (PID: 7536)
- sc.exe (PID: 8972)
- sc.exe (PID: 4212)
- sc.exe (PID: 4244)
- sc.exe (PID: 3396)
- sc.exe (PID: 5436)
- sc.exe (PID: 6820)
Process uninstalls Windows update
- wusa.exe (PID: 3124)
- wusa.exe (PID: 8748)
Script adds exclusion extension to Windows Defender
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
- cmd.exe (PID: 3884)
Manipulates environment variables
- powershell.exe (PID: 6136)
- powershell.exe (PID: 7260)
Uses powercfg.exe to modify the power settings
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
Windows service management via SC.EXE
- sc.exe (PID: 7556)
- sc.exe (PID: 5960)
Creates a new Windows service
- sc.exe (PID: 5256)
Executes as Windows Service
- explorer.exe (PID: 2416)
Drops a system driver (possible attempt to evade defenses)
- explorer.exe (PID: 2416)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
Script adds exclusion process to Windows Defender
- cmd.exe (PID: 3884)
The process executes VB scripts
- cmd.exe (PID: 3884)
INFO
Reads the computer name
- identity_helper.exe (PID: 8180)
- identity_helper.exe (PID: 632)
- curl.exe (PID: 5304)
- Launcher.exe (PID: 7736)
- curl.exe (PID: 7688)
- start.exe (PID: 6416)
- curl.exe (PID: 7944)
- explorer.exe (PID: 2236)
- curl.exe (PID: 8776)
- curl.exe (PID: 6652)
- Launcher.exe (PID: 7720)
- curl.exe (PID: 6476)
Reads Environment values
- identity_helper.exe (PID: 8180)
- identity_helper.exe (PID: 632)
Checks supported languages
- identity_helper.exe (PID: 8180)
- identity_helper.exe (PID: 632)
- chcp.com (PID: 4620)
- chcp.com (PID: 8952)
- chcp.com (PID: 5056)
- chcp.com (PID: 5960)
- curl.exe (PID: 5304)
- chcp.com (PID: 8172)
- chcp.com (PID: 1628)
- Launcher.exe (PID: 7736)
- curl.exe (PID: 7688)
- chcp.com (PID: 7836)
- chcp.com (PID: 7720)
- start.exe (PID: 6416)
- explorer.exe (PID: 2236)
- curl.exe (PID: 7944)
- curl.exe (PID: 8776)
- curl.exe (PID: 6652)
- chcp.com (PID: 6676)
- chcp.com (PID: 7800)
- explorerS.exe (PID: 7948)
- explorer.exe (PID: 2416)
- Launcher.exe (PID: 7720)
- curl.exe (PID: 6476)
- uhssvc.exe (PID: 648)
- java.exe (PID: 7660)
Application launched itself
- msedge.exe (PID: 5048)
- msedge.exe (PID: 9120)
Creates files or folders in the user directory
- lsass.exe (PID: 756)
- explorer.exe (PID: 5492)
- WerFault.exe (PID: 2392)
- dllhost.exe (PID: 6896)
- WerFault.exe (PID: 6248)
Reads security settings of Internet Explorer
- svchost.exe (PID: 2536)
- explorer.exe (PID: 5492)
- RuntimeBroker.exe (PID: 5368)
- dllhost.exe (PID: 7260)
- consent.exe (PID: 8896)
- notepad.exe (PID: 8624)
Reads the time zone
- WmiPrvSE.exe (PID: 8700)
- svchost.exe (PID: 2396)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
- OfficeClickToRun.exe (PID: 3112)
Manual execution by a user
- WinRAR.exe (PID: 1272)
- cmd.exe (PID: 4300)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 7776)
- notepad.exe (PID: 8624)
- cmd.exe (PID: 2968)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1272)
The sample compiled with english language support
- WinRAR.exe (PID: 1272)
- curl.exe (PID: 8776)
- explorerS.exe (PID: 7948)
Reads the software policy settings
- slui.exe (PID: 8096)
- lsass.exe (PID: 756)
- Launcher.exe (PID: 7736)
- slui.exe (PID: 8656)
- consent.exe (PID: 8896)
- Launcher.exe (PID: 7720)
Changes the display of characters in the console
- cmd.exe (PID: 4300)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 7776)
Reads Internet Explorer settings
- mshta.exe (PID: 7548)
- mshta.exe (PID: 7472)
- mshta.exe (PID: 6820)
- mshta.exe (PID: 7932)
- mshta.exe (PID: 7984)
- mshta.exe (PID: 7256)
Creates files in the program directory
- cmd.exe (PID: 3884)
- curl.exe (PID: 5304)
- curl.exe (PID: 7688)
- svchost.exe (PID: 7560)
- curl.exe (PID: 7944)
- cmd.exe (PID: 8988)
- curl.exe (PID: 8776)
- explorerS.exe (PID: 7948)
Execution of CURL command
- cmd.exe (PID: 3884)
- cmd.exe (PID: 8988)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 232)
- powershell.exe (PID: 8612)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 6136)
- powershell.exe (PID: 3968)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 7260)
- powershell.exe (PID: 7688)
- powershell.exe (PID: 960)
- powershell.exe (PID: 7792)
- powershell.exe (PID: 9112)
- powershell.exe (PID: 3016)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 232)
- powershell.exe (PID: 8612)
- powershell.exe (PID: 7012)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 6136)
- powershell.exe (PID: 3968)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 7260)
- powershell.exe (PID: 7688)
- powershell.exe (PID: 8364)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 960)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 9112)
- powershell.exe (PID: 7792)
Reads the machine GUID from the registry
- Launcher.exe (PID: 7736)
- Launcher.exe (PID: 7720)
Disables trace logs
- Launcher.exe (PID: 7736)
- powershell.exe (PID: 7012)
- powershell.exe (PID: 8364)
- Launcher.exe (PID: 7720)
Checks proxy server information
- Launcher.exe (PID: 7736)
- slui.exe (PID: 8656)
- powershell.exe (PID: 7012)
- powershell.exe (PID: 8364)
- Launcher.exe (PID: 7720)
Attempting to use instant messaging service
- svchost.exe (PID: 2196)
- Launcher.exe (PID: 7736)
The sample compiled with japanese language support
- explorer.exe (PID: 2416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
722
Monitored processes
663
Malicious processes
102
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | doskey DATE=MODE | C:\Windows\System32\doskey.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Keyboard History Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | findstr /i "echo" "C:\Users\admin\Desktop\Crack\start.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | powershell -Command "Add-MpPreference -ExclusionPath 'C:\ProgramData\Crack\start.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | findstr /i "echo" "C:\Users\admin\Desktop\Crack\start.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | timeout 0 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 468 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | findstr /i "echo" "C:\Users\admin\Desktop\Crack\start.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4388 --field-trial-handle=2380,i,8915028085540337636,7201168919128313094,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 644 | findstr /i "echo" "C:\Users\admin\Desktop\Crack\start.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | "C:\Program Files\Microsoft Update Health Tools\uhssvc.exe" | C:\Program Files\Microsoft Update Health Tools\uhssvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Update Health Service Version: 10.0.19041.3626 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
481 984
Read events
480 704
Write events
1 025
Delete events
255
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000060346 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:000000000005028A |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D6B2DD02A1912F00 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 02B4E702A1912F00 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394054 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6EB43B3F-AA80-4697-8E33-6E11C3CAD45E} | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394054 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {CED822C7-2600-4BF1-8DC9-52AB02B548C7} | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394054 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {4C88D919-95A1-40BA-8014-1424670A6FC1} | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394054 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {240D1478-CF53-42E8-9B93-95FB84DCC7DA} | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394054 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E113F4C1-B01E-4216-99F7-9159F7C1E646} | |||
| (PID) Process: | (1260) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\UpdateOrchestrator |
| Operation: | write | Name: | SD |
Value: 0100049C5C000000680000000000000014000000020048000300000000001400FF011F0001010000000000051200000000001400A900120001010000000000051300000000001800A900120001020000000000052000000020020000010100000000000512000000010100000000000512000000 | |||
Executable files
140
Suspicious files
709
Text files
476
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b4ea.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b4ea.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b4ea.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b509.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b4fa.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
164
DNS requests
88
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8652 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8652 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
856 | svchost.exe | HEAD | 200 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4a14e89f-4126-4b0a-8347-8c40c8e643a4?P1=1745356202&P2=404&P3=2&P4=iT%2bjbqtcvSNJL2oowRnP4gfqmnwiSNY%2bjMEuUzmVLu2mhyYjzUicTsOp%2f0L3pWvJTOLVamaDJtKPjzlVgIHXOw%3d%3d | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5048 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7332 | msedge.exe | 142.250.186.98:443 | googleads.g.doubleclick.net | — | — | whitelisted |
7332 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7332 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7332 | msedge.exe | 49.13.126.162:443 | t.workupload.com | Hetzner Online GmbH | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
workupload.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7736 | Launcher.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
7736 | Launcher.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
7736 | Launcher.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Telegram |
2196 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |
7720 | Launcher.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
7720 | Launcher.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
7720 | Launcher.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Telegram |